Table Of Contents
Recovering Secure Erase Configuration
Configuring Secure Erase
This chapter describes how to configure Cisco MDS Secure Erase, and has the following sections:
Secure Erase is included in the SSI image. For more information on how to install SSM, refer to the Cisco MDS 9000 Family Storage Services Module Software Installation and Upgrade Guide.
Configuration Overview
Cisco Secure Erase runs on the SSM installed in an MDS 9500 or 9200 series switch.
The Secure Erase software package is included in the SSI image, which is delivered as part of SAN-OS.
For information on how to install the SSM image, refer to the Cisco MDS 9000 Family Storage Services Module Software Installation and Upgrade Guide.
The Secure Erase feature must be provisioned on the SSM.
Configuartion Process
The following sections provide an overview of a typical Secure Erase process:
•
Setting up Cisco Secure Erase
•
Recovering Secure Erase Configuration
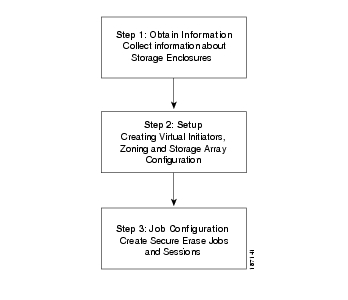
Figure 2-1 Secure Erase Workflow Diagram
Obtaining Information
You need to collect the following information about the target enclosure:
•
Information about the target enclosure or storage array on which you would like to perform Secure Erase. The storage array is also called as Secure Erase storage array.
•
Information about WWNs of the target ports you would like to use to access the target enclosure. The target ports are called Secure Erase target ports and the VSANs where the Secure Erase target ports reside are called Secure Erase VSANs.
•
Information about one or more LUNs on the Secure Erase storage array on which you would like to perform Secure Erase. These LUNs are also called as Secure Erase LUNs.
Setting up Cisco Secure Erase
You need to create the VIs, setup zone, and storage array configuration to preconfigure Secure Erase.
The CLI configuration is preserved across reboots or switch reloads. It is preferred to have one job per storage enclosure. A storage enclosure can have multiple storage ports spanning multiple VSANs and storage LUNs.
Additionally, complete the following tasks:
•
Set up the zone.
Decide on one or more Secure Erase VIs and zone target ports that you would like to use to perform Secure Erase.
•
Program the storage array.
The Secure Erase storage array must be programed to enable Secure Erase VIs to access the Secure Erase LUNs. Secure Erase requires write commands to go directly to the physical media.
Secure Erase sends all write commands with Force Unit Access (FUA) bit on. When the bit is set, the SCSI device is instructed to bypass the cache and perform the command directly on the physical media.
Note
Check with the storage array vendor to confirm that FUA bit is supported in SCSCI writes.
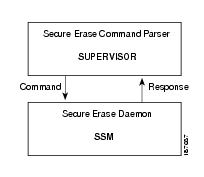
Figure 2-2 Interaction of SUP and SSM
All Secure Erase CLIs are performed at Supervisor. The Secure Erase configuration is stored in persistent memory on the supervisor engine.
Job Configuration
You can configure Cisco Secure Erase jobs and sessions using the CLI. For information about the CLI, refer to the "Secure Erase CLI Command Reference, page A-1".
To create a Secure Erase job and session, follow these steps:
To stop or abort a Secure Erase job and session, follow this step:
Recovering Secure Erase Configuration
The SSM and supervisor engine configuration recovery process consists of the following tasks:
•
All Secure Erase configuration is stored in persistent memory and is automatically recovered on a crash or reload of the SSM or a reload of the Cisco MDS supervisors.
•
After the recovery process is complete, the recovered data is validated by performing a discovery process using this command:
secure-erase module module-id validate job job-id

 Feedback
Feedback