Configurar a reflexão de serviço multicast no Nexus 3000
Opções de download
Linguagem imparcial
O conjunto de documentação deste produto faz o possível para usar uma linguagem imparcial. Para os fins deste conjunto de documentação, a imparcialidade é definida como uma linguagem que não implica em discriminação baseada em idade, deficiência, gênero, identidade racial, identidade étnica, orientação sexual, status socioeconômico e interseccionalidade. Pode haver exceções na documentação devido à linguagem codificada nas interfaces de usuário do software do produto, linguagem usada com base na documentação de RFP ou linguagem usada por um produto de terceiros referenciado. Saiba mais sobre como a Cisco está usando a linguagem inclusiva.
Sobre esta tradução
A Cisco traduziu este documento com a ajuda de tecnologias de tradução automática e humana para oferecer conteúdo de suporte aos seus usuários no seu próprio idioma, independentemente da localização. Observe que mesmo a melhor tradução automática não será tão precisa quanto as realizadas por um tradutor profissional. A Cisco Systems, Inc. não se responsabiliza pela precisão destas traduções e recomenda que o documento original em inglês (link fornecido) seja sempre consultado.
Contents
Introdução
Este documento descreve como configurar e verificar o recurso Service Refletion nos switches Cisco Nexus 3000 Series (modo regular).
Pré-requisitos
Requisitos
Recomendações gerais de que você tenha conhecimento destes tópicos:
- Multicast independente de protocolo (PIM)
- Abra o protocolo OSPF
- Tradução de Endereço de Rede (NAT)
- Protocolo de Gerenciamento de Grupos Internet (IGMP - Internet Group Management Protocol)
Componentes Utilizados
As informações neste documento são baseadas nestas versões de software e hardware:
| Sw1# |
N9K-C93180YC-FX |
NXOS: versão 9.3(5) |
| Sw2# |
N3K-C3548P-XL |
NXOS: versão 7.0(3)I7(9) |
| Sw3# |
N3K-C3172TQ-10GT |
NXOS: versão 7.0(3)I7(9) |
As informações neste documento foram criadas a partir de dispositivos em um ambiente de laboratório específico. Todos os dispositivos utilizados neste documento foram iniciados com uma configuração (padrão) inicial. Se a rede estiver ativa, certifique-se de que você entenda o impacto potencial de qualquer comando.
Informações de Apoio
Plataformas Cisco Nexus 3k suportadas
O recurso de reflexão de serviço multicast é suportado apenas nas plataformas Cisco Nexus 3548-X da versão 7.0(3)I7(2).
Métodos suportados de reflexão de serviço
NAT Multicast de modo regular
No modo regular, os pacotes de entrada como interfaces S1, G1 são convertidos em interfaces S2, G2 e o endereço Media Access Control (MAC) de destino do pacote de saída é convertido como o endereço MAC multicast da interface G2 (por exemplo, o grupo convertido).
Fast-pass e Fast-pass com NAT multicast sem regravação
No modo de passagem rápida, as interfaces S1, G1 são convertidas em interfaces S2, G2 e o endereço MAC destino do pacote de saída tem o endereço MAC multicast que corresponde à interface G1 (por exemplo, o endereço MAC do grupo pré-convertido).
Configurar
Topologia
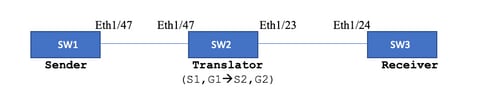
Grupo nativo: 239.194.169.1 (G1)
Grupo traduzido: 233.193.40.196 (G2)
Fonte original: 10.11.11.1 (S1)
Fonte traduzida: 172.16.0.1. (S2)
Configuração
Configuração do switch 1 (remetente)
SW1# show run int eth1/47
interface Ethernet1/47
no switchport
ip address 10.11.11.1/24
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
SW1# show run ospf
feature ospf
router ospf 1
router-id 192.168.1.1
interface Ethernet1/47
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
SW1# show run pim
feature pim
ip pim rp-address 10.10.10.10 group-list 239.194.169.1/32
ip pim ssm range 232.0.0.0/8
interface Ethernet1/47
ip pim sparse-modeConfiguração do Switch 2 (Tradutor)
SW2# show run int eth 1/23,eth1/47
interface Ethernet1/23
no switchport
ip address 10.0.0.1/24
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
no shutdown
interface Ethernet1/47
no switchport
ip address 10.11.11.2/24
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
no shutdown
SW2# show run int lo0,lo411
interface loopback0
ip address 10.10.10.10/32
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
interface loopback411
ip address 172.16.0.1/32
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
ip igmp join-group 239.194.169.1
SW2# show run ospf
feature ospf
router ospf 1
router-id 192.168.1.2
interface loopback0
ip router ospf 1 area 0.0.0.0
interface loopback411
ip router ospf 1 area 0.0.0.0
interface Ethernet1/23
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
interface Ethernet1/47
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
SW2# show run pim
feature pim
ip pim rp-address 10.10.10.10 group-list 239.194.169.1/32
ip pim rp-address 172.16.0.1 group-list 233.193.40.196/32
ip pim ssm range 232.0.0.0/8
interface loopback0
ip pim sparse-mode
interface loopback411
ip pim sparse-mode
interface Ethernet1/23
ip pim sparse-mode
interface Ethernet1/47
ip pim sparse-mode
ip service-reflect mode regular
ip service-reflect destination 239.194.169.1 to 233.193.40.196 mask-len 32 source 172.16.0.1
hardware profile multicast service-reflect port 7
Configuração do switch 3 (receptor)
SW3# show run int eth 1/24
interface Ethernet1/24
ip address 10.0.0.2/24
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
ip igmp join-group 233.193.40.196
no shutdown
SW3# show run ospf
feature ospf
router ospf 1
router-id 192.168.1.3
interface Ethernet1/24
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
SW3# show run pim
feature pim
ip pim rp-address 172.16.0.1 group-list 233.193.40.196/32
ip pim ssm range 232.0.0.0/8
interface Ethernet1/24
ip pim sparse-modeVerificar
Use esta seção para confirmar se a sua configuração funciona corretamente.
Verificar o recurso de reflexão do serviço
Verificação do Switch 1
SW1# show ip mroute
IP Multicast Routing Table for VRF "default"
(*, 232.0.0.0/8), uptime: 3w6d, pim ip
Incoming interface: Null, RPF nbr: 0.0.0.0
Outgoing interface list: (count: 0)
(10.11.11.1/32, 239.194.169.1/32), uptime: 00:06:57, pim ip
Incoming interface: Ethernet1/47, RPF nbr: 10.11.11.1
Outgoing interface list: (count: 1)
Ethernet1/47, uptime: 00:06:57, pim, (RPF)
Verificação do Switch 2
SW2# show ip mroute
IP Multicast Routing Table for VRF "default"
(*, 232.0.0.0/8), uptime: 00:04:39, pim ip
Incoming interface: Null, RPF nbr: 0.0.0.0
Outgoing interface list: (count: 0)
(*, 233.193.40.196/32), uptime: 00:04:11, pim ip
Incoming interface: loopback411, RPF nbr: 172.16.0.1 <-- Translation (ingress) Loopback interface
Outgoing interface list: (count: 1)
Ethernet1/23, uptime: 00:03:59, pim <-- Egress interface for S2,G2
(172.16.0.1/32, 233.193.40.196/32), uptime: 00:00:15, ip mrib pim
Incoming interface: loopback411, RPF nbr: 172.16.0.1
Outgoing interface list: (count: 1)
Ethernet1/23, uptime: 00:00:15, pim
(*, 239.194.169.1/32), uptime: 00:04:34, static pim ip <-- (The NAT router would pull the traffic by using a (*,G) join on loopback )
Incoming interface: loopback0, RPF nbr: 10.10.10.10
Outgoing interface list: (count: 1)
loopback411, uptime: 00:04:34, static <-- Translation (egress) Loopback interface
(10.11.11.1/32, 239.194.169.1/32), uptime: 00:00:17, ip mrib pim
Incoming interface: Ethernet1/47, RPF nbr: 10.11.11.1, internal <-- Ingress interface for S1,G1
Outgoing interface list: (count: 1)
loopback411, uptime: 00:00:17, mrib
SW2# show ip mroute sr <-- (Only SR nat routes)
IP Multicast Routing Table for VRF "default"
(*, 239.194.169.1/32), uptime: 00:09:29, static pim ip
NAT Mode: Ingress
NAT Route Type: Pre
Incoming interface: loopback0, RPF nbr: 10.10.10.10
Translation list: (count: 1)
SR: (172.16.0.1, 233.193.40.196)
(10.11.11.1/32, 239.194.169.1/32), uptime: 00:05:12, ip mrib pim
NAT Mode: Ingress
NAT Route Type: Pre
Incoming interface: Ethernet1/47, RPF nbr: 10.11.11.1, internal
Translation list: (count: 1)
SR: (172.16.0.1, 233.193.40.196)
Verificação do Switch 3
SW3# show ip mroute
IP Multicast Routing Table for VRF "default"
(*, 232.0.0.0/8), uptime: 02:45:09, pim ip
Incoming interface: Null, RPF nbr: 0.0.0.0
Outgoing interface list: (count: 0)
(*, 233.193.40.196/32), uptime: 01:47:02, ip pim igmp
Incoming interface: Ethernet1/24, RPF nbr: 10.0.0.1
Outgoing interface list: (count: 1)
Ethernet1/24, uptime: 01:43:27, igmp, (RPF)
(172.16.0.1/32, 233.193.40.196/32), uptime: 00:02:59, ip mrib pim
Incoming interface: Ethernet1/24, RPF nbr: 10.0.0.1
Outgoing interface list: (count: 1)
Ethernet1/24, uptime: 00:02:59, mrib, (RPF)
Troubleshooting
Esta seção disponibiliza informações para a solução de problemas de configuração.
Se S2 e G2 não forem criados ou o usuário enfrentar problemas de conversão aleatória, você poderá verificar estes pontos:
1. Uma vez que o tráfego é recebido (pré-traduzido), as entradas pós-traduzidas são criadas com base no pkt lançado em mcastfwd.
2. Se você não vir pkt punted em mcastfwd, poderá verificar se recebeu o tráfego solicitado na interface de entrada através da ACL.
3 Se você vir um aumento nos contadores na ACL, verifique se o mesmo tráfego atinge a CPU através do etanalyzer.
4 Também é possível verificar a conversão no histórico de eventos da MRIB:
SW2# show system internal mfwd ip mroute --> Packets Punted in Mcast Forwarding.
MCASTFWD Multicast Routing Table for VRF "default"
(0.0.0.0/0, 232.0.0.0/8)
Software switched packets: 0, bytes: 0
RPF fail packets: 0, bytes: 0
(0.0.0.0/0, 233.193.40.196/32)
Software switched packets: 1, bytes: 84
RPF fail packets: 0, bytes: 0
(172.16.0.1/32, 233.193.40.196/32), data-alive
Software switched packets: 1, bytes: 84
RPF fail packets: 8, bytes: 672
(0.0.0.0/0, 239.194.169.1/32)
Software switched packets: 1, bytes: 84
RPF fail packets: 0, bytes: 0
(10.11.11.1/32, 239.194.169.1/32), data-alive
Software switched packets: 10, bytes: 840
RPF fail packets: 0, bytes: 0
SW2# show ip access-lists test
IP access list test
statistics per-entry
10 permit ip any 239.194.169.1/32 [match=105] <-- Intrested traffic hitting ingress interface
20 permit ip any any [match=11]
interface Ethernet1/47
no switchport
ip access-group test in <-- ACL applied on ingress interface
ip address 10.11.11.2/24
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
no shutdown
SW2# ethanalyzer loca int inband display-filter "ip.addr == 239.194.169.1" limit-captured-frames 0 --> Confirm (S1,G1) seen on CPU
Capturing on inband
wireshark-cisco-mtc-dissector: ethertype=0xde09, devicetype=0x0
2022-09-18 04:21:37.840227 10.11.11.1 -> 239.194.169.1 ICMP Echo (ping) request
2022-09-18 04:21:37.841275 10.11.11.1 -> 239.194.169.1 ICMP Echo (ping) request
2022-09-18 04:21:37.860153 10.11.11.1 -> 239.194.169.1 ICMP Echo (ping) request
2022-09-18 04:21:37.861199 10.11.11.1 -> 239.194.169.1 ICMP Echo (ping) request
2022-09-18 04:21:37.880072 10.11.11.1 -> 239.194.169.1 ICMP Echo (ping) request
2022-09-18 04:21:37.881113 10.11.11.1 -> 239.194.169.1 ICMP Echo (ping) request
SW2# ethanalyzer local interface inband capture-filter "host 172.16.0.1" limit-captured-frames 0 --> Confirm (S2,G2) seen on CPU
Capturing on inband
wireshark-cisco-mtc-dissector: ethertype=0xde09, devicetype=0x0
2022-09-18 03:12:51.423484 172.16.0.1 -> 233.193.40.196 ICMP Echo (ping) request
2022-09-18 03:12:51.423978 10.0.0.2 -> 172.16.0.1 ICMP Echo (ping) reply
2022-09-18 03:12:53.425754 172.16.0.1 -> 233.193.40.196 ICMP Echo (ping) request
2022-09-18 03:12:53.425761 10.0.0.2 -> 172.16.0.1 ICMP Echo (ping) reply
2022-09-18 03:12:55.426719 172.16.0.1 -> 233.193.40.196 ICMP Echo (ping) request
2022-09-18 03:12:55.426726 10.0.0.2 -> 172.16.0.1 ICMP Echo (ping) reply
2022-09-18 03:12:57.428669 172.16.0.1 -> 233.193.40.196 ICMP Echo (ping) request
2022-09-18 03:12:57.429175 10.0.0.2 -> 172.16.0.1 ICMP Echo (ping) reply
2022-09-18 03:12:59.429890 172.16.0.1 -> 233.193.40.196 ICMP Echo (ping) request
2022-09-18 03:12:59.430386 10.0.0.2 -> 172.16.0.1 ICMP Echo (ping) reply
10 packets captured
SW2# show ip pim event-history mrib --> Event history to confirm that the translation is being done
2022 Sep 18 04:28:39.970688: E_DEBUG pim [19433]: Sending ack: xid: 0xeeee00d2
2022 Sep 18 04:28:39.970255: E_DEBUG pim [19433]: MRIB Join notify for (10.11.11.1/32, 239.194.169.1/32)
2022 Sep 18 04:28:39.968875: E_DEBUG pim [19433]: MRIB sr route type notif for (10.11.11.1/32, 239.194.169.1/32) : 1
2022 Sep 18 04:28:39.968859: E_DEBUG pim [19433]: pim_process_mrib_rpf_notify: MRIB RPF notify for (10.11.11.1/32, 239.194.169.1/32), old RPF info: 10.11.11.1 (Ethernet1/47), new RPF info: 10.11.11.1 (Ethernet1/47). LISP source RLOC address
: 0.0.0.0, route-type 1
2022 Sep 18 04:28:39.968307: E_DEBUG pim [19433]: Copied the flags from MRIB for route (10.11.11.1/32, 239.194.169.1/32), (before/after): att F/F, sta F/F, z-oifs T/F, ext F/F, fabric F/F, fabric_src: F/F mofrr F/F
2022 Sep 18 04:28:39.968301: E_DEBUG pim [19433]: MRIB Join notify for (10.11.11.1/32, 239.194.169.1/32)
2022 Sep 18 04:28:39.968294: E_DEBUG pim [19433]: Received a notify message from MRIB xid: 0xeeee00cf for 1 mroutes
2022 Sep 18 04:28:35.904652: E_DEBUG pim [19433]: Sending ack: xid: 0xeeee00cc
2022 Sep 18 04:28:35.904625: E_DEBUG pim [19433]: pim_process_mrib_rpf_notify: MRIB RPF notify for (172.16.0.1/32, 233.193.40.196/32), old RPF info: 172.16.0.1 (loopback411), new RPF info: 172.16.0.1 (loopback411). LISP sourc
e RLOC address: 0.0.0.0, route-type 0
2022 Sep 18 04:28:35.904484: E_DEBUG pim [19433]: pim_process_mrib_rpf_notify: After copying the values for route (0.0.0.0/32, 233.193.40.196/32) we got RPF info: 172.16.0.1 (loopback411). LISP source RLOC address: 0.0.0.0, route-t
ype 0
2022 Sep 18 04:28:35.904476: E_DEBUG pim [19433]: pim_process_mrib_rpf_notify: MRIB RPF notify for (0.0.0.0/32, 233.193.40.196/32), old RPF info: 0.0.0.0 ((null)), new RPF info: 172.16.0.1 (loopback411). LISP source RLOC address: 0
.0.0.0, route-type 0
2022 Sep 18 04:28:35.904400: E_DEBUG pim [19433]: MRIB Join notify for (172.16.0.1/32, 233.193.40.196/32)
2022 Sep 18 04:28:35.904343: E_DEBUG pim [19433]: MRIB Join notify for (0.0.0.0/32, 233.193.40.196/32)
2022 Sep 18 04:27:49.862827: E_DEBUG pim [19433]: pim_process_mrib_rpf_notify: After copying the values for route (*, 239.194.169.1/32) we got RPF info: 10.10.10.10 (loopback0). LISP source RLOC address: 0.0.0.0, route-type 0
2022 Sep 18 04:27:49.862812: E_DEBUG pim [19433]: pim_process_mrib_rpf_notify: MRIB RPF notify for (*, 239.194.169.1/32), old RPF info: 0.0.0.0 ((null)), new RPF info: 10.10.10.10 (loopback0). LISP source RLOC address: 0.0.0.0, route-
type 0
2022 Sep 18 04:27:49.862798: E_DEBUG pim [19433]: MRIB Join notify for (*, 239.194.169.1/32)
2022 Sep 18 04:27:49.862795: E_DEBUG pim [19433]: MRIB Join notify for (172.16.0.1/32, 233.193.40.196/32)
2022 Sep 18 04:27:49.862789: E_DEBUG pim [19433]: MRIB Join notify for (0.0.0.0/32, 233.193.40.196/32)
2022 Sep 18 04:27:49.861870: E_DEBUG pim [19433]: Creating PIM route for (*, 239.194.169.1/32)
2022 Sep 18 04:27:49.861868: E_DEBUG pim [19433]: MRIB Join notify for (*, 239.194.169.1/32)
Summary
- No modo Regular, o tráfego atinge a entrada S, G original na primeira passagem e recircula devido à Lista de Interface de Saída (OIFL) que tem apenas a porta de loopback. Na segunda passagem, ele deriva o MAC de destino para a regravação.
- Na terceira passagem, a consulta de rota multicast acontece no S, G convertido e o pacote é encaminhado para as portas OIFL do grupo convertido correspondente.
- Junção estática adicionada no loopback para forçar o recebimento do tráfego na caixa NAT.
- Quando o primeiro pacote for recebido para (s1, g1), o switch programará (s1, g1) com o novo flag SR (s1, g —> s2, g2) .
- O switch usaria esses metadados para fazer um novo círculo do pacote e apontar o pacote para g2. Uma vez que o pacote (S2, G2) é apontado para sup, a funcionalidade FHR (roteador de primeiro salto) seria acionada na caixa NAT para s2, g2.
- Uma vez que o tráfego é recebido, as entradas pré-traduzidas e pós-traduzidas seriam criadas com base no pkt lançado em mcastfwd.
- Se você não vir o pacote inserido em mcastfwd para o respectivo grupo, poderá usar o processo de solução de problemas mencionado para confirmar se o tráfego interessado atinge o switch
Informações Relacionadas
.
Histórico de revisões
| Revisão | Data de publicação | Comentários |
|---|---|---|
2.0 |
26-Jul-2023
|
Atualizado e republicado. |
1.0 |
21-Sep-2022
|
Versão inicial |
Colaborado por engenheiros da Cisco
- Deepak KeshwaniEngenheiro do Cisco TAC
Contate a Cisco
- Abrir um caso de suporte

- (É necessário um Contrato de Serviço da Cisco)
 Feedback
Feedback