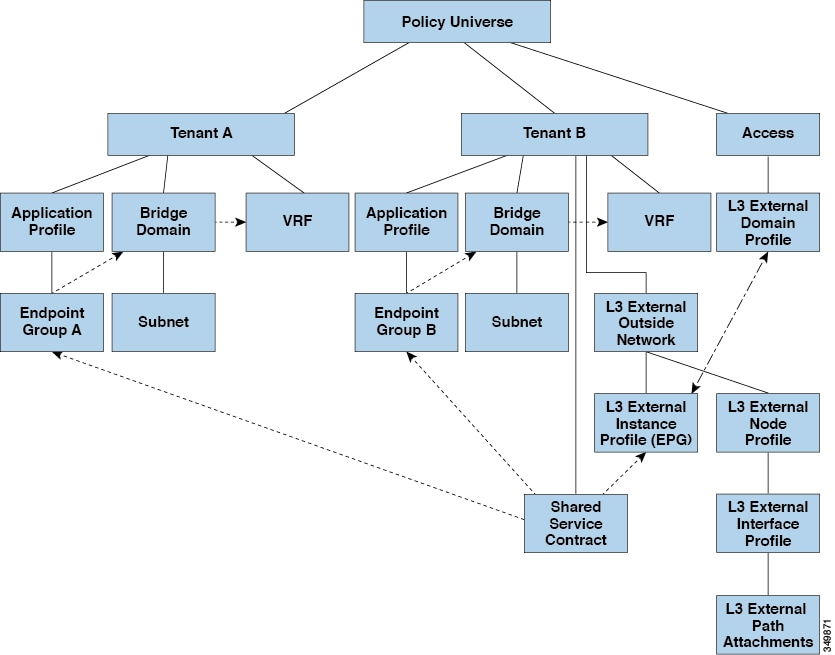
Shared Layer 3 Out
A shared Layer 3 Outside (L3Out or l3extOut) configuration provides routed connectivity to an external network as a shared service across VRF instances or tenants. An
external EPG instance profile (external EPG or l3extInstP) in an L3Out provides the configurations to control which routes can be shared from both the routing perspective and contract
perspective. A contract under an external EPG determines to which VRF instances or tenants those routes should be leaked.
An L3Out can be provisioned as a shared service in any tenant (user, common, infra, or mgmt). An EPG in any tenant can use a shared services contract to connect with an external EPG regardless of where in the fabric
that external EPG is provisioned. This simplifies the provisioning of routed connectivity to external networks; multiple tenants
can share a single external EPG for routed connectivity to external networks. Sharing an external EPG is more efficient because
it consumes only one session on the switch regardless of how many EPGs use the single shared external EPG.
Take note of the following guidelines and limitations for shared L3Out network configurations:
-
No tenant limitations: Tenants A and B can be any kind of tenant (user,
common,infra,mgmt). The shared external EPG does not have to be in thecommontenant. -
Flexible placement of EPGs: EPG A and EPG B in the illustration above are in different tenants. EPG A and EPG B could use the same bridge domain and VRF instance, but they are not required to do so. EPG A and EPG B are in different bridge domains and different VRF instances but still share the same external EPG.
-
A subnet can be private, public, or shared. A subnet that is to be advertised into a consumer or provider EPG of an L3Out must be set to shared. A subnet that is to be exported to an L3Out must be set to public.
-
The shared service contract is exported from the tenant that contains the external EPG that provides shared L3Out network service. The shared service contract is imported into the tenants that contain the EPGs that consume the shared service.
-
Do not use taboo contracts with a shared L3Out; this configuration is not supported.
-
The external EPG as a shared service provider is supported, but only with non-external EPG consumers (where the L3Out EPG is the same as the external EPG).
-
Traffic Disruption (Flap): When an external EPG is configured with an external subnet of 0.0.0.0/0 with the scope property of the external EPG subnet set to shared route control (shared-rctrl), or shared security (shared-security), the VRF instance is redeployed with a global
pcTag. This will disrupt all the external traffic in that VRF instance (because the VRF instance is redeployed with a globalpcTag). -
Prefixes for a shared L3Out must to be unique. Multiple shared L3Out configurations with the same prefix in the same VRF instance will not work. Be sure that the external subnets (external prefixes) that are advertised into a VRF instance are unique (the same external subnet cannot belong to multiple external EPGs). An L3Out configuration (for example, named
L3Out1) with prefix1 and a second L3Out configuration (for example, namedL3Out2) also with prefix1 belonging to the same VRF instance will not work (because only 1 pcTag is deployed). -
Different behaviors of L3Out are possible when configured on the same leaf switch under the same VRF instance. The two possible scenarios are as follows:
-
Scenario 1 has an L3Out with an SVI interface and two subnets (10.10.10.0/24 and 0.0.0.0/0) defined. If ingress traffic on the L3Out network has the matching prefix 10.10.10.0/24, then the ingress traffic uses the external EPG pcTag. If ingress traffic on the L3Out network has the matching default prefix 0.0.0.0/0, then the ingress traffic uses the external bridge pcTag.
-
Scenario 2 has an L3Out using a routed or routed-sub-interface with two subnets (10.10.10.0/24 and 0.0.0.0/0) defined. If ingress traffic on the L3Out network has the matching prefix 10.10.10.0/24, then the ingress traffic uses the external EPG pcTag. If ingress traffic on the L3Out network has the matching default prefix 0.0.0.0/0, then the ingress traffic uses the VRF instance pcTag.
-
As a result of these described behaviors, the following use cases are possible if the same VRF instance and same leaf switch are configured with
L3Out-AandL3Out-Busing an SVI interface:Case 1 is for
L3Out-A: This external EPG has two subnets defined: 10.10.10.0/24 and 0.0.0.0/1. If ingress traffic onL3Out-Ahas the matching prefix 10.10.10.0/24, it uses the external EPG pcTag andcontract-A, which is associated withL3Out-A. When egress traffic onL3Out-Ahas no specific match found, but there is a maximum prefix match with 0.0.0.0/1, it uses the external bridge domain pcTag andcontract-A.Case 2 is for
L3Out-B: This external EPG has one subnet defined: 0.0.0.0/0. When ingress traffic onL3Out-Bhas the matching prefix10.10.10.0/24 (which is defined underL3Out-A), it uses the external EPG pcTag ofL3Out-Aand thecontract-A, which is tied withL3Out-A. It does not usecontract-B, which is tied withL3Out-B.
-
-
Traffic not permitted: Traffic is not permitted when an invalid configuration sets the scope of the external subnet to shared route control (shared-rtctrl) as a subset of a subnet that is set to shared security (shared-security). For example, the following configuration is invalid:
-
shared rtctrl: 10.1.1.0/24, 10.1.2.0/24
-
shared security: 10.1.0.0/16
In this case, ingress traffic on a non-border leaf with a destination IP of 10.1.1.1 is dropped, since prefixes 10.1.1.0/24 and 10.1.2.0/24 are installed with a drop rule. Traffic is not permitted. Such traffic can be enabled by revising the configuration to use the
shared-rtctrlprefixes as shared-security prefixes as well. -
-
Inadvertent traffic flow: Prevent inadvertent traffic flow by avoiding the following configuration scenarios:
-
Case 1 configuration details:
-
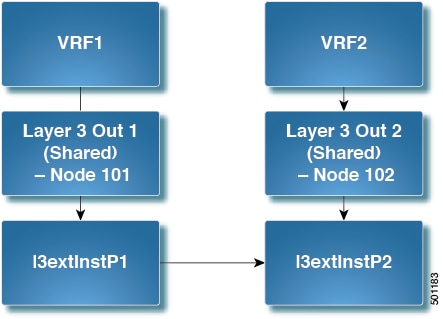
A L3Out network configuration (for example, named
L3Out-1) with VRF1 is calledprovider1. -
A second L3Out network configuration (for example, named
L3Out-2) with VRF2 is calledprovider2. -
L3Out-1VRF1 advertises a default route to the Internet, 0.0.0.0/0, which enables both shared-rtctrl and shared-security. -
L3Out-2VRF2 advertises specific subnets to DNS and NTP, 192.0.0.0/8, which enables shared-rtctrl. -
L3Out-2VRF2 has specific subnet 192.1.0.0/16, which enables shared-security. -
Variation A: EPG traffic goes to multiple VRF instances.
-
Communications between EPG1 and
L3Out-1is regulated by an allow_all contract. -
Communications between EPG1 and
L3Out-2is regulated by an allow_all contract.Result: Traffic from EPG1 to
L3Out-2also goes to 192.2.x.x.
-
-
Variation B: An EPG conforms to the allow_all contract of a second shared L3Out network.
-
Communications between EPG1 and
L3Out-1is regulated by an allow_all contract. -
Communications between EPG1 and
L3Out-2is regulated by an allow_icmp contract.Result: Traffic from EPG1 to
L3Out-2to 192.2.x.x conforms to the allow_all contract.
-
-
-
Case 2 configuration details:
-
An external EPG has one shared prefix and other non-shared prefixes.
-
Traffic coming in with
src = non-sharedis allowed to go to the EPG.-
Variation A: Unintended traffic goes through an EPG.
External EPG traffic goes through an L3Out that has these prefixes:
-
192.0.0.0/8 = import-security, shared-rtctrl -
192.1.0.0/16 = shared-security -
The EPG has
1.1.0.0/16 = shared.
Result: Traffic going from 192.2.x.x also goes through to the EPG.
-
-
Variation B: Unintended traffic goes through an EPG. Traffic coming in a shared L3Out can go through the EPG.
-
The shared L3Out VRF instance has an EPG with
pcTag = prov vrfand a contract set to allow_all. -
The EPG
<subnet> = shared.
Result: The traffic coming in on the L3Out can go through the EPG.
-
-
-
-
 Feedback
Feedback