Contents
- Configuring IEEE 802.1X Port-Based Authentication
- Finding Feature Information
- Prerequisites for Configuring IEEE 802.1X Port-Based Authentication
- Restrictions for IEEE 802.1X Port-Based Authentication
- IEEE 802.1X Port-Based Authentication Configuration Restrictions
- Upgrading from a Previous Software Release
- Information About IEEE 802.1X Port-Based Authentication
- IEEE 802.1X Device Roles
- IEEE 802.1X Authentication Initiation and Message Exchange
- IEEE 802.1X Authentication Process
- IEEE 802.1X Host Mode
- IEEE 802.1X Port Authorization States
- IEEE 802.1X--Conditional Logging
- IEEE 802.1X MIB Support
- How to Use IEEE 802.1X Port-Based Authentication
- Enabling IEEE 802.1X Authentication and Authorization
- Configuring the IEEE 802.1X Host Mode
- Enabling IEEE 802.1X SNMP Notifications on Switch Ports
- Configuration Examples for IEEE 802.1x Features
- Example: Enabling IEEE 802.1X and AAA on a Port
- Example: Configuring the IEEE 802.1X Host Mode
- Example: Displaying IEEE 802.1X Statistics and Status
- Additional References
- Feature Information for IEEE 802.1X Port-Based Authentication
Configuring IEEE 802.1X Port-Based Authentication
IEEE 802.1X port-based authentication is configured on the Cisco integrated services router (ISR) to prevent unauthorized devices (supplicants) from gaining access to the network. The ISR can combine the function of a router, switch, and access point, depending on the fixed configuration or installed modules. The switch functions are provided by either built-in switch ports or a plug-in module with switch ports.
- Finding Feature Information
- Prerequisites for Configuring IEEE 802.1X Port-Based Authentication
- Restrictions for IEEE 802.1X Port-Based Authentication
- Information About IEEE 802.1X Port-Based Authentication
- How to Use IEEE 802.1X Port-Based Authentication
- Configuration Examples for IEEE 802.1x Features
- Additional References
- Feature Information for IEEE 802.1X Port-Based Authentication
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the Feature Information Table at the end of this document.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for Configuring IEEE 802.1X Port-Based Authentication
The following tasks must be completed before implementing the IEEE 802.1X Port-Based Authentication feature:
- IEEE 802.1X must be enabled on the device port.
- The device must have a RADIUS configuration and be connected to the Cisco secure access control server (ACS). You should understand the concepts of the RADIUS protocol and have an understanding of how to create and apply access control lists (ACLs).
- EAP support must be enabled on the RADIUS server.
- You must configure the IEEE 802.1X supplicant to send an EAP-logoff (Stop) message to the switch when the user logs off. If you do not configure the IEEE 802.1X supplicant, an EAP-logoff message is not sent to the switch and the accompanying accounting Stop message is not sent to the authentication server. See the Microsoft Knowledge Base article at the location http://support.microsoft.com and set the SupplicantMode registry to 3 and the AuthMode registry to 1.
- Authentication, authorization, and accounting (AAA) must be configured on the port for all network-related service requests. The authentication method list must be enabled and specified. A method list describes the sequence and authentication method to be queried to authenticate a user. See the IEEE 802.1X Authenticator feature module for information.
- The port must be successfully authenticated.
The IEEE 802.1X Port-Based Authentication feature is available only on Cisco 800, 870, 1800, 2800, and 3800 series integrated switching routers (ISRs) that support switch ports.
The fixed-configuration Cisco 1800 series router platforms and the Cisco 870 series routers have integrated 4-port and 8-port switches.
The following cards or modules support switch ports:
 Note | Not all Cisco ISR routers support all the components listed. For information about module compatibility with a specific router platform, see Cisco EtherSwitch Modules Comparison. |
To determine whether your router has switch ports that can be configured with the IEEE 802.1X port-based authentication feature, use the show interfaces switchport command.
Restrictions for IEEE 802.1X Port-Based Authentication
- IEEE 802.1X Port-Based Authentication Configuration Restrictions
- Upgrading from a Previous Software Release
IEEE 802.1X Port-Based Authentication Configuration Restrictions
- The IEEE 802.1X Port-Based Authentication feature is available only on a Cisco ISR switch port.
- If the VLAN to which an IEEE 802.1X port is assigned is shut down, disabled, or removed, then the port becomes unauthorized. For example, the port is unauthorized after the access VLAN to which a port is assigned shuts down or is removed.
- When IEEE 802.1X authentication is enabled, ports are authenticated before any other Layer 2 or Layer 3 features are enabled.
- If you try to change the mode (for example, from access to trunk) of an IEEE 802.1X-enabled port, an error message appears, and the port mode is not changed.
- Changes to a VLAN to which an IEEE 802.1X-enabled port is assigned are transparent and do not affect the switch port. For example, a change occurs if a port is assigned to a RADIUS server-assigned VLAN and is then assigned to a different VLAN after reauthentication.
- When IEEE 802.1X authentication is enabled on a port, you cannot configure a port VLAN that is equal to a voice VLAN.
- This feature does not support standard ACLs on the switch port.
- The IEEE 802.1X protocol is supported on Layer 2 static-access ports, voice VLAN-enabled ports, and Layer 3 routed ports, but it is not supported on the following port types:
- Dynamic-access ports--If you try to enable IEEE 802.1X authentication on a dynamic-access (VLAN Query Protocol [VQP]) port, an error message appears, and IEEE 802.1X authentication is not enabled. If you try to change an IEEE 802.1X-enabled port to dynamic VLAN assignment, an error message appears, and the VLAN configuration is not changed.
- Dynamic ports--If you try to enable IEEE 802.1X authentication on a dynamic port, an error message appears, and IEEE 802.1X authentication is not enabled. If you try to change the mode of an IEEE 802.1X-enabled port to dynamic, an error message appears, and the port mode is not changed.
- Switched Port Analyzer (SPAN) and Remote SPAN (RSPAN) destination ports--You can enable IEEE 802.1X authentication on a port that is a SPAN or RSPAN destination port. However, IEEE 802.1X authentication is disabled until the port is removed as a SPAN or RSPAN destination port. You can enable IEEE 802.1X authentication on a SPAN or RSPAN source port.
- Trunk port--If you try to enable IEEE 802.1X authentication on a trunk port, an error message appears, and IEEE 802.1X authentication is not enabled. If you try to change the mode of an IEEE 802.1X-enabled port to trunk, an error message appears, and the port mode is not changed.
 Note | A port in dynamic mode can negotiate with its neighbor to become a trunk port. |
- Configuring the same VLAN ID for both access and voice traffic (using the switchport access vlan vlan-id and the switchport voice vlan vlan-id commands) will fail if authentication has already been configured on the port.
- Configuring authentication on a port on which you have already configured switchport access vlan vlan-id and switchport voice vlan vlan-id will fail if the access VLAN and voice VLAN have been configured with the same VLAN ID.
Upgrading from a Previous Software Release
In Cisco IOS Release 12.4(11)T, the implementation for IEEE 802.1X authentication changed from the previous releases. When IEEE 802.1X authentication is enabled, information about Port Fast is no longer added to the configuration.
 Note | Information about any IEEE 802.1X-related commands entered on a port is automatically added to the running configuration to address any backward compatibility issues: dot1xpae authenticator. |
Information About IEEE 802.1X Port-Based Authentication
- IEEE 802.1X Device Roles
- IEEE 802.1X Authentication Initiation and Message Exchange
- IEEE 802.1X Authentication Process
- IEEE 802.1X Host Mode
- IEEE 802.1X Port Authorization States
- IEEE 802.1X--Conditional Logging
- IEEE 802.1X MIB Support
IEEE 802.1X Device Roles
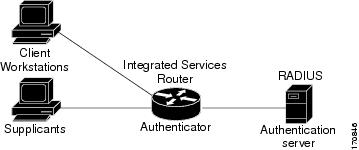
With IEEE 802.1X authentication, the devices in the network have specific roles as shown in the figure below.
- Supplicant--Device (workstation) that requests access to the LAN and switch services and responds to requests from the router. The workstation must be running IEEE 802.1X-compliant client software such as that offered in the Microsoft Windows XP operating system. (The supplicant is sometimes called the client.)
 Note | To resolve Windows XP network connectivity and IEEE 802.1X authentication issues, read the Microsoft Knowledge Base article at this URL: http://support.microsoft.com/kb/q303597/ |
- Authentication server--Device that performs the actual authentication of the supplicant. The authentication server validates the identity of the supplicant and notifies the router whether or not the supplicant is authorized to access the LAN and switch services. The Network Access Device (or ISR router in this instance) transparently passes the authentication messages between the supplicant and the authentication server, and the authentication process is carried out between the supplicant and the authentication server. The particular EAP method used will be decided between the supplicant and the authentication server (RADIUS server). The RADIUS security system with EAP extensions is available in Cisco Secure Access Control Server Version 3.0 or later. RADIUS operates in a client and server model in which secure authentication information is exchanged between the RADIUS server and one or more RADIUS clients.
- Authenticator (integrated services router (ISR) or wireless access point)--Router that controls the physical access to the network based on the authentication status of the supplicant. The router acts as an intermediary between the supplicant and the authentication server, requesting identity information from the supplicant, verifying that information with the authentication server, and relaying a response to the supplicant. The router includes the RADIUS client, which is responsible for encapsulating and decapsulating the EAP frames and interacting with the authentication server.
When the authenticator receives EAPOL frames and relays them to the authentication server, the EAPOL is stripped and the remaining EAP frame is reencapsulated in the RADIUS format. The EAP frames are not modified during encapsulation, and the authentication server must support EAP within the native frame format. When the authenticator receives frames from the authentication server, the server's frame header is removed, leaving the EAP frame, which is then encapsulated for Ethernet and sent to the client.
IEEE 802.1X Authentication Initiation and Message Exchange
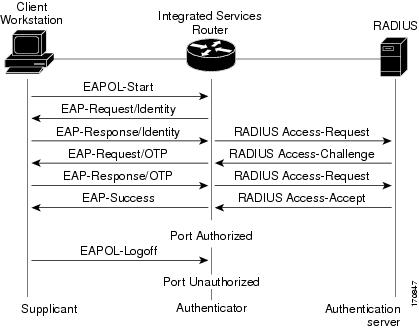
During IEEE 802.1X authentication, the router or the supplicant can initiate authentication. If you enable authentication on a port by using the dot1x port-control auto interface configuration command, the router initiates authentication when the link state changes from down to up or periodically if the port remains up and unauthenticated. The router sends an EAP-request/identity frame to the supplicant to request its identity. Upon receipt of the frame, the supplicant responds with an EAP-response/identity frame.
However, if during bootup the supplicant does not receive an EAP-request/identity frame from the router, the supplicant can initiate authentication by sending an EAPOL-start frame, which prompts the router to request the supplicant's identity.
When the supplicant supplies its identity, the router begins its role as the intermediary, passing EAP frames between the supplicant and the authentication server until authentication succeeds or fails. If the authentication succeeds, the router port becomes authorized. If the authentication fails, authentication can be retried, the port might be assigned to a VLAN that provides limited services, or network access is not granted. For more information, see the Ports in Authorized and Unauthorized States module.
The specific exchange of EAP frames depends on the authentication method being used. The figure below shows a message exchange initiated by the supplicant using the One-Time-Password (OTP) authentication method with a RADIUS server.
IEEE 802.1X Authentication Process
To configure IEEE 802.1X port-based authentication, you must enable authentication, authorization, and accounting (AAA) and specify the authentication method list. A method list describes the sequence and authentication method to be queried to authenticate a user.
The AAA process begins with authentication. When IEEE 802.1X port-based authentication is enabled and the device attempting to authenticate is IEEE 802.1x-capable (meaning it supports the supplicant functionality), this event occurs:
- If the supplicant identity is valid and the IEEE 802.1X authentication succeeds, the router grants the supplicant access to the network.
The router reauthenticates a supplicant when this situation occurs:
You can configure the reauthentication timer to use a router-specific value or to be based on values from the RADIUS server.
After IEEE 802.1X authentication using a RADIUS server is configured, the router uses timers based on the Session-Timeout RADIUS attribute (Attribute [27]) and the Termination-Action RADIUS attribute (Attribute [29]).
The Session-Timeout RADIUS attribute (Attribute [27]) specifies the time after which reauthentication occurs.
The Termination-Action RADIUS attribute (Attribute [29]) specifies the action to take during reauthentication. The actions can be Initialize or ReAuthenticate. When the Initialize action is set (the attribute value is DEFAULT ), the IEEE 802.1x session ends, and connectivity is lost during reauthentication. When the ReAuthenticate action is set (the attribute value is RADIUS-Request), the session is not affected during reauthentication.
You manually reauthenticate the supplicant by entering the dot1x re-authenticate interface interface-id privileged EXEC command.
IEEE 802.1X Host Mode
You can configure an IEEE 802.1X port for single-host or for multihost mode. In single-host mode (see the figure IEEE 802.1X Device Roles in the Device Roles section of this module), only one supplicant can be authenticated by the IEEE 802.1X-enabled switch port. The router detects the supplicant by sending an EAPOL frame when the port link state changes to the up state. If a supplicant leaves or is replaced with another supplicant, the router changes the port link state to down, and the port returns to the unauthorized state.
In multihost mode, you can attach multiple hosts to a single IEEE 802.1X-enabled port. In this mode, only one of the attached supplicants must be authorized for all supplicants to be granted network access. If the port becomes unauthorized (reauthentication fails or an EAPOL-logoff message is received), the router denies network access to all of the attached supplicants.
 Note | Cisco 870 series platforms do not support single-host mode. |
IEEE 802.1X Port Authorization States
During IEEE 802.1X authentication, depending on the port state, the router can grant a supplicant access to the network. The port starts in the unauthorized state. While in this state, the port that is not configured as a voice VLAN port disallows all ingress traffic except for IEEE 802.1X authentication, Cisco Discovery Protocol (CDP), and STP packets. When a supplicant is successfully authenticated, the port changes to the authorized state, allowing all traffic for the supplicant to flow normally. If the port is configured as a voice VLAN port, the port allows VoIP traffic and IEEE 802.1X protocol packets before the supplicant is successfully authenticated.
If a client that does not support IEEE 802.1X authentication connects to an unauthorized IEEE 802.1X port, then the router requests the client's identity. In this situation, if the client does not respond to the request, the port remains in the unauthorized state, and the client is not granted access to the network.
In contrast, when an IEEE 802.1X-enabled supplicant connects to a port that is not running the IEEE 802.1X standard, the supplicant initiates the authentication process by sending the EAPOL-start frame. When no response is received, the supplicant sends the request for a fixed number of times. Because no response is received, the supplicant begins sending frames as if the port is in the authorized state.
If the supplicant is successfully authenticated (receives an Accept frame from the authentication server), the port state changes to authorized, and all frames from the authenticated supplicant are allowed through the port. If the authentication fails, the port remains in the unauthorized state, but authentication can be retried. If the authentication server cannot be reached, the router can resend the request. If no response is received from the server after the specified number of attempts, authentication fails, and network access is not granted.
When a supplicant logs off, it sends an EAPOL-logoff message, causing the router port to change to the unauthorized state.
If the link state of a port changes from up to down, or if an EAPOL-logoff frame is received, the port returns to the unauthorized state.
IEEE 802.1X--Conditional Logging
Use the IEEE 802.1X--Conditional Logging feature for troubleshooting. When the Conditional Logging feature is enabled, the router generates debugging messages for packets entering or leaving the router on a specified interface; the router will not generate debugging output for packets entering or leaving through a different interface. You can specify the interfaces explicitly. For example, you may want to see only debugging messages for one interface or subinterface. You can also turn on debugging for all interfaces that meet the configured condition. This feature is useful on dial access servers, which have a large number of ports.
Normally, the router will generate debugging messages for every interface, resulting in a large number of messages. The large number of messages consumes system resources, and can affect your ability to find the specific information you need. By limiting the number of debugging messages, you can receive messages related to only the ports you want to troubleshoot.
For more information on conditional logging and enabling conditionally triggered debugging, see the "Enabling Conditionally Triggered Debugging" section of the "Troubleshooting and Fault Management" chapter in the Basic System Management Configuration Guide.
IEEE 802.1X MIB Support
Cisco IOS Release 12.4(11)T provides support for the following MIBs that provide SNMP access to IEEE 802.1X feature components:
The IEEE8021-PAE-MIB supports reporting of the following information:
- The state of the IEEE 802.1X state machine on a particular port
- Statistics associated with the state of the IEEE 802.1X state machine
The Cisco-PAE-MIB provides SNMP support for the logging and reporting of events, including:
How to Use IEEE 802.1X Port-Based Authentication
- Enabling IEEE 802.1X Authentication and Authorization
- Configuring the IEEE 802.1X Host Mode
- Enabling IEEE 802.1X SNMP Notifications on Switch Ports
Enabling IEEE 802.1X Authentication and Authorization
- auto --Enables IEEE 802.1X authentication and causes the port to begin in the unauthorized state, allowing only EAPOL frames to be sent and received through the port. The authentication process begins when the link state of the port changes from down to up or when an EAPOL-start frame is received. The router requests the identity of the supplicant and begins relaying authentication messages between the supplicant and the authentication server. Each supplicant attempting to access the network is uniquely identified by the router by using the supplicant MAC address.
- force-authorized ---Disables IEEE 802.1X authentication and causes the port to change to the authorized state without any authentication exchange required. The port sends and receives normal traffic without IEEE 802.1X-based authentication of the client. This is the default setting.
- force-unauthorized --Causes the port to remain in the unauthorized state, ignoring all attempts by the supplicant to authenticate. The router cannot provide authentication services to the supplicant through the port.
DETAILED STEPS
Configuring the IEEE 802.1X Host Mode
- The multi-auth keyword specifies multiple authentications to occur on the 802.1X-authorized port.
- The multi-domain keyword specifies multi-domain authentication (MDA), which is used to enable authentication of both a host and a voice device, such as an IP phone (Cisco or non-Cisco) on the same switch port.
- The multi-host keyword specifies multiple hosts on the 802.1X-authorized port.
- The single-host keyword specifies a single client on the 802.1X-authorized port.
- (Optional) The open keyword specifies that the port is open; that is, there are no access restrictions.
DETAILED STEPS
Enabling IEEE 802.1X SNMP Notifications on Switch Ports
DETAILED STEPS
Configuration Examples for IEEE 802.1x Features
- Example: Enabling IEEE 802.1X and AAA on a Port
- Example: Configuring the IEEE 802.1X Host Mode
- Example: Displaying IEEE 802.1X Statistics and Status
Example: Enabling IEEE 802.1X and AAA on a Port
This example shows how to enable IEEE 802.1X and AAA on Fast Ethernet port 2/1, and how to verify the configuration:
Router# configure terminal Router(config)# dot1x system-auth-control Router(config)# aaa new-model Router(config)# aaa authentication dot1x default group radius Router(config)# interface fastethernet2/1 Router(config-if)# switchport mode access Router(config-if)# dot1x pae authenticator Router(config-if)# dot1x port-control auto Router(config-if)# end Router# show dot1x interface fastethernet7/1 details Dot1x Info for FastEthernet7/1 ----------------------------------- PAE = AUTHENTICATOR PortControl = AUTO ControlDirection = Both HostMode = SINGLE_HOST ReAuthentication = Disabled QuietPeriod = 60 ServerTimeout = 30 SuppTimeout = 30 ReAuthPeriod = 3600 (Locally configured) ReAuthMax = 2 MaxReq = 2 TxPeriod = 30 RateLimitPeriod = 0 Dot1x Authenticator Client List ------------------------------- Supplicant = 1000.0000.2e00 Auth SM State = AUTHENTICATED Auth BEND SM Stat = IDLE Port Status = AUTHORIZED Authentication Method = Dot1x Authorized By = Authentication Server Vlan Policy = N/A
Example: Displaying IEEE 802.1X Statistics and Status
- To display IEEE 802.1X statistics for all ports, use the show dot1x all statistics privileged EXEC command.
- To display IEEE 802.1X statistics for a specific port, use the show dot1x status interface interface-id privileged EXEC command.
- To display the IEEE 802.1X administrative and operational status for the switch, use the show dot1x all [details | statistics | summary]] privileged EXEC command.
- To display the IEEE 802.1X administrative and operational status for a specific port, use the show dot1x interface interface-id privileged EXEC command. For detailed information about the fields in these displays, see the command reference for this release.
The following example displays show dot1x all command output:
Device# show dot1x all
Sysauthcontrol Enabled
Dot1x Protocol Version 2
Dot1x Info for FastEthernet1
-----------------------------------
PAE = AUTHENTICATOR
PortControl = AUTO
ControlDirection = Both
HostMode = MULTI_HOST
ReAuthentication = Disabled
QuietPeriod = 60
ServerTimeout = 30
SuppTimeout = 30
ReAuthPeriod = 3600 (Locally configured)
ReAuthMax = 2
MaxReq = 2
TxPeriod = 30
RateLimitPeriod = 0
Router-871#
The following example displays show dot1x summary command output:
Router-871# show dot1x all summary
Interface PAE Client Status
------------------------------------------------------------------------------------------
Fa1 AUTH 000d.bcef.bfdc AUTHORIZED
Additional References
MIBs
Technical Assistance
|
Description |
Link |
|---|---|
|
The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password. |
Feature Information for IEEE 802.1X Port-Based Authentication
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
| Table 1 | Feature Information for IEEE 802.1X Port-Based Authentication |
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.

 Feedback
Feedback