Configuring L2TP Multihop to Perform Several Hops from the NAS to the LNS
Contents
Introduction
A VPDN (Virtual Private Dialup Network) de vários saltos permite configurar vários saltos no caminho do concentrador de acesso L2TP (LAC) para o LNS (L2TP Network Server). Há suporte para um máximo de quatro nós. O túnel é encerrado em cada salto (LNS) e reiniciado para o destino do próximo salto. Esse processo permite a switching de túnel. Os saltos múltiplos podem ser utilizados entre ISPs para fornecer um serviço por atacado de Acesso à Rede virtual privada (VPN).
O encaminhamento de camada 2 (L2F - Layer 2 Forwarding) e o protocolo de túnel de camada 2 (L2TP - Layer 2 Tunnel Protocol) são suportados neste cenário. No entanto, como o L2TP está se tornando o padrão do setor, este documento se concentra no L2TP.
Prerequisites
Conventions
Para obter mais informações sobre convenções de documento, consulte as Convenções de dicas técnicas Cisco.
Requirements
Não existem requisitos específicos para este documento.
Para obter uma explicação do processo de VPDN, consulte Entendendo a VPDN.
Componentes Utilizados
As informações neste documento são baseadas nas versões de software e hardware abaixo.
-
Software Cisco IOS® versões 12.3(6)
-
L2TP Access Concentrator (LAC): um servidor de acesso Cisco AS5400
-
Servidores de rede L2TP (LNS): Cisco 7200 Routers
As informações neste documento foram criadas a partir de dispositivos em um ambiente de laboratório específico. All of the devices used in this document started with a cleared (default) configuration. Se você estiver trabalhando em uma rede ativa, certifique-se de que entende o impacto potencial de qualquer comando antes de utilizá-lo.
Configurar
Nesta seção, você encontrará informações para configurar os recursos descritos neste documento.
Observação: para encontrar informações adicionais sobre os comandos usados neste documento, use a ferramenta Command Lookup Tool (somente clientes registrados).
Diagrama de Rede
Este documento utiliza a instalação de rede mostrada no diagrama abaixo.
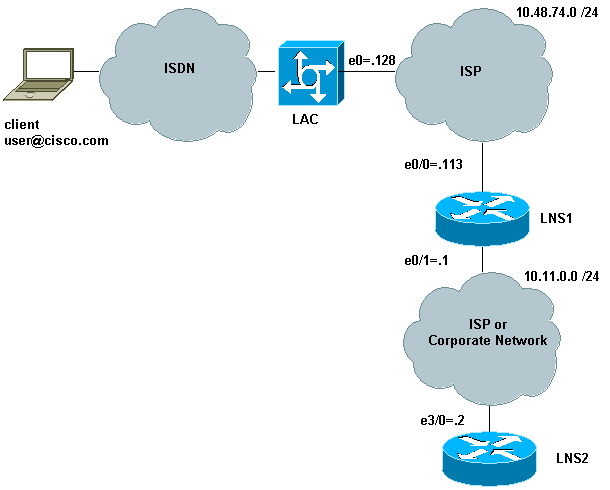
Nesta configuração:
-
O cliente usa ISDN para discar no LAC (ele pode, por exemplo, usar DSL).
-
O LAC usa uma interface de taxa primária (PRI) E1 para aceitar chamadas.
-
Não há túnel aberto entre os dispositivos L2TP.
-
A configuração do túnel e da sessão se baseia no nome de domínio. Não há servidor AAA para autenticação ou autorização.
-
Usa dois LNSs.
O processo é o seguinte:
-
O cliente disca no LAC. O cliente e o LAC negociam as opções LCP. A fase de autenticação é realizada e o LAC obtém o nome de usuário (usuário@cisco.com) e a senha. Com base no nome de domínio (cisco.com em nosso exemplo), ele abre um túnel seguido de uma sessão para o LNS1.
-
Depois que a sessão L2TP estiver aberta entre o LAC e o LNS1, o LNS1 obtém as opções de LCP que foram negociadas entre o LAC e o cliente, juntamente com o nome de usuário e senha (user@cisco.com, password).
-
O LNS1 tem um grupo de VPDN com o mesmo domínio (cisco.com) em sua configuração. Abre um túnel e uma sessão para o LNS2. Se não tiver essa configuração, ele terminará a sessão PPP, pela autenticação do cliente, pela negociação do endereço IP e pela instalação da rota.
-
Quando a sessão L2TP estiver aberta entre LNS1 e LNS2, LNS2 obterá as opções LCP que foram negociadas entre o LAC e o cliente, junto com o usuário e a senha (usuário@cisco.com, senha). Autentica o usuário, negocia IPCP e instala a rota.
Configurações
Este documento utiliza as configurações mostradas abaixo. O número mínimo de comandos é usado aqui. Por exemplo, o LAC não encerrará nenhuma sessão; portanto, não é necessário configurar um endereço IP na interface Dialer1 ou Group-async1. O LNS1 não irá encerrar nenhuma sessão de PPP, portanto não há endereço IP no modelo virtual 1.
| LAC |
|---|
version 12.3 service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname LAC ! boot-start-marker no boot startup-test boot-end-marker ! enable password 7 02050D480809 ! ! ! resource-pool disable spe default-firmware spe-firmware-2 no aaa new-model ip subnet-zero no ip domain lookup ! ip cef ! -- Enables VPDN. vpdn enable ! -- VPDN tunnel authorization is based first on the domain name ! -- (the default is DNIS). ! vpdn search-order domain ! ! -- The LAC opens an L2TP tunnel and session to 10.48.74.113 (LNS1) ! -- using the password LACLNS1 for users whose domain-name is cisco.com. vpdn-group 1 request-dialin protocol l2tp domain cisco.com initiate-to ip 10.48.74.113 l2tp tunnel password LACLNS1 ! isdn switch-type primary-net5 ! ! no voice hpi capture buffer no voice hpi capture destination ! ! controller E1 7/0 pri-group timeslots 1-31 ! interface FastEthernet0/0 ip address 10.48.74.128 255.255.255.0 duplex auto speed auto ! interface Serial7/0:15 no ip address encapsulation ppp dialer rotary-group 1 isdn switch-type primary-net5 ! interface Group-Async1 no ip address encapsulation ppp async mode interactive ppp authentication chap callin group-range 1/00 3/107 ! interface Dialer1 no ip address encapsulation ppp ppp authentication chap callin ! ip classless no ip http server ! ! voice-port 7/0:D ! line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 line 1/00 1/107 modem InOut transport input all line 3/00 3/107 modem InOut transport input all ! scheduler allocate 10000 400 ! end |
| LNS1 |
|---|
version 12.3 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname LNS1 ! boot-start-marker boot-end-marker ! enable password cisco ! clock timezone CET 1 no aaa new-model ip subnet-zero ip cef ! ! no ip domain lookup ! ! -- Enables VPDN. vpdn enable ! -- Enables VPDN multihop. vpdn multihop ! !-- LNS1 accepts L2TP tunnel/session from the router named LAC. !-- The password LACLNS1 is used between LAC and LNS1 for authentication. !-- The virtual-template 1 is used for the PPP phase. vpdn-group FromLAC accept-dialin protocol l2tp virtual-template 1 terminate-from hostname LAC l2tp tunnel password 0 LACLNS1 ! ! -- The LNS1 opens a L2TP tunnel and session to 10.11.0.2 (LNS2) ! -- using the password LNS1LNS2 for users whose domain-name is cisco.com. vpdn-group TowardsLNS2 request-dialin protocol l2tp domain cisco.com initiate-to ip 10.11.0.2 l2tp tunnel password 0 LNS1LNS2 ! ! interface Ethernet0/0 ip address 10.48.74.113 255.255.255.0 no ip proxy-arp half-duplex ! interface Ethernet0/1 ip address 10.11.0.1 255.255.255.0 half-duplex ! interface Virtual-Template1 no ip address ppp authentication chap callin ! no ip http server ip classless ! ! dial-peer cor custom ! line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 exec-timeout 0 0 password ww login ! ntp clock-period 17208915 ntp server 10.48.75.134 ! ! end |
| LNS2 |
|---|
version 12.3 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname LNS2 ! boot-start-marker boot-end-marker ! enable password cisco ! username user@cisco.com password 0 cisco no aaa new-model ip subnet-zero ! ! ip cef ! !-- Enables VPDN. vpdn enable ! !-- LNS2 accepts L2TP tunnel/session from the router named LNS1. !-- The password LNS1LNS2 is used between LNS1 and LNS2 for authentication. !-- The virtual-template 1 is used for the PPP phase. vpdn-group FromLNS1 ! Default L2TP VPDN group accept-dialin protocol l2tp virtual-template 1 l2tp tunnel password 0 LNS1LNS2 ! ! interface Loopback0 ip address 192.168.1.1 255.255.255.0 ! interface Ethernet3/0 ip address 10.11.0.2 255.255.255.0 duplex half ! interface Virtual-Template1 ip unnumbered Loopback0 peer default ip address pool VpdnUsers ppp authentication chap callin ! ip local pool VpdnUsers 192.168.1.2 192.168.1.254 ip classless no ip http server ! ! line con 0 exec-timeout 0 0 transport preferred all transport output all stopbits 1 line aux 0 transport preferred all transport output all stopbits 1 line vty 0 4 login transport preferred all transport input all transport output all ! ! ! end |
Verificar
Esta seção fornece informações que você pode usar para confirmar se sua configuração está funcionando adequadamente.
A Output Interpreter Tool (somente clientes registrados) oferece suporte a determinados comandos show, o que permite exibir uma análise da saída do comando show.
-
show vpdn - Exibe informações sobre o túnel L2TP ou L2F ativo e identificadores de mensagem em uma VPDN.
-
show caller user user detail - Exibe informações do chamador.
A saída ao utilizar esses comandos no LAC, LNS1 e LNS2 é mostrada aqui:
LAC#show vpdn L2TP Tunnel and Session Information Total tunnels 1 sessions 1 LocID RemID Remote Name State Remote Address Port Sessions VPDN Group 18693 28416 LNS1 est 10.48.74.113 1701 1 1 LocID RemID TunID Intf Username State Last Chg Uniq ID 19 21 18693 Se7/0:3 user@cisco.com est 00:02:04 28 %No active L2F tunnels %No active PPTP tunnels LAC#
Vemos que o LNS1 tem dois túneis com uma sessão em cada um.
LNS1#show vpdn L2TP Tunnel and Session Information Total tunnels 2 sessions 2 LocID RemID Remote Name State Remote Address Port Sessions VPDN Group 28416 18693 LAC est 10.48.74.128 1701 1 FromLAC LocID RemID TunID Intf Username State Last Chg Uniq ID 21 19 28416 SSS Circuit user@cisco.com est 00:02:25 13 LocID RemID Remote Name State Remote Address Port Sessions VPDN Group 30255 35837 LNS2 est 10.11.0.2 1701 1 TowardsLNS2 LocID RemID TunID Intf Username State Last Chg Uniq ID 22 9 30255 SSS Circuit user@cisco.com est 00:02:25 13 %No active L2F tunnels %No active PPTP tunnels LNS1#
LNS2#show vpdn
L2TP Tunnel and Session Information Total tunnels 1 sessions 1
LocID RemID Remote Name State Remote Address Port Sessions VPDN Group
35837 30255 LNS1 est 10.11.0.1 1701 1 FromLNS1
LocID RemID TunID Intf Username State Last Chg Uniq ID
9 22 35837 Vi2.1 user@cisco.com est 00:03:22 8
%No active L2F tunnels
%No active PPTP tunnels
LNS2#
LNS2#show caller user user@cisco.com detail
User: user@cisco.com, line Vi2.1, service PPPoVPDN
Connected for 00:03:33, Idle for 00:00:58
Timeouts: Limit Remaining Timer Type
- - -
PPP: LCP Open, CHAP (<-), IPCP
LCP: -> peer, AuthProto, MagicNumber
<- peer, MagicNumber, EndpointDisc
NCP: Open IPCP
IPCP: <- peer, Address
-> peer, Address
IP: Local 192.168.1.1, remote 192.168.1.2
Counts: 56 packets input, 2562 bytes
57 packets output, 2570 bytes
LNS2#
Troubleshoot
Esta seção fornece informações que podem ser usadas para o troubleshooting da sua configuração.
Comandos para Troubleshooting
A Output Interpreter Tool (somente clientes registrados) oferece suporte a determinados comandos show, o que permite exibir uma análise da saída do comando show.
Observação: antes de emitir comandos debug, consulte Informações importantes sobre comandos debug.
Comandos de solução de problemas no LAC
-
debug isdn q931 - Exibe informações sobre a configuração de chamadas e a desconexão de conexões de rede ISDN (Camada 3) entre o roteador local (lado do usuário) e a rede.
-
debug vpdn event - Exibe mensagens sobre eventos e erros de L2TP que fazem parte do estabelecimento ou encerramento normal de VPDNs.
-
debug vpdn error - Troubleshoot Layer 2 Tunnel Protocol Version 3 (L2TPv3) e a infraestrutura de tunelamento da Camada 2 ao redor.
-
debug vpdn l2x-events - Exibe os eventos resultantes de condições de protocolo especificas.
-
vpdn l2x-errors - Exibe os erros que ocorrem em condições específicas ao protocolo.
-
debug ppp negotiation - Exibe se um cliente está passando a negociação PPP. Você pode ver quais opções (por exemplo, retorno de chamada ou MLP) e quais protocolos (como IP e IPX) estão sendo negociados.
Comandos de Troubleshooting no LNS1
-
debug vpdn event
-
debug vpdn error
-
debug vpdn l2x event
-
vpdn l2x-erro
-
negociação de debug ppp
-
debug vtemplate error - Exibe informações de clonagem para uma interface de acesso virtual desde o momento em que é clonada de um modelo virtual até o momento em que a interface de acesso virtual é desativada quando a chamada é encerrada.
-
debug vtemplate event - Exibe informações de clonagem para uma interface de acesso virtual desde o momento em que é clonada de um modelo virtual até o momento em que a interface de acesso virtual é desativada quando a chamada é encerrada.
Troubleshooting de Comandos no LNS2
Alguns como para LNS1, mas com um comando adicional:
-
debug ip peer - Exibe a atividade do endereço e contém uma saída adicional quando grupos de conjuntos são definidos.
Saída da depuração - LAC
A saída de depuração no LAC é como segue:
LAC#
*Apr 23 08:55:23.579: ISDN Se7/0:15 Q931: RX <- SETUP pd = 8 callref = 0x256F
Sending Complete
Bearer Capability i = 0x8890
Standard = CCITT
Transer Capability = Unrestricted Digital
Transfer Mode = Circuit
Transfer Rate = 64 kbit/s
Channel ID i = 0xA18384
Preferred, Channel 4
Calling Party Number i = 0xA1, '8101'
Plan:ISDN, Type:National
Called Party Number i = 0x81, '7070'
Plan:ISDN, Type:Unknown
Locking Shift to Codeset 6
Codeset 6 IE 0x28 i = 'TAC BRI 8101'
*Apr 23 08:55:23.583: ISDN Se7/0:15 Q931: TX -> CALL_PROC pd = 8 callref = 0xA56F
Channel ID i = 0xA98384
Exclusive, Channel 4
*Apr 23 08:55:23.583: ISDN Se7/0:15 Q931: TX -> CONNECT pd = 8 callref = 0xA56F
Channel ID i = 0xA98384
Exclusive, Channel 4
*Apr 23 08:55:23.583: Se7/0:3 PPP: Using dialer call direction
*Apr 23 08:55:23.583: Se7/0:3 PPP: Treating connection as a callin
*Apr 23 08:55:23.583: Se7/0:3 PPP: Phase is ESTABLISHING, Passive Open
*Apr 23 08:55:23.583: Se7/0:3 LCP: State is Listen
*Apr 23 08:55:23.607: ISDN Se7/0:15 Q931: RX <- CONNECT_ACK pd = 8
callref = 0x256F
*Apr 23 08:55:23.695: Se7/0:3 LCP: I CONFREQ [Listen] id 180 len 31
*Apr 23 08:55:23.695: Se7/0:3 LCP: MagicNumber 0x9028FFED (0x05069028FFED)
*Apr 23 08:55:23.695: Se7/0:3 LCP: MRRU 1524 (0x110405F4)
*Apr 23 08:55:23.695: Se7/0:3 LCP: EndpointDisc 1 user@cisco.com
*Apr 23 08:55:23.695: Se7/0:3 LCP: (0x1311017573657240636973636F2E636F)
*Apr 23 08:55:23.695: Se7/0:3 LCP: (0x6D)
*Apr 23 08:55:23.695: Se7/0:3 LCP: O CONFREQ [Listen] id 1 len 15
*Apr 23 08:55:23.695: Se7/0:3 LCP: AuthProto CHAP (0x0305C22305)
*Apr 23 08:55:23.695: Se7/0:3 LCP: MagicNumber 0x050E44FB (0x0506050E44FB)
*Apr 23 08:55:23.695: Se7/0:3 LCP: O CONFREJ [Listen] id 180 len 8
*Apr 23 08:55:23.695: Se7/0:3 LCP: MRRU 1524 (0x110405F4)
*Apr 23 08:55:23.727: Se7/0:3 LCP: I CONFACK [REQsent] id 1 len 15
*Apr 23 08:55:23.727: Se7/0:3 LCP: AuthProto CHAP (0x0305C22305)
*Apr 23 08:55:23.727: Se7/0:3 LCP: MagicNumber 0x050E44FB (0x0506050E44FB)
*Apr 23 08:55:23.751: Se7/0:3 LCP: I CONFREQ [ACKrcvd] id 181 len 27
*Apr 23 08:55:23.751: Se7/0:3 LCP: MagicNumber 0x9028FFED (0x05069028FFED)
*Apr 23 08:55:23.751: Se7/0:3 LCP: EndpointDisc 1 user@cisco.com
*Apr 23 08:55:23.751: Se7/0:3 LCP: (0x1311017573657240636973636F2E636F)
*Apr 23 08:55:23.751: Se7/0:3 LCP: (0x6D)
*Apr 23 08:55:23.751: Se7/0:3 LCP: O CONFACK [ACKrcvd] id 181 len 27
*Apr 23 08:55:23.751: Se7/0:3 LCP: MagicNumber 0x9028FFED (0x05069028FFED)
*Apr 23 08:55:23.751: Se7/0:3 LCP: EndpointDisc 1 user@cisco.com
*Apr 23 08:55:23.751: Se7/0:3 LCP: (0x1311017573657240636973636F2E636F)
*Apr 23 08:55:23.751: Se7/0:3 LCP: (0x6D)
*Apr 23 08:55:23.751: Se7/0:3 LCP: State is Open
*Apr 23 08:55:23.751: Se7/0:3 PPP: Phase is AUTHENTICATING, by this end
*Apr 23 08:55:23.751: Se7/0:3 CHAP: O CHALLENGE id 1 len 24 from "LAC"
*Apr 23 08:55:23.803: Se7/0:3 CHAP: I RESPONSE id 1 len 35 from "user@cisco.com"
*Apr 23 08:55:23.803: Se7/0:3 PPP: Phase is FORWARDING, Attempting Forward
*Apr 23 08:55:23.807: Tnl/Sn 18693/19 L2TP: Session FS enabled
*Apr 23 08:55:23.807: Tnl/Sn 18693/19 L2TP: Session state change
from idle to wait-for-tunnel
*Apr 23 08:55:23.807: Se7/0:3 Tnl/Sn 18693/19 L2TP: Create session
*Apr 23 08:55:23.807: Tnl 18693 L2TP: SM State idle
*Apr 23 08:55:23.807: Tnl 18693 L2TP: O SCCRQ
*Apr 23 08:55:23.807: Tnl 18693 L2TP: Control channel retransmit delay
set to 1 seconds
*Apr 23 08:55:23.807: Tnl 18693 L2TP: Tunnel state change from idle to
wait-ctl-reply
*Apr 23 08:55:23.807: Tnl 18693 L2TP: SM State wait-ctl-reply
*Apr 23 08:55:23.815: Tnl 18693 L2TP: I SCCRP from LNS1
*Apr 23 08:55:23.815: Tnl 18693 L2TP: Got a challenge from remote peer, LNS1
*Apr 23 08:55:23.815: Tnl 18693 L2TP: Got a response from remote peer, LNS1
*Apr 23 08:55:23.815: Tnl 18693 L2TP: Tunnel Authentication success
*Apr 23 08:55:23.815: Tnl 18693 L2TP: Tunnel state change from
wait-ctl-reply to established
*Apr 23 08:55:23.815: Tnl 18693 L2TP: O SCCCN to LNS1 tnlid 28416
*Apr 23 08:55:23.815: Tnl 18693 L2TP: Control channel retransmit
delay set to 1 seconds
*Apr 23 08:55:23.815: Tnl 18693 L2TP: SM State established
*Apr 23 08:55:23.815: Se7/0:3 Tnl/Sn 18693/19 L2TP: O ICRQ to LNS1 28416/0
*Apr 23 08:55:23.815: Se7/0:3 Tnl/Sn 18693/19 L2TP: Session state change
from wait-for-tunnel to wai
t-reply
*Apr 23 08:55:23.831: Se7/0:3 Tnl/Sn 18693/19 L2TP: O ICCN to LNS1 28416/21
*Apr 23 08:55:23.831: Tnl 18693 L2TP: Control channel retransmit delay
set to 1 seconds
*Apr 23 08:55:23.831: Se7/0:3 Tnl/Sn 18693/19 L2TP: Session state change
from wait-reply to establis
hed
*Apr 23 08:55:23.831: Se7/0:3 Tnl/Sn 18693/19 L2TP: VPDN session up
*Apr 23 08:55:23.831: Se7/0:3 PPP: Phase is FORWARDED, Session Forwarded
*Apr 23 08:55:23.831: Se7/0:3 PPP: Process pending packets
LAC#
Saída de depuração - LNS1
A saída de depurações no LNS1 é a seguinte:
LNS1# .Apr 23 08:57:08.900: L2TP: I SCCRQ from LAC tnl 18693 .Apr 23 08:57:08.900: Tnl 28416 L2TP: Got a challenge in SCCRQ, LAC .Apr 23 08:57:08.900: Tnl 28416 L2TP: New tunnel created for remote LAC, address 10.48.74.128 .Apr 23 08:57:08.904: Tnl 28416 L2TP: O SCCRP to LAC tnlid 18693 .Apr 23 08:57:08.904: Tnl 28416 L2TP: Control channel retransmit delay set to 1 seconds .Apr 23 08:57:08.904: Tnl 28416 L2TP: Tunnel state change from idle to wait-ctl-reply .Apr 23 08:57:08.908: Tnl 28416 L2TP: I SCCCN from LAC tnl 18693 .Apr 23 08:57:08.908: Tnl 28416 L2TP: Got a Challenge Response in SCCCN from LAC .Apr 23 08:57:08.912: Tnl 28416 L2TP: Tunnel Authentication success .Apr 23 08:57:08.912: Tnl 28416 L2TP: Tunnel state change from wait-ctl-reply to established .Apr 23 08:57:08.912: Tnl 28416 L2TP: SM State established .Apr 23 08:57:08.912: Tnl 28416 L2TP: I ICRQ from LAC tnl 18693 .Apr 23 08:57:08.916: Tnl/Sn 28416/21 L2TP: Session FS enabled .Apr 23 08:57:08.916: Tnl/Sn 28416/21 L2TP: Session state change from idle to wait-connect .Apr 23 08:57:08.916: Tnl/Sn 28416/21 L2TP: New session created .Apr 23 08:57:08.916: Tnl/Sn 28416/21 L2TP: O ICRP to LAC 18693/19 .Apr 23 08:57:08.920: Tnl 28416 L2TP: Control channel retransmit delay set to 1 seconds .Apr 23 08:57:08.924: Tnl/Sn 28416/21 L2TP: I ICCN from LAC tnl 18693, cl 19 .Apr 23 08:57:08.924: user@cisco.com Tnl/Sn 28416/21 L2TP: Session state change from wait-connect to wait-for-service-selection .Apr 23 08:57:08.932: ppp13 PPP: Phase is ESTABLISHING .Apr 23 08:57:08.932: ppp13 LCP: I FORCED rcvd CONFACK len 11 .Apr 23 08:57:08.932: ppp13 LCP: AuthProto CHAP (0x0305C22305) .Apr 23 08:57:08.936: ppp13 LCP: MagicNumber 0x050E44FB (0x0506050E44FB) .Apr 23 08:57:08.936: ppp13 LCP: I FORCED sent CONFACK len 23 .Apr 23 08:57:08.936: ppp13 LCP: MagicNumber 0x9028FFED (0x05069028FFED) .Apr 23 08:57:08.936: ppp13 LCP: EndpointDisc 1 user@cisco.com .Apr 23 08:57:08.936: ppp13 LCP: (0x1311017573657240636973636F2E636F) .Apr 23 08:57:08.936: ppp13 LCP: (0x6D) .Apr 23 08:57:08.940: ppp13 PPP: Phase is FORWARDING, Attempting Forward .Apr 23 08:57:08.948: Tnl/Sn 30255/22 L2TP: Session FS enabled .Apr 23 08:57:08.952: Tnl/Sn 30255/22 L2TP: Session state change from idle to wait-for-tunnel .Apr 23 08:57:08.952: uid:13 Tnl/Sn 30255/22 L2TP: Create session .Apr 23 08:57:08.952: Tnl 30255 L2TP: SM State idle .Apr 23 08:57:08.952: Tnl 30255 L2TP: O SCCRQ .Apr 23 08:57:08.956: Tnl 30255 L2TP: Control channel retransmit delay set to 1 seconds .Apr 23 08:57:08.956: Tnl 30255 L2TP: Tunnel state change from idle to wait-ctl-reply .Apr 23 08:57:08.956: Tnl 30255 L2TP: SM State wait-ctl-reply .Apr 23 08:57:08.960: Tnl 30255 L2TP: I SCCRP from LNS2 .Apr 23 08:57:08.960: Tnl 30255 L2TP: Got a challenge from remote peer, LNS2 .Apr 23 08:57:08.964: Tnl 30255 L2TP: Got a response from remote peer, LNS2 .Apr 23 08:57:08.964: Tnl 30255 L2TP: Tunnel Authentication success .Apr 23 08:57:08.964: Tnl 30255 L2TP: Tunnel state change from wait-ctl-reply to established .Apr 23 08:57:08.964: Tnl 30255 L2TP: O SCCCN to LNS2 tnlid 35837 .Apr 23 08:57:08.968: Tnl 30255 L2TP: Control channel retransmit delay set to 1 seconds .Apr 23 08:57:08.968: Tnl 30255 L2TP: SM State established .Apr 23 08:57:08.968: uid:13 Tnl/Sn 30255/22 L2TP: O ICRQ to LNS2 35837/0 .Apr 23 08:57:08.968: uid:13 Tnl/Sn 30255/22 L2TP: Session state change from wait-for-tunnel to wait-reply .Apr 23 08:57:08.972: uid:13 Tnl/Sn 30255/22 L2TP: O ICCN to LNS2 35837/9 .Apr 23 08:57:08.976: Tnl 30255 L2TP: Control channel retransmit delay set to 1 seconds .Apr 23 08:57:08.976: uid:13 Tnl/Sn 30255/22 L2TP: Session state change from wait-reply to established .Apr 23 08:57:08.976: uid:13 Tnl/Sn 30255/22 L2TP: VPDN session up .Apr 23 08:57:08.980: ppp13 PPP: Phase is FORWARDED, Session Forwarded .Apr 23 08:57:08.984: user@cisco.com Tnl/Sn 28416/21 L2TP: Session state change from wait-for-service-selection to established .Apr 23 08:57:08.984: user@cisco.com Tnl/Sn 28416/21 L2TP: VPDN session up .Apr 23 08:57:08.984: ppp13 PPP: Process pending ncp packets LNS1#
Saída de depuração - LNS2
A saída de depuração no LNS2 é a seguinte:
LNS2# *Apr 23 08:57:59.615: L2TP: I SCCRQ from LNS1 tnl 30255 *Apr 23 08:57:59.615: Tnl 35837 L2TP: Got a challenge in SCCRQ, LNS1 *Apr 23 08:57:59.615: Tnl 35837 L2TP: New tunnel created for remote LNS1, address 10.11 .0.1 *Apr 23 08:57:59.615: Tnl 35837 L2TP: O SCCRP to LNS1 tnlid 30255 *Apr 23 08:57:59.615: Tnl 35837 L2TP: Control channel retransmit delay set to 1 seconds *Apr 23 08:57:59.615: Tnl 35837 L2TP: Tunnel state change from idle to wait-ctl-reply *Apr 23 08:57:59.623: Tnl 35837 L2TP: I SCCCN from LNS1 tnl 30255 *Apr 23 08:57:59.623: Tnl 35837 L2TP: Got a Challenge Response in SCCCN from LNS1 *Apr 23 08:57:59.623: Tnl 35837 L2TP: Tunnel Authentication success *Apr 23 08:57:59.623: Tnl 35837 L2TP: Tunnel state change from wait-ctl-reply to establ ished *Apr 23 08:57:59.623: Tnl 35837 L2TP: SM State established *Apr 23 08:57:59.627: Tnl 35837 L2TP: I ICRQ from LNS1 tnl 30255 *Apr 23 08:57:59.627: Tnl/Sn 35837/9 L2TP: Session FS enabled *Apr 23 08:57:59.627: Tnl/Sn 35837/9 L2TP: Session state change from idle to wait-conne ct *Apr 23 08:57:59.627: Tnl/Sn 35837/9 L2TP: New session created *Apr 23 08:57:59.627: Tnl/Sn 35837/9 L2TP: O ICRP to LNS1 30255/22 *Apr 23 08:57:59.627: Tnl 35837 L2TP: Control channel retransmit delay set to 1 seconds *Apr 23 08:57:59.635: Tnl/Sn 35837/9 L2TP: I ICCN from LNS1 tnl 30255, cl 22 *Apr 23 08:57:59.635: user@cisco.com Tnl/Sn 35837/9 L2TP: Session state change from wait - connect to wait-for-service-selection *Apr 23 08:57:59.635: ppp8 PPP: Phase is ESTABLISHING *Apr 23 08:57:59.635: ppp8 LCP: I FORCED rcvd CONFACK len 11 *Apr 23 08:57:59.635: ppp8 LCP: AuthProto CHAP (0x0305C22305) *Apr 23 08:57:59.635: ppp8 LCP: MagicNumber 0x050E44FB (0x0506050E44FB) *Apr 23 08:57:59.635: ppp8 LCP: I FORCED sent CONFACK len 23 *Apr 23 08:57:59.635: ppp8 LCP: MagicNumber 0x9028FFED (0x05069028FFED) *Apr 23 08:57:59.635: ppp8 LCP: EndpointDisc 1 user@cisco.com *Apr 23 08:57:59.635: ppp8 LCP: (0x1311017573657240636973636F2E636F) *Apr 23 08:57:59.635: ppp8 LCP: (0x6D) *Apr 23 08:57:59.635: ppp8 PPP: Phase is FORWARDING, Attempting Forward *Apr 23 08:57:59.639: ppp8 PPP: Phase is AUTHENTICATING, Unauthenticated User *Apr 23 08:57:59.639: ppp8 PPP: Phase is FORWARDING, Attempting Forward *Apr 23 08:57:59.639: VT[Vi2]:Sending vaccess request, id 0x73000015 *Apr 23 08:57:59.639: VT:Processing vaccess requests, 1 outstanding *Apr 23 08:57:59.639: VT:Create and clone subif, base Vi2 Vt1 *Apr 23 08:57:59.639: VT[Vi2.1]:Reuse subinterface, recycle queue size 1 *Apr 23 08:57:59.639: VT[Vi2.1]:Recycled subinterface becomes Vi2.1 *Apr 23 08:57:59.639: VT[Vi2.1]:Cloning a recycled vaccess *Apr 23 08:57:59.639: VT[Vi2.1]:Processing vaccess response, id 0x73000015, result success (1) *Apr 23 08:57:59.643: Vi2.1 Tnl/Sn 35837/9 L2TP: Virtual interface created for user@cisco.com, bandwidth 64 Kbps *Apr 23 08:57:59.643: Vi2.1 Tnl/Sn 35837/9 L2TP: VPDN session up *Apr 23 08:57:59.643: Vi2.1 Tnl/Sn 35837/9 L2TP: Session state change from wait-for-service-selection to established *Apr 23 08:57:59.643: Vi2.1 PPP: Phase is AUTHENTICATING, Authenticated User *Apr 23 08:57:59.643: Vi2.1 CHAP: O SUCCESS id 1 len 4 *Apr 23 08:57:59.643: Vi2.1 PPP: Phase is UP *Apr 23 08:57:59.643: Vi2.1 PPP: Process pending ncp packets *Apr 23 08:57:59.643: Vi2.1 IPCP: O CONFREQ [Closed] id 1 len 10 *Apr 23 08:57:59.643: Vi2.1 IPCP: Address 192.168.1.1 (0x0306C0A80101) *Apr 23 08:57:59.667: Vi2.1 IPCP: I CONFREQ [REQsent] id 125 len 10 *Apr 23 08:57:59.667: Vi2.1 IPCP: Address 0.0.0.0 (0x030600000000) *Apr 23 08:57:59.667: Vi2.1 AAA/AUTHOR/IPCP: Start. Her address 0.0.0.0, we want 0.0.0.0 *Apr 23 08:57:59.667: Vi2.1 AAA/AUTHOR/IPCP: Done. Her address 0.0.0.0, we want 0.0.0.0 *Apr 23 08:57:59.667: Vi2.1: Pools to search : VpdnUsers *Apr 23 08:57:59.667: Vi2.1: Pool VpdnUsers returned address = 192.168.1.2 *Apr 23 08:57:59.667: Vi2.1 IPCP: Pool returned 192.168.1.2 *Apr 23 08:57:59.667: Vi2.1 IPCP: O CONFNAK [REQsent] id 125 len 10 *Apr 23 08:57:59.667: Vi2.1 IPCP: Address 192.168.1.2 (0x0306C0A80102) *Apr 23 08:57:59.683: Vi2.1 IPCP: I CONFACK [REQsent] id 1 len 10 *Apr 23 08:57:59.683: Vi2.1 IPCP: Address 192.168.1.1 (0x0306C0A80101) *Apr 23 08:57:59.699: Vi2.1 IPCP: I CONFREQ [ACKrcvd] id 126 len 10 *Apr 23 08:57:59.699: Vi2.1 IPCP: Address 192.168.1.2 (0x0306C0A80102) *Apr 23 08:57:59.699: Vi2.1 IPCP: O CONFACK [ACKrcvd] id 126 len 10 *Apr 23 08:57:59.699: Vi2.1 IPCP: Address 192.168.1.2 (0x0306C0A80102) *Apr 23 08:57:59.699: Vi2.1 IPCP: State is Open *Apr 23 08:57:59.703: Vi2.1 IPCP: Install route to 192.168.1.2 *Apr 23 08:57:59.703: Vi2.1 IPCP: Add link info for cef entry 192.168.1.2 LNS2#
Informações Relacionadas
Histórico de revisões
| Revisão | Data de publicação | Comentários |
|---|---|---|
1.0 |
19-Nov-2007 |
Versão inicial |
Contate a Cisco
- Abrir um caso de suporte

- (É necessário um Contrato de Serviço da Cisco)
 Feedback
Feedback