Bidirectional Forwarding Detection
This document describes how to enable the Bidirectional Forwarding Detection (BFD) protocol. BFD is a detection protocol that is designed to provide fast forwarding path failure detection times for all media types, encapsulations, topologies, and routing protocols.
BFD provides a consistent failure detection method for network administrators, in addition to fast forwarding path failure detection. Because the network administrator can use BFD to detect forwarding path failures at a uniform rate, rather than the variable rates for different routing protocol hello mechanisms, network profiling and planning will be easier, and reconvergence time will be consistent and predictable.
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for Bidirectional Forwarding Detection
-
Cisco Express Forwarding and IP routing must be enabled on all participating switches.
-
One of the IP routing protocols supported by BFD must be configured on the switches before BFD is deployed. You should implement fast convergence for the routing protocol that you are using. See the IP routing documentation for your version of Cisco IOS software for information on configuring fast convergence. See the Restrictions for Bidirectional Forwarding Detection section for more information on BFD routing protocol support in Cisco IOS software.
Restrictions for Bidirectional Forwarding Detection
-
BFD works only for directly connected neighbors. BFD neighbors must be no more than one IP hop away. Multihop configurations are not supported.
-
BFD support is not available for all platforms and interfaces. To confirm BFD support for a specific platform or interface and obtain the most accurate platform and hardware restrictions, see the Cisco IOS software release notes for your software version.
-
BFD packets are not matched in the QoS policy for self-generated packets.
-
BFD packets are matched in the class class-default command. So, the user must make sure of the availability of appropriate bandwidth to prevent dropping of BFD packets due to oversubscription.
-
BFD HA support is not available starting Cisco Denali IOS XE 16.3.1
Information About Bidirectional Forwarding Detection
BFD Operation
BFD provides a low-overhead, short-duration method of detecting failures in the forwarding path between two adjacent routers, including the interfaces, data links, and forwarding planes.
BFD is a detection protocol that you enable at the interface and routing protocol levels. Cisco supports BFD asynchronous mode, which depends on the sending of BFD control packets between two systems to activate and maintain BFD neighbor sessions between routers. Therefore, in order for a BFD session to be created, you must configure BFD on both systems (or BFD peers). Once BFD has been enabled on the interfaces and at the router level for the appropriate routing protocols, a BFD session is created, BFD timers are negotiated, and the BFD peers will begin to send BFD control packets to each other at the negotiated interval.
Neighbor Relationships
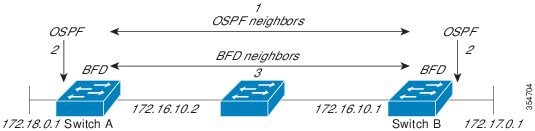
BFD provides fast BFD peer failure detection times independently of all media types, encapsulations, topologies, and routing protocols BGP, EIGRP, IS-IS, and OSPF. By sending rapid failure detection notices to the routing protocols in the local router to initiate the routing table recalculation process, BFD contributes to greatly reduced overall network convergence time. The figure below shows a simple network with two routers running OSPF and BFD. When OSPF discovers a neighbor (1) it sends a request to the local BFD process to initiate a BFD neighbor session with the OSPF neighbor router (2). The BFD neighbor session with the OSPF neighbor router is established (3).
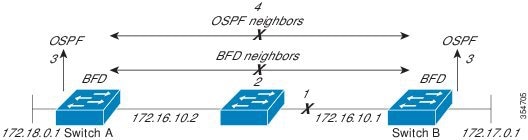
The figure below shows what happens when a failure occurs in the network (1). The BFD neighbor session with the OSPF neighbor router is torn down (2). BFD notifies the local OSPF process that the BFD neighbor is no longer reachable (3). The local OSPF process tears down the OSPF neighbor relationship (4). If an alternative path is available, the routers will immediately start converging on it.
A routing protocol needs to register with BFD for every neighbor it acquires. Once a neighbor is registered, BFD initiates a session with the neighbor if a session does not already exist.
OSPF registers with BFD when:
-
A neighbor finite state machine (FSM) transitions to full state.
-
Both OSPF BFD and BFD are enabled.
On broadcast interfaces, OSPF establishes a BFD session only with the designated router (DR) and backup designated router (BDR), but not between any two routers in DROTHER state.
BFD Detection of Failures
Once a BFD session has been established and timer negations are complete, BFD peers send BFD control packets that act in the same manner as an IGP hello protocol to detect liveliness, except at a more accelerated rate. The following information should be noted:
-
BFD is a forwarding path failure detection protocol. BFD detects a failure, but the routing protocol must take action to bypass a failed peer.
-
Starting Cisco IOS XE Denali 16.3.1, Cisco devices will support BFD version 0, where devices will use one BFD session for multiple client protocols in the implementation. For example, if a network is running OSPF and EIGRP across the same link to the same peer, only one BFD session will be established, and BFD will share session information with both routing protocols.
BFD Version Interoperability
All BFD sessions come up as Version 1 by default and will be interoperable with Version 0. The system automatically performs BFD version detection, and BFD sessions between neighbors will run in the highest common BFD version between neighbors. For example, if one BFD neighbor is running BFD Version 0 and the other BFD neighbor is running Version 1, the session will run BFD Version 0. The output from the show bfd neighbors [details ] command will verify which BFD version a BFD neighbor is running.
See the Example Configuring BFD in an EIGRP Network with Echo Mode Enabled by Default for an example of BFD version detection.
BFD Session Limits
Starting Cisco IOS XE Denali 16.3.1, the number of BFD sessions that can be created has been increased to 100.
BFD Support for Nonbroadcast Media Interfaces
Starting Cisco IOS XE Denali 16.3.1, the BFD feature is supported on routed, SVI and L3 portchannels.
The bfd interval command must be configured on the interface to initiate BFD monitoring.
BFD Support for Nonstop Forwarding with Stateful Switchover
Typically, when a networking device restarts, all routing peers of that device detect that the device went down and then came back up. This transition results in a routing flap, which could spread across multiple routing domains. Routing flaps caused by routing restarts create routing instabilities, which are detrimental to the overall network performance. Nonstop forwarding (NSF) helps to suppress routing flaps in devices that are enabled with stateful switchover (SSO), thereby reducing network instability.
NSF allows for the forwarding of data packets to continue along known routes while the routing protocol information is being restored after a switchover. With NSF, peer networking devices do not experience routing flaps. Data traffic is forwarded through intelligent line cards or dual forwarding processors while the standby RP assumes control from the failed active RP during a switchover. The ability of line cards and forwarding processors to remain up through a switchover and to be kept current with the Forwarding Information Base (FIB) on the active RP is key to NSF operation.
In devices that support dual RPs, SSO establishes one of the RPs as the active processor; the other RP is designated as the standby processor, and then synchronizes information between them. A switchover from the active to the standby processor occurs when the active RP fails, when it is removed from the networking device, or when it is manually taken down for maintenance.
BFD Support for Stateful Switchover
The BFD protocol provides short-duration detection of failures in the path between adjacent forwarding engines. In network deployments that use dual RP routers or switches (to provide redundancy), the routers have a graceful restart mechanism that protects the forwarding state during a switchover between the active RP and the standby RP.
The dual RPs have variable switchover times that depend on the ability of the hardware to detect a communication failure. When BFD is running on the RP, some platforms are not able to detect a switchover before the BFD protocol times out; these platforms are referred to as slow switchover platforms.
BFD Support for Static Routing
Unlike dynamic routing protocols, such as OSPF and BGP, static routing has no method of peer discovery. Therefore, when BFD is configured, the reachability of the gateway is completely dependent on the state of the BFD session to the specified neighbor. Unless the BFD session is up, the gateway for the static route is considered unreachable, and therefore the affected routes will not be installed in the appropriate Routing Information Base (RIB).
For a BFD session to be successfully established, BFD must be configured on the interface on the peer and there must be a BFD client registered on the peer for the address of the BFD neighbor. When an interface is used by dynamic routing protocols, the latter requirement is usually met by configuring the routing protocol instances on each neighbor for BFD. When an interface is used exclusively for static routing, this requirement must be met by configuring static routes on the peers.
If a BFD configuration is removed from the remote peer while the BFD session is in the up state, the updated state of the BFD session is not signaled to IPv4 static. This will cause the static route to remain in the RIB. The only workaround is to remove the IPv4 static BFD neighbor configuration so that the static route no longer tracks BFD session state. Also, if you change the encapsulation type on a serial interface to one that is unsupported by BFD, BFD will be in a down state on that interface. The workaround is to shut down the interface, change to a supported encapsulation type, and then reconfigure BFD.
A single BFD session can be used by an IPv4 static client to track the reachability of next hops through a specific interface. You can assign a BFD group for a set of BFD-tracked static routes. Each group must have one active static BFD configuration, one or more passive BFD configurations, and the corresponding static routes to be BFD-tracked. Nongroup entries are BFD-tracked static routes for which a BFD group is not assigned. A BFD group must accommodate static BFD configurations that can be part of different VRFs. Effectively, the passive static BFD configurations need not be in the same VRF as that of the active configuration.
For each BFD group, there can be only one active static BFD session. You can configure the active BFD session by adding a static BFD configuration and a corresponding static route that uses the BFD configuration. The BFD session in a group is created only when there is an active static BFD configuration and the static route that uses the static BFD configuration. When the active static BFD configuration or the active static route is removed from a BFD group, all the passive static routes are withdrawn from the RIB. Effectively, all the passive static routes are inactive until an active static BFD configuration and a static route to be tracked by the active BFD session are configured in the group.
Similarly, for each BFD group, there can be one or more passive static BFD configurations and their corresponding static routes to be BFD-tracked. Passive static session routes take effect only when the active BFD session state is reachable. Though the active BFD session state of the group is reachable, the passive static route is added to the RIB only if the corresponding interface state is up. When a passive BFD session is removed from a group, it will not affect the active BFD session if one existed, or the BFD group reachability status.
Benefits of Using BFD for Failure Detection
When you deploy any feature, it is important to consider all the alternatives and be aware of any trade-offs being made.
The closest alternative to BFD in conventional EIGRP, IS-IS, and OSPF deployments is the use of modified failure detection mechanisms for EIGRP, IS-IS, and OSPF routing protocols.
If you set EIGRP hello and hold timers to their absolute minimums, the failure detection rate for EIGRP falls to within a one- to two-second range.
If you use fast hellos for either IS-IS or OSPF, these Interior Gateway Protocol (IGP) protocols reduce their failure detection mechanisms to a minimum of one second.
There are several advantages to implementing BFD over reduced timer mechanisms for routing protocols:
-
Although reducing the EIGRP, IS-IS, and OSPF timers can result in minimum detection timer of one to two seconds, BFD can provide failure detection in less than one second.
-
Because BFD is not tied to any particular routing protocol, it can be used as a generic and consistent failure detection mechanism for EIGRP, IS-IS, and OSPF.
-
Because some parts of BFD can be distributed to the data plane, it can be less CPU-intensive than the reduced EIGRP, IS-IS, and OSPF timers, which exist wholly at the control plane.
How to Configure Bidirectional Forwarding Detection
Configuring BFD Session Parameters on the Interface
To configure BFD on an interface, you need to set the baseline BFD session parameters on an interface. Repeat the steps in this procedure for each interface over which you want to run BFD sessions to BFD neighbors.
Procedure
| Command or Action | Purpose | |
|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode.
|
|
Step 2 |
configure terminal Example: |
Enters global configuration mode. |
|
Step 3 |
Perform one of the following steps:
Example: |
|
|
Step 4 |
bfd interval milliseconds min_rx milliseconds multiplier interval-multiplier Example: |
Enables BFD on the interface. The BFD interval configuration is removed when the subinterface on which it is configured is removed.
|
|
Step 5 |
end Example: |
Exits interface configuration mode and returns to privileged EXEC mode. |
Configuring BFD Support for Dynamic Routing Protocols
Configuring BFD Support for eBGP
This section describes the procedure for configuring BFD support for BGP so that BGP is a registered protocol with BFD and will receive forwarding path detection failure messages from BFD.
Before you begin
e BGP must be running on all participating routers.
The baseline parameters for BFD sessions on the interfaces over which you want to run BFD sessions to BFD neighbors must be configured. See the Configuring BFD Session Parameters on the Interface section for more information.
 Note |
Output from the show bfd neighbors details command shows the configured intervals. |
Procedure
| Command or Action | Purpose | |
|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode.
|
|
Step 2 |
configure terminal Example: |
Enters global configuration mode. |
|
Step 3 |
router bgp as-tag Example: |
Specifies a BGP process and enters router configuration mode. |
|
Step 4 |
neighbor ip-address fall-over bfd Example: |
Enables BFD support for fallover. |
|
Step 5 |
end Example: |
Exits router configuration mode and returns the router to privileged EXEC mode. |
|
Step 6 |
show bfd neighbors [details ] Example: |
(Optional) Verifies that the BFD neighbor is active and displays the routing protocols that BFD has registered. |
|
Step 7 |
show ip bgp neighbor Example: |
(Optional) Displays information about BGP and TCP connections to neighbors. |
Configuring BFD Support for EIGRP
This section describes the procedure for configuring BFD support for EIGRP so that EIGRP is a registered protocol with BFD and will receive forwarding path detection failure messages from BFD. There are two methods for enabling BFD support for EIGRP:
-
You can enable BFD for all of the interfaces for which EIGRP is routing by using the bfd all-interfaces command in router configuration mode.
-
You can enable BFD for a subset of the interfaces for which EIGRP is routing by using the bfd interface type number command in router configuration mode.
Before you begin
EIGRP must be running on all participating routers.
The baseline parameters for BFD sessions on the interfaces over which you want to run BFD sessions to BFD neighbors must be configured. See the Configuring BFD Session Parameters on the Interface section for more information.
 Note |
Output from the show bfd neighbors details command shows the configured intervals. |
Procedure
| Command or Action | Purpose | |
|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode.
|
|
Step 2 |
configure terminal Example: |
Enters global configuration mode. |
|
Step 3 |
router eigrp as-number Example: |
Configures the EIGRP routing process and enters router configuration mode. |
|
Step 4 |
Do one of the following:
Example:Example: |
Enables BFD globally on all interfaces associated with the EIGRP routing process. or Enables BFD on a per-interface basis for one or more interfaces associated with the EIGRP routing process. |
|
Step 5 |
end Example: |
Exits router configuration mode and returns the router to privileged EXEC mode. |
|
Step 6 |
show bfd neighbors [details ] Example: |
(Optional) Verifies that the BFD neighbor is active and displays the routing protocols that BFD has registered. |
|
Step 7 |
show ip eigrp interfaces [type number ] [as-number ] [detail ] Example: |
(Optional) Displays the interfaces for which BFD support for EIGRP has been enabled. |
Configuring BFD Support for IS-IS
This section describes the procedures for configuring BFD support for IS-IS so that IS-IS is a registered protocol with BFD and will receive forwarding path detection failure messages from BFD. There are two methods for enabling BFD support for IS-IS:
-
You can enable BFD for all of the interfaces on which IS-IS is supporting IPv4 routing by using the bfd all-interfaces command in router configuration mode. You can then disable BFD for one or more of those interfaces using the isis bfd disable command in interface configuration mode.
-
You can enable BFD for a subset of the interfaces for which IS-IS is routing by using the isis bfd command in interface configuration mode.
To configure BFD support for IS-IS, perform the steps in one of the following sections:
Prerequisites
IS-IS must be running on all participating routers.
The baseline parameters for BFD sessions on the interfaces that you want to run BFD sessions to BFD neighbors over must be configured. See the Configuring BFD Session Parameters on the Interface section for more information.
 Note |
Output from the show bfd neighbors details command shows the configured intervals. The output does not show intervals that were changed because hardware-offloaded BFD sessions were configured with Tx and Rx intervals that are not multiples of 50 ms. |
Configuring BFD Support for IS-IS for All Interfaces
To configure BFD on all IS-IS interfaces that support IPv4 routing, perform the steps in this section.
Procedure
| Command or Action | Purpose | |||
|---|---|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode.
|
||
|
Step 2 |
configure terminal Example: |
Enters global configuration mode. |
||
|
Step 3 |
router isis area-tag Example: |
Specifies an IS-IS process and enters router configuration mode. |
||
|
Step 4 |
bfd all-interfaces Example: |
Enables BFD globally on all interfaces associated with the IS-IS routing process. |
||
|
Step 5 |
exit Example: |
(Optional) Returns the router to global configuration mode. |
||
|
Step 6 |
interface type number Example: |
(Optional) Enters interface configuration mode. |
||
|
Step 7 |
ip router isis [ tag ] Example: |
(Optional) Enables support for IPv4 routing on the interface. |
||
|
Step 8 |
isis bfd [disable ] Example: |
(Optional) Enables or disables BFD on a per-interface basis for one or more interfaces associated with the IS-IS routing process.
|
||
|
Step 9 |
end Example: |
Exits interface configuration mode and returns the router to privileged EXEC mode. |
||
|
Step 10 |
show bfd neighbors [details ] Example: |
(Optional) Displays information that can be used to verify if the BFD neighbor is active and displays the routing protocols that BFD has registered. |
||
|
Step 11 |
show clns interface Example: |
(Optional) Displays information that can be used to verify if BFD for IS-IS has been enabled for a specific IS-IS interface that is associated. |
Configuring BFD Support for IS-IS for One or More Interfaces
To configure BFD for only one or more IS-IS interfaces, perform the steps in this section.
Procedure
| Command or Action | Purpose | |||
|---|---|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode.
|
||
|
Step 2 |
configure terminal Example: |
Enters global configuration mode. |
||
|
Step 3 |
interface type number Example: |
Enters interface configuration mode. |
||
|
Step 4 |
ip router isis [ tag ] Example: |
Enables support for IPv4 routing on the interface. |
||
|
Step 5 |
isis bfd [disable] Example: |
Enables or disables BFD on a per-interface basis for one or more interfaces associated with the IS-IS routing process.
|
||
|
Step 6 |
end Example: |
Exits interface configuration mode and returns the router to privileged EXEC mode. |
||
|
Step 7 |
show bfd neighbors [details ] Example: |
(Optional) Displays information that can help verify if the BFD neighbor is active and displays the routing protocols that BFD has registered. |
||
|
Step 8 |
show clns interface Example: |
(Optional) Displays information that can help verify if BFD for IS-IS has been enabled for a specific IS-IS interface that is associated. |
Configuring BFD Support for OSPF
This section describes the procedures for configuring BFD support for OSPF so that OSPF is a registered protocol with BFD and will receive forwarding path detection failure messages from BFD. You can either configure BFD support for OSPF globally on all interfaces or configure it selectively on one or more interfaces.
There are two methods for enabling BFD support for OSPF:
-
You can enable BFD for all of the interfaces for which OSPF is routing by using the bfd all-interfaces command in router configuration mode. You can disable BFD support on individual interfaces using the ip ospf bfd [disable ] command in interface configuration mode.
-
You can enable BFD for a subset of the interfaces for which OSPF is routing by using the ip ospf bfd command in interface configuration mode.
See the following sections for tasks for configuring BFD support for OSPF:
Configuring BFD Support for OSPF for All Interfaces
To configure BFD for all OSPF interfaces, perform the steps in this section.
If you do not want to configure BFD on all OSPF interfaces and would rather configure BFD support specifically for one or more interfaces, see the Configuring BFD Support for OSPF for One or More Interfaces section.
Before you begin
OSPF must be running on all participating routers.
The baseline parameters for BFD sessions on the interfaces over which you want to run BFD sessions to BFD neighbors must be configured. See the Configuring BFD Session Parameters on the Interface section for more information.
Procedure
| Command or Action | Purpose | |||
|---|---|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode.
|
||
|
Step 2 |
configure terminal Example: |
Enters global configuration mode. |
||
|
Step 3 |
router ospf process-id Example: |
Specifies an OSPF process and enters router configuration mode. |
||
|
Step 4 |
bfd all-interfaces Example: |
Enables BFD globally on all interfaces associated with the OSPF routing process. |
||
|
Step 5 |
exit Example: |
(Optional) Returns the device to global configuration mode. Enter this command only if you want to perform Step 7 to disable BFD for one or more interfaces. |
||
|
Step 6 |
interface type number Example: |
(Optional) Enters interface configuration mode. Enter this command only if you want to perform Step 7 to disable BFD for one or more interfaces. |
||
|
Step 7 |
ip ospf bfd [disable ] Example: |
(Optional) Disables BFD on a per-interface basis for one or more interfaces associated with the OSPF routing process.
|
||
|
Step 8 |
end Example: |
Exits interface configuration mode and returns the router to privileged EXEC mode. |
||
|
Step 9 |
show bfd neighbors [details ] Example: |
(Optional) Displays information that can help verify if the BFD neighbor is active and displays the routing protocols that BFD has registered. |
||
|
Step 10 |
show ip ospf Example: |
(Optional) Displays information that can help verify if BFD for OSPF has been enabled. |
Configuring BFD Support for OSPF for One or More Interfaces
To configure BFD on one or more OSPF interfaces, perform the steps in this section.
Before you begin
OSPF must be running on all participating routers.
The baseline parameters for BFD sessions on the interfaces over which you want to run BFD sessions to BFD neighbors must be configured. See the Configuring BFD Session Parameters on the Interface section for more information.
Procedure
| Command or Action | Purpose | |||
|---|---|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode.
|
||
|
Step 2 |
configure terminal Example: |
Enters global configuration mode. |
||
|
Step 3 |
interface type number Example: |
Enters interface configuration mode. |
||
|
Step 4 |
ip ospf bfd [disable ] Example: |
Enables or disables BFD on a per-interface basis for one or more interfaces associated with the OSPF routing process.
|
||
|
Step 5 |
end Example: |
Exits interface configuration mode and returns the router to privileged EXEC mode. |
||
|
Step 6 |
show bfd neighbors [details ] Example: |
(Optional) Displays information that can help verify if the BFD neighbor is active and displays the routing protocols that BFD has registered. |
||
|
Step 7 |
show ip ospf Example: |
(Optional) Displays information that can help verify if BFD support for OSPF has been enabled. |
Configuring BFD Support for HSRP
Perform this task to enable BFD support for Hot Standby Router Protocol (HSRP.) Repeat the steps in this procedure for each interface over which you want to run BFD sessions to HSRP peers.
HSRP supports BFD by default. If HSRP support for BFD has been manually disabled, you can reenable it at the router level to enable BFD support globally for all interfaces or on a per-interface basis at the interface level.
Before you begin
-
HSRP must be running on all participating routers.
-
Cisco Express Forwarding must be enabled.
Procedure
| Command or Action | Purpose | |
|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode.
|
|
Step 2 |
configure terminal Example: |
Enters global configuration mode. |
|
Step 3 |
ip cef [distributed ] Example: |
Enables Cisco Express Forwarding or distributed Cisco Express Forwarding. |
|
Step 4 |
interface type number Example: |
Enters interface configuration mode. |
|
Step 5 |
ip address ip-address mask Example: |
Configures an IP address for the interface. |
|
Step 6 |
standby [group-number ] ip [ip-address [secondary ]] Example: |
Activates HSRP. |
|
Step 7 |
standby bfd Example: |
(Optional) Enables HSRP support for BFD on the interface. |
|
Step 8 |
exit Example: |
Exits interface configuration mode. |
|
Step 9 |
standby bfd all-interfaces Example: |
(Optional) Enables HSRP support for BFD on all interfaces. |
|
Step 10 |
exit Example: |
Exits global configuration mode. |
|
Step 11 |
show standby neighbors Example: |
(Optional) Displays information about HSRP support for BFD. |
Configuring BFD Support for Static Routing
Perform this task to configure BFD support for static routing. Repeat the steps in this procedure on each BFD neighbor. For more information, see the "Example: Configuring BFD Support for Static Routing" section.
Procedure
| Command or Action | Purpose | |
|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode.
|
|
Step 2 |
configure terminal Example: |
Enters global configuration mode. |
|
Step 3 |
interface type number Example: |
Configures an interface and enters interface configuration mode. |
|
Step 4 |
Perform one of the following steps:
Example: |
|
|
Step 5 |
bfd interval milliseconds mix_rx milliseconds multiplier interval-multiplier Example: |
Enables BFD on the interface. The bfd interval configuration is removed when the subinterface on which it is configured is removed.
|
|
Step 6 |
exit Example: |
Exits interface configuration mode and returns to global configuration mode. |
|
Step 7 |
ip route static bfd interface-type interface-number ip-address [group group-name [passive]] Example: |
Specifies a static route BFD neighbor.
|
|
Step 8 |
ip route [vrf vrf-name] prefix mask {ip-address | interface-type interface-number [ip-address]} [dhcp] [distance] [name next-hop-name] [permanent | track number] [tag tag] Example: |
Specifies a static route BFD neighbor. |
|
Step 9 |
exit Example: |
Exits global configuration mode and returns to privileged EXEC mode. |
|
Step 10 |
show ip static route Example: |
(Optional) Displays static route database information. |
|
Step 11 |
show ip static route bfd Example: |
(Optional) Displays information about the static BFD configuration from the configured BFD groups and nongroup entries. |
|
Step 12 |
exit Example: |
Exits privileged EXEC mode and returns to user EXEC mode. |
Configuring BFD Echo Mode
BFD echo mode is enabled by default, but you can disable it such that it can run independently in each direction.
BFD echo mode works with asynchronous BFD. Echo packets are sent by the forwarding engine and forwarded back along the same path in order to perform detection--the BFD session at the other end does not participate in the actual forwarding of the echo packets. The echo function and the forwarding engine are responsible for the detection process; therefore, the number of BFD control packets that are sent out between two BFD neighbors is reduced. In addition, because the forwarding engine is testing the forwarding path on the remote (neighbor) system without involving the remote system, there is an opportunity to improve the interpacket delay variance, thereby achieving quicker failure detection times than when using BFD Version 0 with BFD control packets for the BFD session.
Echo mode is described as without asymmetry when it is running on both sides (both BFD neighbors are running echo mode).
Prerequisites
BFD must be running on all participating routers.
Before using BFD echo mode, you must disable the sending of Internet Control Message Protocol (ICMP) redirect messages by entering the no ip redirects command, in order to avoid high CPU utilization.
The baseline parameters for BFD sessions on the interfaces over which you want to run BFD sessions to BFD neighbors must be configured. See the Configuring BFD Session Parameters on the Interface section for more information.
Restrictions
BFD echo mode does not work in conjunction with Unicast Reverse Path Forwarding (uRPF) configuration. If BFD echo mode and uRPF configurations are enabled, then the sessions will flap.
Disabling BFD Echo Mode Without Asymmetry
The steps in this procedure show how to disable BFD echo mode without asymmetry—no echo packets will be sent by the router, and the router will not forward BFD echo packets that are received from any neighbor routers.
Repeat the steps in this procedure for each BFD router.
Procedure
| Command or Action | Purpose | |
|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode.
|
|
Step 2 |
configure terminal Example: |
Enters global configuration mode. |
|
Step 3 |
no bfd echo Example: |
Disables BFD echo mode.
|
|
Step 4 |
end Example: |
Exits global configuration mode and returns to privileged EXEC mode. |
Creating and Configuring BFD Templates
You can configure a single-hop template to specify a set of BFD interval values. BFD interval values specified as part of the BFD template are not specific to a single interface.
 Note |
Configuring bfd-template will disable echo mode. |
Configuring a Single-Hop Template
Perform this task to create a BFD single-hop template and configure BFD interval timers.
Procedure
| Command or Action | Purpose | |
|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode.
|
|
Step 2 |
configure terminal Example: |
Enters global configuration mode. |
|
Step 3 |
bfd-template single-hop template-name Example: |
Creates a single-hop BFD template and enters BFD configuration mode. |
|
Step 4 |
interval min-tx milliseconds min-rx milliseconds multiplier multiplier-value Example: |
Configures the transmit and receive intervals between BFD packets, and specifies the number of consecutive BFD control packets that must be missed before BFD declares that a peer is unavailable. |
|
Step 5 |
end Example: |
Exits BFD configuration mode and returns the device to privileged EXEC mode. |
Monitoring and Troubleshooting BFD
This section describes how to retrieve BFD information for maintenance and troubleshooting. The commands in these tasks can be entered as needed, in any order desired.
This section contains information for monitoring and troubleshooting BFD for the following Cisco platforms:
Monitoring and Troubleshooting BFD
To monitor or troubleshoot BFD on Cisco 7600 series routers, perform one or more of the steps in this section.
Procedure
| Command or Action | Purpose | |
|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode.
|
|
Step 2 |
show bfd neighbors [details ] Example: |
(Optional) Displays the BFD adjacency database.
|
|
Step 3 |
debug bfd [packet | event ] Example: |
(Optional) Displays debugging information about BFD packets. |
Feature Information for Bidirectional Forwarding Detection
|
Feature Name |
Release |
Feature Information |
|---|---|---|
| Bidirectional Forwarding Detection |
Cisco IOS XE Everest 16.5.1a |
This feature was introduced |
 Feedback
Feedback