Contents
- Configuring FlexVPN Spoke to Spoke
- Finding Feature Information
- Prerequisites for FlexVPN Spoke to Spoke
- Information About FlexVPN Spoke to Spoke
- FlexVPN and NHRP
- NHRP Resolution Request and Reply in FlexVPN
- How to Configure FlexVPN Spoke to Spoke
- Configuring the Virtual Tunnel Interface on FlexVPN Server
- Configuring NHRP Shortcuts on FlexVPN Spoke
- Configuring the Virtual Tunnel Interface on FlexVPN Spoke
- Configuration Examples for FlexVPN Spoke to Spoke
- Example: Configuring FlexVPN Spoke to Spoke with Static Routing
- Example: Configuring FlexVPN Spoke to Spoke with Dynamic Routing using BGP
- Additional References
- Feature Information for FlexVPN Spoke to Spoke
Configuring FlexVPN Spoke to Spoke
The FlexVPN Spoke to Spoke feature enables a FlexVPN client to establish a direct crypto tunnel with another FlexVPN client leveraging virtual tunnel interfaces (VTI), Internet Key Exchange Version 2 (IKEv2) and Next Hop Resolution Protocol (NHRP) to build spoke-to-spoke connections.
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for FlexVPN Spoke to Spoke
IKEv2, the FlexVPN server, and the FlexVPN spoke must be configured.
Information About FlexVPN Spoke to Spoke
FlexVPN and NHRP
FlexVPN is Cisco's implementation of the IKEv2 standard featuring a unified paradigm and CLI that combines site to site, remote access, hub and spoke topologies and partial meshes (spoke to spoke direct). FlexVPN offers a simple but modular framework that extensively uses the tunnel interface paradigm while remaining compatible with legacy VPN implementations using the crypto maps.
The FlexVPN server provides the server side functionality of FlexVPN. The FlexVPN client establishes a secure IPsec VPN tunnel between a FlexVPN client and another FlexVPN server.
NHRP is an Address Resolution Protocol (ARP)-like protocol that alleviates nonbroadcast multiaccess (NBMA) network problems. With NHRP, NHRP entities attached to an NBMA network dynamically learn the NBMA address of the other entities that are part of that network, allowing these entities to directly communicate without requiring traffic to use an intermediate hop.
The FlexVPN Spoke to Spoke feature integrates NHRP and FlexVPN client (spoke) to establish a direct crypto channel with another client in an existing FlexVPN network. The connections are built using virtual tunnel interfaces (VTI), IKEv2 and NHRP, where NHRP is used for resolving the FlexVPN clients in the network.
NHRP Resolution Request and Reply in FlexVPN
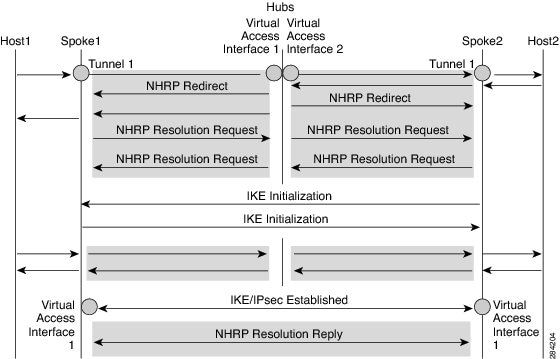
The following diagram illustrates the NHRP resolution request and reply in FlexVPN.
Due to bidirectional traffic, similar events occur in both directions at Spoke1, Spoke2, and hub. For clarity, events from Host1 to Host2 are discussed. Assume that there is a network N1 (192.168.1.0/24) behind Spoke1 and another network N2 (192.168.2.0/24) behind Spoke2. The network between the two spokes is matched through an Access Control List (ACL). This is because ACLs are applied on the IKEv2 policies on both spokes.
The network along with its prefix information from both the spokes is conveyed to the hub via IKEv2 information payload exchanges. This causes a route addition in the routing table by IKEv2 at the hub as follows:
- 192.168.1.0/24--Connected via virtual access interface1
- 192.168.2.0/24--Connected via virtual access interface2
The hub will push a summarized route via IKEv2 to both spokes, and the spokes will install the route in their routing table as follows:
 Note | The routing protocol can also add the route to the routing table. |
Assuming that traffic moves from N1 to N2, the traffic flow is as follows:
- Host1 sends traffic destined to Host2. The traffic reaches the LAN interface of spoke1, looks up the route, hits the summarized route, and routes the packet to interface tunnel 1.
- When the traffic reaches the hub's virtual access interface1, the traffic looks up the route table for a route entry for N2, either directly connected over virtual access interface 2 or via a point-to-point tunnel interface.
- The traffic from Host1 to Host2 traverses the hub through virtual access interface1 and virtual access interface2. The hub determines that ingress and the egress interfaces (virtual access interface1 and virtual access interface2) belong to same NHRP network (network D configured on both the interfaces). The hub sends out an NHRP redirect message to spoke1 on virtual access interface1.
- On receiving the redirect, Spoke1 initiates a resolution request for Host2 over the point-to-point tunnel interface (the same interface over which it received the redirect). The resolution request traverses the routed path (Spoke1-hub-spoke2). On receiving the resolution request, Spoke2 determines that it is the exit point and needs to respond to the resolution request.
- Spoke2 receives the resolution request on the tunnel interface and retrieves the virtual template number from the tunnel interface. The virtual template number is used to create the virtual access interface to start a crypto channel and establishes IKEv2 and IPsec security associations (SAs). Once the crypto SAs between the two spokes are up, Spoke2 installs the necessary NHRP cache entries for Spoke1 and its network under the newly created virtual access interface and sends out the resolution reply over the virtual access interface.
- After receiving the resolution request over the virtual access interface, Spoke1 installs the necessary cache entries for Spoke2 and its network. Spoke1 also deletes the temporary cache entry pointing to the hub to resolve the network under tunnel interface1.
- NHRP adds shortcut routes as next-hop override (NHO) or H route. For more information on shortcut switching, refer to Shortcut Switching Enhancements for NHRP in DMVPN Networks.
How to Configure FlexVPN Spoke to Spoke
- Configuring the Virtual Tunnel Interface on FlexVPN Server
- Configuring NHRP Shortcuts on FlexVPN Spoke
- Configuring the Virtual Tunnel Interface on FlexVPN Spoke
Configuring the Virtual Tunnel Interface on FlexVPN Server
DETAILED STEPS
Configuring NHRP Shortcuts on FlexVPN Spoke
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
Step 1 |
enable
Example: Device> enable |
Enables privileged EXEC mode. |
Step 2 |
configure terminal
Example: Device# configure terminal |
Enters global configuration mode. |
Step 3 |
interface tunnel
number
Example: Device(config)# interface tunnel 1 |
Configures the FlexVPN client interface and enters interface configuration mode. |
Step 4 |
ip nhrp shortcut
virtual-template-number
Example: Device(config-if)# ip nhrp shortcut 1 |
Enables NHRP shortcuts on the FlexVPN client tunnel interface. This is necessary to establish spoke-to-spoke tunnels. The virtual-template number specified in this configuration and the virtual-template number specified in the Configuring the Virtual Tunnel Interface on FlexVPN Client task must be same. |
Step 5 |
exit
Example: Device(config-if)# exit |
Exits interface configuration mode and returns to global configuration mode. |
Configuring the Virtual Tunnel Interface on FlexVPN Spoke
DETAILED STEPS
Configuration Examples for FlexVPN Spoke to Spoke
- Example: Configuring FlexVPN Spoke to Spoke with Static Routing
- Example: Configuring FlexVPN Spoke to Spoke with Dynamic Routing using BGP
Example: Configuring FlexVPN Spoke to Spoke with Static Routing
The following example shows how to configure FlexVPN spoke to spoke with IKE-propagated static routing on FlexVPN server and FlexVPN client. The following is the configuration on the FlexVPN server:
hostname hub ! crypto ikev2 authorization policy default pool flex-pool def-domain cisco.com route set interface route set access-list flex-route ! crypto ikev2 profile default match identity remote fqdn domain cisco.com identity local fqdn hub.cisco.com authentication local rsa-sig authentication remote rsa-sig pki trustpoint CA aaa authorization group cert list default default virtual-template 1 ! crypto ipsec profile default set ikev2-profile default ! interface Loopback0 ip address 172.16.1.1 255.255.255.255 ! interface Ethernet0/0 ip address 10.0.0.100 255.255.255.0 ! interface Virtual-Template1 type tunnel ip unnumbered Loopback0 ip nhrp network-id 1 ip nhrp redirect tunnel protection ipsec profile default ! ip local pool flex-pool 172.16.0.1 172.16.0.254 ! ip access-list standard flex-route permit any
The following is the configuration on the first FlexVPN client:
hostname spoke1 ! crypto ikev2 authorization policy default route set interface route set access-list flex-route ! crypto ikev2 profile default match identity remote fqdn domain cisco.com identity local fqdn spoke1.cisco.com authentication local rsa-sig authentication remote rsa-sig pki trustpoint CA aaa authorization group cert list default default virtual-template 1 ! crypto ipsec profile default set ikev2-profile default ! interface Tunnel0 ip address negotiated ip nhrp network-id 1 ip nhrp shortcut virtual-template 1 ip nhrp redirect tunnel source Ethernet0/0 tunnel destination 10.0.0.100 tunnel protection ipsec profile default ! interface Ethernet0/0 ip address 10.0.0.110 255.255.255.0 ! interface Ethernet1/0 ip address 192.168.110.1 255.255.255.0 ! interface Virtual-Template1 type tunnel ip unnumbered Tunnel0 ip nhrp network-id 1 ip nhrp shortcut virtual-template 1 ip nhrp redirect tunnel protection ipsec profile default ! ip access-list standard flex-route permit 192.168.110.0 0.0.0.255
The following is the configuration on the second FlexVPN client:
hostname spoke2 ! crypto ikev2 authorization policy default route set interface route set access-list flex-route ! crypto ikev2 profile default match identity remote fqdn domain cisco.com identity local fqdn spoke2.cisco.com authentication local rsa-sig authentication remote rsa-sig pki trustpoint CA aaa authorization group cert list default default virtual-template 1 ! crypto ipsec profile default set ikev2-profile default ! interface Tunnel0 ip address negotiated ip nhrp network-id 1 ip nhrp shortcut virtual-template 1 ip nhrp redirect tunnel source Ethernet0/0 tunnel destination 10.0.0.100 tunnel protection ipsec profile default ! interface Ethernet0/0 ip address 10.0.0.120 255.255.255.0 ! interface Ethernet1/0 ip address 192.168.120.1 255.255.255.0 ! interface Virtual-Template1 type tunnel ip unnumbered Tunnel0 ip nhrp network-id 1 ip nhrp shortcut virtual-template 1 ip nhrp redirect tunnel protection ipsec profile default ! ip access-list standard flex-route permit 192.168.120.0 0.0.0.255
Example: Configuring FlexVPN Spoke to Spoke with Dynamic Routing using BGP
The following example shows how to configure FlexVPN spoke to spoke with dynamic routing, using BGP on FlexVPN server (with dynamic neighbor discovery) and FlexVPN client. The following is the configuration on the FlexVPN server:
hostname hub ! crypto ikev2 authorization policy default pool flex-pool def-domain cisco.com route set interface ! crypto ikev2 profile default match identity remote fqdn domain cisco.com identity local fqdn hub.cisco.com authentication local rsa-sig authentication remote rsa-sig pki trustpoint CA aaa authorization group cert list default default virtual-template 1 ! crypto ipsec profile default set ikev2-profile default ! interface Loopback0 ip address 172.16.1.1 255.255.255.255 ! interface Ethernet0/0 ip address 10.0.0.100 255.255.255.0 ! interface Virtual-Template1 type tunnel ip unnumbered Loopback0 ip nhrp network-id 1 ip nhrp redirect tunnel protection ipsec profile default ! ip local pool flex-pool 172.16.0.1 172.16.0.254 ! router bgp 65100 bgp router-id 10.0.0.100 bgp log-neighbor-changes bgp listen range 172.16.0.0/24 peer-group spokes neighbor spokes peer-group neighbor spokes remote-as 65100 neighbor spokes transport connection-mode passive neighbor spokes update-source Loopback0 ! address-family ipv4 neighbor spokes activate neighbor spokes default-originate neighbor spokes prefix-list no-default in exit-address-family ! ip prefix-list no-default seq 5 deny 0.0.0.0/0 ip prefix-list no-default seq 10 permit 0.0.0.0/0 le 32
The following is the configuration on the first FlexVPN client:
hostname spoke1 ! crypto ikev2 authorization policy default route set interface ! crypto ikev2 profile default match identity remote fqdn domain cisco.com identity local fqdn spoke1.cisco.com authentication local rsa-sig authentication remote rsa-sig pki trustpoint CA aaa authorization group cert list default default virtual-template 1 ! crypto ipsec profile default set ikev2-profile default ! interface Tunnel0 ip address negotiated ip nhrp network-id 1 ip nhrp shortcut virtual-template 1 ip nhrp redirect tunnel source Ethernet0/0 tunnel destination 10.0.0.100 tunnel protection ipsec profile default ! interface Ethernet0/0 ip address 10.0.0.110 255.255.255.0 ! interface Ethernet1/0 ip address 192.168.110.1 255.255.255.0 ! interface Virtual-Template1 type tunnel ip unnumbered Tunnel0 ip nhrp network-id 1 ip nhrp shortcut virtual-template 1 ip nhrp redirect tunnel protection ipsec profile default ! router bgp 65100 bgp router-id 10.0.0.110 bgp log-neighbor-changes neighbor hubs peer-group neighbor hubs remote-as 65100 neighbor hubs update-source Tunnel0 neighbor 172.16.1.1 peer-group hubs ! address-family ipv4 network 192.168.110.0 neighbor 172.16.1.1 activate exit-address-family
The following is the configuration on the second FlexVPN client:
hostname spoke2 ! crypto ikev2 authorization policy default route set interface route set access-list flex-route ! crypto ikev2 profile default match identity remote fqdn domain cisco.com identity local fqdn spoke2.cisco.com authentication local rsa-sig authentication remote rsa-sig pki trustpoint CA aaa authorization group cert list default default virtual-template 1 ! crypto ipsec profile default set ikev2-profile default ! interface Tunnel0 ip address negotiated ip nhrp network-id 1 ip nhrp shortcut virtual-template 1 ip nhrp redirect tunnel source Ethernet0/0 tunnel destination 10.0.0.100 tunnel protection ipsec profile default ! interface Ethernet0/0 ip address 10.0.0.120 255.255.255.0 ! interface Ethernet1/0 ip address 192.168.120.1 255.255.255.0 ! interface Virtual-Template1 type tunnel ip unnumbered Tunnel0 ip nhrp network-id 1 ip nhrp shortcut virtual-template 1 ip nhrp redirect tunnel protection ipsec profile default ! router bgp 65100 bgp router-id 10.0.0.120 bgp log-neighbor-changes neighbor hubs peer-group neighbor hubs remote-as 65100 neighbor hubs update-source Tunnel0 neighbor 172.16.1.1 peer-group hubs ! address-family ipv4 network 192.168.120.0 neighbor 172.16.1.1 activate exit-address-family
Additional References
Related Documents
Technical Assistance
|
Description |
Link |
|---|---|
|
The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password. |
Feature Information for FlexVPN Spoke to Spoke
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
| Table 1 | Feature Information for FlexVPN Spoke to Spoke |
|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
FlexVPN Spoke to Spoke |
15.2(2)T |
The FlexVPN Spoke to Spoke feature enables a FlexVPN client to establish a direct crypto channel with another FlexVPN client. The feature leverages VTIs, IKEv2, and NHRP to build spoke to spoke connections. In Cisco IOS Release 15.2(2)T, this feature was introduced. The following sections provide information about this feature: The following commands were introduced or modified: ip unnumbered loopback0, tunnel source, tunnel mode gre ip, nhrp network-id, ip nhrp redirect, ip nhrp shortcut. |
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.

 Feedback
Feedback