- Preface
- Cisco Broadband Access Center Overview
- Broadband Access Center Architecture
- Configuration Workflows and Checklists
- CPE Management Overview
- Configuration Templates Management
- Firmware Management
- Parameter Dictionaries
- CPE History and Troubleshooting
- Managing Broadband Access Center
- Database Management
- Monitoring Broadband Access Center
- Configuring CWMP Service
- Configuring CWMP Service Security
- CWMP Device Operations
- Understanding the Administrator User Interface
- Using the Administrator User Interface
- Configuring Broadband Access Center
- Scripting Framework
- RDU and DPE Connection Management
- Cisco BAC Support Tools and Advanced
- Troubleshooting Broadband Access Center
- Appendix A
- Glossary
Cisco Broadband Access Center Administration Guide 3.10
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- June 1, 2015
Chapter: Configuring Broadband Access Center
- Configuring the Class of Service
- Configuring Custom Properties
- Configuring Defaults
- Managing Files
- Managing License Keys
- Managing DPE Feature Pack Extensions
- Managing RDU Extensions
- Publishing Provisioning Data
- Configuring Lease Query
- Updating the Location of FAP at Group Level in the Grid
- Updating the Location of FAP at Chassis Level
- Configuring Location Verification for UMTS
- Configuring 2G Scan and 3G Scan Capability of LTE
- Configuring Static Neighbor List of LTE
- Configuring Remote Reset for Tampered LTE FAP
Configuring Broadband Access Center
This chapter describes the Cisco Broadband Access Center (BAC) configuration tasks that you perform by selecting the options in the Configuration menu.
This chapter includes the following sections:
- Configuring the Class of Service
- Configuring Custom Properties
- Configuring Defaults
- Managing Files
- Managing License Keys
- Managing DPE Feature Pack Extensions
- Managing RDU Extensions
- Publishing Provisioning Data
- Configuring Lease Query
- Updating the Location of FAP at Group Level in the Grid
- Updating the Location of FAP at Chassis Level
- Configuring Location Verification for UMTS
- Configuring 2G Scan and 3G Scan Capability of LTE
- Configuring Static Neighbor List of LTE
- Configuring Remote Reset for Tampered LTE FAP
Configuring the Class of Service
By using the Cisco BAC administrator user interface, you can configure the Classes of Service offered to your customers. You can use the administrator user interface to add, modify, view, or delete any selected Class of Service. Start with the Manage Class of Service page, as shown in Figure 17-1.
Figure 17-1 Manage Class of Service Page
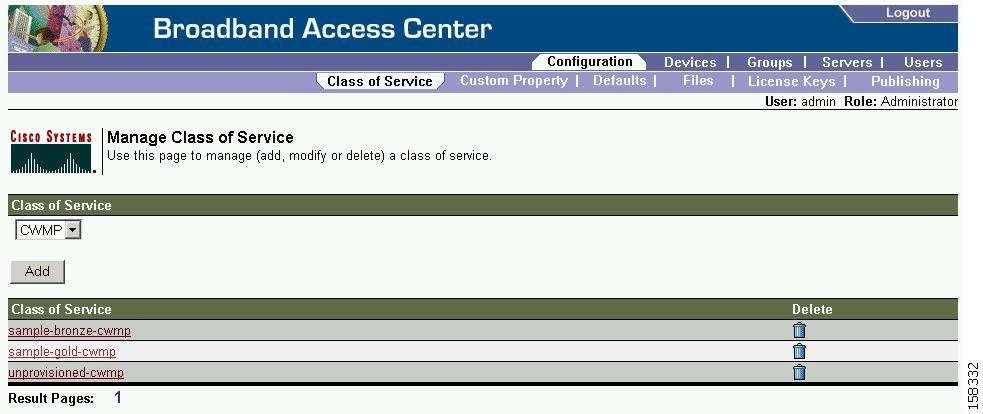
Table 17-1 identifies the fields and buttons shown in Figure 17-1.
|
|
|
|---|---|
|
|
|
A drop-down list that identifies the technology classes of service that you can search for. Available selections, as they appear on screen, include: Note For additional information on these areas of technology, see Configuring Defaults. |
|
|
|
|
Table 17-2 identifies the fields and buttons shown in the Add Class of Service page.
Adding a Class of Service
To add a specific Class of Service:
Step 1![]() Choose Configuration on the Primary Navigation bar.
Choose Configuration on the Primary Navigation bar.
Step 2![]() Choose Class of Service from the Secondary Navigation bar.
Choose Class of Service from the Secondary Navigation bar.
The Add Class of Service page appears. This page identifies the various settings for the selected Class of Service.
Step 4![]() Enter the name of your new class of service.
Enter the name of your new class of service.
For example, assume that you want to create a new Class of Service called Gold-Classic for CWMP. You might enter provisioned-cwmp as the Class of Service Name, and choose CWMP from the service type drop-down list.
Step 5![]() Choose a Configuration Template File. For example, choose sample-cwmp-config.xml from the configuration file template drop-down list.
Choose a Configuration Template File. For example, choose sample-cwmp-config.xml from the configuration file template drop-down list.
Step 6![]() Choose also a Firmware Rule File. For example, choose sample-cwmp-firmware-rules.xml from the firmware rule file drop-down list.
Choose also a Firmware Rule File. For example, choose sample-cwmp-firmware-rules.xml from the firmware rule file drop-down list.
Step 7![]() Enter a Property Name and Property Value in the appropriate fields. This lets you configure standard or custom properties for this class of service object.
Enter a Property Name and Property Value in the appropriate fields. This lets you configure standard or custom properties for this class of service object.
For example, choose as property name /IPDevice/connectionRequestMethod. Choose Discovered from the Property Value drop-down list and then continue with the rest of this procedure.

Note![]() The API constant for /IPDevice/connectionRequestMethod is
The API constant for /IPDevice/connectionRequestMethod is IPDeviceKeys.CONNECTION_REQUEST_METHOD.
Multiple Property Name:Property Value pairs could appear on this page. You use the Delete button to remove any unwanted pairs from the class of service.
Step 8![]() Click Add to add the property to the defining Class of Service.
Click Add to add the property to the defining Class of Service.
Step 9![]() Click Submit to finalize the process or Reset to return all fields to their previous setting.
Click Submit to finalize the process or Reset to return all fields to their previous setting.
After submitting the Class of Service, the Manage Class of Service page appears to show the newly added Class of Service.
Modifying a Class of Service
You can modify the Classes of Service by selecting the various properties and assigning appropriate property values. When creating a Class of Service for the first time you select all of the appropriate properties and assign values to them.
If you make a mistake, or your business requirements for a certain Class of Service change, you can either change the property value before submitting your previous changes or delete the Property Name:Property Value pair altogether.

Note![]() Changes to the Class of Service object trigger the Instruction Generation Service (IGS) to regenerate instructions for all affected devices and send instructions to the DPEs. IGS does this task as a background job. The status of the IGS can be observed using the View RDU Details page.
Changes to the Class of Service object trigger the Instruction Generation Service (IGS) to regenerate instructions for all affected devices and send instructions to the DPEs. IGS does this task as a background job. The status of the IGS can be observed using the View RDU Details page.
To add, delete, or modify Class of Service properties:
Step 1![]() Choose Configuration on the Primary Navigation bar.
Choose Configuration on the Primary Navigation bar.
Step 2![]() Choose Class of Service from the Secondary Navigation bar.
Choose Class of Service from the Secondary Navigation bar.
Step 3![]() Choose the Class of Service to be modified.
Choose the Class of Service to be modified.
Step 4![]() Click the link corresponding to the correct Class of Service.
Click the link corresponding to the correct Class of Service.
The Modify Class of Service page appears; note that the selected Class of Service name and type appear below the page description.
–![]() Select the first property that you want assigned to the selected Class of Service, from the Property Name drop-down and then, after choosing the appropriate value for that property, click Add.
Select the first property that you want assigned to the selected Class of Service, from the Property Name drop-down and then, after choosing the appropriate value for that property, click Add.
–![]() Repeat for any other properties you want to assign to the selected Class of Service.
Repeat for any other properties you want to assign to the selected Class of Service.
–![]() Locate the unwanted property in the list immediately above the Property Name drop-down.
Locate the unwanted property in the list immediately above the Property Name drop-down.
–![]() Delete the appropriate property as described above.
Delete the appropriate property as described above.
–![]() Add the same property back to the Class of Service while entering the new Property Value.
Add the same property back to the Class of Service while entering the new Property Value.

Note![]() If you delete a property that is required for your business process, you must add it back, and select the appropriate value, before you submit the change.
If you delete a property that is required for your business process, you must add it back, and select the appropriate value, before you submit the change.
Step 5![]() Click Submit to make the modifications to the class of service.
Click Submit to make the modifications to the class of service.
Each property added to a Class of Service, appears when you click Submit. After doing so, a confirmation page appears to regenerate the instructions for the devices with the selected Class of Service.
The modified Class of Service will be available in the Manage Class of Service page.
Deleting a Class of Service
You can delete any existing Class of Service but, before you attempt to do so, you must ensure that there are no devices associated with that Class of Service.

Tip![]() Where there are large numbers of devices associated with a Class of Service to be deleted, use the Cisco BAC application programmers interface (API) to write a program to iterate through these devices to reassign another Class of Service to the devices.
Where there are large numbers of devices associated with a Class of Service to be deleted, use the Cisco BAC application programmers interface (API) to write a program to iterate through these devices to reassign another Class of Service to the devices.
Step 1![]() Choose Configuration on the Primary Navigation bar.
Choose Configuration on the Primary Navigation bar.
Step 2![]() Choose Class of Service from the Secondary Navigation bar.
Choose Class of Service from the Secondary Navigation bar.
Step 3![]() Click the Delete icon (
Click the Delete icon ( ) for the correct Class of Service, and a confirmation dialog box appears.
) for the correct Class of Service, and a confirmation dialog box appears.

Note![]() A Class of Service cannot be deleted if devices are associated with it or, if it is designated as the default Class of Service. Therefore, you cannot delete the unprovisioned-cwmp Class of Service object.
A Class of Service cannot be deleted if devices are associated with it or, if it is designated as the default Class of Service. Therefore, you cannot delete the unprovisioned-cwmp Class of Service object.
Step 4![]() Click OK to delete the file, or Cancel to return to the Manage Class of Service page. (See Figure 17-1.)
Click OK to delete the file, or Cancel to return to the Manage Class of Service page. (See Figure 17-1.)
If you try to delete a Class of Service with devices associated with it, this error message is displayed:
Error: Class Of Service [sample-COS] has devices associated with it, unable to delete
Please correct the error(s) and resubmit your request.
The specific Class of Service is specified within the error message. In this example this is represented by sample-COS.
Configuring Custom Properties
Custom properties let you specify additional customizable device information to be stored in the RDU database. The Custom Property configuration page is found under the Configuration menu, and you use this page to add or delete custom properties.

After the custom property is defined, you can use it in this property hierarchy. See Authoring Configuration Templates, for how to use the property hierarchy. Properties can be configured on the following objects for use in the property hierarchy:
Group priorities in the property hierarchy (see Property Hierarchy) are handled through group types.
Step 1![]() Choose Configuration on the Primary Navigation bar.
Choose Configuration on the Primary Navigation bar.
Step 2![]() Choose Custom Property on the Secondary Navigation bar,
Choose Custom Property on the Secondary Navigation bar,
The Manage Cisco BAC Custom Properties page appears.
a.![]() Click Add on the Manage Cisco BAC Custom Properties page,
Click Add on the Manage Cisco BAC Custom Properties page,
The Add Custom Property page appears.
b.![]() Enter the name of the new custom property.
Enter the name of the new custom property.
c.![]() Choose a custom property value type from the drop-down list.
Choose a custom property value type from the drop-down list.
d.![]() Click Submit when complete.
Click Submit when complete.
After the property has been added to the administrative database, the Manage Cisco BAC Custom Properties page appears.
a.![]() Identify the custom property to be deleted from the Manage Cisco BAC Custom Properties page.
Identify the custom property to be deleted from the Manage Cisco BAC Custom Properties page.
b.![]() Click the Delete icon corresponding to the correct custom property,
Click the Delete icon corresponding to the correct custom property,
The custom properties deletion dialog box appears.
c.![]() Click OK to delete the custom property.
Click OK to delete the custom property.
Custom Property for Creating GRID ID for Additional Authentication
A new custom property, FC-GRID-ID-FORMAT, of string type, is available in Cisco BAC to support construction of FC-GRID-ID of the device. The FC-GRID-ID can be used as an additional authentication at the HNB-gateway.
You can edit the value of FC-GRID-ID-FORMAT to support any property, using the below pattern:
You can also include discovered data as property. For example:
SiteId=${FC-SITE-ID},Version=${FC-MNC},RatIid=${FC-RAT-ID}
If you have configured empty string for FC-GRID-ID-FORMAT, the default value will be:
In this case, the GRID ID of the device will be returned (as FC-GRID-ID property) as part of authentication, by taking the values for only the three properties – FC-ENTERPRISE-ID, FC-SITE-ID, and FC-GROUP-ID.
If you have configured invalid values for FC-GRID-ID-FORMAT, then the FC-GRID-ID value will be empty.
The creation of FC-GRID-ID also requires installation of the corresponding RDU extension, and configuration of the Service Level Extension Point in CWMP Defaults (see New Class for DNPrefix Extension and CWMP Defaults)
Custom Property for Creating DNPrefix
A new custom property, FC-DN-PREFIX-FORMAT, of string type, is available in Cisco BAC to support the construction of FC-DN-PREFIX.
The FC-DN-PREFIX can especially be applied to the fault systems so that all applicable identification information such as the enterprise, site, or chassis IDs are included.
You can edit the value for FC-DN-PREFIX-FORMAT to support any property, using the below pattern:
You can also include discovered data as property. For example:
If you have configured empty string for FC-DN-PREFIX-FORMAT, the default value is applied as follows:
RatId=${FC-RAT-ID}
If you have configured invalid values for FC-DN-PREFIX-FORMAT, then the FC-DN-PREFIX value will be empty.
The creation of FC-DN-PREFIX also requires installation of the corresponding RDU extension, and configuration of the Service Level Extension Point in CWMP Defaults (see New Class for DNPrefix Extension and CWMP Defaults).
Setting the Custom Properties for LTE Provisioning
For setting the LTE parameter values on the LTE device, the following custom properties need to be set in the Modify Device page:
This ensures that, if the GPS location is valid, all the LTE parameters with values specified in the configuration template are set to the LTE device, and the FC-SERVICE-STATUS of the LTE device is Operational.
Setting the Custom Properties for NWL
Cisco BAC helps you to configure the network listen function (NWL) of FAP using the following custom properties:
- FC-DNB-CONFIG-NWL-LIST-COUNT - Use this property (integer) to configure the value of number of neighbors received from FAP based on max power (the top 'n' number of neighbors is sorted based on power). If this property is not configured, the default value of 12 is used.
- FC-DNB-FREQ-MATCH - Set this property to true if you want to compare the neighbor identities using frequency. The default values is false, which compares the neighbor identities using GUID (instead of frequency).

Note![]() The periodic NWL based location check of FAP is performed based on the success or failure of the check. If the location check fails, the custom property FC-NWL-SCAN-INTERVAL is automatically set to 20 minutes, till the location check is successful. Once the location check is successful, this property is automatically set to 1440 minutes (24 hours).
The periodic NWL based location check of FAP is performed based on the success or failure of the check. If the location check fails, the custom property FC-NWL-SCAN-INTERVAL is automatically set to 20 minutes, till the location check is successful. Once the location check is successful, this property is automatically set to 1440 minutes (24 hours).
Configuring Defaults
The Defaults page, found under the Configuration option, lets you access the default settings for the overall system, including the Regional Distribution Unit (RDU), and the CWMP technology.
Selecting Configuration Options
The procedure for configuring specific default types is identical. Complete this procedure to access the desired defaults page and then refer to the appropriate section within this chapter for a description of the various page components.
Step 1![]() Choose Configuration on either the Primary Navigation bar or Main Menu page.
Choose Configuration on either the Primary Navigation bar or Main Menu page.
Step 2![]() Choose Defaults from the Secondary Navigation bar.
Choose Defaults from the Secondary Navigation bar.
The Configure Defaults page appears.
Step 3![]() Choose the correct default type from the list to the left of the screen.
Choose the correct default type from the list to the left of the screen.
The appropriate defaults page appears.
CWMP Defaults
The CWMP Defaults page (Figure 17-2) displays a list of CWMP technology configuration settings.
Figure 17-2 Configure CWMP Defaults Page

Table 17-3 describes all fields and buttons appearing in Figure 17-2.
RDU Defaults
When you click the RDU defaults link, the RDU Defaults page (see Figure 17-3) appears. Use this page to configure settings affecting RDU operations.
Figure 17-3 Configure RDU Defaults Page
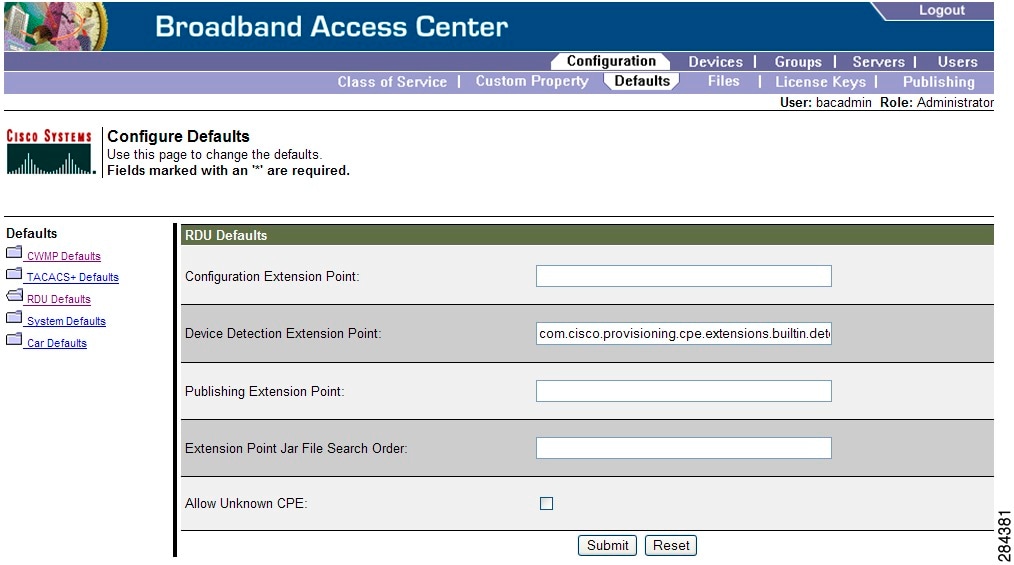
Table 17-4 describes all fields and buttons appearing in Figure 17-3.

Note![]() See Managing RDU Extensions, for related information on RDU extension points.
See Managing RDU Extensions, for related information on RDU extension points.
System Defaults
When you click the Systems Defaults link, the System Defaults page (see Figure 17-4) appears.
Figure 17-4 System Defaults Page
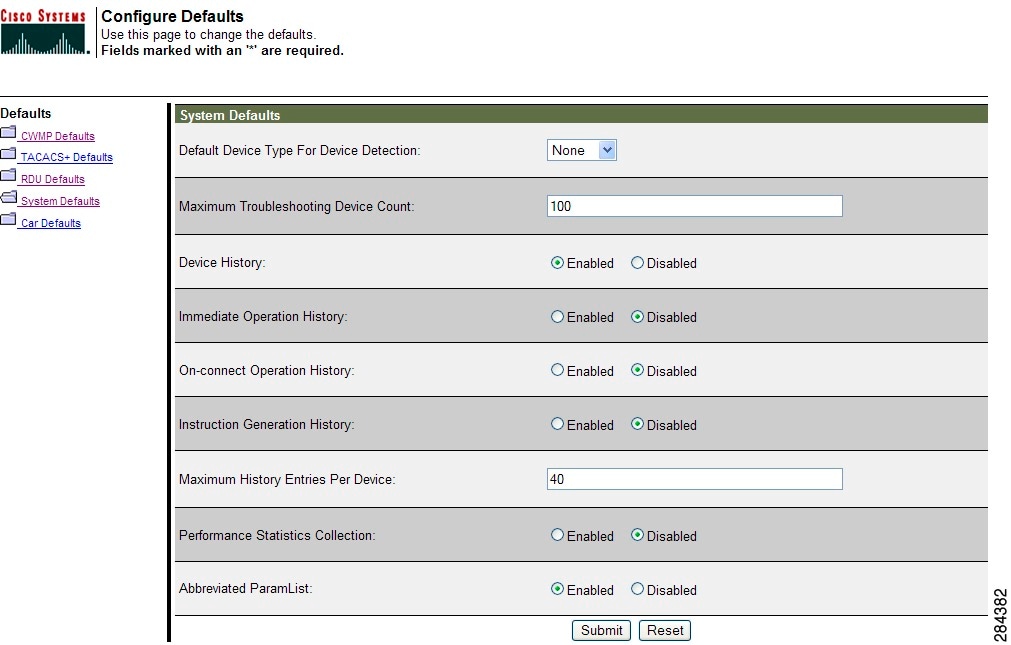
Table 17-5 describes all fields and buttons appearing in Figure 17-4.
|
|
|
|---|---|
Identifies the default device type for a device not previously registered in the RDU. The options include: If the device detection extension is unable to identify the device type, the “default type” (CWMP or None) specifies the device type. If you set the Default Device Type as None, the device record is not added to the RDU. Unregistered devices can request the RDU for configurations only if you have enabled the service cwmp num allow-unknown-cpe option from the DPE command line interface. Otherwise, a request from an unknown device is not forwarded to the RDU. |
|
Identifies the maximum number of devices that you can troubleshoot at any one time. The default number is 100. |
|
Identifies if logging device record and device configurations is enabled or disabled. |
|
Identifies if logging of history of device operation initiated from the API using immediate mode is enabled or disabled. |
|
Identifies if logging of history of device operation initiated from the API using on-connect mode is enabled or disabled. |
|
Identifies if logging the history of device instruction generation is enabled or disabled. |
|
Defines the maximum number of entries of device history that will be stored for each device. The default number of entries is 40. |
|
Determines if statistics collection is enabled. See Monitoring Performance Statistics, on performance statistics. |
|
Enable this if you want to abbreviate the parameter names available in the configuration template. If enabled, parameter names are replaced with a dot (.). |
|
TACACS+ Defaults
When you click the TACACS+ Defaults link, the TACACS+ Defaults page appears.
Figure 17-5 TACACS+ Defaults Page
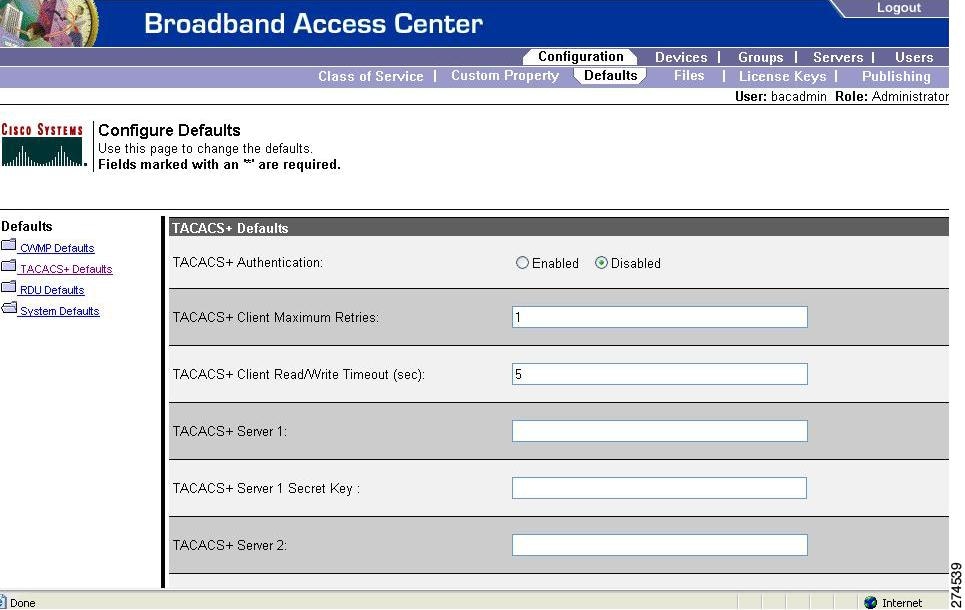
Table 17-6 describes all fields and buttons appearing in Figure 17-5.
If you remove one TACACS+ server and replace it with another server, the newly added server will have the same priority as the removed server.
To change the order of the TACACS+ servers in the priority list, remove all server addresses and re-enter them in the desired order.
Managing Files
By using the Cisco BAC administrator user interface, you can manage the template files and the parameter dictionaries for dynamic generation for CWMP files, or software images for devices (see Figure 17-6). You can add, delete, replace, or export any file type, including:
- Configuration Template—These are XML files that contain CWMP configuration policy, including parameter value settings, Notification attributes and Access Control attributes. See Authoring Configuration Templates, for additional information.
- Firmware File—These are images of device firmware, which can be downloaded to devices to upgrade their functionality. Cisco BAC treats this file type like any other binary file. See Firmware Management, for additional information.
- Firmware Rules Template—These are XML files written according to a published schema document. Each firmware rules template contains one or more rules that trigger firmware updates based on specific conditions. See Firmware Management, for additional information.
- JAR File—This file type is used to load Cisco BAC extensions.
- Parameter Dictionary—These are XML files that list valid objects and parameters used by Cisco BAC to configure a device. The dictionaries validate the objects and parameters used in the configuration and firmware rule templates. See Parameter Dictionaries, for additional information.
- Parameter List—These XML files list a predefined set of parameters from the device that are retrieved every time the device contacts Cisco BAC.
- DPE Extension Script—These script files are main extension scripts having the main provisioning logic. For more information on extension scripts, see Scripting Framework.
- Helper Script—These script files are utilities which can be used by multiple main extension scripts. The helper scripts are called from both the main extension scripts and other helper scripts.

Note![]() Figure 17-6 is displayed after clicking the Search button on the Manage Files page.
Figure 17-6 is displayed after clicking the Search button on the Manage Files page.
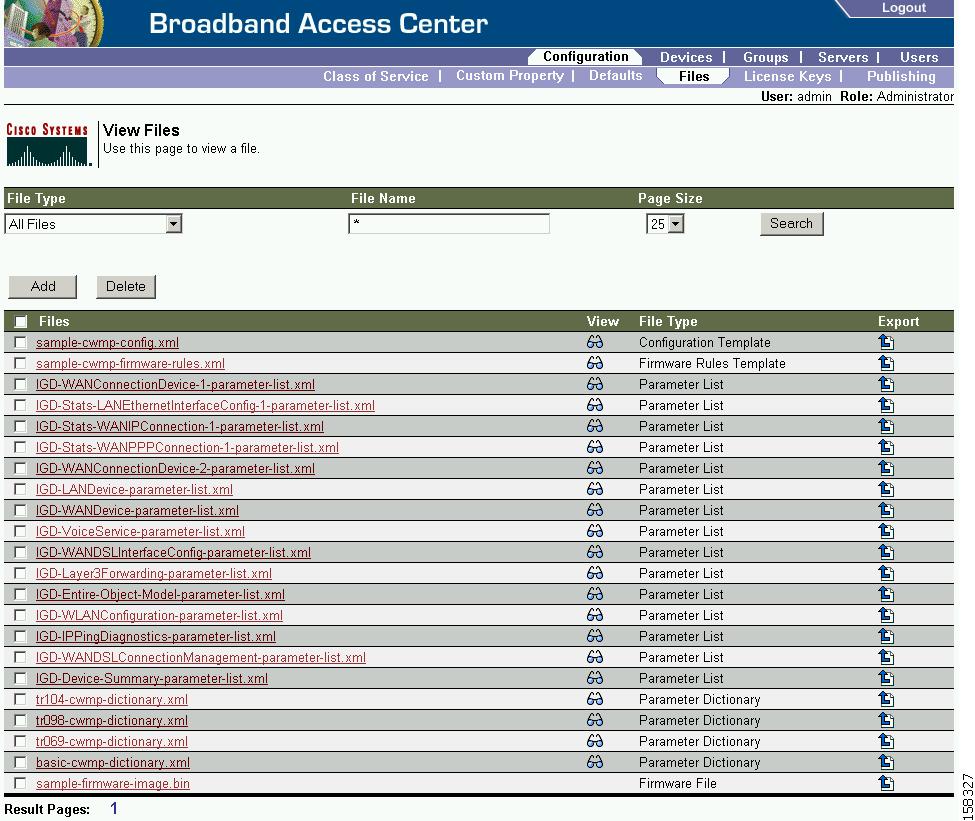
Table 17-7 identifies the fields and buttons shown in Figure 17-6.
Adding Files
To add an existing file to the RDU database:
Step 1![]() Choose Configuration on the Primary Navigation bar.
Choose Configuration on the Primary Navigation bar.
Step 2![]() Choose Files on the Secondary Navigation bar.
Choose Files on the Secondary Navigation bar.

Note![]() For Firmware file type, two additional fields are provided: Firmware Version and Description, both of which are purely informational. You can enter any string in these fields.
For Firmware file type, two additional fields are provided: Firmware Version and Description, both of which are purely informational. You can enter any string in these fields.
Step 5![]() Browse for the Source File Name.
Browse for the Source File Name.
By default, file sizes up to 20 MB are supported.
The View Files page appears to indicate that the file has been added.
Cisco BAC now extends the http file service so that it can read the firmware file from the DPE file system or DPE cache.
When the firmware image size is very large (say 100 MB), adding the file through RDU may not be efficient. These files can be manually transferred to all the DPEs using tools such as scp, ftp and later when device requests for these files, they can be transferred to the device from the DPE.
Viewing Files
To view the contents of a file:
Step 1![]() Choose Configuration on the Primary Navigation bar.
Choose Configuration on the Primary Navigation bar.
Step 2![]() Choose Files on the Secondary Navigation bar.
Choose Files on the Secondary Navigation bar.
Step 3![]() Search for the required file by using File Type.
Search for the required file by using File Type.
Step 4![]() Click the View Details icon (
Click the View Details icon ( ) corresponding to the File Type you had specified for a search.
) corresponding to the File Type you had specified for a search.
Replacing Files
Step 1![]() Choose Configuration on the Primary Navigation bar.
Choose Configuration on the Primary Navigation bar.
Step 2![]() Choose Files on the Secondary Navigation bar.
Choose Files on the Secondary Navigation bar.
Step 3![]() Select the link that corresponds to the file you want to replace from the search output list.
Select the link that corresponds to the file you want to replace from the search output list.
The Replace File page appears. Note that the selected filename already appears on this page.
Step 4![]() Browse for the source file to be used as a replacement for the displayed filename.
Browse for the source file to be used as a replacement for the displayed filename.
If you are updating a configuration or firmware template which is associated with a Class of Service, after submitting the replacement file, a confirmation page appears to indicate that Cisco BAC will regenerate instructions for the affected devices.
The Instruction Generation Service automatically regenerates instructions for all devices associated with this template using the Class of Service association and sends new instructions to the appropriate DPEs.
Exporting Files
You can copy files to your local hard drive by using the export function.

Note![]() The procedure described below assumes that you are using Internet Explorer. This procedure is different if you are using Netscape Navigator.
The procedure described below assumes that you are using Internet Explorer. This procedure is different if you are using Netscape Navigator.
Step 1![]() Choose Configuration on the Primary Navigation bar.
Choose Configuration on the Primary Navigation bar.
Step 2![]() Choose Files from the Secondary Navigation bar.
Choose Files from the Secondary Navigation bar.
Step 3![]() Identify the file that you want to export.
Identify the file that you want to export.
Step 5![]() Return to the Cisco BAC administrator user interface.
Return to the Cisco BAC administrator user interface.
Deleting Files
Complete this procedure to delete an existing file:
Step 1![]() Choose Configuration on the Primary Navigation bar.
Choose Configuration on the Primary Navigation bar.
Step 2![]() Choose Files on the Secondary Navigation bar.
Choose Files on the Secondary Navigation bar.
Step 3![]() In the Files area, enter the filename of the file that you want to modify.
In the Files area, enter the filename of the file that you want to modify.
The appropriate file appears in the Files list.
Step 5![]() Choose the appropriate file or files.
Choose the appropriate file or files.


Note![]() You cannot delete a file associated with a Class of Service. You must remove the Class of Service association before proceeding. See Configuring the Class of Service, for additional information.
You cannot delete a file associated with a Class of Service. You must remove the Class of Service association before proceeding. See Configuring the Class of Service, for additional information.
Managing License Keys
Software licenses are used to activate specific features or to increase the functionality of your installation. Each license is available as either a permanent license or an evaluation license.
- Permanent—A permanent license is purchased for use in your network environment and activates the specific features for which it is intended.
- Evaluation—An evaluation license enables functionality for a specific amount of time after installation. You can upgrade an evaluation license to a permanent license by entering a new permanent license number.

When you upgrade from an evaluation license to a permanent license, you do not have to re-install the software or reconfigure Cisco BAC. You simply have to provide the permanent license using the Cisco BAC administrator user interface.
The Manage License Keys page (Figure 17-7) displays a list of licenses that have been entered for your implementation. This Cisco BAC release supports both evaluation and permanent licenses for the CWMP-compliant devices, and DPEs. The status of each available license appears as active, expired, or identifies the expiration date.

Note![]() You can upgrade a permanent license to increase the number of authorized devices by adding an additional license. When you reach the limit of your number of licensed devices you cannot provision new devices, but existing devices that are already provisioned continue to receive service.
You can upgrade a permanent license to increase the number of authorized devices by adding an additional license. When you reach the limit of your number of licensed devices you cannot provision new devices, but existing devices that are already provisioned continue to receive service.
Figure 17-7 Manage License Keys Page
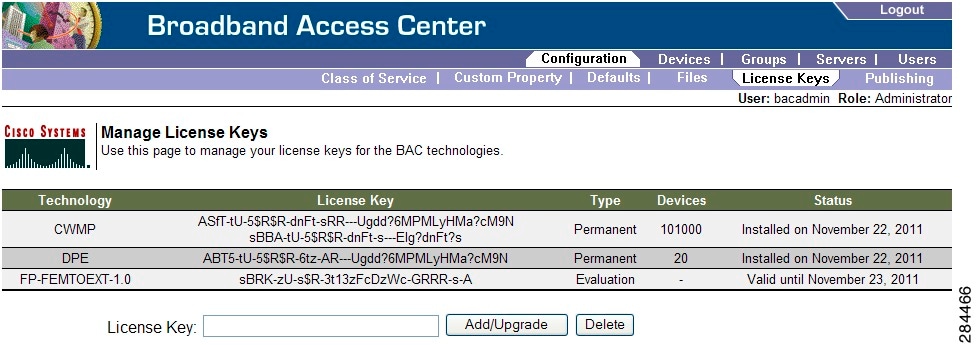
Adding and Modifying a License
To add, modify, or upgrade a license:
Step 1![]() Choose Configuration on the Primary Navigation bar.
Choose Configuration on the Primary Navigation bar.
Step 2![]() Choose License Keys on the Secondary Navigation bar.
Choose License Keys on the Secondary Navigation bar.
Step 3![]() Obtain your new license key from either your Cisco Systems representative or the Cisco Technical Assistance Center (TAC) website. See the Preface in this guide for TAC contact information.
Obtain your new license key from either your Cisco Systems representative or the Cisco Technical Assistance Center (TAC) website. See the Preface in this guide for TAC contact information.
Step 4![]() Enter the new license key in the License Key field.
Enter the new license key in the License Key field.
Step 5![]() Click Add/Upgrade to install the new license key.
Click Add/Upgrade to install the new license key.
Managing DPE Feature Pack Extensions
Cisco BAC provides a mechanism to license DPE feature packs extension. The feature pack licenses indicate the count of the devices that can be processed by the feature pack extension. The feature pack licenses can be added to the RDU through BAC admin UI (Configuration -> License Key) or API independently with or without CWMP or DPE licenses.
You must buy enough CWMP licenses to cover the number of devices that would use the feature pack extensions. For instance, if you buy a Femto feature pack license for X number of devices and DLC feature pack license for Y number of devices, then you must buy CWMP License for at least X+Y number of devices.
The feature pack licensing leverages BAC's existing licensing mechanism. Adding feature pack licenses to the RDU is similar to adding other licenses such as DPE and CWMP.
The DPE feature pack license is similar to RDU, DPE and CWMP license. However, in the case of DPE feature pack license, the MANIFEST of the DPE feature pack extension JAR should have the attribute Extension-Name defined and its value should be in the format FP- Technology Name - versionnumber.
FP —Denotes it is a feature pack license.
ExtensionName — DPE extension technology name. For example, Femto, DLC, CPEaaS.
VersionNumber — DPE extension technology version. This version number must be the same or lower than the version of the feature pack license added in DPE. If not, the DPE registration fails.
A few examples for FP- Technology Name - versionnumber would be FP-CPEaas-1.0, FP-CPEaas2.0, FP-Femto-10, FP-DLC-1.0 and so on.
Writing a New Class for DPE Feature Pack Extensions
This procedure illustrates how to write a new class for DPE feature pack extension. This section also provides details about how to add a new class and integrate it with the DPE.
Step 1![]() Create a Java source file for the custom publishing extension, and compile it.
Create a Java source file for the custom publishing extension, and compile it.
Step 2![]() Create a manifest file for the JAR file that will contain the extension class.
Create a manifest file for the JAR file that will contain the extension class.
For detailed information on creating a manifest file and using the command-line JAR tool, see Java documentation.
Manifest-Version: 1.0
Ant-Version: Apache Ant 1.6.2
Created-By: 17.0-b16 (Sun Microsystems Inc.)
Implementation-Title: Cisco Broadband Access Center Femtocell Extension
Implementation-Version: FEMTOEXT 3.7 (test-build)
Implementation-Vendor: Cisco Systems, Inc.
Extension-Name: FP-femtoext-3.7
Java JAR file manifests contain attributes that are formatted as name-value pairs and support a group of attributes that provide package versioning information.

Note![]() Cisco BAC accepts only those extension JAR files that include a manifest with the Extension-Name attribute in the files.
Cisco BAC accepts only those extension JAR files that include a manifest with the Extension-Name attribute in the files.
Step 3![]() For each new class being subclassed, create a mapping file in the directory META-INF/services.
For each new class being subclassed, create a mapping file in the directory META-INF/services.
The name of the mapping file is the same as the new class being subclassed. This mapping file contains the names of the new subclasses of that class.
For example create the mapping file:
This file consists of the following:
Step 4![]() Create the JAR file for the custom extension point in the directory <BAC_HOME>/dpe/conf/.
Create the JAR file for the custom extension point in the directory <BAC_HOME>/dpe/conf/.

Note![]() You can give the JAR file any name. The name can be descriptive, but do not duplicate another existing JAR filename.
You can give the JAR file any name. The name can be descriptive, but do not duplicate another existing JAR filename.
Managing RDU Extensions
Creating a custom extension point is a programming activity that can, when used with the Cisco BAC administrator user interface, allow you to augment Cisco BAC behavior or add support for new device technologies.
Before familiarizing yourself with managing extensions, you should know the RDU extension points that Cisco BAC requires. At least one disruption extension must be attached to the associated technology’s disruption extension point when disrupting devices on behalf of a batch.
Table 17-8 lists the RDU extension points that Cisco BAC requires to execute extensions.

Note![]() You can specify multiple extension points by making them run one after another. You do this by specifying the extensions points in a comma-separated list.
You can specify multiple extension points by making them run one after another. You do this by specifying the extensions points in a comma-separated list.
Writing a New Class for RDU
This procedure illustrates the entire custom extension creation process. You can create many different types of extensions; for the purposes of this procedure, a new Publishing Extension Point is used.
Step 1![]() Create a Java source file for the custom publishing extension, and compile it.
Create a Java source file for the custom publishing extension, and compile it.
Step 2![]() Create a manifest file for the JAR file that will contain the extension class.
Create a manifest file for the JAR file that will contain the extension class.
For detailed information on creating a manifest file and using the command-line JAR tool, see Java documentation.
Java JAR file manifests contain attributes that are formatted as name-value pairs and support a group of attributes that provide package versioning information.
While Cisco BAC accepts extension JAR files that do not contain this information, we recommend that you include a manifest with versioning information in the files to track custom RDU extensions.
You can view manifest information from the administrator user interface using the Servers > RDU > View Regional Distribution Unit Details page.
Detailed information on the installed extension JAR files and the loaded extension class files appears after the Device Statistics section. You can view manifest information from the RDU logs also.
Step 3![]() Create the JAR file for the custom extension point.
Create the JAR file for the custom extension point.

Note![]() You can give the JAR file any name. The name can be descriptive, but do not duplicate another existing JAR filename.
You can give the JAR file any name. The name can be descriptive, but do not duplicate another existing JAR filename.
New Class for DNPrefix Extension
For constructing Grid-ID and DNPrefix extension, a new class - FormatValidatorExtension - is included in the jar file, formatvalidatorext.jar, which is available in BAC_3.10_RDU_FORMATVALIDATORExtension.gtar.gz (part of the release bundle). You need to install this.jar file in the RDU to support construction of FC-GRID-ID and FC-DN-PREFIX (see Installing RDU Custom Extensions).
Installing RDU Custom Extensions
After a Jar file is created, use the administrator user interface to install it:
Step 1![]() To add the new Jar file, see Adding Files.
To add the new Jar file, see Adding Files.
Use the Browse function to locate the Jar file created in the procedure, Writing a New Class for RDU, and select this file as the Source File; leaving the File Name blank assigns the same filename for both source and external. The filename is what you will see through the administrator user interface.
Step 3![]() Return to the RDU Defaults page and note that the newly added Jar file appears in the Extension Point Jar File Search Order field.
Return to the RDU Defaults page and note that the newly added Jar file appears in the Extension Point Jar File Search Order field.
Step 4![]() Enter the extension class name in the Publishing Extension Point field.
Enter the extension class name in the Publishing Extension Point field.
The RDU returns an error if the class name does not exist within the jar file or if Cisco BAC detects any other errors. This error occurs mostly when replacing a Jar file, if, for example, the class you set up is not found in the replacement Jar file.
Step 5![]() Click Submit to commit the changes to the RDU database.
Click Submit to commit the changes to the RDU database.
Step 6![]() View the RDU extensions to ensure that the correct extensions are loaded.
View the RDU extensions to ensure that the correct extensions are loaded.
Viewing RDU Extensions
You can view the attributes of all RDU extensions directly from the View Regional Distribution Unit Details page. This page displays details on the installed extension Jar files and the loaded extension class files.
Publishing Provisioning Data
Cisco BAC has the capability to publish the provisioning data it tracks to an external datastore in real time. To do this, a publishing plug-in must be developed to write the data to the desired datastore. The Manage Publishing page identifies information such as the plug-in name, its current status (whether it is enabled or disabled), and switch to enable or disable it.
You can enable as many plug-ins as required by your implementation but care must be exercised because the use of publishing plug-ins can decrease system performance.

Note![]() Cisco BAC does not ship with any publishing plug-ins. You must create your own plug-ins and load them into Cisco BAC in the same way as JAR files are (see Adding Files). Then, manage the plug-ins from the Manage Publishing page.
Cisco BAC does not ship with any publishing plug-ins. You must create your own plug-ins and load them into Cisco BAC in the same way as JAR files are (see Adding Files). Then, manage the plug-ins from the Manage Publishing page.
Publishing Datastore Changes
To enable or disable a publishing plug-in:
Step 1![]() Choose Configuration on the Primary Navigation bar.
Choose Configuration on the Primary Navigation bar.
Step 2![]() Choose Publishing on the Secondary Navigation bar.
Choose Publishing on the Secondary Navigation bar.
The Manage Publishing page appears. This page displays a list of all available database plug-ins and identifies the current status of each. C
Step 3![]() Click on the appropriate status indicator to enable or disable the required plug-in. Note that as you click the status, it toggles from enabled to disabled.
Click on the appropriate status indicator to enable or disable the required plug-in. Note that as you click the status, it toggles from enabled to disabled.
Modifying Publishing Plug-In Settings
These settings are a convenient way for plug-in writers to store plug-in settings in the RDU for their respective datastore. To modify the publishing plug-in settings:
Step 1![]() Choose Configuration on the Primary Navigation bar.
Choose Configuration on the Primary Navigation bar.
Step 2![]() Choose Publishing on the Secondary Navigation bar,
Choose Publishing on the Secondary Navigation bar,
The Manage Publishing page appears.
Step 3![]() Click the link corresponding to the plug-in you want to modify.
Click the link corresponding to the plug-in you want to modify.
The Modify Publishing Plug-Ins page appears.
Table 17-9 identifies the fields shown in the Modify Publishing Plug-Ins page.
Step 4![]() Enter the required values in the Server, Port, IP Address, User, Password, and Confirm Password fields. These are all required fields and you must supply this information before proceeding.
Enter the required values in the Server, Port, IP Address, User, Password, and Confirm Password fields. These are all required fields and you must supply this information before proceeding.
Click Submit to make the changes to the selected plug-in, or click Reset to clear all fields on this page.
Configuring Lease Query
Cisco BAC, by default, binds to the IP addresses and ports that are described in the below table.
|
|
|
|
|---|---|---|
The wildcard is a special local IP address. It usually means "any" and can only be used for bind operations.
You can also configure the IP address and port of your choice for lease query communication using the same properties. For example:
/cnrQuery/clientSocketAddress=10.1.2.3:166
Using this property, the DPE binds to the IP address and the port that you specify.
Updating the Location of FAP at Group Level in the Grid
Cisco BAC identifies the location of an anchor Femtocell Access Point (FAP) (or anchor FAP) within a grid. This location is updated at group or subgroup level so that other devices in the grid are also updated with the location details of the same anchor FAP.
For details about the creation of group or subgroup, see Group Management.
To achieve this location verification (LV) at group or subgroup level, Cisco BAC uses three custom properties that are associated with chained intra grid (CIG), and need to be defined at device level:
Cisco BAC also skips location verification of other devices in the same grid if one of the connected devices has successfully verified the location of the anchor FAP.
The properties of the anchor FAP, which are updated at group level are:
- FC-CIG-GPS-LAT — GPS latitude value
- FC-CIG-GPS-LONG — GPS longitude value
- FC-CIG-GPS-LOCK-TS — GPS lock timestamp
- FC-CIG-ANCHOR-AP-EID — DeviceID of the anchor FAP
- FC-CIG-GPS-DISTANCE — GPS distance value
- FC-ANCHOR-GPS-LOCK — Status (boolean) of anchor FAP GPS lock
The properties of the anchor FAP, which are updated at subgroup level are:
- FC-CIG-GPS-LAT — GPS latitude value
- FC-CIG-GPS-LONG — GPS longitude value
- FC-CIG-GPS-LOCK-TS — GPS lock timestamp
- FC-CIG-ANCHOR-AP-EID — DeviceID of the anchor FAP
- FC-CIG-GPS-DISTANCE — GPS distance value
- FC-SUBSITE-ANCHOR-GPS-LOCK — Status (boolean) of subgroup anchor FAP GPS lock
The property of the anchor FAP, which is updated at device level, is FC-CURRENT-GPS-LOCK — Status (boolean) of current GPS lock
Configuring BAC and the Device for CIG
To configure Cisco BAC and the device for chained intra grid (CIG) in the Admin UI:
Step 1![]() In the BAC RDU Admin UI, configure the Chained Grid Group Generation configuration extension.
In the BAC RDU Admin UI, configure the Chained Grid Group Generation configuration extension.
Go to Configuration > Defaults > Configuration Generation Extension Point, and enter the following extension name –
com.cisco.provisioning.cpe.extensions.builtin.generation.ChainedGridGroupGeneration
Step 2![]() For all the devices in the grid, configure the following custom properties to be available in /IPDevice/properties/available/pg :
For all the devices in the grid, configure the following custom properties to be available in /IPDevice/properties/available/pg :
Step 3![]() For all the devices in the grid, set the following values for the properties:
For all the devices in the grid, set the following values for the properties:
Here group type is the name of the group type that is related to the device. This also supports comma-separated values (multiple group type names), and is helpful if subgroups are used in the configuration.
For the anchor FAP, if the GPS location identified by the property, FC-ANCHOR-AP-LV-LIST, is valid at the first time, this location information is updated at group or subgroup level.
This means, if FC-ANCHOR-AP-LV-LIST=GPS, then the location information is updated at group or subgroup level.
To identify the name of group type to update, the value provided for the property FC-CIG-GROUP-TYPE is used. The corresponding group name is retreived from the DPE, and the anchor FAP details are updated for that group or subgroup.
Later, if the GPS location of the anchor FAP changes, the new location is also updated in each associated device (of the same group or subgroup) using the above properties.

Note![]() After the anchor FAP is identified, if its GPS location is invalid, or if the anchor FAP itself is blocked or it reports benchmark failure, the anchor FAP details are also deleted at group and subgroup level. During the next reboot, another FAP, which has successfully verified the location, becomes the anchor FAP.
After the anchor FAP is identified, if its GPS location is invalid, or if the anchor FAP itself is blocked or it reports benchmark failure, the anchor FAP details are also deleted at group and subgroup level. During the next reboot, another FAP, which has successfully verified the location, becomes the anchor FAP.
If the parent anchor FAP is removed, the parent group is updated with another anchor FAP taken from one of the subgroups.
BAC triggers a group update event whenever a Group/Sub Group in BAC is getting either added or deleted with Anchor AP details.
If the property FC-CIG-ENABLED is set to true for a device, it sends a request to know the connected FAP’s DeviceID within the grid. This request is sent only after the GPS, REM 2G, REM 3G, or REM 4G scan is completed for the device.
As a response to this request, if the anchor FAP DeviceId is present in the connected FAP’s DeviceId, then the CIG is successfull.
Updating the Location of FAP at Chassis Level
In Cisco BAC, you can use the Chained Intra Chassis (CIC) Location Verification to skip the location verification on one technology type (either 3G or 4G) from same chassis, if the other technology type has already completed the location verification. This method is applicable together with other location verification methods like GPS, CIG, REM scan and so on.
Cisco BAC identifies the location of an anchor Femtocell Access Point (FAP) (or anchor FAP) based on the configured location verification methods. If all the configured location verification methods are successful and there is no peer RAT or the neighbor device in the same chassis has no details of anchor FAP, then the current device becomes an anchor FAP within the chassis.
To achieve this location verification at chassis level, Cisco BAC uses the following custom properties that are associated with chained intra chassis (CIC):
- FC-CIC-ENABLED - Need to be always set as true to update the remaining custom properties (shown below) in the device record
- FC-CIC-STATUS
- FC-CIC-STATUS-TS
- FC-CIC-ANCHOR-AP-EID
- FC-CHASSIS-ID
- FC-PEER-RAT-ID
Cisco BAC also skips location verification of other devices or peer devices in the same chassis if one of the connected device has successfully passed the location verification and it is an anchor FAP. The anchor AP details will be updated on the current device.
Configuring BAC and the Device for CIC
To configure Cisco BAC and the device for chained intra chassis (CIC) in Admin UI:
Step 1![]() Configure the following custom properties related to Chained Intra Chassis location verification in Configuration > Custom Property > Manage BAC Custom Properties, using Add :
Configure the following custom properties related to Chained Intra Chassis location verification in Configuration > Custom Property > Manage BAC Custom Properties, using Add :
Step 2![]() For all the devices in the chassis, configure the following custom properties to be available in /IPDevice/properties/available/pg :
For all the devices in the chassis, configure the following custom properties to be available in /IPDevice/properties/available/pg :

Note![]() FC-CIC-ENABLED is applicable at Device, CoS, Group, and Provisioning Group levels.
FC-CIC-ENABLED is applicable at Device, CoS, Group, and Provisioning Group levels.

Note![]() After the anchor FAP is identified, if the anchor FAP itself is blocked or it reports benchmark failure or if a shutdown occurs, the anchor FAP details are deleted for all devices on the chassis. During the next reboot, another FAP, which has successfully verified the chassis location, becomes the anchor FAP.
After the anchor FAP is identified, if the anchor FAP itself is blocked or it reports benchmark failure or if a shutdown occurs, the anchor FAP details are deleted for all devices on the chassis. During the next reboot, another FAP, which has successfully verified the chassis location, becomes the anchor FAP.
If the property FC-CIC-ENABLED is set to false or removed for a device, then when the device reboot occurs, it checks if it was an anchor FAP previously, and removes the anchor FAP details. The neighbor device or peer device anchor FAP details are removed after reboot.
Configuring Location Verification for UMTS
The FAP location verification method for UMTS can be configured in Cisco BAC. You can:
- Delay the GPS verification for the FAP during initial boot up, before the NWL based location verification is initiated
- Ensure that the NWL benchmark is updated if the DNM location verification of FAP is successful, even though DNB location verification is not successful
To configure delayed GPS verification during the initial boot up, use the custom property FC-GPS-TIME-OUT, and set the required value (in seconds). This ensures that, if the initial GPS location verification is Unknown or Time out, the location verification method waits for sometime (as specified by FC-GPS-TIME-OUT), before proceeding to NWL based location verification.
To give priority for DNM location verification, use the custom property FC-DNM-BENCHMARK-UPDATE. The default value is true, which ensures that the NWL benchmark is updated if DNM location verification is successful and DNB is not successful (Failure).
You can also define the action to be taken for DNB location verification failure, using the custom property FC-DNB-FAIL-ACTION:
Configuring 2G Scan and 3G Scan Capability of LTE
Cisco BAC provides the option to discover the 2G scan and 3G scan capability of LTE and use it for location verification, even though the custom parameters FC-2G-REM-SCAN and FC-3G-REM-SCAN are set to true for the device.
To discover these capabilities from the LTE, go to Configuration > Defaults > CWMP Defaults > Custom Discover Parameters, and enter the following:
The technology type REM scan is completed for the LTE only if these discovered parameters are also true.
Configuring Static Neighbor List of LTE
Cisco BAC helps you to define the entire neighbor list configuration of an LTE, without considering the detected neighbors by the LTE as a result of the REM scan process. This release supports inter-RAT configuration, and you can configure up to 32 instances for the inter-RAT table.
To achieve this, you need to first disable the REM scan process, by setting the following parameters (described in the TR-196 Issue 2 Femto Access Point Service Data Model (FAPService:2.0)) to false :
To set the neighbor list of LTE, you can create a configuration template and assign values to all the parameters under the following objects:
- .FAPService.{i}.CellConfig.LTE.RAN.NeighborList.LTECell.{i}
- .FAPService.{i}.CellConfig.LTE.RAN.NeighborList.InterRATCell.UMTS.{i}
- .FAPService.{i}.CellConfig.LTE.RAN.NeighborList.InterRATCell.GSM.{i}
- .FAPService.{i}.CellConfig.LTE.RAN.NeighborList.InterRATCell.CDMA2000.{i}
Cisco BAC also supports reading values from the neighbor list that is used by the LTE. You can create configuration template to read values for all the parameters under the following objects:
- .FAPService.{i}.CellConfig.LTE.RAN.NeighborListInUse.LTECell.{i}
- .FAPService.{i}.CellConfig.LTE.RAN.NeighborListInUse.InterRATCell.UMTS.{i}
- .FAPService.{i}.CellConfig.LTE.RAN.NeighborListInUse.InterRATCell.GSM.{i}
- .FAPService.{i}.CellConfig.LTE.RAN.NeighborListInUse.InterRATCell.CDMA2000.{i}
Example 17-1 Sample Configuration Template for Setting the Neighbor List
Configuring Remote Reset for Tampered LTE FAP
Cisco BAC identifies tampered LTE FAPs and provides the option to remotely reset those devices. This avoids the need to manually reset the tampered device at the location.
Step 1![]() Configure the following custom properties to be available in /IPDevice/properties/available/pg, for the LTE FAP:
Configure the following custom properties to be available in /IPDevice/properties/available/pg, for the LTE FAP:
Step 2![]() Set the properties FC-TAMPERED-ENABLED= true and FC-TAMPER-CLEAR= true.
Set the properties FC-TAMPERED-ENABLED= true and FC-TAMPER-CLEAR= true.
If the device gets tampered, the reset happens as the value of FC-TAMPER-CLEAR is true. This enables the device for initialization and further processing according to the flow.

Note![]() After the reset, the FC-TAMPER-CLEAR property gets removed from /IPDevice/properties/available/pg. You need to add it again for subsequent reset.
After the reset, the FC-TAMPER-CLEAR property gets removed from /IPDevice/properties/available/pg. You need to add it again for subsequent reset.
If FC-TAMPER-CLEAR is set to false and the device gets tampered, then FC-TAMPERED is automatically set to true, and this stops the initialization and further processing of the device.
 ) and you are prompted to either open the file or save it.
) and you are prompted to either open the file or save it.
 Feedback
Feedback