- Release 15.5SY Supervisor Engine 6T Software Configuration Guide
- Preface
- Product Overview
- Command-Line Interfaces
- Smart Port Macros
- Virtual Switching Systems (VSS)
- Enhanced Fast Software Upgrade (eFSU)
- Fast Software Upgrades
- Stateful Switchover (SSO)
- Non-Stop Forwarding (NSF)
- RPR Supervisor Engine Redundancy
- Interface Configuration
- UniDirectional Link Detection (UDLD)
- Instant Access
- EnergyWise
- Power Management
- Environmental Monitoring
- Online Diagnostics
- Onboard Failure Logging (OBFL)
- Switch Fabric Functionality
- Cisco IP Phone Support
- Power over Ethernet
- Layer 2 LAN Port Configuration
- Flex Links
- EtherChannels
- IEEE 802.1ak MVRP and MRP
- VLAN Trunking Protocol (VTP)
- VLANs
- Private VLANs (PVLANs)
- Private Hosts
- IEEE 802.1Q Tunneling
- Layer 2 Protocol Tunneling
- Spanning Tree Protocols (STP, MST)
- Optional STP Features
- IP Unicast Layer 3 Switching
- Policy Based Routing (PBR)
- Layer 3 Interface Configuration
- Unidirectional Ethernet (UDE) and unidirectional link routing (UDLR)
- Multiprotocol Label Switching (MPLS)
- MPLS VPN Support
- Ethernet over MPLS (EoMPLS)
- Virtual Private LAN Services (VPLS)
- L2VPN Advanced VPLS (A-VPLS)
- Ethernet Virtual Connections (EVC)
- Layer 2 over Multipoint GRE (L2omGRE)
- Campus Fabric
- IPv4 Multicast Layer 3 Features
- IPv4 Multicast IGMP Snooping
- IPv4 PIM Snooping
- IPv4 Multicast VLAN Registration (MVR)
- IPv4 IGMP Filtering
- IPv4 Router Guard
- IPv4 Multicast VPN Support
- IPv6 Multicast Layer 3 Features
- IPv6 MLD Snooping
- NetFlow Hardware Support
- System Event Archive (SEA)
- Backplane Platform Monitoring
- Local SPAN, RSPAN, and ERSPAN
- SNMP IfIndex Persistence
- Top-N Reports
- Layer 2 Traceroute Utility
- Mini Protocol Analyzer
- PFC QoS Guidelines and Restrictions
- PFC QoS Overview
- PFC QoS Classification, Marking, and Policing
- PFC QoS Policy Based Queueing
- PFC QoS Global and Interface Options
- AutoQoS
- MPLS QoS
- PFC QoS Statistics Data Export
- Cisco IOS ACL Support
- Cisco TrustSec (CTS)
- AutoSecure
- MAC Address-Based Traffic Blocking
- Port ACLs (PACLs)
- VLAN ACLs (VACLs)
- Policy-Based Forwarding (PBF)
- Denial of Service (DoS) Protection
- Control Plane Policing (CoPP)
- Dynamic Host Configuration Protocol (DHCP) Snooping
- Configuring IGMP Proxy
- IP Source Guard
- Dynamic ARP Inspection (DAI)
- Traffic Storm Control
- Unknown Unicast and Multicast Flood Control
- IEEE 802.1X Port-Based Authentication
- Configuring Web-Based Authentication
- Port Security
- Lawful Intercept
- Online Diagnostic Tests
Release 15.5SY Supervisor Engine 6T Software Configuration Guide
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- August 14, 2014
Chapter: Dynamic ARP Inspection (DAI)
- Prerequisites for DAI
- Restrictions for DAI
- Information About DAI
- Default Settings for DAI
- How to Configure DAI
- Configuration Examples for DAI
Dynamic ARP Inspection (DAI)
- Prerequisites for DAI
- Restrictions for DAI
- Information About DAI
- Default Settings for DAI
- How to Configure DAI
- Configuration Examples for DAI

Note ●![]() For complete syntax and usage information for the commands used in this chapter, see these publications:
For complete syntax and usage information for the commands used in this chapter, see these publications:
http://www.cisco.com/en/US/products/ps11846/prod_command_reference_list.html
- Cisco IOS Release 15.4SY supports only Ethernet interfaces. Cisco IOS Release 15.4SY does not support any WAN features or commands.
- The PFC and any DFCs support DAI in hardware.
http://www.cisco.com/en/US/products/hw/switches/ps708/tsd_products_support_series_home.html
Participate in the Technical Documentation Ideas forum
Prerequisites for DAI
Restrictions for DAI
- Hardware-accelerated DAI is enabled by default.
- When DAI is hardware-accelerated, you can configure CoPP to rate limit ARP traffic that would be processed by the RP (for example, packets with a broadcast destination MAC address or the MAC address of the RP; see Chapter 39, “Control Plane Policing (CoPP)”).
- DAI logging, including both ACL logging and DHCP logging, is not compatible with DAI hardware acceleration. When DAI is hardware-accelerated, DAI logging is disabled.

Note![]() Regardless of the enable state of DAI hardware acceleration, DAI configured to use an ARP ACL with the acl-match matchlog keywords is processed in software and supports logging.
Regardless of the enable state of DAI hardware acceleration, DAI configured to use an ARP ACL with the acl-match matchlog keywords is processed in software and supports logging.
- Because DAI is an ingress security feature, it does not perform any egress checking.
- DAI is not effective for hosts connected to switches that do not support DAI or that do not have this feature enabled. Because man-in-the-middle attacks are limited to a single Layer 2 broadcast domain, separate the domain with DAI checks from the one with no checking. This action secures the ARP caches of hosts in the domain enabled for DAI.
- DAI depends on the entries in the DHCP snooping binding database to verify IP-to-MAC address bindings in incoming ARP requests and ARP responses. Make sure to enable DHCP snooping to permit ARP packets that have dynamically assigned IP addresses. For configuration information, see Chapter40, “Dynamic Host Configuration Protocol (DHCP) Snooping”
- When DHCP snooping is disabled or in non-DHCP environments, use ARP ACLs to permit or to deny packets.
- DAI is supported on access ports, trunk ports, EtherChannel ports, and private VLAN ports.
- A physical port can join an EtherChannel port channel only when the trust state of the physical port and the channel port match. When you change the trust state on the port channel, the switch configures a new trust state on all the physical ports that comprise the channel.
- The operating rate for the port channel is cumulative across all the physical ports within the channel. For example, if you configure the port channel with an ARP rate limit of 400 pps, all the interfaces combined on the channel receive an aggregate 400 pps. The rate of incoming ARP packets on EtherChannel ports is equal to the sum of the incoming rate of packets from all the channel members. Configure the rate limit for EtherChannel ports only after examining the rate of incoming ARP packets on the channel-port members.
The rate of incoming packets on a physical port is checked against the port-channel configuration rather than the physical-ports configuration. The rate-limit configuration on a port channel is independent of the configuration on its physical ports.
If the EtherChannel receives more ARP packets than the configured rate, the channel (including all physical ports) is placed in the error-disabled state.
- Make sure to limit the rate of ARP packets on incoming trunk ports. Configure trunk ports with higher rates to reflect their aggregation and to handle packets across multiple DAI-enabled VLANs. You also can use the ip arp inspection limit none interface configuration command to make the rate unlimited. A high rate-limit on one VLAN can cause a denial-of-service attack to other VLANs when the software places the port in the error-disabled state.
Information About DAI
- Information about ARP
- ARP Spoofing Attacks
- DAI and ARP Spoofing Attacks
- Interface Trust States and Network Security
- Rate Limiting of ARP Packets
- Relative Priority of ARP ACLs and DHCP Snooping Entries
- Logging of Dropped Packets
Information about ARP
ARP provides IP communication within a Layer 2 broadcast domain by mapping an IP address to a MAC address. For example, Host B wants to send information to Host A but does not have the MAC address of Host A in its ARP cache. Host B generates a broadcast message for all hosts within the broadcast domain to obtain the MAC address associated with the IP address of Host A. All hosts within the broadcast domain receive the ARP request, and Host A responds with its MAC address.
ARP Spoofing Attacks
ARP spoofing attacks and ARP cache poisoning can occur because ARP allows a gratuitous reply from a host even if an ARP request was not received. After the attack, all traffic from the device under attack flows through the attacker’s computer and then to the router, switch, or host.
An ARP spoofing attack can target hosts, switches, and routers connected to your Layer 2 network by poisoning the ARP caches of systems connected to the subnet and by intercepting traffic intended for other hosts on the subnet. Figure 42-1 shows an example of ARP cache poisoning.
Figure 42-1 ARP Cache Poisoning
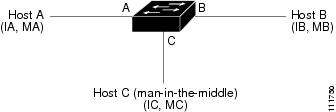
Hosts A, B, and C are connected to the switch on interfaces A, B and C, all of which are on the same subnet. Their IP and MAC addresses are shown in parentheses; for example, Host A uses IP address IA and MAC address MA. When Host A needs to communicate to Host B at the IP layer, it broadcasts an ARP request for the MAC address associated with IP address IB. When the switch and Host B receive the ARP request, they populate their ARP caches with an ARP binding for a host with the IP address IA and a MAC address MA; for example, IP address IA is bound to MAC address MA. When Host B responds, the switch and Host A populate their ARP caches with a binding for a host with the IP address IB and the MAC address MB.
Host C can poison the ARP caches of the switch for Host A, and Host B by broadcasting forged ARP responses with bindings for a host with an IP address of IA (or IB) and a MAC address of MC. Hosts with poisoned ARP caches use the MAC address MC as the destination MAC address for traffic intended for IA or IB. This means that Host C intercepts that traffic. Because Host C knows the true MAC addresses associated with IA and IB, it can forward the intercepted traffic to those hosts by using the correct MAC address as the destination. Host C has inserted itself into the traffic stream from Host A to Host B, which is the topology of the classic man-in-the middle attack.
DAI and ARP Spoofing Attacks
The PFC and any DFCs provide hardware support for DAI. DAI is a security feature that validates ARP packets in a network. DAI intercepts, logs, and discards ARP packets with invalid IP-to-MAC address bindings. This capability protects the network from some man-in-the-middle attacks.
DAI ensures that only valid ARP requests and responses are relayed. The switch performs these activities:
- Intercepts all ARP requests and responses on untrusted ports
- Verifies that each of these intercepted packets has a valid IP-to-MAC address binding before updating the local ARP cache or before forwarding the packet to the appropriate destination
- Drops invalid ARP packets
DAI determines the validity of an ARP packet based on valid IP-to-MAC address bindings stored in a trusted database, the DHCP snooping binding database. This database is built by DHCP snooping if DHCP snooping is enabled on the VLANs and on the switch. If the ARP packet is received on a trusted interface, the switch forwards the packet without any checks. On untrusted interfaces, the switch forwards the packet only if it is valid.
DAI can validate ARP packets against user-configured ARP access control lists (ACLs) for hosts with statically configured IP addresses (see “Applying ARP ACLs for DAI Filtering” section). The switch logs dropped packets (see the “Logging of Dropped Packets” section).
You can configure DAI to drop ARP packets when the IP addresses in the packets are invalid or when the MAC addresses in the body of the ARP packets do not match the addresses specified in the Ethernet header (see the “Enabling Additional Validation” section).
Interface Trust States and Network Security
DAI associates a trust state with each interface on the switch. Packets arriving on trusted interfaces bypass all DAI validation checks, and those arriving on untrusted interfaces undergo the DAI validation process.
In a typical network configuration, you configure all switch ports connected to host ports as untrusted and configure all switch ports connected to switches as trusted. With this configuration, all ARP packets entering the network from a given switch bypass the security check. No other validation is needed at any other place in the VLAN or in the network. You configure the trust setting by using the ip arp inspection trust interface configuration command.

In Figure 42-2, assume that both Switch A and Switch B are running DAI on the VLAN that includes Host 1 and Host 2. If Host 1 and Host 2 acquire their IP addresses from the DHCP server connected to Switch A, only Switch A binds the IP-to-MAC address of Host 1. Therefore, if the interface between Switch A and Switch B is untrusted, the ARP packets from Host 1 are dropped by Switch B. Connectivity between Host 1 and Host 2 is lost.
Figure 42-2 ARP Packet Validation on a VLAN Enabled for DAI
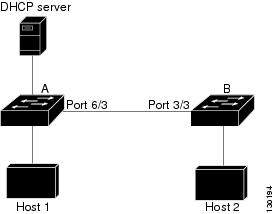
Configuring interfaces to be trusted when they are actually untrusted leaves a security hole in the network. If Switch A is not running DAI, Host 1 can easily poison the ARP cache of Switch B (and Host 2, if the link between the switches is configured as trusted). This condition can occur even though Switch B is running DAI.
DAI ensures that hosts (on untrusted interfaces) connected to a switch running DAI do not poison the ARP caches of other hosts in the network. However, DAI does not prevent hosts in other portions of the network from poisoning the caches of the hosts that are connected to a switch running DAI.
In cases in which some switches in a VLAN run DAI and other switches do not, configure the interfaces connecting such switches as untrusted. However, to validate the bindings of packets from switches where DAI is not configured, configure ARP ACLs on the switch running DAI. When you cannot determine such bindings, isolate switches running DAI at Layer 3 from switches not running DAI. For configuration information, see the “One Switch Supports DAI” section.

Note![]() Depending on the setup of the DHCP server and the network, it might not be possible to validate a given ARP packet on all switches in the VLAN.
Depending on the setup of the DHCP server and the network, it might not be possible to validate a given ARP packet on all switches in the VLAN.
Rate Limiting of ARP Packets
The switch performs DAI validation checks, which rate limits incoming ARP packets to prevent a denial-of-service attack. By default, the rate for untrusted interfaces is 15 packets per second (pps). Trusted interfaces are not rate limited. You can change this setting by using the ip arp inspection limit interface configuration command.
When the rate of incoming ARP packets exceeds the configured limit, the switch places the port in the error-disabled state. The port remains in that state until you intervene. You can use the errdisable recovery global configuration command to enable error disable recovery so that ports automatically emerge from this state after a specified timeout period.
For configuration information, see the “Configuring ARP Packet Rate Limiting” section.
Relative Priority of ARP ACLs and DHCP Snooping Entries
DAI uses the DHCP snooping binding database for the list of valid IP-to-MAC address bindings.
ARP ACLs take precedence over entries in the DHCP snooping binding database. The switch uses ACLs only if you configure them by using the ip arp inspection filter global configuration command. The switch first compares ARP packets to user-configured ARP ACLs. If the ARP ACL denies the ARP packet, the switch also denies the packet even if a valid binding exists in the database populated by DHCP snooping.
Logging of Dropped Packets
When the switch drops a packet, it places an entry in the log buffer and then generates system messages on a rate-controlled basis. After the message is generated, the switch clears the entry from the log buffer. Each log entry contains flow information, such as the receiving VLAN, the port number, the source and destination IP addresses, and the source and destination MAC addresses.
You use the ip arp inspection log-buffer global configuration command to configure the number of entries in the buffer and the number of entries needed in the specified interval to generate system messages. You specify the type of packets that are logged by using the ip arp inspection vlan logging global configuration command. For configuration information, see the “Configuring DAI Logging” section.
Default Settings for DAI
How to Configure DAI
- Enabling DAI on VLANs
- Configuring DAI Hardware Acceleration
- Configuring the DAI Interface Trust State
- Applying ARP ACLs for DAI Filtering
- Configuring ARP Packet Rate Limiting
- Enabling DAI Error-Disabled Recovery
- Enabling Additional Validation
- Configuring DAI Logging
- Displaying DAI Information
Enabling DAI on VLANs
To enable DAI on VLANs, perform this task:
|
|
|
|
|---|---|---|
Router(config)# ip arp inspection vlan { vlan_ID | vlan_range } |
||
Router(config-if)# do show ip arp inspection vlan { vlan_ID | vlan_range } | begin Vlan |
You can enable DAI on a single VLAN or a range of VLANs:
- To enable a single VLAN, enter a single VLAN number.
- To enable a range of VLANs, enter a dash-separated pair of VLAN numbers.
- You can enter a comma-separated list of VLAN numbers and dash-separated pairs of VLAN numbers.
This example shows how to enable DAI on VLANs 10 through 12:
This example shows another way to enable DAI on VLANs 10 through 12:
This example shows how to enable DAI on VLANs 10 through 12 and VLAN 15:
This example shows how to verify the configuration:
Configuring DAI Hardware Acceleration
When DAI is enabled, by default DAI hardware acceleration is also enabled. To configure the DAI hardware acceleration state, perform this task:
|
|
|
|
|---|---|---|
Router(config)# do show ip arp inspection | include Acceleration |
This example shows how to reenable DAI hardware acceleration:
Configuring the DAI Interface Trust State
The switch forwards ARP packets that it receives on a trusted interface, but does not check them.
On untrusted interfaces, the switch intercepts all ARP requests and responses. It verifies that the intercepted packets have valid IP-to-MAC address bindings before updating the local cache and before forwarding the packet to the appropriate destination. The switch drops invalid packets and logs them in the log buffer according to the logging configuration specified with the ip arp inspection vlan logging global configuration command. For more information, see the “Configuring DAI Logging” section.
To configure the DAI interface trust state, perform this task:
|
|
|
|
|---|---|---|
Router(config)# interface { type slot/port | port-channel number } |
Specifies the interface connected to another switch, and enter interface configuration mode. |
|
This example shows how to configure Gigabit Ethernet port 5/12 as trusted:
Applying ARP ACLs for DAI Filtering
To apply an ARP ACL, perform this task:
|
|
|
|
|---|---|---|
Router# ip arp inspection filter arp_acl_name vlan { vlan_ID | vlan_range } [static] |
||
Router(config)# do show ip arp inspection vlan { vlan_ID | vlan_range } |
- See the command reference for information about the arp access-list command.
- For vlan_range, you can specify a single VLAN or a range of VLANs:
–![]() To specify a single VLAN, enter a single VLAN number.
To specify a single VLAN, enter a single VLAN number.
–![]() To specify a range of VLANs, enter a dash-separated pair of VLAN numbers.
To specify a range of VLANs, enter a dash-separated pair of VLAN numbers.
–![]() You can enter a comma-separated list of VLAN numbers and dash-separated pairs of VLAN numbers.
You can enter a comma-separated list of VLAN numbers and dash-separated pairs of VLAN numbers.
- (Optional) Specify static to treat implicit denies in the ARP ACL as explicit denies and to drop packets that do not match any previous clauses in the ACL. DHCP bindings are not used.
If you do not specify this keyword, it means that there is no explicit deny in the ACL that denies the packet, and DHCP bindings determine whether a packet is permitted or denied if the packet does not match any clauses in the ACL.
- ARP packets containing only IP-to-MAC address bindings are compared against the ACL. Packets are permitted only if the access list permits them.
This example shows how to apply an ARP ACL named example_arp_acl to VLANs 10 through 12 and VLAN 15:
Configuring ARP Packet Rate Limiting

Note![]() When DAI is hardware-accelerated, you can configure CoPP to rate limit ARP traffic that would be processed by the RP (for example, packets with a broadcast destination MAC address or the MAC address of the RP; see Chapter 39, “Control Plane Policing (CoPP)”).
When DAI is hardware-accelerated, you can configure CoPP to rate limit ARP traffic that would be processed by the RP (for example, packets with a broadcast destination MAC address or the MAC address of the RP; see Chapter 39, “Control Plane Policing (CoPP)”).
When nonaccelerated DAI is enabled, the switch performs ARP packet validation checks, which makes the switch vulnerable to an ARP-packet denial-of-service attack. ARP packet rate limiting can prevent an ARP-packet denial-of-service attack.
To configure ARP packet rate limiting on a port, perform this task:
|
|
|
|
|---|---|---|
Router(config)# interface { type slot/port | port-channel number } |
||
Router(config-if)# ip arp inspection limit { rate pps [ burst interval seconds ] | none } |
||
- The default rate is 15 pps on untrusted interfaces and unlimited on trusted interfaces.
- For rate pps, specify an upper limit for the number of incoming packets processed per second. The range is 0 to 2048 pps.
- The rate none keywords specify that there is no upper limit for the rate of incoming ARP packets that can be processed.
- (Optional) For burst interval seconds (default is 1), specify the consecutive interval, in seconds, over which the interface is monitored for a high rate of ARP packets.The range is 1 to 15.
- When the rate of incoming ARP packets exceeds the configured limit, the switch places the port in the error-disabled state. The port remains in the error-disabled state until you enable error-disabled recovery, which allows the port to emerge from the error-disabled state after a specified timeout period.
- Unless you configure a rate-limiting value on an interface, changing the trust state of the interface also changes its rate-limiting value to the default value for the configured trust state. After you configure the rate-limiting value, the interface retains the rate-limiting value even when you change its trust state. If you enter the no ip arp inspection limit interface configuration command, the interface reverts to its default rate-limiting value.
- For configuration guidelines about limiting the rate of incoming ARP packets on trunk ports and EtherChannel ports, see the “Restrictions for DAI” section.
This example shows how to configure ARP packet rate limiting on Gigabit Ethernet port 5/14:
Enabling DAI Error-Disabled Recovery
To enable DAI error-disabled recovery, perform this task:
|
|
|
|
|---|---|---|
Router(config)# do show errdisable recovery | include Reason|---|arp- |
This example shows how to enable DAI error disabled recovery:
Enabling Additional Validation
DAI intercepts, logs, and discards ARP packets with invalid IP-to-MAC address bindings. You can enable additional validation on the destination MAC address, the sender and target IP addresses, and the source MAC address.
To enable additional validation, perform this task:
|
|
|
|
|---|---|---|
Router(config)# ip arp inspection validate {[ dst-mac ] [ ip ] [ src-mac ]} |
||
The additional validations do the following:
- dst-mac —Checks the destination MAC address in the Ethernet header against the target MAC address in ARP body. This check is performed for ARP responses. When enabled, packets with different MAC addresses are classified as invalid and are dropped.
- ip —Checks the ARP body for invalid and unexpected IP addresses. Addresses include 0.0.0.0, 255.255.255.255, and all IP multicast addresses. Sender IP addresses are checked in all ARP requests and responses, and target IP addresses are checked only in ARP responses.
- src-mac —Checks the source MAC address in the Ethernet header against the sender MAC address in the ARP body. This check is performed on both ARP requests and responses. When enabled, packets with different MAC addresses are classified as invalid and are dropped.
When enabling additional validation, note the following information:
- You must specify at least one of the keywords.
- Each ip arp inspection validate command overrides the configuration from any previous commands. If an ip arp inspection validate command enables src-mac and dst-mac validations, and a second ip arp inspection validate command enables IP validation only, the src-mac and dst-mac validations are disabled as a result of the second command.
This example shows how to enable src-mac additional validation:
This example shows how to enable dst-mac additional validation:
This example shows how to enable ip additional validation:
This example shows how to enable src-mac and dst-mac additional validation:
This example shows how to enable src-mac, dst-mac, and ip additional validation:
Configuring DAI Logging
DAI Logging Overview
When DAI drops a packet, it places an entry in the log buffer and then generates system messages on a rate-controlled basis. After the message is generated, DAI clears the entry from the log buffer. Each log entry contains flow information, such as the receiving VLAN, the port number, the source and destination IP addresses, and the source and destination MAC addresses.
A log-buffer entry can represent more than one packet. For example, if an interface receives many packets on the same VLAN with the same ARP parameters, DAI combines the packets as one entry in the log buffer and generates a single system message for the entry.
If the log buffer overflows, it means that a log event does not fit into the log buffer, and the display for the show ip arp inspection log privileged EXEC command is affected. Two dashes (“--”) appear instead of data except for the packet count and the time. No other statistics are provided for the entry. If you see this entry in the display, increase the number of entries in the log buffer or increase the logging rate.
DAI Logging Restrictions
DAI logging, including both ACL logging and DHCP logging, is not compatible with DAI hardware acceleration. When DAI is hardware-accelerated, DAI logging is disabled. Regardless of the enable state of DAI hardware acceleration, DAI configured to use an ARP ACL with the acl-match matchlog keywords is processed in software and supports logging.
Configuring the DAI Logging Buffer Size
To configure the DAI logging buffer size, perform this task:
|
|
|
|
|---|---|---|
Configures the DAI logging buffer size (range is 0 to 1024). |
||
Router(config)# do show ip arp inspection log | include Size |
This example shows how to configure the DAI logging buffer for 64 messages:
Configuring the DAI Logging System Messages
To configure the DAI logging system messages, perform this task:
|
|
|
|
|---|---|---|
Router(config)# ip arp inspection log-buffer logs number_of_messages interval length_in_seconds |
||
- For logs number_of_messages (default is 5), the range is 0 to 1024. A 0 value means that the entry is placed in the log buffer, but a system message is not generated.
- For interval length_in_seconds (default is 1), the range is 0 to 86400 seconds (1 day). A 0 value means that a system message is immediately generated (and the log buffer is always empty). An interval setting of 0 overrides a log setting of 0.
- System messages are sent at the rate of number_of_messages per length_in_seconds.
This example shows how to configure DAI logging to send 12 messages every 2 seconds:
This example shows how to configure DAI logging to send 20 messages every 60 seconds.
Configuring DAI Log Filtering
To configure DAI log filtering, perform this task:
- By default, all denied packets are logged.
- For vlan_range, you can specify a single VLAN or a range of VLANs:
–![]() To specify a single VLAN, enter a single VLAN number.
To specify a single VLAN, enter a single VLAN number.
–![]() To specify a range of VLANs, enter a dash-separated pair of VLAN numbers.
To specify a range of VLANs, enter a dash-separated pair of VLAN numbers.
–![]() You can enter a comma-separated list of VLAN numbers and dash-separated pairs of VLAN numbers.
You can enter a comma-separated list of VLAN numbers and dash-separated pairs of VLAN numbers.
- acl-match matchlog—Logs packets based on the DAI ACL configuration. If you specify the matchlog keyword in this command and the log keyword in the permit or deny ARP access-list configuration command, ARP packets permitted or denied by the ACL are logged.
- acl-match none —Does not log packets that match ACLs.
- dhcp-bindings all—Logs all packets that match DHCP bindings.
- dhcp-bindings none—Does not log packets that match DHCP bindings.
- dhcp-bindings permit—Logs DHCP-binding permitted packets.
This example shows how to configure the DAI log filtering for VLAN 100 not to log packets that match ACLs:
Displaying DAI Information
Configuration Examples for DAI
Two Switches Support DAI
Overview
This procedure shows how to configure DAI when two switches support this feature. Host 1 is connected to Switch A, and Host 2 is connected to Switch B as shown in Figure 42-2. Both switches are running DAI on VLAN 1 where the hosts are located. A DHCP server is connected to Switch A. Both hosts acquire their IP addresses from the same DHCP server. Switch A has the bindings for Host 1 and Host 2, and Switch B has the binding for Host 2. Switch A Gigabit Ethernet port 6/3 is connected to the Switch B Gigabit Ethernet port 3/3.

Note ●![]() DAI depends on the entries in the DHCP snooping binding database to verify IP-to-MAC address bindings in incoming ARP requests and ARP responses. Make sure to enable DHCP snooping to permit ARP packets that have dynamically assigned IP addresses. For configuration information, see Chapter40, “Dynamic Host Configuration Protocol (DHCP) Snooping”
DAI depends on the entries in the DHCP snooping binding database to verify IP-to-MAC address bindings in incoming ARP requests and ARP responses. Make sure to enable DHCP snooping to permit ARP packets that have dynamically assigned IP addresses. For configuration information, see Chapter40, “Dynamic Host Configuration Protocol (DHCP) Snooping”
- This configuration does not work if the DHCP server is moved from Switch A to a different location.
- To ensure that this configuration does not compromise security, configure Gigabit Ethernet port 6/3 on Switch A and Gigabit Ethernet port 3/3 on Switch B as trusted.
Configuring Switch A
To enable DAI and configure Gigabit Ethernet port 6/3 on Switch A as trusted, follow these steps:
Step 1![]() Verify the connection between switches Switch A and Switch B:
Verify the connection between switches Switch A and Switch B:
Step 2![]() Enable DAI on VLAN 1 and verify the configuration:
Enable DAI on VLAN 1 and verify the configuration:
Step 3![]() Configure Gigabit Ethernet port 6/3 as trusted:
Configure Gigabit Ethernet port 6/3 as trusted:
Step 5![]() Check the statistics before and after DAI processes any packets:
Check the statistics before and after DAI processes any packets:
If Host 1 then sends out two ARP requests with an IP address of 10.1.1.2 and a MAC address of 0002.0002.0002, both requests are permitted, as reflected in the following statistics:
If Host 1 then tries to send an ARP request with an IP address of 10.1.1.3, the packet is dropped and an error message is logged:
The statistics will display as follows:
Configuring Switch B
To enable DAI and configure Gigabit Ethernet port 3/3 on Switch B as trusted, follow these steps:
Step 1![]() Verify the connectivity:
Verify the connectivity:
Step 2![]() Enable DAI on VLAN 1, and verify the configuration:
Enable DAI on VLAN 1, and verify the configuration:
Step 3![]() Configure Gigabit Ethernet port 3/3 as trusted:
Configure Gigabit Ethernet port 3/3 as trusted:
Step 4![]() Verify the list of DHCP snooping bindings:
Verify the list of DHCP snooping bindings:
Step 5![]() Check the statistics before and after DAI processes any packets:
Check the statistics before and after DAI processes any packets:
If Host 2 then sends out an ARP request with the IP address 10.1.1.1 and the MAC address 0001.0001.0001, the packet is forwarded and the statistics are updated appropriately:
If Host 2 attempts to send an ARP request with the IP address 10.1.1.2, DAI drops the request and logs a system message:
The statistics display as follows:
One Switch Supports DAI
This procedure shows how to configure DAI when Switch B shown in Figure 42-2 does not support DAI or DHCP snooping.
If switch Switch B does not support DAI or DHCP snooping, configuring Gigabit Ethernet port 6/3 on Switch A as trusted creates a security hole because both Switch A and Host 1 could be attacked by either Switch B or Host 2.
To prevent this possibility, you must configure Gigabit Ethernet port 6/3 on Switch A as untrusted. To permit ARP packets from Host 2, you must set up an ARP ACL and apply it to VLAN 1. If the IP address of Host 2 is not static, which would make it impossible to apply the ACL configuration on Switch A, you must separate Switch A from Switch B at Layer 3 and use a router to route packets between them.
To set up an ARP ACL on switch Switch A, follow these steps:
Step 1![]() Configure the access list to permit the IP address 10.1.1.1 and the MAC address 0001.0001.0001, and verify the configuration:
Configure the access list to permit the IP address 10.1.1.1 and the MAC address 0001.0001.0001, and verify the configuration:
Step 2![]() Apply the ACL to VLAN 1, and verify the configuration:
Apply the ACL to VLAN 1, and verify the configuration:
Step 3![]() Configure Gigabit Ethernet port 6/3 as untrusted, and verify the configuration:
Configure Gigabit Ethernet port 6/3 as untrusted, and verify the configuration:
When Host 2 sends 5 ARP requests through Gigabit Ethernet port 6/3 on Switch A and a “get” is permitted by Switch A, the statistics are updated appropriately:
http://www.cisco.com/en/US/products/hw/switches/ps708/tsd_products_support_series_home.html
Participate in the Technical Documentation Ideas forum
 Feedback
Feedback