Table Of Contents
Overview of the VoIP Wireless Network
Understanding the Wireless LAN
Understanding WLAN Standards and Technologies
802.11 Standards for WLAN Communications
802.11 Data Rates, Tx Power, Ranges, and Decibel Tolerances
Wireless Modulation Technologies
AP, Channel, and Domain Relationships
Components of the VoIP Wireless Network
Networking Protocols Used with Cisco Unified Wireless IP Phones
Interacting with Cisco Unified Wireless APs
Voice QoS in a Wireless Network
Interacting with Cisco Unified Communications Manager
Phone Configuration Files and Profile Files
Interacting with the Dynamic Host Configuration Protocol Server
Security for Voice Communications in WLANs
Choosing AP Authentication and Encryption Methods
Performing a Site Survey Verification
Using the Neighbor List Utility
Overview of the VoIP Wireless Network
This chapter provides an overview of the interaction between the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G and other key components of a VoIP network in a wireless local area network (WLAN) environment. It contains the following sections:
•
Understanding the Wireless LAN
•
Understanding WLAN Standards and Technologies
•
Components of the VoIP Wireless Network
•
Security for Voice Communications in WLANs
For detailed information, see the Enterprise Mobility 4.1 Design Guide: http://www.cisco.com/en/US/docs/solutions/Enterprise/Mobility/emob41dg/eMob4.1.pdf.
Understanding the Wireless LAN
With the introduction of wireless communication, wireless IP phones can provide voice communication within the corporate WLAN. The Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G depends upon and interacts with wireless access points (APs) and key Cisco IP telephony components, including Cisco Unified Communications Manager Administration, to provide wireless voice communication.
In a traditional LAN, IP phones and computers use cables to transmit messages and data packets. Cisco Unified WLAN delivers security, scalability, reliability, ease of deployment, and management similar to wired LANs. It includes RF capabilities that enable real-time access to core business applications and provides proven enterprise-class secure connectivity. The WLAN is an integrated end-to-end solution that uses wireless IP phones and APs, network infrastructure, network management, and mobility services.
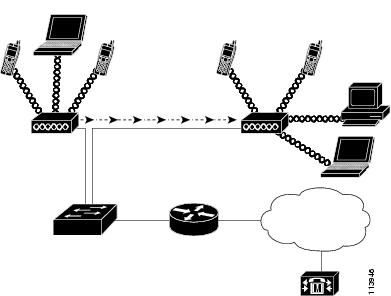
Figure 2-1 shows a typical WLAN topology that enables the wireless transmission of voice for wireless IP telephony.
Figure 2-1 WLAN with Wireless IP Phones
When a wireless IP phone powers on, it searches for and becomes associated with an AP. As users move from one location to another, the wireless IP phone roams out-of-range of one AP into the range of another AP. The wireless IP phone builds and maintains a list of eligible APs and reconnects to an AP in that list. See "Associating to APs" section for more information.
The AP uses its connection to the wired network to transmit data and voice packets to and from the switches and routers. Voice signaling transmits to the Cisco Unified Communications Manager server for call processing and routing. APs are critical components in a WLAN because they provide the wireless links or "hot spots" to the network.
Each AP has a wired connection to an Ethernet switch, such as a Cisco Catalyst 3750 Series, that is configured on a LAN. The switch provides access to gateways and the Cisco Unified Communications Manager server to support wireless IP telephony.
The following documents have more information on WLANs, APs (including supported models), antennas, and wireless IP telephony:
•
Cisco Unified Wireless IP Phone 7925 and 7926 Series Deployment Guide
•
Cisco Cius WLAN Deployment Guide
•
Cisco WLAN Deployment Guide
Understanding WLAN Standards and Technologies
This section describes the following concepts:
•
802.11 Standards for WLAN Communications
•
802.11 Data Rates, Tx Power, Ranges, and Decibel Tolerances
•
Wireless Modulation Technologies
•
AP, Channel, and Domain Relationships
802.11 Standards for WLAN Communications
Wireless LANs must follow the Institute of Electrical and Electronics Engineers (IEEE) 802.11 standards that define the protocols that govern all Ethernet-based wireless traffic. The Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G supports the following standards:
•
802.11a—Uses the 5 GHz band that provides more channels and improved data rates by using Orthogonal Frequency Division Multiplexing (OFDM) technology. Dynamic Frequency Selection (DFS) and Transmit Power Control (TPC) supports this standard.
•
802.11b—Specifies the radio frequency (RF) of 2.4 GHz for both transmitting and receiving data at lower data rates (1, 2, 5.5, 11 Mbps). Commonly called the Wi-Fi standard.
•
802.11d—Enables APs to communicate available radio channels and acceptable power levels.The Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G always give precedence to 802.11d to determine which channels and powers to use. If the information is unavailable, then the phone reverts to the locally configured regulatory domain.
•
802.11e—Supports Quality of Service (QoS).
•
802.11g—Uses the same unlicensed 2.4 GHz band as 802.11b, but extends the data rates to provide greater performance by using OFDM technology. OFDM is a physical-layer encoding technology for transmitting signals using RF.
•
802.11h—Supports the 5 GHz spectrum and transmit power management.
•
802.11i—Specifies security standards.
Radio Frequency Ranges
WLAN communications use the following RF ranges:
•
2.4 GHz—Does not require licensing. To reduce interference within this bandwidth, WLANs transmit on non-overlapping channels, which are typically limited to three channels, although Japan uses four channels.
Many devices operate in the 2.4 GHz bandwidth including cordless phones and microwave ovens and these devices can interfere with wireless communications. Interference does not destroy the signal, but can reduce the transmission speed from 11 Mbps to 1 Mbps. RF interference can affect voice quality over the wireless network.
•
5 GHz—Divided into several sections called Unlicensed National Information Infrastructure (UNII) bands and has four channels each. The channels are spaced at 20 MHz to provide non-overlapping channels and more channels than 802.11b or 802.11g.
For more information, see the Cisco Unified Wireless IP Phone 7925 and 7926 Series Deployment Guide.
The following tables show the frequency band ranges and operating channels by regulatory domain for each of the phones.
Note
802.11j (channels 34, 38, 42, 46) and channel 165 are not supported
802.11 Data Rates, Tx Power, Ranges, and Decibel Tolerances
Table 2-4 lists the Tx power capacities, data rates, ranges in feet and meters, and decibels tolerated by the receiver for the 801.11 standard.
Table 2-4 Tx Power, Data Rates, Ranges, and Decibels by Standard
16 dBm
6 Mbps
604 ft (184 m)
-91 dBm
9 Mbps
604 ft (184 m)
-90 dBm
12 Mbps
551 ft (168 m)
-88 dBm
18 Mbps
545 ft (166 m)
-86 dBm
24 Mbps
512 ft (156 m)
-82 dBm
36 Mbps
420 ft (128 m)
-80 dBm
48 Mbps
322 ft (98 m)
-77 dBm
54 Mbps
289 ft (88 m)
-75 dBm
16 dBm
6 Mbps
709 ft (216 m)
-91 dBm
9 Mbps
650 ft (198 m)
-90 dBm
12 Mbps
623 ft (190 m)
-87 dBm
18 Mbps
623 ft (190 m)
-86 dBm
24 Mbps
623 ft (190 m)
-82 dBm
36 Mbps
495 ft (151 m)
-80 dBm
48 Mbps
413 ft (126 m)
-77 dBm
54 Mbps
394 ft (120 m)
-76 dBm
17 dBm
1 Mbps
1,010 ft (308 m)
-96 dBm
2 Mbps
951 ft (290 m)
-85 dBm
5.5 Mbps
919 ft (280 m)
-90 dBm
11 Mbps
902 ft (275 m)
-87 dBm
1 Adjusts dynamically when associating with an AP if the AP client setting is enabled.
2 Advertised rates by the APs are used. If the Restricted Data Rates functionality is enabled in the Cisco Unified Communications Manager Administration phone configuration, then the Traffic Stream Rate Set IE (CCX V4) is used.
Wireless Modulation Technologies
Wireless communications uses the following modulation technologies for signaling:
•
Direct-Sequence Spread Spectrum (DSSS)—Prevents interference by spreading the signal over the frequency range or bandwidth. DSSS technology multiplexes chunks of data over several frequencies so that multiple devices can communicate without interference. Each device has a special code that identifies its data packets and all others are ignored. Cisco wireless 802.11b/g products use DSSS technology to support multiple devices on the WLAN.
•
Orthogonal Frequency Division Multiplexing (OFDM)—Transmits signals by using RF. OFDM is a physical-layer encoding technology that breaks one high-speed data carrier into several lower-speed carriers to transmit in parallel across the RF spectrum. OFDM, when used with 802.11g and 802.11a, can support data rates as high as 54 Mbps.
Table 2-5 provides a comparison of data rates, number of channels, and modulation technologies by standard.
AP, Channel, and Domain Relationships
APs transmit and receive RF signals over channels within the 2.4 GHz or 5 GHz frequency band. To provide a stable wireless environment and reduce channel interference, you must specify non-overlapping channels for each AP. The recommended 2.4 GHz channels to be used are 1, 6, and 11.
Regulatory domains determine the number of channels that wireless communications can use within the frequency band. Table 2-1, Table 2-2, and Table 2-3 list the frequency ranges, operating channels, and product numbers for the regulatory domains. The Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G uses the fourth domain for all other regions in the world. Wireless LANs in the rest of the world use 802.11d to identify band ranges and channels.
Note
In a non-controller-based wireless network, we recommend that you statically configure channels for each AP. If your wireless network uses a controller, use the Auto-RF feature with minimal voice disruption. Some channels may need to be statically configured if there is an intermittent interferer, to avoid disruptions in that area.
The AP coverage area depends on the type of antenna and transmission power. The AP coverage range is from 500 to 1000 feet with effective isotropic radiated power (EIRP) output. To provide effective coverage, APs need a range overlap of approximately 20 percent to allow uninterrupted connections as phone users roam from one AP to another.
Wireless networks use a service set identifier (SSID). The SSID differentiates one WLAN from another, so all APs and all devices attempting to connect to a specific WLAN must use the same SSID. The SSID groups user devices and associates the group with the APs.
For more information about wireless network components and design, see the Overview: Cisco Unified Wireless Network at http://www.cisco.com/en/US/solutions/ns175/networking_solutions_products_genericcontent0900aecd80529a5f.html.
WLANs and Roaming
Wireless IP phones provide communication mobility to users within the WLAN environment. Unlike cellular phones that have a broad coverage, the coverage area for the wireless IP phone is smaller; therefore, phone users frequently roam from one AP to another. To understand some of the limitations of roaming with wireless IP phones, these examples provide information about the WLAN environment.
•
Pre-call Roaming—A wireless IP phone user powers on the phone in the office, and the phone associates with the nearby AP. The user leaves the building, moves to another building, and then places a call. The phone associates with a different AP in order to place the call from the new location. If the associated AP is within the same Layer 2 VLAN, the IP address remains the same for the phone. But, if the roaming phone crosses a Layer 3 boundary with DHCP enabled and Layer 3 mobility is not enabled, the phone recognizes that it is no longer in the same subnet. The phone must request a new IP address before it can connect to the network and place the call. If Layer 3 mobility is enabled, the phone does not need to reconnect to the network.
Note
If a user leaves the WLAN coverage area and then comes back into the same WLAN area, the phone must reconnect to the network. Pressing a key on the phone causes the phone to perform immediate scans to find and connect to the network.
•
Mid-call Roaming—A wireless IP phone user is actively engaged in a call and moves from one building to another. The roaming event occurs when the phone moves into the range of a different AP, and then the phone authenticates and associates with the new AP. The previous AP hands the call over to the new AP while maintaining continuous audio connection without user intervention. As long as the APs are in the same Layer 2 subnet, the wireless IP phone keeps the same IP address and the call continues. As a wireless IP phone roams between APs, it must re-authenticate with each new AP. See "Authentication Methods" section for information about authentication.
If roaming across Layer 2 boundaries, then Layer 3 mobility must be enabled to have seamless roaming, and to preserve an existing call.
If the wireless IP phone user moves from an AP that covers IP Subnet A to an AP that covers IP Subnet B without Layer 3 mobility enabled, the phone no longer has an IP address or gateway that is valid within the new subnet and the call can disconnect.
•
Layer 3 Roaming—With the release of the Cisco Catalyst 6500 Series Wireless LAN Services Module (WLSM), the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G supports Layer 3 roaming for autonomous mode APs. This roaming is specific to autonomous APs and is not valid for Cisco Unified Access Point and WLC deployments. For details about the Cisco WLSM, see the product documentation available at:
http://www.cisco.com/univercd/cc/td/doc/product/lan/cat6000/cfgnotes/wlsm_1_1/index.htm
Layer 3 roaming with Cisco Unified Access Points is accomplished by controllers that use dynamic interface tunneling and requires Layer 3 mobility to be enabled. Clients that roam across controllers and VLANS can keep their IP address when using the same SSID.
•
Fast and Secure Roaming—Cisco Centralized Key Management (CCKM) enables authenticated client devices to roam securely from one AP to another without any perceptible delay during reassociation. With the support of the CCKM protocol, the wireless IP phone negotiates the handoff from one AP to another easily. During the roaming process, the phone scans for the nearby APs, determines which AP can provide the best service, and then reassociates with the new AP. When implementing stronger authentication methods, such as WPA2 and EAP, the number of information exchanges increases and causes more delay during roaming. To avoid delays, use CCKM.
CCKM, a centralized key management protocol, provides a cache of session credentials on the wireless domain server (WDS). As the phone roams from one AP to the next, CCKM compresses the number of message exchanges during roaming by providing a master key stored on the WDS for the AP to use. The reassociation exchange is reduced to two messages, thereby reducing the off-network or audio gap time.
For details about CCKM, see the "Cisco Fast Secure Roaming Application Note" at:
http://www.cisco.com/en/US/products/hw/wireless/ps4570/prod_technical_reference09186a00801c5223.html
Note
In dual band WLANs, it is possible to roam between 2.4 GHz bands (802.11b/g) and 5 GHz bands (802.11a). The phone moves out of range of one AP using one band and into the range of another that has the same SSID but is using a different band.
Related Topics
•
Voice QoS in a Wireless Network
Bluetooth Wireless Technology
Bluetooth enables low-bandwidth wireless connections within a range of 30 feet (10 meters). The best performance is in the 3-to-6-foot (1- to 2-meter) range. Bluetooth wireless technology operates in the 2.4 GHz band, which is the same as the 802.11b/g band. There can be a potential for interference issues, We recommend that you:
•
Use 802.11a, which operates in the 5 GHz band
•
Reduce the proximity to other 802.11b/g devices, Bluetooth devices, microwave ovens, and large metal objects
Components of the VoIP Wireless Network
The wireless IP phone must interact with several network components in the WLAN to successfully place and receive calls. The following topics describe network components:
•
Networking Protocols Used with Cisco Unified Wireless IP Phones
•
Interacting with Cisco Unified Wireless APs
•
Voice QoS in a Wireless Network
•
Interacting with Cisco Unified Communications Manager
•
Interacting with the Dynamic Host Configuration Protocol Server
For more information, see the following documents:
•
Cisco Unified Wireless IP Phone 7925 and 7926 Series Deployment Guide
•
Cisco WLAN Deployment Guide
Networking Protocols Used with Cisco Unified Wireless IP Phones
Cisco Unified IP Phones support several networking protocols for voice communication. Table 2-6 describes the networking protocols that the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G supports.
Related Topics
•
Understanding the Phone Startup Process, page 3-17
•
Components of the VoIP Wireless Network
•
Configuring DHCP Settings, page 5-5
Interacting with Cisco Unified Wireless APs
Wireless IP phones use the same APs as wireless data devices. However, voice traffic over a WLAN requires different equipment configurations and layouts than a WLAN that is used exclusively for data traffic. Data transmission can tolerate a higher level of RF noise, packet loss, and channel contention than voice transmission. Packet loss during voice transmission can cause choppy or broken audio and make the phone call inaudible.
Wireless IP Phones users are mobile and often roam across a campus or between floors in a building while connected to a call. In contrast, data users remain in one place or occasionally move to another location. The ability to roam while maintaining a call is one of the advantages of wireless voice so RF coverage needs to include stairwells, elevators, quiet corners outside conference rooms, passage ways and so on.
To ensure good voice quality and optimal RF signal coverage, you must perform a site survey. The site survey determines the AP platform and antenna type, AP placement, channel assignments and transmit power levels that are required for the deployment.
After you deploy and use wireless voice, you should continue to perform postinstallation site surveys. When you add a group of new users, install more equipment, or stack large amounts of inventory, you are changing the wireless environment. A postinstallation survey verifies that the AP coverage remains adequate for optimal voice communications. See "Site Survey Verification" section for more information.
Associating to APs
At startup, the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G scans for APs with SSIDs and encryption types that it recognizes. The phone builds and maintains a list of eligible APs and uses the following variables to determine the best AP.
•
Received Signal Strength Indicator (RSSI)—Signal strength of available APs within the RF coverage area. The phone attempts to associate with the AP with the highest RSSI value.
•
Traffic Specification (TSpec)—Calculation of call limits and WLAN load balancing. The TSpec value of each voice stream allows the system to allocate bandwidth to voice devices on a first-come, first-served basis. For more information, see "Voice QoS in a Wireless Network" section.
The wireless IP phone associates with the AP with the highest RSSI and lowest channel usage values (QBSS) that have matching SSID and encryption types. To ensure that voice traffic is handled properly, you must configure the correct QoS in the AP. For configuration information, see Cisco Unified Wireless IP Phone 7925 and 7926 Series Deployment Guide.
Related Topics
•
Security for Voice Communications in WLANs
Voice QoS in a Wireless Network
Voice traffic on the Wireless LAN, like data traffic, is susceptible to delay, jitter, and packet loss. These issues do not impact the data end user, but have serious implications for a voice call. To ensure that voice traffic receives timely and reliable treatment with low delay and low jitter, you must use Quality of Service (QoS), and use separate virtual LANs (VLANs) for voice and data. By isolating the voice traffic onto a separate VLAN, you can use QoS to provide priority treatment for voice packets when traveling across the network. Also, use a separate VLAN for data traffic, not the default native VLAN that is typically used for all network devices.
You typically need at least three VLANs on the network switches and the APs that support voice connections on the WLAN. These VLANs are:
•
Voice VLAN—Voice traffic to and from the wireless IP phone
•
Data VLAN—Data traffic to and from the wireless PC
•
Native VLAN—Data traffic to and from other wireless infrastructure devices
Assign an SSID to the voice VLAN and a different SSID to the data VLAN. If you configure a separate management VLAN in the WLAN, do not associate an SSID with the management VLAN.
By separating the phones into a voice VLAN and marking voice packets with higher QoS, you can ensure that voice traffic gets priority treatment over data traffic, resulting in lower packet delay and fewer lost packets.
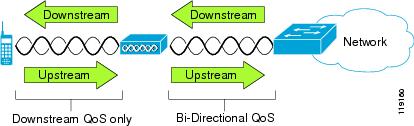
Unlike wired networks with dedicated bandwidths, wireless LANs consider traffic direction when implementing QoS. Traffic is classified as upstream or downstream from the point of view of the AP as shown in Figure 2-2.
Figure 2-2 Voice Traffic in a Wireless Network
Beginning with Cisco IOS release 12.2(11)JA, Cisco Aironet APs support the contention-based channel access mechanism called Enhanced Distributed Coordination Function (EDCF). The EDCF-type of QoS has up to eight queues for downstream (toward the 802.11b/g clients) QoS. You can allocate the queues based on these options:
•
Differentiated Services Code Point (DSCP) settings for the packets
•
Layer 2 or Layer 3 access lists
•
VLANs for specific traffic
Different traffic types are sent to different priority queues. The following are the queues:
•
Best Effort (BE) = 0, 3
•
Background (BK) = 1, 2
•
Video (VI) = 4, 5
•
Video (VO) = 6. 7
Call Control (SCCP) is sent on UP4 (VI) and voice is sent as UP6 (VO).
Although 802.11b/g EDCF does not guarantee that voice traffic is protected from data traffic, you should get the best statistical results by using this queuing model.
Note
The Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G marks the call control packets with a DSCP value of 24 and voice packets with DSCP value of 46.
To improve reliability of voice transmissions in a nondeterministic environment, the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G supports the IEEE 802.11e industry standard and is Wi-Fi Multimedia (WMM) capable. WMM enables differentiated services for voice, video, best effort data and other traffic. However, in order for these differentiated services to provide sufficient QoS for voice packets, only a certain amount of voice bandwidth can be serviced or admitted on a channel at one time. If the network can handle "N" voice calls with reserved bandwidth, when the amount of voice traffic is increased beyond this limit, (to N+1 calls), the quality of all calls suffers.
To help address the problems of VoIP stability and roaming, an initial Call Admission Control (CAC) scheme is required. With CAC, QoS is maintained in a network overload scenario by ensuring that the number of active voice calls does not exceed the configured limits on the AP. The Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G can integrate layer 2 TSpec admission control with layer 3 Cisco Unified Communications Manager admission control (RSVP). During times of network congestion, calling or called parties receive a Network Busy message. The system maintains a small bandwidth reserve so that wireless phone clients can roam into a neighboring AP, even when the AP is at full capacity. After reaching the voice bandwidth limit, the next call is load-balanced to a neighboring AP without affecting the quality of the existing calls on the channel.
Implementing QoS in the connected Ethernet switch is highly desirable to maintain good voice quality. The COS and DSCP values that the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G sets do not need to be modified. To configure QoS correctly on the AP, see Cisco Unified Wireless IP Phone 7925 and 7926 Series Deployment Guide.
Related Topics
•
Interacting with Cisco Unified Communications Manager
Interacting with Cisco Unified Communications Manager
Cisco Unified Communications Manager is the call control component in the network that handles and routes calls for the wireless IP phones. Cisco Unified Communications Manager manages the components of the IP telephony system—the phones, access gateways, and the resources—for such features as call conferencing and route planning. When deploying Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G, you must use Cisco Unified Communications Manager Release 4.3 and later, and SCCP protocol.
Before Cisco Unified Communications Manager can recognize a phone, the phone must register with Cisco Unified Communications Manager and be configured in the database. For information about setting up phones in Cisco Unified Communications Manager, see "Overview of Configuring and Installing the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G" section on page 1-15.
You can find more information about configuring Cisco Unified Communications Manager to work with the IP phones and IP devices in the Cisco Unified Communications Manager Administration Guide and Cisco Unified Communications Manager System Guide.
Related Topics
•
Phone Configuration Files and Profile Files
Phone Configuration Files and Profile Files
Phone configuration files define parameters for connecting to Cisco Unified Communications Manager and are stored on the TFTP server. In general, any time you make a change in Cisco Unified Communications Manager Administration that requires the phone to reset, the phone configuration file changes automatically.
Configuration files also contain information about the correct image load for the phone. If this image load differs from the one currently loaded on a phone, the phone contacts the TFTP server to request the new image file.
The phone first requests the configuration file SEPxxxxxxxxxxxx.cnf.xml, where each xx is the two-digit lowercase hexadecimal representation of each integer in the MAC address. If the phone cannot find this file, it requests the configuration file XMLDefault.cnf.xml.
After the phone obtains the *.cnf.xml files, it requests a phone-specific profile file. If a phone cannot find this profile file, it requests the appropriate common profile file.
After the phone finds one of the profile files, or if it cannot find a profile file, it continues with its startup process.
Related Topic
Understanding the Phone Startup Process, page 3-17
Interacting with the Dynamic Host Configuration Protocol Server
Dynamic Host Configuration Protocol (DHCP) is a communications protocol that lets network administrators manage and automate the assignment of IP addresses in a network. When an IP device is added to the network, it must have a unique IP address. Without DHCP, the IP address must be entered manually at each device. DHCP allocates IP addresses dynamically and reuses IP addresses when devices no longer need them.
If DHCP is enabled in the network, the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G uses the DHCP scope settings in the DHCP server to perform the phone provisioning bootup process. You must configure the settings of the DHCP server in the Cisco Unified Communications Manager network.
The DHCP scope settings include the following:
•
TFTP servers
•
DNS server IP address (optional unless using host names)
•
Pool and range of the subnet mask, IP address, and gateway
The priority of the DHCP settings for the TFTP server is unique to the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G, as shown in Table 2-7.
Table 2-7 DHCP Settings Priority
1
DHCP option 150
2
DHCP option 66
3
SIADDR
4
ciscoCM1
If DHCP is disabled, the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G uses the following network settings in Table 2-8 to perform the phone provisioning bootup process. You must configure these static parameters for each Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G.
Security for Voice Communications in WLANs
Because all WLAN devices that are within range can receive all other WLAN traffic, securing voice communications is critical in WLANs. To ensure that voice traffic is not manipulated or intercepted by intruders, the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G and Cisco Aironet APs are supported in the Cisco SAFE Security architecture. For more information about security in networks, see http://www.cisco.com/en/US/netsol/ns744/networking_solutions_program_home.html.
This section contains the following items:
•
Choosing AP Authentication and Encryption Methods
Authentication Methods
The Cisco Wireless IP telephony solution provides wireless network security that prevents unauthorized logins and compromised communications by using the following authentication methods.
•
Open Authentication—Any wireless device can request authentication in an open system. The AP that receives the request may grant authentication to any requestor or only to requestors on a list of users. Communication between the wireless device and AP could be non-encrypted.
•
Open Authentication with WEP—This is similar to Open Authentication in the preceding bullet, except with improved security. Communication between the wireless device and AP use Wired Equivalent Privacy (WEP) keys to provide security.
•
Shared Key Authentication—The AP sends an unencrypted challenge text string to any device attempting to communicate with the AP. The device that requests authentication uses a preconfigured WEP key to encrypt the challenge text and sends the encrypted challenge text back to the AP. If the challenge text is encrypted correctly, the AP allows the requesting device to authenticate. A device can authenticate only if its WEP key matches the WEP key on the APs.
Shared key authentication can be less secure than open authentication with WEP because someone can monitor the challenges. An intruder can calculate the WEP key by comparing the unencrypted and encrypted challenge text strings.
•
Extensible Authentication Protocol-Flexible Authentication via Secure Tunneling (EAP-FAST) Authentication—This client server security architecture encrypts EAP transactions within a Transport Level Security (TLS) tunnel between the AP and the RADIUS server such as the Cisco Access Control Server (ACS).
The TLS tunnel uses Protected Access Credentials (PAC) for authentication between the client (phone) and the RADIUS server. The server sends an Authority ID (AID) to the client (phone), which in turn selects the appropriate PAC. The client (phone) returns a PAC-Opaque to the RADIUS server. The server decrypts the PAC with its master-key. Both end points now have the PAC key and a TLS tunnel is created. EAP-FAST supports automatic PAC provisioning, but you must enable it on the RADIUS server.
Note
In the Cisco ACS, by default, the PAC expires in one week. If the phone has an expired PAC, authentication with the RADIUS server takes longer while the phone gets a new PAC. To avoid the PAC provisioning delays, set the PAC expiration period to 90 days or longer on the ACS or RADIUS server.
•
Extended Authentication Protocol Transport Level Security (EAP-TLS) Authentication—EAP-TLS/RFC 2716 uses the TLS protocol (RFC 2246), which is the latest IETF version of the SSL security protocol. TLS provides a way to use certificates for both user and server authentication, and for dynamic session key generation.
Microsoft Windows XP provides support for 802.1x, allowing EAP authentication protocols (including EAP-TLS) to be used for authentication. The authentication used in EAP-TLS is mutual: the server authenticates the user and the user authenticates the server. Mutual authentication is required in a WLAN. EAP-TLS provides excellent security but requires client certificate management.
EAP-TLS uses Public Key Infrastructure (PKI) with the following conditions:
–
A Wireless LAN client (user machine) requires a valid certificate to authenticate to the WLAN network.
–
An authentication server (typically a RADIUS server) requires a server certificate to validate its identity to the clients.
–
A Certificate Authority (CA) server infrastructure issues certificates to the authentication server and the clients.
•
Protected Extensible Authentication Protocol (PEAP) Authentication—PEAP uses server-side public key certificates to authenticate clients by creating an encrypted SSL/TLS tunnel between the client and the authentication server. This functionality is disabled by default and is enabled in Cisco Unified Communications Manager Administration.
•
PEAP with Server Certificate Authentication—The Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G can validate the server certificate during the authentication handshakes over an 802.11 wireless link.
The exchange of authentication information is encrypted and the user credentials are safe from eavesdropping. MS-CHAP v2 is the supported inner authentication protocol.
•
Light Extensible Authentication Protocol (LEAP)—Cisco proprietary password-based mutual authentication scheme between the client (phone) and a RADIUS server. Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G can use LEAP for authentication with the wireless network.
•
Auto (AKM)—Selects the 802.11 Authentication mechanism automatically from the configuration information exhibited by the AP. Supports WPA/WPA2-PSK or LEAP with 802.ax+WEP or WPA/WPA2.
This section describes the following concepts:
Authenticated Key Management
The following authentication schemes use the RADIUS server to manage authentication keys:
•
Wireless Protected Access (WPA)—Uses information on a RADIUS server to generate unique keys for authentication. Because these keys are generated at the centralized RADIUS server and are not saved on the phone or AP, WPA provides more security than WPA Pre-Shared Key (WPA PSK). WPA2 provides more security than WPA.
•
Cisco Centralized Key Management (CCKM)—Uses information on a RADIUS server and a wireless domain server (WDS) to manage and authenticate keys. The WDS creates a cache of security credentials for CCKM-enabled client devices for fast and secure reauthentication.
With WPA and CCKM, encryption keys are not entered on the phone, but are automatically derived between the AP and phone. The EAP username and password that are used for authentication must be entered on each phone.
Authenticated key management supports WPA/WPA2-PSK and WPA/WPA2/802.1x+WEP utilizing LEAP for the EAP type. CCKM can optionally be used with WPA/WPA2/802.1x+WEP mode.
Encryption Methods
To ensure that voice traffic is secure, the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G supports WEP, TKIP, and Advanced Encryption Standards (AES) for encryption. When using these mechanisms for encryption, both the signaling Skinny Client Control Protocol (SCCP) packets and voice Real-Time Transport Protocol (RTP) packets are encrypted between the AP and the wireless IP phone.
•
WEP—When using WEP in the wireless network, authentication happens at the AP by using open or shared-key authentication. The WEP key that is set up on the phone must match the WEP key that is configured at the AP for successful connections. The Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G supports WEP keys that use 40-bit encryption or a 128-bit encryption and remain static on the phone and AP.
EAP and CCKM authentication can use WEP keys for encryption. The RADIUS server manages the WEP key and passes a unique key to the AP after authentication for encrypting all voice packets; consequently, these WEP keys can change with each authentication.
•
Temporal Key Integrity Protocol (TKIP)—WPA and CCKM use TKIP encryption that has several improvements over WEP. TKIP provides per-packet key ciphering and longer initialization vectors (IVs) that strengthen encryption. In addition, a message integrity check (MIC) ensures that encrypted packets are not being altered. TKIP removes the predictability of WEP that helps intruders decipher the WEP key.
•
AES—An encryption method used for WPA2 authentication. This national standard for encryption uses a symmetrical algorithm that has the same key for encryption and decryption. AES uses Cipher Blocking Chain (CBC) encryption of 128 bits in size, supporting key sizes of 128, 192 and 256 bits, as a minimum.
Choosing AP Authentication and Encryption Methods
Authentication and encryption schemes are set up within the wireless LAN. VLANS are configured in the network and on the APs and specify different combinations of authentication and encryption. An SSID is associated with a VLAN and its particular authentication and encryption scheme. In order for wireless client devices to authenticate successfully, you must configure the same SSIDs with their authentication and encryption schemes on the APs and on the wireless IP phone.
Some authentication schemes require specific types of encryption. With Open authentication, you can use static WEP for encryption for added security. But if you are using Shared Key authentication, you must set static WEP for encryption, and you must configure a WEP key on the phone.
When using Authenticated Key Management (AKM) for the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G, several choices for both authentication and encryption can be set up on the APs with different SSIDs. When the phone attempts to authenticate, it chooses the AP that advertises the authentication and encryption scheme that the phone can support. Auto (AKM) mode can authenticate by using WPA, WPA2, WPA Pre-shared key, or CCKM.
Note
•
When using WPA Pre-shared key or WPA2 Pre-shared key, the pre-shared key must be statically set on the phone. These keys must match the keys configured on the AP.
•
When using Auto (AKM), encryption options are automatically configured for WPA, WPA2, WPA Pre-shared key, WPA2 Pre-shared key, or CCKM.
•
In AKM mode, the phone will authenticate with LEAP if it is configured with WPA, WPA2, or CCKM key management.
•
The Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G does not support auto EAP negotiation; to use EAP-FAST mode, you must specify it.
•
If AKM and 802.1x are used, the authentication method is LEAP.
•
The Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G uses network EAP for 802.1x but you can enable open EAP.
Table 2-9 provides a list of authentication and encryption schemes configured on the Cisco Aironet APs supported by the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G. The table shows the network configuration option for the phone that corresponds to the AP configuration.
For additional information about Cisco WLAN Security, see http://www.cisco.com/en/US/products/hw/wireless/ps430/prod_brochure09186a00801f7d0b.html
For more information about configuring authentication and encryption schemes on APs, see the Cisco Aironet Configuration Guide for your model and release at this URL:
Related Topics
•
Networking Protocols Used with Cisco Unified Wireless IP Phones
•
Interacting with Cisco Unified Communications Manager
•
Components of the VoIP Wireless Network
Site Survey Verification
Before the initial deployment of wireless phones in the WLAN, perform a site survey to verify that the APs are providing adequate coverage and that wireless phones can roam from one AP to another with no audio problems. After the initial deployment, it is a good practice to perform site surveys at regular intervals to ensure continued coverage and roaming.
From the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G, you can use the Neighbor List utility or Site Survey utility from the SETTINGS > Status menu.
The Neighbor List utility provides information about the current AP and the closest neighbors tracked by the phone. For more information, see Using the Neighbor List Utility.
The Site Survey utility produces a report, written as a temporary HTML file, upon termination of the survey. This Site Survey Report is accessible from the phone web page to view or send to Cisco TAC for troubleshooting purposes. For more information, see Using the Site Survey Utility.
Use the following topics for information about performing the site survey:
•
Performing a Site Survey Verification
•
Using the Neighbor List Utility
•
Using the Site Survey Utility
Performing a Site Survey Verification
Perform these tasks to verify wireless voice network operation. Check that the wireless IP phones:
1.
Associate with all APs in the WLAN.
2.
Authenticate with all APs in the WLAN.
3.
Register with Cisco Unified Communications Manager.
4.
Can make stationary phone calls with good quality audio.
5.
Can make roaming phone calls with good quality audio and no disconnections.
6.
Can place multiple calls, especially in areas designated for high density use.
After phones are installed, request that users report any problems when using their wireless IP phones.
When you perform a site survey verification and encounter problems, see Chapter 10, "Troubleshooting the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G" for assistance with finding the cause of the problem.
Related Topics
•
Using the Neighbor List Utility
•
Using the Site Survey Utility
Using the Neighbor List Utility
The Neighbor List utility displays a list of the current AP and the closest neighbors tracked by the phone. The phone typically does not scan while it is idle, so often there is only one entry, which is the currently associated AP, in the list.
To use the Neighbor List utility, follow these steps:
Procedure
Step 1
Configure the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G with the same SSID and encryption/authentication settings as the APs.
Step 2
Power on the phone so that it associates with the WLAN.
Step 3
Choose SETTINGS > Status > Neighbor List.
The phone displays the current AP and the closest neighbors. For example:
SSID: abcd
Step 4
To see more information about an AP, scroll to the desired line and press Details. The following is an example of the details for a specific AP:
SSID: voiceChannel: 36BSSID: 00:13:1a:16:cf:d0RSSI:-59CU:10Step 5
To verify the ability to roam between APs, walk through all areas where phones are used and take readings. Approach areas from different directions to assure successful roaming conditions.
Step 6
Adjust AP and antenna placement and AP power settings to provide adequate coverage overlap.
Using the Site Survey Utility
The Site Survey utility is used to actively and passively scan the wireless medium across all channels and to locate APs that belong to the Basic Service Set (BSS). The results of the scans can help to identify areas of low coverage, if any, and to determine whether the APs are configured consistently as recommended in the Cisco deployment guidelines.
When you start the Site Survey utility, the phone disassociates from the current AP and remains disassociated for the duration of the operation.
For more information, see Viewing the Site Survey Report on the Web, page 4-39.
CautionDuring Site Survey, both active and passive scans are performed at a rapid rate. These scans will result in the phone battery life depleting faster than normal and might cause disruption to the wireless medium.
To use the Site Survey utility, follow these steps:
Procedure
Step 1
Configure the Cisco Unified Wireless IP Phone 7925G, 7925G-EX, and 7926G with the same SSID and encryption/authentication settings as the APs.
Step 2
Power on the phone so that it associates with the WLAN.
Step 3
Choose SETTINGS > Status > Site Survey.
The phone displays a list of APs within range that have the same SSID and security settings as the phone. To see more information about an AP, scroll to the desired line and press Details.
Step 4
To verify the ability to roam between APs, walk through all areas where phones are used and take readings. Approach areas from different directions to assure successful roaming conditions.
Step 5
Adjust AP and antenna placement and AP power settings to provide approximately 20 percent coverage overlap.
Step 6
When you terminate the site survey, a report is generated for you to view from the phone web page. For more information, see Viewing the Site Survey Report on the Web, page 4-39.
Related Topics
•
Performing a Site Survey Verification

 Feedback
Feedback