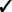-
User Guide for Cisco Security MARS Local Controller, Release 5.2.x
-
Preface
-
STM Task Flow Overview
-
Reporting and Mitigation Devices Overview
-
Configuring Router and Switch Devices
-
Configuring Firewall Devices
-
Configuring VPN Devices
-
Configuring Network-based IDS and IPS Devices
-
Configuring Host-Based IDS and IPS Devices
-
Configuring Antivirus Devices
-
Configuring Vulnerability Assessment Devices
-
Configuring Generic, Solaris, Linux, and Windows Application Hosts
-
Configuring Database Applications
-
Configuring Web Server Devices
-
Configuring Web Proxy Devices
-
Configuring AAA Devices
-
Configuring Custom Devices
-
Policy Table Lookup on Cisco Security Manager
-
Network Summary
-
Case Management
-
Incident Investigation and Mitigation
-
Queries and Reports
-
Rules
-
Sending Alerts
-
Management Tab Overview
-
System Maintenance
-
Cisco Security MARS XML API Reference
-
Regular Expression Reference
-
Date/Time Format Specfication
-
System Rules and Reports Reference
-
Glossary
-
Index
-
Table Of Contents
Policy Table Lookup on Cisco Security Manager
Overview of Cisco Security Manager Policy Table Lookup
More About Cisco Security Manager Device Lookup
More About Cisco Security Manager Policy Table Lookup
Prerequisites for Policy Table Lookup
Restrictions for Policy Table Lookup
Checklist for Security Manager-to-MARS Integration
Bootstrapping Cisco Security Manager Server to Communicate with MARS
Add a Cisco Security Manager Server to MARS
Procedure for Invoking Cisco Security Manager Policy Table Lookup from Cisco Security MARS
Policy Table Lookup on Cisco Security Manager
MARS and Cisco Security Manager (Security Manager) can be configured to provide round-trip policy audit features and improve traffic flow analysis and debugging. Using this feature, you can identify the ACL on a router or firewall that generated a syslog message received by MARS. It is important to understand that the integration between MARS and Security Manager is unique; MARS can provide users of Security Manager with better analytical tools.
When using MARS as your STM solution, you must understand that MARS suggests and makes changes to devices without notifying Security Manager of the suggested changes. Specifically, you can use the "Big Red" button to shutdown a port for support L2 devices. For a layer 3 device, MARS suggest ACL changes to block the traffic. In such cases, you can use Security Manager to manually mitigate using the ACL recommendations provided by MARS, thereby, ensuring that the configuration management solution stays abreast of the mitigation responses. Security Manager can also publish the same change to all like devices that it manages, providing a more robust containment.
For example, consider the following case where a user cannot connect to destination X from source Y. To troubleshoot this issue, an administrator can do the following:
1.
Log into the MARS web interface, and using an on-demand query, determine whether an event has been received that shows that traffic from source Y to destination X has been blocked.
2.
If such events are found, the administrator can continue by determining which ACL is actually blocking the traffic. To do so, the administrator would click the policy query icon in the row of one of the selected events. MARS then queries Security Manager to retrieve the list of ACLs that match that traffic flow, and assuming Security Manager was used to configure the routers and firewalls between source Y and destination X, then a list of matching ACLs are returned.
3.
Next, the administrator can log into the Security Manager user interface and modify the identified policy, or ACL, to allow traffic between source Y and destination X.
This chapter describes how to configure Security Manager and MARS to ensure optimal functionality and seamless integration.
Overview of Cisco Security Manager Policy Table Lookup
When MARS receives a syslog from a Cisco PIX firewall, Cisco Adaptive Security Appliance (Cisco ASA), Cisco Firewall Services Module (Cisco FWSM), or Cisco IOS, and can derive the five tuple information required to establish an event (source IP, destination IP, source port, destination port, and protocol) the Security Manager Policy Table Lookup icon
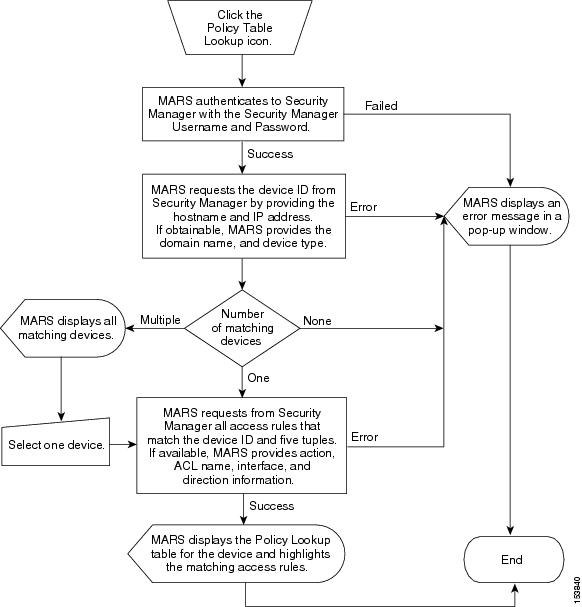
appears in the Reporting Device column of the MARS session display. Clicking the icon invokes a query to the Security Manager, the result of which is to identify the access rule in the policy table of the device which created the traffic incident or event. Figure 16-1 depicts the policy query process between MARS and Security Manager.
Figure 16-1 Cisco Security MARS Policy Table Query Process
The syslog that generated the MARS incident or event may not have sufficient information for Security Manager to uniquely identify the device or the access rule. In these ambiguous cases, Security Manager returns a list of all possible devices to MARS in a pop-up window. When the MARS user manually selects a reporting device, the policy table is then displayed for that device. Access rules that match the query criteria are highlighted.
Note
The policy table displayed by MARS is the Security Manager Committed View, not the Deployed View, meaning the displayed Security Manager policies are saved in the Security Manager database but not yet deployed on the device. If the deployed and committed views are not identical, the access rule generating the MARS event may not be visible in the policy table displayed by MARS. For further information on Cisco Security Manager operation, please access the documentation at the following URL:
http://www.cisco.com/en/US/products/ps6498/tsd_products_support_series_home.html
More About Cisco Security Manager Device Lookup
MARS requests the Policy Table of a Security Manager device by supplying the following criteria to Security Manager:
•
Device Name—Derived from MARS Device Name
•
IP Address—Derived from MARS Reporting IP
•
Domain Name—If available, derived from the device name in MARS (for example, c3550-225-125.clab.cisco.com)
•
Device Type—If available from MARS
The Device Lookup query includes the following actions between MARS and Security Manager:
1.
Security Manager matches the MARS Device Name to the Security Manager host names. If only one matching host name is discovered, the process for Policy Table Lookup is invoked.
2.
If the Security Manager host name is undefined, then Security Manager matches the MARS Device Name with the Security Manager Display Name (display names are unique, but the host name may be a substring of many display names.)
3.
If there are multiple matches on host name and no unique display name matches, the domain name (if available) is used to narrow the choices.
4.
If the domain name is not available, MARS Reporting IP is used to narrow the choices.
5.
If a unique device cannot be identified, MARS displays a list of possible devices in a pop-up window that shows the IP address, host name, display name, and domain name for all possible device matches. The user manually selects the device and the process for the policy table lookup is invoked.
More About Cisco Security Manager Policy Table Lookup
The device lookup information is combined with the event information to perform the Security Manager policy table lookup.
The following MARS event information derived from the reporting device raw message is passed to Security Manager:
•
Event Five Tuple—Source IP Address, Destination IP address, Source Port, Destination Port, and Protocol defining session. The event five tuple must match the five tuples of the target access rule. For ICMP logs, ICMP type and code, when available, are passed instead of the source and destination ports.
•
Action—If available, permit or deny. If not available, access rules with both permit and deny are highlighted.
•
ACL name—If available, the name of the ACL or Access Group that triggers the syslog. With the ACL name, Security Manager can reduce the number of matching access rules.
•
Interface—If available, the interface names are parsed from the event's raw message.
•
Direction—If available, keyword such as "inbound" and "outbound" identify the direction.
The device, five tuple, action, ACL name, interface, and direction information comprise the policy query criteria submitted to the Security Manager. MARS displays the policy table in a pop-up window. The matching access rule is displayed in highlight. If MARS was unable to provide the interface, direction, and action information, multiple matched access rules may be highlighted.
Sample Cisco PIX Firewall Syslog Messages with Direction and Protocol Information
10.33.10.2 <142>%PIX-6-302013: Built outbound TCP connection 2021 for inside:10.1.1.10/4000 (10.1.1.10/4000) to dmz:192.168.1.10/80 (192.168.1.10/80)10.33.10.2 <142>%PIX-6-302013: Built inbound TCP connection 2000 for outside:1.234.58.149/12000 (1.234.58.149/12000) to inside:192.168.1.10/25 (100.1.4.10/25)Sample Cisco PIX Firewall Syslog Messages with Access Group Name Information
10.33.10.2 <142>%PIX-4-106023: Deny tcp src inside:10.1.5.234/3010 dst outside:5.6.7.8/21 by access-group "Cisco Security Manager-acl-inside"Sample Cisco IOS 12.2 Syslog Messages with ACL Name Information
100.1.20.2 Mon Jun 9 14:46:31 2003 <46>485232: Jun 9 14:46:29 PDT: %SEC-6-IPACCESSLOGP: list Cisco Security Manager-acl-FastEthernet0/0 permitted tcp 1.234.51.255(12000) -> 100.1.4.10(25), 1540 packet10.34.1.1 <46>146570: Dec 19 21:01:57 PST: %SEC-6-IPACCESSLOGP: list Cisco Security Manager-acl-FastEthernet1/0 denied tcp 10.10.1.20(59399) -> 10.1.5.11(23), 1 packetPrerequisites for Policy Table Lookup
•
MARS Local Controller running software version 4.2.1 or more recent version.
•
Cisco Security Manager version 3.0.1 or more recent
•
MARS configured for operation with Cisco Security Manager as explained in the section, Checklist for Security Manager-to-MARS Integration
Restrictions for Policy Table Lookup
•
A Local Controller can be configured to retrieve the policy tables from only one Cisco Security Manager server at a time.
•
The Policy Table Lookup icon in MARS is displayed only for traffic logs which are reported by the following MARS device types:
–
Cisco Switch-IOS
–
Cisco PIX firewalls
–
Cisco Adaptive Security Appliance (Cisco ASA)
–
Cisco Firewall Services Module (Cisco FWSM)
•
MARS displays the Cisco Security Manager security policy committed views, not the deployed views. The access rule causing the MARS event may not be visible in the policy table. To examine the deployed policies view of a device, you must login to the device or Cisco Security Manager directly.
•
MARS examines only Layer 3 ACLs for traffic events on the supported reporting devices. The policy table lookup cannot directly indicate the cause of a traffic event caused by a deny not related to the displayed access rules, though the policy table can be displayed for the event (For instance, a no route deny, or a Network Address Translation [NAT] deny due to a NAT misconfiguration).
•
The Security Manager Policy Table Lookup icon displays only for those events with 5-tuple event data (source and destination address, protocol, source and destination port). In the MARS web interface, the all matching events query diplays the text "session five tuple" for events with no 5-tuple event data. These events will not have a policy query icon.
•
The Security Manager Policy Table Lookup icon displays for NetFlow events even though they are not triggered by an ACL. This extra event data allows you to determine whether there is a policy permitting that traffic, which ensures you are able to tune accordingly.
Note
Because this is NetFlow data, it may not match the exact ACL or match multiple ACLs.
•
The same events received by MARS can display the Security Manager Policy Table Lookup icon inconsistently between the low-latency, real-time event query and standard queries, such as sessions ranked by time. Specifically, the icon will not appear in the low-latency, real-time query, but it may appear in queries against sessionized events.
This behavior is expected. When MARS receives events, they are parsed, sessionized, written to an event shared buffer, and then written to the database. Because sessionization takes time, sometimes keeping an event in cache for 2 minutes, the low-latency event query displays events right after parsing, but before sessionization. Displaying the event at this point allows the low-latency query to achieve a close to real-time effect. For some events, parsing cannot determine some part of the 5-tuple data, such as a destination address. Later, sessionization later fills in such missing data using configuration data. As a result, the 5-tuple data displayed by the low-latency event query can be different from values stored in the database, which are used to populate the standard queries.
•
An error can occur with the policy query if a device configuration is discovered using Security Manager but it is not submited in Security Manager. The following error message is an example of this issue:
<190>2312080: *May 9 23:50:02.199: %SEC-6-IPACCESSLOGDP: list permit-all permitted icmp 10.2.3.8 -> 10.4.21.2 (0/0), 1 packetAn error occurred while querying policies from Cisco Security Manager. Reason: Failed to retrieve policy information from CSM. Reason: Cisco Security Manager Internal error: Failed to get interfaces in the device!The device LC2DTM was discovered by CSM without any errors.Before you perform policy queries, verify that all discovered devices have been submitted in Security Manager.
Checklist for Security Manager-to-MARS Integration
Security Manager-to-MARS integration deals with identifying the required and optional points of integration, configuring the applications and devices, and ensuring proper authorization among the two management platforms. This checklist assumes a greenfield install of both Security Manager and MARS.
The following checklist describes the tasks required to understand the decision-making process and the basic flow required to integrate MARS with a Security Manager server and the reporting and mitigation devices managed by that Security Manager server. Each step might contain several substeps; the steps and substeps should be performed in order. The checklist contains references to the specific procedures used to perform each task.
Note
For a comprehensive checklist on configuring MARS to operate most effectively as an STM, see
STM Task Flow Overview, page 1-1.
1.
Inventory overlapping reporting devices and mitigation devices.
MARS supports round-trip policy audit analysis for reporting and mitigation devices that are both managed by Security Manager and monitored by a MARS Appliance. In other words, MARS can query the policy rules that generated an audit event log only when the policies are defined using Security Manager. As such, the first step in integrating MARS and Security Manager involves identifying those devices for which Security Manager is used to define policy rules. You must also ensure that devices are running a software versions supported by both MARS and Security Manager.
This list focuses on those devices that Security Manager manages and should include all of the following devices:
•
Cisco ASA appliances, PIX appliances, and FWSM modules
•
Cisco Catalyst 6500 Series Switches
•
Cisco Routers running supported versions of Cisco IOS software
Note
MARS supports PIX 7.0 and ASA 7.0.1 releases; however, it does not support FWSM 3.1. FWSM support is restricted to FWSM 1.1, 2.2, and 2.3. For current device support information, see Supported and Interoperable Devices and Software for Cisco Security MARS Local Controller 4.2.x and 5.2.x.
Note
FWSM support is supported only in Cisco Security Manager Enterprise Edition (Professional-50) and higher, The Professional version includes support for the management of Cisco Catalyst® 6500 Series switches and associated services modules; the Standard versions do not include this support.
Result: The list of devices for which Security Manager manages the security and audit log policies is defined. The details of each device include device name, reporting IP address, management IP address, management protocol, administrative account information, and the logging features, levels, and protocols to enable.
For more information, see:
•
Supported Devices and Software Versions for Cisco Security Manager 3.0
•
Selecting the Devices to Monitor, page 2-2
•
Levels of Operation, page 2-1
•
Deployment Planning Guidelines, page 2-1 in Install and Setup Guide for Cisco Security Monitoring, Analysis, and Response System
2.
Identify and enable all required traffic flows.
After you identify the devices managed by the Security Manager server, you must verify that the network services they use for management, reporting, and notification are permitted along the required traffic flows. Using the detailed Device Inventory Worksheet identified in Step 1., ensure that the management, logging, and notification traffic between the MARS Appliance and each supporting device, reporting device, and mitigation device is allowed by intermediate gateways.
In addition, network services of supporting devices, such as DNS, e-mail, AAA, and NTP servers, must also be permitted to flow among the MARS Appliance, the supporting devices, and the reporting devices and mitigation devices on your network.
TipIt is a recommended security practice to have all devices, including MARS Appliances, synchronized to the same time.
Result: You have verified that all intermediate gateways permit the log, management, and notification traffic between the devices and the MARS Appliance.
For more information, see:
•
Deployment Planning Guidelines, page 2-1, in Install and Setup Guide for Cisco Security Monitoring, Analysis, and Response System
•
Supporting Devices, page 2-1, in Install and Setup Guide for Cisco Security Monitoring, Analysis, and Response System
•
Required Traffic Flows, page 2-2, in Install and Setup Guide for Cisco Security Monitoring, Analysis, and Response System
•
Specify the Time Settings, page 5-10, in Install and Setup Guide for Cisco Security Monitoring, Analysis, and Response System
•
Event Timestamps and Processing in Top Issues for the Cisco Security Monitoring, Analysis, and Response System
3.
Bootstrap the reporting devices and mitigation devices managed by Security Manager.
For each device identified in Task 1., you must prepare, or bootstrap, that device to ensure that the desired communications with MARS occur. Bootstrapping a device involves configuring the settings for that device, based on its role in the STM system. Perform the following subtasks as applicable to a device type and its role:
•
Enable management of the device by the MARS Appliance for mitigation and access.
•
Turn on the correct logging level and logging services.
•
Direct the logs to the MARS Appliance.
•
Enable discovery of the device settings.
Note
While many Cisco devices support the EMBLEM syslog format, this format is not compatible with MARS. As part of this task, you must verify that the devices are not reporting to the MARS Appliance using the EMBLEM format.
You must configure the router and switch settings using the CLI, as Security Manager does not support those features. However, for ASA, FSWM, and PIX, you can use the Security Manager user interface to configure the management and log settings.
TipAny events published by a device to MARS prior to adding and activating the device in the web interface can be queried using the reporting IP address of the device as a match criterion. This technique can be useful for verifying that the device is properly bootstrapped.
You may also need to enable alternate settings on the to provide richer data. For more information on these possible settings, see Task 5 in the Checklist for Provisioning Phase, page 1-2 found in the STM Task Flow Overview chapter.
Result: The correct logging levels are enabled on the reporting devices and mitigation devices. The MARS Appliance can receive or pull any necessary logs from those devices, and it can retrieve configuration settings and push ACLS to the supported mitigation devices. While the MARS Appliance picks up and stores the events it receives, it does not inspect them until the reporting devices and mitigation devices are defined and activated in web interface.
For more information, see:
•
Device Inventory Worksheet, page 1-18
•
Bootstrap Summary Table, page 2-12
•
Cisco Router Devices, page 3-1
•
Cisco Switch Devices, page 3-9
User Guide for Cisco Security Manager 3.0
•
Understanding Device Credentials
See SNMP credentials.
•
Managing Firewall Devices (ASA, PIX, and FWSM)
See device access, SNMP settings, logging policies, and static routes as needed.
Note
When defining SNMP settings for the FWSM and ASA, you should define these setting for the admin context.
•
Field definitions for the Logging Policies (ASA, PIX, and FWSM)
•
Managing Routers (Cisco IOS Routers)
See device access, SNMP, 802.1x, NAC, and static routes as needed.
•
Using the Catalyst 6500/7600 Device Manager (Cisco Switches)
See Spanning Tree Settings (STP).
4.
Define the devices in MARS.
After you identify and bootstrap the reporting devices and mitigation devices and enable the required traffic flows, you must represent those devices in MARS, which uses this information to communicate with the devices. You can do this by adding individual devices in the web interface or by importing a comma separated vector (CSV) file, which can define the required settings for basic device types and give you a headstart on defining the more complicated devices. After you add the devices, you must activate them by clicking Activate on any page in the web interface.
To display all devices that are either added incorrectly or not activated in MARS, you can define one of two queries:
•
Select "Unknown Reporting Device" in the Devices field. This query returns the events only for those devices that are reporting events that do not matching the one of the reporting IPs defined in MARS. When MARS receives events, it first determines if the IP from which the events are received matches one of reporting IPs identified in the Reporting and Monitor Devices page. Only if MARS finds a match does it attempt to parse the events. Therefore, if the Reporting IP is defined incorrectly for a reporting device, the events from that device are not parsed. This query essentially identifies events that are not parsed.
•
Select the "Unknown Device Event Type" in the Events field. This query returns events from known devices that for some reason the event is not parsed by MARS (for example, if the MARS signature list is not current with the device event lists), and it returns events reported by unknown devices.
For both queries, if you are looking for a specific reporting IP address, enter that address in the Keyword field to filter the results down to those that include that IP address.
Result: All reporting devices and mitigation devices are defined and activated in MARS. When the devices are bootstrapped and defined in MARS, MARS begins to inspect the logs received from the devices. Until the devices are added in MARS, MARS picks up and stores the events it receives without inspecting them.
For more information, see:
•
Device Inventory Worksheet, page 1-18
•
Selecting the Access Type, page 2-10
•
Add Reporting and Mitigation Devices Individually, page 2-17
•
Add Multiple Reporting and Mitigation Devices Using a Seed File, page 2-20
•
Adding Reporting and Mitigation Devices Using Automatic Topology Discovery, page 2-25
•
Cisco Firewall Devices (PIX, ASA, and FWSM), page 4-1
•
Cisco Router Devices, page 3-1
•
Cisco Switch Devices, page 3-9
•
Supported Reporting and Mitigation Devices, page 3 (CSV Keyword column)
•
Verify Connectivity with the Reporting and Mitigation Devices, page 2-26
5.
Bootstrap each Security Manager server and add it to the correct MARS Local Controller.
The required setup of the Security Manager server is quite simple:
•
Verify that HTTPS is enabled on the Security Manager server.
•
Define an account with requisite privileges for use by MARS when performing policy queries.
•
Ensure that the MARS Appliance, as a host, has permission to access the Security Manager server.
•
Ensure the HTTPS traffic flows are permitted between the two hosts. You can verify connectivity by clicking Test Connectivity when defining a Security Manager server. It does not perform a lookup, but it does authenticate to the Security Manager server.
Note
Each Local Controller can only manage one Security Manager server. All policy lookups for syslog messages received on a Local Controller are directed to the Security Manager server configured for that Local Controller.
In addition, you should ensure that the user account used by MARS is exclusive on the Security Manager server. An exclusive account allows you to more easily detect any fraudulent use of the account.
MARS does not retrieve any audit log data from the Security Manager server. It merely accesses the set of policy rules that are defined on the server.
Once you prepare the Security Manager server, you must return to the MARS web interface and add the Security Manager server.
Result: The correct settings are enabled on each Security Manager server. The MARS Appliance can request and receive queries from no more than one Security Manager server. After adding the Security Manager server to the MARS web interface, you can test the connectivity by performing a policy lookup query on any of the events that have been received from one of the managed reporting devices and mitigation devices.
For more information, see:
•
Bootstrapping Cisco Security Manager Server to Communicate with MARS
•
Add a Cisco Security Manager Server to MARS
•
Supported Reporting and Mitigation Devices, page 3
•
Procedure for Invoking Cisco Security Manager Policy Table Lookup from Cisco Security MARS
6.
Perform policy lookups as required.
Once an event generated by one of the Security Manager-managed devices is received by MARS, you can perform a policy lookup operation. This operation allows you to, from a given incident or an event query, retrieve a list of the possible policies that could have affected the generation of that event from the Security Manager server.
For more information, see:
•
More About Cisco Security Manager Device Lookup
•
More About Cisco Security Manager Policy Table Lookup
•
Prerequisites for Policy Table Lookup
•
Restrictions for Policy Table Lookup
•
Procedure for Invoking Cisco Security Manager Policy Table Lookup from Cisco Security MARS
7.
Using Security Manager for mitigation response.
While MARS suggests ACL changes to mitigate attacks, and in the case of Layer 2 devices such as Cisco switches, it can push changes to layer 2 device via the "Big Red" button (which shuts down a port on a switch), you must ensure accuracy between the policy defined in Security Manager and the configuration running on the managed devices. This synchronization ensures an accurate understanding of your network configuration and improves your ability to troubleshoot issues using the policy analysis tools provided in Security Manager.
Therefore, we recommend that you perform the device mitigation by applying the rules recommended by MARS with Security Manager. This approach also prevents you from having to manually synchronize your policy between Security Manager and the mitigation devices. As an added benefit, you can enable and remove containment rules on multiple devices via global rules, thereby further restricting the spread of possibly undetected infections. Using comments in the rules, you can document the attack responses, allowing for future analysis when considering global network stances and when developing attack response strategies.
Bootstrapping Cisco Security Manager Server to Communicate with MARS
To prepare the Security Manager server to be queried by MARS, you must configure the following settings:
•
Define an admin account in Security Manager that MARS can use to perform queries. A separate account is recommended to provide a cleaner audit trail on the Security Manager server. The following security levels defined in Common Services 3.0 server satisfy the authorization requirements of MARS-to-Security Manager policy query:
–
Help Desk
–
Network Operator
–
Network Administrator
–
System Administrator
Note
Cisco does not recommend using System Administrator for this account. Instead, we recommend least privilege settings (only enabling those privileges required to perform the job). As such, we recommend defining an admin account with the Help Desk security level.
For more information on defining admin accounts on the Common Services 3.0 server, see:
•
Enable HTTPS access to the Common Services 3.0 server by the MARS Appliance. If you are using AAA authentication, such as Cisco Secure ACS, on the Common Services 3.0 server, you must update the administrative access settings to ensure that the MARS Appliance has the necessary access to the Security Manager server.
•
Before MARS can query the policies defined on the Security Manager server, you must enable HTTPS on the Security Manager server. For more information on enabling HTTPS, see:
Add a Cisco Security Manager Server to MARS
The Security Manager server is represented in MARS by defining a host with a software application residing on that host. Once you have identified the reporting devices to a Local Controller, you can add the Security Manager server that manages the policies for those reporting devices.
Each Local Controller can query one Security Manager server only; you cannot define more than one Security Manager server per Local Controller. You can define the same Security Manager server on multiple Local Controllers. When planning the zones for Global Controller/multi-Local Controller deployments, ensure that each Local Controller maps to the Security Manager server that manages the reporting devices monitored by that Local Controller.
To identify a Security Manager server to use for policy lookups from within the web interface of MARS, follow these steps;
Step 1
Select Admin > System Setup > Security and Monitor Devices > Add.
Step 2
Do one of the following:
•
Select Add SW Security apps on a new host from the Device Type list, and continue with Step 3
•
Select Add SW security apps on existing host from the Device Type list. Select the device to which you want to add the software application and click Add. Continue with Step 6.
Step 3
Specify values for the following fields:
•
Device Name — Enter the name of the device. This name must exactly match the hostname shown in the Cisco Security Manager user interface. MARS maps this name to the reporting IP address. This name is used in topology maps, queries, and as the primary management station in the Security and Monitoring Device list.
•
Access IP — This s address is used to pull query data from a Security Manager server using HTTPS, enabling MARS to discover settings and perform policy queries from this device. This address represents the physical IP address of the Security Manager server. To learn more about the access IP address, its role, and dependencies, see Understanding Access IP, Reporting IP, and Interface Settings, page 2-8.
•
Reporting IP — (Optional) If the Security Manager server is host to a reporting device other than Cisco Security Manager, enter the IP address of the interface in the Security Manager server from which MARS. This address represents the physical IP address of the Security Manager server. To learn more about the reporting IP address, its role, and dependencies, see Understanding Access IP, Reporting IP, and Interface Settings, page 2-8.
•
Operating System — (Optional) If the Security Manager server is host to a reporting device other than Cisco Security Manager, you may need to specify the operating system type.
Step 4
Under Enter interface information, enter the interface name, IP address, and netmask value of each interface in the Security Manager server from which configuration information will be queried.
This address represents the physical IP address of the Security Manager server. This information is used to ensure that the topology generated by MARS represents all network connections for the Security Manager server. It is also used to calculate possible attack paths that might include the Security Manager server.
Step 5
Click Apply to save these settings.
Step 6
Click Next to access the Reporting Applications tab.
Step 7
Select the Cisco Security Manager ANY from the Select Application list, and click Add.
Step 8
If you entered an address in the Access IP field on the host that represents this Security Manager server, specify values for the following fields:
•
User Name— Identifies the Cisco Security Manager administrative account to be used to discover configuration settings.
•
Password — Identifies the password associated with the User Name account.
•
Access Type — This value identifies the protocol used to discover configuration information. Select HTTPS.
•
Access Port — The default access port for HTTPS is port 443.
Step 9
(Optional) To verify that the settings are correct and that the MARS Appliance can communicate with this Security Manager server, click Test Connectivity.
Result: If the username and password are correct and the MARS Appliance is configured as an administrative host for the device, the "Connectivity successful." dialog box appears when the discovery operation completes. Otherwise, an error message appears, which you can click on the View Error link for more information.
Step 10
To add this device to the MARS database, click Submit.
Result: The submit operation records the changes in the database tables. However, it does not load the changes into working memory of the MARS Appliance. The activate operation loads submitted changes into working memory.
Step 11
Click Activate.
Result: Once the MARS Appliance is activated, it can query the Security Manager server to perform policy lookups.
Procedure for Invoking Cisco Security Manager Policy Table Lookup from Cisco Security MARS
Do the following steps to view a Cisco Security Manager policy table from the Cisco Security MARS:
Step 1
Log on to MARS as an Administrator or Security Analyst.
Step 2
Identify the incident or event to investigate.
In this procedure, and incident to investigate appears on the Recent Incidents section of the Dashboard, as shown in Figure 16-2.
Figure 16-2 Recent Incidents on MARS Summary Page
Step 3
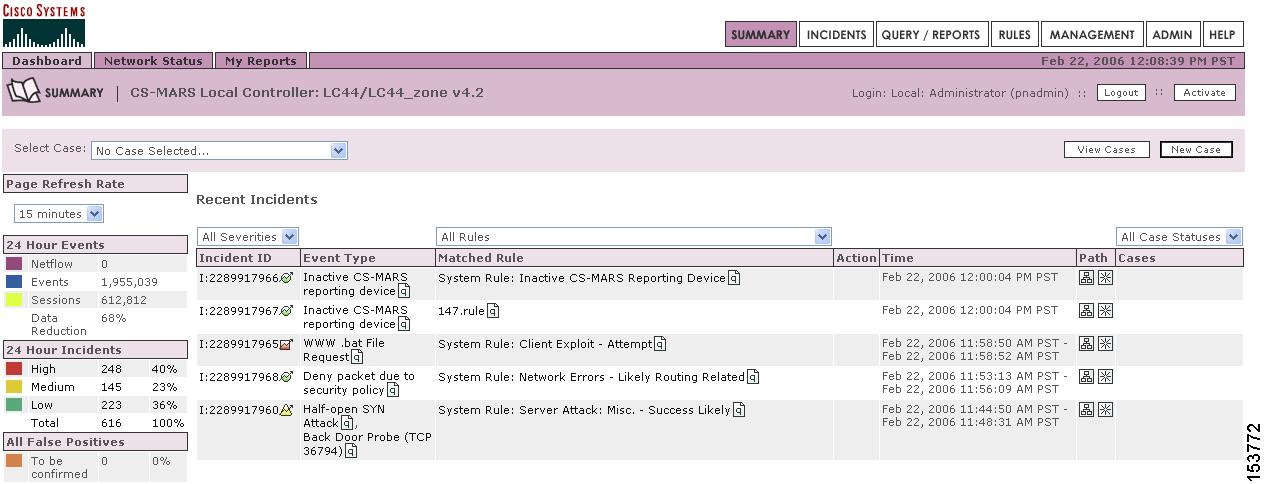
Click Incident ID of the incident to examine. The Incident Page appears as shown in Figure 16-3.
Figure 16-3 MARS Incident Page Displaying the Cisco Security Manager Icon in the
Reporting Device Field
Step 4
Click the Security Manager Policy Query icon in the Reporting Device field to invoke the
Security Manager policy table lookup. One of the following three pop-up windows may appear:–
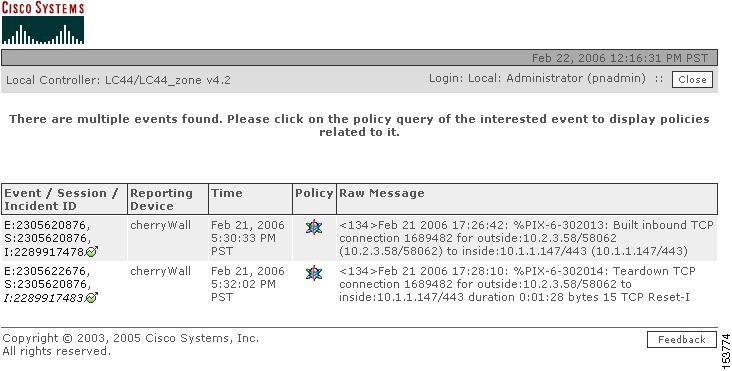
Multiple Events window— Lists all Security Manager device events in the session, this window appears in this step when there are two or more events in the session.
–
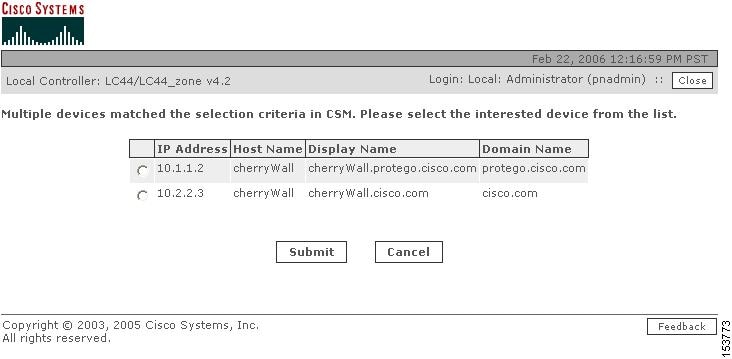
Multiple Devices window—Lists all matching Security Manager devices that meet criteria available to MARS, this window appears in this step when there are two or more matching devices.
–
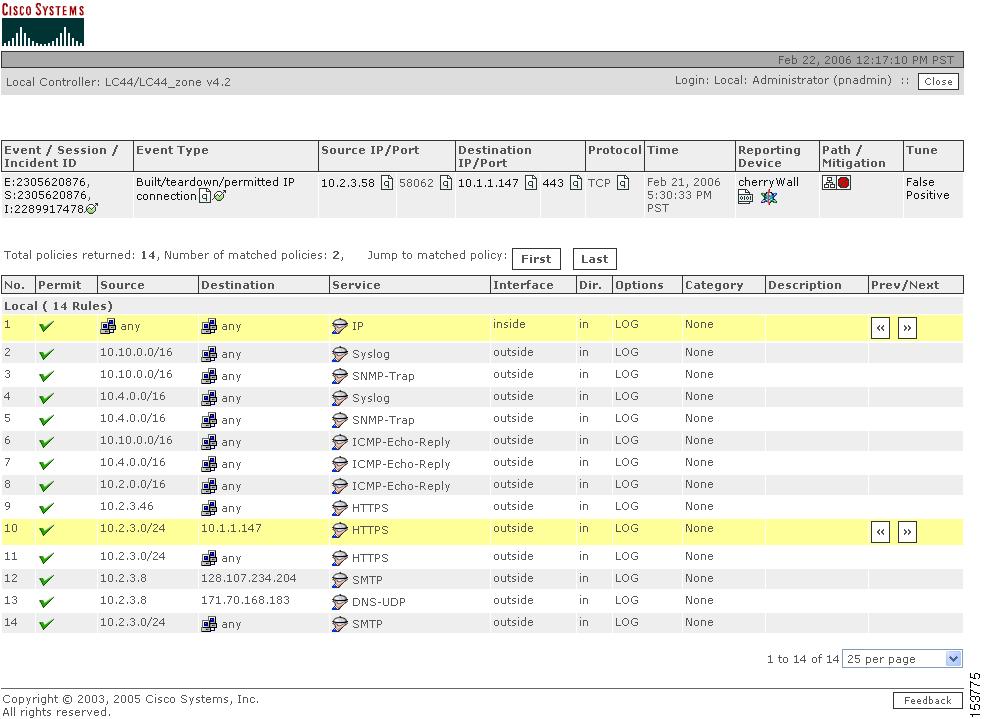
Policy Table window—Lists the policy table of the reporting device. Access rules that match the MARS criteria are highlighted, this window appears in this step when there is one event and a unique Security Manager device identified.
In this procedure, the Multiple Events window appears, as shown in Figure 16-4.
Figure 16-4 MARS Multiple Events Pop-up Window
Step 5
Click the Security Manager icon in the Policy field of the appropriate event. One of the following two pop-up windows may appear:
–
Multiple Devices window
–
Policy Table window
In this procedure the Multiple Device pop-up window is displayed, as shown in Figure 16-5.
Figure 16-5 MARS Multiple Devices Pop-up Window
Step 6
Click the radio button of the appropriate Security Manager Device. Click Submit. The Policy Table pop-up window appears for the selected device, as shown in Figure 16-6.
Figure 16-6 Policy Table Pop-up Window
Cisco Security Manager
The access rules that match the MARS query criteria appear in highlight. The access rules displayed in the Policy Table window are derived from the Security Manager committed view, not the deployed view. You must login to Security Manager or the specific device to examine or alter the access rule generating the MARS event or incident. If the committed and deployed views are identical, locating the policy is simplified. A MARS event can be generated from a deployed access rule not visible in the
committed view.Step 7
Login to Cisco Security Manager or the specific device to alter the security rule creating the MARS event.
This ends the Procedure for Accessing Cisco Security Manager Logs from Cisco Security MARS.
Note
Incidents, events, and sessions related to devices managed by Cisco Security Manager can also be viewed with an inline Query or a report.

 Feedback
Feedback