Inspecting Allowed Traffic For Intrusions and Malware
License: Protection or Malware
Intrusion and file policies govern the system’s intrusion prevention, file control, and AMP capabilities as a last line of defense before traffic is allowed to its destination. Security Intelligence-based traffic filtering, SSL inspection decisions (including decryption), decoding and preprocessing, and access control rule selection occur before intrusion and file inspection.
By associating an intrusion or file policy with an access control rule, you are telling the system that before it passes traffic that matches the access control rule’s conditions, you first want to inspect the traffic with an intrusion policy, a file policy, or both. Access control rule conditions can be simple or complex; you can control traffic by security zone, network or geographical location, port, application, requested URL, and user.
The system matches traffic to access control rules in the order you specify. In most cases, the system handles network traffic according to the first access control rule where all the rule’s conditions match the traffic. An access control rule’s action determines how the system handles matching traffic. You can monitor, trust, block, or allow (with or without further inspection) matching traffic; see Using Rule Actions to Determine Traffic Handling and Inspection
Note that an Interactive Block rule has the same inspection options as an Allow rule. This is so you can inspect traffic for malicious content when a user bypasses a blocked website by clicking through a warning page. For more information, see Interactive Blocking Actions: Allowing Users to Bypass Website Blocks
Traffic that does not match any of the non-Monitor access control rules in a policy is handled by the default action. Note that the system can inspect traffic allowed by the default action for intrusions, but not prohibited files or malware. You cannot associate a file policy with the access control default action.
 Note |
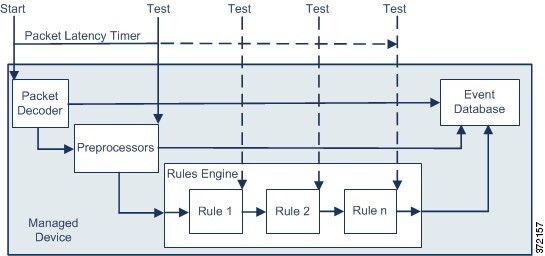
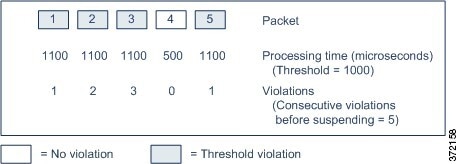
Sometimes, when a connection is analyzed by an access control policy, the system must process the first few packets in that connection, allowing them to pass, before it can decide which access control rule (if any) will handle the traffic. However, so these packets do not reach their destination uninspected, you can use an intrusion policy—called the default intrusion policy—to inspect them and generate intrusion events. |
For more information on the above scenario and instructions on associating file and intrusion policies with access control rules and the access control default action, see:
Understanding File and Intrusion Inspection Order
License: Protection or Malware
 Note |
Traffic allowed by an Intrusion Prevention default action can be inspected for intrusions, but cannot be inspected for prohibited files or malware. You cannot associate a file policy with the access control default action. |
You do not have to perform both file and intrusion inspection in the same rule. For a connection matching an Allow or Interactive Block rule:
-
without a file policy, traffic flow is determined by the intrusion policy
-
without an intrusion policy, traffic flow is determined by the file policy
 Tip |
The system does not perform any kind of inspection on trusted traffic. |
For any single connection handled by an access control rule, file inspection occurs before intrusion inspection. That is, the system does not inspect files blocked by a file policy for intrusions. Within file inspection, simple blocking by type takes precedence over malware inspection and blocking.
 Note |
Until a file is detected and blocked in a session, packets from the session may be subject to intrusion inspection. |
For example, consider a scenario where you normally want to allow certain network traffic as defined in an access control rule. However, as a precaution, you want to block the download of executable files, examine downloaded PDFs for malware and block any instances you find, and perform intrusion inspection on the traffic.
You create an access control policy with a rule that matches the characteristics of the traffic you want to provisionally allow, and associate it with both an intrusion policy and a file policy. The file policy blocks the download of all executables, and also inspects and blocks PDFs containing malware:
-
First, the system blocks the download of all executables, based on simple type matching specified in the file policy. Because they are immediately blocked, these files are subject to neither malware cloud lookup nor intrusion inspection.
-
Next, the system performs malware cloud lookups for PDFs downloaded to a host on your network. Any PDFs with a malware file disposition are blocked, and are not subject to intrusion inspection.
-
Finally, the system uses the intrusion policy associated with the access control rule to inspect any remaining traffic, including files not blocked by the file policy.
Configuring an Access Control Rule to Perform AMP or File Control
License: Protection or Malware
An access control policy can have multiple access control rules associated with file policies. You can configure file inspection for any Allow or Interactive Block access control rule, which permits you to match different file and malware inspection profiles against different types of traffic on your network before it reaches its final destination.
When the system detects a prohibited file (including malware) according to the settings in the file policy, it automatically logs an event. If you do not want to log file or malware events, you can disable this logging on a per-access-control-rule basis. After you associate the file policy with the access control rule, clear the Log Files check box on the Logging tab of the access control rule editor. For more information, see Disabling File and Malware Event Logging for Allowed Connections
The system also logs the end of the associated connection, regardless of the logging configuration of the invoking access control rule. SeeConnections Associated with File and Malware Events (Automatic)
To associate a file policy with an access control rule:
Procedure
| Step 1 |
Select > > > . The Access Control Policy page appears. |
| Step 2 |
Click the edit icon ( |
| Step 3 |
Create a new rule or edit an existing rule; seeCreating and Editing Access Control Rules The access control rule editor appears. |
| Step 4 |
Ensure the rule action is set to Allow, Interactive Block, or Interactive Block with reset. |
| Step 5 |
Select the Inspection tab. The Inspection tab appears. |
| Step 6 |
Select a File Policy to inspect traffic that matches the access control rule, or select None to disable file inspection for matching traffic. You can click the edit ( |
| Step 7 |
Click Add to save the rule. Your rule is saved. You must save and apply the access control policy for your changes to take effect; see Deploying Configuration Changes |
Configuring an Access Control Rule to Perform Intrusion Prevention
License: Protection
An access control policy can have multiple access control rules associated with intrusion policies. You can configure intrusion inspection for any Allow or Interactive Block access control rule, which permits you to match different intrusion inspection profiles against different types of traffic on your network before it reaches its final destination.
Whenever the system uses an intrusion policy to evaluate traffic, it uses an associated variable set . Variables in a set represent values commonly used in intrusion rules to identify source and destination IP addresses and ports. You can also use variables in intrusion policies to represent IP addresses in rule suppressions and dynamic rule states.
 Tip |
Even if you use system-provided intrusion policies, Cisco strongly recommends you configure the system’s intrusion variables to accurately reflect your network environment. At a minimum, modify default variables in the default set; see Optimizing Predefined Default Variables |
Although you can associate a different intrusion policy-variable set pair with each Allow and Interactive Block rule (as well as with the default action), you cannot apply an access control policy if the target devices have insufficient resources to perform inspection as configured. For more information, see Simplifying Rules to Improve Performance
Understanding System-Provided and Custom Intrusion Policies
Cisco delivers several intrusion policies with the ASA FirePOWER module. By using system-provided intrusion policies, you can take advantage of the experience of the Cisco Vulnerability Research Team (VRT). For these policies, the VRT sets intrusion and preprocessor rule states, as well as provides the initial configurations for advanced settings. You can use system-provided policies as-is, or you can use them as the base for custom policies. Building custom policies can improve the performance of the system in your environment and provide a focused view of the malicious traffic and policy violations occurring on your network.
In addition to custom policies that you create, the system provides two custom policies: Initial Inline Policy and Initial Passive Policy. These two intrusion policies use the Balanced Security and Connectivity intrusion policy as their base. The only difference between them is their Drop When Inline setting, which enables drop behavior in the inline policy and disables it in the passive policy. For more information, see Comparing System-Provided with Custom Policies
Connection and Intrusion Event Logging
When an intrusion policy invoked by an access control rule detects an intrusion, it generates an intrusion event. The system also automatically logs the end of the connection where the intrusion occurred, regardless of the logging configuration of the access control rule. See Connections Associated with Intrusion (Automatic)
To associate an intrusion policy with an access control rule:
Procedure
| Step 1 |
Select > > > . The Access Control Policy page appears. |
||
| Step 2 |
Click the edit icon ( |
||
| Step 3 |
Create a new rule or edit an existing rule; see Creating and Editing Access Control Rules The access control rule editor appears. |
||
| Step 4 |
Ensure the rule action is set to Allow, Interactive Block, or Interactive Block with reset. |
||
| Step 5 |
Select the Inspection tab. The Inspection tab appears. |
||
| Step 6 |
Select a system-provided or custom Intrusion Policy, or select None to disable intrusion inspection for traffic that matches the access control rule. If you select a custom intrusion policy, you can click the edit icon (
|
||
| Step 7 |
Optionally, change the Variable Set associated with the intrusion policy. You can click the edit icon ( |
||
| Step 8 |
Click Save to save the rule. Your rule is saved. You must save and apply the access control policy for your changes to take effect; see Deploying Configuration Changes |
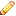 ) next to the access control policy where you want to configure AMP or file control using access control rules.
) next to the access control policy where you want to configure AMP or file control using access control rules.

 Feedback
Feedback