- Preface
- Getting Started
- Configuring Dashboards
- Using the Startup Wizard
- Setting Up the Sensor
- Configuring Interfaces
- Configuring Policies
- Defining Signatures
- Using the Signature Wizard
- Configuring Event Action Rules
- Configuring Anomaly Detections
- Configuring SSH and Certificates
- Configuring Attack Response Controller for Blocking and Rate Limiting
- Configuring SNMP
- Configuring External Product Interfaces
- Managing the Sensor
- Monitoring the Sensor
- Initializing the Sensor
- Logging In to the Sensor
- Obtaining Software
- Upgrading, Downgrading, and Installing System Images
- System Architecture
- Signature Engines
- Troubleshooting
- Open Source License Files
- Glossary
- Index
Cisco Intrusion Prevention System Device Manager Configuration Guide for IPS 6.2
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- October 28, 2008
Chapter: Obtaining Software
Obtaining Software
This chapter describes how to obtain and install the latest Cisco IPS software, and contains the following topics:
•![]() Upgrading Cisco IPS Software to 6.2
Upgrading Cisco IPS Software to 6.2
•![]() Cisco Security Intelligence Operations
Cisco Security Intelligence Operations
Obtaining Cisco IPS Software
You can download the latest Cisco IPS software from Cisco.com. You must be logged into Cisco.com to access the software download site. You set up an account with cryptographic access the first time you download software. You can sign up for IPS Alert Bulletins to receive information on the latest software releases.

You can find major and minor updates, service packs, signature and signature engine updates, system and recovery files, firmware upgrades, and readmes on the Download Software site on Cisco.com.
Signature updates are posted to Cisco.com approximately every week, more often if needed. Service packs are posted to Cisco.com as needed. Major and minor updates are also posted periodically. Check Cisco.com regularly for the latest IPS software.

Note ![]() You must be logged in to Cisco.com to download software. You must have an active IPS maintenance contract and a Cisco.com password to download software. You must have a license to apply signature updates.
You must be logged in to Cisco.com to download software. You must have an active IPS maintenance contract and a Cisco.com password to download software. You must have a license to apply signature updates.
Downloading IPS Software
To download software on Cisco.com, follow these steps:
Step 1 ![]() Log in to Cisco.com.
Log in to Cisco.com.
Step 2 ![]() From the Support drop-down menu, choose Download Software.
From the Support drop-down menu, choose Download Software.
Step 3 ![]() Under Select a Software Product Category, choose Security Software.
Under Select a Software Product Category, choose Security Software.
Step 4 ![]() Choose Intrusion Prevention System (IPS).
Choose Intrusion Prevention System (IPS).
Step 5 ![]() Enter your username and password.
Enter your username and password.
Step 6 ![]() In the Download Software window, choose IPS Appliances > Cisco Intrusion Prevention System and then click the version you want to download.
In the Download Software window, choose IPS Appliances > Cisco Intrusion Prevention System and then click the version you want to download.

Note ![]() You must have an IPS subscription service license to download software.
You must have an IPS subscription service license to download software.
Step 7 ![]() Click the type of software file you need. The available files appear in a list in the right side of the window. You can sort by file name, file size, memory, and release date. And you can access the Release Notes and other product documentation.
Click the type of software file you need. The available files appear in a list in the right side of the window. You can sort by file name, file size, memory, and release date. And you can access the Release Notes and other product documentation.
Step 8 ![]() Click the file you want to download. The file details appear.
Click the file you want to download. The file details appear.
Step 9 ![]() Verify that it is the correct file, and click Download.
Verify that it is the correct file, and click Download.
Step 10 ![]() Click Agree to accept the software download rules. The first time you download a file from Cisco.com, you must fill in the Encryption Software Export Distribution Authorization form before you can download the software.
Click Agree to accept the software download rules. The first time you download a file from Cisco.com, you must fill in the Encryption Software Export Distribution Authorization form before you can download the software.
•![]() Fill out the form and click Submit.
Fill out the form and click Submit.
The Cisco Systems Inc. Encryption Software Usage Handling and Distribution Policy appears.
•![]() Read the policy and click I Accept.
Read the policy and click I Accept.
The Encryption Software Export/Distribution Form appears.
If you previously filled out the Encryption Software Export Distribution Authorization form, and read and accepted the Cisco Systems Inc. Encryption Software Usage Handling and Distribution Policy, these forms are not displayed again. The File Download dialog box appears.
Step 11 ![]() Open the file or save it to your computer.
Open the file or save it to your computer.
Step 12 ![]() Follow the instructions in the Readme to install the update.
Follow the instructions in the Readme to install the update.

Note ![]() Major and minor updates, service packs, recovery files, signature and signature engine updates are the same for all sensors. System image files are unique per platform.
Major and minor updates, service packs, recovery files, signature and signature engine updates are the same for all sensors. System image files are unique per platform.
For More Information
•![]() For the procedure for obtaining and installing the license key, see Configuring Licensing.
For the procedure for obtaining and installing the license key, see Configuring Licensing.
•![]() For an explanation of the IPS file versioning scheme, see IPS Software Versioning.
For an explanation of the IPS file versioning scheme, see IPS Software Versioning.
IPS Software Versioning

Note ![]() The software version installed on your sensor is listed in the Sensor Information gadget in the Home pane of IDM.
The software version installed on your sensor is listed in the Sensor Information gadget in the Home pane of IDM.
When you download IPS software images from Cisco.com, you should understand the versioning scheme so that you know which files are base files, which are cumulative, and which are incremental.
Major Update
A major update contains new functionality or an architectural change in the product. For example, the Cisco IPS 6.0 base version includes everything (except deprecated features) since the previous major release (the minor update features, service pack fixes, and signature updates) plus any new changes. Major update 6.0(1) requires 5.x. With each major update there are corresponding system and recovery packages.

Note ![]() The 6.0(1) major update is only used to upgrade 5.x sensors to 6.0(1) If you are reinstalling 6.0(1) on a sensor that already has 6.0(1) installed, use the system image or recovery procedures rather than the major update.
The 6.0(1) major update is only used to upgrade 5.x sensors to 6.0(1) If you are reinstalling 6.0(1) on a sensor that already has 6.0(1) installed, use the system image or recovery procedures rather than the major update.
Minor Update
A minor update is incremental to the major version. Minor updates are also base versions for service packs. The first minor update for 6.0 is 6.1(1). Minor updates are released for minor enhancements to the product. Minor updates contain all previous minor features (except deprecated features), service pack fixes, signature updates since the last major version, and the new minor features being released. You can install the minor updates on the previous major or minor version (and often even on earlier versions). The minimum supported version needed to upgrade to the newest minor version is listed in the Readme that accompanies the minor update. With each minor update there are corresponding system and recovery packages.
Service Pack
A service pack is cumulative following a base version release (minor or major). Service packs are used for the release of defect fixes with no new enhancements. Service packs contain all service pack fixes since the last base version (minor or major) and the new defect fixes being released. Service packs require the minor version. The minimum supported version needed to upgrade to the newest service pack is listed in the Readme that accompanies the service pack. Service packs also include the latest engine update. For example, if service pack 6.0(3) is released, and E3 is the latest engine level, the service pack is released as 6.0(3)E3.
Patch Release
A patch release is used to address defects that are identified in the upgrade binaries after a software release. Rather than waiting until the next major or minor update, or service pack to address these defects, a patch can be posted. Patches include all prior patch releases within the associated service pack level. The patches roll into the next official major or minor update, or service pack.
Before you can install a patch release, the most recent major or minor update, or service pack must be installed. For example, patch release 6.0(1p1) requires 6.0(1).

Note ![]() Upgrading to a newer patch does not require you to uninstall the old patch. For example, you can upgrade from patch 6.0(1p1) to 6.0(1p2) without first uninstalling 6.0(1p1).
Upgrading to a newer patch does not require you to uninstall the old patch. For example, you can upgrade from patch 6.0(1p1) to 6.0(1p2) without first uninstalling 6.0(1p1).
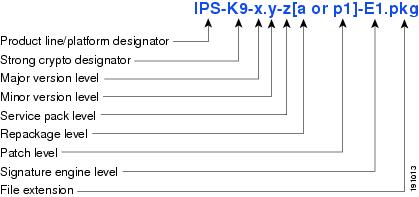
Figure 19-1 illustrates what each part of the IPS software file represents for major and minor updates, service packs, and patch releases.
Figure 19-1 IPS Software File Name for Major and Minor Updates, Service Packs, and Patch Releases
Signature Update
A signature update is a package file containing a set of rules designed to recognize malicious network activities. Signature updates are released independently from other software updates. Each time a major or minor update is released, you can install signature updates on the new version and the next oldest version for a period of at least six months. Signature updates are dependent on a required signature engine version. Because of this, a req designator lists the signature engine required to support a particular signature update.
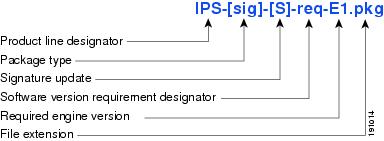
Figure 19-2 illustrates what each part of the IPS software file represents for signature updates.
Figure 19-2 IPS Software File Name for Signature Updates
Signature Engine Update
A signature engine update is an executable file containing binary code to support new signature updates. Signature engine files require a specific service pack, which is also identified by the req designator.
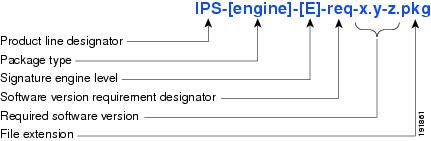
Figure 19-3 illustrates what each part of the IPS software file represents for signature engine updates.
Figure 19-3 IPS Software File Name for Signature Engine Updates
Recovery and System Image Files
Recovery and system image files contain separate versions for the installer and the underlying application. The installer version contains a major and minor version field. The major version is incremented by one of any major changes to the image installer, for example, switching from .tar to rpm or changing kernels. The minor version can be incremented by any one of the following:
•![]() Minor change to the installer, for example, a user prompt added.
Minor change to the installer, for example, a user prompt added.
•![]() Repackages require the installer minor version to be incremented by one if the image file must be repackaged to address a defect or problem with the installer.
Repackages require the installer minor version to be incremented by one if the image file must be repackaged to address a defect or problem with the installer.
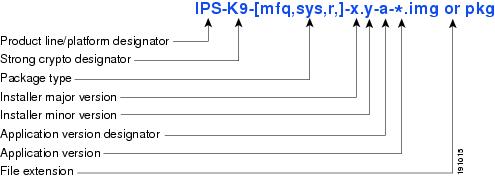
Figure 19-4 illustrates what each part of the IPS software file represents for recovery and system image files.
Figure 19-4 IPS Software File Name for Recovery and System Image Files
Software Release Examples
Table 19-1 lists platform-independent Cisco IPS 6.x software release examples. Refer to the Readmes that accompany the software files for detailed instructions on how to install the files.
|
|
|
|
|
|
|---|---|---|---|---|
Signature update1 |
Weekly |
sig |
S353 |
IPS-sig-S353-req-E3.pkg |
Signature engine update2 |
As needed |
engine |
E3 |
IPS-engine-E3-req-6.2-1.pkg |
Service packs3 |
Semi-annually |
— |
6.1(3) |
IPS-K9-6.2-3-E3.pkg |
Minor version update4 |
Annually |
— |
6.1(1) |
IPS-K9-6.2-1-E3.pkg Note |
Major version update5 |
Annually |
— |
6.0(1) |
IPS-K9-6.0-1-E3.pkg |
Patch release6 |
As needed |
patch |
6.0(1p1) |
IPS-K9-patch-6.2-1pl-E3.pkg |
Recovery package7 |
Annually or as needed |
r |
1.1-6.1(1) |
IPS-K9-r-1.1-a-6.2-1-E3.pkg |
1 Signature updates include the latest cumulative IPS signatures. 2 Signature engine updates add new engines or engine parameters that are used by new signatures in later signature updates. 3 Service packs include defect fixes. 4 Minor versions include new minor version features and/or minor version functionality. 5 Major versions include new major version functionality or new architecture. 6 Patch releases are for interim fixes. 7 The r 1.1 can be revised to r 1.2 if it is necessary to release a new recovery package that contains the same underlying application image. If there are defect fixes for the installer, for example, the underlying application version may still be 6.0(1), but the recovery partition image will be r 1.2. |
Table 19-2 describes platform-dependent software release examples.
|
|
|
|
|
|
|---|---|---|---|---|
System image1 |
Annually |
sys |
Separate file for each sensor platform |
IPS 4240-K9-sys-1.1-a-6.2-1-E3.img |
Maintenance partition image2 |
Annually |
mp |
IDSM2 |
c6svc-mp.2-1-2.bin.gz |
Bootloader |
As needed |
bl |
AIM IPS |
pse_aim_x.y.z.bin |
Mini-kernel |
As needed |
mini-kernel |
AIM IPS |
pse_mini_kernel_1.1.10.64.bz2 |
1 The system image includes the combined recovery and application image used to reimage an entire sensor. 2 The maintenance partition image includes the full image for the IDSM2 maintenance partition. The file is installed from but does not affect the IDSM2 application partition. |
Table 19-3 describes the platform identifiers used in platform-specific names.
For More Information
•![]() For instructions on how to access these files on Cisco.com, see Obtaining Cisco IPS Software.
For instructions on how to access these files on Cisco.com, see Obtaining Cisco IPS Software.
•![]() For procedures for installing the various software files, see Chapter 20 "Upgrading, Downgrading, and Installing System Images."
For procedures for installing the various software files, see Chapter 20 "Upgrading, Downgrading, and Installing System Images."
Upgrading Cisco IPS Software to 6.2
Observe the following when upgrading your sensor:
•![]() The minimum required version for upgrading to 6.2 is 5.0(1) or later, which is available as a download from Cisco.com.
The minimum required version for upgrading to 6.2 is 5.0(1) or later, which is available as a download from Cisco.com.
•![]() Use IPS-AIM-K9-6.2-1-E3.pkg to upgrade the AIM IPS and IPS-NME-K9-6.2-1-E3 to upgrade the NME IPS. For all other supported sensors, use the IPS-K9-6.2-1-E3.pkg upgrade file.
Use IPS-AIM-K9-6.2-1-E3.pkg to upgrade the AIM IPS and IPS-NME-K9-6.2-1-E3 to upgrade the NME IPS. For all other supported sensors, use the IPS-K9-6.2-1-E3.pkg upgrade file.
•![]() After you upgrade any IPS software on your sensor, you must restart the IDM to see the latest software features.
After you upgrade any IPS software on your sensor, you must restart the IDM to see the latest software features.
•![]() If you configured Auto Update for your sensor, copy the Cisco IPS 6.2(1)E3 update files to the directory on the server that your sensor polls for updates. If you install an update on your sensor and the sensor is unusable after it reboots, you must reimage your sensor.
If you configured Auto Update for your sensor, copy the Cisco IPS 6.2(1)E3 update files to the directory on the server that your sensor polls for updates. If you install an update on your sensor and the sensor is unusable after it reboots, you must reimage your sensor.
•![]() If you are using automatic update with a mixture of AIM IPS, NME IPS, and other IPS appliances or modules, make sure you put both the 6.2(1)E3 upgrade file (IPS-K9-6.2-1-E3.pkg), the AIM IPS upgrade file (IPS-AIM-K9-6.2-1-E3.pkg), and the NME IPS upgrade file (IPS-NME-K9-6.2-1-E3) on the automatic update server so that the AIM IPS and the NME IPS can correctly detect which file needs to be automatically downloaded and installed. If you only put the 6.2(1)E3 upgrade file (IPS-K9-6.2-1-E3.pkg) on the server, the AIM IPS and the NME IPS will download and try to install the wrong file.
If you are using automatic update with a mixture of AIM IPS, NME IPS, and other IPS appliances or modules, make sure you put both the 6.2(1)E3 upgrade file (IPS-K9-6.2-1-E3.pkg), the AIM IPS upgrade file (IPS-AIM-K9-6.2-1-E3.pkg), and the NME IPS upgrade file (IPS-NME-K9-6.2-1-E3) on the automatic update server so that the AIM IPS and the NME IPS can correctly detect which file needs to be automatically downloaded and installed. If you only put the 6.2(1)E3 upgrade file (IPS-K9-6.2-1-E3.pkg) on the server, the AIM IPS and the NME IPS will download and try to install the wrong file.
You can reimage your sensor in the following ways:
•![]() For all sensors, use the recover command.
For all sensors, use the recover command.
•![]() For IPS 4240, IPS 4255, IPS 4260, and IPS 4270-20, use the ROMMON to restore the system image.
For IPS 4240, IPS 4255, IPS 4260, and IPS 4270-20, use the ROMMON to restore the system image.
•![]() For the AIM IPS and the NME IPS, use the bootloader.
For the AIM IPS and the NME IPS, use the bootloader.
•![]() For the IDSM2, reimage the application partition from the maintenance partition.
For the IDSM2, reimage the application partition from the maintenance partition.

Note ![]() You cannot upgrade the IDSM (WS-X6381) to IPS 6.x. You must replace your IDSM (WS-X6381) with the IDSM2 (WS-SVC-IDSM2-K9), which supports version 6.2(1)E3.
You cannot upgrade the IDSM (WS-X6381) to IPS 6.x. You must replace your IDSM (WS-X6381) with the IDSM2 (WS-SVC-IDSM2-K9), which supports version 6.2(1)E3.
•![]() For the AIP SSM and AIP SSC-5, reimage from the adaptive security appliance using the hw-module module 1 recover configure/boot command.
For the AIP SSM and AIP SSC-5, reimage from the adaptive security appliance using the hw-module module 1 recover configure/boot command.

For More Information
•![]() For the procedure for accessing downloads on Cisco.com, see Obtaining Cisco IPS Software.
For the procedure for accessing downloads on Cisco.com, see Obtaining Cisco IPS Software.
•![]() For the procedure for using the upgrade command to upgrade the sensor, see Upgrading the Sensor.
For the procedure for using the upgrade command to upgrade the sensor, see Upgrading the Sensor.
•![]() For the procedure for configuring automatic upgrades on the sensor, see Configuring Automatic Upgrades.
For the procedure for configuring automatic upgrades on the sensor, see Configuring Automatic Upgrades.
•![]() For the procedure for using the recover command, see Recovering the Application Partition on Appliances.
For the procedure for using the recover command, see Recovering the Application Partition on Appliances.
•![]() For the procedures for using ROMMON to restore the system image, see Installing the IPS 4240 and IPS 4255 System Images, Installing the IPS 4260 System Image, and.Installing the IPS 4270-20 System Image.
For the procedures for using ROMMON to restore the system image, see Installing the IPS 4240 and IPS 4255 System Images, Installing the IPS 4260 System Image, and.Installing the IPS 4270-20 System Image.
•![]() For the procedure for restoring the AIM IPS system image, see Installing the AIM IPS System Image.
For the procedure for restoring the AIM IPS system image, see Installing the AIM IPS System Image.
•![]() For the procedure for restoring the NME IPS system image, see Installing the NME IPS System Image.
For the procedure for restoring the NME IPS system image, see Installing the NME IPS System Image.
•![]() For the procedure for reimaging the IDSM2 application partition from the maintenance partition, see Installing the IDSM2 System Image.
For the procedure for reimaging the IDSM2 application partition from the maintenance partition, see Installing the IDSM2 System Image.
•![]() For the procedure for using the hw-module module 1 recover configure/boot command to reimage the AIP SSM and AIP SSC-5, see Installing the AIP SSM and AIP SSC-5 System Image.
For the procedure for using the hw-module module 1 recover configure/boot command to reimage the AIP SSM and AIP SSC-5, see Installing the AIP SSM and AIP SSC-5 System Image.
Accessing IPS Documentation
You can find IPS documentation at this URL:
http://www.cisco.com/en/US/products/hw/vpndevc/ps4077/tsd_products_support_series_home.html
Or to access IPS documentation from Cisco.com, follow these steps:
Step 1 ![]() Log in to Cisco.com.
Log in to Cisco.com.
Step 2 ![]() Click Support.
Click Support.
Step 3 ![]() Under Support at the bottom of the page, click Documentation.
Under Support at the bottom of the page, click Documentation.
Step 4 ![]() Choose Products > Security > Intrusion Prevention System (IPS) > IPS Appliances > Cisco IPS 4200 Series Sensors. The Cisco IPS 4200 Series Sensors page appears. All of the most up-to-date IPS documentation is on this page.
Choose Products > Security > Intrusion Prevention System (IPS) > IPS Appliances > Cisco IPS 4200 Series Sensors. The Cisco IPS 4200 Series Sensors page appears. All of the most up-to-date IPS documentation is on this page.

Note ![]() Although you will see references to other IPS documentation sites on Cisco.com, this is the site with the most complete and up-to-date IPS documentation.
Although you will see references to other IPS documentation sites on Cisco.com, this is the site with the most complete and up-to-date IPS documentation.
Step 5 ![]() Click one of the following categories to access Cisco IPS documentation:
Click one of the following categories to access Cisco IPS documentation:
•![]() Download Software—Takes you to the Download Software site.
Download Software—Takes you to the Download Software site.

Note ![]() You must be logged into Cisco.com to access the software download site.
You must be logged into Cisco.com to access the software download site.
•![]() Release and General Information—Contains documentation roadmaps and release notes.
Release and General Information—Contains documentation roadmaps and release notes.
•![]() Reference Guides—Contains command references and technical references.
Reference Guides—Contains command references and technical references.
•![]() Design—Contains design guide and design tech notes.
Design—Contains design guide and design tech notes.
•![]() Install and Upgrade—Contains hardware installation and regulatory guides.
Install and Upgrade—Contains hardware installation and regulatory guides.
•![]() Configure—Contains configuration guides for IPS CLI, IDM, and IME.
Configure—Contains configuration guides for IPS CLI, IDM, and IME.
•![]() Troubleshoot and Alerts—Contains TAC tech notes and field notices.
Troubleshoot and Alerts—Contains TAC tech notes and field notices.
Cisco Security Intelligence Operations
The Cisco Security Intelligence Operations site on Cisco.com provides intelligence reports about current vulnerabilities and security threats. It also has reports on other security topics that help you protect your network and deploy your security systems to reduce organizational risk.
You should be aware of the most recent security threats so that you can most effectively secure and manage your network. Cisco Security Intelligence Operations contains the top ten intelligence reports listed by date, severity, urgency, and whether there is a new signature available to deal with the threat.
Cisco Security Intelligence Operations contains a Security News section that lists security articles of interest. There are related security tools and links.
You can access Cisco Security Intelligence Operations at this URL:
http://tools.cisco.com/security/center/home.x
Cisco Security Intelligence Operations is also a repository of information for individual signatures, including signature ID, type, structure, and description.
You can search for security alerts and signatures at this URL:
http://tools.cisco.com/security/center/search.x
 Feedback
Feedback