- About This Book
-
- Getting Started
- Setting Up the Prime Fulfillment Services for L2VPN
- Creating a FlexUNI/EVC Ethernet Policy
- Creating a FlexUNI/EVC Ethernet Service Request
- Creating a FlexUNI/EVC ATM-Ethernet Interworking Policy
- Creating a FlexUNI/EVC ATM-Ethernet Interworking Service Request
- Creating an L2VPN Policy
- Creating an L2VPN Service Request
- Creating a VPLS Policy
- Creating a VPLS Service Request
- Deploying, Monitoring, and Auditing Service Requests
- Using Auto Discovery for L2 Services
- Sample Configlets
- Setting Up VLAN Translation
-
- Getting Started with MPLS VPN
- Setting Up the Prime Fulfillment Services
- Independent VRF Management
- IPv6 and 6VPE Support in MPLS VPN
- MPLS VPN Service Policies
- MPLS VPN Service Requests
- Provisioning Regular PE-CE Links
- Provisioning Multi-VRFCE PE-CE Links
- Provisioning Management VPN
- Provisioning Cable Services
- Provisioning Carrier Supporting Carrier
- Provisioning Multiple Devices
- Spanning Multiple Autonomous Systems
- Sample Configlets
- Troubleshooting MPLS VPNs
Cisco Prime Fulfillment User Guide 6.1
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- March 20, 2015
Chapter: User Access Log
User Access Log
This section shows a detailed report of every activity by every user.
Choose Administration > User Access Log > User Access Log and follow these steps:
Step 1 ![]() After you choose Administration > User Access Log > User Access Log, a window appears as shown in Figure 71-1.
After you choose Administration > User Access Log > User Access Log, a window appears as shown in Figure 71-1.
Figure 71-1 User Access Log Viewer with Simple Filter
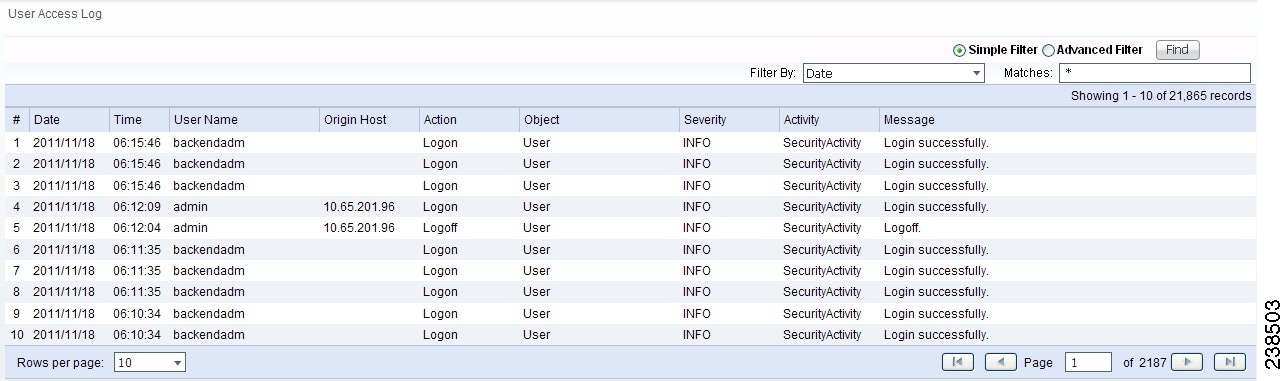
All the log information about user actions appears.

Note ![]() The types of activities or objects to be logged can be configured. This can be done directly through SQL. By default, security-related activities and activities on objects listed in the Role editor are logged.
The types of activities or objects to be logged can be configured. This can be done directly through SQL. By default, security-related activities and activities on objects listed in the Role editor are logged.
Step 2 ![]() The default Simple Filter radio button is selected. To filter using the Simple Filter, continue with Step 3. To filter using Advanced Filter, proceed to Step 5.
The default Simple Filter radio button is selected. To filter using the Simple Filter, continue with Step 3. To filter using Advanced Filter, proceed to Step 5.
Step 3 ![]() To filter the information with Simple Filter, keep the Simple Filter radio button selected and from Filter By, choose: Date, User Name, Origin Host, Action, Severity, or Activity (also column names). For Matches, enter the beginning characters of what you want to match followed by *. Then click Find. The result is that only the log information matching the entered filter appears.
To filter the information with Simple Filter, keep the Simple Filter radio button selected and from Filter By, choose: Date, User Name, Origin Host, Action, Severity, or Activity (also column names). For Matches, enter the beginning characters of what you want to match followed by *. Then click Find. The result is that only the log information matching the entered filter appears.
Step 4 ![]() To exit this log report, choose another feature from the main product tabs.
To exit this log report, choose another feature from the main product tabs.
Step 5 ![]() To filter the information with Advanced Filter, click the Advanced Filter radio button.
To filter the information with Advanced Filter, click the Advanced Filter radio button.
A window as shown in Figure 71-2 appears.
Figure 71-2 User Access Log Viewer with Advanced Filter
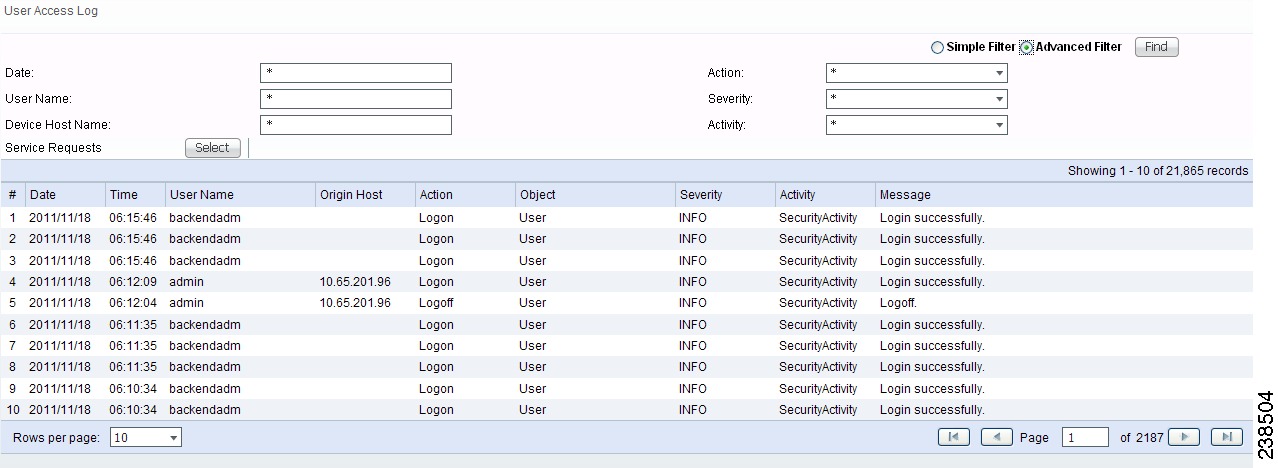
All the log information about user actions appears.
Step 6 ![]() Enter filter information you want to match in one or more of the following categories and then click Find.
Enter filter information you want to match in one or more of the following categories and then click Find.

Note ![]() When you choose multiple filters, the log results that appear are only the ones that match all the specified filter information.
When you choose multiple filters, the log results that appear are only the ones that match all the specified filter information.
•![]() Date Enter the beginning characters of the date you want to view followed by a *, in the format given in the Date column.
Date Enter the beginning characters of the date you want to view followed by a *, in the format given in the Date column.
•![]() User Name Enter the beginning characters of the specific User Name you want to view followed by a *.
User Name Enter the beginning characters of the specific User Name you want to view followed by a *.
•![]() Device Host Name Enter the beginning characters of the specific Host Name you want to view followed by a *.
Device Host Name Enter the beginning characters of the specific Host Name you want to view followed by a *.
•![]() Action Click the drop-down list and choose from: UNKNOWN; View; Create; Modify; Delete; Logon; Logoff; Session Timeout. If you decide not to use this filter, just keep *.
Action Click the drop-down list and choose from: UNKNOWN; View; Create; Modify; Delete; Logon; Logoff; Session Timeout. If you decide not to use this filter, just keep *.
•![]() Severity Click the drop-down list and choose from: UNKNOWN; INFO; WARNING; ERROR. If you decide not to use this filter, just keep *.
Severity Click the drop-down list and choose from: UNKNOWN; INFO; WARNING; ERROR. If you decide not to use this filter, just keep *.
•![]() Activity Click the drop-down list and choose from: UNKNOWN; SecurityActivity; or UserActivity. The result is that only the log information matching the entered filter appears.
Activity Click the drop-down list and choose from: UNKNOWN; SecurityActivity; or UserActivity. The result is that only the log information matching the entered filter appears.
Step 7 ![]() Service Requests has a selection of Select/Deselect. Click this and you receive a list of Service Requests in the system from which you can check check box(es) for the User Access Log to handle. Then click the Select button. These Service Requests then appear on Figure 71-2.
Service Requests has a selection of Select/Deselect. Click this and you receive a list of Service Requests in the system from which you can check check box(es) for the User Access Log to handle. Then click the Select button. These Service Requests then appear on Figure 71-2.
Step 8 ![]() To exit this log report, choose another feature from the main product tabs.
To exit this log report, choose another feature from the main product tabs.
 Feedback
Feedback