Table Of Contents
Policy Combining Algorithm and Obligation
Resource Group Policy Combining Algorithm
Policy Combining Algorithm and Obligation
This section explores how the PDP yields a single decision out of a combination of multiple entitlement policies on a single resource object using the policy combining algorithm (PCA) and gives a single result.
Policy Combining Algorithm
A policy is the core evaluation entity of the CEPM Access control. Policies are composed of rules. The result of executing the rules of policies can be combined using a Policy Combining Algorithm. A resource can have multiple user-based, role-based, and group-based policies.
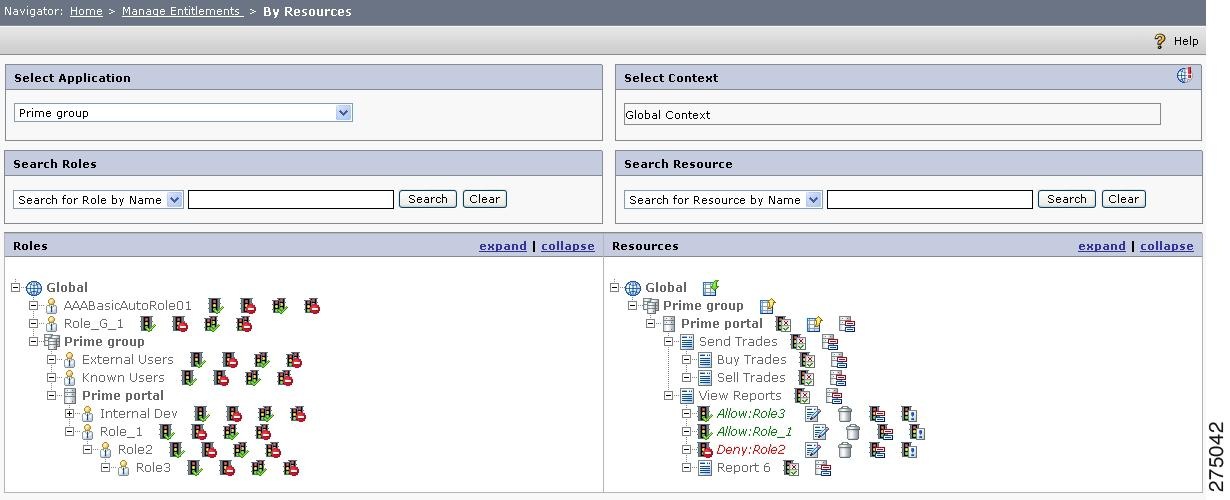
The PCA can be configured on an application or at the resource level of the resource tree. The PCA decides the outcome in situations where multiple policies are created on a resource for the same user/group/role. Consider the following sample resource-based entitlement:
Figure A-1
Resource-based Entitlement
In Resource-based Entitlement Role1 and Role3 have Allow policies on the View Reports and Role2 has a Deny policy on the same resource. Now, if a user Mary who belongs to all roles, Role1, Role2, and Role3 requests for Resource2, then the result of executing all the policies is Deny or Allow
These kinds of complex situations multiple policies on a single resource object can be resolved by imposing appropriate PCA on the requested resource object.
Decision can be Permit, Deny, Not Applicable, or Indeterminate.
Note
Not Applicable Toggle: This functionality comes into effect when a policy has a rule and that rule evaluates to False. If a resource has a Permit policy and while evaluating, the rule configured on that policy returns False, the decision would be "Not Applicable". For example, if Role1 has Allow policy on View Reports, but the rule does not satisfy, the resultant policy evaluation will be "Not Applicable" if "Not Applicable Toggle" is checked in the "Edit Policy" pop-up window. If this option is unchecked, the decision result will be Deny.
CEPM supports six policy combining algorithm out of which some are from the XACML 2.0 core specification and some are Cisco's own PCAs. For example, Deny-overrides, Permit-overrides, First-applicable, and Only-one-applicable are adapted from XACML 2.0. Lower-role-overrides and User-based-overrides are Cisco's own PCA.
1.
Deny-overrides:
When this algorithm is selected for a specified resource object, if one of the policies evaluates to Deny, then the PDP gives the decision as Deny irrespective of an Allow policy configured for the same user.
Table A-1 illustrates the possible scenarios, when Deny-overrides is selected as the PCA on a resource:
2.
Permit-Overrides:
This algorithm is similar to Deny-Overrides. An Allow policy on the resource will override all the deny policies. illustrates the possible scenarios, when Permit-overrides is selected as the PCA on a resource:
3.
First-Applicable:
This algorithm arrives at a decision based on the first policy configured on the requested resource.
For example, in resource-based entitlement (see Resource-based Entitlement), assuming that "Allow:Role1" policy has been created at the first instance, the PDP gives Allow decision for Mary to access View Trades until the rule evaluation returns false.
Note
If the first policy on the resource is `Not Applicable', it would consider the immediate policy configured on the same resource.
4.
Only-One-Applicable:
The PDP retains the decision of the evaluation of the sole policy configured on the resource object. If there is more than one policy on a resource and Only-one-applicable is selected as the PCA on that resource, the PDP will evaluate the request as Indeterminate.
5.
Lower-Role-Overrides:
This algorithm, if imposed on a resource object, picks up the policy configured on the lowest role in the role hierarchy.
For example, in resource-based entitlement (see Resource-based Entitlement), if you see the roles tree viewed in the Roles table (in the left), Role3 is the lowest role in the hierarchy and Role3 has an Allow policy defined on View Trades. The PDP evaluates the request to Allow unless and until the rule evaluation returns false.
6.
User-Based-Overrides:
When this algorithm is set on a resource object, the PDP while addressing the access request, searches for a user-based policy among the multiple policies configured on that specified resource. If the PDP finds a user-based policy, the PDP sends a response accordingly. In case there is no user-based policy, the PDP sends the response as Not Applicable.
For example, in resource based entitlement (see Resource-based Entitlement), if there is a policy called Allow:Mary on the View Trades, the PDP gives a decision as Allow. If Mary has a deny policy (as Deny:Mary), the decision would be Deny. If there is no user-based policy for Mary on that resource, the PDP sends the response as Not Applicable.
7.
Select-as a PCA:
The Superuser has the option of imposing a default PCA on any of the resource object. If the object is an application, it should be Deny-Overrides whereas for a resource, the Superuser must choose Select as the PCA. When Select is chosen, the PDP gives a decision based on the PCA set on the immediate parent resource of the resource in question. In case the parent resource follows the suit, it extends the search for a PCA to one level up until it reaches the application. If the application has a PCA, the PDP considers it and evaluate the policy based on that PCA. If not, it considers the Deny-Overrides.
For example, the resource with the FQN as Prime group:Prime portal:View Reports:Report6 (see Resource-based Entitlement). Set -Select- as the PCA on Report6. When a user request to access Report6 reaches the PDP, the PDP checks the PCA imposed on Report6. The concerned resource does not have a PCA and the PDP tries to evaluate the request-based on the PCA configured on the immediate parent resource of Report6, View Reports. If the latter is having a PCA, the PDP gives the decision accordingly. In case of absence of PCA on View Reports, the PDP extends the search for a PCA to the application level, such a s on the Prime portal. If the Prime portal has a PCA, the PDP evaluates the request according to the PCA set on the application. In case the Prime portal does not have a PCA, the PDP considers Deny-Overrides as the default PCA at application level and thus for Report6.
Resource Group Policy Combining Algorithm
If the PDP yields multiple decisions for a resource object due to its memberships across multiple resource groups, the PDP checks the Resource Group Policy Combining Algorithm (RGPCA) set on that resource and gives a single decision.
Similar to Policy Combining Algorithm, CEPM supports six Resource Group Policy Combining Algorithm such as Deny-overrides, Permit-overrides, First-applicable, and Only-one-applicable are adapted from XACML 2.0, Lower-role-overrides and User-based-overrides are Cisco's own PCA.
The Resource Group Policy Combining Algorithms types work the same way as in case of the Policy Combining Algorithms.
Note
Deny-overrides is set as the default RGPCA. When there is no RGPCA selected for a resource, the PDP picks the Deny-overrides as the RGPCA and gives the decision as Deny.
Example - A resource called Report3 is a member of two resource groups, RGroup1 and RGroup2. User John has an Allow policy on RGroup1 and a Deny policy on RGroup2. When John tries to access Report3, the PDP checks the RGPCA of Report3 as there is a conflict of policies on RGroup1 and Rgroup2. If the RGPCA is Permit-overrides, it gives Allow decision for Report3 even though it has a deny policy due to the membership of RGroup2
Obligations
Obligation binds the PDP to limit its decision query up to the level of resources irrespective of the courses of action demanded in the PEP request. The three types of obligations can be set on a resource:
•
This Resource Entitlement only—The PDP gives a decision on the requested resource only if it has child resources. For example, if this particular obligation has been set on the resource called Send Trades and the PEP sends a request, such as Mary, Prime group:Prime portal:Send Trades, then the PDP takes the Send Trades into consideration to give a decision. The PDP's decision does not cover the child resources of the specified resource.
•
1-level of child resource entitlements—If this obligation is set on any resource, the PDP's decision will be extended up to one level of child resources. Considering the preceding example, if the resource Send Trade has five child resources and each child resource has few more subresources, the PDP will consider all the child resources and not their subresources.
•
Entitlements for all resources (Recursive)—If you set this obligation, the PDP gives a decision for all child resources and their subresources up to the leaf level of the selected resource in a recursive manner.

 Feedback
Feedback