
Use Case: You want to establish a site-to-site VPN tunnel between the security appliance and a remote UC500 to provide voice and data services to phones at a remote site.

Solution: When you use Cisco Configuration Assistant (CCA) Multisite Manager (MSM) to configure the site-to-site VPN settings on the UC500, CCA MSM uses the default IKE policy and transform set. In this case, the security appliance must create an IPsec VPN policy as follows to establish the site-to-site VPN tunnel with the UC500.
Use Case: The UC500 device is behind the security appliance. You want to establish a site-to-site VPN tunnel between two security appliances to provide voice and data services to phones at a remote site.
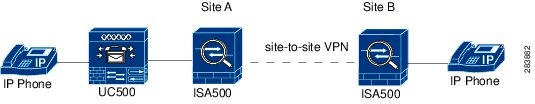
Solution: When you configure the site-to-site VPN on the security appliances, make sure that the local network on the security appliance at Site A is set as “Any” and the remote network on the security appliance at Site B is set as “Any”.
Because the security appliance provides the firewall, Network Address Translation (NAT), and SIP Application Level Gateway (SIP ALG) for your network, you must disable those functions on the UC500. For instructions, refer to the documentation or online Help for the Cisco Configuration Assistant (CCA).
To allow the hosts in non-native subnets of the security appliance to access the Internet over the VPN tunnels, you must manually create advanced NAT rules on your security appliance. Go to the Firewall > NAT > Advanced NAT page to do this. For example, you can create an advanced NAT rule as follows to allow the hosts in the data LAN (10.25.1.0/24) behind the UC500 to access the Internet: