Silent Monitoring
Customers need to guarantee the quality of customer service provided by their employees who service their customers, such as call center agents. Customers also need to meet compliance, guidelines and protect themselves from legal liability. These requirements are satisfied by monitoring and recording agent-customer conversations.
The silent call monitoring feature allows a supervisor to eavesdrop on any conversation; neither of the call participants can hear the supervisor voice.
Terminology
This document uses the following terms to discuss call monitoring:
- Agent
-
The call party that is monitored.
- Customer
-
Any call participant other than the agent or the supervisor.
- Local stream
-
The media stream from agent to customer.
- Remote stream
-
The media stream from customer to agent.
- Supervisor
-
The person who is silently monitoring the call.
- Supervisor desktop application
-
A silent monitoring-enabled application that is used to invoke a monitoring session.
- Silent monitoring
-
The feature which allows a monitoring party (a supervisor) to listen to a conversation between a near-end party (an agent) and a far-end party (a customer); neither the agent nor the customer hears the monitoring party voice.
Introduction
With silent call monitoring, the supervisor can listen in on any call for quality control and performance evaluation. By default, the agent is not aware of the monitoring session. In IP phone-based silent call monitoring, the monitoring stream comprises a mix of the customer voice and the agent voice. Only a CTI application can trigger a silent monitoring session.
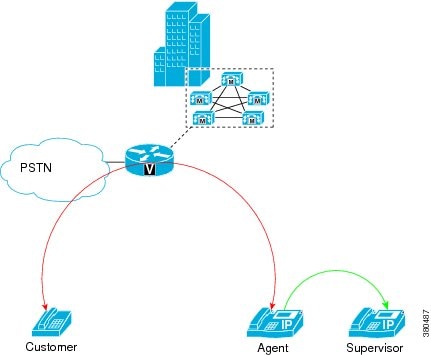
Architecture
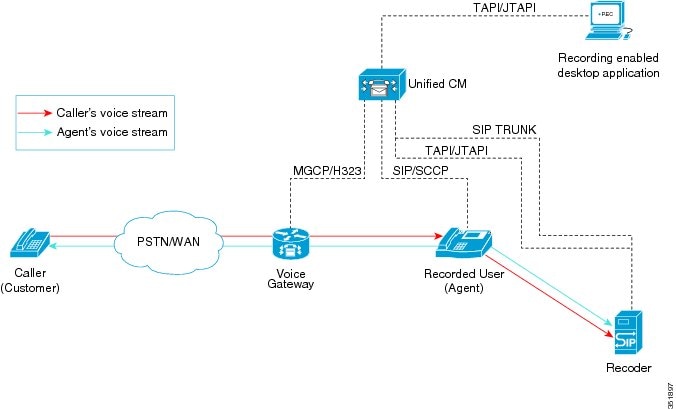
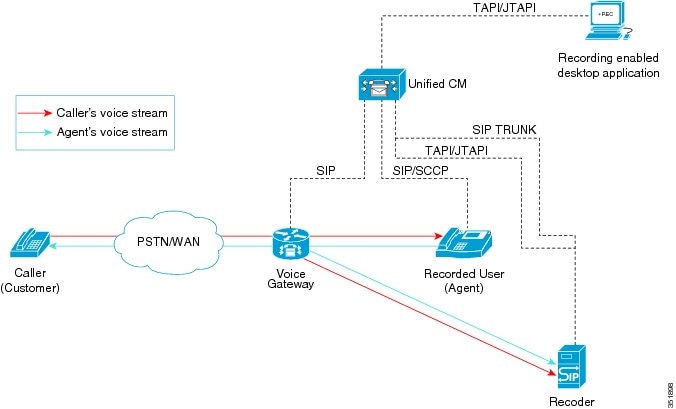
Cisco Unified Communications Manager uses an IP phone-based architecture to provide call monitoring whereby the agent phone mixes the agent voice with the customer voice and sends a single, combined, or mixed stream of both voices to the supervisor phone.
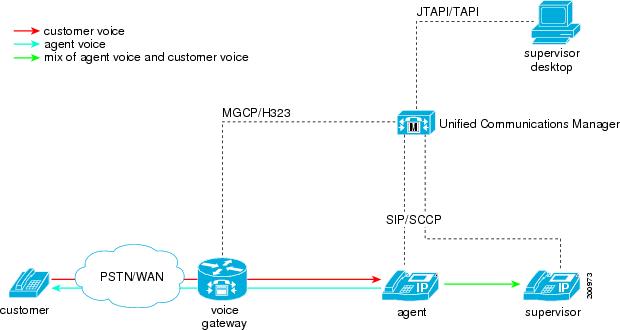
Applications can initiate monitoring through the JTAPI or TAPI interfaces. Many Cisco applications, such as Cisco Unified Contact Center Enterprise and Cisco Unified Contact Center Express have the ability to use the silent monitoring feature.
Monitoring exhibits the following characteristics:
-
Silent monitoring is call based; the supervisor selects a specific call on a line appearance of an agent phone to be monitored.
-
The start-monitoring request from the application triggers the supervisor phone to go off hook automatically to make a special monitoring call to the agent.
-
The agent phone automatically answers the monitoring call. The monitoring call is not presented to the agent.
The following requirements apply:
-
The CTI application user needs to be a member of the Standard CTI Allow Call Monitoring user group.
-
The agent device needs to be in the CTI application user's controlled device list.
For a monitoring call, the supervisor phone displays "From Monitoring [agent username/DN]".
One-Way Media
A monitoring call comprises one-way media from an agent phone to a supervisor phone.
Monitoring calls go through normal call admission control.
Network Address Translation (NAT) separating agent and supervisor or customer remains transparent within the limitations of Cisco Unified Communications Manager.
Firewall Considerations
Firewall software needs to know the destination IP address and destination port as well as the source IP address to allow the RTP streams.
Be aware that SCCP messages for media are not symmetric; SIP is acceptable.
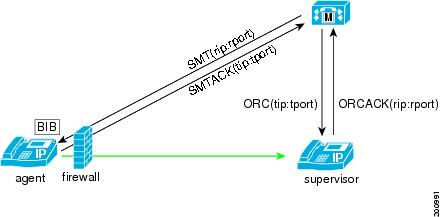
The SCCP version 12 enhancement for one-way media provides the following additions:
-
New StartMediaTransmissionAck (SMTACK) message with transmission IP and port
-
OpenReceiveChannel (ORC) with additional transmission IP and port
Codec Selection
The agent phone and the supervisor phone negotiate the codec for the monitoring call using Cisco Unified Communications Manager region settings.
Call Preservation
If the agent call that is being monitored goes to call preservation, Cisco Unified Communications Manager puts the monitoring call into call preservation mode.
The agent call is not affected if the monitoring call goes to call preservation mode.
Notification Tones
In certain jurisdictions, a notification tone must be played to either the agent, customer, or both indicating the call is being monitored.
Use the following service parameters to set the default notification-tone options:
-
Play Monitoring Notification Tone To Observed Target (agent)
-
Play Monitoring Notification Tone To Observed Connected Parties (customer)
CTI applications can specify the notification tone option in the monitoring request.
Play Tone Behavior
The following table specifies the behavior of tones during a monitoring session.
|
Play To |
Agent Hears |
Customer Hears |
Supervisor Hears |
|---|---|---|---|
|
None |
Nothing |
Nothing |
Nothing |
|
Agent |
Tone |
Nothing |
Nothing |
|
Customer |
Nothing |
Tone |
Nothing |
|
Both |
Tone |
Tone |
Nothing |
Silent Monitoring Usage Scenarios
The following section provides usage scenarios for Call Monitoring.
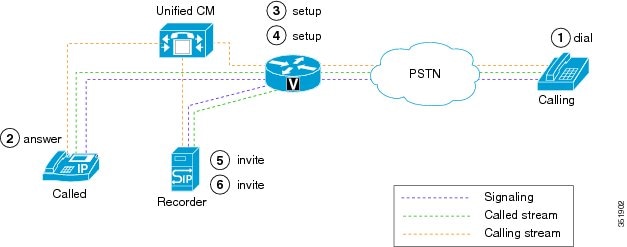
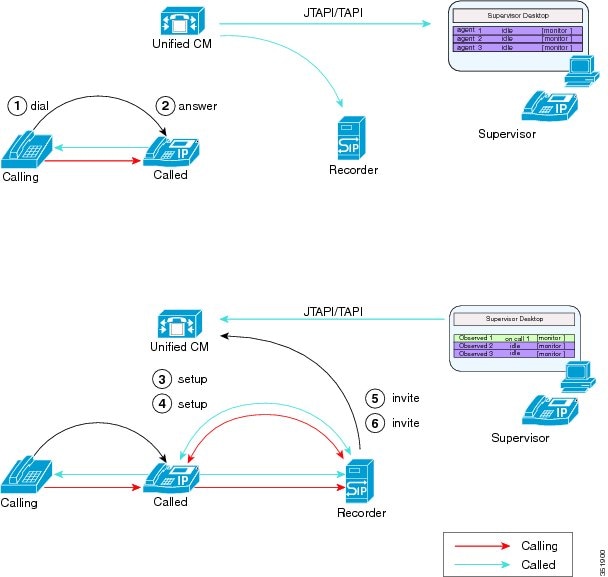
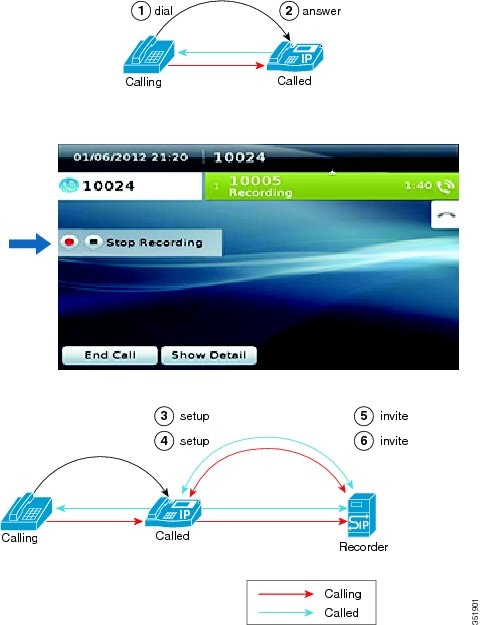
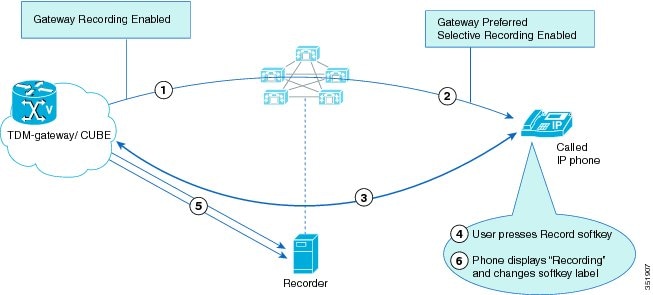
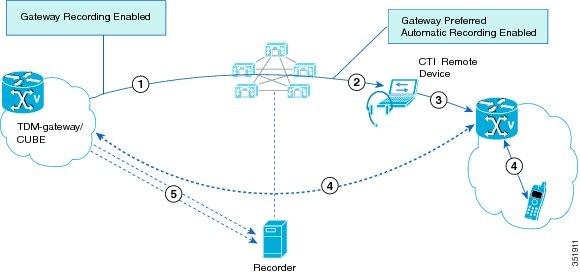
Invocation of a Silent Monitoring Session
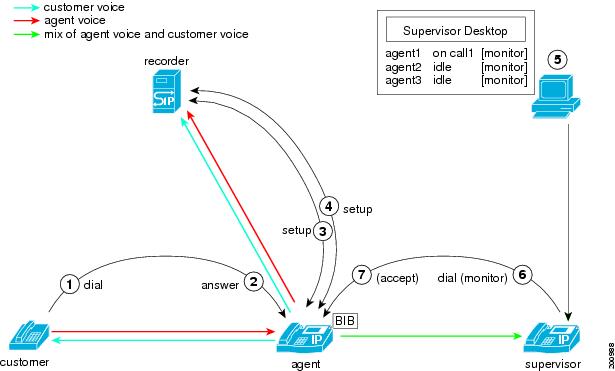
A supervisor can initiate a silent monitoring session by using a desktop application after the agent answers a call.
The following figure illustrates a silent monitoring session.

When the supervisor initiates a monitoring session, the following steps take place:
-
The customer calls into the call center. The call gets routed to the agent.
-
The agent answers the call. A two-way media stream is set up between the agent IP phone and the customer.
-
The supervisor selects the agent from the desktop application, and then clicks Monitoring.
-
The supervisor phone automatically goes off hook.
-
The supervisor phone makes a monitoring call to the agent.
-
The built-in bridge (BIB) of the agent phone automatically accepts the monitoring call. The agent phone starts to mix media of the agent voice and the customer voice and sends the mix to the supervisor phone.
The supervisor can transfer the monitoring call anywhere after the monitoring call is initiated.
The supervisor can stop monitoring the call anytime after the call starts, either through the application or simply by hanging up.
The supervisor can put the monitoring call on hold (no MOH gets inserted) and resume the monitoring call from the same or a different device.
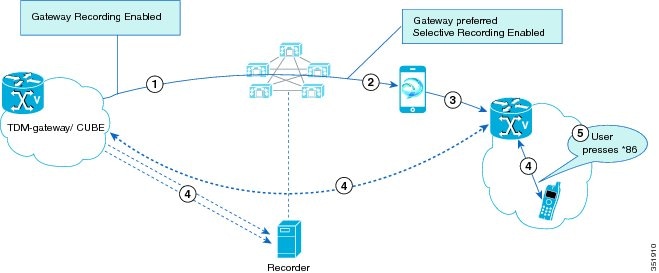
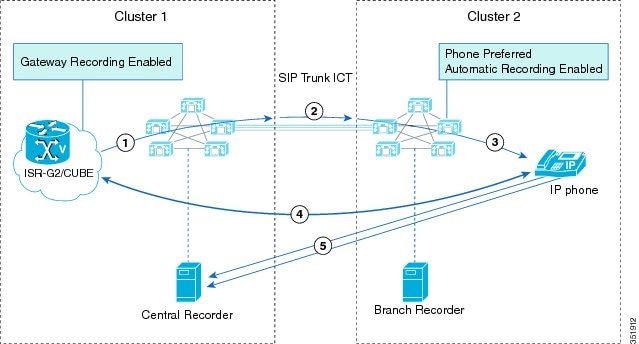
Supervisor Transfers the Monitoring Call
The following figure illustrates the supervisor transfer of a monitoring call.
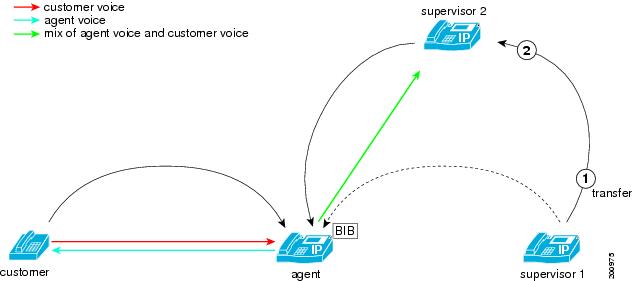
During a monitoring call, the supervisor transfers the monitoring call, and the following steps take place:
-
Supervisor 1 presses the Transfer softkey and dials the phone number of supervisor 2.
-
Supervisor 2 answers the call.
-
Supervisor 1 completes the transfer by pressing the Transfer softkey again.
-
The monitoring call transfers to supervisor 2. Supervisor 2 starts to receive the mix of the agent voice and the customer voice.
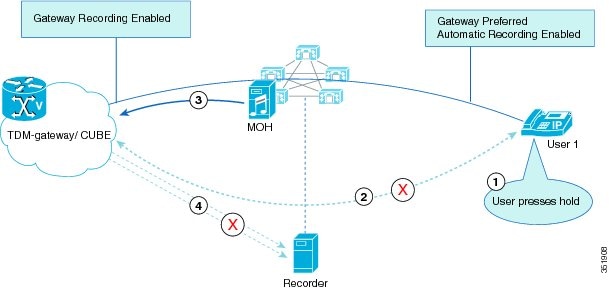
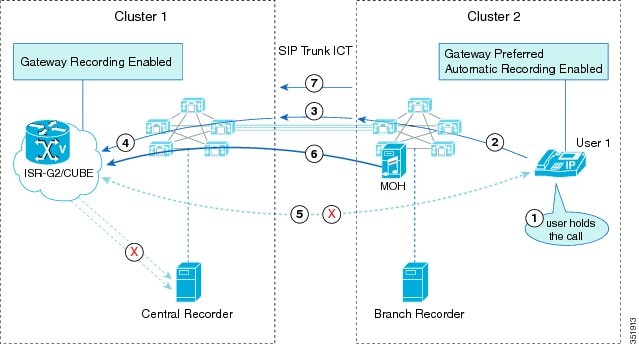
Agent Cannot Control a Monitoring Call
The agent does not have direct control over the monitoring call; however, the agent action on the primary call causes a corresponding action for the monitoring call.
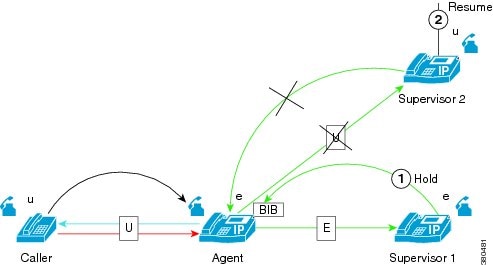
The following figure illustrates the scenario where the agent puts the customer on hold while the supervisor is monitoring the agent.
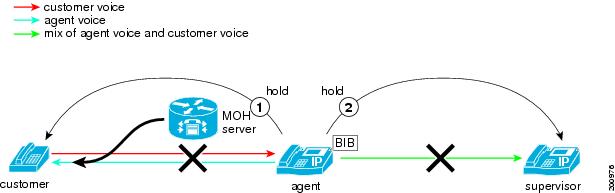
While an agent is being monitored, the agent puts the customer on hold, and the following steps take place:
-
The agent puts the customer on hold. MOH gets inserted and played to the customer.
-
Cisco Unified Communications Manager automatically puts the supervisor on hold. No MOH gets inserted to the supervisor.
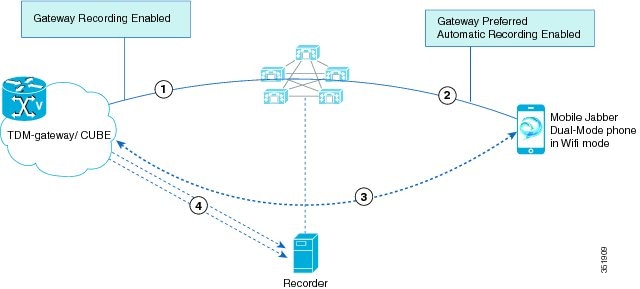
Multiple Monitoring Sessions
The following figure illustrates the call flows during multiple monitoring sessions.
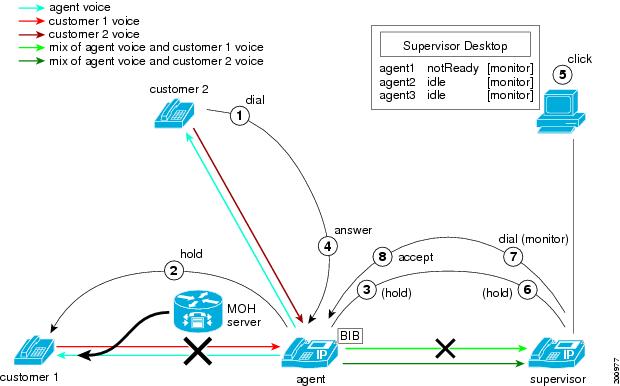
During multiple monitoring sessions, the following steps take place:
-
Customer 2 calls the agent while the agent is in a call with customer 1 and supervisor is monitoring the agent call with customer 1.
-
The agent puts customer 1 on hold; MOH gets inserted to customer 1.
-
Cisco Unified Communications Manager puts the supervisor on hold. No MOH gets inserted to the supervisor.
-
The agent answers the call from customer 2.
-
The supervisor initiates a second monitoring request for the agent call with customer 2.
-
The supervisor phone goes off hook and makes the second monitoring call to the agent.
-
The agent IP phone (BIB of the agent IP phone) automatically accepts the monitoring call. The mix of agent voice and customer 2 voice gets sent to the supervisor phone.
Barging or Monitoring an Agent Call
If the agent call is being monitored, the barge-in call from a shared line fails.
If the agent call has already been barged, the monitoring request gets rejected with a No Resource Available error.
Monitoring an Agent in a Conference
An agent in a call center sometime needs to bring in another party into the conversation with the customer.
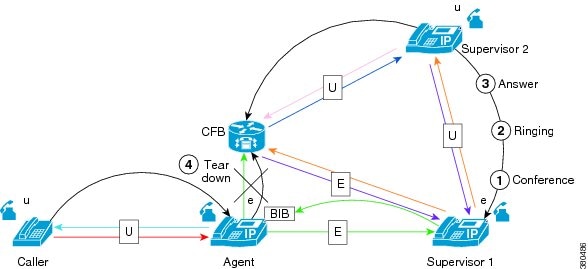
The following figure illustrates a case where agent 1 starts an ad hoc conference to include agent 2 in the conversation with the customer. The supervisor for agent 1 monitors the original call with the customer.
During the setting-up process, the media of the monitoring call briefly disconnect. After the conference completes, the supervisor can hear all the parties that are included in the conference.
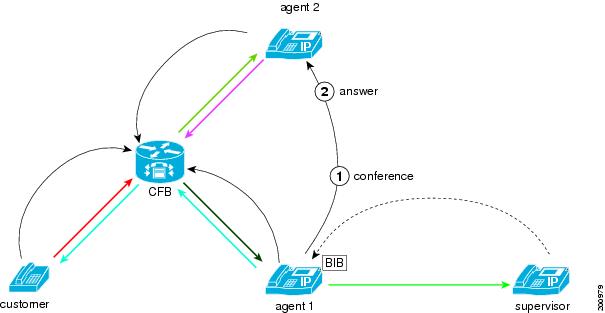
Agent Conferences in the Supervisor
The agent may create a conference with the supervisor while that supervisor is monitoring that agent.
The supervisor must put the monitoring call on hold before joining the conference.
This figure shows the final connection when the supervisor puts the monitoring call on hold and joins the conference. The monitoring session remains in the Hold state while the supervisor participates in the conference. After the supervisor leaves the conference, the supervisor can then resume the monitoring session.
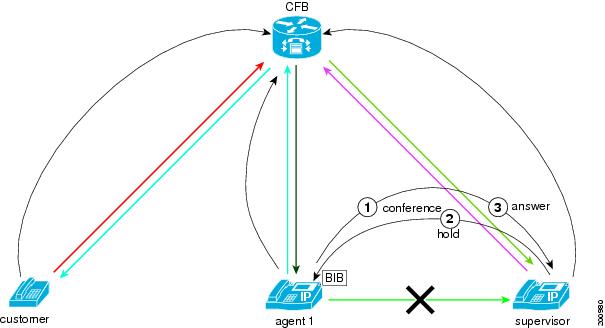
Supervisor Conferences In Another Supervisor
A supervisor can conference in another supervisor for the monitoring session.
The following figure illustrates this scenario.
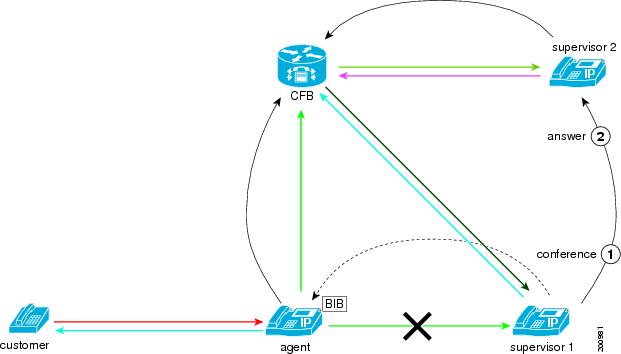
In the example shown, supervisor 1, who started a monitoring call to the agent, conferences in supervisor 2 to the monitoring call. The customer and agent can still hear each other and are not aware of either of the monitoring supervisors. Both supervisor 1 and the supervisor 2 can hear the conversation of the agent with the customer. The two supervisors can hear each other.
Whisper Coaching
Whisper coaching allows supervisors to talk to agents during a monitoring session. To start a whisper coaching session, a monitoring session must already be in progress. A whisper coaching session is initiated by any CTI application (JTAPI/TAPI), such as Cisco Unified Contact Center Enterprise or Cisco Unified Contact Center Express.
Supervisors can toggle between monitoring and whisper coaching sessions as needed using a CTI application.
To enable whisper coaching, follow the instructions to enable monitoring. No additional configuration is needed for whisper coaching.
Secure Silent Monitoring
Secure silent monitoring allows encrypted media (sRTP) calls to be monitored . Monitoring calls are always established using the highest level of security determined by the capabilities of the agent phone regardless of the security status of the call being observed. The highest level of security is maintained by exchanging the secure media key in any call between the customer, agent, and supervisor. Monitoring calls using secured media carries approximately 4000 bits per second of additional bandwidth overhead, same as standard secure media (sRTP) calls.
If the agent phone has encryption enabled, then the supervisor phone must have encryption enabled to silently monitor agent calls. If the agent phone has encryption enabled, but the supervisor phone does not, then requests to monitor the agent are rejected.
Secure Silent Monitoring and Transcoders
Cisco Unified Communications Manager transcoders do not support encrypted media. If a transcoder is required to establish the secure silent monitoring session between supervisor and agent, and the agent's phone is enabled for encrypted media, the monitoring session is not allowed. A tone is played to the supervisor and cause code 57 (Bearer capability not authorized) is used to disconnect the call. The CTI application notifies the supervisor that the monitoring session was disconnected.
Secure Silent Monitoring Icons
The following
table describes the secure icons.
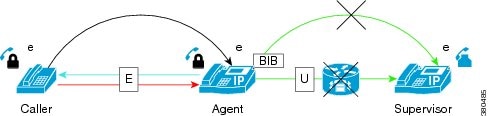
|
Icon |
Description |
|---|---|
|
e |
Indicates that both devices can make and receive secure calls. |
|
E |
Indicates that the call media is encrypted using sRTP. |
|
Lock Symbol |
Indicates that the call is secure. |
Secure Silent Monitoring Usage Scenarios
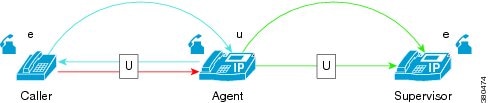
Unsecure Silent Monitoring Call
Supervisor’s phone is enabled for secure media, but the agent is not, so the silent monitoring call is unsecure.
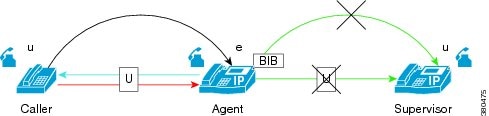
Secure Silent Monitoring Call
Supervisor's phone is not enabled for secure media, but the agent phone is enabled for secure media, so the silent monitoring call is rejected. Supervisor's phone does not meet or exceed security capabilities of agent device.
Encrypted Silent Monitoring Call
All phones support secure media, so all calls are encrypted.
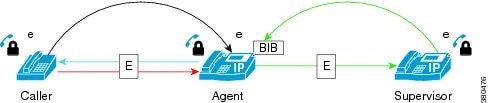
Unencrypted Silent Monitoring Call
Agent and supervisor phones both support secure media, so the silent monitoring call is encrypted, while the customer-agent call is unencrypted.
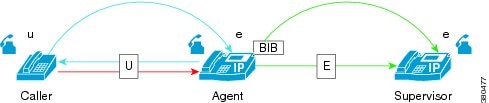
Supervisor Places Monitoring Call On Hold
Supervisor placing the monitoring call on hold has no affect on the caller-agent call. Monitoring session resumes when the supervisor resumes the call.
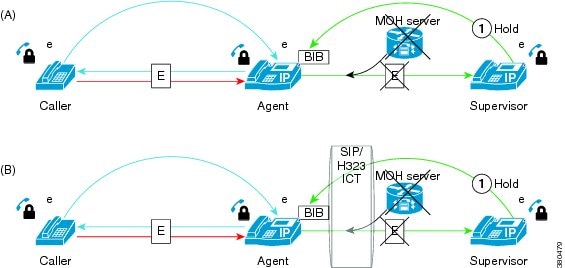
Call Security Upgrades as a Result of the Caller Transfer
Cisco Unified Communications Manager determines if a call should be secured by examining the device capabilities of call-participants. When all call participant devices support sRTP, Cisco Unified Communications Manager automatically secures the call. When one or more call participant devices are not enabled for secure media using Secure Real Time Transfer Protocol (sRTP), the call is unsecure. If the agent device is enabled for sRTP, the Supervisor device must also be enabled for sRTP to establish a monitoring session. When caller 1 transfers to caller 2, the security of the call upgrades to secure media because caller 2’s phone is enabled for sRTP. The Secure Icons appear on the agent and caller 2 phones. The monitoring call is not affected as the supervisor’s phone is enabled for sRTP. The same scenario applies when the caller i-diverts to another destination or if caller 2 resumes the call via a shared line.
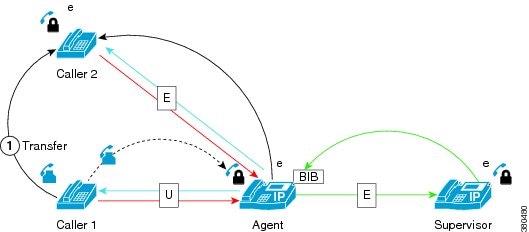
Transfer A Secure Monitoring Session to a Nonsecure Device
-
Supervisor 1 monitors the agent in a secure monitoring session
-
Supervisor 1 then transfers the monitoring call to supervisor 2
-
Since supervisor 2’s device is not enabled for encrypted media, the monitoring call is disconnected.
-
Tone is played to supervisor 2 and cause code 57 (Bearer capability not authorized) is used to disconnect this call.
-
CTI notifies the application connected to the original supervisor who started the monitoring session (supervisor1) that the monitoring session was disconnected.
-
If the monitoring call is held, then resumed using a shared line on another phone not enabled for encryption, the same behavior results
Supervisor Transfers Monitoring Call Across Inter-Cluster Trunk
Cisco
Unified Communications Manager does not support transferring secure
monitoring calls over an Inter-Cluster trunk. The secure monitoring call is
disconnected.call.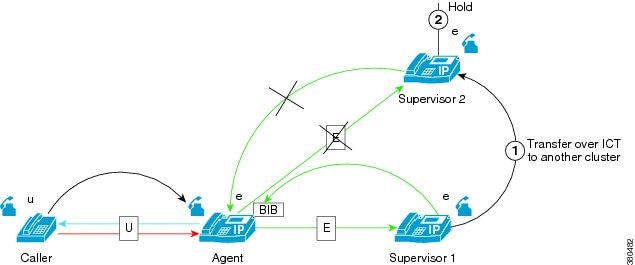
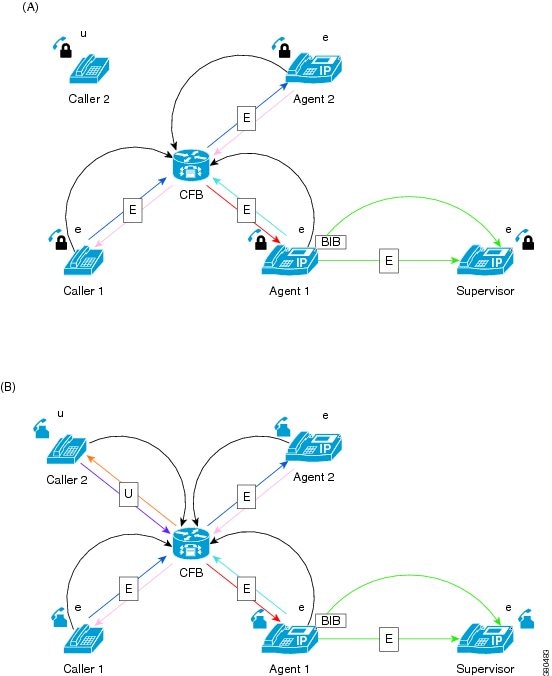
Secure Monitoring a Conference Call
-
Caller 1 and agent 1 are engaged in a secure call
-
Supervisor establishes a secure monitoring session
-
Caller 2 joins the call from a non-secure device, so call security is downgraded to unsecure.
The secure silent monitoring session remains “encrypted” because agent 1 and supervisor both support encrypted media
-
Caller 2 leaves the call
All remaining participants support encryption, so call security is upgraded automatically to use encrypted media
-
The original silent monitoring session was established as a secure call, so it remains unaffected
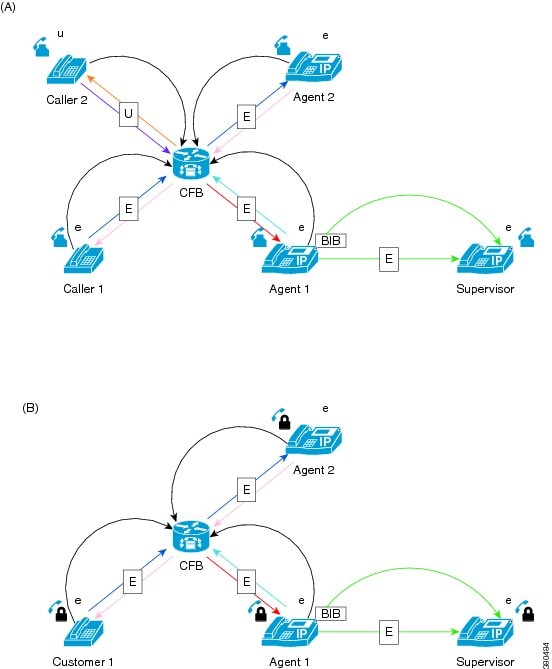
Transfer Secure Silent Monitoring Calls
Supervisors can conference and transfer secure silent monitoring calls. Transfer of secure silent monitoring is possible if the transfer participant phone meets or exceeds the security capabilities of the Agent being monitored.
-
Supervisor 1 is monitoring Agent in a secure monitoring session.
-
Supervisor 1 transfers the call to Supervisor 2, whose phone is not enabled for encryption. When the call is transferred, the secure monitoring session call is disconnected.
-
No tones are played to Supervisor 2. Supervisor 1 receives a CTI notification that the monitoring session was disconnected.
System Requirements
The following section provides the system requirements for monitoring.
Supported Devices
For more information about verification of agent phone models that are supported for call monitoring, see http://developer.cisco.com/web/sip/wikidocs/-/wiki/Main/Unified+CM+Silent+Monitoring+Recording+Supported+Device+Matrix
CTI Requirements
Computer Telephony Integration (CTI) provides the ability for applications to monitor calls on a per-call basis. Cisco defines the monitor target as the party that is monitored (agent) and the monitor initiator as the monitoring party (supervisor).
If a single CTI application monitors both the agent and supervisor phones, that application receives the call events that are necessary for silent monitoring. If different CTI applications monitor the agent and supervisor phones, the CTI application that monitors the agent phone must provide the call information to the application that observes the supervisor phone.
CTI applications that monitor calls must have the corresponding monitoring privileges enabled for the application-user or end-user account.
Configuration
This section provides the steps that are necessary to configure monitoring.
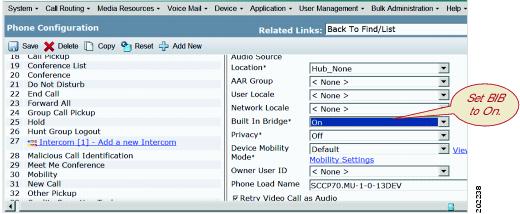
Turn on IP Phone Built-In-Bridge to Allow Monitoring
The built-in bridge (BIB) of the agent phone must be set to On to allow its calls to be monitored.
You can also set the Built-in Bridge Enable service parameter to On and leave the Built-in Bridge in the Phone Configuration window set to Default.
Use the menu option in Cisco Unified Communications Manager Administration to perform the necessary configuration.
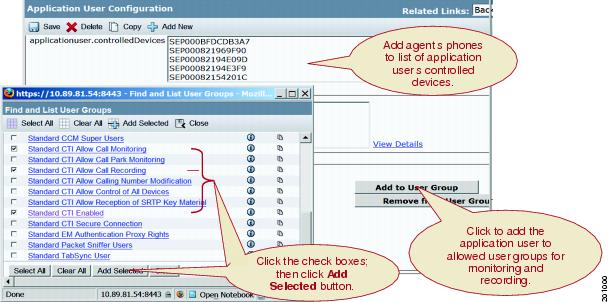
Add Supervisor to Groups That Allow Monitoring
Add the supervisor to the user groups: Standard CTI Allow Call Monitoring user group and the Standard CTI Enabled user group.
Use the User Management menu option in Cisco Unified Communications Manager Administration to perform the necessary configuration.
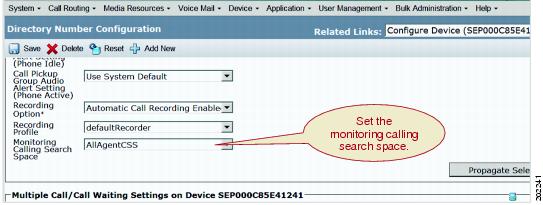
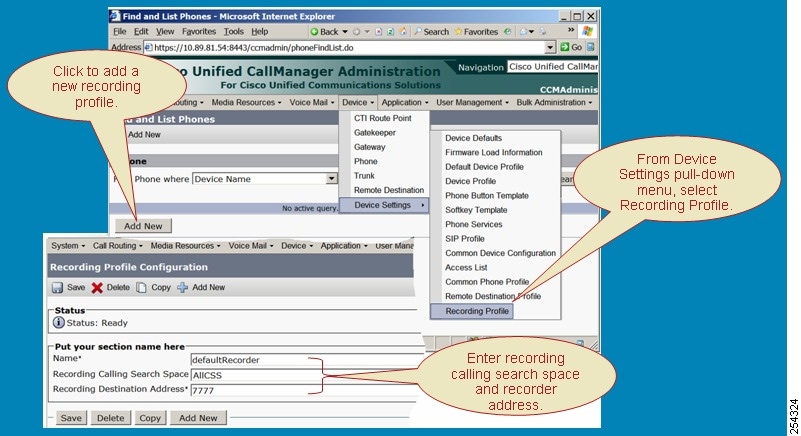
Configure Monitoring Calling Search Space
The monitoring calling search space of the supervisor line appearance must include the agent line or device partition.
Set the monitoring calling search space in the supervisor line appearance window.
Use the menu option in Cisco Unified Communications Manager Administration to perform the necessary configuration. When you display the Phone Configuration window for a phone, click on a line, such as Line [1], in the Association Information pane. (You can choose either a DN that is already associated with this phone or you can add a new DN to associate with this phone.) In the Directory Number Configuration window that displays, configure the Monitoring Calling Search Space field for the chosen line on this phone.
Configure Notification Tones for Monitoring
Set the service parameters for playing tone to True to allow tones to be played to the agent, the customer, or both.
CTI applications that initiate monitoring can also pass the play tone option to Cisco Unified Communications Manager. The monitoring tone plays when either the service parameter or the CTI application specifies the play tone option.
Use the menu option in Cisco Unified Communications Manager Administration to configure notification tones for monitoring.
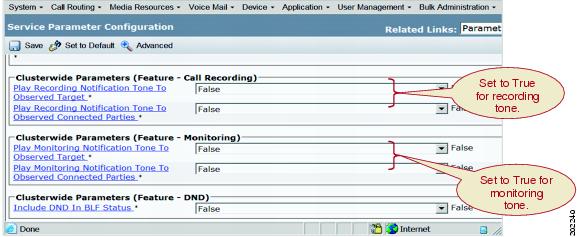
Set the Monitoring Service Parameters
This section describes the service parameters that are related to the silent monitoring feature.
Notification
The following service parameters affect the playing of notification tones to the parties that are monitored by the call monitoring feature:
Clusterwide Parameters (Feature - Monitoring)
-
Play Monitoring Notification Tone To Observed Target
-
Play Monitoring Notification Tone To Observed Connected Parties
The default value for these service parameters is False. You must change the value of each parameter to True to enable the particular notification tone to play.
Built-In-Bridge
The following service parameter enables or disables the built-in bridge on phones:
Clusterwide Parameters (Device - Phone)
Built-in Bridge Enable
For more information about this service parameter, see "Turn on IP phone BIB to allow Monitoring".
Secure Silent Monitoring Provisioning Phone Configuration
To configure the phone for secure silent monitoring, follow these steps:
Procedure
| Step 1 |
Create a security profile for the Supervisor's phone type. |
| Step 2 |
Set the Device Security Mode in the security profile to Encrypted. |
| Step 3 |
Apply the device security profile to the Supervisor's device. |


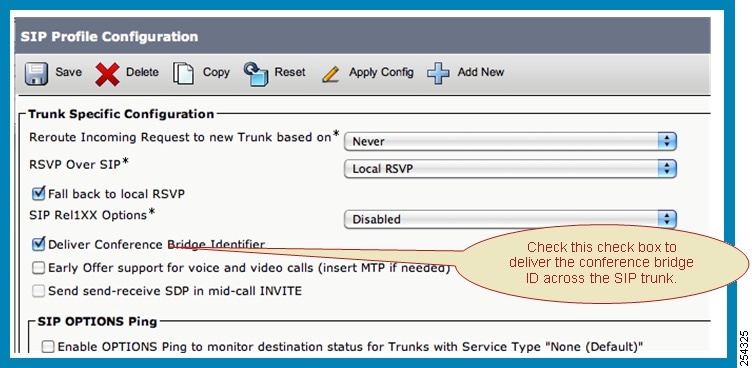
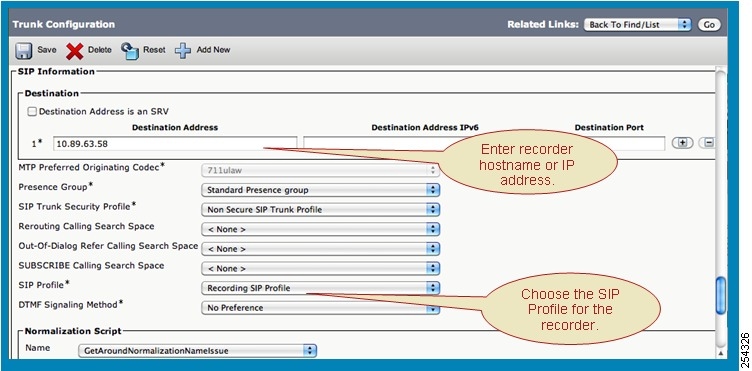
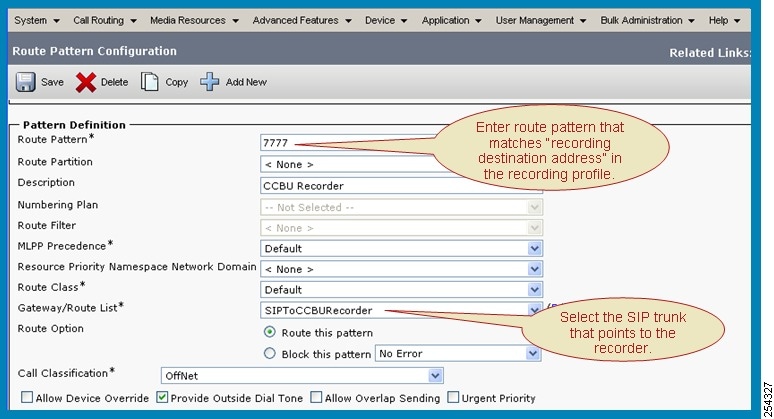
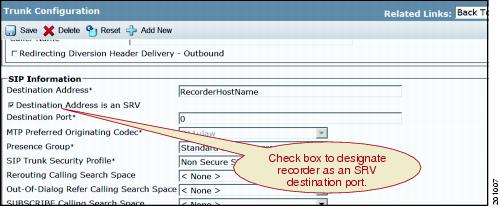
 Feedback
Feedback