- Preface
- Using the WAAS Command-Line Interface
- Cisco WAAS Software Command Summary
- CLI Commands
- EXEC Mode Commands
- Global Configuration Mode Commands
- Interface Configuration Mode Commands
- Standard ACL Configuration Mode Commands
- Extended ACL Configuration Mode Commands
- Preposition Configuration Mode Commands
- PKI Certification Authority Configuration Mode Commands
- PKI Global Settings Configuration Mode Commands
- SSL Accelerated Service Configuration Mode Commands
- SSL Cipher List Configuration Mode Commands
- SSL Global Service Configuration Mode Commands
- SSL Host Peering Service Configuration Mode Commands
- SSL Management Service Configuration Mode Commands
- WCCP Configuration Mode Commands
- Service Context Configuration Mode Commands
- Service Node Group Configuration Mode Commands
- Service Node Configuration Mode Commands
- Service Context Configuration Mode Commands
- Class Map Configuration Mode Commands
- Policy Map Configuration Mode Commands
- Policy Map Class Configuration Mode Commands
- Acronyms and Abbreviations
- Command Summary by Mode
Cisco Wide Area Application Services Command Reference 6.4.1x
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- October 18, 2018
Chapter: EXEC Mode Commands
- cd
- clear arp-cache
- clear bmc
- clear cache
- clear cache http-object-cache invalidate
- clear cdp
- clear connection
- clear dre
- clear ip
- clear ip v6
- clear license
- clear logging
- clear object-cache
- clear service-policy
- clear statistics
- clear statistics accelerator
- clear statistics accelerator http object-cache
- clear statistics connection
- clear statistics monitor appnav-controller traffic
- clear statistics vn-service vpath
- clear transaction-log
- clear users
- clear windows-domain
- clear windows-domain-log
- clock
- cms
- cms secure-store
- configure
- copy disk
- copy ftp
- copy http
- copy monitoring-log
- copy running-config
- copy scp
- copy secure-http
- copy startup-config
- copy sysreport
- copy system-status
- copy tech-support
- copy tftp
- cpfile
- crypto delete
- crypto export
- crypto generate
- crypto import
- crypto pki
- debug aaa accounting
- debug aaa authorization
- debug accelerator
- debug accelerator http object-cache
- debug accelerator mapi rpchttp -layer
- debug all
- debug appnav-controller connection
- debug appnav-controller drop capture
- debug authentication
- debug auto-discovery
- debug buf
- debug cdp
- debug cli
- debug cmm
- debug cms
- debug connection
- debug controllers
- debug dataserver
- debug dhcp
- debug dre
- debug egress-method
- debug encryption-service
- debug fda
- debug fdm
- debug filtering
- debug flow
- debug generic-gre
- debug hw-raid
- debug imd
- debug inline
- debug key-manager
- debug logging
- debug monapi
- debug nplogd
- debug ntp
- debug object-cache database
- debug object-cache existence-cache
- debug object-cache load-monitor
- debug punt
- debug rbcp
- debug rmd
- debug rpc
- debug service-insertion
- debug service-policy
- debug snmp
- debug standby
- debug statistics
- debug synq
- debug tfo
- debug translog
- debug wafs
- debug wccp
- delfile
- deltree
- dir
- disable
- disk
- dnslookup
- enable
- exit
- find-pattern
- help
- install
- less
- license add
- lls
- ls
- lsusb
- mkdir
- mkfile
- monitor appnav-controller traffic
- ntpdate
- packet-capture
- ping
- ping6
- pwd
- reload
- rename
- restore
- rmdir
- scp
- script
- setup
- show aaa accounting
- show aaa authorization
- show accelerator
- show accelerator http object-cache
- show alarms
- show appnav-controller flow-distribution
- show arp
- show authentication
- show auto-discovery
- show auto-register
- show banner
- show bmc
- show bridge
- show cache http-metadatacache
- show cache object-cache
- show cdp
- show class-map
- show clock
- show cms
- show cms secure-store
- show crypto
- show debugging
- show device-id
- show device-mode
- show disks
- show dre
- show filtering list
- show flash
- show flow record
- show hardware
- show hosts
- show inetd
- show interception-method
- show interface
- show inventory
- show ip access-list
- show ip routes
- show ipv6
- show kdump
- show kerberos
- show key-manager
- show license
- show logging
- show memory
- show monitor
- show ntp
- show peer optimization
- show policy-map
- show policy-sub-class
- show processes
- show radius-server
- show reload
- show running-config
- show service-insertion
- show service-policy
- show services
- show smb-conf
- show snmp
- show ssh
- show startup-config
- show statistics accelerator
- show statistics accelerator http object-cache
- show statistics accelerator http preposition
- show statistics aoim
- show statistics application
- show statistics appnav-controller
- show statistics authentication
- show statistics auto-discovery
- show statistics class-default
- show statistics class-map
- show statistics connection
- show statistics connection auto-discovery
- show statistics connection closed
- show statistics connection conn-id
- show statistics connection egress-methods
- show statistics connection optimized
- show statistics connection pass-through
- show statistics crypto ssl ciphers
- show statistics datamover
- show statistics dre
- show statistics encryption-services
- show statistics filtering
- show statistics flow
- show statistics generic-gre
- show statistics icmp
- show statistics icmp6
- show statistics ip
- show statistics ipv6
- show statistics monitor appnav-controller traffic
- show statistics netstat
- show statistics pass-through
- show statistics peer
- show statistics policy-sub-class
- show statistics punt
- show statistics radius
- show statistics service-insertion
- show statistics services
- show statistics sessions
- show statistics snmp
- show statistics synq
- show statistics system cpu
- show statistics tacacs
- show statistics tcp
- show statistics tfo
- show statistics udp
- show statistics vn-service vpath
- show statistics wccp
- show statistics windows-domain
- show synq list
- show sysfs volumes
- show tacacs
- show tcp
- show tech-support
- show telnet
- show tfo tcp
- show transaction-logging
- show user
- show users administrative
- show version
- show wccp
- show windows-domain
- show windows-domain encrypted services
- shutdown
- ssh
- tcpdump
- telnet
- terminal
- test
- tethereal
- top
- traceroute
- traceroute6
- transaction-log
- type
- type-tail
- vm
- waas-tcptrace
- whoami
- windows-domain
- write
- zzdebugshell
EXEC Mode Commands
Use the EXEC mode for setting, viewing, and testing system operations. In general, the user EXEC commands allow you to connect to remote devices, change terminal line settings on a temporary basis, perform basic tests, and list system information.
The EXEC mode is divided into two access levels: user and privileged.
The user EXEC mode is used by local and general system administrators, while the privileged EXEC mode is used by the root administrator. Use the enable and disable commands to switch between the two levels. Access to the user-level EXEC command line requires a valid password.
The user-level EXEC commands are a subset of the privileged-level EXEC commands. The user-level EXEC prompt is the hostname followed by a right angle bracket (>). The prompt for the privileged-level EXEC command line is the pound sign (#). To execute an EXEC command, enter the command at the EXEC system prompt and press the Return key.

Note![]() You can change the hostname using the hostname global configuration command.
You can change the hostname using the hostname global configuration command.
The following example shows how to access the privileged-level EXEC command line from the user level:
To leave EXEC mode, use the exit command at the system prompt:
cd
To change from one directory to another directory in the WAAS software, use the cd EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use this command to navigate between directories and for file management. The directory name becomes the default prefix for all relative paths. Relative paths do not begin with a slash (/). Absolute paths begin with a slash (/).
Examples
The following example shows how to change to a directory using a relative path:
The following example shows how to change to a directory using an absolute path:
Related Commands
clear arp-cache
To clear the ARP cache, use the clear arp-cache EXEC command.
clear arp-cache [ ipaddress | interface { GigabitEthernet slot/port | PortChannel index | Standby grpNumber | TenGigabitEthernet slot/port | InlinePort slot/grpnumber {lan | wan} }]
Syntax Description
(Optional) Clears all ARP entries on the designated interface. |
|
Clears the inline port interface (slot/group). Specify lan for the LAN interface or wan for the WAN interface. |
Defaults
No default behavior or values.
Note that on ISR-WAAS, the default-gateway (ISR host's interface address) cannot be cleared from ARP cache.
Command Modes

Device Modes

Examples
The following example shows how to clear the ARP cache on the WAAS device:
Related Commands
clear bmc
To clear the BMC logs and events, use the clear bmc EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to clear the entries recorded in the BMC system event log on the WAAS device:
Related Commands
clear cache
To clear cached objects, use the clear cache EXEC command.
clear cache http-metadatacache https {conditional-response | redirect-response | unauthorized-response }
clear cache http-metadatacache { all | conditional-response | redirect-response | unauthorized-response} [ url ]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
After you use the clear cache dre command, the first 1 MB of data is not optimized. The Cisco WAAS software does not optimize the first 1 MB of data after a restart of the tcpproxy service. The data that is transmitted after the first 1 MB of data will be optimized according to the configured policy.
The clear cache dre command may cause the system to reboot, but you are asked to confirm before the command continues and you are given a chance to save any configuration changes that have been made to the running configuration.
The clear cache dre command does not delete the DRE cache contents but expires it by removing markers in the content to prevent reuse. If you want to delete the cache contents, use the disk delete-data-partitions command.
Examples
The following example shows how to clear the HTTP metadata cache for conditional responses:
Related Commands
clear cache http-object-cache invalidate
To clear the object cache, use the clear cache http object-cache EXEC command.
clear cache http-object-cache invalidate

Command Default


Command Modes


Device Modes Default


Usage Guidelines

This command clears all entries in the cache directory as a background task, but leaves entries up to 60 seconds prior to the command being given. It can take a few minutes to complete, but the CE is functional while the process is ongoing. Data on the disk remains and is not overwritten. Log entries appear indicating the beginning and end of the operation.

Examples

The following example shows how to clear the HTTP object cache:
clear cdp
To clear Cisco Discovery Protocol statistics, use the clear cdp EXEC command.
clear cdp { counters | table }
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to clear the CDP counter statistics on the WAAS device:
Related Commands
clear connection
To reset one or more connections, use the clear connection EXEC command.
clear connection [ client-ip { ip_address | hostname } | client-port port | flow-id id | server-ip { ip_address | hostname } | server-port port]
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to reset connection number 45 on the WAAS device:
The following example shows how to reset connections with server port 80 on the WAAS device:
Related Commands
clear dre
To clear DRE configurations, use the clear dre EXEC command.
clear dre auto-bypass [ { ip_address | hostname } port ]
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to clear all DRE auto-bypass entries :
The following example shows how to clear the DRE auto-bypass entry for a specific port on a specific server :
Related Commands
clear ip
To clear IP access list statistics, use the clear ip EXEC command.
clear ip access-list counters [ acl-num | acl-name ]
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to clear the IP access list counters on the WAAS device:
Related Commands
clear ipv6
To clear IPv6 neighbor cache entries, use the clear ipv6 neighbors EXEC command.
clear ipv6 neighbors {GigabitEthernet [slot number/port] | Portchannel [Etherchannel index] | standby [standby index] }
clear ipv6 neighbors virtual slot/port
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to clear the neighboring cache entries for a GigabitEthernet interface on the WAAS device:
Related Commands
clear license
To clear licensing configuration, use the clear license EXEC command.
clear license [ license-name ]
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to clear the licensing configuration on the WAAS device:
Related Commands
clear logging
To clear syslog messages saved in a disk file, use the clear logging EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The clear logging command removes all current entries from the syslog.txt file but does not make an archive of the file. It puts a “Syslog cleared” message in the syslog.txt file to indicate that the syslog has been cleared.
Examples
The following example shows how to clear all entries in the syslog.txt file on the WAAS device:
Related Commands
clear object-cache
To remove objects from object cache that match specified criteria, use the clear object-cache EXEC command.
clear object-cache [accelerator smb] all
Syntax Description
Defaults

Command Modes


Device Modes Default


Usage Guidelines

The clear object-cache command removes all objects from the object cache, or all objects from cache that match specified criteria,

Examples

The following example shows how to clear objects from object cache that match the criteria of the SMB AO and the URL www.sampletestdomain.com.
WAE# clear object-cache accelerator http url www.sampletestdomain.com

Related Commands

clear service-policy
To clear class map and policy map counters for AppNav and optimization policies, use the clear service-policy EXEC command.
clear service-policy [ type { appnav | waas }] counters
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
When specified without the type keyword, this command clears counters for both AppNav and WAAS optimization class maps and policy maps.
Examples
The following example shows how to clear both AppNav and WAAS optimization class map and policy map counters:
The following example shows how to clear only AppNav class map and policy map counters:
Related Commands
clear statistics
To reset statistics data, use the clear statistics EXEC command.
clear statistics { all | aoim | appnav-controller all | authentication | auto-discovery { all | blacklist } | class-map { appnav | waas } | datamover | dre [ global ] | exporter | filtering | flow monitor type performance-monitor tcpstat-v1 | generic-gre | icmp | inline | ip | ipv6 {internal} | pass-through | peer dre | punt | radius | service-insertion { appnav-controller ip_address | appnav-controller-group | data-path | service-context | service-node ip_address | service-node-group name } | snmp | synq | tacacs | tcp | tfo | udp | wccp | windows-domain | windows-print }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The clear statistics command clears all statistical counters from the parameters given. Use this command to monitor fresh statistical data for some or all features without losing cached objects or configurations.
Not all command options are applicable for a device in central-manager mode.
Note that from software version 6.x onwards, clear statistics snmp does not clear all statistical counters due to net snmp implementation.
Examples
The following example shows how to clear all authentication, RADIUS and TACACS+ information on the WAAS device:
Related Commands
clear statistics accelerator
To clear all global statistics, use the clear statistics accelerator EXEC command.
clear statistics accelerator { epm | generic | http | mapi | smb | ssl }
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to clear the statistics for the SMB application accelerator on the WAAS device:
Related Commands
clear statistics accelerator http object-cache
To clear object cache statistics for a WAAS device, use the clear statistics accelerator HTTP object-cache EXEC command.
clear statistics accelerator http object-cache

Syntax Description


Command Default


Command Modes


Device Modes Default


Usage Guidelines


Example

The following example shows how to clear object cache statistics for a WAAS device.

Related Commands

clear statistics connection
To clear connection statistics, use the clear statistics connection EXEC command.
clear statistics connection conn-id connection_id
clear statistics connection optimized [ client-ip { ip_address | hostname } | client-port port | { epm | http | ica | mapi | smb | ssl | tfo | wansecure } dre | peer-id peer_id | server-ip { ip_address | hostname } | server-port port]
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to clear the connection 1 statistics on the WAAS device:
Related Commands
clear statistics monitor appnav-controller traffic
To clear traffic monitoring statistics for an AppNav Controller Interface Module, use the clear statistics monitor appnav-controller traffic EXEC command.
clear statistics monitor appnav-controller traffic
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to clear the traffic monitoring statistics:
Related Commands
clear statistics vn-service vpath
To clear VPATH statistics for your vWAAS device, use the clear statistics vn-service vpath EXEC command.
clear statistics vn-service vpath
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The clear statistics vn-service vpath command removes all current entries from the syslog.txt file but does not make an archive of the file. It puts a “Syslog cleared” message in the syslog.txt file to indicate that the syslog has been cleared.
Examples
The following example shows how to clear all VPATH entries in the syslog.txt file on the vWAAS device:
Related Commands
clear transaction-log
To archive a working transaction log file, use the clear transaction-log EXEC command.
clear transaction-log { accelerator | flow }
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to archive t he flow transaction log file on the WAAS device:
Related Commands
clear users
To clear user connections or to unlock users that have been locked out, use the clear users EXEC command.
clear users [ administrative | locked-out { all | username username }]
Syntax Description
(Optional) Clears the connections (logins) of administrative users authenticated through a remote login service. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
The clear users administrative command clears the connections for all administrative users who are authenticated through a remote login service, such as TACACS. This command does not affect an administrative user who is authenticated through the local database. Only locally authenticated administrative users can run this command.
The clear users locked-out command unlocks user accounts that have been locked out. If a strong password policy is enabled (see the (config) authentication strict-password-policy command) a user account will be locked out if the user fails three consecutive login attempts. (This restriction does not apply to the admin account.)
Examples
The following example shows how to clear the connections of all authenticated users:
The following example shows how to clear the connections of all administrative users authenticated through a remote login service (it does not affect administrative users authenticated through the local database):
The following example shows how to unlock all locked-out user accounts:
The following example shows how to unlock the account for username darcy:
Related Commands
clear windows-domain
To clear Windows domain server information for a WAAS device, use the clear windows-domain EXEC command.
clear windows-domain encryption-service blacklist { identity tagName | service spn }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the clear windows-domain EXEC command to clear Windows domain server information.
Examples
The following example shows how to clear the Windows domain server information:
Related Commands
clear windows-domain-log
To clear the Windows domain server log file, use the clear windows-domain-log EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to clear all entries in the Windows domain log file on the WAAS device:
Related Commands
clock
To set clock functions or update the calendar, use the clock EXEC command.
clock { read-calendar | set time day month year | update-calendar }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
If you have an outside source on your network that provides time services (such as a NTP server), you do not need to set the system clock manually. When setting the clock, enter the local time. The WAAS device calculates the UTC based on the time zone set by the clock timezone global configuration command.
Two clocks exist in the system: the software clock and the hardware clock. The software uses the software clock. The hardware clock is used only at bootup to initialize the software clock.
Examples
The following example shows how to set the software clock on the WAAS device:
Related Commands
cms
To configure the Centralized Management System (CMS) embedded database parameters for a WAAS device, use the cms EXEC command.
cms { config-sync | deregister [ force ] | lcm { enable | disable } | maintenance { full | regular } | recover { identity word } | restore filename | validate }
cms database { backup {config} | create | delete
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the cms config-sync command to enable registered WAAS devices and standby WAAS Central Manager to contact the primary WAAS Central Manager immediately for a getUpdate (get configuration poll) request before the default polling interval of 5 minutes. For example, when a node is registered with the primary WAAS Central Manager and activated, it appears as Pending in the WAAS Central Manager GUI until it sends a getUpdate request. The cms config-sync command causes the registered node to send a getUpdate request at once, and the status of the node changes as Online.
Use the cms database create command to initialize the CMS database for a device that is already registered with the WAAS Central Manager. Then use the cms enable command to enable the CMS. For a device that is not registered with a WAAS Central Manager, use only the cms enable command to initialize the CMS database tables, register the node, and enable the CMS.

Note![]() For a vWAAS device, the model type must be configured before enabling management services.
For a vWAAS device, the model type must be configured before enabling management services.
Before a node can join a WAAS network, it must first be registered and then activated. Activate the node by using the WAAS Central Manager GUI.
The cms deregister command removes the node from the WAAS network by deleting registration information and database tables.
The cms deregister force command forces the removal of the node from the WAAS network by deleting registration information and database tables. If disk encryption is enabled on the device, it is disabled after you confirm this action. All data in encrypted file systems and imported certificates and private keys for the SSL accelerator are lost after a reload.
To back up the existing management database for the WAAS Central Manager, use the cms database backup command. For database backups, specify the following items:
The naming convention for backup files includes the time stamp and the WAAS version number.
After the backup is complete, use the copy disk ftp command to move the backup file to a remote system.

Note![]() For information on the procedure to back up and restore the CMS database on the WAAS Central Manager, see the Cisco Wide Area Application Services Configuration Guide.
For information on the procedure to back up and restore the CMS database on the WAAS Central Manager, see the Cisco Wide Area Application Services Configuration Guide.

Note![]() Do not run multiple instances of the cms database backup command simultaneously on a device. If a backup is in progress, you must wait for it to finish before using the command again.
Do not run multiple instances of the cms database backup command simultaneously on a device. If a backup is in progress, you must wait for it to finish before using the command again.
When you use the cms recover identity word command when recovering lost registration information, or replacing a failed node with a new node that has the same registration information, you must specify the device recovery key that you configured in the Modifying Config Property, System.device.recovery.key window of the WAAS Central Manager GUI.

Note![]() All CMS-related commands are disabled when running the cms restore command.
All CMS-related commands are disabled when running the cms restore command.
Use the lcm command to configure local/central management (LCM) on a WAE. The LCM feature allows settings that are configured using the device CLI or GUI to be stored as part of the WAAS network-wide configuration data (enable or disable).
When you enter the cms lcm enable command, the CMS process running on WAEs and the standby WAAS Central Manager detects the configuration changes that you made on these devices using CLIs and sends the changes to the primary WAAS Central Manager.
When you enter the cms lcm disable command, the CMS process running on the WAEs and the standby WAAS Central Manager does not send the CLI changes to the primary WAAS Central Manager. Settings configured using the device CLIs will not be sent to the primary WAAS Central Manager.
If LCM is disabled, the settings configured through the WAAS Central Manager GUI will overwrite the settings configured from the WAEs; however, this rule applies only to those local device settings that have been overwritten by the WAAS Central Manager when you have configured the local device settings. If you (as the local CLI user) change the local device settings after the particular configuration has been overwritten by the WAAS Central Manager, the local device configuration will be applicable until the WAAS Central Manager requests a full device statistics update from the WAEs (clicking the Force full database update button from the Device Dashboard window of the WAAS Central Manager GUI triggers a full update). When the WAAS Central Manager requests a full update from the device, the WAAS Central Manager settings will overwrite the local device settings.
Examples
The following example shows how to back up the cms database management tables on the WAAS Central Manager named waas-cm:
The following example shows how to validate the cms database management tables on the WAAS Central Manager named waas-cm:
Related Commands
cms secure-store
To configure secure store encryption, use the cms secure-store EXEC commands.
cms secure-store { init | open | change | clear | reset | mode { user-passphrase | auto-passphrase }}
Syntax Description
Defaults
A new Central Manager is configured for auto-generated passphrase mode with the secure store open.
Command Modes

Device Modes

Usage Guidelines
Secure store encryption provides strong encryption and key management for your WAAS system. The WAAS Central Manager and WAE devices use secure store encryption for handling passwords, managing encryption keys, and for data encryption.
On a new Central Manager, secure store is initialized and open and in auto-generated passphrase mode. The only options are to change the pass phrase (which sets the secure store to user-provided passphrase mode) or to change to user-provided passphrase mode. To change to user-provided passphrase mode, use the cms secure-store mode user-passphrase command.

Note![]() There may be a delay of a few minutes for the any changes you submit with the cms secure-store command to take effect. There may also be a delay for any changes to take effect if you submit changes at the WAAS CM Configure > Security > Secure Store Settings window.
There may be a delay of a few minutes for the any changes you submit with the cms secure-store command to take effect. There may also be a delay for any changes to take effect if you submit changes at the WAAS CM Configure > Security > Secure Store Settings window.
For secure store on the Central Manager, the data is encrypted using a key encryption key generated from the pass phrase with SHA-1 hashing and an AES 256-bit algorithm. When you enable secure store on a WAE device, the data is encrypted using a 256-bit key encryption key generated by SecureRandom, a cryptographically strong pseudorandom number. You can use your own password to enable secure store, but it is not necessary in auto-generated passphrase mode (the default), where the Central Manager generates a unique password automatically. A user-supplied password must conform to the following rules:
- Be 8 to 64 characters in length
- Contain characters only from the allowed set: A-Za-z0-9~%'!#$^&*()|;:,"<>/
- Contain at least one digit
- Contain at least one lowercase and one uppercase letter
If you are using the user-provided passphrase mode, when you reboot the Central Manager, you must manually reopen secure store using the cms secure-store open command. Until you open the secure store, a critical alarm is displayed on the Central Manager and services that use encryption (such as the SSL application accelerator) are not available. If you are using the auto-generated passphrase mode (the default), the Central Manager automatically opens the secure store after a reboot by using its own generated pass phrase.
The secure store passphrase mode on the primary Central Manager is replicated to the standby Central Manager (within the standard replication time). If the primary Central Manager is switched to auto-generated passphrase mode, the standby Central Manager secure store changes to the open state. If the primary Central Manager is switched to user-provided passphrase mode or the passphrase is changed, the standby Central Manager secure store changes to the initialized but not open state and an alarm is raised. You must manually open the secure store on the standby Central Manager.
When you enable secure store on a WAE, the WAE initializes and retrieves a new encryption key from the Central Manager. The WAE uses this key to encrypt user passwords and dynamic share credentials stored on the WAE. When you reboot the WAE after enabling secure store, the WAE retrieves the key from the Central Manager automatically, allowing normal access to the data that is stored in the WAAS persistent storage. If key retrieval fails, an alarm is raised and secure store will be in the initialized but not open state. You must open secure store manually.
If you have made any other CLI configuration changes on a WAE within the datafeed poll rate time interval (5 minutes by default) before you entered the cms secure-store command, you will lose those prior configuration changes and you will need to redo them.
Use the cms secure-store reset command if you reload a Central Manager that is configured in user-provided passphrase mode and you forget the secure store password. This command deletes all encrypted data, certificate and key files, and key manager keys. The secure store is left in the open state using auto-generated passphrase mode. For the complete procedure for resetting the secure store, see the “Resetting Secure Store Encryption on a Central Manager” section on page 9-17 in the Cisco Wide Area Application Services Configuration Guide.
Examples
The following example shows how to change the pass phrase mode of the secure store encryption on the WAAS Central Manager:
Related CommandsRelated Commands
configure
To enter global configuration mode, use the configure EXEC command. You must be in global configuration mode to enter global configuration commands.
To exit global configuration mode, use the end or exit commands. You can also press Ctrl-Z to exit from global configuration mode.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to enable global configuration mode on a WAAS device:
Related Commands
copy disk
To copy the configuration or image data from a disk to a remote location using FTP or to the startup configuration, use the copy disk EXEC command.
copy disk { ftp { hostname | ip-address } remotefiledir remotefilename localfilename | startup-config filename }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the copy disk ftp EXEC command to copy files from a SYSFS partition to an FTP server. Use the copy disk startup-config EXEC command to copy a startup-configuration file to NVRAM.
Examples
The following example shows how to copy a startup-configuration file to NVRAM:
Related Commands
copy ftp
To copy software configuration or image data from an FTP server, use the copy ftp EXEC command.
copy ftp disk { hostname | ip-address } remotefiledir remotefilename localfilename
copy ftp install { hostname | ip-address } remotefiledir remotefilename
copy ftp wow-recovery { hostname | ip-address } remotefiledir remotefilename
Syntax Description
Directory on the FTP server where the image file to be copied is located. |
|
Copies the file from an FTP server and installs the software release or firmware file to the local device. |
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the copy ftp disk EXEC command to copy a file from an FTP server to a SYSFS partition on the WAAS device. To show progress, this command prints a number sign (#) for each 1 MB of data that is copied.
Use the copy ftp install EXEC command to install an image file from an FTP server on a WAAS device. Part of the image goes to a disk and part goes to flash memory. This command can also be used to install a BIOS or other firmware update by specifying the appropriate update file.
You can also use the copy ftp install EXEC command to redirect your transfer to a different location. A username and a password have to be authenticated with a primary domain controller (PDC) before the transfer of the software release file to the WAAS device is allowed.
To show progress, this command prints a number sign (#) for each 1 MB of data that is copied.
Examples
The following example shows how to copy an image file from an FTP server and install the file on the local device:
The following example shows how to upgrade the BIOS. All output is written to a separate file (/local1/.bios_upgrade.txt) for traceability. The hardware-dependent files that are downloaded from Cisco.com for the BIOS upgrade are automatically deleted from the WAAS device after the BIOS upgrade procedure has been completed.
Related Commands
copy http
To copy configuration or image files from an HTTP server to the WAAS device, use the copy http EXEC command.
copy http install { hostname | ip-address } remotefiledir remotefilename [ port portnum ] [ proxy proxy_portnum ] [ username username password ]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the copy http install EXEC command to install an image file from an HTTP server and install it on a WAAS device. It transfers the image from an HTTP server to the WAAS device using HTTP as the transport protocol and installs the software on the device. Part of the image goes to a disk and part goes to flash memory. Use the copy http central EXEC command to download a software image into the repository from an HTTP server.
You can also use the copy http install EXEC commands to redirect your transfer to a different location or HTTP proxy server by specifying the proxy hostname | ip-address option. A username and a password have to be authenticated with a primary domain controller (PDC) before the transfer of the software release file to the WAAS device is allowed.
Examples
The following example shows how to copy an image file from an HTTP server and install the file on the WAAS device:
The following example shows how to upgrade the BIOS. All output is written to a separate file (/local1/.bios_upgrade.txt) for traceability. The hardware-dependent files that are downloaded from Cisco.com for the BIOS upgrade are automatically deleted from the WAAS device after the BIOS upgrade procedure has been completed.
Related Commands
copy monitoring-log
To copy SMB statistics data to the local disk or an FTP server, use the copy monitoring-log EXEC command.
copy monitoring-log { disk filename | ftp { hostname | ip-address } remotefiledir remotefilename }
Syntax Description
Copies the statistics in CSV format to the specified local disk file in the /local/local1 directory. |
|
Copies the statistics in CSV format to the specified remote file on an FTP server. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
Use this command to write the last 14 days of statistics data that has been collected by the stats-collector logging global configuration command. The data is written as a CSV file compressed in tar archive format.
Examples
The following example shows how to copy statistics data to an FTP server:
Related Commands
copy running-config
To copy a configuration or image data from the current configuration, use the copy running-config EXEC command.
copy running-config { disk filename | startup-config | tftp { hostname | ip-address } remotefilename }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the copy running-config EXEC command to copy the running system configuration of the WAAS device to a SYSFS partition, flash memory, or TFTP server. The copy running-config startup-config EXEC command is equivalent to the write memory EXEC command.
Examples
The following example shows how to copy the current system configuration to startup configuration (NVRAM):
Related Commands
copy scp
To securely copy configuration or image files from a source to a destination location, use the copy scp EXEC command.
copy scp { { disk { hostname | ip-address} remote_dir remote_file local_file} | { install { hostname | ip-address } remote_dir remote_file }}
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the copy scp disk EXEC command to copy a file from an SCP server to a SYSFS partition on the WAAS device.
Use the copy scp install EXEC command to install a software release or firmware file from an SCP server on a WAAS device.
Examples
The following example shows how to securely install the software release or firmware file from a source to a destination location:
Related Commands
copy secure-http
To securely copy configuration or image files from a source http server, use the copy secure-http EXEC command.
copy secure-http install {hostname | ip-address}
copy secure-http install usb filename
Copies the file from a source server and installs the software release or firmware file to the local device. |
|
The filename on the USB flash drive installed in a WAVE or ENCS device. |
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the copy secure-http install EXEC command to copy and install a software release from a secure HTTP server on a WAAS device.
Examples
The following example shows how to securely install the software release or firmware file from a sourcehttp server to a destination location:
Related Commands
copy startup-config
To copy configuration or image data from the startup configuration, use the copy startup-config EXEC command.
copy startup-config { disk filename | running-config | tftp { hostname | ip-address } remotefilename }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the copy startup-config EXEC command to copy the startup configuration file to a TFTP server or to a SYSFS partition.
Examples
The following example shows how to copy the startup configuration file to the running configuration:
Related Commands
copy sysreport
To copy system troubleshooting information from the device, use the copy sysreport EXEC command.
copy sysreport disk filename [ start-date { day month | month day } year [ end-date { day month | month day } year ]]
copy sysreport ftp { hostname | ip-address } remotedirectory remotefilename [ start-date { day month | month day } year [ end-date { day month | month day } year ]]
copy sysreport scp { hostname | ip-address } remotedirectory remotefilename [ start-date { day month | month day } year [ end-date { day month | month day } year ]]
copy sysreport tftp { hostname | ip-address } remotefilename } [ start-date { day month | month day } year [ end-date { day month | month day } year ]]
copy sysreport usb filename [ start-date { day month | month day } year [ end-date { day month | month day } year ]]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
A system report is a comprehensive report, which you must generate before contacting Cisco technical support. The system report contains output from many commands and system logs, including show commands, network and other statistics, graphs, log content, and configuration settings.

Note![]() The copy sysreport command consumes significant CPU and disk resources and can adversely affect system performance while it is running. The system report can be from 30 MB to 100MB in size, or larger, depending on your system configuration.
The copy sysreport command consumes significant CPU and disk resources and can adversely affect system performance while it is running. The system report can be from 30 MB to 100MB in size, or larger, depending on your system configuration.
–![]() Before generating a system report, use the test command to run diagnostic tests, so that diagnostic information is also included in the system report.
Before generating a system report, use the test command to run diagnostic tests, so that diagnostic information is also included in the system report.
–![]() Before generating a system report on a WAAS CM or standby WAAS CM, make a database backup by using the cms database backup command.
Before generating a system report on a WAAS CM or standby WAAS CM, make a database backup by using the cms database backup command.
- To generate a system report and store it on an FTP server, use the following form of the sysreport command:
- Generating the system report:
When you run the copy sysreport disk command, the system report must be saved to the local1 directory.

Note![]() When you run the copy sysreport disk command, the system report save process differs depending on the version of WAAS you are running.
When you run the copy sysreport disk command, the system report save process differs depending on the version of WAAS you are running.
For WAAS versions 6.1.x and later, the copy sysreport disk command saves the system report to the present working directory. Therefore, you must be in the local1 directory path when you run the copy sysreport disk command. If you are not in the local1 directory, the error message “Could not generate sysreport in location your-current-location” is displayed.
To display your present working directory, use the pwd command. To change your directory, use the cd command.
For WAAS versions earlier than 6.1.x, the copy sysreport disk command saves the system report to the local1 directory, irregardless of your present working directory. Therefore, you can be in any system directory when you run the copy sysreport disk command, and the system report is saved to the local1 directory.
Because the system report is such a large file, after you run the copy sysreport disk command, move the report file out of the disk, to save significant disk space. To do this, follow these steps:
1. WAE# copy generatedSysreport-name ftp server-name
The generated system report is copied from the current disk location and a copy is stored to a non-current-disk destination.
2. WAE# delfile generatedSysreport-name
The original generated system report on the current disk is deleted.
Examples
The following example shows how to copy the system information to the file mysysinfo on the local WAAS device:
The following example shows how to copy system information by FTP to the file myfile in the root directory of the FTP server named myserver:
Related Commands
copy system-status
To copy status information from the system for debugging, use the copy system-status EXEC command.
copy system-status disk filename
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the copy system-status EXEC command to create a file on a SYSFS partition that contains hardware and software status information.
Examples
The following example shows how to copy the system status to a disk file:
Related Commands
copy tech-support
To copy the configuration or image data from the system to use when working with Cisco TAC, use the copy tech-support EXEC command.
copy tech-support { disk filename | ftp { hostname | ip-address } remotedirectory remotefilename | scp { hostname | ip-address} remotedirectory remotefilename | tftp { hostname | ip-address } remotefilename }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the copy tech-support tftp EXEC command to copy technical support information to a TFTP server or to a SYSFS partition.
Examples
The following example shows how to copy system information for tech support to a disk file:
Related Commands
copy tftp
To copy configuration or image data from a TFTP server, use the copy tftp EXEC command.
copy tftp disk { hostname | ip-address } remotefilename localfilename
copy tftp running-config { hostname | ip-address } remotefilename
copy tftp startup-config { hostname | ip-address } remotefilename
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to copy configuration or image data from a TFTP server to the running configuration:
Related Commands
cpfile
To make a copy of a file, use the cpfile EXEC command.
cpfile oldfilename newfilename
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Examples
The following example shows how to create a copy of a file:
Related Commands
crypto delete
To remove SSL certificate and key files, use the crypto delete EXEC command.
crypto delete {ca-certificate filename | pkcs12 {filename | admin }}
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the crypto delete EXEC command to remove a certificate from your WAE’s secure store. If you only want to disassociate a certificate from an accelerated service, use no server-cert-key in crypto ssl services accelerated-service mode.
If you use the crypto delete pkcs12 admin command to delete a custom certificate and key that were installed for the Central Manager admin service, the admin service uses its built-in self-signed certificate.
Examples
The following example shows how to delete the CA certificate file mycert.ca:
Related Commands
crypto export
To export SSL certificate and key files, use the crypto export EXEC command.
crypto export {ca-certificate filename | pkcs12 { factory-self-signed | admin | filename} {pem-cert-key | pem-cert-only | pem-key-only | pkcs12}}{disk pathname | ftp address | sftp address | terminal | tftp address}
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to export a CA certificate file named mycert.ca to an FTP server:
The following example shows how to export the certificate and private key from a PKCS12 file named myfile.p12 to a PEM file on the local1 directory on the hard drive:
Related Commands
crypto generate
To generate a self-signed certificate or a certificate signing request, use the crypt generate EXEC command.
crypto generate {csr rsa modulus {1024 | 1536 | 2048 | 512 | 768}{disk pathname | ftp address | sftp address | terminal | tftp address} | self-signed-cert filename [exportable] rsa modulus {1024 | 1536 | 2048 | 512 | 768}}
Syntax Description
Specifies the size (number of bits) used for the RSA modulus for a CSR or a self-signed certificate. 
Note |
|
Generates the file to a disk. Type the disk filename including the full path. |
|
Generates the file to FTP. Type the FTP server’s IP address or hostname. |
|
Generates the file to secure FTP. Type the secure FTP server’s IP address or hostname. |
|
Generates the file to TFTP. Type the TFTP server’s IP address or hostname. |
|
Generates a self-signed SSL encryption certificate. The filename of the self-signed certificate to be generated must have the.p12 file extension. |
|
(Optional) Allows the self-signed certificate to be exported. |
|
Specifies the size of the RSA modulus to be used when generating the self-signed certificate. |
Defaults
Command Modes

Device Modes


Usage Guidelines

The valid size (number of bits) for the RSA modulus for a self-signed certificate is dependent on the WAAS version:

Note![]() A self-signed certificate on WAAS Version 6.1.x or earlier with an RSA modulus size of 512 is not compatible with Mozilla FireFox Version 39 and later, or with Google Chrome Version 48 and later. A self-signed certificate on WAAS Version 6.1.x or earlier with an RSA modulus size of 512 is compatible with Internet Explorer 8 and later.
A self-signed certificate on WAAS Version 6.1.x or earlier with an RSA modulus size of 512 is not compatible with Mozilla FireFox Version 39 and later, or with Google Chrome Version 48 and later. A self-signed certificate on WAAS Version 6.1.x or earlier with an RSA modulus size of 512 is compatible with Internet Explorer 8 and later.
If you have previously configured the RSA modulus size as 512: to access the WAAS CM with Mozilla FireFox Version 39 and later, or with Google Chrome Version 48 and later, you must regenerate the self-signed certificate with an RSA modulus size of 2048, and then upgade to the specified version of Mozilla FireFox or Google Chrome.
Examples
The following example shows how to create an exportable self-signed certificate. The certificate file is named myfile.p12 and is created using a 2048-bit RSA modulus.
Related Commands
crypto import
To import SSL certificates and key files, use the crypto import EXEC command.
crypto import ca-certificate filename {disk pathname | ftp host | http host | scep url | sftp host | terminal | tftp host}
crypto import pkcs12 {filename | admin} [exportable] [ignore-cert-chain-order] pem-cert-key {disk pathname | ftp host | http host | scep url | sftp host | terminal | tftp host}
crypto import pcsk12 {filename | admin} [exportable] [ignore-cert-chain-order] pkcs12 {disk pathname | ftp host | http host | sftp host | terminal | tftp host}
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The Central Manager admin service uses a self-signed certificate and key by default. You can use the crypto import pkcs12 admin command to import a custom certificate and key in PKCS12 or PEM format. If you delete the custom certificate and key, the self-signed certificate and key again become active.

Note![]() DSA certificates and keys cannot be imported.
DSA certificates and keys cannot be imported.
Examples
The following example shows how to import a CA certificate file named mycert.ca from a TFTP server:
Related Commands
crypto pki
To initialize the PKI managed store, use the crypto pki EXEC command.
crypto pki managed-store initialize
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to initialize the PKI managed store:
Related Commands
debug aaa accounting
To monitor and record AAA accounting debugging, use the debug aaa accounting EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable AAA accounting debug monitoring:
Related Commands
debug aaa authorization
To monitor and record AAA authorization debugging, use the debug aaa authorization EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable AAA authorization debug monitoring:
Related Commands
debug accelerator
To monitor and record accelerator debugging, use the debug accelerator EXEC command. To disable debugging, use the undebug form of this command.
debug accelerator generic [ connection | misc | shell | stats | all ]
no debug accelerator generic [ connection | misc | shell | stats | all ]
debug accelerator http [ bypass-list | cli | conditional-response | connection | dre-hints | metadatacache | redirect-response | shell | subnet | supress-server-encoding | transaction | unauthorized-response | all ]
no debug accelerator http [ bypass-list | cli | conditional-response | connection | dre-hints | metadatacache | redirect-response | shell | subnet | supress-server-encoding | transaction | unauthorized-response | all ]
debug accelerator mapi [ all | Common-flow | DCERPC-layer | EMSMDB-layer | IO | ROP-layer | ROP-parser | RPCHTTP-layer | RCP-parser | shell | Transport | Utilities ]
no debug accelerator mapi [ all | Common-flow | DCERPC-layer | EMSMDB-layer | IO | ROP-layer | ROP-parser | RPCHTTP-layer | RCP-parser | shell | Transport | Utilities ]
debug accelerator ica [ all | ao-connectionmgr | ao-parser | cgp | connection | crypto | detectionparser | failure | hash | ica | initialization | io | main | pipe | shell ]
no debug accelerator ica [ all | ao-connectionmgr | ao-parser | cgp | connection | crypto | detectionparser | failure | hash | ica | initialization | io | main | pipe | shell ]
debug accelerator smb [ cli | cmd-close | cmd-create | cmd-lock | cmd-others | cmd-query-info | cmd-read | cmd-set-info | cmd-write | flow | large-data-flush | lock-manager | meta-data | named-pipe | not-found-cache | packeter | parser | read-ahead | shell | vfn | all ]
no debug accelerator smb [ cli | cmd-close | cmd-create | cmd-lock | cmd-others | cmd-query-info | cmd-read | cmd-set-info | cmd-write | flow | large-data-flush | lock-manager | meta-data | named-pipe | not-found-cache | packeter | parser | read-ahead | shell | vfn | all ]
debug accelerator ssl [ accelerated-svc | alarm | all | am | am-generic-svc | bio | ca | ca-pool | cipherlist | client-to-server | dataserver | flow-shutdown | generic | ocsp | oom-manager | openssl-internal | parser | peering-svc | session-cache | shell | sm-alert | sm-generic | sm-io | sm-pipethrough | synchronization | verify | waas-to-waas ]
no debug accelerator ssl [ accelerated-svc | alarm | all | am | am-generic-svc | bio | ca | ca-pool | cipherlist | client-to-server | dataserver | flow-shutdown | generic | ocsp | oom-manager | openssl-internal | parser | peering-svc | session-cache | shell | sm-alert | sm-generic | sm-io | sm-pipethrough | synchronization | verify | waas-to-waas ]
debug accelerator wansecure [ all | flow | mux | ocsp | shell | ssl ]
no debug accelerator wansecure [ all | flow | mux | ocsp | shell | ssl ]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The output associated with the debug accelerator name module command for an application accelerator is written to the file name ao-errorlog.current, where name is the accelerator name. The accelerator information manager debug output is written to the file aoim-errorlog.current.
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all accelerator debug monitoring:
Related Commands
debug accelerator http object-cache
To enable object-cache debugging, use the debug accelerator http object-cache EXEC command.
debug accelerator http object-cache {all | configuration | gate-keeper | logger | preposition | response-headers | statistics | traffic-plugin}
Syntax Description

Command Default


Command Modes


Device Modes Default


Usage Guidelines

Use the debug accelerator http object-cache EXEC command to enable debugging for all object-cache debugging, or to specifying debugging for a particular object-cache area, such as configuration, cache preposition, or statistics.

Examples

The following example shows how to enable debugging for all parameters for the HTTP object cache:
debug accelerator mapi rpchttp-layer
To enable debugging of the MAPI RPC HTTP accelerator, use the debug accelerator mapi rpchttp EXEC command. To disable debugging, use the no form of this command.
debug accelerator mapi rpchttp-layer
no debug accelerator mapi rpchttp -layer
Defaults
Command Modes

Device Modes


Usage Guidelines

Use the debug accelerator mapi rpchttp-layer EXEC command to enable debugging of the mapi RPC HTTP application accelerator.
Examples
The following example shows how to enable debugging for the MAPI object cache i/o:
Related Commands
debug all
To monitor and record all debugging, use the debug all EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all debug monitoring:
Related Commands
debug appnav-controller connection
To enable connection-specific debugging on an AppNav Controller Interface Module, use the debug appnav-controller connection EXEC command. To disable debugging, use the undebug form of this command.
debug appnav-controller connection access-list acl-name
undebug appnav-controller connection
Syntax Description
Enables access list connection debugging. Access list name is an alphanumeric identifier up to 30 characters, beginning with a letter. |
Defaults
Command Modes

Device Modes

Usage Guidelines
The ACL specified in this command is shared by the monitor appnav-controller traffic and packet-capture commands.
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable connection-specific debug monitoring for an AppNav Controller Interface Module:
Related Commands
debug appnav-controller drop capture
To enable debugging on an AppNav Controller Interface Module to capture dropped packets, use the debug appnav-controller drop capture EXEC command. To disable debugging, use the no form of this command.
debug appnav-controller drop capture index index limit limit
no debug appnav-controller drop capture
Syntax Description
The maximum size of the packet capture file. The default limit is 65535. |
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
To display the index, use the show controllers np counters direct-access drop command.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to a new log file in PCAP format.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to show dropped packets for the AppNav Controller Interface Module using an index of 20 and a limit of 500:
Related Commands
debug authentication
To monitor and record authentication debugging, use the debug authentication EXEC command. To disable debugging, use the undebug form of this command.
debug authentication { user | windows-domain }
undebug authentication { user | windows-domain }
Syntax Description
Enables debugging of the user login against the system authentication. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable user authentication debug monitoring, verify that it is enabled, and then disable debug monitoring:
Related Commands
debug auto-discovery
To trace connections in the auto discovery module, use the debug auto-discovery EXEC command. To disable debugging, use the undebug form of this command.
debug auto-discoveryconnection
undebug auto-discovery connection
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable auto discovery connection debugging:
Related Commands
debug buf
To monitor and record buffer manager debugging, use the debug buf EXEC command. To disable debugging, use the undebug form of this command.
debug buf { all | dmbuf | dmsg }
undebug buf { all | dmbuf | dmsg }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all buffer manager debug monitoring:
Related Commands
debug cdp
To monitor and record CDP debugging, use the debug cdp EXEC command. To disable debugging, use the undebug form of this command.
debug cdp { adjacency | events | ip | packets }
undebug cdp { adjacency | events | ip | packets }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable CDP events debug monitoring:
Related Commands
debug cli
To monitor and record CLI debugging, use the debug cli EXEC command. To disable debugging, use the undebug form of this command.
debug cli { all | bin | parser }
undebug cli { all | bin | parser }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all CLI debug monitoring:
Related Commands
debug cmm
To monitor and record cluster membership manager debugging, use the debug cmm EXEC command. To disable debugging, use the undebug form of this command.
debug cmm { all | cli | events | ipc | misc | packets | shell | timers }
undebug cmm { all | cli | events | ipc | misc | packets | shell | timers }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all cmm debug monitoring:
Related Commands
debug cms
To monitor and record CMS debugging, use the debug cms EXEC command. To disable debugging, use the undebug form of this command.
debug cms{router-config | stats}
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable CMS debug monitoring:
Related Commands
debug connection
To enable connection-specific debugging, use the debug connection EXEC command. To disable debugging, use the undebug form of this command.
debug connection { all | access-list acl-name }
undebug connection { all | access-list acl-name }
Syntax Description
Enables access list connection debugging. Access list name is an alphanumeric identifier up to 30 characters, beginning with a letter. |
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all connection-specific debug monitoring:
Related Commands
debug controllers
To monitor and record interface controller capture debugging, use the debug controllers EXEC command. To disable debugging, use the undebug form of this command.
debug controllers NP { crash-dump | dump-cfg }
undebug controllers NP { crash-dump | dump-cfg }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to request a crash dump:
Related Commands
debug dataserver
To monitor and record data server debugging, use the debug dataserver EXEC command. To disable debugging, use the undebug form of this command.
debug dataserver { all | clientlib | server }
undebug dataserver { all | clientlib | server }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all data server debug monitoring:
Related Commands
debug dhcp
To monitor and record DHCP debugging, use the debug dhcp EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable DHCP debug monitoring:
Related Commands
debug dre
To monitor and record DRE debugging, use the debug dre EXEC command. To disable debugging, use the undebug form of this command.
debug dre { aggregation | all | cache | chunking | connection { aggregation [ acl ] | cache [ acl ] | chunking [ acl ] | core [ acl ] | message [ acl ] | misc [ acl ] | acl } | core | lz | message | misc | nack | packet }
undebug dre { aggregation | all | cache | chunking | connection { aggregation [ acl ] | cache [ acl ] | chunking [ acl ] | core [ acl ] | message [ acl ] | misc [ acl ] | acl } | core | lz | message | misc | nack | packet }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all DRE debug monitoring:
Related Commands
debug egress-method
To monitor and record egress method debugging, use the debug egress-method EXEC command. To disable debugging, use the undebug form of this command.
debug egress-method connection
undebug egress-method connection
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all egress method debug monitoring:
Related Commands
debug encryption-service
To monitor and record encryption service debugging, use the debug encryption-service EXEC command. To disable debugging, use the undebug form of this command.
debug encryption-service { all | application-layer | cfgmgr | dcerpc-layer | gss | io | secure-store | server | shell | transport-lib | utilities }
undebug encryption-service { all | application-layer | cfgmgr | dcerpc-layer | gss | io | secure-store | server | shell | transport-lib | utilities }
Syntax Description
Enables debugging of the encryption services application layer. |
|
Enables debugging of the encryption services configuration manager. |
|
Enables debugging of the encryption services transport library. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable debugging of all encryption services components:
Related Commands
debug fda
To monitor and record flow distribution agent debugging, use the debug fda EXEC command. To disable debugging, use the undebug form of this command.
debug fda { all | events | infra | messages }
undebug fda { all | events | infra | messages }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all flow distribution agent debug monitoring:
Related Commands
debug fdm
To monitor and record flow distribution manager debugging, use the debug fdm EXEC command. To disable debugging, use the undebug form of this command.
debug fdm { all | events | infra | messages }
undebug fdm { all | events | infra | messages }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all flow distribution manager debug monitoring:
Related Commands
debug filtering
To trace filtering connections setup, use the debug filtering EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable filtering module connection debugging:
Related Commands
debug flow
To monitor and record network traffic flow debugging, use the debug flow EXEC command. To disable debugging, use the undebug form of this command.
debug flow monitor type performance-monitor tcpstat-v1
undebug flow monitor type performance-monitor tcpstat-v1
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable network traffic flow debug monitoring:
Related Commands
debug generic-gre
To monitor and record generic GRE egress method debugging, use the debug generic-gre EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable generic GRE egress method debug monitoring:
Related Commands
debug hw-raid
To monitor and record hardware RAID debugging, use the debug hw-raid EXEC command. To disable debugging, use the undebug form of this command.
debug hw-raid { all | cli | daemon }
undebug hw-raid { all | cli | daemon }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all hardware RAID debug monitoring:
Related Commands
debug imd
To monitor and record interface manager debugging, use the debug imd EXEC command. To disable debugging, use the undebug form of this command.
debug imd { all | cli | infra | nprm | stats }
undebug fdm { all | cli | infra | nprm | stats }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all interface manager debug monitoring:
Related Commands
debug inline
To enable inline module debugging, use the debug inline EXEC command. To disable debugging, use the undebug form of this command.
debug inline { debug | info | warn }
undebug inline { debug | info | warn }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to set the log level for inline modules to warning level:
Related Commands
debug key-manager
To monitor and record key manager debugging, use the debug key-manager EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable monitoring API debug monitoring:
Related Commands
debug logging
To monitor and record logging debugging, use the debug logging EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all logging debug monitoring:
Related Commands
debug monapi
To monitor and record monitor API debugging, use the debug monapi EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable monitoring API debug monitoring:
Related Commands
debug nplogd
To monitor and record NP log daemon debugging, use the debug nplogd EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable NP log daemon debug monitoring:
Related Commands
debug ntp
To monitor and record NTP debugging, use the debug ntp EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable NTP debug monitoring:
Related Commands
debug object-cache database
To enable debugging of the object cache database, use the debug object-cache database EXEC command. To disable debugging, use the no form of this command.
no debug object-cache database
Syntax Description
Defaults
Command Modes

Device Modes


Usage Guidelines

Use the debug object-cache database EXEC command to enable debugging for the object cache database.
Examples
The following example shows how to enable debugging for the object cache database.
Related Commands
debug object-cache existence-cache
To enable debugging of the object cache existence cache database, use the debug object-cache existence-cache database EXEC command. To disable debugging, use the no form of this command.
debug object-cache existence-cache
no debug object-cache existence-cache
Syntax Description
Defaults
Command Modes

Device Modes


Usage Guidelines

Use the debug object-cache existence-cache EXEC command to enable debugging for the existence cache, which maintains information on whether or not an object is present in the object databases.
Examples
The following example shows how to enable debugging for the object cache existence cache.
Related Commands
debug object-cache load-monitor
To enable debugging of the object cache load monitor function, use the debug object-cache load-monitor enable EXEC command. To disable debugging, use the no form of this command.
debug object-cache load-monitor
no debug object-cache load-monitor
Syntax Description
Defaults
Command Modes

Device Modes


Usage Guidelines

Use the debug object-cache load-monitor EXEC command to enable debugging of the object cache load monitor function, which monitors disk load and usage.
Examples
The following example shows how to enable debugging for the object cache load monitor function.
Related Commands
debug punt
To monitor and record punt handler debugging, use the debug punt EXEC command. To disable debugging, use the undebug form of this command.
debug punt { all | module | packets | socket }
undebug punt { all | module | packets | socket }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all punt handler debug monitoring:
Related Commands
debug rbcp
To monitor and record RBCP debugging, use the debug rbcp EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable RBCP debug monitoring:
Related Commands
debug rmd
To monitor and record route manager debugging, use the debug rmd EXEC command. To disable debugging, use the undebug form of this command.
debug rmd { all | cli | infra | nprm }
undebug rmd { all | cli | infra | nprm }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all route manager debug monitoring:
Related Commands
debug rpc
To monitor and record remote procedure calls (RPC) debugging, use the debug rpc EXEC command. To disable debugging, use the undebug form of this command.
undebug rpc { detail | trace }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable RPC detail debug monitoring:
Related Commands
debug service-insertion
To trace connections in the service-insertion module, use the debug service-insertion EXEC command. To disable debugging, use the undebug form of this command.
debug service-insertion connection
undebug service-insertion connection
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all service-insertion module debug monitoring:
Related Commands
debug service-policy
To monitor and record service policy debugging, use the debug service-policy EXEC command. To disable debugging, use the undebug form of this command.
debug service-policy type { appnav | waas }
undebug service-policy type { appnav | waas }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable WAAS service policy debug monitoring:
Related Commands
debug snmp
To monitor and record SNMP debugging, use the debug snmp EXEC command. To disable debugging, use the undebug form of this command.
debug snmp { all | cli | main | mib | traps }
undebug snmp { all | cli | main | mib | traps }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all SNMP debug monitoring:
Related Commands
debug standby
To enable standby debugging, use the debug standby EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
(Optional) Enables standby debugging using all debug features. |
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all standby debug monitoring:
Related Commands
debug statistics
To monitor and record statistics debugging, use the debug statistics EXEC command. To disable debugging, use the undebug form of this command.
debug statistics { all | ao | client | collector | ipc | messages | serializer | sqm }
undebug statistics { all | ao | client | collector | ipc | messages | serializer | sqm }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all statistics debug monitoring:
Related Commands
debug synq
To trace synq connections setup, use the debug synq EXEC command. To disable debugging, use the undebug form of this command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable synq module connection debugging:
Related Commands
debug tfo
To monitor and record TFO flow optimization debugging, use the debug tfo EXEC command. To disable debugging, use the undebug form of this command.
debug tfo {all | buffer-mgr | dre-flow | netio | scheduler }
undebug tfo {all | buffer-mgr | dre-flow | netio | scheduler }
Syntax Description
Enables TFO connection debugging for the network input/output module. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable all TFO flow optimization debug monitoring:
Related Commands
debug translog
To monitor and record transaction logging debugging, use the debug translog EXEC command. To disable debugging, use the undebug form of this command.
debug translog { detail | export | info }
undebug translog { detail | export | info }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable transaction logging detail debug monitoring:
Related Commands
debug wafs
To set the log level of the WAFS Device Manager component, use the debug wafs EXEC command. To disable debugging, use the undebug form of this command.
debug wafs manager { debug | error | info | warn }
undebug wafs manager { debug | error | info | warn }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to set the log level for all WAFS components to error level:
Related Commands
debug wccp
To monitor and record WCCP information debugging, use the debug wccp EXEC command. To disable debugging, use the undebug form of this command.
debug wccp { all | detail | error | events | keepalive | packets }
undebug wccp { all | detail | error | events | keepalive | packets }
Syntax Description
Enables the debugging for WCCP keepalives that are sent to the applications. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
Because the performance of the WAAS device degrades when you use the debug command, we recommend that you use this command only at the direction of Cisco TAC. For more information, see the “$paratext>” section.
If the watchdog utility is not running, the message “WAAS is not running” appears.
Use the show debugging command to display enabled debug options.
The output associated with the debug command is written to either the syslog file in /local1/syslog.txt or the debug log associated with the module in the file /local1/errorlog/ module_name -errorlog.current.
The debug log file associated with a module will be rotated to a backup file when the current file reaches its maximum size. The backup files are named as follows: name -errorlog. #, where # is the backup file number.
For any debug command, system logging must be enabled. The command to enable logging is the logging disk enable global configuration command, which is enabled by default.
If a debug command module uses the syslog for debug output, then you must use the logging disk priority debug global configuration command (the default is logging disk priority notice).
If a debug command module uses the debug log for output, then the output can be filtered based on the priority level configuration for the four different levels of debug log output, as follows:
- For filtering on critical debug messages only, use the logging disk priority critical g lobal configuration command.
- For filtering on critical and error level debug messages, use the logging disk priority error global configuration command.
- For filtering on critical, error, and trace debug level debug messages, use the logging disk priority debug global configuration command.
- For seeing all debug log messages, which include critical, error, trace and detail messages, use the logging disk priority detail global configuration command.
Regardless of the priority level configuration, any syslog messages at the LOG_ERROR or higher priority will be automatically written to the debug log associated with a module.
We recommend that you use the debug and undebug commands only at the direction of Cisco Systems technical support personnel.
Examples
The following example shows how to enable WCCP information debug monitoring:
Related Commands
delfile
To delete a file from the current directory, use the delfile EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the delfile EXEC command to remove a file from a SYSFS partition on the disk drive of the WAAS device.
Examples
The following example shows how to delete a temporary file from the /local1 directory using an absolute path:
Related Commands
deltree
To remove a directory with all of its subdirectories and files, use the deltree EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the deltree EXEC command to remove a directory and all files within the directory from the WAAS SYSFS file system. No warning is given that you are removing the subdirectories and files.

Note![]() Make sure that you do not remove files or directories required for the WAAS device to function properly.
Make sure that you do not remove files or directories required for the WAAS device to function properly.
Examples
The following example shows how to delete the testdir directory from the /local1 directory:
Related Commands
dir
To view details of one file or all files in a directory, use the dir EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the dir EXEC command to view a detailed list of files contained within the working directory, including information about the file name, size, and time created. The lls EXEC command produces the same output.
Examples
The following example shows how to create a detailed list of all the files for the current directory:
------------- ------------------------- -----------
4096 Fri Feb 24 14:40:00 2006 <DIR> actona
4096 Tue Mar 28 14:42:44 2006 <DIR> core_dir
4096 Wed Apr 12 20:23:10 2006 <DIR> crash
4506 Tue Apr 11 13:52:45 2006 dbupgrade.log
4096 Tue Apr 4 22:50:11 2006 <DIR> downgrade
4096 Sun Apr 16 09:01:56 2006 <DIR> errorlog
4096 Wed Apr 12 20:23:41 2006 <DIR> logs
16384 Thu Feb 16 12:25:29 2006 <DIR> lost+found
4096 Wed Apr 12 03:26:02 2006 <DIR> sa
24576 Sun Apr 16 23:38:21 2006 <DIR> service_logs
4096 Thu Feb 16 12:26:09 2006 <DIR> spool
9945390 Sun Apr 16 23:38:20 2006 syslog.txt
10026298 Thu Apr 6 12:25:00 2006 syslog.txt.1
10013564 Thu Apr 6 12:25:00 2006 syslog.txt.2
10055850 Thu Apr 6 12:25:00 2006 syslog.txt.3
10049181 Thu Apr 6 12:25:00 2006 syslog.txt.4
4096 Thu Feb 16 12:29:30 2006 <DIR> var
508 Sat Feb 25 13:18:35 2006 wdd.sh.signed
The following example shows how to display the detailed information for only the logs directory:
Related Commands
disable
To turn off privileged EXEC commands, use the disable EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the WAAS software CLI EXEC mode for setting, viewing, and testing system operations. This command mode is divided into two access levels, user and privileged. To access privileged-level EXEC mode, enter the enable EXEC command at the user access level prompt and specify the admin password when prompted for a password.
The disable command places you in the user-level EXEC shell (notice the prompt change).
Examples
The following example shows how to enter the user-level EXEC mode from the privileged EXEC mode:
Related Commands
disk
To configure disks on a WAAS device, use the disk EXEC command.
disk delete-partitions diskname
disk disk-name diskxx enable force
disk disk-name disk xx replace
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
- The WAAS software supports hot-swap functionality for both failed disk replacement and scheduled disk maintenance. On the WAE-612, use the disk disk-name diskxx shutdown global configuration command to shut down a disk for scheduled disk maintenance. (For the scheduled disk maintenance procedure, see the chapter “Maintaining Your WAAS System” in the Cisco Wide Area Application Services Configuration Guide.)
–![]() The disk hot-swap functionality automatically disables a failed disk if the system detects one critical disk alarm. The software removes the failed disk automatically regardless of the setting for disk error-handling.
The disk hot-swap functionality automatically disables a failed disk if the system detects one critical disk alarm. The software removes the failed disk automatically regardless of the setting for disk error-handling.
–![]() For WAE-612 models, when you replace a failed disk that was automatically disabled by the software, use the disk insert EXEC command to bring the disk back into service. For all other models, see the (config) disk disk-name command section.
For WAE-612 models, when you replace a failed disk that was automatically disabled by the software, use the disk insert EXEC command to bring the disk back into service. For all other models, see the (config) disk disk-name command section.
- To identify which disks have been identified as failed or bad, use the show disks failed-disk-id EXEC command. Do not reinsert any disk with a serial number shown in this list.
- Use the disk delete-partitions EXEC command to remove all disk partitions on a single disk drive on a WAAS device or to remove the disk partition on the logical drive for RAID-5 systems.

–![]() The disk delete-data-partitions command deletes the DRE caches.
The disk delete-data-partitions command deletes the DRE caches.
–![]() After using the disk delete-data-partitions command, you must reload the device.
After using the disk delete-data-partitions command, you must reload the device.

Note After using the disk delete-data-partitions command, you must reload the device with a cold boot. If you reload the device with a warm boot, all data is not cleared, which may prevent the device from establishing connections.
The data partitions are automatically re-created and the caches are initialized, which can take several minutes. DRE optimization is not done until the DRE cache has finished initializing. The show statistics dre EXEC command reports “TFO: Initializing disk cache” until then. It is best not to interrupt DRE cache initialization by reloading the device again until after cache initialization has finished. However, if DRE cache initialization is interrupted, on the next reboot the disk is checked, which takes extra time, and DRE initialization is completed again.
- When you upgrade to software version 6.1.1, and execute disk-delete-preserve-software command for the first time, all data and system partitions are re-created.
–![]() Use the disk delete-preserve-software command if you want to delete all existing data and system partitions, and yet want to preserve the software version and the device registration details with the Central Manager. This changes the software store partition size from 1 GB to 2GB. This command is applicable for all vWAAS devices, ISR WAAS devices and SM-SRE devices.
Use the disk delete-preserve-software command if you want to delete all existing data and system partitions, and yet want to preserve the software version and the device registration details with the Central Manager. This changes the software store partition size from 1 GB to 2GB. This command is applicable for all vWAAS devices, ISR WAAS devices and SM-SRE devices.
Examples
The following example shows how to recreate the RAID-5 array:
Related Commands
dnslookup
To resolve a host or domain name to an IP address(IPv4/IPv6), use the dnslookup EXEC command.
dnslookup { hostname | domainname| IPv4/IPv6 address }
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how the dnslookup command is used to resolve the hostname myhost to IP address172.31.69.11
The following example shows how the dnslookup command is used to resolve the hostname abd.com to IP address 192.168.219.25:
The following example shows how the dnslookup command is used to resolve an IP address used as a hostname to 10.0.11.0:
The following example shows how the dnslookup command is used to resolve an IP address to a hostname:
enable
To access privileged EXEC commands, use the enable EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the WAAS software CLI EXEC mode for setting, viewing, and testing system operations. This command mode is divided into two access levels: user and privileged. To access privileged-level EXEC mode, enter the enable EXEC command at the user access level prompt and specify the admin password when prompted for a password.
If using TACACS+ authentication, there is an enable password feature in TACACS+ that allows an administrator to define a different enable password for each user. If a TACACS+ user enters the enable EXEC command to access privileged EXEC mode, that user must enter the admin password defined by the TACACS+ server.
The disable command takes you from privileged EXEC mode to user EXEC mode.
Examples
The following example shows how to access privileged EXEC mode:
Related Commands
exit
To terminate privileged-level EXEC mode and return to the user-level EXEC mode, use the exit command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The exit EXEC command is equivalent to pressing Ctrl-Z or entering the end command. Entering the exit command in the user level EXEC shell terminates the console or Telnet session.
Examples
The following example shows how to terminate privileged-level EXEC mode and return to the user-level EXEC mode:
Related Commands
find-pattern
To search for a particular pattern in a file, use the find-pattern command in EXEC mode.
find-pattern {binary reg-express filename | count reg-express filename | lineno reg-express filename | match reg-express filename | nomatch reg-express filename | recursive reg-express filename }
find-pattern case { binary reg-express filename | count reg-express filename | lineno reg-express filename | match reg-express filename | nomatch reg-express filename | recursive reg-express filename }
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to search a file recursively for a case-sensitive pattern:
The following example shows how to search a file for a pattern and print the matching lines:
The following example shows how to search a file for a pattern and print the number of matching lines:
Related Commands
help
To obtain online help for the command-line interface, use the help EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
You can obtain help at any point in a command by entering a question mark (?). If nothing matches, the help list will be empty, and you must back up until entering a ? shows the available options.
Examples
The following example shows how to display the output of the help EXEC command:
Related Commands
install
To install a new software image (such as the WAAS software) on the WAAS device, use the install EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The install command loads the system image into flash memory and copies the disk-based software component to the software file system (swfs) partition. This command can also be used to install a BIOS or other firmware update by specifying the appropriate update file.

Note![]() If you are installing a system image that contains optional software, make sure that an SWFS partition is mounted.
If you are installing a system image that contains optional software, make sure that an SWFS partition is mounted.
To install a system image, copy the image file to the SYSFS directory local1. Before executing the install command, change the present working directory to the directory where the system image resides. When the install command is executed, the image file is expanded. The expanded files overwrite the existing files on the WAAS device. The newly installed version takes effect after the system image is reloaded.

Note![]() The install command does not accept.pax files. Files should be of the type.bin (for example, cache-sw.bin). Also, if the release being installed does not require a new system image, then it may not be necessary to write to flash memory. If the newer version has changes that require a new system image to be installed, then the install command may result in a write to flash memory.
The install command does not accept.pax files. Files should be of the type.bin (for example, cache-sw.bin). Also, if the release being installed does not require a new system image, then it may not be necessary to write to flash memory. If the newer version has changes that require a new system image to be installed, then the install command may result in a write to flash memory.
Close your browser and restart the browser session to the WAAS Central Manager, if you installed a new software image to the primary WAAS Central Manager.
Examples
The following example shows how to load the system image contained in the wae512-cache-300.bin file:
Related Commands
less
To display a file using the Less application, use the less EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Less is a pager application that displays text files one page at a time. You can use Less to view the contents of a file, but not edit it. Less offers some additional features when compared to conventional text file viewer applications such as Type. These features include the following:
- Backward movement—Allows you to move backward in the displayed text. Use k, Ctrl-k, y, or Ctrl-y to move backward. See the summary of Less commands for more details; to view the summary, press h or H while displaying a file in Less.
- Searching and highlighting—Allows you to search for text in the file that you are viewing. You can search forward and backward. Less highlights the text that matches your search to make it easy to see where the match is.
- Multiple file support—Allows you to switch between different files, remembering your position in each file. You can also do a search that spans all the files you are working with.
Examples
The following example shows how to display the text of the syslog.txt file using the Less application:
Related Commands
license add
To add a software license to a device, use the license add EXEC command.
Syntax Description
Name of the software license to add. The following license names are supported: |
Defaults
Command Modes

Device Modes

Examples
The following example shows how to install the enterprise license:
Related Commands
clear arp-cache license
lls
To view a long list of directory names, use the lls EXEC command.
Syntax Description
(Optional) Name of the directory for which you want a long list of files. |
Defaults
Command Modes

Device Modes

Usage Guidelines
The lls command provides detailed information about files and subdirectories stored in the present working directory (including the size, date, time of creation, SYSFS name, and long name of the file). This information can also be viewed with the dir command.
Examples
The following example shows how to display a detailed list of the files in the current directory:
-------------- ------------------------- -----------
4096 Fri Feb 24 14:40:00 2006 <DIR> actona
4096 Tue Mar 28 14:42:44 2006 <DIR> core_dir
4096 Wed Apr 12 20:23:10 2006 <DIR> crash
4506 Tue Apr 11 13:52:45 2006 dbupgrade.log
4096 Tue Apr 4 22:50:11 2006 <DIR> downgrade
4096 Sun Apr 16 09:01:56 2006 <DIR> errorlog
4096 Wed Apr 12 20:23:41 2006 <DIR> logs
16384 Thu Feb 16 12:25:29 2006 <DIR> lost+found
4096 Wed Apr 12 03:26:02 2006 <DIR> sa
24576 Sun Apr 16 23:54:30 2006 <DIR> service_logs
4096 Thu Feb 16 12:26:09 2006 <DIR> spool
9951236 Sun Apr 16 23:54:20 2006 syslog.txt
10026298 Thu Apr 6 12:25:00 2006 syslog.txt.1
4096 Thu Feb 16 12:29:30 2006 <DIR> var
508 Sat Feb 25 13:18:35 2006 wdd.sh.signed
Related Commands
ls
To view a list of files or subdirectory names within a directory on the device hard disk, use the ls EXEC command.
Syntax Description
(Optional) Name of the directory for which you want a list of files. |
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the ls directory command to list the filenames and subdirectories within a particular directory.
Use the ls command to list the filenames and subdirectories of the current working directory.
Examples
The following example shows how to display the files and subdirectories that are listed within the root directory:
actona
core_dir
crash
dbupgrade.log
downgrade
errorlog
logs
lost+found
sa
service_logs
spool
syslog.txt
syslog.txt.1
var
wdd.sh.signed
Related Commands
lsusb
To view a list of files or subdirectory names within a directory on a USB storage device, use the lsusb EXEC command.
Syntax Description
(Optional) Name of the directory for which you want a list of files. |
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the lsusb directory command to list the filenames and subdirectories within a particular directory on the USB device.
Use the lsusb command to list the filenames and subdirectories of the current working directory on the USB device.
This command is available only on WAAS devices that support external USB storage devices.
Examples
The following example shows how to display the files and subdirectories that are listed within the root directory of a USB device:
directory1
afile.txt
Related Commands
mkdir
To create a directory, use the mkdir EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to create a new directory, oldpaxfiles :
Related Commands
mkfile
To create a new file, use the mkfile EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the mkfile EXEC command to create a new file in any directory of the WAAS device.
Examples
The following example shows how to create a new file, traceinfo, in the root directory:
Related Commands
monitor appnav-controller traffic
To enable traffic monitoring on an AppNav Controller Interface Module, use the monitor appnav-controller traffic EXEC command.
monitor appnav-controller traffic { access-list acl-name | disable }
Syntax Description
Name of the access list that determines which flows are monitored. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
Use this command to enable the AppNav Controller Interface Module to supply monitoring statistics for traffic flows that match the specified ACL. The ACL must be defined by the ip access-list global configuration command.
The ACL specified in this command is shared by the packet-capture and debug appnav-controller commands.
Use the show statistics monitor appnav-controller traffic EXEC command to display the monitoring statistics.
Use the show monitor EXEC command to display the status of traffic monitoring.
Examples
The following example shows how to enable traffic monitoring with an ACL:
Related Commands
ntpdate
To set the software clock (time and date) on a WAAS device using an NTP server, use the ntpdate EXEC command.
ntpdate { hostname | ip-address } [ key { authentication-key }]
Syntax Description
(Optional) Specifies to use authentication with the NTP server. |
|
Authentication key string to use with the NTP server authentication. This value must be between 0 and 4294967295. |
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the ntpdate command to find the current time of day and set the current time on the WAAS device to match. You must save the time to the hardware clock using the clock save command if you want to restore the time after a reload.
Examples
The following example shows how to set the software clock on the WAAS device using a NTP server:
Related Commands
packet-capture
To capture packets on a device interface, use the packet-capture EXEC command.
packet-capture all-interfaces { access-list { acl-name | acl-num } | destination-ip { hostname | ip-address } | destination-port port | source-ip { hostname | ip-address } | source-port port } [ file-size size [ number-of-files num | stop-after-num-files num ] ] | packet-size | non-encapsulated | [ capture-filename ]
packet-capture appnav-controller { access-list { acl-name | acl-num } | interface { GigabitEthernet slot/port | TenGigabitEthernet slot/port | PortChannel index | standby grpnumber } access-list { acl-name | acl-num }} [ file-size size [ number-of-files num | stop-after-num-files num ] ] | packet-size | non-encapsulated | [ capture-filename ]
packet-capture interface { GigabitEthernet slot/port | TenGigabitEthernet slot/port | PortChannel index | standby grpnumber } | virtual slot/port | { access-list { acl-name | acl-num } | destination-ip { hostname | ip-address } | destination-port port | source-ip { hostname | ip-address } | source-port port } [ file-size size [ number-of-files num | stop-after-num-files num ] ] | packet-size | non-encapsulated | [ capture-filename ]
packet-capture decode [ destination-ip { hostname | ip-address } | destination-port port | source-ip { hostname | ip-address } | source-port port ] [ file-size size [ number-of-files num | stop-after-num-files num ] ] | packet-size | non-encapsulated | [ capture-filename ]
packet-capture stop [file-size size [number-of-files num | stop-after-num-files num] ] | packet-size | nonencapsulated [ capture-filename ]
Syntax Description
Defaults
Command Modes

Device Modes

Note the following device mode usage for the packet-capture command:
–![]() Used with packet-capture all-interfaces, packet-capture interface, packet-capture decode, and packet-capture stop.
Used with packet-capture all-interfaces, packet-capture interface, packet-capture decode, and packet-capture stop.
–![]() Used with packet-capture all-interfaces, packet-capture interface, packet-capture appnav-controller, packet-capture decode, and packet-capture stop.
Used with packet-capture all-interfaces, packet-capture interface, packet-capture appnav-controller, packet-capture decode, and packet-capture stop.
–![]() Used with packet-capture all-interfaces, packet-capture interface, packet-capture decode, and packet-capture stop.
Used with packet-capture all-interfaces, packet-capture interface, packet-capture decode, and packet-capture stop.
Usage Guidelines
The following are usage guidelines for the packet-capture command:
The packet-capture command is preferred over the deprecated commands tcpdump and tethereal, and is required to capture data plane traffic on an AppNav Controller Interface Module interface.
Examples
The following example shows how to capture packets on a general interface:
The following example shows how to capture packets on all interfaces on an AppNav Controller Interface Module:
Related Commands
ping
To send echo packets for diagnosing basic network connectivity on networks, use the ping EXEC command.
ping [ management ] { hostname | ip-address }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
To use the ping command with the hostname argument, make sure that DNS functionality is configured on the WAAS device. To force the timeout of a nonresponsive host, or to eliminate a loop cycle, press Ctrl-C.
Examples
The following example shows how to send echo packets to a machine with address 172.19.131.189 to verify its availability on the network:
Related Commands
ping6
To send echo packets for diagnosing basic network connectivity on IPv6 networks, use the ping6 EXEC command.
ping6 { hostname | ip-address }[ management ]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
To use the ping6 command with the hostname argument, make sure that DNS functionality is configured on the WAAS device. To force the timeout of a nonresponsive host, or to eliminate a loop cycle, press Ctrl-C.
When you use a device’s management interface to establish connectivity to another device, using ping6 command, and the management interface goes down, the communication will still succeed if the address of the end device is reachable from any other interface.
Examples
The following example shows how to send echo packets to a machine with address 2013:1:1:10::5
to verify its availability on the network:
Related Commands
pwd
To view the present working directory on a WAAS device, use the pwd EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to display the current working directory:
Related Commands
reload
To halt the operation and perform a cold restart on a WAAS device, use the reload EXEC command.
reload [ force | in m | cancel ]
Syntax Description
(Optional) Schedules a reboot after a specified interval (1-10080 minutes). |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
To reboot a WAAS device, use the reload command. If no configurations are saved to flash memory, you are prompted to enter configuration parameters upon a restart. Any open connections are dropped after you enter the reload command, and the file system is reformatted upon restart.
The reload command can include the option to schedule a reload of the software to take effect in a specified number of minutes. After entering this command, you are asked to confirm the reload by typing y and then confirm WCCP shutdown by typing y again (if WCCP is active).
Examples
The following example shows how to halt the operation of the WAAS device and reboot with the configuration saved in flash memory. You are not prompted for confirmations during the process.
Related Commands
rename
To rename a file on a WAAS device, use the rename EXEC command.
rename oldfilename newfilename
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the rename command to rename any SYSFS file without making a copy of the file.
Examples
The following example shows how to rename the errlog.txt file to old_errlog.txt :
Related Commands
restore
To restore the device to its manufactured default status by removing the user data from the disk and flash memory, use the restore EXEC command.
restore { factory-default [ preserve basic-config ] | rollback }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the restore EXEC command to restore data on a disk and in flash memory to the factory default, while preserving particular time-stamp evaluation data, or to roll back the configuration to the last functional data and device configuration.
This command erases all existing content on the device; however, your network settings are preserved and the device is accessible through a Telnet and Secure Shell (SSH) session after it reboots.
Backing up the Central Manager Database
Before you use the restore factory-default command on your primary WAAS Central Manager or change over from the primary to a standby WAAS Central Manager, make sure that you back up the WAAS Central Manager database and copy the backup file to a safe location that is separate from the WAAS Central Manager. You must halt the operation of the WAAS Central Manager before you enter the backup and restore commands.

By removing the WAAS Central Manager database, all configuration records for the entire WAAS network are deleted. If you do not have a valid backup file or a standby WAAS Central Manager, you must reregister every WAE with the WAAS Central Manager because all previously configured data is lost.
If you used your standby WAAS Central Manager to store the database while you reconfigured the primary, you can register the former primary as a new standby WAAS Central Manager.
If you created a backup file while you configured the primary WAAS Central Manager, you can copy the backup file to this newly reconfigured WAAS Central Manager.
Rolling Back the Configuration
You can roll back the software and configuration of a WAAS device to a previous version using the restore rollback command. You would roll back the software only in cases in which a newly installed version of the WAAS software is not functioning properly.
The restore rollback command installs the last saved WAAS.bin image on the system disk. A WAAS.bin image is created during software installation and stored on the system disk. If the WAAS device does not have a saved version, the software is not rolled back.

Note![]() WAFS to WAAS migration is supported. Rollback from WAAS to WAFS is not supported.
WAFS to WAAS migration is supported. Rollback from WAAS to WAFS is not supported.
Examples
The following examples show how to use the restore factory-default and restore factory-default preserve basic-config commands. Because configuration parameters and data are lost, prompts are given before initiating the restore operation to ensure that you want to proceed.
[yes/no]
[yes/no]

Note![]() You can enter basic configuration parameters (such as the IP address, hostname, and name server) at this point, or you can enter these parameters later through entries in the command-line interface.
You can enter basic configuration parameters (such as the IP address, hostname, and name server) at this point, or you can enter these parameters later through entries in the command-line interface.
The following example shows how to verify that the restore command has removed data from the SYSFS, WAAS, and PRINTSPOOLFS partitioned file systems:
The following example shows how to upgrade or restore an older version of the WAAS software. In the example, version Y of the software is installed (using the copy command), but the administrator has not switched over to it yet, so the current version is still version X. The system is then reloaded (using the reload command), and it verifies that version Y is the current version running.
The following example shows how to roll back the software to version X (using the restore rollback command), and reload the software:
Because flash memory configurations were removed after the restore command was used, the show startup-config command does not return any flash memory data. The show running-config command returns the default running configurations.
Related Commands
rmdir
To delete a directory on a WAAS device, use the rmdir EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the rmdir EXEC command to remove any directory from the WAAS file system. The rmdir command only removes empty directories.
Examples
The following example shows how to delete the oldfiles directory from the local1 directory:
Related Commands
scp
To copy files between network hosts, use the scp command.
scp [ 4 ][ 6 ][ B ][ C ][ p ][ q ][ r ][ v ] [ c cipher ] [ F config-file ] [ i id-file ] [ o ssh_option ] [ P port ] [ S program ]
[[ user @ ] host : file ] [... ] [[ user-n @ ] host-n : file-n ]
Syntax Description
Command Modes

Device Modes

Usage Guidelines
The scp command uses SSH for transferring data between hosts.This command is enabled by default.
This command prompts you for passwords or pass phrases when needed for authentication.
Related Commands
script
To execute a script provided by Cisco or check the script for errors, use the script EXEC command.
script { check | execute } file_name
Syntax Description
Executes the script. The script file must be a SYSFS file in the current directory. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
The script EXEC command opens the script utility, which allows you to execute Cisco-supplied scripts or check errors in those scripts. The script utility can read standard terminal input from the user if the script you run requires input from the user.

Note![]() The script utility is designed to run only Cisco-supplied scripts. You cannot execute script files that lack Cisco signatures or that have been corrupted or modified.
The script utility is designed to run only Cisco-supplied scripts. You cannot execute script files that lack Cisco signatures or that have been corrupted or modified.
Examples
The following example shows how to check for errors in the script file test_script.pl :
setup
To configure basic configuration settings (general settings, device network settings, interception type, disk configuration, and licenses) on the WAAS device or to complete basic configuration after upgrading to the WAAS software, use the setup EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
For instructions on using the setup command, see the Cisco Wide Area Application Services Quick Configuration Guide.
For proper display of the setup command, leave the terminal length set to the default value of 24 lines.
show aaa accounting
To display the AAA accounting configuration information for a WAAS device, use the show aaa accounting EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show aaa accounting EXEC command to display configuration information for the following AAA accounting types:
Examples
Table 3-1 describes the fields shown in the show aaa accounting command display.
Related Commands
show aaa authorization
To display the AAA authorization configuration information for a WAAS device, use the show aaa authorization EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show aaa authorizaiton EXEC command to display configuration and state information related to AAA authorization.
Examples
Table 3-2 describes the fields shown in the show aaa authorization command display.
|
|
|
|---|---|
AAA authorization configuration for the following types of user accounts: |
|
Related Commands
show accelerator
To display the status and configuration of the application accelerators, use the show accelerator EXEC command.
show accelerator [ detail | epm | http [ debug ]| ica | interposer-ssl | mapi | smb | ssl | wansecure ]
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example displays the output for the show accelerator http command:
Table 3-3 describes the fields shown in the show accelerator command display for all application accelerators. Specific application accelerators display additional configuration status information.
If you use the show accelerator http or the show accelerator smb command, the output contains an extra section called Accelerator Config Item, which appears before the Policy Engine Config Item section. In the Accelerator Config Item section, each item shows the status of an HTTP accelerator configuration item. The Mode column shows Default if the item is configured with the default setting or User if the item is configured with a different setting by the user. The Value column shows the current value of the item (Enabled, Disabled, or an alpha-numeric setting).
Related Commands
show accelerator http object-cache
To display HTTP object cache configuration and status information for a WAAS device, use the show accelerator http object-cache EXEC command.
show accelerator http object-cache

Syntax Description


Command Default


Command Modes


Device Modes Default


Usage Guidelines

Use the show accelerator http object-cache command to display HTTP object cache configuration and status information for a WAAS device.

Examples

The following example shows output from the show accelerator http object-cache command:
-------------------------------

Related Commands

show alarms
To display information about various types of alarms, their status, and history on a WAAS device, use the show alarms EXEC command.
show alarms critical [ detail [ support ]]
show alarms detail [ support ]
show alarms history [ start_num [ end_num [ detail [ support ]]]] | critical [ start_num [ end_num [ detail [ support ]]]]
show alarms major [ start_num [ end_num [ detail [ support ]]]]
show alarms minor [ start_num [ end_num [ detail [ support ]]]]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The Node Health Manager in the WAAS software enables WAAS applications to raise alarms to draw attention in error/significant conditions. The Node Health Manager, which is the data repository for such alarms, aggregates the health and alarm information for the applications, services, and resources (for example, disk drives) that are being monitored on the WAAS device. For example, this feature gives you a mechanism to determine if a WAE is receiving overwhelming number of alarms. These alarms are referred to as WAAS software alarms.
The WAAS software uses SNMP to report error conditions by generating SNMP traps. The following WAAS applications can generate a WAAS software alarm:
The three levels of alarms in the WAAS software are as follows:
- Critical—Alarms that affect the existing traffic through the WAE and are considered fatal (the WAE cannot recover and continue to process traffic).
- Major—Alarms that indicate a major service (for example, the cache service) has been damaged or lost. Urgent action is necessary to restore this service. However, other node components are fully functional and the existing service should be minimally impacted.
- Minor—Alarms that indicate that a condition that will not affect a service has occurred, but that corrective action is required to prevent a serious fault from occurring.
You can configure alarms using the snmp-server enable traps alarms global configuration command.
Use the show alarms critical EXEC command to display the current critical alarms being generated by WAAS software applications. Use the show alarms critical detail EXEC command to display additional details for each of the critical alarms being generated. Use the show alarms critical detail support EXEC command to display an explanation about the condition that triggered the alarm and how you can find out the cause of the problem. Similarly, you can use the show alarms major and show alarms minor EXEC commands to display the details of major and minor alarms.
Use the show alarms history EXEC command to display a history of alarms that have been raised and cleared by the WAAS software on the WAAS device since the last software reload. The WAAS software retains the last 100 alarm raise and clear events only.
Use the show alarms status EXEC command to display the status of current alarms and the alarm overload status of the WAAS device and alarm overload configuration.
Examples
Table 3-4 describes the fields shown in the show alarms history command display.
Table 3-5 describes the fields shown in the show alarms status command display.
Related Commands
show appnav-controller flow-distribution
To display ANC flow distribution information, use the show appnav-controller flow-distribution EXEC command.
show appnav-controller flow-distribution [ client-ip ip_address | client-port port | peer-id peer_id | server-ip ip_address | server-port port ]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
This command can be used to determine how a flow would be classified and redirected.
Examples
The following is sample output from the show appnav-controller flow-distribution command that shows how a flow would be redirected:
Related Commands
show arp
To display the Address Resolution Protocol (ARP) table for a WAAS device, use the show arp EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show arp command to display the Internet-to-Ethernet address translation tables of the Address Resolution Protocol. Without flags, the current ARP entry for the host name is displayed.
On an ISR-WAAS device, no ARP entries are present for IP addresses on the same subnet as the ISR-WAAS device; there is an entry only for the defined gateway.
The ARP cache is cleared based on the gc_stale_time; the default time is 60 seconds.
Cache entry states, described in Table 3-6, function as follows:
1.![]() An entry in the ARP table with a Reachable state is moved to the Stale state after the ReachableTime is exceeded, or an UnsolicitedNeighbor advertisement is received.
An entry in the ARP table with a Reachable state is moved to the Stale state after the ReachableTime is exceeded, or an UnsolicitedNeighbor advertisement is received.
2.![]() After an entry in the ARP table is moved to the Stale state, it sends an ARP request and is moved to the Delay state. It remains in the Delay state until it receives an acknowledgment.
After an entry in the ARP table is moved to the Stale state, it sends an ARP request and is moved to the Delay state. It remains in the Delay state until it receives an acknowledgment.
3.![]() Depending on the next action, the entry is then moved to the Reachable state or the Probe state:
Depending on the next action, the entry is then moved to the Reachable state or the Probe state:
–![]() If the entry receives an acknowledgment on time, it is moved to the Reachable state.
If the entry receives an acknowledgment on time, it is moved to the Reachable state.
–![]() If the entry does not receive an acknowledgment on time, it is moved to the Probe state.
If the entry does not receive an acknowledgment on time, it is moved to the Probe state.
Examples
Table 3-6 describes the fields shown in the show arp command display.
show authentication
To display the authentication configuration for a WAAS device, use the show authentication EXEC command.
show authentication { user | strict-password-policy}
Syntax Descriptions
Displays authentication configuration for user login to the system. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
When the WAAS device authenticates a user through an NTLM, LDAP, TACACS+, RADIUS, or Windows domain server, a record of the authentication is stored locally. As long as the entry is stored, subsequent attempts to access restricted Internet content by the same user do not require additional server lookups. To display the local and remote authentication configuration for user login, use the show authentication user EXEC command.
To display the strict password policy configuration information, use the show authentication strict-password-policy EXEC command.
Examples
Table 3-7 describes the fields shown in the show authentication user command display.
Table 3-8 describes the fields in the show authentication strict-password-policy command display. If the strict password policy is not enabled, the command displays, “Strict password policy is disabled.”
Related Commands
(config) authentication configuration
show auto-discovery
To display Traffic Flow Optimization (TFO) auto-discovery information for a WAE, use the show auto-discovery EXEC command.
show auto-discovery { blacklist [ netmask netmask ] | list [ | { begin regex [ regex ] | exclude regex [ regex ] | include regex [ regex ]}] | asymmetric-connections }
Syntax Description
Command Modes

Device Modes

Usage Guidelines
The asymmetric-connections option displays the last 1000 asymmetric connections seen on the device.
Examples
The following is sample output from the show auto-discovery list command:
Related Commands
show auto-register
To display the status of the automatic registration feature on a WAE, use the show auto-register EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-9 describes the output in the show auto-register command display.
|
|
|
|---|---|
Related Commands
show banner
To display the message of the day (MOTD), login, and EXEC banner settings, use the show banner EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-10 describes the fields shown in the show banner command display.
|
|
|
|---|---|
Related Commands
show bmc
To display the Baseboard Management Controller (BMC) system event log, use the show bmc EXEC command.
show bmc { info | fru | event-log [all | event | range | |] | management |}
Syntax Description
Displays the BMC system event log (by default, the last 10 events). |
|
Displays a single event number from the BMC system event log. |
|
Defaults
Command Modes

Device Modes

Examples
The following is a sample output from the show bmc command:
Related Commands
show bridge
To display bridge interface information for an AppNav Controller using inline interception, use the show bridge EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-11 describes the fields shown in the show bridge command display.
|
|
|
|---|---|
Displayed only if interface is configured with link state propagation. |
|
Status of link state propagation setting (enabled or disabled). |
|
Related Commands
show cache http-metadatacache
To display HTTP metadata cache information for a WAE, use the show cache http-metadatacache EXEC command.
show cache http-metadatacache https { conditional-response | redirect-response | sharepoint-prefetch | unauthorized-response }
show cache http-metadatacache { all | conditional-response | redirect-response |
sharepoint-prefetch | unauthorized-response } [ url ]
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-12 describes the fields shown in the show cache http-metadatacache all command display.
Related Commands
show cache object-cache
To display a list of individual objects in the cache, one per line, use the show cache object-cache EXEC command.
show cache object-cache [accelerator ao-name] {server-ip server-ip | server-host hostname | url path}
Syntax Description

Command Default


Command Modes


Device Modes Default


Usage Guidelines

Use the show cache object-cache command to display a list of individual objects in the cache, one per line. You can display a list of all individual objects, or only those that match specified criteria, such as server IP address or hostname, or path of a specified URL.

Examples

The following is sample output from the show cache object-cache command:
show cdp
To display CDP configuration information, use the show cdp EXEC command.
show cdp entry {* | neighbor} [ protocol | version ]
show cdp interface
[ GigabitEthernet slot/port | TenGigabitEthernet slot/port | InlinePort slot/port {lan | wan} ]
show cdp neighbors
[ detail | GigabitEthernet slot/port [ detail ] | TenGigabitEthernet slot/port [ detail ] | InlinePort slot/port/{lan/wan} [ detail ]]
show cdp {holdtime | run | timer | traffic}
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show cdp command displays information about how frequently CDP packets are resent to neighbors, the length of time that CDP packets are held by neighbors, the disabled status of CDP Version 2 multicast advertisements, CDP Ethernet interface ports, and general CDP traffic information. This command supports VLAN (802.1Q) tagged packets

Note![]() The CDP protocol is not supported for OVS (Open Virtual Switch) on RHEL KVM on CentOS, therefore the show cdp command cannot be used for vWAAS on RHEL KVM on CentOS.
The CDP protocol is not supported for OVS (Open Virtual Switch) on RHEL KVM on CentOS, therefore the show cdp command cannot be used for vWAAS on RHEL KVM on CentOS.
Examples
Table 3-13 describes the fields shown in the show cdp command display.
Table 3-14 describes the fields shown in the show cdp entry neighbor command display.
Table 3-15 describes the fields shown in the show cdp entry neighbor protocol command display.
Table 3-16 describes the fields shown in the show cdp entry neighbor version command display.
|
|
|
|---|---|
Table 3-17 describes the field in the show cdp holdtime command display.
Table 3-18 describes the fields shown in the show cdp interface command display.
Table 3-19 describes the fields shown in the show cdp neighbors command display.
Table 3-20 describes the fields shown in the show cdp neighbors detail command display.
Table 3-21 describes the field in the show cdp run command display.
|
|
|
|---|---|
Table 3-22 describes the field in the show cdp timer command display.
|
|
|
|---|---|
Table 3-23 describes the fields shown in the show cdp traffic command display.
Related Commands
show class-map
To display the matching criteria configured for an AppNav or optimization class map, use the show class-map EXEC command.
show class-map type { appnav | waas } [ classmap-name ]
Syntax Description
Displays the specified AppNav class map, or all class maps if no class map is specified. |
|
Displays the specified WAAS optimization class map, or all class maps if no class map is specified. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
This command displays the matching criteria for all class maps or a specified class map in the active policy. It also displays the number of flows that have matched each condition, in all uses of the class map, including in nested policy maps.
Examples
The following is sample output from the show class-map type appnav command.
Related Commands
show clock
To display information about the system clock on a WAAS device, use the show clock EXEC command.
show clock [ detail | standard-timezones { all | details timezone | regions | zones region-name } ]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The WAAS device has several predefined standard time zones. Some of these time zones have built-in summer time information while others do not. For example, if you are in an eastern region of the United States (US), you must use the US/Eastern time zone that includes summer time information for the system clock to adjust automatically every April and October. There are about 1500 standard time zone names.
Strict checking disables the clock summertime command when you configure a standard time zone is configured. You can configure summer time only if the time zone is not a standard time zone (that is, if the time zone is a customized zone).
The show clock standard-timezones all EXEC command enables you to browse through all standard timezones and choose from these predefined time zones so that you can choose a customized name that does not conflict with the predefined names of the standard time zones. Most predefined names of the standard time zones have two components, a region name and a zone name. You can list time zones by several criteria, such as regions and zones. To display all first level time zone names organized into directories by region, use the show clock standard-timezones region EXEC command.
The show clock command displays the local date and time information and the show clock detail command shows optional detailed date and time information.
Examples
Table 3-24 describes the field in the show clock command display.
|
|
|
|---|---|
Day of the week, month, date, time (hh:mm:ss), and year in local time relative to the UTC offset. |
Table 3-25 describes the fields shown in the show clock detail command display.
|
|
|
|---|---|
Related Commands
show cms
To display Centralized Management System (CMS) embedded database content and maintenance status and other information for a WAAS device, use the show cms EXEC command.
show cms { database content { dump filename | text | xml } | info | secure-store | device status name }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show cms device status command is not available on a standby Central Manager.
Examples
Table 3-26 describes the fields shown in the show cms info command display for WAAS application engines.
Table 3-27 describes the fields shown in the show cms info command display for WAAS Central Managers.
Table 3-28 describes the field in the show cms database content text command display.
Table 3-29 describes the field in the show cms database content xml command display.
Related Commands
show cms secure-store
To display secure store status, use the show cms secure-store EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show cms secure-store command will display one of the following status messages ( Table 3-30 ):
Examples
The following is sample output from the show cms secure-store command:
Related Commands
show crypto
To display crypto layer information, use the show crypto EXEC command.
show crypto {certificate-detail {factory-self-signed | management | admin | filename} | certificates | ssl services {accelerated-service service | host-service peering}}
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-31 describes the fields in the show crypto certificate-detail command display.
Table 3-32 describes the fields in the show crypto certificates command display.
Related Commands
show debugging
To display the state of each debugging option that was previously enabled on a WAAS device, use the show debugging EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show debugging command shows which debug options have been enabled or disabled. If there are no debug options configured, the show debugging command shows no output.
The dre, epm, flow, print-spooler, rbcp, tfo, translog, and wccp command options are supported in the application-accelerator device mode only. The emdb and rpc command options are supported in the central manager device mode only.
The show debugging command displays only the type of debugging enabled, not the specific subset of the command.
Examples
The following is sample output from the show debugging command:
In this example, the debug tfo buffer-mgr and the debug tfo connection commands coupled with the show debugging command display the states of tfo buffer-mgr and tfo connection debugging options.
Related Commands
show device-id
To display the device ID of a WAAS device, use the show device-id EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
This command displays the device ID, as follows:
Related Commands
show device-mode
To display the configured or current device mode of a WAAS device, use the show device-mode EXEC command.
show device-mode { configured | current | profile-branch }
Syntax Description
Displays the configured device mode, which has not taken effect yet. |
|
Displays the branch profile mode, for use with the WAVE-7571, which enables the device to function as a branch device. |
Defaults
Command Modes

Device Modes

Usage Guidelines
To display the configured device mode that has not yet taken effect, enter the show device-mode configured EXEC command. For example, if you had entered the device mode central-manager global configuration command on a WAAS device to change its device mode to central manager but have not yet entered the copy run start EXEC command to save the running configuration on the device, then if you were to enter the show device-mode configured command on the WAAS device, the command output would indicate that the configured device mode is central-manager.
Examples
The following is sample output from the show device mode command. It displays the current mode in which the WAAS device is operating.
Table 3-33 describes the field in the show device-mode current command display.
|
|
|
|---|---|
The following is sample output from the show device configured command. It displays the configured device mode that has not yet taken effect.
Table 3-34 describes the field in the show device-mode configured command display.
|
|
|
|---|---|
Device mode that has been configured, but has not yet taken effect. |
Related Commands
show disks
To view information about the WAAS device disks, use the show disks EXEC command.
show disks {cache-details | details | failed-disk-id | failed-sectors [ disk_name ] | tech-support [ details | fwlogs ]}
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show disks details EXEC command displays the percentage or amount of disk space allocated to each file system, and the operational status of the disk drives, after reboot.
The WAAS software supports filtering of multiple syslog messages for a single, failed section on IDE, SCSI, and SATA disks.

Note![]() When the system software recovery procedure is used and the system reboots and begins optimizing traffic, the show disks details command may show that the /dre1 partition is 98% or more used, due to the preallocation of DRE cache space. Use the show statistics dre command to display the actual DRE cache usage.
When the system software recovery procedure is used and the system reboots and begins optimizing traffic, the show disks details command may show that the /dre1 partition is 98% or more used, due to the preallocation of DRE cache space. Use the show statistics dre command to display the actual DRE cache usage.
Proactively Monitoring Disk Health with SMART
The ability to proactively monitor the health of disks is available using SMART. SMART provides you with hard drive diagnostic information and information about impending disk failures.
SMART is supported by most disk vendors and is a standard method used to determine how healthy a disk is. SMART attributes include several read-only attributes (for example, the power on hours attribute, the load and unload count attribute) that provide the WAAS software with information regarding the operating and environmental conditions that may indicate an impending disk failure.
SMART support is vendor and drive technology (IDE, SCSI, and Serial Advanced Technology Attachment [SATA] disk drive) dependent. Each disk vendor has a different set of supported SMART attributes.
Even though SMART attributes are vendor dependent there is a common way of interpreting most SMART attributes. Each SMART attribute has a normalized current value and a threshold value. When the current value exceeds the threshold value, the disk is considered to have “failed.” The WAAS software monitors the SMART attributes and reports any impending failure through syslog messages, SNMP traps, and alarms.
To display SMART information, use the show disks tech-support EXEC command. To display more detailed SMART information, enter the show disks tech-support details EXEC command. The output from the show tech-support EXEC command also includes SMART information.
Examples
The following is sample output from the show disks failed-sectors command. It displays a list of failed sectors on all disk drives.
WAE# show disks failed-sectors
disk00
=========
89923
9232112
disk01
=========
(None)
The following is sample output from the show disks failed-sectors command when you specify a disk drive. It displays a list of failed sectors for disk01.
WAE# show disks failed-sectors disk01
disk01
=========
(None)
If there are disk failures, a message is displayed, notifying you about this situation when you log in.
Table 3-35 describes the fields shown in the show disks failed-disk-id command display.
|
|
|
|---|---|
The following is sample output from the show disks cache- details command.
WAE# show disks cache-details
Mode # oc-weight2
Name Default MB Existing MB Configured MB Configured %
----------------------------------------------------------------------------------------
Akamai 189440 MB 189440 MB 64512 MB 20.26%
Object-cache 129024 MB 129024 MB 253952 MB 79.74%
Table 3-36 describes the fields shown in the show disks cache-details command display.
Table 3-37 describes the fields shown in the show disks details command display.
The following is sample output from the show disks tech-support command. The output shows that partition 04 and partition 05 on disks disk00 and disk01 are GOOD, and the RAIDed partitions /dev/md4 & /dev/md5 are in NORMAL OPERATION. However, the RAIDed partition /dev/md8 has an issue with one of the drives. Disk04 with partition 00 is GOOD, but the status shows ONE OR MORE DRIVES ABNORMAL because there is no pair on this partition.
Table 3-38 describes some typical fields in the show disks tech-support command display for a RAID-1 appliance that supports SMART. SMART attributes are vendor dependent; each disk vendor has a different set of supported SMART attributes.
Table 3-39 describes the fields shown in the show disks tech-support command display for a RAID-5 appliance.
Table 3-40 describes the fields in the show disks tech-support details command display for a RAID-1 appliance that supports SMART. Details in this display depend on the drive manufacturer and vary between drives.
Related Commands
show dre
To view DRE configuration information, use the show dre EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following is sample output from the show dre EXEC command:
Related Commands
show filtering list
To display information about the incoming and outgoing TFO flows that the WAE currently has, use the show filtering list EXEC command.
show filtering list [ | { begin regex [ regex ] | exclude regex [ regex ] | include regex [ regex ] }] [ | { begin regex [ regex ] | exclude regex [ regex ] | include regex [ regex ]}]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show filtering list command lists TCP flows that the WAE is currently optimizing. It also includes TCP flows that are not being optimized but that are being passed through by the WAE. A “P” in the State column indicates a passed through flow.
Examples
The following is sample output from the show filtering list command. It displays TFO connection information for the WAE.

Note![]() The “ED” state occurs when one socket in the pair is closed (D), but the mate is still established (E).
The “ED” state occurs when one socket in the pair is closed (D), but the mate is still established (E).
Related Commands
show flash
To display the flash memory version and usage information for a WAAS device, use the show flash EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-41 describes the fields shown in the show flash command display.
show flow record
To display collection information for a WAAS device, use the show flow record EXEC command. Collection information includes source and destination address, source and destination port, class name, number of optimized and unoptimized packets, input/output information for DRE and LZ compression, and average latency encode/decode information for DRE and LZ compression.
show flow record {RecordName [template]}
Syntax Description
The identity of the template associated with this flow record. |
Defaults

Device Modes

Command Modes
Examples
The following is sample output from the show flow record command.
Table 3-42 describes the fields shown in the show flow record command display.
|
|
|
|---|---|
Unique ID of the template matching the type of NetFlow data it exports. |
|
Related Commands
show hardware
To display system hardware status for a WAAS device, use the show hardware EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show hardware command lists the system hardware status, including the version number, the startup date and time, the run time since startup, the microprocessor type and speed, the amount of physical memory available, and a list of disk drives.
Examples
Table 3-43 describes the fields shown in the show hardware command display. The display may vary depending on the hardware platform.
Related Commands
show hosts
To view the hosts on a WAAS device, use the show hosts EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show hosts command lists the name servers and their corresponding IP addresses. It also lists the hostnames, their corresponding IP addresses, and their corresponding aliases (if applicable) in a host table summary.
Examples
Table 3-44 describes the fields shown in the show hosts command display.
|
|
|
|---|---|
Name configured for the current device based on the host global configuration command. |
|
Related Commands
(config) ip hosts
show inetd
To display the status of TCP/IP services on a WAAS device, use the show inetd EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show inetd EXEC command displays the enabled or disabled status of TCP/IP services on the WAAS device. You can ignore the TFTP service status because TFTP is not supported on WAAS.
Examples
Table 3-45 describes the fields shown in the show inetd command display.
|
|
|
|---|---|
Related Commands
show interception-method
To display the configured interception method, use the show interception-method EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following is sample output from the show interception-method command:
Related Commands
show interface
To display the hardware interface information for a WAAS device, use the show interface EXEC command.
show interface { GigabitEthernet slot/port | InlineGroup slot / grpnumber |
InlinePort slot / grpnumber { lan | wan } | PortChannel index | standby grpnumber |
virtual slot/port | TenGigabitEthernet slot/port | bvi bridge-id } [ detail ]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelinescentral-manager
On an AppNav Controller device with a port-channel interface configured, interception statistics are collected only for the port-channel interface, not for the individual member interfaces.
Usage Guidelines
The show interface command displays hardware interface information for a WAAS device, such as interface operating mode, interception statistics, packets sent, and active optimized flows.

Note![]() When you use the show interface PortChannel index detail command on an interface with an AppNav Controller, the output may display an error count larger than zero (0) for the Length Error Frames Received counter. The displayed error count does not impact WAAS performance: the packets will not be dropped and will undergo further processing.
When you use the show interface PortChannel index detail command on an interface with an AppNav Controller, the output may display an error count larger than zero (0) for the Length Error Frames Received counter. The displayed error count does not impact WAAS performance: the packets will not be dropped and will undergo further processing.

Note![]() If a WAAS device is running for an extended period of time (13 hours or more) without a restart, output for the show interface command may erroneously show input errors for the device. To clear these statistics, reload the device, run the show interface command, and the input errors count will be cleared to zero.
If a WAAS device is running for an extended period of time (13 hours or more) without a restart, output for the show interface command may erroneously show input errors for the device. To clear these statistics, reload the device, run the show interface command, and the input errors count will be cleared to zero.
Examples
The following is sample output from the show interface command. It displays information for GigabitEthernet interface 0 in slot 0:
Table 3-46 describes the fields shown in the show interface GigabitEthernet command. Most of the other show interface command options display similar output.
Table 3-47 describes the fields shown in the show interface InlineGroup command.
Related Commands
(config) interface GigabitEthernet
show inventory
To display the system inventory information for a WAAS device, use the show inventory EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show inventory EXEC command allows you to view the UDI for a WAAS device. This identity information is stored in the nonvolatile memory of the WAAS device.
The UDI is electronically accessed by the product operating system or network management application to enable identification of unique hardware devices. The data integrity of the UDI is vital to customers. The UDI that is programmed into the nonvolatile memory of the WAAS device is equivalent to the UDI that is printed on the product label and on the carton label. This UDI is also equivalent to the UDI that can be viewed through any electronic means and in all customer-facing systems and tools. Currently, there is only CLI access to the UDI; there is no SNMP access to the UDI information.
You can also use the show tech-support EXEC command to display the WAAS device UDI.
Examples
Table 3-48 describes the fields shown in the show inventory command display.
Related Commands
show ip access-list
To display the access lists that are defined and applied to specific interfaces or applications on a WAAS device, use the show ip access-list EXEC command.
show ip access-list [ acl-name | acl-num ]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show ip access-list EXEC command to display the access lists that have been defined on the WAAS device and what rules are being hit. Unless you identify a specific access list by name or number, the system displays information about all the defined access lists, including the following sections:
- Available space for new lists and conditions
- Defined access lists
- References by interface and application
Interception access lists are shown under the Application access list references section.
Examples
Table 3-49 describes the fields shown in the show ip access-list command display.
Related Commands
show ip routes
To display the IP routing table for a WAAS device, use the show ip routes EXEC command.
show ip routes [ data | management ]
Syntax Description
Defaults
Displays the routing table for both data and management traffic.
Command Modes

Device Modes

Usage Guidelines
The show ip routes command displays the IP route table, which lists all of the different routes that are configured on the WAE. The WAE uses this table to determine the next hop. This table includes routes from three sources: the WAE interfaces, any user-configured static routes, and the default gateway. The last line in the Data Routes table shows the default route.
Examples
Table 3-50 describes the fields shown in the show ip routes command display.
|
|
|
|---|---|
Related Commands
show ipv6
To display the IPv6 configuration for a WAAS device, use the show ip v6 EXEC command.
show ipv6 { neighbors {virtual slot/port | GigabitEthernet [slot number/port] | Portchannel [Etherchannel index] | standby [standby index] } | routes {data | management }}
Syntax Description
Defaults
Displays the neighbor details and routing table for both data and management traffic.
Command Modes

Device Modes

Usage Guidelines
The show ipv6 command displays the IPv6 configuration on a WAAS device, This includes the ipv6 address, local-link addresses and the default gateway of all the cached entries for the neighbor interfaces on a WAAS device. The show ipv6 routes command displays the IP route table, which lists all of the different routes that are configured on the WAE. The WAE uses this table to determine the next hop. This table includes routes from three sources: the WAE interfaces, any user-configured static routes, and the default gateway. The last line in the Data Routes table shows the default route
Examples
Table 3-51 describes the fields shown in the show ipv6 command display.
|
|
|
|---|---|
Related Commands
show kdump
To display the kernel crash dump information for a WAAS device, use the show kdump EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-52 describes the fields shown in the show kdump command display.
|
|
|
|---|---|
If the kdump package is not installed, this line alerts you. |
|
Related Commands
show kerberos
To display the Kerberos authentication configuration for a WAAS device, use the show kerberos EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-53 describes the fields shown in the show kerberos command display.
|
|
|
|---|---|
Name of the host running the Key Distribution Center for the realm. |
|
Port that the Kerberos server is using for incoming requests from clients. The default is port 88. |
|
Related Commands
show key-manager
To display the key manager information for a WAAS Central Manager, use the show key-manager EXEC command.
show key-manager { key-token | status }
Syntax Description
Displays the encryption key token for each registered WAE device. |
|
Displays the encryption status for each registered WAE device. |
Defaults
Command Modes

Device Modes

Usage Guidelines
Examples
Table 3-54 describes the fields shown in the show key-manager key-token command display. The set of fields is displayed for each key used on each WAE registered to the Central Manager.
|
|
|
|---|---|
Related Commands
show license
To display license information for a WAAS device, use the show license EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following is sample output from the show license command. It lists the WAAS licenses, giving the name, status, date applied, and the name of the user that applied the license for each active license.
Related Commands
show logging
To display the system message log configuration for a WAAS device, use the show logging EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the system message log to view information about events that have occurred on a WAAS device. The syslog.txt file is contained in the /local1 directory.
Examples
The following is sample output from the show logging command. It displays the syslog host configuration on a WAAS device.
Related Commands
show memory
To display memory blocks and statistics for a WAAS device, use the show memory EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-55 describes the fields shown in the show memory command display.
|
|
|
|---|---|
Total amount of system memory in kilobytes (KB), not including the amount reserved for the rescue kernel. |
|
show monitor
To show the status of traffic monitoring on an AppNav Controller Interface Module, use the show monitor EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to display traffic monitoring status:
Related Commands
clear statistics monitor appnav-controller traffic
show ntp
To display the NTP parameters for a WAAS device, use the show ntp EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-56 describes the fields shown in the show ntp status command display.
Related Commands
show peer optimization
To display the configured serial peers for a WAAS device, use the show peer optimization EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following example shows how to display the device IDs of the configured nonoptimizing peer devices:
Related Commands
show policy-map
To display the policy map rules configured for an AppNav or optimization class map, use the show policy-map EXEC command.
show policy-map type { appnav | waas } [ policymap-name ]
Syntax Description
Displays the specified AppNav policy map, or all policy maps if no policy map is specified. |
|
Displays the specified WAAS optimization policy map, or all policy maps if no policy map is specified. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
This command displays the policy rules for all policy maps or a specified policy map. It also displays the number of flows that have matched each class map and the total number of flows that have matched the policy. For nested policy maps, a match is counted for each policy map involved in the classification of a connection.
Examples
The following is sample output from the show policy-map type appnav command.
Related Commands
show policy-sub-class
To display the matching criteria and flows for an AppNav class map, use the show policy-sub-class EXEC command.
show policy-sub-class type appnav [ all | level1-class classmap-name [ level2-class classmap-name ]]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show policy-sub-class type appnav command displays a list of all the class maps in the active AppNav policy map and any nested policy maps. It also displays the number of flows that have matched each class map, in all uses of the class map, including in all nested policy maps.
The show policy-sub-class type appnav all command displays a list of class maps and their matching criteria for all class maps in the active AppNav policy map and any nested policy maps. It also displays the number of flows that have matched each class map and condition, in all uses of the class map, including in all nested policy maps.
The show policy-sub-class type appnav level1-class classmap-name command displays the matching criteria for the specified class map in the top-level AppNav policy map, including matching criteria for all class maps in any nested policies. It also displays the number of flows that have matched each class map and condition, in all uses of the class map within the specified top-level class map.
The show policy-sub-class type appnav level1-class classmap-name level2-class classmap-name command displays the matching criteria for the specified class map in a nested AppNav policy map. It also displays the number of flows that have matched the class map and each condition, only within the nested policy map level for the specified top-level class map.
Examples
The following is sample output from the show policy-sub-class type appnav all command.
Related Commands
show processes
To display CPU or memory processes for a WAAS device, use the show processes EXEC command.
show processes [ cpu | debug pid | memory | system [ delay secs | count num ]]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the EXEC commands shown in this section to track and analyze system CPU utilization. For real time CPU utilization information, use the top EXEC command.
The show processes debug command displays extensive internal system call information and a detailed account of each system call (along with arguments) made by each process and the signals it has received.
Use the show processes system command to display system load information in terms of updates. The delay option specifies the delay between updates, in seconds. The count option specifies the number of updates that are displayed. The show processes debug command displays these items:
- A list of all processes in wide format.
- Two tables listing the processes that utilize CPU resources. The first table displays the list of processes in descending order of utilization of CPU resources based on a snapshot taken after the processes system (ps) output is displayed. The second table displays the same processes based on a snapshot taken 5 seconds after the first snapshot.
- Virtual memory used by the corresponding processes in a series of five snapshots, each separated by 1 second.

Note![]() CPU utilization and system performance are severely affected when you use these commands. We therefore recommend that you avoid using these commands, especially the show processes debug command, unless it is absolutely necessary.
CPU utilization and system performance are severely affected when you use these commands. We therefore recommend that you avoid using these commands, especially the show processes debug command, unless it is absolutely necessary.
Examples
Table 3-57 describes the fields shown in the show processes command display.
Related Commands
show radius-server
To display RADIUS configuration information for a WAAS device, use the show radius-server EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-58 describes the fields shown in the show radius-server command display.
Related Commands
show reload
To display scheduled reload information, use the show reload EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Related Commands
show running-config
To display a WAAS device current running configuration on the terminal, use the show running-config EXEC command. The show running-config command replaces the write terminal command.
show running-config [interface | no-policy | policy | snmp | wccp]
Syntax Description
(Optional) Does not display the policy engine configuration. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
Use this EXEC command in conjunction with the show startup-config command to compare the information in running memory to the startup configuration used during bootup.
Examples
The following is sample output from the show running-config command. It displays the currently running configuration of a WAAS device.
Related Commands
show service-insertion
To display information about the entities (WNs, WNGs, ANCs, ANCG, and a service context) defined in an AppNav Cluster configuration and the cluster status, use the show service-insertion EXEC command.
show service-insertion { data-path mtu | pass-through offload | service-context [ detail ] | appnav-controller ip-address | appnav-controller-group | service-node [ ip-address ] | service-node-group [ sngroupname ]}
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
This command returns minimal information if the entity or service context is disabled, or if the entity is not attached to the service context.
Although software version 6.x.x does not support Video and CIFS traffic acceleration, the Video and CIFS load markers have been retained in the show service-insertion service-node command for backward compatibility. This is to ensure that an AppNav Controller in version 5.x.x is able to forward a request for traffic acceleration to a Service Node in version 6.x.x.
Examples
Table 3-59 describes the fields shown in the show service-insertion service-context command display.
Table 3-60 describes the additional fields shown in the show service-insertion service-context detail command display. The AppNav Controller Group and AppNav Controller sections of this table also describe the fields shown in the show service-insertion appnav-controller-group command display. The AppNav Controller section of this table also describes the fields shown in the show service-insertion appnav-controller command display.
The Service Node Group and Service Node sections of this table also describe the fields shown in the show service-insertion service-node-group command display. The Service Node section of this table also describes the fields shown in the show service-insertion service-node command display.
Related Commands
show service-policy
To display information about the optimization or AppNav policies, use the show service-policy EXEC command.
show service-policy type { appnav { dynamic [ detail | server-ip ip_address | server-port port ]| epm | status } | waas { application-name | dynamic [ app-id { app-id | mapi | ms-ad-rep | ms-exch-nspi | ms-frs | ms-frs-api | ms-rfr | ms-sql | msn-messenger | netlogon }| detail | dm-index index | server-ip ip_address | server-port port ]| status }}
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-61 describes the fields shown in the show service-policy type appnav status command display.
Table 3-62 describes the fields shown in the show service-policy type waas status command display.
Table 3-63 describes the fields shown in the show service-policy type appnav epm command display.
The following is sample output from the show service-policy type appnav epm command:
Table 3-64 describes the fields shown in the show service-policy type waas application-name command display.
|
|
|
|---|---|
Related Commands
show services
To display services-related information for a WAAS device, use the show services EXEC command.
show services { ports [ port-num ] | summary }
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following is sample output from the show services command. It displays a summary of the services.
show smb-conf
To view the current values of the Samba configuration file, smb.conf, on a WAAS device, use the show smb-conf EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show smb-conf command displays the global, print$, and printers parameters values of the smb.conf file for troubleshooting purposes. For a description of these parameters and their values, see the (config) smb-conf command.
Examples
The following is sample output from the show smb-conf command. It displays all of the parameter values for the current configuration.
Related Commands
show snmp
To check the status of SNMP communications for a WAAS device, use the show snmp EXEC command.
show snmp { alarm-history | engineID | event | group | stats | user }
Syntax Description
Displays events configured through the Event MIB. This keyword applies only to application-accelerator device mode. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
The show snmp alarm-history command provides information on various SNMP variables and statistics on SNMP operations.
Examples
Table 3-65 describes the fields shown in the show snmp alarm-history command display.
Table 3-66 summarizes the mapping of module names to module IDs.
|
|
|
|---|---|
Table 3-67 summarizes the mapping of category names to category IDs.
|
|
|
|---|---|
Table 3-68 describes the fields shown in the show snmp engineID command display.
|
|
|
|---|---|
String that identifies the copy of SNMP on the local device. |
Table 3-69 describes the fields shown in the show snmp event command display. The show snmp event command displays information about the SNMP events that were set using the ssh command:
Table 3-70 describes the fields shown in the show snmp group command display.
|
|
|
|---|---|
Name of the SNMP group, or collection of users who have a common access policy. |
|
Table 3-71 describes the fields shown in the show snmp stats command display.
Table 3-72 describes the fields shown in the show snmp user command display.
Related Commands
(config) snmp-server community
(config) snmp-server enable traps
show ssh
To display the status and configuration information of the Secure Shell (SSH) service for a WAAS device, use the show ssh EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-73 describes the fields shown in the show ssh command display.
|
|
|
|---|---|
Status of whether the SSH service is enabled or not enabled. |
|
SSH key has not been generated or previous key has been removed. |
|
Related Commands
show startup-config
To display the startup configuration for a WAAS device, use the show startup-config EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use this EXEC command to display the configuration used during an initial bootup, stored in NVRAM. Note the difference between the output of this command versus the show running-config command.
Examples
The following is sample output from the show startup-config command. It displays the configuration saved for use on startup of the WAAS device.
Related Commands
show statistics accelerator
To display application accelerator general statistics for a WAAS device, use the show statistics accelerator EXEC command.
show statistics accelerator detail
show statistics accelerator epm [ detail ]
show statistics accelerator generic { connections { epm | http | ica | mapi | smb | ssl }| detail }
show statistics accelerator http [ debug | detail | https ]
show statistics accelerator ica [ detail ]
show statistics accelerator mapi [ detail ]
show statistics accelerator mapi detail rpchttp
show statistics accelerator smb [ debug | detail | inc Print | request ]
show statistics accelerator ssl [ detail | payload {http | other} ]
show statistics accelerator wansecure [ detail ]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Using the show statistics accelerator command with no options displays a summary of the statistical information for all application accelerators. To obtain detailed statistics for an application accelerator, use the command options to filter the results.
Examples
Table 3-74 describes the fields shown in the show statistics accelerator epm detail command display.
|
|
|
|---|---|
Table 3-75 describes the fields shown in the show statistics accelerator generic connections detail command display. This command shows the aggregated statistics for all connections.
Table 3-76 describes the fields shown in the show statistics accelerator http detail command display.
Table 3-77 describes the fields shown in the show statistics accelerator http debug command display.
Table 3-78 describes the fields shown in the show statistics accelerator http https command display.
Table 3-79 describes the fields shown in the show statistics accelerator ica detail command display.
Table 3-80 describes the fields shown in the show statistics accelerator mapi detail command display.
Table 3-81 describes the fields shown in the show statistics accelerator mapi detail rpchttp command display.
Table 3-82 describes the fields shown in the show statistics accelerator smb detail command display.
Table 3-83 describes the fields shown in the show statistics accelerator smb debug command display.
Table 3-83 Field Descriptions for the show statistics accelerator smb d ebug Command (continued)
Table 3-84 describes the fields shown in the show statistics accelerator smb | inc Print command display.
Table 3-85 describes the fields shown in the show statistics accelerator ssl detail command display.
Table 3-86 describes the fields shown in the show statistics accelerator ssl payload http command display.
Table 3-87 describes the fields shown in the show statistics accelerator ssl payload other command display.
Related Commands
show statistics accelerator http object-cache
To display object cache statistics for a WAAS device, use the show statistics accelerator http object-cache EXEC command.
show statistics accelerator http object-cache

Syntax Description


Command Default


Command Modes


Device Modes Default


Usage Guidelines

Use show statistics accelerator http object-cache to display a summary of the number of HTTP transactions to the specified host. The top hosts list is always displayed after the cache-type statistics, and contains between 0-10 hosts. This same information can be displayed in graphics form in the Monitor > Caching >Akamai Connect section of the WCM.

Note![]() Depending on which cache types are enabled and what traffic is seen, the output may show statistics for any or all of the following cache types: bypass, standard, advanced, connected cache, OTT-youtube, OTT-generic, or unknown.
Depending on which cache types are enabled and what traffic is seen, the output may show statistics for any or all of the following cache types: bypass, standard, advanced, connected cache, OTT-youtube, OTT-generic, or unknown.

Examples

The following example shows sample output from the show statistics accelerator http object-cache command:
Object Cache Caching Type: ott-youtube
Object cache transactions served from cache: 7
Object cache request bytes for cache-hit transactions: 5560
Object cache response bytes for cache-hit transactions: 962534
Object cache transactions requiring freshness check: 1
Object cache responses not cached: 43
Object cache responses stored in cache: 295
Object Cache Caching Type: standard
Object cache transactions served from cache: 31
Object cache request bytes for cache-hit transactions: 10770
Object cache response bytes for cache-hit transactions: 50235
Object cache response time savings for cache-hit transactions: 5546
Average response time saved per cache-hit transactions (ms) 5
Percentage response time saving for cache-hit transactions: 60
Object cache transactions requiring freshness check: 3
Object cache responses not cached: 364
Object cache responses stored in cache: 65
Object cache top hosts ordered by: hit count
Object cache host name: au.download.windowsupdate.com
Object cache transaction count: 197
Object cache WAN response bytes: 54245680
Object cache LAN response bytes: 54260258
Object cache host name: r13---sn-hp576ne7.googlevideo.com
Object cache transaction count: 123
Object cache WAN response bytes: 40209279
Object cache LAN response bytes: 41180077
Object cache host name: s.youtube.com
Object cache transaction count: 102
Object cache WAN response bytes: 43160
Object cache LAN response bytes: 54551
Object cache top hosts ordered by: Total Response Time Savings
Object cache host name: www.carnival.com
Object cache transaction count: 31
Object cache WAN response bytes: 15
Object cache WAN response bytes: 329919

Related Commands

show statistics accelerator http preposition
To display preposition task status information for a WAAS device, use the show statistics accelerator http preposition EXEC command.
show statistics accelerator http preposition

Syntax Description


Command Default


Command Modes


Device Modes Default


Usage Guidelines

Use show statistics accelerator http preposition to display task status information for a WAAS device.

Examples

The following example shows output from the show statistics accelerator http preposition command:
show statistics aoim
To display AO (accelerator) Information Manager statistics for a WAAS device, use the show statistics aoim EXEC command.
show statistics aoim [ local | peer | detail]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show statistics aoim command with no options to display statistical information for locally registered application accelerators and all peer WAAS devices that the local WAAS device has encountered.
Examples
Table 3-88 describes the statistics that are displayed by the show statistics aoim EXEC command. Only the Local AOIM Statistics section is displayed when you use the local option. Only the Peer AOIM Statistics section is displayed when you use the peer option. The Detailed AOIM Statistics section is displayed only when you use the detail option.
Related Commands
show statistics application
To view the performance statistics for applications running on your WAAS device, use the show statistics application EXEC command.
show statistics application [ name app_name | savings [ appname app_name]]
Syntax Description
(Optional) Savings statistics for the specified application. |
Defaults
Command Modes

Device Modes

Usage Guidelines
The show statistics application command displays statistics for all of the application traffic running on your network. To view the statistics for one specific class of applications only, use the name keyword.
Table 3-89 lists the valid app_name values you can use with the show statistics application EXEC command. For a description of the applications supported by WAAS, see Appendix A, “Predefined Application Policies” in the Cisco Wide Area Application Services Configuration Guide.
If the HTTP connection to the client aborts while the file transfer is in progress, the show statistics application command output may display a higher total for optimized traffic than for original traffic. This is because the HTTP cache always caches the complete file, even if the connection to the client is aborted before the file transfer has completed.
|
|
|||
|---|---|---|---|
Examples
Table 3-90 describes the statistics for each class of application that are displayed by the show statistics application EXEC command.
Table 3-91 describes the result values shown for the statistics in the show statistics application command display.
Related Commands
show statistics appnav-controller
To display statistics for an AppNav Controller, use the show statistics appnav-controller EXEC command.
show statistics appnav-controller connection [ client-ip ip_address | client-port port | server-ip ip_address | server-port port | detail [client-ip ip_address | client-port port | server-ip ip_address | server-port port ] | summary ]
show statistics appnav-controller drop
show statistics appnav-controller flow-asymmetry
show statistics appnav-controller flow-management [ app-sess | appnav-controller-ip ip_address | detail | flow-table | syn ]
show statistics appnav-controller ip
show statistics appnav-controller sessions [ client-ip ip_address | server-ip ip_address | server-port port | detail [client-ip ip_address | server-ip ip_address | server-port port ] ]
Syntax Description
Defaults
Command Modes

Device Modes

Related Commands
show statistics authentication
To display authentication statistics for a WAAS device, use the show statistics authentication EXEC command.
show statistics authentication
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show statistics authentication command to display the number of authentication access requests, denials, and allowances recorded.
Examples
The following is sample output from the show statistics authentication command. It displays the statistics related to authentication on the WAAS device.
Related Commands
show statistics auto-discovery
To display Traffic Flow Optimization (TFO) auto-discovery statistics for a WAE, use the show statistics auto-discovery EXEC command.
show statistics auto-discovery [ blacklist ]
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-92 describes the result values shown for the statistics in the show statistics application command display.
Related Commands
show statistics class-default
To display statistics information about the class-default class map, use the show statistics class-default EXEC command.
show statistics class-default top-talkers
Syntax Description
Displays the statistics for the top 10 ports with the most traffic. |
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show statistics class-default top-talkers EXEC command to view statistics for traffic matched by the class-default class map. Statistics are displayed for the top 10 ports by traffic volume.
Examples
The following shows an example of output from the show statistics class-default top-talkers command.
Related Commands
show statistics class-map
To display statistics information about class maps, use the show statistics class-map EXEC command.
show statistics class-map type { appnav classmap-name | waas
[ name classmap-name | summary [ active | all ]]}
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show statistics class-map EXEC command to view statistics for class maps.
Examples
The following is sample output from the show statistics class-map type appnav command.
Related Commands
show statistics connection
To display all connection statistics for a WAAS device, use the show statistics connection EXEC command.
show statistics connection
auto-discovery{ client-ip [ ip_address | hostname ] | client port port | peer-id peer_id | server-ip { ip_address | hostname } | server-port port } |
client-ip { ip_address | hostname } | client-port port |
closed |
detail [client-ip { ip_address | hostname } | client-port port | peer-id peer_id | server-ip { ip_address | hostname } | server-port port ] |
egress methods |
optimized |
pass-through |
peer-id peer_id |
server-ip { ip_address | hostname } |
server-port port ] |
conn-id connection_id
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show statistics connection command displays the statistics for all TCP connections. This information is updated in real time.
Consider the following guidelines for the show statistics connection command:
Displays a summary of all the TCP connections on the WAE. To obtain detailed statistics for a connection, use the command options to filter the connection. While most filters show detail statistics, some filters (such as peer-id) show summary information and not details.
–![]() A new connection immediately replaces an old connection. If a connection termination takes less than 10 seconds, then the new connection replaces it. However, WAAS has pass-through connection entry for both new and old connections (connections lasting 10 seconds or more). Therefore, in a scenario where pass-through entries take 10 seconds or more to expire, the output from show statistics connection will show totals for both old and new connections.
A new connection immediately replaces an old connection. If a connection termination takes less than 10 seconds, then the new connection replaces it. However, WAAS has pass-through connection entry for both new and old connections (connections lasting 10 seconds or more). Therefore, in a scenario where pass-through entries take 10 seconds or more to expire, the output from show statistics connection will show totals for both old and new connections.
–![]() Unlike optimized flow, WAAS does not inspect each packet at TCP level to confirm when the connection got reset. Therefore, when there is no activity for 10 seconds, the pass-through flow entry get removed. The pass-through flows are then a count of pass-through flows seen in less than 10 seconds.
Unlike optimized flow, WAAS does not inspect each packet at TCP level to confirm when the connection got reset. Therefore, when there is no activity for 10 seconds, the pass-through flow entry get removed. The pass-through flows are then a count of pass-through flows seen in less than 10 seconds.
a.![]() Use the show statistics connection conn-id connection id to compare optimized traffic packet level bytes calculation (the amount of traffic that went across the WAN) with original traffic (the amount of traffic that went out the WAN) for a specific identifier.
Use the show statistics connection conn-id connection id to compare optimized traffic packet level bytes calculation (the amount of traffic that went across the WAN) with original traffic (the amount of traffic that went out the WAN) for a specific identifier.
|
|
|
|
|
|
78,7408
|
92,939
|
|
|
40,1764
|
117,657
|
|
|
1,189,172
|
210,596
|
b.![]() For this single connection, the amount of bytes that went across the WAN (210,596) is significantly less than the amount of bytes that went out the WAN (1,189,172).
For this single connection, the amount of bytes that went across the WAN (210,596) is significantly less than the amount of bytes that went out the WAN (1,189,172).
c.![]() To calculate the reduction in traffic use this formula:
To calculate the reduction in traffic use this formula:
1 - (total optimized bytes/total original bytes)
d.![]() In this example, the calculation is:
In this example, the calculation is:
1 - (210596/1189172) =.82290535 or 82.291%
e.![]() If the amount of optimized bytes is greater than the amount of original bytes, you see a total reduction ratio of 0.00%.
If the amount of optimized bytes is greater than the amount of original bytes, you see a total reduction ratio of 0.00%.
Table 3-93 describes the fields shown in the show statistics connection command display.
|
|
|
|---|---|
Number of current active optimized TCP connections of all types. |
|
Number of current active connections using DRE/LZ optimization or handled by an accelerator. |
|
Number of current active connections using TFO optimization only. |
|
Number of current active connections that were originated by an accelerator to acquire data in anticipation of its future use. |
|
Number of current active connections in the auto-discovery state. |
|
Number of connections reserved for the MAPI accelerator. It appears for all accelerators. |
|
Number of closed TCP connections for which statistical data exists. |
|
Types of acceleration in use on the connection. |
|
Relative reduction ratio (in bytes) for a particular connection. |
|
Connection type (see Table 3-94 ). |
Table 3-94 describes the possible values found in the ConnType field.
Related Commands
show statistics connection auto-discovery
To display auto-discovery connection statistics for a WAAS device, use the show statistics connection auto-discovery EXEC command.
show statistics connection auto-discovery
client-ip { ip_address | hostname } | client-port port | peer-id peer_id |
server-ip { ip_address | hostname } | server-port port
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
This command displays the statistics for auto-discovery TCP connections. This information is updated in real time.
To obtain detailed statistics for a connection, use the command options to filter the connection. While most filters show detail statistics, some filters (such as peer-id) show summary information and not details.
Examples
Table 3-95 describes the fields shown in the show statistics connection auto-discovery display.
|
|
|
|---|---|
Number of current active optimized TCP connections of all types. |
|
Number of current active connections using DRE/LZ optimization or handled by an accelerator. |
|
Number of current active connections using TFO optimization only. |
|
Number of current active connections that were originated by an accelerator to acquire data in anticipation of its future use. |
|
Number of current active connections in the auto-discovery state. |
|
Number of closed TCP connections for which statistical data exists. |
|
Origin state of the connection. |
|
Terminal state of the connection. |
|
Type of the connection (see Table 3-94 ). |
Related Commands
show statistics connection closed
To display closed connection statistics for a WAAS device, use the show statistics connection closed EXEC command.
show statistics connection closed
[detail | dre | epm | http | mapi | ssl | tfo | [client-ip { ip_address | hostname } |
client-port port | conn-id connection_id | peer-id peer_id | server-ip { ip_address | hostname } | server-port port ]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Using the show statistics connection closed command with no options displays a summary of the closed TCP connections on the WAE. To obtain detailed statistics for a connection, use the command options to filter the connection. While most filters show detail statistics, some filters (such as peer-id) show summary information and not details.
Examples
Table 3-96 describes the fields shown in the show statistics connection closed command display.
Related Commands
show statistics connection conn-id
To display connection ID statistics for a WAAS device, use the show statistics connection conn-id EXEC command.
show statistics connection conn-id connection_id
Syntax Description
(Optional) Connection statistics for the connection with the specified identifier number. |
Defaults
Command Modes

Device Modes

Usage Guidelines
The show statistics connection conn-id command displays the statistics for individual TCP connections. This information is updated in real time.
Examples
Table 3-97 describes the fields shown in the show statistics connection conn-id command display.
|
|
|
|---|---|
Flow was originated by an accelerator to acquire data in anticipation of its future use: true or false. |
|
Number of bytes that have been read and written on the original (incoming) side and the optimized (outgoing) side. |
|
Aggregated statistics for compressed messages. msg = Total number of messages. in = Number of bytes before decompression. out = Number of bytes after decompression. ratio = Percentage of the total number of bytes that were compressed. |
|
Percentage of total messages that fall within indicated size ranges. |
|
Total number of messages processed and the number of blocks used per message. |
|
Type of connection (see Table 3-94 ). |
|
Socket states, including read-shut, write-shut, close, choke, and envoy. |
|
Number of DRE hints sent for the local, remote, and active connections. |
|
Size of the messages waiting in the decode queue, including maximum size, current size, average size, and the number of flow-control stop messages. |
|
Number of calls encoded and decoded, the message latency (in ms), and the number of transmitted data/acknowledgment frames. |
|
Size of the messages waiting in the write queue, including maximum size, current size, average size, and the number of flow-control stop messages. |
|
Size of the messages written, total number of messages, the average size, and the message latency (in ms). |
Related Commands
show statistics connection egress-methods
To display detailed egress method-related information about the connection segments for a WAE, use the show statistics connection egress-methods EXEC command.
show statistics connection egress-methods
client-ip { ip_address | hostname } | client-port port | peer-id peer_id |
server-ip { ip_address | hostname } | server-port port
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Using the show statistics connection egress-methods command without options displays detailed information about each of the TFO connections for a WAE.
The show statistics connection egress-methods command displays egress method-related information about connection segments in an environment where the data flow from start-point to end-point is being transparently intercepted by multiple devices. A connection tuple represents one segment of an end-to-end connection that is intercepted by a WAAS device (WAE) for processing.
For example, a single client-server connection may have three segments (see Figure 3-1):
- Between the client and the Edge WAE
- Between the Edge WAE and the Core WAE
- Between the Core WAE and the server
In this example, the Edge WAE has two connection tuples for the two segments that it participates in the following:
- One connection tuple to represent the Client—Edge segment
- One connection tuple to represent the Edge—Core segment
In the show output, these two connection tuples appear as TUPLE and MATE. (See Table 3-98 .) The important information to view is the local and remote IP address of the connection tuple and not whether it is marked as TUPLE or MATE.
Figure 3-1 Topology with Three Segments and Corresponding Connection Tuples
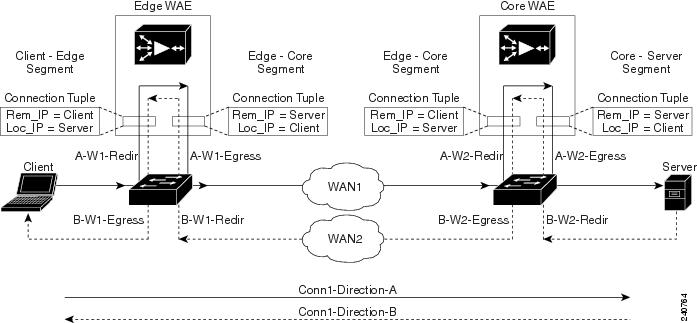
Because the WAAS device is transparent to both the client-end of the connection and the server-end of the connection, the local IP address for a connection tuple depends on the segment in the end-to-end topology.
For example, when WAAS intercepts a packet from the client, this packet enters the connection tuple that represents the Client—Edge segment. On this tuple, the WAAS device appears to the client as though it were the server: the local IP address in this connection tuple is the IP address of the server, while the remote IP address in this connection tuple is that of the client. Similarly, when the Edge WAE sends data to the client, the packet egresses from this connection tuple as though it were coming from the server.
When WAAS sends a packet to the server, the packet egresses from the connection tuple that represents the Edge—Core segment. On this tuple, the WAAS device appears to the server as though it were the client: the local IP address in the connection tuple is the IP address of the client, while the remote IP address in this connection tuple is that of the server. Similarly, when the Edge WAE intercepts a packet from the Core WAE, the data in this connection tuple appears to be coming from the server.
Examples
Table 3-98 describes the fields shown in the show tfo egress-methods connection command display.
Each time a packet enters the connection tuple, the intercepting device IP address or MAC address is recorded. The updates field in the command output indicates whether the intercepting device IP address or intercepting device MAC address has been recorded. If, for example, the ID MAC address updates field is zero (0), the MAC address was not recorded, and the ID MAC address field will be blank. The recorded intercepting device information is used when a packet egresses from the WAE.
If the egress method for the connection tuple is IP forwarding, the updates fields are always zero (0) because the intercepting device information is neither required nor recorded for the IP forwarding egress method.
If the intercept method is WCCP GRE redirect and the egress method is WCCP GRE, only the IP address field is updated and recorded. The MAC address information is neither required nor recorded because the destination address in the GRE header only accepts an IP address.
If the intercept method is WCCP L2 redirect and the egress method is WCCP GRE, both the MAC address and the IP address fields are updated and recorded because incoming WCCP L2 packets contain only a MAC header. The MAC address is recorded and the intercepting device IP address is derived from a reverse ARP lookup and is then recorded, also. When packets egress the connection tuple in this scenario, they will have a GRE header with the destination IP address of the intercepting device that was recorded.
The updates count may be greater than 1 in certain topologies. For example, in a redundant router topology, where for the same direction of the same connection between two hosts, packets may be coming in from different intercepting routers. Each time a packet comes in, the intercepting device MAC or IP address is compared against the last recorded address. If the MAC or IP address has changed, the updates field is incremented and the new MAC or IP address is recorded.
Related Commands
show statistics connection optimized
To display optimized connection statistics for a WAAS device, use the show statistics connection optimized EXEC command.
show statistics connection optimized
[client-ip { ip_address | hostname } | client-port port | peer-id peer_id | server-ip { ip_address | hostname } | server-port port |
{ http | ica | mapi | smb | ssl | wansecure | {detail | dre { all | savings | { http | ica | mapi | smb | ssl | wansecure }}]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show statistics connection optimized command displays the statistics for optimized TCP connections. This information is updated in real time.
Using the show statistics connection optimized command with no options displays a summary of all the optimized TCP connections on the WAE. To obtain detailed statistics for a connection, use the command options to filter the connection. While most filters show detail statistics, some filters (such as peer-id) show summary information and not details.
Examples
Table 3-99 describes the fields shown in the show statistics connection optimized command display.
Related Commands
show statistics connection pass-through
To display pass through connection statistics for a WAAS device, use the show statistics connection pass-through EXEC command.
show statistics connection pass-through
client-ip { ip_address | hostname } | client-port port | peer-id peer_id |
server-ip { ip_address | hostname } | server-port port
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show statistics connection pass-through command displays the statistics for passed through TCP connections. This information is updated in real time.
Using the show statistics connection pass-through command with no options displays a summary of all the passed through TCP connections on the WAE. To obtain detailed statistics for a connection, use the command options to filter the connection. While most filters show detail statistics, some filters (such as peer-id) show summary information and not details.
Examples
Table 3-100 describes the fields shown in the show statistics connection pass-through command display.
|
|
|
|---|---|
Number of current active optimized TCP connections of all types. |
|
Number of current active connections using DRE/LZ optimization or handled by an accelerator. |
|
Number of current active connections using TFO optimization only. |
|
Number of current active connections that were originated by an accelerator to acquire data in anticipation of its future use. |
|
Number of current active connections in the auto-discovery state. |
|
Number of closed TCP connections for which statistical data exists. |
|
Status of the connection (see Table 3-94 ). |
Related Commands
show statistics crypto ssl ciphers
To display crypto SSL cipher usage statistics, use the show statistics crypto ssl ciphers EXEC command.
show statistics crypto ssl ciphers
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show statistics crypto ssl ciphers command displays the number of times each cipher was used on each segment of optimized flows.
Examples
Table 3-101 describes the fields shown in the show statistics crypto ssl ciphers command display.
|
|
|
|---|---|
Related Commands
show statistics datamover
To display statistics about the internal datamover component, use the show statistics datamover EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show statistics datamover command displays the statistics for the internal datamover component.
Examples
Table 3-102 describes the fields shown in the show statistics datamover command display.
show statistics dre
To display Data Redundancy Elimination (DRE) general statistics for a WAE, use the show statistics dre EXEC command,
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-103 describes the fields shown in the show statistics dre detail command display. This command shows the aggregated statistics for all connections.
The following example shows output from the show statistics dre command.
The following example shows sample output using the cwoDre parameter. The output provides two types of MIB DRE statistics—DRE cache statistics and DRE performance statistics:
Related Commands
show statistics encryption-services
To display encryption-services general statistics for a WAE, use the show statistics encryption-services EXEC command,
show statistics encryption-services {interposer-ssl (detail) | sake}
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-104 describes the fields shown in the show statistics interposer-ssl detail command.
Table 3-105 describes the fields shown in the show statistics sake detail command.
show statistics filtering
To display statistics about the incoming and outgoing TFO flows that the WAE currently has, use the show statistics filtering EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show statistics filtering command displays statistics about the TCP flows that the WAE is handling.
Examples
Table 3-107 describes the fields shown in the show statistics filtering command display.
Related Commands
show statistics flow
To display flow statistics for a WAAS device, use the show statistics flow EXEC command.
show statistics flow { filters | monitor type performance-monitor tcpstat-v1 } | monitor MonitorName | exporter ExporterName
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-108 describes the fields shown in the show statistics flow filters command display.
Table 3-109 describes the fields shown in the show statistics flow monitor command display.
Related Commands
show statistics generic-gre
To view the GRE tunnel statistics for each intercepting router, use the show statistics generic-gre EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the clear statistics generic-gre EXEC command to clear the generic GRE statistics.
Examples
Table 3-110 describes the fields shown in the show statistics generic-gre command display.
Related Commands
show statistics icmp
To display ICMP statistics for a WAAS device, use the show statistics icmp EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-111 describes the fields shown in the show statistics icmp command display.
Related Commands
show statistics icmp6
To display ICMP statistics for a WAAS device, use the show statistics icmp EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-111 describes the fields shown in the show statistics icmp6 command display.
Related Commands
show statistics ip
To display IP statistics for a WAAS device, use the show statistics ip EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-113 describes the fields shown in the show statistics ip command display.
Related Commands
show statistics ipv6
To display IPv6 statistics for a WAAS device, use the show statistics ipv6 EXEC command.
Defaults
Command Modes

Device Modes

Examples
Table 3-114 describes the fields shown in the show statistics ipv6 internal command display.
Related Commands
show statistics monitor appnav-controller traffic
To display traffic monitoring statistics for an AppNav Controller Interface Module, use the show statistics monitor appnav-controller traffic EXEC command.
show statistics monitor appnav-controller traffic
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following is sample output from the show statistics monitor appnav-controller traffic command:
Related Commands
clear statistics monitor appnav-controller traffic
show statistics netstat
To display Internet socket connection statistics for a WAAS device, use the show statistics netstat EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-115 describes the fields shown in the show statistics netstat command display.
show statistics pass-through
To display pass-through traffic statistics for a WAAS device, use the show statistics pass-through EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-116 describes the fields shown in the show statistics pass-through command display.
show statistics peer
To display peer Data Redundancy Elimination (DRE) statistics for a WAE, use the show statistics peer EXEC command.
show statistics peer dre [context context-value | peer-id peer-id | peer-ip ip-address | peer-no peer-no]
show statistics peer dre detail [context context-value | peer-id peer-id | peer-ip ip-address | peer-no peer-no ]]
Syntax Description
Displays peer statistics for the specified context (0–4294967295). |
|
(Optional) Specifies the MAC address of the peer (0–4294967295). |
|
Defaults
Command Modes

Device Modes

Examples
Table 3-117 describes the fields shown in the show statistics peer dre detail command display. This command shows the peer DRE device connection information.
Related Commands
show statistics policy-sub-class
To display the statistics for an AppNav class map, use the show statistics policy-sub-class EXEC command.
show statistics policy-sub-class type appnav [ level1-class classmap-name [ level2-class classmap-name ]]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show statistics policy-sub-class type appnav command displays statistics for all the class maps in the active AppNav policy map and any nested policy maps.
The show statistics policy-sub-class type appnav level1-class classmap-name command displays statistics for the specified class map in the top-level AppNav policy map, including statistics for all class maps in any nested policies. The nested policy class maps display statistics only from connections that match both the top-level and nested class maps.
The show statistics policy-sub-class type appnav level1-class classmap-name level2-class classmap-name command displays statistics for the specified class map in a nested AppNav policy map. The nested policy class map displays statistics only from connections that match both the top-level and nested class maps.
Examples
The following is sample output from the show statistics policy-sub-class type appnav command for a nested class map.
Related Commands
show statistics punt
To display punt statistics, use the show statistics punt EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following is sample output from the show statistics punt command.
Related Commands
show statistics radius
To display RADIUS authentication statistics for a WAAS device, use the show statistics radius EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-118 describes the fields shown in the show statistics radius command display.
|
|
|
|---|---|
Related Commands
show statistics service-insertion
To display statistics about the entities (WNs, WNGs, ANCs, ANCG, and a service context) defined in an AppNav Cluster configuration, use the show statistics service-insertion EXEC command.
show statistics service-insertion { appnav-controller ip_address | appnav-controller-group [ detail ] | data-path | service-context | service-node [ ip_address ] | service-node-group [ detail | name sng-name ]}
Syntax Description
Defaults
Command Modes

Device Modes

Related Commands
show statistics services
To display services statistics for a WAAS device, use the show statistics services EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-119 describes the fields shown in the show statistics services command display.
|
|
|
|---|---|
Service-related statistics for each port on the WAAS device. |
|
Related Commands
show statistics sessions
To display the dynamic match session statistics, use the show statistics sessions EXEC command.
show statistics sessions [ detail ] [ app-id { app-id | mapi | ms-ad-rep | ms-exch-nspi | ms-frs | ms-frs-api | ms-rfr | ms-sql | msn-messenger | netlogon }]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The show statistics sessions command displays session statistics for all the dynamic matched flows. You can optionally specify an application ID or traffic type identifier to see session statistics for only that traffic type.
The show statistics sessions details command displays detailed session statistics for all the dynamic matched flows. You can optionally specify an application ID or traffic type identifier to see detailed session statistics for only that traffic type.
Related Commands
show statistics snmp
To display SNMP statistics for a WAAS device, use the show statistics snmp EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-120 describes the fields shown in the show statistics snmp command display.
Related Commands
show statistics synq
To display the cumulative statistics for the SynQ module, use the show statistics synq EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show statistics synq command to display statistics for the SynQ module.
Examples
The following is sample output from the show statistics synq command:
Related Commands
show statistics system cpu
To display the detailed parameters of the cpu utilization, use the show statistics system cpu EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show statistics system cpu command to display statistics for the system cpu utilization.
Examples
The following is sample output from the show statistics system cpu command:
show statistics tacacs
To display TACACS+ authentication and authorization statistics for a WAAS device, use the show statistics tacacs EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-121 describes the fields shown in the show statistics tacacs command display.
|
|
|
|---|---|
Related Commands
show statistics tcp
To display TCP statistics for a WAAS device, use the show statistics tcp EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-122 describes the fields shown in the show statistics tcp command display.
Related Commands
show statistics tfo
To display Traffic Flow Optimization (TFO) statistics for a WAE, use the show statistics tfo EXEC command.
show statistics tfo [ connection | detail ]
show statistics tfo peer [peer-id peer-id | peer-ip peer-ip | peer-no peer-no ]
Syntax Description
Command Modes

Device Modes

Examples
Table 3-123 describes the fields shown in the show statistics tfo command. The Policy Engine Statistics and Auto-Discovery Statistics sections are displayed only when you use the detail option.
Related Commands
show statistics udp
To display User Datagram Protocol (UDP) statistics for a WAAS device, use the show statistics udp EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-124 describes the fields shown in the show statistics udp command display.
show statistics vn-service vpath
To display VPATH interception statistics for your vWAAS device, use the show statistics vn-service vpath EXEC command.
show statistics vn-service vpath
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show statistics vn-service vpath EXEC command to display statistics about VPATH interception on your vWAAS device.

Note![]() Only one type of interception can be enabled at a time on a vWAAS device (VPATH or WCCP).
Only one type of interception can be enabled at a time on a vWAAS device (VPATH or WCCP).
Examples
Table 3-125 describes the fields shown in the show statistics vn-service vpath command display.
Related Commands
show statistics wccp
To display WCCP statistics for a WAE, use the show statistics wccp EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The output of this command differs depending on the device mode of the WAE.
Examples
Table 3-126 describes the fields shown in the show statistics wccp gre command display for an application accelerator device.
Table 3-127 describes the fields shown in the show statistics wccp command display for an ANC device.
|
|
|
|---|---|
Related Commands
show statistics windows-domain
To display Windows domain server information for a WAAS device, use the show statistics windows-domain EXEC command.
show statistics windows-domain
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show statistics windows-domain EXEC command to view the Windows domain server statistics, then clear the counters for these statistics by entering the clear statistics windows-domain EXEC command.
Examples
Table 3-128 describes the fields shown in the show statistics windows-domain command display.
|
|
|
|---|---|
Related Commands
show synq list
To display the connections for the SynQ module, use the show synq list EXEC command.
show synq list [ | { begin regex [ regex ] | exclude regex [ regex ] | include regex [ regex ]}] [ | { begin regex [ regex ] | exclude regex [ regex ] | include regex [ regex ]}]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show synq list command to list connections that are currently being tracked in the SynQ module.
Examples
The following is sample output from the show synq list command:
Related Commands
show sysfs volumes
To display system file system (sysfs) information for a WAAS device, use the show sysfs volumes EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The system file system (sysfs) stores log files, including transaction logs, syslogs, and internal debugging logs. It also stores system image files and operating system files.
Examples
Table 3-129 describes the fields shown in the show sysfs volumes command display.
|
|
|
|---|---|
Related CommandsRelated Commands
show tacacs
To display TACACS+ authentication protocol configuration information for a WAAS device, use the show tacacs EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-130 describes the fields shown in the show tacacs command display.
Related Commands
show tcp
To display TCP configuration information for a WAAS device, use the show tcp EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-131 describes the fields shown in the show tcp command display. This command displays the settings configured with the tcp global configuration command.
Related Commands
show tech-support
To view information necessary for Cisco TAC to assist you, use the show tech-support EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show tech-support command to view system information necessary for Cisco TAC to assist you with a WAAS device. We recommend that you log the output to a disk file. (See the (config) logging console command.)
Examples
The following is sample output from the show tech-support command:

Note![]() Because the show tech-support command output can be long, excerpts are shown in this example.
Because the show tech-support command output can be long, excerpts are shown in this example.
Related Commands
show disks details
show processes memory
show cdp entry
show cdp neighbors
show alarms all
show statistics auto-discovery
show disks SMART-info
show disks SMART-info details
show disks failed-sectors
show telnet
To display Telnet services configuration for a WAAS device, use the show telnet EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following is sample output from the show telnet command. It shows whether or not Telnet is enabled on the WAAS device.
Related Commands
show tfo tcp
To display global Traffic Flow Optimization (TFO) TCP buffer information for a WAE, use the show tfo tcp EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Examples
The following is sample output from the show tfo tcp command. It displays TCP buffer information for the WAE.
Related Commands
show statistics auto-discovery
show transaction-logging
To display the transaction log configuration settings and a list of archived transaction log files for a WAE, use the show transaction-logging EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the show transaction-logging EXEC command to display information about the current configuration of transaction logging on a WAE. Transaction log file information is displayed for TFO transactions.

Note![]() For security reasons, passwords are never displayed in the output of the show transaction-logging EXEC command.
For security reasons, passwords are never displayed in the output of the show transaction-logging EXEC command.
Examples
The following is sample output from the show transaction-logging command. It lists information about the current configuration of transaction logging on a WAE.
Related Commands
show user
To display user identification number and username information for a particular user of a WAAS device, use the show user EXEC command.
show user {uid number | username name}
Syntax Description
Displays user information based on the identification number of the user (0–65535). |
|
Command Default
Command Modes

Device Modes

Examples
Table 3-132 describes the fields shown in the show user command display.
|
|
|
|---|---|
Login password. This field does not display the actual password. |
|
Related Commands
show users administrative
To display users with administrative privileges to the WAAS device, use the show users administrative EXEC command.
show users administrative [ history | locked-out | logged-in ]
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-133 describes the fields shown in the show users administrative history command display.
Table 3-134 describes the fields shown in the show users administrative logged-in command display.
Related Commands
show version
To display version information about the WAAS software that is running on the WAAS device, use the show version EXEC command.
show version [ last | pending ]
Syntax Description
(Optional) Displays the version information for the last saved image. |
|
(Optional) Displays the version information for the pending upgraded image. |
Defaults
Command Modes

Device Modes

Examples
Table 3-135 describes the fields shown in the show version command display.
show wccp
To display Web Cache Connection Protocol (WCCP) information for a WAE, use the show wccp EXEC command.
show wccp flows tcp-promiscuous [ summary ]
show wccp masks tcp-promiscuous
Syntax Description
Defaults
Command Modes

Device Modes

Examples
Table 3-136 describes the fields shown in the show wccp statistics command display.
The following is sample output from the show wccp clients command:
The following is sample output from the show wccp services command:
Services configured on this File Engine
TCP Promiscuous 61
TCP Promiscuous 62
The following is sample (partial) output from the show wccp services detail command:
The following is sample output from the show wccp routers command:
The following is sample output from the show wccp routers detail command:
The following is sample output from the show wccp status command:
The Configured State refers to the state configured. The Operational State refers to the actual system state, which could differ from the configured state. For example, if an ANC is converging due to a cluster change, the system disables WCCP until convergence is completed.
The following is sample output from the show wccp egress command:
Related Commands
show windows-domain
To display Windows domain configuration information for a WAAS device, use the show windows-domain EXEC command.
Syntax Description
Defaults

Device Modes

Examples
Table 3-137 describes the fields shown in the show windows-domain command display.
Related Commands
show windows-domain encrypted services
To display Windows domain encrypted services information for a WAAS device, use the show windows-domain encrypted services EXEC command.
show windows-domain encrypted services { identity [detail] | blacklist identity | status | keylist user }
Syntax Description
Defaults

Device Modes

Related Commands
shutdown
To shut down the WAAS device, use the shutdown EXEC command.
Syntax Description
(Optional) Turns off the power after closing all applications and operating system. |
Defaults
Command Modes

Device Modes

Usage Guidelines
A controlled shutdown refers to the process of properly shutting down a WAAS device without turning off the power on the device. With a controlled shutdown, all of the application activities and the operating system are properly stopped on a WAE, but the power remains on. Controlled shutdowns of a WAAS device can help you minimize the downtime when the WAAS device is being serviced.


Note![]() A WAAS device cannot be powered on again through the WAAS software after a software poweroff. You must press the power button once on a WAAS device to bring it back online.
A WAAS device cannot be powered on again through the WAAS software after a software poweroff. You must press the power button once on a WAAS device to bring it back online.
The shutdown EXEC command facilitates a proper shutdown for WAAS device, and is supported on all WAE hardware models. The shutdown poweroff command is also supported by all of the WAE hardware models as they support the ACPI.
The shutdown command closes all applications and stops all system activities, but keeps the power on. The fans continue to run and the power LED is on, indicating that the device is still powered on. The device console displays the following menu after the shutdown process is completed:
The shutdown poweroff command closes all applications and the operating system, stops all system activities, and turn off the power. The fans stop running and the power LED starts flashing, indicating that the device has been powered off.

Note![]() If you use the shutdown or shutdown poweroff commands, the device does not perform a file system check when you power on and boot the device the next time.
If you use the shutdown or shutdown poweroff commands, the device does not perform a file system check when you power on and boot the device the next time.
Table 3-138 describes the shutdown-only operation and the shutdown poweroff operation for a WAAS device.
You can enter the shutdown EXEC command from a console session or from a remote session (Telnet or SSH version 2) to shut down a WAAS device.
To shut down a WAAS device, enter the shutdown EXEC command as follows:
WAE# shutdown
When you are asked if you want to save the system configuration, enter yes.
When you are asked if you want to proceed with the shutdown, press Enter to proceed with the shutdown operation.
Device can not be powered on again through software after shutdown.
Proceed with shutdown?[confirm]
A message appears, reporting that all services are being shut down on this WAE.
Shutting down all services, will timeout in 15 minutes.
shutdown in progress..System halted.
After the system is shut down (the system has halted), a WAAS software shutdown shell displays the current state of the system (for example, “System has been shut down”) on the console. You are asked whether you want to perform a software power off (the Power down system by software option), or if you want to reload the system through the software.
================= SHUTDOWN SHELL =================
System has been shut down.
You can either
Power down system by pressing and holding power button
or
1. Reload system through software
2. Power down system through software
To power down the WAAS device, press and hold the power button on the WAAS device, or use one of the following methods to perform a shutdown poweroff:
================= SHUTDOWN SHELL =================
System has been shut down.
You can either
Power down system by pressing and holding power button
or
1. Reload system through software
2. Power down system through software
WAE# shutdown poweroffWhen you are asked if you want to save the system configuration, enter yes.
System configuration has been modified. Save?[yes]:yes
When you are asked to confirm your decision, press Enter.
Device can not be powered on again through software after poweroff.
Proceed with poweroff?[confirm]
Shutting down all services, will timeout in 15 minutes.
poweroff in progress..Power down.
Examples
The following example shows how to close all applications and stop all system activities using the shutdown command:
The following example shows how to close all applications, stop all system activities, and then turn off power to the WAAS device using the shutdown poweroff command:
ssh
To allow secure encrypted communications between an untrusted client machine and a WAAS device over an insecure network, use the ssh EXEC command.
Syntax Description
Options to use with the ssh EXEC command. Options include the following:
For more information about SSH, see RFC 4254. For more information on SSH and ciphers, see RFC 4253. |
|
Uses the designated management interface for the SSH operation. |
Defaults
By default, the Secure Shell (SSH) feature is disabled on a WAAS device.
Command Modes

Device Modes

Usage Guidelines
SSH consists of a server and a client program. Like Telnet, you can use the client program to remotely log in to a machine that is running the SSH server, but unlike Telnet, messages transported between the client and the server are encrypted. The functionality of SSH includes user authentication, message encryption, and message authentication. The SSH client accepts both IPv4 and IPv6 addresses.

Note![]() The Telnet daemon can still be used with the WAAS device. SSH does not replace Telnet.
The Telnet daemon can still be used with the WAAS device. SSH does not replace Telnet.
Examples
The following example shows how to log in to a WAAS device using the SSH client:
Related Commands
tcpdump
To dump network traffic, use the tcpdump EXEC command.
Syntax Description
(Optional) Dump options. For more information see the “Usage Guidelines” section. |
Defaults
Command Modes

Device Modes

Usage Guidelines
TCPdump is a utility that allows a user to intercept and capture packets passing through a network interface, making it useful for troubleshooting network applications.

Note![]() In WAAS version 5.0, TCPdump cannot capture data plane traffic on an AppNav Controller Interface Module interface; only control plane traffic is captured. Instead, use the packet-capture EXEC command to capture data plane traffic.
In WAAS version 5.0, TCPdump cannot capture data plane traffic on an AppNav Controller Interface Module interface; only control plane traffic is captured. Instead, use the packet-capture EXEC command to capture data plane traffic.
During normal network operation, only the packets which are addressed to a network interface are intercepted and passed on to the upper layers of the TCP/IP protocol layer stack. Packets which are not addressed to the interface are ignored. In Promiscuous mode, the packets which are not intended to be received by the interface are also intercepted and passed on to the higher levels of the protocol stack. TCPdump works by putting the network interface into promiscuous mode. TCPdump uses the free libpcap (packet capture library).
Use the -h option to view the options available, as shown in the following example:
You can use either linux interface port names (for example, eth0) or WAAS port names (for example, GigabitEthernet 1/0 port 80, or InlinePort 1/0 lan) to designate the interface from which you want to capture packets. You cannot specify an inlineGroup.
Examples
The following example shows how to start a network traffic dump to a file named tcpdump.txt :
Related Commands
telnet
To log in to a WAAS device using the Telnet client, use the telnet EXEC command.
telnet { hostname | ip-address } [ portnum ] [ management ]
Syntax Description
(Optional) Port number (1–65535). The default port number is 23. |
|
Uses the designated management interface for the Telnet operation. |
Defaults
Command Modes

Device Modes

Usage Guidelines
UNIX shell functions such as escape and the suspend command are not available in the Telnet client. Multiple Telnet sessions are also not supported. This Telnet client allows you to specify a destination port.
Examples
The following example shows how to log in to a WAAS device using the Telnet client in several ways:
Related Commands
terminal
To set the number of lines displayed in the console window, or to display the current console debug command output, use the terminal EXEC command.
terminal { length length | monitor [ disable ]}
Syntax Description
Sets the length of the display on the terminal (0–512). Setting the length to 0 means there is no pausing. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
When 0 is entered as the length parameter, the output to the screen does not pause. For all nonzero values of length, the -More- prompt is displayed when the number of output lines matches the specified length number. The -More- prompt is considered a line of output. To view the next screen, press the Spacebar. To view one line at a time, press the Enter key.
The terminal monitor command allows a Telnet session to display the output of the debug commands that appear on the console. Monitoring continues until the Telnet session is terminated.
For proper display of the setup command, leave the terminal length set to the default value of 24 lines.
Examples
The following example shows how to set the number of lines to display to 20:
The following example shows how to configure the terminal for no pausing:
Related Commands
test
To perform authentication and diagnostic tests for the Radius/Tacacs/Windows users, use the test EXEC command.
test aaa {radius | tacacs | windows} username password
test self-diagnostic [ system | basic | connectivity | interfaces | application-security | tfo | wccp | inline ] | all
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
If you use the test self-diagnostic command with the all option, all applicable tests are performed. You can specify one or more test options to perform just those tests.
The last diagnostic test report is stored on the device in the following file: /local1/diagnostic_report.txt.
Examples
The following example shows how to perform the basic, connectivity, interfaces, and WCCP tests:
Table 3-139 describes the error messages that can be returned by the test self-diagnostics command.
tethereal
To analyze network traffic from the command line, use the tethereal EXEC command.
Syntax Description
(Optional) Options. For more information see the “Usage Guidelines” and “Examples” sections. |
Defaults
Command Modes

Device Modes

Usage Guidelines
Tethereal is the command-line version of the network traffic analyzer tool Ethereal. Like TCPdump, it also uses the packet capture library (libpcap). Aside from network traffic analysis, Tethereal also provides facilities for decoding packets.

Note![]() In WAAS version 5.0, Tethereal cannot capture data plane traffic on an AppNav Controller Interface Module interface; only control plane traffic is captured. Instead, use the packet-capture EXEC command to capture data plane traffic.
In WAAS version 5.0, Tethereal cannot capture data plane traffic on an AppNav Controller Interface Module interface; only control plane traffic is captured. Instead, use the packet-capture EXEC command to capture data plane traffic.
When using the -a option to print heavy traffic to the screen, it can take significantly longer than the autostop duration to display the information on the screen. Wait for the command to finish. Displaying output to the console can take significantly longer than through telnet or SSH, therefore console display is not recommended.
When using the -f option with the host or not host filter expression, the wrong traffic may be captured with WCCP GRE encapsulated or VLAN traffic. With WCCP GRE traffic, tethereal sees only the outermost IP address, not the original IP address inside the encapsulated packets. Add the proto 47 keyword into the -f filter expression to capture the correct traffic (protocol 47 is GRE traffic). Additionally, for VLAN traffic, add the vlan keyword into the -f filter expression so that VLAN traffic is parsed correctly.
When using the -a filesize option together with the -R option, tethereal may stop unexpectedly and print the message "Memory limit is reached" before reaching the specified autostop file size. In this case, the maximum memory limit for the command was reached before the autostop file size limit.
You can use either Linux interface port names (for example, eth0) or WAAS port names (for example, GigabitEthernet 1/0 port 80, or InlinePort 1/0 lan) to designate the interface from which you want to capture packets. You cannot specify an inlineGroup.
Examples
The following example shows how to display the options available with the WAAS tethereal command:
Related Commands
top
To view the current top CPU activities, use the top EXEC command.
top -hv | -cisS -d delay -n iterations [-u user | -U user ] -p pid [, pid...]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The top command is a system-defined alias for the Linux top command, which displays and updates information about the top CPU processes. It provides a real-time view of the processor activity. It lists the most CPU-intensive tasks on the system, and provides an interactive interface for manipulating processes. It can sort the tasks by CPU usage, memory usage, and runtime.
The command runs in an interactive environment and you can interact with the output by pressing various keys. Press h or ? to display the following help for interactive commands:
Examples
The following example shows how to display the options available with the WAAS top command:

Note![]() The -b option is not supported.
The -b option is not supported.
The following example shows an example of the interactive command output:
Related Commands
traceroute
To trace the route between a WAAS device to a remote host, use the traceroute EXEC command.
traceroute [ management ] { hostname | ip-address } [tcp-syn]
Syntax Description
(Optional) Uses the designated management interface for the traceroute. |
|
(Optional) Sends TCP-SYN packets for trace routing instead of UDP |
Defaults
Command Modes

Device Modes

Usage Guidelines
Traceroute is a widely available utility on most operating systems. Much like ping, it is a valuable tool for determining connectivity in a network. Ping allows the user to find out if there is a connection between two end systems. Traceroute does this as well, but also lists the intermediate routers between the two systems. Users can therefore see the possible routes packets can take from one system to another. Use traceroute to find the route to a remote host, when either the hostname or the IP address is known.
Examples
The following example shows how to trace the route between the WAAS device and a device with an IP address of 10.0.0.0
Related Commands
traceroute6
To trace the route between a WAAS device to a remote host with an IPv6 address, use the traceroute6 EXEC command.
traceroute6 [ management ] { hostname | ip-address }
Syntax Description
(Optional) Uses the designated management interface for the traceroute. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
Traceroute is a widely available utility on most operating systems. Much like ping, it is a valuable tool for determining connectivity in a network. Ping allows the user to find out if there is a connection between two end systems. Traceroute does this as well, but also lists the intermediate routers between the two systems. Users can therefore see the possible routes packets can take from one system to another. Use traceroute6 to find the route to a remote host, when either the hostname or the IP address is known.
If a device’s management interface is used to trace the route between two end systems using traceroute6 and the management interface goes down, the communication will still succeed if the end device’s address is reachable from any other interface.
Examples
The following example shows how to trace the route between the WAAS device and a device with an IP address of 2013:1:1:2::4:
Related Commands
transaction-log
To force the exporting or the archiving of the transaction log, use the transaction-log EXEC command.
transaction-log force { archive | export | flow }
Syntax Description
Forces the archiving or exporting of the Traffic Flow Optimization (TFO) transaction log file. |
Defaults
Command Modes

Device Modes

Examples
The following example shows how to force the archiving of the TFO transaction log file on the WAE:
Related Commands
type
To display a file, use the type EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the type command to display the contents of a file within any file directory on a WAAS device. The type command may be used to monitor features such as transaction logging or system logging (syslog).
Examples
The following example shows how to display the contents of the syslog.txt file:
Related Commands
type-tail
To view a specified number of lines of the end of a log file, to view the end of the file continuously as new lines are added to the file, to start at a particular line in the file, or to include or exclude specific lines in the file, use the type-tail EXEC command.
type-tail filename [ line | follow | | { begin LINE | exclude LINE | include LINE }]
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
The type-tail command allows you to monitor a log file by letting you view the end of the file. You can specify the number of lines at the end of the file that you want to view, or you can follow the last line of the file as it continues to log new information. To stop the last line from continuously scrolling as with the follow option, use the key sequence Ctrl-C.
You can further indicate the type of information to display using the output modifiers. These allow you to include or exclude specific lines or to indicate where to begin displaying the file.
Examples
The following example shows how to looks for a list of log files in the /local1 directory and then displays the last ten lines of the syslog.txt file. In this example, the number of lines to display is not specified, so the default of ten lines is used:
actona
core_dir
crash
dbupgrade.log
downgrade
errorlog
logs
lost+found
sa
service_logs
spool
syslog.txt
syslog.txt.1
syslog.txt.2
syslog.txt.3
syslog.txt.4
var
wdd.sh.signed
equest throughput stats(error 4)
Apr 17 00:21:09 edge-wae-11 java: %CE-CMS-4-700001: ds_getStruct got err
r : 4 for key stat/cache/ftp connection 5
Apr 17 00:21:09 edge-wae-11 java: %CE-CMS-4-700001: ds_getStruct: unable
to get `stat/cache/ftp' from dataserver
Apr 17 00:21:09 edge-wae-11 java: %CE-CMS-4-700001: unable to get ftp-ov
r-http request throughput stats(error 4)
Apr 17 00:21:09 edge-wae-11 java: %CE-CMS-4-700001: setValues getMethod
all...
Apr 17 00:21:09 edge-wae-11 java: %CE-CMS-4-700001: setValues found...
Apr 17 00:21:48 edge-wae-11 java: %CE-CMS-4-700001: ds_getStruct got err
r : 4 for key stat/cache/http/perf/throughput/requests/sum connection 5
Apr 17 00:21:48 edge-wae-11java: %CE-CMS-4-700001: ds_getStruct: unable
to get `stat/cache/http/perf/throughput/requests/sum' from dataserver
Apr 17 00:21:48 edge-wae-11 java: %CE-CMS-4-700001: unable to get http r
quest throughput stats(error 4)
Apr 17 00:23:20 edge-wae-11 java: %CE-TBD-3-100000: WCCP_COND_ACCEPT: TU
LE DELETE conditional accept tuple {Source IP [port] = 0.0.0.0 [0] Destinatio
IP [port] = 32.60.43.2 [53775] }returned error: -1 errno 9
The following example shows how to follow the syslog.txt file as it grows:
vm
To initialize the virtual machine after the VMware cloning operation, or to configure the host clock sync setting, use the vm EXEC command.
vm {{clock-sync {disable | enable | status} | init}
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the vm for vWAAS virtual machine operations. To speed up vWAAS deployments, you can create a clone of the vWAAS virtual machine. However, since the clone is an exact copy of the original vWAAS VM, you must use the vm init command to remove the certificate hash and the device registration information before the new vWAAS VM will register with the Central Manager.
You must reload the device after running vm init.
Use the vm clock-sync command to manually change the host clock sync setting without configuring NTP.
Examples
The following example shows how to initialize the virtual machine after the VMware cloning operation:
Related Commands
waas-tcptrace
To list all the WAAS devices in the path to a destination host, use the waas-tcptrace EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use waas-tcptrace to list all the WAAS devices in the path between the device on which this command is run and the specified destination host. The path is traversed in both directions.
This command returns the configured application accelerators, system policy, and effective system policy for each WAAS device found in the path, as well as the overall system policy for the connection.
You can use this command to find the overall policy applied to the connection and to find asymmetric paths.
Examples
The following example shows how to trace the route between the WAAS device and a destination host with an IP address of 2.75.227.50 on port 80:
Related Commands
whoami
To display the username of the current user, use the whoami EXEC command.
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the whoami command to display the username of the current user.
Examples
The following example shows how to display your username:
Related Commands
windows-domain
To join or leave a Windows domain or access the Windows domain utilities on a WAAS device, use the windows-domain EXEC command.
windows-domain join domain-name domain [organization-unit org_unit] user username [debug]
windows-domain leave [user username]
windows-domain diagnostics
{ domain-controller {list | status | time [domain-name domain_name]} |
encryption-service {get-key fqdn domain_name} | getent |
group {gid gid_no | groupname groupname | username username} | machine-account-info | user [sid sid_name | uid user_no | username username] | verify join }
Syntax Description
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the windows-domain command to join or leave a Windows domain or activate the selected Windows domain diagnostic utility.
When you use the windows-domain join command, it automatically discovers the windows domain configuration parameters and prompts you to approve the changes. You can respond with yes to approve the changes, quit to do nothing and exit the command, or no to enter interactive edit mode where you can edit any of the parameters before submitting the change.
If you do not specify the password as part of the command, you are prompted for the password and it is not shown on the console when you enter it.

Note![]() When you use the command windows-domain diagnostics encryption-service get-key user username domain-name domain_name to configure WAAS as an identity server, you must execute this command two times to ensure that the key retrieval process is complete.
When you use the command windows-domain diagnostics encryption-service get-key user username domain-name domain_name to configure WAAS as an identity server, you must execute this command two times to ensure that the key retrieval process is complete.
As shown below, the first time you execute this command an in-progress message is displayed, and the second time a completion message is displayed.WAE# windows-domain diagnostics encryption-service get-key user username domain-name domain_name
WAE# Key retrieval in progress.
WAE# windows-domain diagnostics encryption-service get-key user username domain-name domain_name
WAE# The key for the user username is now in the cache.
Examples
The following example shows how to join a Windows domain and includes the interactive output:
The following example shows how to leave a Windows domain:

Note![]() In version 5.1.1, although the windows-domain leave operation disables the machine account on Active Directory (AD), it does not delete it.
In version 5.1.1, although the windows-domain leave operation disables the machine account on Active Directory (AD), it does not delete it.
The following example shows how to display the options available for the Get Entity utility:
Related Commands
write
To save startup configurations on a WAAS device, use the write EXEC command.
write [ erase | memory | mib-data | terminal ]
Syntax Description
(Optional) Writes the configuration to NVRAM. This is the default location for saving startup information. |
|
Defaults
Command Modes

Device Modes

Usage Guidelines
Use the write command to either save running configurations to NVRAM or to erase memory configurations. Following a write erase command, no configuration is held in memory, and a prompt for configuration specifics occurs after you reboot the WAAS device.
Use the write terminal command to display the current running configuration in the terminal session window. The equivalent command is show running-config.
Examples
The following example shows how to save the current startup configuration to memory:
Related Commands
zzdebugshell
To enter debug shell mode, use the zzdebugshell EXEC command. To exit from the shell environment, use the exit command.

Syntax Description
Defaults
Command Modes
Usage Guidelines
As highlighted in the above Caution note, the zzdebugshell command can only be used by Cisco support personnel during a live support session. The zzdebugshell command requires both administrative WAAS user credentials and a special authentication token from Cisco TAC personnel. For more information, see the “$paratext>” section.
 Feedback
Feedback