- Index
- Preface
- Overview
- Using the Command-Line Interface
- Assigning the Switch IP Address and Default Gateway
- Configuring Cisco IOS Configuration Engine
- Administering the Switch
- Configuring SDM Templates
- Configuring Switch-Based Authentication
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring Web-Based Authentication
- Configuring Interface Characteristics
- Configuring Smartports Macros
- Configuring VLANs
- Configuring VTP
- Configuring Voice VLAN
- Configuring Private VLANs
- Configuring IEEE 802.1Q and Layer 2 Protocol Tunneling
- Configuring STP
- Configuring MSTP
- Configuring Optional Spanning-Tree Features
- Configuring Flex Links and the MAC Address-Table Move Update Feature
- Configuring DHCP and IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring IGMP Snooping and MVR
- Configuring Port-Based Traffic Control
- Configuring CDP
- Configuring LLDP, LLDP-MED, and Wired Location Service
- Configuring UDLD
- Configuring SPAN and RSPAN
- Configuring RMON
- Configuring System Message Logging
- Configuring SNMP
- Configuring Network Security with ACLs
- Configuring QoS
- Configuring EtherChannels and Layer 2 Trunk Failover
- Configuring IP Unicast Routing
- Configuring IPv6 Host Functions
- Configuring IPv6 MLD Snooping
- Configuring IPv6 ACLs
- Configuring HSRP and Enhanced Object Tracking
- Configuring Cisco IOS IP SLAs Operations
- Troubleshooting
- Configuring Online Diagnostics
- Supported MIBs
- Working with the Cisco IOS File System, Configuration Files, and Software Images
- Unsupported Commands in Cisco IOS Release 12.2(52)SE
Cisco Catalyst Blade Switch 3020 for HP Software Configuration Guide, 12.2(52)SE
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- March 20, 2015
Chapter: Configuring IGMP Snooping and MVR
- Understanding IGMP Snooping
- Configuring IGMP Snooping
- Default IGMP Snooping Configuration
- Enabling or Disabling IGMP Snooping
- Setting the Snooping Method
- Configuring a Multicast Router Port
- Configuring a Blade Server Statically to Join a Group
- Enabling IGMP Immediate Leave
- Configuring the IGMP Leave Timer
- Configuring TCN-Related Commands
- Configuring the IGMP Snooping Querier
- Disabling IGMP Report Suppression
- Displaying IGMP Snooping Information
- Understanding Multicast VLAN Registration
- Configuring MVR
- Displaying MVR Information
- Configuring IGMP Filtering and Throttling
- Displaying IGMP Filtering and Throttling Configuration
Configuring IGMP Snooping and MVR
This chapter describes how to configure Internet Group Management Protocol (IGMP) snooping on the switch, including an application of local IGMP snooping, Multicast VLAN Registration (MVR). It also includes procedures for controlling multicast group membership by using IGMP filtering and procedures for configuring the IGMP throttling action.

Note ![]() For IP Version 6 (IPv6) traffic, Multicast Listener Discovery (MLD) snooping performs the same function as IGMP snooping for IPv4 traffic. For information about MLD snooping, see Chapter 37, "Configuring IPv6 MLD Snooping."
For IP Version 6 (IPv6) traffic, Multicast Listener Discovery (MLD) snooping performs the same function as IGMP snooping for IPv4 traffic. For information about MLD snooping, see Chapter 37, "Configuring IPv6 MLD Snooping."

Note ![]() For complete syntax and usage information for the commands used in this chapter, see the switch command reference for this release and the "IP Multicast Routing Commands" section in the Cisco IOS IP Command Reference, Volume 3 of 3:Multicast, Release 12.2 from the Cisco.com page under Documentation > Cisco IOS Software > 12.2 Mainline > Command References.
For complete syntax and usage information for the commands used in this chapter, see the switch command reference for this release and the "IP Multicast Routing Commands" section in the Cisco IOS IP Command Reference, Volume 3 of 3:Multicast, Release 12.2 from the Cisco.com page under Documentation > Cisco IOS Software > 12.2 Mainline > Command References.
This chapter consists of these sections:
•![]() Displaying IGMP Snooping Information
Displaying IGMP Snooping Information
•![]() Understanding Multicast VLAN Registration
Understanding Multicast VLAN Registration
•![]() Configuring IGMP Filtering and Throttling
Configuring IGMP Filtering and Throttling
•![]() Displaying IGMP Filtering and Throttling Configuration
Displaying IGMP Filtering and Throttling Configuration

Note ![]() You can either manage IP multicast group addresses through features such as IGMP snooping and MVR, or you can use static IP addresses.
You can either manage IP multicast group addresses through features such as IGMP snooping and MVR, or you can use static IP addresses.
Understanding IGMP Snooping
Layer 2 switches can use IGMP snooping to constrain the flooding of multicast traffic by dynamically configuring Layer 2 interfaces so that multicast traffic is forwarded to only those interfaces associated with IP multicast devices. As the name implies, IGMP snooping requires the LAN switch to snoop on the IGMP transmissions between the host and the router and to keep track of multicast groups and member ports. When the switch receives an IGMP report from a host for a particular multicast group, the switch adds the host port number to the forwarding table entry; when it receives an IGMP Leave Group message from a host, it removes the host port from the table entry. It also periodically deletes entries if it does not receive IGMP membership reports from the multicast clients.

Note ![]() For more information on IP multicast and IGMP, see RFC 1112 and RFC 2236.
For more information on IP multicast and IGMP, see RFC 1112 and RFC 2236.
The multicast router sends out periodic general queries to all VLANs. All hosts interested in this multicast traffic send join requests and are added to the forwarding table entry. The switch creates one entry per VLAN in the IGMP snooping IP multicast forwarding table for each group from which it receives an IGMP join request.
The switch supports IP multicast group-based bridging, rather than MAC-addressed based groups. With multicast MAC address-based groups, if an IP address being configured translates (aliases) to a previously configured MAC address or to any reserved multicast MAC addresses (in the range 224.0.0.xxx), the command fails. Because the switch uses IP multicast groups, there are no address aliasing issues.
The IP multicast groups learned through IGMP snooping are dynamic. However, you can statically configure multicast groups by using the ip igmp snooping vlan vlan-id static ip_address interface interface-id global configuration command. If you specify group membership for a multicast group address statically, your setting supersedes any automatic manipulation by IGMP snooping. Multicast group membership lists can consist of both user-defined and IGMP snooping-learned settings.
You can configure an IGMP snooping querier to support IGMP snooping in subnets without multicast interfaces because the multicast traffic does not need to be routed. For more information about the IGMP snooping querier, see the "Configuring the IGMP Snooping Querier" section.
If a port spanning-tree, a port group, or a VLAN ID change occurs, the IGMP snooping-learned multicast groups from this port on the VLAN are deleted.
These sections describe IGMP snooping characteristics:
•![]() IGMP Configurable-Leave Timer
IGMP Configurable-Leave Timer
IGMP Versions
The switch supports IGMP Version 1, IGMP Version 2, and IGMP Version 3. These versions are interoperable on the switch. For example, if IGMP snooping is enabled on an IGMPv2 switch and the switch receives an IGMPv3 report from a host, the switch can forward the IGMPv3 report to the multicast router.

Note ![]() The switch supports IGMPv3 snooping based only on the destination multicast MAC address. It does not support snooping based on the source MAC address or on proxy reports.
The switch supports IGMPv3 snooping based only on the destination multicast MAC address. It does not support snooping based on the source MAC address or on proxy reports.
An IGMPv3 switch supports Basic IGMPv3 Snooping Support (BISS), which includes support for the snooping features on IGMPv1 and IGMPv2 switches and for IGMPv3 membership report messages. BISS constrains the flooding of multicast traffic when your network includes IGMPv3 hosts. It constrains traffic to approximately the same set of ports as the IGMP snooping feature on IGMPv2 or IGMPv1 hosts.

Note ![]() IGMPv3 join and leave messages are not supported on switches running IGMP filtering or MVR.
IGMPv3 join and leave messages are not supported on switches running IGMP filtering or MVR.
An IGMPv3 switch can receive messages from and forward messages to a device running the Source Specific Multicast (SSM) feature. For more information about source-specific multicast with IGMPv3 and IGMP, see the following URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121newft/121t/121t5/dtssm5t.htm
Joining a Multicast Group
When a blade server connected to the switch wants to join an IP multicast group and it is an IGMP Version 2 client, it sends an unsolicited IGMP join message, specifying the IP multicast group to join. Alternatively, when the switch receives a general query from the router, it forwards the query to all ports in the VLAN. IGMP Version 1 or Version 2 blade servers wanting to join the multicast group respond by sending a join message to the switch. The switch CPU creates a multicast forwarding-table entry for the group if it is not already present. The CPU also adds the interface where the join message was received to the forwarding-table entry. The blade server associated with that interface receives multicast traffic for that multicast group. See Figure 23-1.
Figure 23-1 Initial IGMP Join Message
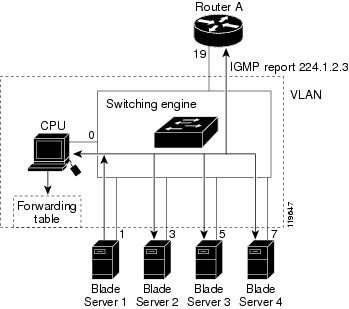
Router A sends a general query to the switch, which forwards the query to ports 2 through 5, which are all members of the same VLAN. Blade Server 1 wants to join multicast group 224.1.2.3 and multicasts an IGMP membership report (IGMP join message) to the group. The switch CPU uses the information in the IGMP report to set up a forwarding-table entry, as shown in Table 23-1, that includes the port numbers of Blade Server 1 and the router.
|
|
|
|
|---|---|---|
224.1.2.3 |
IGMP |
1, 2 |
The switch hardware can distinguish IGMP information packets from other packets for the multicast group. The information in the table tells the switching engine to send frames addressed to the 224.1.2.3 multicast IP address that are not IGMP packets to the router and to the host that has joined the group.
If another blade server (for example, Blade Server 4) sends an unsolicited IGMP join message for the same group (Figure 23-2), the CPU receives that message and adds the port number of Blade Server 4 to the forwarding table as shown in Table 23-2. Note that because the forwarding table directs IGMP messages only to the CPU, the message is not flooded to other ports on the switch. Any known multicast traffic is forwarded to the group and not to the CPU.
Figure 23-2 Second Host Joining a Multicast Group
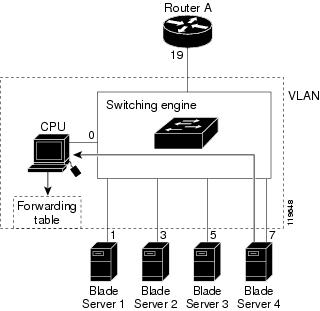
|
|
|
|
|---|---|---|
224.1.2.3 |
IGMP |
1, 2, 5 |
Leaving a Multicast Group
The router sends periodic multicast general queries, and the switch forwards these queries through all ports in the VLAN. Interested blade servers respond to the queries. If at least one blade server in the VLAN wishes to receive multicast traffic, the router continues forwarding the multicast traffic to the VLAN. The switch forwards multicast group traffic only to those blade servers listed in the forwarding table for that IP multicast group maintained by IGMP snooping.
When blade servers want to leave a multicast group, they can silently leave, or they can send a leave message. When the switch receives a leave message from a blade server, it sends a group-specific query to learn if any other devices connected to that interface are interested in traffic for the specific multicast group. The switch then updates the forwarding table for that MAC group so that only those blade servers interested in receiving multicast traffic for the group are listed in the forwarding table. If the router receives no reports from a VLAN, it removes the group for the VLAN from its IGMP cache.
Immediate Leave
Immediate Leave is only supported on IGMP Version 2 hosts.
The switch uses IGMP snooping Immediate Leave to remove from the forwarding table an interface that sends a leave message without the switch sending group-specific queries to the interface. The VLAN interface is pruned from the multicast tree for the multicast group specified in the original leave message. Immediate Leave ensures optimal bandwidth management for all blade servers on a switched network, even when multiple multicast groups are simultaneously in use.

Note ![]() You should only use the Immediate Leave feature on VLANs where a single blade server is connected to each port. If Immediate Leave is enabled in VLANs where more than one blade server is connected to a port, some blade servers might inadvertently be dropped.
You should only use the Immediate Leave feature on VLANs where a single blade server is connected to each port. If Immediate Leave is enabled in VLANs where more than one blade server is connected to a port, some blade servers might inadvertently be dropped.
For configuration steps, see the "Enabling IGMP Immediate Leave" section.
IGMP Configurable-Leave Timer
You can configure the time that the switch waits after sending a group-specific query to determine if hosts are still interested in a specific multicast group. The IGMP leave response time can be configured from 100 to 5000 milliseconds. The timer can be set either globally or on a per-VLAN basis. The VLAN configuration of the leave time overrides the global configuration.
For configuration steps, see the "Configuring the IGMP Leave Timer" section.
IGMP Report Suppression

Note ![]() IGMP report suppression is supported only when the multicast query has IGMPv1 and IGMPv2 reports. This feature is not supported when the query includes IGMPv3 reports.
IGMP report suppression is supported only when the multicast query has IGMPv1 and IGMPv2 reports. This feature is not supported when the query includes IGMPv3 reports.
The switch uses IGMP report suppression to forward only one IGMP report per multicast router query to multicast devices. When IGMP router suppression is enabled (the default), the switch sends the first IGMP report from all blade servers for a group to all the multicast routers. The switch does not send the remaining IGMP reports for the group to the multicast routers. This feature prevents duplicate reports from being sent to the multicast devices.
If the multicast router query includes requests only for IGMPv1 and IGMPv2 reports, the switch forwards only the first IGMPv1 or IGMPv2 report from all blade servers for a group to all the multicast routers. If the multicast router query also includes requests for IGMPv3 reports, the switch forwards all IGMPv1, IGMPv2, and IGMPv3 reports for a group to the multicast devices.
If you disable IGMP report suppression, all IGMP reports are forwarded to the multicast routers. For configuration steps, see the "Disabling IGMP Report Suppression" section.
Configuring IGMP Snooping
IGMP snooping allows switches to examine IGMP packets and make forwarding decisions based on their content. These sections contain this configuration information:
•![]() Default IGMP Snooping Configuration
Default IGMP Snooping Configuration
•![]() Enabling or Disabling IGMP Snooping
Enabling or Disabling IGMP Snooping
•![]() Configuring a Multicast Router Port
Configuring a Multicast Router Port
•![]() Configuring a Blade Server Statically to Join a Group
Configuring a Blade Server Statically to Join a Group
•![]() Enabling IGMP Immediate Leave
Enabling IGMP Immediate Leave
•![]() Configuring the IGMP Leave Timer
Configuring the IGMP Leave Timer
•![]() Configuring TCN-Related Commands
Configuring TCN-Related Commands
•![]() Configuring the IGMP Snooping Querier
Configuring the IGMP Snooping Querier
•![]() Disabling IGMP Report Suppression
Disabling IGMP Report Suppression
Default IGMP Snooping Configuration
Table 23-3 shows the default IGMP snooping configuration.
|
|
|
|---|---|
IGMP snooping |
Enabled globally and per VLAN |
Multicast routers |
None configured |
Multicast router learning (snooping) method |
PIM-DVMRP |
IGMP snooping Immediate Leave |
Disabled |
Static groups |
None configured |
TCN1 flood query count |
2 |
TCN query solicitation |
Disabled |
IGMP snooping querier |
Disabled |
IGMP report suppression |
Enabled |
1 TCN = Topology Change Notification |
Enabling or Disabling IGMP Snooping
By default, IGMP snooping is globally enabled on the switch. When globally enabled or disabled, it is also enabled or disabled in all existing VLAN interfaces. IGMP snooping is by default enabled on all VLANs, but can be enabled and disabled on a per-VLAN basis.
Global IGMP snooping overrides the VLAN IGMP snooping. If global snooping is disabled, you cannot enable VLAN snooping. If global snooping is enabled, you can enable or disable VLAN snooping.
Beginning in privileged EXEC mode, follow these steps to globally enable IGMP snooping on the switch:
To globally disable IGMP snooping on all VLAN interfaces, use the no ip igmp snooping global configuration command.
Beginning in privileged EXEC mode, follow these steps to enable IGMP snooping on a VLAN interface:
To disable IGMP snooping on a VLAN interface, use the no ip igmp snooping vlan vlan-id global configuration command for the specified VLAN number.
Setting the Snooping Method
Multicast-capable router ports are added to the forwarding table for every Layer 2 multicast entry. The switch learns of such ports through one of these methods:
•![]() Snooping on IGMP queries, Protocol Independent Multicast (PIM) packets, and Distance Vector Multicast Routing Protocol (DVMRP) packets
Snooping on IGMP queries, Protocol Independent Multicast (PIM) packets, and Distance Vector Multicast Routing Protocol (DVMRP) packets
•![]() Listening to Cisco Group Management Protocol (CGMP) packets from other routers
Listening to Cisco Group Management Protocol (CGMP) packets from other routers
•![]() Statically connecting to a multicast router port with the ip igmp snooping mrouter global configuration command
Statically connecting to a multicast router port with the ip igmp snooping mrouter global configuration command
You can configure the switch either to snoop on IGMP queries and PIM/DVMRP packets or to listen to CGMP self-join or proxy-join packets. By default, the switch snoops on PIM/DVMRP packets on all VLANs. To learn of multicast router ports through only CGMP packets, use the ip igmp snooping vlan vlan-id mrouter learn cgmp global configuration command. When this command is entered, the router listens to only CGMP self-join and CGMP proxy-join packets and to no other CGMP packets. To learn of multicast router ports through only PIM-DVMRP packets, use the ip igmp snooping vlan vlan-id mrouter learn pim-dvmrp global configuration command.

Note ![]() If you want to use CGMP as the learning method and no multicast routers in the VLAN are CGMP proxy-enabled, you must enter the ip cgmp router-only command to dynamically access the router.
If you want to use CGMP as the learning method and no multicast routers in the VLAN are CGMP proxy-enabled, you must enter the ip cgmp router-only command to dynamically access the router.
Beginning in privileged EXEC mode, follow these steps to alter the method in which a VLAN interface dynamically accesses a multicast router:
To return to the default learning method, use the no ip igmp snooping vlan vlan-id mrouter learn cgmp global configuration command.
This example shows how to configure IGMP snooping to use CGMP packets as the learning method:
Switch# configure terminal
Switch(config)# ip igmp snooping vlan 1 mrouter learn cgmp
Switch(config)# end
Configuring a Multicast Router Port
To add a multicast router port (add a static connection to a multicast router), use the ip igmp snooping vlan mrouter global configuration command on the switch.

Note ![]() Static connections to multicast routers are supported only on switch ports.
Static connections to multicast routers are supported only on switch ports.
Beginning in privileged EXEC mode, follow these steps to enable a static connection to a multicast router:
To remove a multicast router port from the VLAN, use the no ip igmp snooping vlan vlan-id mrouter interface interface-id global configuration command.
This example shows how to enable a static connection to a multicast router:
Switch# configure terminal
Switch(config)# ip igmp snooping vlan 200 mrouter interface gigabitethernet0/2
Switch(config)# end
Configuring a Blade Server Statically to Join a Group
Blade servers that are connected to Layer 2 ports normally join multicast groups dynamically. You can also statically configure a Layer 2 port, to which a blade server is connected, so that the port joins a multicast group.
Beginning in privileged EXEC mode, follow these steps to add a Layer 2 port as a member of a multicast group:
To remove the Layer 2 port from the multicast group, use the no ip igmp snooping vlan vlan-id static mac-address interface interface-id global configuration command.
This example shows how to statically configure a blade server on a port:
Switch# configure terminal
Switch(config)# ip igmp snooping vlan 105 static 224.2.4.12 interface gigabitethernet0/1
Switch(config)# end
Enabling IGMP Immediate Leave
When you enable IGMP Immediate Leave, the switch immediately removes a port when it detects an IGMP Version 2 leave message on that port. You should only use the Immediate-Leave feature when there is a single receiver present on every port in the VLAN.

Note ![]() Immediate Leave is supported only on IGMP Version 2 blade servers.
Immediate Leave is supported only on IGMP Version 2 blade servers.
Beginning in privileged EXEC mode, follow these steps to enable IGMP Immediate Leave:
To disable IGMP Immediate Leave on a VLAN, use the no ip igmp snooping vlan vlan-id immediate-leave global configuration command.
This example shows how to enable IGMP Immediate Leave on VLAN 130:
Switch# configure terminal
Switch(config)# ip igmp snooping vlan 130 immediate-leave
Switch(config)# end
Configuring the IGMP Leave Timer
Follows these guidelines when configuring the IGMP leave timer:
•![]() You can configure the leave time globally or on a per-VLAN basis.
You can configure the leave time globally or on a per-VLAN basis.
•![]() Configuring the leave time on a VLAN overrides the global setting.
Configuring the leave time on a VLAN overrides the global setting.
•![]() The default leave time is 1000 milliseconds.
The default leave time is 1000 milliseconds.
•![]() The IGMP configurable leave time is only supported on hosts running IGMP Version 2.
The IGMP configurable leave time is only supported on hosts running IGMP Version 2.
•![]() The actual leave latency in the network is usually the configured leave time. However, the leave time might vary around the configured time, depending on real-time CPU load conditions, network delays and the amount of traffic sent through the interface.
The actual leave latency in the network is usually the configured leave time. However, the leave time might vary around the configured time, depending on real-time CPU load conditions, network delays and the amount of traffic sent through the interface.
Beginning in privileged EXEC mode, follow these steps to enable the IGMP configurable-leave timer:
To globally reset the IGMP leave timer to the default setting, use the no ip igmp snooping last-member-query-interval global configuration command.
To remove the configured IGMP leave-time setting from the specified VLAN, use the no ip igmp snooping vlan vlan-id last-member-query-interval global configuration command.
Configuring TCN-Related Commands
These sections describe how to control flooded multicast traffic during a TCN event:
•![]() Controlling the Multicast Flooding Time After a TCN Event
Controlling the Multicast Flooding Time After a TCN Event
•![]() Disabling Multicast Flooding During a TCN Event
Disabling Multicast Flooding During a TCN Event
Controlling the Multicast Flooding Time After a TCN Event
You can control the time that multicast traffic is flooded after a TCN event by using the ip igmp snooping tcn flood query count global configuration command. This command configures the number of general queries for which multicast data traffic is flooded after a TCN event. Some examples of TCN events are when the client changed its location and the receiver is on same port that was blocked but is now forwarding, and when a port went down without sending a leave message.
If you set the TCN flood query count to 1 by using the ip igmp snooping tcn flood query count command, the flooding stops after receiving 1 general query. If you set the count to 7, the flooding until 7 general queries are received. Groups are relearned based on the general queries received during the TCN event.
Beginning in privileged EXEC mode, follow these steps to configure the TCN flood query count:
To return to the default flooding query count, use the no ip igmp snooping tcn flood query count global configuration command.
Recovering from Flood Mode
When a topology change occurs, the spanning-tree root sends a special IGMP leave message (also known as global leave) with the group multicast address 0.0.0.0. However, when you enable the ip igmp snooping tcn query solicit global configuration command, the switch sends the global leave message whether or not it is the spanning-tree root. When the router receives this special leave, it immediately sends general queries, which expedite the process of recovering from the flood mode during the TCN event. Leaves are always sent if the switch is the spanning-tree root regardless of this configuration command. By default, query solicitation is disabled.
Beginning in privileged EXEC mode, follow these steps to enable the switch to send the global leave message whether or not it is the spanning-tree root:
To return to the default query solicitation, use the no ip igmp snooping tcn query solicit global configuration command.
Disabling Multicast Flooding During a TCN Event
When the switch receives a TCN, multicast traffic is flooded to all the ports until 2 general queries are received. If the switch has many ports with attached hosts that are subscribed to different multicast groups, this flooding might exceed the capacity of the link and cause packet loss. You can use the ip igmp snooping tcn flood interface configuration command to control this behavior.
Beginning in privileged EXEC mode, follow these steps to disable multicast flooding on an interface:
To re-enable multicast flooding on an interface, use the ip igmp snooping tcn flood interface configuration command.
Configuring the IGMP Snooping Querier
Follow these guidelines when configuring the IGMP snooping querier:
•![]() Configure the VLAN in global configuration mode.
Configure the VLAN in global configuration mode.
•![]() Configure an IP address on the VLAN interface. When enabled, the IGMP snooping querier uses the IP address as the query source address.
Configure an IP address on the VLAN interface. When enabled, the IGMP snooping querier uses the IP address as the query source address.
•![]() If there is no IP address configured on the VLAN interface, the IGMP snooping querier tries to use the configured global IP address for the IGMP querier. If there is no global IP address specified, the IGMP querier tries to use the VLAN switch virtual interface (SVI) IP address (if one exists). If there is no SVI IP address, the switch uses the first available IP address configured on the switch. The first IP address available appears in the output of the show ip interface privileged EXEC command. The IGMP snooping querier does not generate an IGMP general query if it cannot find an available IP address on the switch.
If there is no IP address configured on the VLAN interface, the IGMP snooping querier tries to use the configured global IP address for the IGMP querier. If there is no global IP address specified, the IGMP querier tries to use the VLAN switch virtual interface (SVI) IP address (if one exists). If there is no SVI IP address, the switch uses the first available IP address configured on the switch. The first IP address available appears in the output of the show ip interface privileged EXEC command. The IGMP snooping querier does not generate an IGMP general query if it cannot find an available IP address on the switch.
•![]() The IGMP snooping querier supports IGMP Versions 1 and 2.
The IGMP snooping querier supports IGMP Versions 1 and 2.
•![]() When administratively enabled, the IGMP snooping querier moves to the nonquerier state if it detects the presence of a multicast router in the network.
When administratively enabled, the IGMP snooping querier moves to the nonquerier state if it detects the presence of a multicast router in the network.
•![]() When it is administratively enabled, the IGMP snooping querier moves to the operationally disabled state under these conditions:
When it is administratively enabled, the IGMP snooping querier moves to the operationally disabled state under these conditions:
–![]() IGMP snooping is disabled in the VLAN.
IGMP snooping is disabled in the VLAN.
–![]() PIM is enabled on the SVI of the corresponding VLAN.
PIM is enabled on the SVI of the corresponding VLAN.
Beginning in privileged EXEC mode, follow these steps to enable the IGMP snooping querier feature in a VLAN:
This example shows how to set the IGMP snooping querier source address to 10.0.0.64:
Switch# configure terminal
Switch(config)# ip igmp snooping querier 10.0.0.64
Switch(config)# end
This example shows how to set the IGMP snooping querier maximum response time to 25 seconds:
Switch# configure terminal
Switch(config)# ip igmp snooping querier query-interval 25
Switch(config)# end
This example shows how to set the IGMP snooping querier timeout to 60 seconds:
Switch# configure terminal
Switch(config)# ip igmp snooping querier timeout expiry 60
Switch(config)# end
This example shows how to set the IGMP snooping querier feature to version 2:
Switch# configure terminal
Switch(config)# no ip igmp snooping querier version 2
Switch(config)# end
Disabling IGMP Report Suppression

Note ![]() IGMP report suppression is supported only when the multicast query has IGMPv1 and IGMPv2 reports. This feature is not supported when the query includes IGMPv3 reports.
IGMP report suppression is supported only when the multicast query has IGMPv1 and IGMPv2 reports. This feature is not supported when the query includes IGMPv3 reports.
IGMP report suppression is enabled by default. When it is enabled, the switch forwards only one IGMP report per multicast router query. When report suppression is disabled, all IGMP reports are forwarded to the multicast routers.
Beginning in privileged EXEC mode, follow these steps to disable IGMP report suppression:
To re-enable IGMP report suppression, use the ip igmp snooping report-suppression global configuration command.
Displaying IGMP Snooping Information
You can display IGMP snooping information for dynamically learned and statically configured router ports and VLAN interfaces. You can also display MAC address multicast entries for a VLAN configured for IGMP snooping.
To display IGMP snooping information, use one or more of the privileged EXEC commands in Table 23-4.
For more information about the keywords and options in these commands, see the command reference for this release.
Understanding Multicast VLAN Registration
Multicast VLAN Registration (MVR) is designed for applications using wide-scale deployment of multicast traffic across an Ethernet ring-based service-provider network (for example, the broadcast of multiple television channels over a service-provider network). MVR allows a subscriber on a port to subscribe and unsubscribe to a multicast stream on the network-wide multicast VLAN. It allows the single multicast VLAN to be shared in the network while subscribers remain in separate VLANs. MVR provides the ability to continuously send multicast streams in the multicast VLAN, but to isolate the streams from the subscriber VLANs for bandwidth and security reasons.
MVR assumes that subscriber ports subscribe and unsubscribe (join and leave) these multicast streams by sending out IGMP join and leave messages. These messages can originate from an IGMP Version-2-compatible blade server with an Ethernet connection. Although MVR operates on the underlying mechanism of IGMP snooping, the two features operate independently of each other. One can be enabled or disabled without affecting the behavior of the other feature. However, if IGMP snooping and MVR are both enabled, MVR reacts only to join and leave messages from multicast groups configured under MVR. Join and leave messages from all other multicast groups are managed by IGMP snooping.
The switch CPU identifies the MVR IP multicast streams and their associated IP multicast group in the switch forwarding table, intercepts the IGMP messages, and modifies the forwarding table to include or remove the subscriber as a receiver of the multicast stream, even though the receivers might be in a different VLAN from the source. This forwarding behavior selectively allows traffic to cross between different VLANs.
You can set the switch for compatible or dynamic mode of MVR operation:
•![]() In compatible mode, multicast data received by MVR hosts is forwarded to all MVR data ports, regardless of MVR host membership on those ports. The multicast data is forwarded only to those receiver ports that MVR hosts have joined, either by IGMP reports or by MVR static configuration. IGMP reports received from MVR hosts are never forwarded from MVR data ports that were configured in the blade server.
In compatible mode, multicast data received by MVR hosts is forwarded to all MVR data ports, regardless of MVR host membership on those ports. The multicast data is forwarded only to those receiver ports that MVR hosts have joined, either by IGMP reports or by MVR static configuration. IGMP reports received from MVR hosts are never forwarded from MVR data ports that were configured in the blade server.
•![]() In dynamic mode, multicast data received by MVR hosts on the switch is forwarded from only those MVR data and client ports that the MVR hosts have joined, either by IGMP reports or by MVR static configuration. Any IGMP reports received from MVR hosts are also forwarded from all the MVR data ports in the blade server. This eliminates using unnecessary bandwidth on MVR data port links, which occurs when the blade server runs in compatible mode.
In dynamic mode, multicast data received by MVR hosts on the switch is forwarded from only those MVR data and client ports that the MVR hosts have joined, either by IGMP reports or by MVR static configuration. Any IGMP reports received from MVR hosts are also forwarded from all the MVR data ports in the blade server. This eliminates using unnecessary bandwidth on MVR data port links, which occurs when the blade server runs in compatible mode.
Only Layer 2 ports take part in MVR. You must configure ports as MVR receiver ports. Only one MVR multicast VLAN per switch is supported.
Using MVR in a Multicast Television Application
In a multicast television application, a PC or a television with a set-top box can receive the multicast stream. Multiple set-top boxes or PCs can be connected to one subscriber port, which is a switch port configured as an MVR receiver port. Figure 23-3 is an example configuration. DHCP assigns an IP address to the set-top box or the PC. When a subscriber selects a channel, the set-top box or PC sends an IGMP report to Switch A to join the appropriate multicast. If the IGMP report matches one of the configured IP multicast group addresses, the switch CPU modifies the hardware address table to include this receiver port and VLAN as a forwarding destination of the specified multicast stream when it is received from the multicast VLAN. Uplink ports that send and receive multicast data to and from the multicast VLAN are called MVR source ports.
Figure 23-3 Multicast VLAN Registration Example
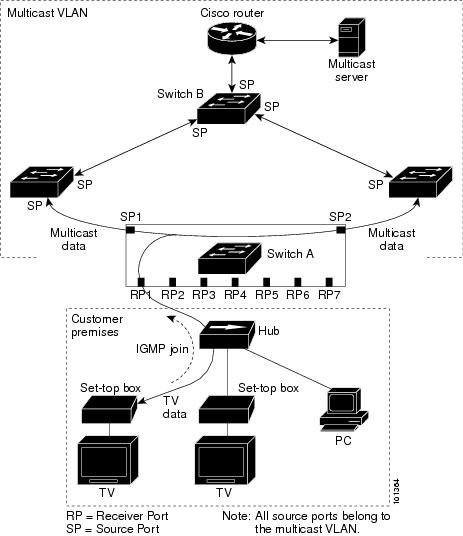
When a subscriber changes channels or turns off the television, the set-top box sends an IGMP leave message for the multicast stream. The switch CPU sends a MAC-based general query through the receiver port VLAN. If there is another set-top box in the VLAN still subscribing to this group, that set-top box must respond within the maximum response time specified in the query. If the CPU does not receive a response, it eliminates the receiver port as a forwarding destination for this group.
Without Immediate Leave, when the switch receives an IGMP leave message from a subscriber on a receiver port, it sends out an IGMP query on that port and waits for IGMP group membership reports. If no reports are received in a configured time period, the receiver port is removed from multicast group membership. With Immediate Leave, an IGMP query is not sent from the receiver port on which the IGMP leave was received. As soon as the leave message is received, the receiver port is removed from multicast group membership, which speeds up leave latency. Enable the Immediate-Leave feature only on receiver ports to which a single receiver device is connected.
MVR eliminates the need to duplicate television-channel multicast traffic for subscribers in each VLAN. Multicast traffic for all channels is only sent around the VLAN trunk once—only on the multicast VLAN. The IGMP leave and join messages are in the VLAN to which the subscriber port is assigned. These messages dynamically register for streams of multicast traffic in the multicast VLAN on the Layer 3 device. Switch B. The access layer switch, Switch A, modifies the forwarding behavior to allow the traffic to be forwarded from the multicast VLAN to the subscriber port in a different VLAN, selectively allowing traffic to cross between two VLANs.
IGMP reports are sent to the same IP multicast group address as the multicast data. The Switch A CPU must capture all IGMP join and leave messages from receiver ports and forward them to the multicast VLAN of the source (uplink) port, based on the MVR mode.
Configuring MVR
These sections contain this configuration information:
•![]() MVR Configuration Guidelines and Limitations
MVR Configuration Guidelines and Limitations
•![]() Configuring MVR Global Parameters
Configuring MVR Global Parameters
Default MVR Configuration
Table 23-5 shows the default MVR configuration.
MVR Configuration Guidelines and Limitations
Follow these guidelines when configuring MVR:
•![]() Receiver ports can only be access ports; they cannot be trunk ports. Receiver ports on a switch can be in different VLANs, but should not belong to the multicast VLAN.
Receiver ports can only be access ports; they cannot be trunk ports. Receiver ports on a switch can be in different VLANs, but should not belong to the multicast VLAN.
•![]() The maximum number of multicast entries (MVR group addresses) that can be configured on a switch (that is, the maximum number of television channels that can be received) is 256.
The maximum number of multicast entries (MVR group addresses) that can be configured on a switch (that is, the maximum number of television channels that can be received) is 256.
•![]() MVR multicast data received in the source VLAN and leaving from receiver ports has its time-to-live (TTL) decremented by 1 in the switch.
MVR multicast data received in the source VLAN and leaving from receiver ports has its time-to-live (TTL) decremented by 1 in the switch.
•![]() Because MVR on the switch uses IP multicast addresses instead of MAC multicast addresses, aliased IP multicast addresses are allowed on the switch. However, if the switch is interoperating with Catalyst 3550 or Catalyst 3500 XL switches, you should not configure IP addresses that alias between themselves or with the reserved IP multicast addresses (in the range 224.0.0.xxx).
Because MVR on the switch uses IP multicast addresses instead of MAC multicast addresses, aliased IP multicast addresses are allowed on the switch. However, if the switch is interoperating with Catalyst 3550 or Catalyst 3500 XL switches, you should not configure IP addresses that alias between themselves or with the reserved IP multicast addresses (in the range 224.0.0.xxx).
•![]() Do not configure MVR on private VLAN ports.
Do not configure MVR on private VLAN ports.
•![]() MVR can coexist with IGMP snooping on a switch.
MVR can coexist with IGMP snooping on a switch.
•![]() MVR data received on an MVR receiver port is not forwarded to MVR source ports.
MVR data received on an MVR receiver port is not forwarded to MVR source ports.
•![]() MVR does not support IGMPv3 messages.
MVR does not support IGMPv3 messages.
Configuring MVR Global Parameters
You do not need to set the optional MVR parameters if you choose to use the default settings. If you do want to change the default parameters (except for the MVR VLAN), you must first enable MVR.

Note ![]() For complete syntax and usage information for the commands used in this section, see the command reference for this release.
For complete syntax and usage information for the commands used in this section, see the command reference for this release.
Beginning in privileged EXEC mode, follow these steps to configure MVR parameters:
To return the switch to its default settings, use the no mvr [mode | group ip-address | querytime | vlan] global configuration commands.
This example shows how to enable MVR, configure the group address, set the query time to 1 second (10 tenths), specify the MVR multicast VLAN as VLAN 22, and set the MVR mode as dynamic:
Switch(config)# mvr
Switch(config)# mvr group 228.1.23.4
Switch(config)# mvr querytime 10
Switch(config)# mvr vlan 22
Switch(config)# mvr mode dynamic
Switch(config)# end
You can use the show mvr members privileged EXEC command to verify the MVR multicast group addresses on the switch.
Configuring MVR Interfaces
Beginning in privileged EXEC mode, follow these steps to configure Layer 2 MVR interfaces:
To return the interface to its default settings, use the no mvr [type | immediate | vlan vlan-id | group] interface configuration commands.
This example shows how to configure a port as a receiver port, statically configure the port to receive multicast traffic sent to the multicast group address, configure Immediate Leave on the port, and verify the results.
Switch(config)# mvr
Switch(config)# interface gigabitethernet0/2
Switch(config-if)# mvr type receiver
Switch(config-if)# mvr vlan 22 group 228.1.23.4
Switch(config-if)# mvr immediate
Switch(config)# end
Switch# show mvr interface
Port Type Status Immediate Leave
---- ---- ------- ---------------
Gi0/2 RECEIVER ACTIVE/DOWN ENABLED
Displaying MVR Information
You can display MVR information for the switch or for a specified interface. Beginning in privileged EXEC mode, use the commands in Table 23-6 to display MVR configuration:
Configuring IGMP Filtering and Throttling
In some environments, for example, metropolitan or multiple-dwelling unit (MDU) installations, you might want to control the set of multicast groups to which a user on a switch port can belong. You can control the distribution of multicast services, such as IP/TV, based on some type of subscription or service plan. You might also want to limit the number of multicast groups to which a user on a switch port can belong.
With the IGMP filtering feature, you can filter multicast joins on a per-port basis by configuring IP multicast profiles and associating them with individual switch ports. An IGMP profile can contain one or more multicast groups and specifies whether access to the group is permitted or denied. If an IGMP profile denying access to a multicast group is applied to a switch port, the IGMP join report requesting the stream of IP multicast traffic is dropped, and the port is not allowed to receive IP multicast traffic from that group. If the filtering action permits access to the multicast group, the IGMP report from the port is forwarded for normal processing. You can also set the maximum number of IGMP groups that a Layer 2 interface can join.
IGMP filtering controls only group-specific query and membership reports, including join and leave reports. It does not control general IGMP queries. IGMP filtering has no relationship with the function that directs the forwarding of IP multicast traffic. The filtering feature operates in the same manner whether CGMP or MVR is used to forward the multicast traffic.
IGMP filtering is applicable only to the dynamic learning of IP multicast group addresses, not static configuration.
With the IGMP throttling feature, you can set the maximum number of IGMP groups that a Layer 2 interface can join. If the maximum number of IGMP groups is set, the IGMP snooping forwarding table contains the maximum number of entries, and the interface receives an IGMP join report, you can configure an interface to drop the IGMP report or to replace the randomly selected multicast entry with the received IGMP report.

Note ![]() IGMPv3 join and leave messages are not supported on switches running IGMP filtering.
IGMPv3 join and leave messages are not supported on switches running IGMP filtering.
These sections contain this configuration information:
•![]() Default IGMP Filtering and Throttling Configuration
Default IGMP Filtering and Throttling Configuration
•![]() Configuring IGMP Profiles (optional)
Configuring IGMP Profiles (optional)
•![]() Applying IGMP Profiles (optional)
Applying IGMP Profiles (optional)
•![]() Setting the Maximum Number of IGMP Groups (optional)
Setting the Maximum Number of IGMP Groups (optional)
•![]() Configuring the IGMP Throttling Action (optional)
Configuring the IGMP Throttling Action (optional)
Default IGMP Filtering and Throttling Configuration
Table 23-7 shows the default IGMP filtering configuration.
When the maximum number of groups is in forwarding table, the default IGMP throttling action is to deny the IGMP report. For configuration guidelines, see the "Configuring the IGMP Throttling Action" section.
Configuring IGMP Profiles
To configure an IGMP profile, use the ip igmp profile global configuration command with a profile number to create an IGMP profile and to enter IGMP profile configuration mode. From this mode, you can specify the parameters of the IGMP profile to be used for filtering IGMP join requests from a port. When you are in IGMP profile configuration mode, you can create the profile by using these commands:
•![]() deny: Specifies that matching addresses are denied; this is the default.
deny: Specifies that matching addresses are denied; this is the default.
•![]() exit: Exits from igmp-profile configuration mode.
exit: Exits from igmp-profile configuration mode.
•![]() no: Negates a command or returns to its defaults.
no: Negates a command or returns to its defaults.
•![]() permit: Specifies that matching addresses are permitted.
permit: Specifies that matching addresses are permitted.
•![]() range: Specifies a range of IP addresses for the profile. You can enter a single IP address or a range with a start and an end address.
range: Specifies a range of IP addresses for the profile. You can enter a single IP address or a range with a start and an end address.
The default is for the switch to have no IGMP profiles configured. When a profile is configured, if neither the permit nor deny keyword is included, the default is to deny access to the range of IP addresses.
Beginning in privileged EXEC mode, follow these steps to create an IGMP profile:
To delete a profile, use the no ip igmp profile profile number global configuration command.
To delete an IP multicast address or range of IP multicast addresses, use the no range ip multicast address IGMP profile configuration command.
This example shows how to create IGMP profile 4 allowing access to the single IP multicast address and how to verify the configuration. If the action was to deny (the default), it would not appear in the show ip igmp profile output display.
Switch(config)# ip igmp profile 4
Switch(config-igmp-profile)# permit
Switch(config-igmp-profile)# range 229.9.9.0
Switch(config-igmp-profile)# end
Switch# show ip igmp profile 4
IGMP Profile 4
permit
range 229.9.9.0 229.9.9.0
Applying IGMP Profiles
To control access as defined in an IGMP profile, use the ip igmp filter interface configuration command to apply the profile to the appropriate interfaces. You can apply IGMP profiles only to Layer 2 access ports; you cannot apply IGMP profiles to routed ports or SVIs. You cannot apply profiles to ports that belong to an EtherChannel port group. You can apply a profile to multiple interfaces, but each interface can have only one profile applied to it.
Beginning in privileged EXEC mode, follow these steps to apply an IGMP profile to a switch port:
To remove a profile from an interface, use the no ip igmp filter profile number interface configuration command.
This example shows how to apply IGMP profile 4 to a port:
Switch(config)# interface gigabitethernet0/2
Switch(config-if)# ip igmp filter 4
Switch(config-if)# end
Setting the Maximum Number of IGMP Groups
You can set the maximum number of IGMP groups that a Layer 2 interface can join by using the ip igmp max-groups interface configuration command. Use the no form of this command to set the maximum back to the default, which is no limit.
This restriction can be applied to Layer 2 ports only; you cannot set a maximum number of IGMP groups on routed ports or SVIs. You also can use this command on a logical EtherChannel interface but cannot use it on ports that belong to an EtherChannel port group.
Beginning in privileged EXEC mode, follow these steps to set the maximum number of IGMP groups in the forwarding table:
To remove the maximum group limitation and return to the default of no maximum, use the no ip igmp max-groups interface configuration command.
This example shows how to limit to 25 the number of IGMP groups that a port can join.
Switch(config)# interface gigabitethernet0/2
Switch(config-if)# ip igmp max-groups 25
Switch(config-if)# end
Configuring the IGMP Throttling Action
After you set the maximum number of IGMP groups that a Layer 2 interface can join, you can configure an interface to replace the existing group with the new group for which the IGMP report was received by using the ip igmp max-groups action replace interface configuration command. Use the no form of this command to return to the default, which is to drop the IGMP join report.
Follow these guidelines when configuring the IGMP throttling action:
•![]() This restriction can be applied only to Layer 2 ports. You can use this command on a logical EtherChannel interface but cannot use it on ports that belong to an EtherChannel port group.
This restriction can be applied only to Layer 2 ports. You can use this command on a logical EtherChannel interface but cannot use it on ports that belong to an EtherChannel port group.
•![]() When the maximum group limitation is set to the default (no maximum), entering the ip igmp max-groups action {deny | replace} command has no effect.
When the maximum group limitation is set to the default (no maximum), entering the ip igmp max-groups action {deny | replace} command has no effect.
•![]() If you configure the throttling action and set the maximum group limitation after an interface has added multicast entries to the forwarding table, the forwarding-table entries are either aged out or removed, depending on the throttling action.
If you configure the throttling action and set the maximum group limitation after an interface has added multicast entries to the forwarding table, the forwarding-table entries are either aged out or removed, depending on the throttling action.
–![]() If you configure the throttling action as deny, the entries that were previously in the forwarding table are not removed but are aged out. After these entries are aged out and the maximum number of entries is in the forwarding table, the switch drops the next IGMP report received on the interface.
If you configure the throttling action as deny, the entries that were previously in the forwarding table are not removed but are aged out. After these entries are aged out and the maximum number of entries is in the forwarding table, the switch drops the next IGMP report received on the interface.
–![]() If you configure the throttling action as replace, the entries that were previously in the forwarding table are removed. When the maximum number of entries is in the forwarding table, the switch replaces a randomly selected entry with the received IGMP report.
If you configure the throttling action as replace, the entries that were previously in the forwarding table are removed. When the maximum number of entries is in the forwarding table, the switch replaces a randomly selected entry with the received IGMP report.
To prevent the switch from removing the forwarding-table entries, you can configure the IGMP throttling action before an interface adds entries to the forwarding table.
Beginning in privileged EXEC mode, follow these steps to configure the throttling action when the maximum number of entries is in the forwarding table:
To return to the default action of dropping the report, use the no ip igmp max-groups action interface configuration command.
Displaying IGMP Filtering and Throttling Configuration
You can display IGMP profile characteristics, and you can display the IGMP profile and maximum group configuration for all interfaces on the switch or for a specified interface. You can also display the IGMP throttling configuration for all interfaces on the switch or for a specified interface.
Use the privileged EXEC commands in Table 23-8 to display IGMP filtering and throttling configuration:
 Feedback
Feedback