- Preface
- Getting Started
- Configuring Device Lists
- Configuring Dashboards
- Configuring RSS Feeds
- Using the Startup Wizard
- Setting Up the Sensor
- Configuring Interfaces
- Configuring Policies
- Defining Signatures
- Using the Signature Wizard
- Configuring Event Action Rules
- Configuring Anomaly Detection
- Configuring Global Correlation
- Configuring SSH and Certificates
- Configuring Attack Response Controller for Blocking and Rate Limiting
- Configuring SNMP
- Configuring External Product Interfaces
- Managing the Sensor
- Monitoring the Sensor
- Configuring Event Monitoring
- Configuring and Generating Reports
- Logging In to the Sensor
- Initializing the Sensor
- Obtaining Software
- Upgrading, Downgrading, and Installing System Images
- System Architecture
- Signature Engines
- Troubleshooting
- Open Source License Files
- Glossary
- Index
Cisco Intrusion Prevention System Manager Express Configuration Guide for IPS 7.0
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- April 20, 2009
Chapter: Configuring Event Action Rules
- Understanding Security Policies
- Event Action Rules Components
- Configuring Event Action Rules Policies
- Understanding the rules0 Pane
- Configuring Event Action Overrides
- Configuring Event Action Filters
- Configuring IPv4 Target Value Rating
- Configuring IPv6 Target Value Rating
- Configuring OS Identifications
- Configuring Event Variables
- Configuring Risk Category
- Configuring General Settings
Configuring Event Action Rules
This chapter explains how to add event action rules policies and how to configure event action rules. It contains the following sections:
•![]() Understanding Security Policies
Understanding Security Policies
•![]() Event Action Rules Components
Event Action Rules Components
•![]() Configuring Event Action Rules Policies
Configuring Event Action Rules Policies
•![]() Understanding the rules0 Pane
Understanding the rules0 Pane
•![]() Configuring Event Action Overrides
Configuring Event Action Overrides
•![]() Configuring Event Action Filters
Configuring Event Action Filters
•![]() Configuring IPv4 Target Value Rating
Configuring IPv4 Target Value Rating
•![]() Configuring IPv6 Target Value Rating
Configuring IPv6 Target Value Rating
•![]() Configuring OS Identifications
Configuring OS Identifications

Note ![]() In the Event Action Rules pane, you can create event action rules policies and configure them. You can also configure event action rules in the lower half of the IPS Policies pane: Configuration > sensor_name > Policies > IPS Policies.
In the Event Action Rules pane, you can create event action rules policies and configure them. You can also configure event action rules in the lower half of the IPS Policies pane: Configuration > sensor_name > Policies > IPS Policies.
Understanding Security Policies

Note ![]() The AIM IPS and NME IPS do not support multiple policies.
The AIM IPS and NME IPS do not support multiple policies.
You can create multiple security policies and apply them to individual virtual sensors. A security policy is made up of a signature definition policy, an event action rules policy, and an anomaly detection policy. Cisco IPS contains a default signature definition policy called sig0, a default event action rules policy called rules0, and a default anomaly detection policy called ad0. You can assign the default policies to a virtual sensor or you can create new policies. The use of multiple security policies lets you create security policies based on different requirements and then apply these customized policies per VLAN or physical interface.
Event Action Rules Components
This section describes the various components of event action rules, and contains the following topics:
•![]() Understanding Event Action Rules
Understanding Event Action Rules
•![]() Understanding Event Action Overrides
Understanding Event Action Overrides
•![]() Understanding Event Action Filters
Understanding Event Action Filters
•![]() Signature Event Action Processor
Signature Event Action Processor
Understanding Event Action Rules
Event action rules are a group of settings you configure for the event action processing component of the sensor. These rules dictate the actions the sensor performs when an event occurs.
The event action processing component is responsible for the following functions:
•![]() Calculating the risk rating
Calculating the risk rating
•![]() Adding event action overrides
Adding event action overrides
•![]() Filtering event action
Filtering event action
•![]() Executing the resulting event action
Executing the resulting event action
•![]() Summarizing and aggregating events
Summarizing and aggregating events
•![]() Maintaining a list of denied attackers
Maintaining a list of denied attackers

Note ![]() Rate limiting and blocking are not supported for IPv6 traffic. If a signature is configured with a block or rate limit event action and is triggered by IPv6 traffic, an alert is generated but the action is not carried out.
Rate limiting and blocking are not supported for IPv6 traffic. If a signature is configured with a block or rate limit event action and is triggered by IPv6 traffic, an alert is generated but the action is not carried out.
Calculating the Risk Rating

Note ![]() The risk rating is associated with alerts not signatures.
The risk rating is associated with alerts not signatures.
A risk rating (RR) is a value between 0 and 100 that represents a numerical quantification of the risk associated with a particular event on the network. The calculation takes into account the value of the network asset being attacked (for example, a particular server), so it is configured on a per-signature basis using the attack severity rating and the signature fidelity rating, and on a per-server basis using the target value rating. The risk rating is calculated from several components, some of which are configured, some collected, and some derived.
Risk ratings let you prioritize alerts that need your attention. These risk rating factors take into consideration the severity of the attack if it succeeds, the fidelity of the signature, the reputation score of the attacker from the Global Correlation data, and the overall value of the target host to you. The risk rating is reported in the evIdsAlert.
The following values are used to calculate the risk rating for a particular event:
•![]() Signature fidelity rating (SFR)—A weight associated with how well this signature might perform in the absence of specific knowledge of the target. The signature fidelity rating is configured per signature and indicates how accurately the signature detects the event or condition it describes.
Signature fidelity rating (SFR)—A weight associated with how well this signature might perform in the absence of specific knowledge of the target. The signature fidelity rating is configured per signature and indicates how accurately the signature detects the event or condition it describes.
The signature fidelity rating is calculated by the signature author on a per-signature basis. The signature author defines a baseline confidence ranking for the accuracy of the signature in the absence of qualifying intelligence on the target. It represents the confidence that the detected behavior would produce the intended effect on the target platform if the packet under analysis were allowed to be delivered. For example, a signature that is written with very specific rules (specific regular expression) has a higher signature fidelity rating than a signature that is written with generic rules.

Note ![]() The signature fidelity rating does not indicate how bad the detected event may be.
The signature fidelity rating does not indicate how bad the detected event may be.
•![]() Attack severity rating (ASR)—A weight associated with the severity of a successful exploit of the vulnerability.
Attack severity rating (ASR)—A weight associated with the severity of a successful exploit of the vulnerability.
The attack severity rating is derived from the alert severity parameter (informational, low, medium, or high) of the signature. The attack severity rating is configured per signature and indicates how dangerous the event detected is.

Note ![]() The attack severity rating does not indicate how accurately the event is detected.
The attack severity rating does not indicate how accurately the event is detected.
•![]() Target value rating (TVR)—A weight associated with the perceived value of the target.
Target value rating (TVR)—A weight associated with the perceived value of the target.
The target value rating is a user-configurable value (zero, low, medium, high, or mission critical) that identifies the importance of a network asset (through its IP address). You can develop a security policy that is more stringent for valuable corporate resources and looser for less important resources. For example, you could assign a target value rating to the company web server that is higher than the target value rating you assign to a desktop node. In this example, attacks against the company web server have a higher risk rating than attacks against the desktop node. The target value rating is configured in the Event Action Rules policy.
•![]() Attack relevance rating (ARR)—A weight associated with the relevancy of the targeted operating system.
Attack relevance rating (ARR)—A weight associated with the relevancy of the targeted operating system.
Attack relevance rating is a derived value (relevant, unknown, or not relevant), which is determined at alert time. The relevant operating systems are configured per signature.
•![]() Promiscuous delta (PD)—A weight associated with the promiscuous delta, which can be subtracted from the overall risk rating in promiscuous mode.
Promiscuous delta (PD)—A weight associated with the promiscuous delta, which can be subtracted from the overall risk rating in promiscuous mode.
The promiscuous delta is in the range of 0 to 30 and is configured per signature.

Note ![]() If the trigger packet is not inline, the promiscuous delta is subtracted from the rating.
If the trigger packet is not inline, the promiscuous delta is subtracted from the rating.
•![]() Watch list rating (WLR)—A weight associated with the CSA MC watch list in the range of 0 to 100 (CSA MC only uses the range 0 to 35).
Watch list rating (WLR)—A weight associated with the CSA MC watch list in the range of 0 to 100 (CSA MC only uses the range 0 to 35).
If the attacker for the alert is found on the watch list, the watch list rating for that attacker is added to the rating.
Figure 12-1 illustrates the risk rating formula.
Figure 12-1 Risk Rating Formula
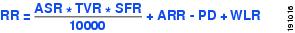
Understanding Threat Rating
Threat rating is risk rating that has been lowered by event actions that have been taken. Nonlogging event actions have a threat rating adjustment. The largest threat rating from all the event actions taken is subtracted from the risk rating.
The event actions have the following threat ratings:
•![]() Deny attacker inline—45
Deny attacker inline—45
•![]() Deny attacker victim pair inline—40
Deny attacker victim pair inline—40
•![]() Deny attacker service pair inline—40
Deny attacker service pair inline—40
•![]() Deny connection inline—35
Deny connection inline—35
•![]() Deny packet inline—35
Deny packet inline—35
•![]() Modify packet inline—35
Modify packet inline—35
•![]() Request block host—20
Request block host—20
•![]() Request block connection—20
Request block connection—20
•![]() Reset TCP connection—20
Reset TCP connection—20
•![]() Request rate limit—20
Request rate limit—20
Understanding Event Action Overrides
You can add an event action override to change the actions associated with an event based on the risk rating of that event. Event action overrides are a way to add event actions globally without having to configure each signature individually. Each event action has an associated risk rating range. If a signature event occurs and the risk rating for that event falls within the range for an event action, that action is added to the event. For example, if you want any event with a risk rating of 85 or more to generate an SNMP trap, you can set the risk rating range for Request SNMP Trap to 85-100. If you do not want to use action overrides, you can disable the entire event action override component.
Understanding Event Action Filters
Event action filters are processed as an ordered list and you can move filters up or down in the list. Filters let the sensor perform certain actions in response to the event without requiring the sensor to perform all actions or remove the entire event. Filters work by removing actions from an event. A filter that removes all actions from an event effectively consumes the event.

Note ![]() When filtering sweep signatures, we recommend that you do not filter the destination addresses. If there are multiple destination addresses, only the last address is used for matching the filter.
When filtering sweep signatures, we recommend that you do not filter the destination addresses. If there are multiple destination addresses, only the last address is used for matching the filter.
Event Action Summarization
Summarization decreases the volume of alerts sent out from the sensor by providing basic aggregation of events into a single alert. Special parameters are specified for each signature and they influence the handling of the alerts. Each signature is created with defaults that reflect a preferred normal behavior. However, you can tune each signature to change this default behavior within the constraints for each engine type.
The nonalert-generating actions (deny, block, TCP reset) go through the filters for each signature event unsummarized. The alert-generating actions are not performed on these summarized alerts; instead the actions are applied to the one summary alert and then put through the filters.
If you select one of the other alert-generating actions and do not have it filtered out, the alert is created even if you do not select Produce Alert. To prevent alerts from being created, you must have all alert-generating actions filtered out.
Summarization and event actions are processed after the Meta engine has processed the component events. This lets the sensor watch for suspicious activity transpiring over a series of events.
Event Action Aggregation
Basic aggregation provides two operating modes. The simple mode involves configuring a threshold number of hits for a signature that must be met before the alert is sent. A more advanced mode is timed-interval counting. In this mode, the sensor tracks the number of hits per second and only sends alerts when that threshold is met. In this example, a hit is a term used to describe an event, which is basically an alert, but it is not sent out of the sensor as an alert until the threshold number of hits has been exceeded.
You can choose from the following summarization options:
•![]() Fire All—Fire All mode fires an alert each time the signature is triggered. If the threshold is set for summarization, alerts are fired for each execution until summarization occurs. After summarization starts only one alert every summary interval fires for each address set. Alerts for other address sets are either all seen or separately summarized. The signature reverts to Fire All mode after a period of no alerts for that signature.
Fire All—Fire All mode fires an alert each time the signature is triggered. If the threshold is set for summarization, alerts are fired for each execution until summarization occurs. After summarization starts only one alert every summary interval fires for each address set. Alerts for other address sets are either all seen or separately summarized. The signature reverts to Fire All mode after a period of no alerts for that signature.
•![]() Summary—Summary mode fires an alert the first time a signature is triggered, and then additional alerts for that signature are summarized for the duration of the summary interval. Only one alert every summary interval should fire for each address set. If the global summary threshold is reached, the signature goes into Global Summarization mode.
Summary—Summary mode fires an alert the first time a signature is triggered, and then additional alerts for that signature are summarized for the duration of the summary interval. Only one alert every summary interval should fire for each address set. If the global summary threshold is reached, the signature goes into Global Summarization mode.
•![]() Global Summarization—Global Summarization mode fires an alert for every summary interval. Signatures can be preconfigured for global summarization.
Global Summarization—Global Summarization mode fires an alert for every summary interval. Signatures can be preconfigured for global summarization.
•![]() Fire Once—Fire Once mode fires an alert for each address set. You can upgrade this mode to Global Summarization mode.
Fire Once—Fire Once mode fires an alert for each address set. You can upgrade this mode to Global Summarization mode.
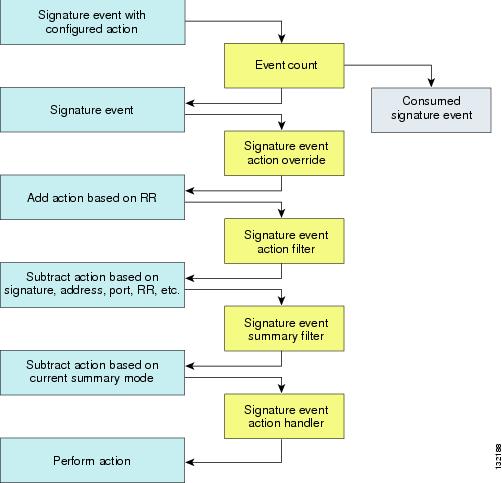
Signature Event Action Processor
The Signature Event Action Processor coordinates the data flow from the signature event in the Alarm Channel to processing through the Signature Event Action Override, the Signature Event Action Filter, and the Signature Event Action Handler. It consists of the following components:
•![]() Alarm Channel
Alarm Channel
The unit that represents the area to communicate signature events from the SensorApp inspection path to signature event handling.
•![]() Signature Event Action Override
Signature Event Action Override
Adds actions based on the risk rating value. Signature Event Action Override applies to all signatures that fall in the range of the configured risk rating threshold. Each Signature Event Action Override is independent and has a separate configuration value for each action type.
•![]() Signature Event Action Filter
Signature Event Action Filter
Subtracts actions based on the signature ID, addresses, and risk rating of the signature event. The input to the Signature Event Action Filter is the signature event with actions possibly added by the Signature Event Action Override.

Note ![]() The Signature Event Action Filter can only subtract actions, it cannot add new actions.
The Signature Event Action Filter can only subtract actions, it cannot add new actions.
The following parameters apply to the Signature Event Action Filter:
–![]() Signature ID
Signature ID
–![]() Subsignature ID
Subsignature ID
–![]() Attacker address
Attacker address
–![]() Attacker port
Attacker port
–![]() Victim address
Victim address
–![]() Victim port
Victim port
–![]() Risk rating threshold range
Risk rating threshold range
–![]() Actions to subtract
Actions to subtract
–![]() Sequence identifier (optional)
Sequence identifier (optional)
–![]() Stop-or-continue bit
Stop-or-continue bit
–![]() Enable action filter line bit
Enable action filter line bit
–![]() Victim OS relevance or OS relevance
Victim OS relevance or OS relevance
•![]() Signature Event Action Handler
Signature Event Action Handler
Performs the requested actions. The output from the Signature Event Action Handler is the actions being performed and possibly an evIdsAlert written to the Event Store.
Figure 12-2 illustrates the logical flow of the signature event through the Signature Event Action Processor and the operations performed on the action for this event. It starts with the signature event with configured action received in the Alarm Channel and flows top to bottom as the signature event passes through the functional components of the Signature Event Action Processor.
Figure 12-2 Signature Event Through Signature Event Action Processor
Event Actions
Cisco IPS has the following event actions:
•![]() Alert and Log Actions:
Alert and Log Actions:
–![]() Product Alert—Writes the event to the Event Store as an alert.
Product Alert—Writes the event to the Event Store as an alert.

Note ![]() The Product Alert action is not automatic when you enable alerts for a signature. To have an alert created in the Event Store, you must select Product Alert. If you add a second action, you must include Product Alert if you want an alert sent to the Event Store. Also, every time you configure the event actions, a new list is created and it replaces the old list. Make sure you include all the event actions you need for each signature.
The Product Alert action is not automatic when you enable alerts for a signature. To have an alert created in the Event Store, you must select Product Alert. If you add a second action, you must include Product Alert if you want an alert sent to the Event Store. Also, every time you configure the event actions, a new list is created and it replaces the old list. Make sure you include all the event actions you need for each signature.

Note ![]() There are other event actions that force a Product Alert. These actions use Product Alert as the vehicle for performing the action. Even if Product Alert is not selected or is filtered, the alert is still produced. The actions are the following: Produce Verbose Alert, Request SNMP Trap, Log Attacker Packets, Log Victim Packets, and Log Pair Packets.
There are other event actions that force a Product Alert. These actions use Product Alert as the vehicle for performing the action. Even if Product Alert is not selected or is filtered, the alert is still produced. The actions are the following: Produce Verbose Alert, Request SNMP Trap, Log Attacker Packets, Log Victim Packets, and Log Pair Packets.

Note ![]() A Produce Alert event action is added for an event when global correlation has increased the risk rating of an event, and has added either the Deny Packet Inline or Deny Attacker Inline event action.
A Produce Alert event action is added for an event when global correlation has increased the risk rating of an event, and has added either the Deny Packet Inline or Deny Attacker Inline event action.
–![]() Produce Verbose Alert—Includes an encoded dump of the offending packet in the alert. This action causes an alert to be written to the Event Store, even if Produce Alert is not selected.
Produce Verbose Alert—Includes an encoded dump of the offending packet in the alert. This action causes an alert to be written to the Event Store, even if Produce Alert is not selected.
–![]() Log Attacker Packets—Starts IP logging on packets that contain the attacker address and sends an alert. This action causes an alert to be written to the Event Store, even if Produce Alert is not selected.
Log Attacker Packets—Starts IP logging on packets that contain the attacker address and sends an alert. This action causes an alert to be written to the Event Store, even if Produce Alert is not selected.
–![]() Log Victim Packets—Starts IP Logging on packets that contain the victim address and sends an alert. This action causes an alert to be written to the Event Store, even if Produce Alert is not selected.
Log Victim Packets—Starts IP Logging on packets that contain the victim address and sends an alert. This action causes an alert to be written to the Event Store, even if Produce Alert is not selected.
–![]() Log Attacker/Victim Pair Packets—Starts IP Logging on packets that contain the attacker/victim address pair. This action causes an alert to be written to the Event Store, even if Produce Alert is not selected.
Log Attacker/Victim Pair Packets—Starts IP Logging on packets that contain the attacker/victim address pair. This action causes an alert to be written to the Event Store, even if Produce Alert is not selected.
–![]() Request SNMP Trap—Sends a request to the Notification Application component of the sensor to perform SNMP notification. This action causes an alert to be written to the Event Store, even if Produce Alert is not selected. You must have SNMP configured on the sensor to implement this action.
Request SNMP Trap—Sends a request to the Notification Application component of the sensor to perform SNMP notification. This action causes an alert to be written to the Event Store, even if Produce Alert is not selected. You must have SNMP configured on the sensor to implement this action.
•![]() Deny Actions:
Deny Actions:
–![]() Deny Packet Inline—(inline mode only) Terminates the packet.
Deny Packet Inline—(inline mode only) Terminates the packet.

Note ![]() You cannot delete the event action override for Deny Packet Inline because it is protected. If you do not want to use that override, disable it.
You cannot delete the event action override for Deny Packet Inline because it is protected. If you do not want to use that override, disable it.
–![]() Deny Connection Inline—(inline mode only) Terminates the current packet and future packets on this TCP flow.
Deny Connection Inline—(inline mode only) Terminates the current packet and future packets on this TCP flow.
–![]() Deny Attacker Victim Pair Inline—(inline mode only) Does not transmit this packet and future packets on the attacker/victim address pair for a specified period of time.
Deny Attacker Victim Pair Inline—(inline mode only) Does not transmit this packet and future packets on the attacker/victim address pair for a specified period of time.

Note ![]() For deny actions, to set the specified period of time and maximum number of denied attackers, choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > General Settings.
For deny actions, to set the specified period of time and maximum number of denied attackers, choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > General Settings.
–![]() Deny Attacker Service Pair Inline—(inline mode only) Does not transmit this packet and future packets on the attacker address victim port pair for a specified period of time.
Deny Attacker Service Pair Inline—(inline mode only) Does not transmit this packet and future packets on the attacker address victim port pair for a specified period of time.
–![]() Deny Attacker Inline—(inline mode only) Terminates the current packet and future packets from this attacker address for a specified period of time.
Deny Attacker Inline—(inline mode only) Terminates the current packet and future packets from this attacker address for a specified period of time.
The sensor maintains a list of attackers being denied by the system. To remove an entry from the denied attacker list, you can view the list of attackers and clear the entire list, or you can wait for the timer to expire. The timer is a sliding timer for each entry. Therefore, if attacker A is being denied, but issues another attack, the timer for attacker A is reset and attacker A remains in the denied attacker list until the timer expires. If the denied attacker list is at capacity and cannot add a new entry, the packet is still denied.

Note ![]() This is the most severe of the deny actions. It denies current and future packets from a single attacker address. To clear all denied attacker entries, choose Configuration > sensor_name > Sensor Monitoring > Time-Based Actions > Denied Attackers > Clear List, which permits the addresses back on the network.
This is the most severe of the deny actions. It denies current and future packets from a single attacker address. To clear all denied attacker entries, choose Configuration > sensor_name > Sensor Monitoring > Time-Based Actions > Denied Attackers > Clear List, which permits the addresses back on the network.
–![]() Modify Packet Inline— Modifies packet data to remove ambiguity about what the end point might do with the packet.
Modify Packet Inline— Modifies packet data to remove ambiguity about what the end point might do with the packet.

Note ![]() Modify Packet Inline is not an option for Add Event Action Filter or Add Event Action Override.
Modify Packet Inline is not an option for Add Event Action Filter or Add Event Action Override.
•![]() Other Actions:
Other Actions:

Note ![]() IPv6 does not support the following event actions: Request Block Host, Request Block Connection, or Request Rate Limit.
IPv6 does not support the following event actions: Request Block Host, Request Block Connection, or Request Rate Limit.
–![]() Request Block Connection—Sends a request to ARC to block this connection. You must have blocking devices configured to implement this action.
Request Block Connection—Sends a request to ARC to block this connection. You must have blocking devices configured to implement this action.
–![]() Request Block Host—Sends a request to ARC to block this attacker host. You must have blocking devices configured to implement this action.
Request Block Host—Sends a request to ARC to block this attacker host. You must have blocking devices configured to implement this action.

Note ![]() For block actions, to set the duration of the block, choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > General Settings.
For block actions, to set the duration of the block, choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > General Settings.
–![]() Request Rate Limit—Sends a rate limit request to ARC to perform rate limiting. You must have rate limiting devices configured to implement this action.
Request Rate Limit—Sends a rate limit request to ARC to perform rate limiting. You must have rate limiting devices configured to implement this action.

Note ![]() Request Rate Limit applies to a select set of signatures.
Request Rate Limit applies to a select set of signatures.
–![]() Reset TCP Connection—Sends TCP resets to hijack and terminate the TCP flow. Reset TCP Connection only works on TCP signatures that analyze a single connection. It does not work for sweeps or floods.
Reset TCP Connection—Sends TCP resets to hijack and terminate the TCP flow. Reset TCP Connection only works on TCP signatures that analyze a single connection. It does not work for sweeps or floods.
Understanding Deny Packet Inline
For signatures that have Deny Packet Inline configured as an action or for an event action override that adds Deny Packet Inline as an action, the following actions may be taken:
•![]() Dropped Packet
Dropped Packet
•![]() Denied Flow
Denied Flow
•![]() TCP One Way Reset Sent
TCP One Way Reset Sent
The deny packet inline action is represented as a dropped packet action in the alert. When a deny packet inline occurs for a TCP connection, it is automatically upgraded to a deny connection inline action and seen as a denied flow in the alert. If the IPS denies just one packet, the TCP continues to try to send that same packet again and again, so the IPS denies the entire connection to ensure it never succeeds with the resends.
When a deny connection inline occurs, the IPS also automatically sends a TCP one-way reset, which shows up as a TCP one-way reset sent in the alert. When the IPS denies the connection, it leaves an open connection on both the client (generally the attacker) and the server (generally the victim). Too many open connections can result in resource problems on the victim. So the IPS sends a TCP reset to the victim to close the connection on the victim side (usually the server), which conserves the resources of the victim. It also prevents a failover that would otherwise allow the connection to fail over to a different network path and reach the victim. The IPS leaves the attacker side open and denies all traffic from it.
TCP Reset Differences Between IPS Appliances and the AIP SSM
The IPS appliance sends TCP reset packets to both the attacker and victim when Reset TCP Connection is selected. The IPS appliance sends a TCP reset packet only to the victim under the following circumstances:
•![]() When a Deny Packet Inline or Deny Connection Inline is selected
When a Deny Packet Inline or Deny Connection Inline is selected
•![]() When TCP-based signatures and Reset TCP Connection have NOT been selected
When TCP-based signatures and Reset TCP Connection have NOT been selected
In the case of the AIP SSM, the TCP reset request is sent to the ASA, and then the ASA sends the TCP reset packets. The ASA sends TCP reset packets to both the attacker and victim when the Reset TCP Connection is selected. When Deny Packet Inline or Deny Connection Inline is selected, the ASA sends the TCP reset packet to either the attacker or victim depending on the configuration of the signature. Signatures configured to swap the attacker and victim when reporting the alert can cause the ASA to send the TCP reset packet to the attacker.
For More Information
•![]() For the procedure for configuring the general settings, see Configuring General Settings.
For the procedure for configuring the general settings, see Configuring General Settings.
•![]() For the procedure for configuring SNMP, see Chapter 16 "Configuring SNMP."
For the procedure for configuring SNMP, see Chapter 16 "Configuring SNMP."
•![]() For the procedure for configuring denied attackers, see Configuring and Monitoring Denied Attackers.
For the procedure for configuring denied attackers, see Configuring and Monitoring Denied Attackers.
Configuring Event Action Rules Policies
This section describes how to create event action rules policies, and contains the following topics:
•![]() Event Action rules Pane Field Definitions
Event Action rules Pane Field Definitions
•![]() Add and Clone Policy Dialog Boxes Field Definitions
Add and Clone Policy Dialog Boxes Field Definitions
•![]() Adding, Cloning, and Deleting Event Action Rules Policies
Adding, Cloning, and Deleting Event Action Rules Policies
Event Action Rules Pane

Note ![]() You must be administrator or operator to add, clone, or delete event action rules policies.
You must be administrator or operator to add, clone, or delete event action rules policies.

In the Event Action Rules pane, you can add, clone, or delete an event action rules policy. The default event action rules policy is rules0. When you add a policy, a control transaction is sent to the sensor to create the policy instance. If the response is successful, the new policy instance is added under Event Action Rules. If the control transaction fails, for example because of resource limitations, an error message appears.
If your platform does not support virtual policies, this means you can only have one instance for each component and you cannot create new ones or delete the existing one. In this case, the Add, Clone, and Delete buttons are disabled.
Event Action rules Pane Field Definitions
The following fields are found in the Event Action Rules pane:
•![]() Policy Name—Identifies the name of this event action rules policy.
Policy Name—Identifies the name of this event action rules policy.
•![]() Assigned Virtual Sensor—Identifies the virtual sensor for which this event action rules policy is assigned.
Assigned Virtual Sensor—Identifies the virtual sensor for which this event action rules policy is assigned.
Add and Clone Policy Dialog Boxes Field Definitions
The following field is found in the Add and Clone Policy dialog boxes:
•![]() Policy Name—Lets you create a unique name for the new policy.
Policy Name—Lets you create a unique name for the new policy.
Adding, Cloning, and Deleting Event Action Rules Policies
To add, clone, or delete an event action rules policy, follow these steps:
Step 1 ![]() Log in to IME using an account with administrator or operator privileges.
Log in to IME using an account with administrator or operator privileges.
Step 2 ![]() Choose Configuration > sensor_name > Policies > Event Action Rules, and then click Add.
Choose Configuration > sensor_name > Policies > Event Action Rules, and then click Add.
Step 3 ![]() In the Policy Name field, enter a name for the event action rules policy.
In the Policy Name field, enter a name for the event action rules policy.

Tip ![]() To discard your changes and close the dialog box, click Cancel.
To discard your changes and close the dialog box, click Cancel.
Step 4 ![]() Click OK.
Click OK.
The event action rules policy appears in the list in the Event Action Rules pane.
Step 5 ![]() To clone an existing event action rules policy, select it in the list, and then click Clone.
To clone an existing event action rules policy, select it in the list, and then click Clone.
The Clone Policy dialog box appears with "_copy" appended to the existing event action rules policy name.
Step 6 ![]() In the Policy Name field, enter a unique name.
In the Policy Name field, enter a unique name.

Tip ![]() To discard your changes and close the dialog box, click Cancel.
To discard your changes and close the dialog box, click Cancel.
Step 7 ![]() Click OK.
Click OK.
The cloned event action rules policy appears in the list in the Event Action Rules pane.
Step 8 ![]() To remove an event action rules policy, select it, and then click Delete.
To remove an event action rules policy, select it, and then click Delete.
The Delete Policy dialog box asks if you are sure you want to delete this policy permanently.

Step 9 ![]() Click Yes.
Click Yes.
The event action rules policy no longer appears in the list in the Event Action Rules pane.
Understanding the rules0 Pane
The Event Action Rules (rules0) pane contains seven tabs on which you can configure event action overrides, event action filters, target value ratings, OS identifications, event variables, risk categories, and general settings for the event action rules policies that you added in the Configuration > sensor_name > Policies > Event Action Rules pane.
You can also configure event action rules in the lower half of the Configuration > sensor_name > Policies > IPS Policies pane.
Configuring Event Action Overrides
This section describes how to configure event action overrides, and contains the following topics:
•![]() Event Action Overrides Tab Field Definitions
Event Action Overrides Tab Field Definitions
•![]() Add and Edit Event Action Override Dialog Boxes Field Definitions
Add and Edit Event Action Override Dialog Boxes Field Definitions
•![]() Adding, Editing, Deleting, Enabling, and Disabling Event Action Overrides
Adding, Editing, Deleting, Enabling, and Disabling Event Action Overrides
Event Action Overrides Tab

Note ![]() You must be administrator or operator to add or edit event action overrides.
You must be administrator or operator to add or edit event action overrides.
On the Event Action Overrides tab, you can add an event action override to change the actions associated with an event based on specific details about that event.
Event Action Overrides Tab Field Definitions
The following fields are found on the Event Action Overrides tab:
•![]() Use Event Action Overrides—If checked, lets you use any event action override that is enabled.
Use Event Action Overrides—If checked, lets you use any event action override that is enabled.
•![]() Risk Rating—Indicates the risk rating level that should be used to trigger this event action override.
Risk Rating—Indicates the risk rating level that should be used to trigger this event action override.
If an event occurs with a risk rating that matches this level, the event action is added to this event.
•![]() Actions to Add—Specifies the event action that will be added to an event if the conditions of this event action override are satisfied.
Actions to Add—Specifies the event action that will be added to an event if the conditions of this event action override are satisfied.
•![]() Enabled—Indicates whether or not the override is enabled.
Enabled—Indicates whether or not the override is enabled.
Add and Edit Event Action Override Dialog Boxes Field Definitions
The following fields are found in the Add and Edit Event Action Override dialog boxes:
•![]() Risk Rating—Indicates the risk rating range, either low, medium, or high risk, that should be used to trigger this event action override.
Risk Rating—Indicates the risk rating range, either low, medium, or high risk, that should be used to trigger this event action override.
If an event occurs with an risk rating that corresponds to the risk you configure, the event action is added to this event.
•![]() Available Actions to Add—Specifies the event action that will be added to an event if the conditions of this event action override are satisfied.
Available Actions to Add—Specifies the event action that will be added to an event if the conditions of this event action override are satisfied.
•![]() Enabled—Check the check box to enable the action when the event action override is triggered.
Enabled—Check the check box to enable the action when the event action override is triggered.
Adding, Editing, Deleting, Enabling, and Disabling Event Action Overrides
To add, edit, delete, enable, and disable event action overrides, follow these steps:
Step 1 ![]() Log in to IME using an account with administrator or operator privileges.
Log in to IME using an account with administrator or operator privileges.
Step 2 ![]() Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > Event Action Overrides.
Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > Event Action Overrides.
Step 3 ![]() To create a event action override, click Add.
To create a event action override, click Add.
Step 4 ![]() From the Risk Rating drop-down menu, assign a risk rating range to this network asset.
From the Risk Rating drop-down menu, assign a risk rating range to this network asset.
Step 5 ![]() From the Available Actions to Add list, check the event actions to which this event action override.
From the Available Actions to Add list, check the event actions to which this event action override.
Step 6 ![]() Check the Enabled check boxes for the actions you want to enable in the override.
Check the Enabled check boxes for the actions you want to enable in the override.

Tip ![]() To discard your changes and close the Add Event Action Override dialog box, click Cancel.
To discard your changes and close the Add Event Action Override dialog box, click Cancel.
Step 7 ![]() Click OK.
Click OK.
The new event action override now appears in the list on the Event Action Overrides tab.
Step 8 ![]() Check the Use Event Action Overrides check box.
Check the Use Event Action Overrides check box.

Note ![]() You must check the Use Event Action Overrides check box on the Event Action Overrides tab or none of the event action overrides will be enabled regardless of the value you set.
You must check the Use Event Action Overrides check box on the Event Action Overrides tab or none of the event action overrides will be enabled regardless of the value you set.
Step 9 ![]() To edit an existing event action override, select it in the list, and then click Edit.
To edit an existing event action override, select it in the list, and then click Edit.
Make any changes needed.

Tip ![]() To discard your changes and close the Edit Event Action Override dialog box, click Cancel.
To discard your changes and close the Edit Event Action Override dialog box, click Cancel.
Step 10 ![]() Click OK.
Click OK.
The edited event action override now appears in the list on the Event Action Overrides tab.
Step 11 ![]() Check the Use Event Action Overrides check box.
Check the Use Event Action Overrides check box.

Note ![]() You must check the Use Event Action Overrides check box on the Event Action Overrides tab or none of the event action overrides will be enabled regardless of the value you set.
You must check the Use Event Action Overrides check box on the Event Action Overrides tab or none of the event action overrides will be enabled regardless of the value you set.
Step 12 ![]() To delete an event action override, select it in the list, and then click Delete.
To delete an event action override, select it in the list, and then click Delete.
The event action override no longer appears in the list on the Event Action Overrides tab.

Note ![]() You cannot delete the event action override for Deny Packet Inline because it is protected. If you do not want to use that override, disable it.
You cannot delete the event action override for Deny Packet Inline because it is protected. If you do not want to use that override, disable it.
Step 13 ![]() To enable or disable an event action override, select it in the list, and then click Edit.
To enable or disable an event action override, select it in the list, and then click Edit.
Step 14 ![]() To disable an event action override, clear the Enabled check boxes for any event actions that you have assigned to that event action override. To enable an event action override, check any Enabled check boxes for any event actions that you have assigned to that event action override.
To disable an event action override, clear the Enabled check boxes for any event actions that you have assigned to that event action override. To enable an event action override, check any Enabled check boxes for any event actions that you have assigned to that event action override.

Tip ![]() To discard your changes, click Reset.
To discard your changes, click Reset.
Step 15 ![]() Click Apply to apply your changes and save the revised configuration.
Click Apply to apply your changes and save the revised configuration.
For More Information
For detailed information on event actions, see Event Actions.
Configuring Event Action Filters
This section describes how to configure event action filters, and contains the following topics:
•![]() Event Action Filters Tab Field Definitions
Event Action Filters Tab Field Definitions
•![]() Add and Edit Event Action Filter Dialog Boxes Field Definitions
Add and Edit Event Action Filter Dialog Boxes Field Definitions
•![]() Adding, Editing, Deleting, Enabling, Disabling, and Moving Event Action Filters
Adding, Editing, Deleting, Enabling, Disabling, and Moving Event Action Filters
Event Action Filters Tab

Note ![]() You must be administrator or operator to add, edit, enable, disable, or delete event action filters.
You must be administrator or operator to add, edit, enable, disable, or delete event action filters.
You can configure event action filters to remove specific actions from an event or to discard an entire event and prevent further processing by the sensor. You can use the variables that you defined on the Event Variables pane to group addresses for your filters.


Note ![]() You must preface the variable with a dollar sign ($) to indicate that you are using a variable rather than a string. Otherwise, you receive the
You must preface the variable with a dollar sign ($) to indicate that you are using a variable rather than a string. Otherwise, you receive the Bad source and destination error.
Event Action Filters Tab Field Definitions
The following fields are found on the Event Action Filters tab:
•![]() Name—Lets you name the filter you are adding. You need to name your filters so that you can move them around in the list and move them to the inactive list if needed.
Name—Lets you name the filter you are adding. You need to name your filters so that you can move them around in the list and move them to the inactive list if needed.
•![]() Enabled—Indicates whether or not this filter is enabled.
Enabled—Indicates whether or not this filter is enabled.
•![]() Sig ID—Identifies the unique numerical value assigned to this signature. This value lets the sensor identify a particular signature. You can also enter a range of signatures.
Sig ID—Identifies the unique numerical value assigned to this signature. This value lets the sensor identify a particular signature. You can also enter a range of signatures.
•![]() SubSig ID—Identifies the unique numerical value assigned to this subsignature. The subSig ID identifies a more granular version of a broad signature. You can also enter a range of subSig IDs.
SubSig ID—Identifies the unique numerical value assigned to this subsignature. The subSig ID identifies a more granular version of a broad signature. You can also enter a range of subSig IDs.
•![]() Attacker (IPv4/IPv6/port)—Identifies the IP address and/or port of the host that sent the offending packet. You can also enter a range of addresses.
Attacker (IPv4/IPv6/port)—Identifies the IP address and/or port of the host that sent the offending packet. You can also enter a range of addresses.
•![]() Victim (IPv4/IPv6/port)—Identifies the IP address and/or port used by the attacker host. This is the port from where the offending packet originated. You can also enter a range of ports.
Victim (IPv4/IPv6/port)—Identifies the IP address and/or port used by the attacker host. This is the port from where the offending packet originated. You can also enter a range of ports.
•![]() Risk Rating—Indicates the risk rating range between 0 and 100 that should be used to trigger this event action filter. If an event occurs with a risk rating that falls within the minimum-maximum range you configure here, the event is processed against the rules of this event filter.
Risk Rating—Indicates the risk rating range between 0 and 100 that should be used to trigger this event action filter. If an event occurs with a risk rating that falls within the minimum-maximum range you configure here, the event is processed against the rules of this event filter.
•![]() Actions to Subtract—Indicates the actions that should be removed from the event, should the conditions of the event meet the criteria of the event action filter.
Actions to Subtract—Indicates the actions that should be removed from the event, should the conditions of the event meet the criteria of the event action filter.
Add and Edit Event Action Filter Dialog Boxes Field Definitions
The following fields are found in the Add and Edit Event Action Filters dialog boxes:
•![]() Name—Lets you name the filter you are adding. You need to name your filters so that you can move them around in the list and move them to the inactive list if needed.
Name—Lets you name the filter you are adding. You need to name your filters so that you can move them around in the list and move them to the inactive list if needed.
•![]() Enabled—Lets you enable this filter.
Enabled—Lets you enable this filter.
•![]() Signature ID—Identifies the unique numerical value assigned to this signature. This value lets the sensor identify a particular signature. You can also enter a range of signatures.
Signature ID—Identifies the unique numerical value assigned to this signature. This value lets the sensor identify a particular signature. You can also enter a range of signatures.
•![]() Subsignature ID—Identifies the unique numerical value assigned to this subsignature. The subsignature ID identifies a more granular version of a broad signature. You can also enter a range of subsignature IDs.
Subsignature ID—Identifies the unique numerical value assigned to this subsignature. The subsignature ID identifies a more granular version of a broad signature. You can also enter a range of subsignature IDs.
•![]() Attacker IPv4 Address—Identifies the IP address of the host that sent the offending packet. You can also enter a range of addresses.
Attacker IPv4 Address—Identifies the IP address of the host that sent the offending packet. You can also enter a range of addresses.
•![]() Attacker IPv6 Address—Identifies the range set of attacker IPv6 addresses of the host that sent the offending packet in the following format:
Attacker IPv6 Address—Identifies the range set of attacker IPv6 addresses of the host that sent the offending packet in the following format:
<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>[,<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>]
For example:
2001:0db8:1234:1234:1234:1234:1234:1234,2001:0db8:1234:1234:1234:1234:1234:8888. The second IPv6 address in the range must be greater than or equal to the first IPv6 address.

Note ![]() IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
•![]() Attacker Port—Identifies the port used by the attacker host. This is the port from where the offending packet originated. You can also enter a range of ports.
Attacker Port—Identifies the port used by the attacker host. This is the port from where the offending packet originated. You can also enter a range of ports.
•![]() VictimIPv4 Address—Identifies the IP address of the host being attacked (the recipient of the offending packet). You can also enter a range of addresses.
VictimIPv4 Address—Identifies the IP address of the host being attacked (the recipient of the offending packet). You can also enter a range of addresses.
•![]() VictimIPv6 Address—Identifies the range set of victim IPv6 addresses of the host that is the being attacked (the recipient of the offending packet) in the following format:
VictimIPv6 Address—Identifies the range set of victim IPv6 addresses of the host that is the being attacked (the recipient of the offending packet) in the following format:
<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>[,<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>]
For example:
2001:0db8:1234:1234:1234:1234:1234:1234,2001:0db8:1234:1234:1234:1234:1234:8888. The second IPv6 address in the range must be greater than or equal to the first IPv6 address.

Note ![]() IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
•![]() Victim Port—Identifies the port through which the offending packet was received. You can also enter a range of ports.
Victim Port—Identifies the port through which the offending packet was received. You can also enter a range of ports.
•![]() Risk Rating—Indicates the risk rating range between 0 and 100 that should be used to trigger this event action filter. If an event occurs with a risk rating that falls within the minimum-maximum range you configure here, the event is processed against the rules of this event filter.
Risk Rating—Indicates the risk rating range between 0 and 100 that should be used to trigger this event action filter. If an event occurs with a risk rating that falls within the minimum-maximum range you configure here, the event is processed against the rules of this event filter.
•![]() Actions to Subtract—Opens the Edit Actions dialog box and lets you choose the actions that should be removed from the event, should the conditions of the event meet the criteria of the event action filter.
Actions to Subtract—Opens the Edit Actions dialog box and lets you choose the actions that should be removed from the event, should the conditions of the event meet the criteria of the event action filter.
•![]() Active—Lets you add the filter to the filter list so that it takes effect on filtering events.
Active—Lets you add the filter to the filter list so that it takes effect on filtering events.
•![]() OS Relevance—Lets you filter out events where the attack is not relevant to the victim OS.
OS Relevance—Lets you filter out events where the attack is not relevant to the victim OS.
•![]() Deny Percentage—Determines the percentage of packets to deny for deny attacker features. The valid range is 0 to 100. The default is 100 percent.
Deny Percentage—Determines the percentage of packets to deny for deny attacker features. The valid range is 0 to 100. The default is 100 percent.
•![]() Stop on Match—Determines whether or not this event will be processed against remaining filters in the event action filters list.
Stop on Match—Determines whether or not this event will be processed against remaining filters in the event action filters list.
If set to No, the remaining filters are processed for a match until a Stop flag is encountered.
If set to Yes, no further processing is done. The actions specified by this filter are removed and the remaining actions are performed.
•![]() Comments—Displays the user comments associated with this filter.
Comments—Displays the user comments associated with this filter.
Adding, Editing, Deleting, Enabling, Disabling, and Moving Event Action Filters

Note ![]() Global Correlation Inspection and the Reputation Filtering deny features do not support IPv6 addresses. For global correlation inspection, the sensor does not receive or process reputation data for IPv6 addresses. The risk rating for IPv6 addresses is not modified for global correlation inspection. Similarly, network participation does not include event data for attacks from IPv6 addresses. And finally, IPv6 addresses do not appear in the deny list.
Global Correlation Inspection and the Reputation Filtering deny features do not support IPv6 addresses. For global correlation inspection, the sensor does not receive or process reputation data for IPv6 addresses. The risk rating for IPv6 addresses is not modified for global correlation inspection. Similarly, network participation does not include event data for attacks from IPv6 addresses. And finally, IPv6 addresses do not appear in the deny list.

Note ![]() Rate limiting and blocking are not supported for IPv6 traffic. If a signature is configured with a block or rate limit event action and is triggered by IPv6 traffic, an alert is generated but the action is not carried out.
Rate limiting and blocking are not supported for IPv6 traffic. If a signature is configured with a block or rate limit event action and is triggered by IPv6 traffic, an alert is generated but the action is not carried out.
To add, edit, delete, enable, disable, and move event action filters, follow these steps:
Step 1 ![]() Log in to IME using an account with administrator or operator privileges.
Log in to IME using an account with administrator or operator privileges.
Step 2 ![]() Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > Event Action Filters, and then click Add.
Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > Event Action Filters, and then click Add.
Step 3 ![]() In the Name field, enter a name for the event action filter.
In the Name field, enter a name for the event action filter.
A default name is supplied, but you can change it to a more meaningful name.
Step 4 ![]() In the Enabled field, click the Yes radio button to enable the filter.
In the Enabled field, click the Yes radio button to enable the filter.
Step 5 ![]() In the Signature ID field, enter the signature IDs of all signatures to which this filter should be applied.
In the Signature ID field, enter the signature IDs of all signatures to which this filter should be applied.
You can use a list (2001, 2004), or a range (2001-2004), or one of the SIG variables you defined on the Event Variables tab. Preface the variable with $.
Step 6 ![]() In the SubSignature ID field, enter the subsignature IDs of the subsignatures to which this filter should be applied.
In the SubSignature ID field, enter the subsignature IDs of the subsignatures to which this filter should be applied.
Step 7 ![]() In the Attacker IPv4 Address field, enter the IP address of the source host.
In the Attacker IPv4 Address field, enter the IP address of the source host.
You can use a variable you defined on the Event Variables tab. Preface the variable with $. You can also enter a range of addresses (for example, 0.0.0.0-255.255.255.255).
Step 8 ![]() In the Attacker IPv6 Address field, enter the range set of attacker IPv6 addresses of the source host in the following format:
In the Attacker IPv6 Address field, enter the range set of attacker IPv6 addresses of the source host in the following format:
<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>[,<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>].
The second IPv6 address in the range must be greater than or equal to the first IPv6 address.

Note ![]() IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
You can also use a variable you defined on the Event Variables tab. Preface the variable with $.
Step 9 ![]() In the Attacker Port field, enter the port number used by the attacker to send the offending packet.
In the Attacker Port field, enter the port number used by the attacker to send the offending packet.
Step 10 ![]() In the Victim IPv4 Address field, enter the IP address of the recipient host in the following format:
In the Victim IPv4 Address field, enter the IP address of the recipient host in the following format:
You can use one of the variables if you defined them on the Event Variables tab. Preface the variable with $. You can also enter a range of addresses (for example, 0.0.0.0-255.255.255.255).
Step 11 ![]() In the Victim IPv6 Address field, enter the range set of IPv6 address of the recipient host in the following format.
In the Victim IPv6 Address field, enter the range set of IPv6 address of the recipient host in the following format.
<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>[,<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>].
The second IPv6 address in the range must be greater than or equal to the first IPv6 address.

Note ![]() IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
You can use a variable you defined on the Event Variables tab. Preface the variable with $.
Step 12 ![]() In the Victim Port field, enter the port number used by the victim host to receive the offending packet.
In the Victim Port field, enter the port number used by the victim host to receive the offending packet.
Step 13 ![]() In the Risk Rating field, enter a risk rating range for this filter.
In the Risk Rating field, enter a risk rating range for this filter.
If the risk rating for an event falls within the range you specify, the event is processed against the criteria of this filter.
Step 14 ![]() In the Actions to Subtract field, click the Note icon to open the Edit Actions dialog box.
In the Actions to Subtract field, click the Note icon to open the Edit Actions dialog box.
Check the check boxes of the actions you want this filter to remove from the event.

Note ![]() IPv6 does not support the following event actions: Request Block Host, Request Block Connection, or Request Rate Limit.
IPv6 does not support the following event actions: Request Block Host, Request Block Connection, or Request Rate Limit.

Tip ![]() To choose more than one event action in the list, hold down the Ctrl key.
To choose more than one event action in the list, hold down the Ctrl key.
Step 15 ![]() In the Active field, click the Yes radio button to add this filter to the list so that it takes effect on filtering events.
In the Active field, click the Yes radio button to add this filter to the list so that it takes effect on filtering events.
Step 16 ![]() In the OS Relevance drop-down list, choose whether you want to know if the alert is relevant to the OS that has been identified for the victim.
In the OS Relevance drop-down list, choose whether you want to know if the alert is relevant to the OS that has been identified for the victim.
Step 17 ![]() In the Deny Percentage field, enter the percentage of packets to deny for deny attacker features.
In the Deny Percentage field, enter the percentage of packets to deny for deny attacker features.
The default is 100 percent.
Step 18 ![]() In the Stop on Match field, click one of the following radio buttons:
In the Stop on Match field, click one of the following radio buttons:
a. ![]() Yes—If you want the Event Action Filters component to stop processing after the actions of this particular filter have been removed.
Yes—If you want the Event Action Filters component to stop processing after the actions of this particular filter have been removed.
Any remaining filters will not be processed; therefore, no additional actions can be removed from the event.
b. ![]() No—If you want to continue processing additional filters.
No—If you want to continue processing additional filters.
Step 19 ![]() In the Comments field, enter any comments that you want to store with this filter, such as the purpose of this filter or why you have configured this filter in a particular way.
In the Comments field, enter any comments that you want to store with this filter, such as the purpose of this filter or why you have configured this filter in a particular way.

Tip ![]() To discard your changes and close the Add Event Action Filter dialog box, click Cancel.
To discard your changes and close the Add Event Action Filter dialog box, click Cancel.
Step 20 ![]() Click OK.
Click OK.
The new event action filter now appears in the list on the Event Action Filters tab.
Step 21 ![]() To edit an existing event action filter, select it in the list, and then click Edit.
To edit an existing event action filter, select it in the list, and then click Edit.
Step 22 ![]() Make any changes needed.
Make any changes needed.

Tip ![]() To discard your changes and close the Edit Event Action Filter dialog box, click Cancel.
To discard your changes and close the Edit Event Action Filter dialog box, click Cancel.
Step 23 ![]() Click OK. The edited event action filter now appears in the list on the Event Action Filters tab.
Click OK. The edited event action filter now appears in the list on the Event Action Filters tab.
Step 24 ![]() To delete an event action filter, select it in the list, and then click Delete. The event action filter no longer appears in the list on the Event Action Filters tab.
To delete an event action filter, select it in the list, and then click Delete. The event action filter no longer appears in the list on the Event Action Filters tab.
Step 25 ![]() To move an event action filter up or down in the list, select it, and then click the Move Up or Move Down arrow icons.
To move an event action filter up or down in the list, select it, and then click the Move Up or Move Down arrow icons.

Tip ![]() To discard your changes, click Reset.
To discard your changes, click Reset.
Step 26 ![]() Click Apply to apply your changes and save the revised configuration.
Click Apply to apply your changes and save the revised configuration.
Configuring IPv4 Target Value Rating
This section describes how to configure IPv4 target value ratings, and contains the following topics:
•![]() IPv4 Target Value Rating Tab Field Definitions
IPv4 Target Value Rating Tab Field Definitions
•![]() Add and Edit IPv4 Target Value Rating Dialog Boxes Field Definitions
Add and Edit IPv4 Target Value Rating Dialog Boxes Field Definitions
•![]() Adding, Editing, and Deleting IPv4 Target Value Ratings
Adding, Editing, and Deleting IPv4 Target Value Ratings
IPv4 Target Value Rating Tab

Note ![]() You must be administrator or operator to add, edit, or delete target value ratings.
You must be administrator or operator to add, edit, or delete target value ratings.
You can assign a target value rating to your network assets. The target value rating is one of the factors used to calculate the risk rating value for each alert. You can assign different target value ratings to different targets. Events with a higher risk rating trigger more severe signature event actions.
IPv4 Target Value Rating Tab Field Definitions
The following fields are found on the IPv4 Target Value Rating tab:
•![]() Target Value Rating (TVR)—Identifies the value assigned to this network asset. The value can be High, Low, Medium, Mission Critical, or No Value.
Target Value Rating (TVR)—Identifies the value assigned to this network asset. The value can be High, Low, Medium, Mission Critical, or No Value.
•![]() Target IP Address—Identifies the IP address of the network asset you want to prioritize with a target value rating.
Target IP Address—Identifies the IP address of the network asset you want to prioritize with a target value rating.
Add and Edit IPv4 Target Value Rating Dialog Boxes Field Definitions
The following fields are found in the Add and Edit IPv4 Target Value Rating dialog boxes:
•![]() Target Value Rating (TVR)—Lets you assign a value to this network asset. The value can be High, Low, Medium, Mission Critical, or No Value.
Target Value Rating (TVR)—Lets you assign a value to this network asset. The value can be High, Low, Medium, Mission Critical, or No Value.
•![]() Target IPv4 Address(es)—Identifies the IP address of the network asset you want to prioritize with a target value rating.
Target IPv4 Address(es)—Identifies the IP address of the network asset you want to prioritize with a target value rating.
Adding, Editing, and Deleting IPv4 Target Value Ratings
To add, edit, and delete the IPv4 target value rating for network assets, follow these steps:
Step 1 ![]() Log in to IME using an account with administrator or operator privileges.
Log in to IME using an account with administrator or operator privileges.
Step 2 ![]() Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > IPv4 Target Value Rating, and then click Add.
Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > IPv4 Target Value Rating, and then click Add.
Step 3 ![]() To assign a target value rating to a new group of assets, follow these steps:
To assign a target value rating to a new group of assets, follow these steps:
a. ![]() From the Target Value Rating (TVR) drop-down list, choose a rating.
From the Target Value Rating (TVR) drop-down list, choose a rating.
The values are High, Low, Medium, Mission Critical, or No Value.
b. ![]() In the Target IPv4 Address(es) field, enter the IP address of the network asset.
In the Target IPv4 Address(es) field, enter the IP address of the network asset.
To enter a range of IP addresses, enter the lowest address followed by a hyphen and then the highest address in the range. For example: 10.10.2.1-10.10.2.30.

Tip ![]() To discard your changes and close the Add IPv4 Target Value Rating dialog box, click Cancel.
To discard your changes and close the Add IPv4 Target Value Rating dialog box, click Cancel.
Step 4 ![]() Click OK. The new target value rating for the new asset appears in the list on the IPv4 Target Value Rating tab.
Click OK. The new target value rating for the new asset appears in the list on the IPv4 Target Value Rating tab.
Step 5 ![]() To edit an existing target value rating, select it in the list, and then click Edit.
To edit an existing target value rating, select it in the list, and then click Edit.
Step 6 ![]() Make any changes needed.
Make any changes needed.

Tip ![]() To discard your changes and close the Edit IPv4 Target Value Rating dialog box, click Cancel.
To discard your changes and close the Edit IPv4 Target Value Rating dialog box, click Cancel.
Step 7 ![]() Click OK. The edited network asset now appears in the list on the IPv4 Target Value Rating tab.
Click OK. The edited network asset now appears in the list on the IPv4 Target Value Rating tab.
Step 8 ![]() To delete a network asset, select it in the list, and then click Delete. The network asset no longer appears in the list on the Ipv4 Target Value Rating tab.
To delete a network asset, select it in the list, and then click Delete. The network asset no longer appears in the list on the Ipv4 Target Value Rating tab.

Tip ![]() To discard your changes, click Reset.
To discard your changes, click Reset.
Step 9 ![]() Click Apply to apply your changes and save the revised configuration.
Click Apply to apply your changes and save the revised configuration.
Configuring IPv6 Target Value Rating
This section describes how to configure IPv6 target value ratings, and contains the following topics:
•![]() IPv6 Target Value Rating Tab Field Definitions
IPv6 Target Value Rating Tab Field Definitions
•![]() Add and Edit IPv6 Target Value Rating Dialog Boxes Field Definitions
Add and Edit IPv6 Target Value Rating Dialog Boxes Field Definitions
•![]() Adding, Editing, and Deleting IPv6 Target Value Ratings
Adding, Editing, and Deleting IPv6 Target Value Ratings
IPv6 Target Value Rating Tab

Note ![]() You must be administrator or operator to add, edit, or delete target value ratings.
You must be administrator or operator to add, edit, or delete target value ratings.
You can assign a target value rating to your network assets. The target value rating is one of the factors used to calculate the risk rating value for each alert. You can assign different target value ratings to different targets. Events with a higher risk rating trigger more severe signature event actions.
IPv6 Target Value Rating Tab Field Definitions
The following fields are found on the IPv6 Target Value Rating tab:
•![]() Target Value Rating (TVR)—Identifies the value assigned to this network asset. The value can be High, Low, Medium, Mission Critical, or No Value.
Target Value Rating (TVR)—Identifies the value assigned to this network asset. The value can be High, Low, Medium, Mission Critical, or No Value.
•![]() Target IP Address—Identifies the IP address of the network asset you want to prioritize with a target value rating.
Target IP Address—Identifies the IP address of the network asset you want to prioritize with a target value rating.
Add and Edit IPv6 Target Value Rating Dialog Boxes Field Definitions
The following fields are found in the Add and Edit IPv6 Target Value Rating dialog boxes:
•![]() Target Value Rating (TVR)—Lets you assign a value to this network asset. The value can be High, Low, Medium, Mission Critical, or No Value.
Target Value Rating (TVR)—Lets you assign a value to this network asset. The value can be High, Low, Medium, Mission Critical, or No Value.
•![]() Target IPv6 Address(es)—Identifies the IPv6 address of the network asset you want to prioritize with a target value rating in the following format:
Target IPv6 Address(es)—Identifies the IPv6 address of the network asset you want to prioritize with a target value rating in the following format:
<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>[,<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>]
For example: 2001:0db8:1234:1234:1234:1234:1234:1234,2001:0db8:1234:1234:1234:1234:1234:8888. The second IPv6 address in the range must be greater than or equal to the first IPv6 address.

Note ![]() IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
Adding, Editing, and Deleting IPv6 Target Value Ratings

Note ![]() Global Correlation Inspection and the Reputation Filtering deny features do not support IPv6 addresses. For global correlation inspection, the sensor does not receive or process reputation data for IPv6 addresses. The risk rating for IPv6 addresses is not modified for global correlation inspection. Similarly, network participation does not include event data for attacks from IPv6 addresses. And finally, IPv6 addresses do not appear in the deny list.
Global Correlation Inspection and the Reputation Filtering deny features do not support IPv6 addresses. For global correlation inspection, the sensor does not receive or process reputation data for IPv6 addresses. The risk rating for IPv6 addresses is not modified for global correlation inspection. Similarly, network participation does not include event data for attacks from IPv6 addresses. And finally, IPv6 addresses do not appear in the deny list.

Note ![]() Rate limiting and blocking are not supported for IPv6 traffic. If a signature is configured with a block or rate limit event action and is triggered by IPv6 traffic, an alert is generated but the action is not carried out.
Rate limiting and blocking are not supported for IPv6 traffic. If a signature is configured with a block or rate limit event action and is triggered by IPv6 traffic, an alert is generated but the action is not carried out.
To add, edit, and delete the IPv6 target value rating for network assets, follow these steps:
Step 1 ![]() Log in to IME using an account with administrator or operator privileges.
Log in to IME using an account with administrator or operator privileges.
Step 2 ![]() Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > IPv6 Target Value Rating, and then click Add.
Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > IPv6 Target Value Rating, and then click Add.
Step 3 ![]() To assign a target value rating to a new group of assets, follow these steps:
To assign a target value rating to a new group of assets, follow these steps:
a. ![]() From the Target Value Rating (TVR) drop-down list, choose a rating. The values are High, Low, Medium, Mission Critical, or No Value.
From the Target Value Rating (TVR) drop-down list, choose a rating. The values are High, Low, Medium, Mission Critical, or No Value.
b. ![]() In the Target IPv6 Address(es) field, enter the IP address of the network asset.
In the Target IPv6 Address(es) field, enter the IP address of the network asset.
<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>[,<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>].
You can also use a variable you defined on the Event Variables tab. Preface the variable with $. The second IPv6 address in the range must be greater than or equal to the first IPv6 address.

Note ![]() IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.

Tip ![]() To discard your changes and close the Add IPv6 Target Value Rating dialog box, click Cancel.
To discard your changes and close the Add IPv6 Target Value Rating dialog box, click Cancel.
Step 4 ![]() Click OK. The new target value rating for the new asset appears in the list on the IPv6 Target Value Rating tab.
Click OK. The new target value rating for the new asset appears in the list on the IPv6 Target Value Rating tab.
Step 5 ![]() To edit an existing target value rating, select it in the list, and then click Edit.
To edit an existing target value rating, select it in the list, and then click Edit.
Step 6 ![]() Make any changes needed.
Make any changes needed.

Tip ![]() To discard your changes and close the Edit IPv6 Target Value Rating dialog box, click Cancel.
To discard your changes and close the Edit IPv6 Target Value Rating dialog box, click Cancel.
Step 7 ![]() Click OK. The edited network asset now appears in the list on the IPv6 Target Value Rating tab.
Click OK. The edited network asset now appears in the list on the IPv6 Target Value Rating tab.
Step 8 ![]() To delete a network asset, select in the list, and then click Delete. The network asset no longer appears in the list on the IPv6 Target Value Rating tab.
To delete a network asset, select in the list, and then click Delete. The network asset no longer appears in the list on the IPv6 Target Value Rating tab.

Tip ![]() To discard your changes, click Reset.
To discard your changes, click Reset.
Step 9 ![]() Click Apply to apply your changes and save the revised configuration.
Click Apply to apply your changes and save the revised configuration.
Configuring OS Identifications
This section describes how to configure OS identifications, and contains the following topics:
•![]() Understanding Passive OS Fingerprinting
Understanding Passive OS Fingerprinting
•![]() Configuring Passive OS Fingerprinting
Configuring Passive OS Fingerprinting
•![]() OS Identifications Tab Field Definitions
OS Identifications Tab Field Definitions
•![]() Add and Edit Configured OS Map Dialog Boxes Field Definitions
Add and Edit Configured OS Map Dialog Boxes Field Definitions
•![]() Adding, Editing, Deleting, and Moving Configured OS Maps
Adding, Editing, Deleting, and Moving Configured OS Maps
OS Identifications Tab

Note ![]() You must be administrator or operator to add, edit, and delete configured OS maps.
You must be administrator or operator to add, edit, and delete configured OS maps.
Use the OS Identifications tab to configure OS host mappings, which take precedence over learned OS mappings. On the OS Identifications tab you can add, edit, and delete configured OS maps. You can move them up and down in the list to change the order in which the sensor computes the attack relevance rating and risk rating for that particular IP address and OS type combination.
You can also move them up and down in the list to change the order in which the sensor resolves the OS associated with a particular IP address. Configured OS mappings allow for ranges, so for network 192.168.1.0/24 an administrator might define the following (Table 12-1):
|
|
|
|---|---|
192.168.1.1 |
IOS |
192.168.1.2-192.168.1.10,192.168.1.25 |
UNIX |
192.168.1.1-192.168.1.255 |
Windows |
More specific mappings should be at the beginning of the list. Overlap in the IP address range sets is allowed, but the entry closest to the beginning of the list takes precedence.
Understanding Passive OS Fingerprinting
Passive OS fingerprinting lets the sensor determine the OS that hosts are running. The sensor analyzes network traffic between hosts and stores the OS of these hosts with their IP addresses. The sensor inspects TCP SYN and SYNACK packets exchanged on the network to determine the OS type.
The sensor then uses the OS of the target host OS to determine the relevance of the attack to the victim by computing the attack relevance rating component of the risk rating. Based on the relevance of the attack, the sensor may alter the risk rating of the alert for the attack and/or the sensor may filter the alert for the attack. You can then use the risk rating to reduce the number of false positive alerts (a benefit in IDS mode) or definitively drop suspicious packets (a benefit in IPS mode). Passive OS fingerprinting also enhances the alert output by reporting the victim OS, the source of the OS identification, and the relevance to the victim OS in the alert.
Passive OS fingerprinting consists of three components:
•![]() Passive OS learning
Passive OS learning
Passive OS learning occurs as the sensor observes traffic on the network. Based on the characteristics of TCP SYN and SYNACK packets, the sensor makes a determination of the OS running on the host of the source IP address.
•![]() User-configurable OS identification
User-configurable OS identification
You can configure OS host mappings, which take precedence over learned OS mappings.
•![]() Computation of attack relevance rating and risk rating
Computation of attack relevance rating and risk rating
The sensor uses OS information to determine the relevance of the attack signature to the targeted host. The attack relevance is the attack relevance rating component of the risk rating value for the attack alert. The sensor uses the OS type reported in the host posture information imported from the CSA MC to compute the attack relevance rating.
There are three sources of OS information. The sensor ranks the sources of OS information in the following order:
1. ![]() Configured OS mappings—OS mappings you enter.
Configured OS mappings—OS mappings you enter.
Configured OS mappings reside in the Event Action Rules policy and can apply to one or many virtual sensors.

2. ![]() Imported OS mappings—OS mappings imported from an external data source.
Imported OS mappings—OS mappings imported from an external data source.
Imported OS mappings are global and apply to all virtual sensors.

Note ![]() Currently CSA MC is the only external data source.
Currently CSA MC is the only external data source.
3. ![]() Learned OS mappings—OS mappings observed by the sensor through the fingerprinting of TCP packets with the SYN control bit set.
Learned OS mappings—OS mappings observed by the sensor through the fingerprinting of TCP packets with the SYN control bit set.
Learned OS mappings are local to the virtual sensor that sees the traffic.
When the sensor needs to determine the OS for a target IP address, it consults the configured OS mappings. If the target IP address is not in the configured OS mappings, the sensor looks in the imported OS mappings. If the target IP address is not in the imported OS mappings, the sensor looks in the learned OS mappings. If it cannot find it there, the sensor treats the OS of the target IP address as unknown.

Note ![]() Passive OS fingerprinting is enabled by default and the IPS contains a default vulnerable OS list for each signature.
Passive OS fingerprinting is enabled by default and the IPS contains a default vulnerable OS list for each signature.
Configuring Passive OS Fingerprinting
You do not have to configure passive OS fingerprinting for it to function. IPS provides a default vulnerable OS list for each signature and passive analysis is enabled by default.
You can configure the following aspects of passive OS fingerprinting:
•![]() Define OS mappings
Define OS mappings
We recommend configuring OS mappings to define the identity of the OS running on critical systems. It is best to configure OS mappings when the OS and IP address of the critical systems are unlikely to change.
•![]() Limit the attack relevance rating calculation to a specific IP address range
Limit the attack relevance rating calculation to a specific IP address range
This limits the attack relevance rating calculations to IP addresses on the protected network.
•![]() Import OS mappings
Import OS mappings
Importing OS mappings provides a mechanism for accelerating the learning rate and fidelity of the OS identifications made through passive analysis. If you have an external product interface, such as the CSA MC, you can import OS identifications from it.
•![]() Define event action rules filters using the OS relevancy value of the target
Define event action rules filters using the OS relevancy value of the target
This provides a way to filter alerts solely on OS relevancy.
•![]() Disable passive analysis
Disable passive analysis
Stops the sensor from learning new OS mappings.
•![]() Edit signature vulnerable OS lists
Edit signature vulnerable OS lists
The vulnerable OS list specifies what OS types are vulnerable to each signature. The default, general-os, applies to all signatures that do not specify a vulnerable OS list.
OS Identifications Tab Field Definitions
The following fields are found on the OS Identifications tab:
•![]() Enable passive OS fingerprinting analysis—When checked, lets the sensor perform passive OS analysis.
Enable passive OS fingerprinting analysis—When checked, lets the sensor perform passive OS analysis.
•![]() Restrict OS mapping and ARR to these IP addresses—Lets you configure the mapping of OS type to a specific IP address and have the sensor calculate the attack relevance rating for that IP address.
Restrict OS mapping and ARR to these IP addresses—Lets you configure the mapping of OS type to a specific IP address and have the sensor calculate the attack relevance rating for that IP address.
•![]() Configured OS Map—Displays the attributes of the configured OS map.
Configured OS Map—Displays the attributes of the configured OS map.
–![]() Name—The name you give the configured OS map.
Name—The name you give the configured OS map.
–![]() Active—Whether this configured OS map is active or inactive.
Active—Whether this configured OS map is active or inactive.
–![]() IP Address—The IP address of this configured OS map.
IP Address—The IP address of this configured OS map.
–![]() OS Type—The OS type of this configured OS map.
OS Type—The OS type of this configured OS map.
Add and Edit Configured OS Map Dialog Boxes Field Definitions
The following fields are found in the Add and Edit Configured OS Map dialog boxes:
•![]() Name—Lets you name this configured OS map.
Name—Lets you name this configured OS map.
•![]() Active—Lets you choose to have the configured OS map active or inactive.
Active—Lets you choose to have the configured OS map active or inactive.
•![]() IP Address—Lets you enter the IP address associated with this configured OS map.
IP Address—Lets you enter the IP address associated with this configured OS map.
The IP address for configured OS mappings (and only configured OS mappings) can be a set of IP addresses and IP address ranges. The following are all valid IP address values for configured OS mappings:
–![]() 10.1.1.1,10.1.1.2,10.1.1.15
10.1.1.1,10.1.1.2,10.1.1.15
–![]() 10.1.2.1
10.1.2.1
–![]() 10.1.1.1-10.2.1.1,10.3.1.1
10.1.1.1-10.2.1.1,10.3.1.1
–![]() 10.1.1.1-10.1.1.5
10.1.1.1-10.1.1.5
•![]() OS Type—Lets you choose one of the following OS Types to associate with the IP address:
OS Type—Lets you choose one of the following OS Types to associate with the IP address:
–![]() AIX
AIX
–![]() BSD
BSD
–![]() General OS
General OS
–![]() HP UX
HP UX
–![]() IOS
IOS
–![]() IRIX
IRIX
–![]() Linux
Linux
–![]() Mac OS
Mac OS
–![]() Netware
Netware
–![]() Other
Other
–![]() Solaris
Solaris
–![]() UNIX
UNIX
–![]() Unknown OS
Unknown OS
–![]() Win NT
Win NT
–![]() Windows
Windows
–![]() Windows NT/2K/XP
Windows NT/2K/XP
Adding, Editing, Deleting, and Moving Configured OS Maps
To add, edit, delete, and move configured OS maps, follow these steps:
Step 1 ![]() Log in to IME using an account with administrator or operator privileges.
Log in to IME using an account with administrator or operator privileges.
Step 2 ![]() Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > OS Identifications, and then click Add.
Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > OS Identifications, and then click Add.
Step 3 ![]() In the Name field, enter a name for the configured OS map.
In the Name field, enter a name for the configured OS map.
Step 4 ![]() In the Active field, click the Yes radio button to add this configured OS map to the list so that it takes effect.
In the Active field, click the Yes radio button to add this configured OS map to the list so that it takes effect.
Step 5 ![]() In the IP Address field, enter the IP address of the host that you are mapping to an OS. For example, use this format, 10.10.5.5,10.10.2.1-10.10.2.30.
In the IP Address field, enter the IP address of the host that you are mapping to an OS. For example, use this format, 10.10.5.5,10.10.2.1-10.10.2.30.
Step 6 ![]() From the OS Type drop-down list, choose the OS that will be mapped to the IP address.
From the OS Type drop-down list, choose the OS that will be mapped to the IP address.

Tip ![]() To discard your changes and close the Add Configured OS Map dialog box, click Cancel.
To discard your changes and close the Add Configured OS Map dialog box, click Cancel.
Step 7 ![]() Click OK. The new configured OS map now appears in the list on the OS Identifications tab.
Click OK. The new configured OS map now appears in the list on the OS Identifications tab.
Step 8 ![]() Check the Enable passive OS fingerprinting analysis check box.
Check the Enable passive OS fingerprinting analysis check box.

Note ![]() You must check the Enable passive OS fingerprinting analysis check box on the OS Identifications tab or none of the configured OS maps will be enabled regardless of the value you set in the Add Configured OS Map dialog box.
You must check the Enable passive OS fingerprinting analysis check box on the OS Identifications tab or none of the configured OS maps will be enabled regardless of the value you set in the Add Configured OS Map dialog box.
Step 9 ![]() To edit a configured OS map, select it in the list, and then click Edit.
To edit a configured OS map, select it in the list, and then click Edit.
Step 10 ![]() Make any changes needed.
Make any changes needed.

Tip ![]() To discard your changes and close the Edit Configured OS Map dialog box, click Cancel.
To discard your changes and close the Edit Configured OS Map dialog box, click Cancel.
Step 11 ![]() Click OK. The edited configured OS map now appears in the list on the OS Identifications tab.
Click OK. The edited configured OS map now appears in the list on the OS Identifications tab.
Step 12 ![]() Check the Enable passive OS fingerprinting analysis check box.
Check the Enable passive OS fingerprinting analysis check box.

Note ![]() You must check the Enable passive OS fingerprinting analysis check box on the OS Identifications tab or none of the configured OS maps will be enabled regardless of the value you set in the Edit Configured OS Map dialog box.
You must check the Enable passive OS fingerprinting analysis check box on the OS Identifications tab or none of the configured OS maps will be enabled regardless of the value you set in the Edit Configured OS Map dialog box.
Step 13 ![]() To delete a configured OS map, select it in the list, and then click Delete. The configured OS map no longer appears in the list on the OS Identifications tab.
To delete a configured OS map, select it in the list, and then click Delete. The configured OS map no longer appears in the list on the OS Identifications tab.
Step 14 ![]() To move a configured OS map up or down in the list, select it, and then click the Move Up or Move Down arrows.
To move a configured OS map up or down in the list, select it, and then click the Move Up or Move Down arrows.

Tip ![]() To discard your changes, click Reset.
To discard your changes, click Reset.
Step 15 ![]() Click Apply to apply your changes and save the revised configuration.
Click Apply to apply your changes and save the revised configuration.
Configuring Event Variables
This section describes how to configure event variables, and contains the following topics:
•![]() Event Variables Tab Field Definitions
Event Variables Tab Field Definitions
•![]() Add and Edit Event Variable Dialog Boxes Field Definitions
Add and Edit Event Variable Dialog Boxes Field Definitions
•![]() Adding, Editing, and Deleting Event Variables
Adding, Editing, and Deleting Event Variables
Event Variables Tab

Note ![]() You must be administrator or operator to add, edit, or delete event variables.
You must be administrator or operator to add, edit, or delete event variables.
You can create event variables and then use those variables in event action filters. When you want to use the same value within multiple filters, use a variable. When you change the value of the variable, any filter that uses that variable is updated with the new value.

Note ![]() You must preface the variable with a dollar ($) sign to indicate that you are using a variable rather than a string.
You must preface the variable with a dollar ($) sign to indicate that you are using a variable rather than a string.
Some variables cannot be deleted because they are necessary to the signature system. If a variable is protected, you cannot select it to edit it. You receive an error message if you try to delete protected variables. You can edit only one variable at a time.
When configuring IPv4 addresses, specify the full IP address or ranges or set of ranges:
•![]() 10.89.10.10-10.89.10.23
10.89.10.10-10.89.10.23
•![]() 10.90.1.1
10.90.1.1
•![]() 192.56.10.1-192.56.10.255
192.56.10.1-192.56.10.255
•![]() 10.1.1.1-10.2.255.255, 10.89.10.10-10.89.10.23
10.1.1.1-10.2.255.255, 10.89.10.10-10.89.10.23
When configuring IPv6 addresses, use the following format:
<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>[,<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>]

Note ![]() IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
Timesaver ![]() For example, if you have an IP address space that applies to your engineering group and there are no Windows systems in that group, and you are not worried about any Windows-based attacks to that group, you could set up a variable to be the IP address space of the engineering group. You could then use this variable to configure a filter that would ignore all Windows-based attacks for this group.
For example, if you have an IP address space that applies to your engineering group and there are no Windows systems in that group, and you are not worried about any Windows-based attacks to that group, you could set up a variable to be the IP address space of the engineering group. You could then use this variable to configure a filter that would ignore all Windows-based attacks for this group.
Event Variables Tab Field Definitions
The following fields are found on the Event Variables tab:
•![]() Name—Lets you assign a name to this variable.
Name—Lets you assign a name to this variable.
•![]() Type—Identifies the variable as an address.
Type—Identifies the variable as an address.
•![]() Value—Lets you add the value(s) represented by this variable.
Value—Lets you add the value(s) represented by this variable.
Add and Edit Event Variable Dialog Boxes Field Definitions
The following fields are found in the Add and Edit Event Variable dialog boxes:
•![]() Name—Lets you assign a name to this variable.
Name—Lets you assign a name to this variable.
•![]() Type—Identifies the variable as an IPv4 or IPv6 address:
Type—Identifies the variable as an IPv4 or IPv6 address:
–![]() For IPv4 address use a full IP address or range or set of ranges.
For IPv4 address use a full IP address or range or set of ranges.
–![]() For IPv6 address use the following format:
For IPv6 address use the following format:
<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>[,<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>]

Note ![]() IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
•![]() Value—Lets you add the value(s) represented by this variable.
Value—Lets you add the value(s) represented by this variable.
Adding, Editing, and Deleting Event Variables

Note ![]() Global Correlation Inspection and the Reputation Filtering deny features do not support IPv6 addresses. For global correlation inspection, the sensor does not receive or process reputation data for IPv6 addresses. The risk rating for IPv6 addresses is not modified for global correlation inspection. Similarly, network participation does not include event data for attacks from IPv6 addresses. And finally, IPv6 addresses do not appear in the deny list.
Global Correlation Inspection and the Reputation Filtering deny features do not support IPv6 addresses. For global correlation inspection, the sensor does not receive or process reputation data for IPv6 addresses. The risk rating for IPv6 addresses is not modified for global correlation inspection. Similarly, network participation does not include event data for attacks from IPv6 addresses. And finally, IPv6 addresses do not appear in the deny list.

Note ![]() Rate limiting and blocking are not supported for IPv6 traffic. If a signature is configured with a block or rate limit event action and is triggered by IPv6 traffic, an alert is generated but the action is not carried out.
Rate limiting and blocking are not supported for IPv6 traffic. If a signature is configured with a block or rate limit event action and is triggered by IPv6 traffic, an alert is generated but the action is not carried out.
To add, edit, and delete event variables, follow these steps:
Step 1 ![]() Log in to IME using an account with administrator or operator privileges.
Log in to IME using an account with administrator or operator privileges.
Step 2 ![]() Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > Event Variables, and then click Add.
Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > Event Variables, and then click Add.
Step 3 ![]() In the Name field, enter a name for this variable.
In the Name field, enter a name for this variable.

Note ![]() A valid name can only contain numbers or letters. You can also use a hyphen (-) or an underscore (_).
A valid name can only contain numbers or letters. You can also use a hyphen (-) or an underscore (_).
Step 4 ![]() From the Type drop-down list, choose address for an IPv4 address or ipv6-address for an IPv6 address.
From the Type drop-down list, choose address for an IPv4 address or ipv6-address for an IPv6 address.
Step 5 ![]() In the Value field, enter the values for this variable.
In the Value field, enter the values for this variable.
For IPv4 addresses, specify the full IP address or ranges or set of ranges. For example:
•![]() 10.89.10.10-10.89.10.23
10.89.10.10-10.89.10.23
•![]() 10.90.1.1
10.90.1.1
•![]() 192.56.10.1-192.56.10.255
192.56.10.1-192.56.10.255

Note ![]() You can use commas as delimiters. Make sure there are no trailing spaces after the comma. Otherwise, you receive a
You can use commas as delimiters. Make sure there are no trailing spaces after the comma. Otherwise, you receive a Validation failed error.
For IPv6 address, use the following format:
<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>[,<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>-<XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX:XXXX>]

Note ![]() IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.
IPv6 addresses are 128 bits represented in hexadecimal and divided into eight 16-bit groups separated by colons. You can skip the leading zeros and you can represent the zeroed groups in the middle with a double colon (::). You must start the address with the 2001:db8 prefix.

Tip ![]() To discard your changes and close the Add Event Variable dialog box, click Cancel.
To discard your changes and close the Add Event Variable dialog box, click Cancel.
Step 6 ![]() Click OK. The new variable appears in the list on the Event Variables tab.
Click OK. The new variable appears in the list on the Event Variables tab.
Step 7 ![]() To edit an existing variable, select it in the list, and then click Edit.
To edit an existing variable, select it in the list, and then click Edit.
Step 8 ![]() Make any changes needed.
Make any changes needed.

Tip ![]() To discard your changes and close the Edit Event Variable dialog box, click Cancel.
To discard your changes and close the Edit Event Variable dialog box, click Cancel.
Step 9 ![]() Click OK. The edited event variable now appears in the list on the Event Variables tab.
Click OK. The edited event variable now appears in the list on the Event Variables tab.
Step 10 ![]() To delete an event variable, select it in the list, and then click Delete. The event variable no longer appears in the list on the Event Variables tab.
To delete an event variable, select it in the list, and then click Delete. The event variable no longer appears in the list on the Event Variables tab.

Tip ![]() To discard your changes, click Reset.
To discard your changes, click Reset.
Step 11 ![]() Click Apply to apply your changes and save the revised configuration.
Click Apply to apply your changes and save the revised configuration.
Configuring Risk Category
This section describes how to configure risk categories, and contains the following topics:
•![]() Risk Category Tab Field Definitions
Risk Category Tab Field Definitions
•![]() Add and Edit Risk Level Dialog Boxes Field Definitions
Add and Edit Risk Level Dialog Boxes Field Definitions
•![]() Adding, Editing, and Deleting Risk Categories
Adding, Editing, and Deleting Risk Categories
Risk Category Tab

Note ![]() You must be administrator to add and edit risk levels.
You must be administrator to add and edit risk levels.
On the Risk Category tab, you can use predefined risk categories (HIGHRISK, MEDIUMRISK, AND LOWRISK) or you can define your own labels. Risk categories link a category name to a numeric range defining the risk rating. You specify the low threshold for the category to make sure that the ranges are contiguous. The upper category is either the next higher category or 100.
You can then group the threats in red, yellow, and green categories. These red, yellow, and green threshold statistics are used in event action overrides and are also shown in the Network Security Gadget on the Home page.

Note ![]() You cannot delete a predefined risk category.
You cannot delete a predefined risk category.
The red, yellow, and green threshold statistics represent the state of network security with red being the most critical. If you change a threshold, any event action overrides that had the same range as the risk category are changed to reflect the new range.
The new category is inserted in to the Risk Category list according to its threshold value and is automatically assigned actions that cover its range.
Risk Category Tab Field Definitions
The following fields are found on the Risk Category tab:
•![]() Risk Category Name—Name of this risk level. The predefined categories have the following values:
Risk Category Name—Name of this risk level. The predefined categories have the following values:
–![]() HIGHRISK—90 (means 90 to 100)
HIGHRISK—90 (means 90 to 100)
–![]() MEDIUMRISK—70 (means 70 to 89)
MEDIUMRISK—70 (means 70 to 89)
–![]() LOWRISK—1 (means 1 to 69)
LOWRISK—1 (means 1 to 69)
•![]() Risk Threshold—Threshold number for this risk. The value is a number from 0 to 100.
Risk Threshold—Threshold number for this risk. The value is a number from 0 to 100.
•![]() Risk Range—Risk rating range for his risk category.
Risk Range—Risk rating range for his risk category.
The risk rating is a range between 0 and 100 that represents a numerical quantification of the risk associated with a particular event on the network.
•![]() Network Security Health Statistics—Lists the numbers for the red, yellow, and green thresholds. The overall network security value represents the least secure value (green is the most secure and red is the least secure).
Network Security Health Statistics—Lists the numbers for the red, yellow, and green thresholds. The overall network security value represents the least secure value (green is the most secure and red is the least secure).
–![]() Red Threat Thresholds
Red Threat Thresholds
–![]() Yellow Threat Thresholds
Yellow Threat Thresholds
–![]() Green Threat Thresholds
Green Threat Thresholds
These color thresholds refer to the Sensor Health gadget on the Home pane.
Add and Edit Risk Level Dialog Boxes Field Definitions
The following fields are found in the Add and Edit Risk Level dialog boxes:
•![]() Risk Name—Lets you name this risk level.
Risk Name—Lets you name this risk level.
•![]() Risk Threshold—Lets you assign a risk threshold for this risk level.
Risk Threshold—Lets you assign a risk threshold for this risk level.
You specify or change only the lower threshold for the category so that the risk categories are contiguous. The upper threshold is either the next higher category or 100.
•![]() Active—Lets you make this risk level active.
Active—Lets you make this risk level active.
Adding, Editing, and Deleting Risk Categories
To add, edit, and delete risk categories, follow these steps:
Step 1 ![]() Log in to IME using an account with administrator or operator privileges.
Log in to IME using an account with administrator or operator privileges.
Step 2 ![]() Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > Risk Category, and then click Add.
Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > Risk Category, and then click Add.
Step 3 ![]() In the Risk Name field, enter a name for this risk category.
In the Risk Name field, enter a name for this risk category.
Step 4 ![]() In the Risk Threshold field, enter a numerical value for the risk threshold (minimum 0, maximum 100).
In the Risk Threshold field, enter a numerical value for the risk threshold (minimum 0, maximum 100).
This number represents the lower boundary of risk. The range appears in the Risk Range field and in the red, yellow, and green threshold fields.
Step 5 ![]() To make this risk category active, click the Yes radio button.
To make this risk category active, click the Yes radio button.

Tip ![]() To discard your changes and close the Add Risk Category dialog box, click Cancel.
To discard your changes and close the Add Risk Category dialog box, click Cancel.
Step 6 ![]() Click OK. The new risk category appears in the list on the Risk Category tab.
Click OK. The new risk category appears in the list on the Risk Category tab.
Step 7 ![]() To edit an existing risk category, select it in the list, and then click Edit.
To edit an existing risk category, select it in the list, and then click Edit.
Step 8 ![]() Make any changes needed.
Make any changes needed.

Tip ![]() To discard your changes and close the Edit Risk Category dialog box, click Cancel.
To discard your changes and close the Edit Risk Category dialog box, click Cancel.
Step 9 ![]() Click OK. The edited risk category now appears in the list on the Risk Category tab.
Click OK. The edited risk category now appears in the list on the Risk Category tab.
Step 10 ![]() To delete a risk category, select in the list, and then click Delete. The risk category no longer appears in the list on the Risk Category tab.
To delete a risk category, select in the list, and then click Delete. The risk category no longer appears in the list on the Risk Category tab.

Tip ![]() To discard your changes, click Reset.
To discard your changes, click Reset.
Step 11 ![]() Click Apply to apply your changes and save the revised configuration.
Click Apply to apply your changes and save the revised configuration.
Configuring General Settings
This section describes how to configure the general settings, and contains the following topics:
•![]() General Tab Field Definitions
General Tab Field Definitions
•![]() Configuring the General Settings
Configuring the General Settings
General Tab

Note ![]() You must be administrator or operator to configure the general settings for event action rules.
You must be administrator or operator to configure the general settings for event action rules.
You can configure the general settings that apply globally to event action rules, such as whether you want to use the Summarizer and the Meta Event Generator. The Summarizer groups events into a single alert, thus decreasing the number of alerts the sensor sends out. The Meta Event Generator processes the component events, which lets the sensor watch for suspicious activity transpiring over a series of events

You can also use threat rating adjustment, event action filters, and you can enable one-way TCP reset. The one-way TCP reset operates for inline mode only and is an automatic addition to the deny packet inline actions. It sends a TCP reset to the victim of the alert, thus creating a black hole for the attacker and clearing the TCP resources of the victim.You can configure how long you want to deny attackers, the maximum number of denied attackers, and how long you want blocks to last.

Note ![]() An inline sensor now denies packets for any alert with a risk rating of greater than or equal to 90. It also issues a one-way TCP reset on TCP alerts with a risk rating of greater than or equal to 90.
An inline sensor now denies packets for any alert with a risk rating of greater than or equal to 90. It also issues a one-way TCP reset on TCP alerts with a risk rating of greater than or equal to 90.
General Tab Field Definitions
The following fields are found the on the General tab:
•![]() Use Summarizer—Enables the Summarizer component.
Use Summarizer—Enables the Summarizer component.
By default, the Summarizer is enabled. If you disable it, all signatures are set to Fire All with no summarization. If you configure individual signatures to summarize, this configuration will be ignored if the Summarizer is not enabled.
•![]() Use Meta Event Generator—Enables the Meta Event Generator.
Use Meta Event Generator—Enables the Meta Event Generator.
By default, the Meta Event Generator is enabled. If you disable the Meta Event Generator, all Meta engine signatures are disabled.
•![]() Use Threat Rating Adjustment—Enables threat rating adjustment, which adjusts the risk rating. If disabled, the risk rating is equal to threat rating.
Use Threat Rating Adjustment—Enables threat rating adjustment, which adjusts the risk rating. If disabled, the risk rating is equal to threat rating.
•![]() Use Event Action Filters—Enables the event action filter component. You must check this check box to use any filter that is enabled.
Use Event Action Filters—Enables the event action filter component. You must check this check box to use any filter that is enabled.
•![]() Enable One Way TCP Reset—(inline mode only) Enables a one-way TCP reset for deny packet inline actions for TCP-based alerts. It sends a TCP reset to the victim of the alert thus clearing the TCP resources of the victim.
Enable One Way TCP Reset—(inline mode only) Enables a one-way TCP reset for deny packet inline actions for TCP-based alerts. It sends a TCP reset to the victim of the alert thus clearing the TCP resources of the victim.
•![]() Deny Attacker Duration—Number of seconds to deny the attacker inline. The valid range is 0 to 518400. The default is 3600.
Deny Attacker Duration—Number of seconds to deny the attacker inline. The valid range is 0 to 518400. The default is 3600.
•![]() Block Action Duration—Number of minutes to block a host or connection. The valid range is 0 to 10000000. The default is 30.
Block Action Duration—Number of minutes to block a host or connection. The valid range is 0 to 10000000. The default is 30.
•![]() Maximum Denied Attackers—Limits the number of denied attackers possible in the system at any one time. The valid range is 0 to 100000000. The default is 10000.
Maximum Denied Attackers—Limits the number of denied attackers possible in the system at any one time. The valid range is 0 to 100000000. The default is 10000.
Configuring the General Settings

To configure the general settings for event action rules, follow these steps:
Step 1 ![]() Log in to IME using an account with administrator or operator privileges.
Log in to IME using an account with administrator or operator privileges.
Step 2 ![]() Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > General.
Choose Configuration > sensor_name > Policies > Event Action Rules > rules0 > General.
Step 3 ![]() To enable the summarizer feature, check the Use Summarizer check box.
To enable the summarizer feature, check the Use Summarizer check box.

Step 4 ![]() To enable the meta event generator, check the Use Meta Event Generator check box.
To enable the meta event generator, check the Use Meta Event Generator check box.

Step 5 ![]() To enable threat rating adjustment, check the Use Threat Rating Adjustment check box.
To enable threat rating adjustment, check the Use Threat Rating Adjustment check box.
Step 6 ![]() To enable event action filters, check the Use Event Action Filters check box.
To enable event action filters, check the Use Event Action Filters check box.

Note ![]() You must check the Use Event Action Filters check box on the General pane so that any event action filters you configured in the Configuration > sensor_name > Policies > Event Action Rules > rules0 > Event Action Filters pane are active.
You must check the Use Event Action Filters check box on the General pane so that any event action filters you configured in the Configuration > sensor_name > Policies > Event Action Rules > rules0 > Event Action Filters pane are active.
Step 7 ![]() To enable one way TCP reset for deny packet inline actions, check the Enable One Way TCP Reset check box.
To enable one way TCP reset for deny packet inline actions, check the Enable One Way TCP Reset check box.
Step 8 ![]() In the Deny Attacker Duration field, enter the number of seconds you want to deny the attacker inline.
In the Deny Attacker Duration field, enter the number of seconds you want to deny the attacker inline.
Step 9 ![]() In the Block Action Duration field, enter the number of minutes you want to block a host or connection.
In the Block Action Duration field, enter the number of minutes you want to block a host or connection.
Step 10 ![]() In the Maximum Denied Attackers field, enter the maximum number of denied attackers you want at any one time.
In the Maximum Denied Attackers field, enter the maximum number of denied attackers you want at any one time.

Tip ![]() To discard your changes, click Reset.
To discard your changes, click Reset.
Step 11 ![]() Click Apply to apply your changes and save the revised configuration.
Click Apply to apply your changes and save the revised configuration.
 Feedback
Feedback