- Preface
- Introducing the Sensor
- Installing IPS-4240 and IPS-4255
- Installing IPS-4260
- Installing IPS 4270-20
- Installing AIM-IPS
- Installing AIP-SSC-5
- Installing AIP-SSM
- Installing IDSM-2
- Installing NME-IPS
- Initializing the Sensor
- Logging In to the Sensor
- Obtaining Software
- Upgrading, Downgrading, and Installing System Images
- Troubleshooting
- Glossary
- Index
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 6.2
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- November 21, 2008
Chapter: Installing NME-IPS
Installing NME-IPS

Note ![]() All IPS platforms allow ten concurrent CLI sessions.
All IPS platforms allow ten concurrent CLI sessions.
This chapter describes how to install NME-IPS. It contains the following sections:
•![]() Software and Hardware Requirements
Software and Hardware Requirements
•![]() Interoperability with Other IPS Modules
Interoperability with Other IPS Modules
•![]() Installation and Removal Instructions
Installation and Removal Instructions
Specifications
Table 9-1 lists the specifications for NME-IPS.
Before Installing NME-IPS
Follow these recommendations before installing NME-IPS:
•![]() Upgrade or downgrade software when you can take all applications that run on the router out of service or offline.
Upgrade or downgrade software when you can take all applications that run on the router out of service or offline.
•![]() Make sure that you have the correct router and software for the module.
Make sure that you have the correct router and software for the module.
•![]() For safety and regulatory information, read Cisco Network Modules and Interface Cards Regulatory Compliance and Safety Information.
For safety and regulatory information, read Cisco Network Modules and Interface Cards Regulatory Compliance and Safety Information.
•![]() Make a note of the location of the module in the router (slot_number/port_number). The port value is 0, and the slot number field specifies the physical slot number for NME-IPS (slot_number/IDS-Sensor 0).
Make a note of the location of the module in the router (slot_number/port_number). The port value is 0, and the slot number field specifies the physical slot number for NME-IPS (slot_number/IDS-Sensor 0).

Note ![]() After you install the module, you can get this information by using the show running-config command. You need the module slot number to configure the interfaces on the module.
After you install the module, you can get this information by using the show running-config command. You need the module slot number to configure the interfaces on the module.
For More Information
•![]() For the supported routers and software, see Software and Hardware Requirements.
For the supported routers and software, see Software and Hardware Requirements.
•![]() For more information, refer to Setting Up Interfaces on NME-IPS and the Router.
For more information, refer to Setting Up Interfaces on NME-IPS and the Router.
Software and Hardware Requirements
The router and NME-IPS have the following software and hardware requirements:
•![]() The router must be running Cisco IOS release 12.4(20)YA or 12.4(22)T or later.
The router must be running Cisco IOS release 12.4(20)YA or 12.4(22)T or later.

Note ![]() Use the show version command in the router CLI to determine which Cisco IOS release your router is running.
Use the show version command in the router CLI to determine which Cisco IOS release your router is running.
•![]() The module must be running IPS 6.1(1) or later.
The module must be running IPS 6.1(1) or later.

Note ![]() Use the service-module IDS-Sensor slot/port status command in the IOS CLI to determine which IPS release your sensor is running. Or use the show version command in the module CLI.
Use the service-module IDS-Sensor slot/port status command in the IOS CLI to determine which IPS release your sensor is running. Or use the show version command in the module CLI.
•![]() Supported routers:
Supported routers:
–![]() Cisco 2800 series (2811, 2821, and 2851)
Cisco 2800 series (2811, 2821, and 2851)
–![]() Cisco 3800 series (3825 and 3845)
Cisco 3800 series (3825 and 3845)

Note ![]() The Cisco routers support up to one NME-IPS per platform.
The Cisco routers support up to one NME-IPS per platform.
•![]() Supported Cisco IOS Feature Sets:
Supported Cisco IOS Feature Sets:
–![]() Cisco IOS Advanced Security
Cisco IOS Advanced Security
–![]() Cisco IOS Advanced IP Services
Cisco IOS Advanced IP Services
–![]() Cisco IOS Advanced Enterprise Services
Cisco IOS Advanced Enterprise Services
Interoperability with Other IPS Modules

The Cisco access routers only support one IDS/IPS module per router. If you have more than one IDS/IPS module installed, the most capable card is enabled. The most capable hierarchy is:
1. ![]() NME-IPS
NME-IPS
2. ![]() AIM-IPS
AIM-IPS
3. ![]() NM-CIDS
NM-CIDS
This means, for example, that if all modules are installed, NME-IPS disables all other modules. AIM-IPS disables all NM-CIDS. If there are multiple modules with the same level of capability, the first one discovered is enabled and all others are disabled.
You cannot bring up, enable, or configure a disabled module. To bring up a less capable module, you must remove the more capable module from the router and reboot. Disabled modules are reported in the show diag command output. The state of the module is reported as present but disabled.
If the most capable module slot and port do not match the interface ids slot/port configuration command, the most capable module is disabled with the following warning:
The module in slot x will be disabled and configuration ignored.
The correct slot/port number are displayed so that you can change the configuration.
For More Information
For more information on NM-CIDS, refer to Introducing NM-CIDS and Installing NM-CIDS.
Restrictions
The following restrictions apply to NME-IPS:
•![]() Do not deploy IOS IPS and NME-IPS at the same time.
Do not deploy IOS IPS and NME-IPS at the same time.
•![]() When NME-IPS is used with an IOS firewall, make sure SYN flood prevention is done by the IOS firewall.
When NME-IPS is used with an IOS firewall, make sure SYN flood prevention is done by the IOS firewall.
NME-IPS and the IOS firewall complement each other's abilities to create security zones in the network and inspect traffic in those zones. Because NME-IPS and the IOS firewall operate independently, sometimes they are unaware of the other's activities. In this situation, the IOS firewall is the best defense against a SYN flood attack.
•![]() The Cisco access routers only support one IDS/IPS per router.
The Cisco access routers only support one IDS/IPS per router.

For More Information
•![]() For more information on how NME-IPS functions with other IPS modules, see Interoperability with Other IPS Modules.
For more information on how NME-IPS functions with other IPS modules, see Interoperability with Other IPS Modules.
•![]() For more information about shutting down NME-IPS, refer to Rebooting, Resetting, and Shutting Down NME-IPS.
For more information about shutting down NME-IPS, refer to Rebooting, Resetting, and Shutting Down NME-IPS.
Hardware Interfaces
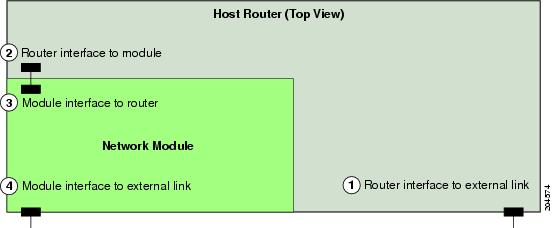
Figure 9-1 shows the router and NME-IPS interfaces used for internal and external communication. You can configure the router interfaces through the Cisco IOS CLI and the NME-IPS interfaces through the IPS CLI, IDM, IME, or CSM.
Figure 9-1 NME-IPS and Router Interfaces
For More Information
•![]() For more information on the IPS CLI, refer to Configuring the Cisco Intrusion Prevention System Sensor Using the Command Line Interface 6.2.
For more information on the IPS CLI, refer to Configuring the Cisco Intrusion Prevention System Sensor Using the Command Line Interface 6.2.
•![]() For more information on IDM, refer to Installing and Using Cisco Intrusion Prevention System Device Manager 6.2.
For more information on IDM, refer to Installing and Using Cisco Intrusion Prevention System Device Manager 6.2.
•![]() For IME, refer to Installing and Using Cisco Intrusion Prevention System Manager Express 6.2.
For IME, refer to Installing and Using Cisco Intrusion Prevention System Manager Express 6.2.
Installation and Removal Instructions
For instructions on how to install and remove NME-IPS, refer to Installing Cisco Network Modules in Cisco Access Routers.
To comply with the Telcordia GR-1089 NEBS standard for electromagnetic compatibility and safety, connect NME-IPS only to intrabuilding or nonexposed wiring or cabling. The intrabuilding cable must be shielded and the shield must be grounded at both ends.
For More Information
•![]() For the procedure for verifying that NME-IPS is installed properly, see Verifying Installation.
For the procedure for verifying that NME-IPS is installed properly, see Verifying Installation.
•![]() For the procedure for using the setup command to initialize NME-IPS, see Initializing the Sensor.
For the procedure for using the setup command to initialize NME-IPS, see Initializing the Sensor.
•![]() For more information about obtaining the most recent Cisco IPS software, see Obtaining Cisco IPS Software.
For more information about obtaining the most recent Cisco IPS software, see Obtaining Cisco IPS Software.
•![]() For the procedure to configure NME-IPS to receive IPS traffic, refer to Setting Up Interfaces on NME-IPS and the Router.
For the procedure to configure NME-IPS to receive IPS traffic, refer to Setting Up Interfaces on NME-IPS and the Router.
•![]() For the procedure for using HTTPS to log in to IDM, refer to Logging In to IDM.
For the procedure for using HTTPS to log in to IDM, refer to Logging In to IDM.
•![]() For the procedures for configuring intrusion prevention on your sensor, refer to the following guides:
For the procedures for configuring intrusion prevention on your sensor, refer to the following guides:
–![]() Installing and Using Cisco Intrusion Prevention System Device Manager 6.2
Installing and Using Cisco Intrusion Prevention System Device Manager 6.2
–![]() Installing and Using Cisco Intrusion Prevention System Manager Express 6.2
Installing and Using Cisco Intrusion Prevention System Manager Express 6.2
–![]() Configuring the Cisco Intrusion Prevention System Sensor Using the Command Line Interface 6.2
Configuring the Cisco Intrusion Prevention System Sensor Using the Command Line Interface 6.2
Verifying Installation
Use the show inventory command in privileged EXEC mode to verify the installation of NME-IPS.

Note ![]() You can also use this command to find the serial number of your NME-IPS for use in troubleshooting with TAC. The serial number appears in the PID line, for example, SN: FHH1117001R.
You can also use this command to find the serial number of your NME-IPS for use in troubleshooting with TAC. The serial number appears in the PID line, for example, SN: FHH1117001R.
To verify the installation of NME-IPS, follow these steps:
Step 1 ![]() Log in to the router.
Log in to the router.
Step 2 ![]() Enter privileged EXEC mode on the router.
Enter privileged EXEC mode on the router.
router> enable
Step 3 ![]() Verify that NME-IPS is part of the router inventory.
Verify that NME-IPS is part of the router inventory.
router# show inventory
NAME: "3845 chassis", DESCR: "3845 chassis"
PID: CISCO3845 , VID: V01 , SN: FTX1002C255
NAME: "c3845 Motherboard with Gigabit Ethernet on Slot 0", DESCR: "c3845 Motherb
oard with Gigabit Ethernet"
PID: CISCO3845-MB , VID: V03 , SN: FOC09514J4Y
NAME: "4 Port FE Switch on Slot 0 SubSlot 0", DESCR: "4 Port FE Switch"
PID: HWIC-4ESW , VID: V01 , SN: FOC1102394U
NAME: "High Speed WAN Interface Card - 1 Port Gigabit Ethernet on Slot 0 SubSlot
3", DESCR: "High Speed WAN Interface Card - 1 Port Gigabit Ethernet"
PID: HWIC-1GE-SFP , VID: V01 , SN: FOC10164DAR
NAME: "1000BASE-T SFP", DESCR: "1000BASE-T SFP"
PID: SP7041 , VID: C , SN: 00000MTC101608RB
NAME: "Cisco Intrusion Prevention System NM on Slot 2", DESCR: "Cisco Intrusion
Prevention System NM"
PID: NME-IPS-K9 , VID: V01, SN: FHH1117001R
router#
 Feedback
Feedback