Cisco Proxy TFTP Server Deployment Models
Cisco Proxy TFTP Server supports two deployment models.
Cisco Proxy TFTP Server Deployment Model 1
For the deployment model illustrated in the following figure, the Primary TFTP Server should have Unified CM version 8.6 (2) or later.
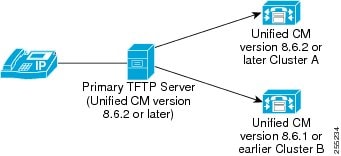
The two remote clusters, Cluster A and Cluster B, are configured to the Primary TFTP Server. However, you can configure any number of remote clusters to the Primary TFTP Server. Whenever an endpoint sends a request for configuration file, the Primary TFTP Server looks into the local cache and the configured remote clusters. So, an endpoint that is configured to the Primary TFTP Server Cluster, Cluster A, and Cluster B can retrieve the configuration file and register to the Cisco Unified Communications Manager.
 Note |
Cisco recommends that you use deployment model 1 for better system performance. However, if you do not wish to change your existing Centralized TFTP (8.6 (1) or earlier), you can use deployment model 2. |
Cisco Proxy TFTP Server Deployment Model 2
In the deployment model illustrated in the following figure, the centralized Unified CM TFTP server acts as a Primary TFTP server.
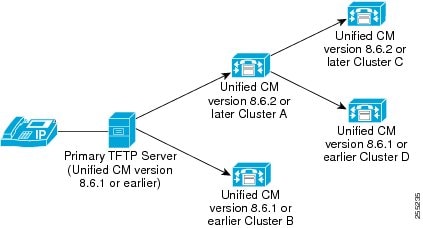
The two remote clusters - Cluster A and Cluster B have been configured to the Primary TFTP Server. However, you can configure any number of remote clusters to the Primary TFTP Server. Two more remote clusters have been added to the Cluster A. Whenever an endpoint sends a request for configuration file, the Primary TFTP Server looks into the local cache and the configured remote clusters (Cluster A and Cluster B). Cluster A further looks into its configured remote clusters (Cluster C and Cluster D). Thus, all the endpoints configured to the Primary TFTP Server Cluster, Cluster A, Cluster B, Cluster C and Cluster D can get the configuration file and get registered to the Cisco Unified Communications Manager.
Use Cases and Best Practices
Consider the following scenarios that detail how Proxy TFTP can be used and the best practices for implementation.
-
The cluster can act as just a proxy TFTP cluster with no other purpose. In this case, the cluster has no relationship with the other clusters, and does not process calls. For this scenario, the Remote Cluster TFTP is manually defined and rollback to pre-8.0 is recommended.

Note
Autoregistration will not work in this scenario.
-
The cluster is a remote cluster that is also acting as a Proxy TFTP server for remote clusters. The remote cluster is manually defined, and Autoregistration should not be enabled.

 Feedback
Feedback