Contents
- Configuring Scalable Hub-and-Spoke MPLS VPNs
- Finding Feature Information
- Prerequisites for Configuring Scalable Hub-and-Spoke MPLS VPNs
- Restrictions for Configuring Scalable Hub-and-Spoke MPLS VPNs
- Information about Configuring Scalable Hub-and-Spoke MPLS VPNs
- Overview
- Upstream and Downstream VRFs
- Reverse Path Forwarding Check
- How to Ensure that MPLS VPN Clients Use the Hub PE Router
- Configuring the Upstream and Downstream VRFs on the PE Router or the Spoke PE Router
- Associating VRFs
- Configuring the Downstream VRF for an AAA Server
- Verifying the Configuration
- Configuration Examples for Configuring Scalable Hub-and-Spoke MPLS VPNs
- Configuring the Upstream and Downstream VRFs on the PE Router and the Spoke PE Router Example
- Associating VRFs Example
- Configuring Scalable Hub-and-Spoke MPLS VPNs--Basic Configuration Example
- Example
- Additional References
- Feature Information for Configuring Scalable Hub-and-Spoke MPLS VPNs
Configuring Scalable Hub-and-Spoke MPLS VPNs
This module explains how to ensure that virtual private network (VPN) clients that connect to the same provider edge (PE) router at the edge of the Mutliprotocol (MPLS) Virtual Private Network (VPN) use the hub site. This feature prevents the VPN clients from communicating directly with each other, bypassing the hub site. This feature also provides scalable hub-and-spoke connectivity for subscribers of an MPLS VPN service by removing the requirement of one VRF per spoke.
- Finding Feature Information
- Prerequisites for Configuring Scalable Hub-and-Spoke MPLS VPNs
- Restrictions for Configuring Scalable Hub-and-Spoke MPLS VPNs
- Information about Configuring Scalable Hub-and-Spoke MPLS VPNs
- How to Ensure that MPLS VPN Clients Use the Hub PE Router
- Configuration Examples for Configuring Scalable Hub-and-Spoke MPLS VPNs
- Additional References
- Feature Information for Configuring Scalable Hub-and-Spoke MPLS VPNs
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the Feature Information Table at the end of this document.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for Configuring Scalable Hub-and-Spoke MPLS VPNs
You must have a working MPLS core network.
Restrictions for Configuring Scalable Hub-and-Spoke MPLS VPNs
- In both the upstream and downstream VRFs, routing protocols are not supported on interfaces configured with this feature. Interfaces that are not configured with this feature, however, do not have this restriction for the upstream or downstream VRFs.
- You can configure this feature only on virtual access interfaces (VAIs) and virtual template interfaces (VTIs).
- Only unnumbered interfaces are supported.
- Multicast is not supported on interfaces configured for hub-and-spoke MPLS VPNs.
Information about Configuring Scalable Hub-and-Spoke MPLS VPNs
Overview
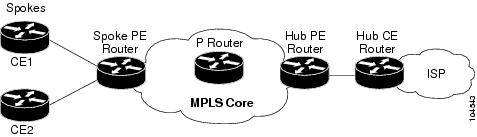
This feature prevents local connectivity between subscribers at the spoke provider edge (PE) router and ensures that a hub site provides subscriber connectivity. Any sites that connect to the same PE router must forward intersite traffic using the hub site. This ensures that the routing done at the spoke site moves from the access-side interface to the network-side interface or from the network-side interface to the access-side interface, but never from the access-side interface to the access-side interface.
This feature prevents situations where the PE router locally switches the spokes without passing the traffic through the hub site. This prevents subscribers from directly connecting to each other.
This feature eases configuration by removing the requirement of one VRF per spoke. In prior releases, when spokes connected to the same PE router, each spoke was configured in a separate VRF to ensure that the traffic between the spokes traversed the central link between the wholesale service provider and the ISP. However, this solution was not scalable. When many spokes connected to the same PE router, configuration of VRFs for each spoke became quite complex and greatly increased memory usage. This was especially true in large-scale environments that supported high-density remote access to Layer 3 VPNs.
The figure below shows a sample hub-and-spoke topology.
Upstream and Downstream VRFs
This feature uses two unidirectional VRFs to forward IP traffic between the spokes and the hub PE router:
- The upstream VRF forwards the IP traffic from the spokes toward the hub PE router. This VRF typically contains only a default route but might also contain summary routes and multiple default routes. The default route points to the interface on the hub PE router that connects to the upstream ISP. The router dynamically learns about the default route from the routing updates that the hub PE router or home gateway sends. The upstream VRF also contains the VAIs that connect the spokes, but it contains no other local interfaces.
- The downstream VRF forwards traffic from the hub PE router back to the spokes. This VRF contains Point-to-Point Protocol (PPP) peer routes for the spokes and per-user static routes received from the Authentication, Authorization, and Accounting (AAA) server. It also contains the routes imported from the hub PE router.
The router redistributes routes from the downstream VRF into Multiprotocol Border Gateway Protocol (MP-BGP). The spoke PE router typically advertises a summary route across the MPLS core for the connected spokes. The VRF configured on the hub PE router imports the advertised summary route.
Reverse Path Forwarding Check
The unicast Reverse Path Forwarding (RPF) check ensures that an IP packet that enters a router uses the correct inbound interface. This feature supports unicast RPF check on the spoke-side interfaces. Because different VRFs are used for downstream and upstream forwarding, the RPF mechanism ensures that source address checks occur in the downstream VRF.
How to Ensure that MPLS VPN Clients Use the Hub PE Router
- Configuring the Upstream and Downstream VRFs on the PE Router or the Spoke PE Router
- Associating VRFs
- Configuring the Downstream VRF for an AAA Server
- Verifying the Configuration
Configuring the Upstream and Downstream VRFs on the PE Router or the Spoke PE Router
To configure the upstream and downstream VRFs on the PE router or on the spoke PE router, use the following procedure.
DETAILED STEPS
Associating VRFs
The virtual template interface is used to create and configure a virtual access interface (VAI). After you define and configure the VRFs on the PE routers, associate each VRF with the following:
To associate a VRF, enter the following commands on the PE router.
DETAILED STEPS
Configuring the Downstream VRF for an AAA Server
To configure the downstream VRF for an AAA server, enter the following Cisco attribute value:
lcp:interface-config=ip vrf forwarding U downstream D
For more information about configuring a RADIUS server, see Configuring Virtual Template Interfaces.
Verifying the Configuration
DETAILED STEPS
Configuration Examples for Configuring Scalable Hub-and-Spoke MPLS VPNs
- Configuring the Upstream and Downstream VRFs on the PE Router and the Spoke PE Router Example
- Associating VRFs Example
- Configuring Scalable Hub-and-Spoke MPLS VPNs--Basic Configuration Example
- Example
Configuring the Upstream and Downstream VRFs on the PE Router and the Spoke PE Router Example
The following example configures an upstream VRF named U:
Router> enable Router# configure terminal Router(config)# ip vrf U Router(config-vrf)# rd 1:0 Router(config-vrf)# route-target import 1:0
The following example configures a downstream VRF named D:
Router> enable Router# configure terminal Router(config)# ip vrf D Router(config-vrf)# rd 1:8 Router(config-vrf)# route-target export 1:100
Associating VRFs Example
The following example associates the VRF named U with the virtual-template 1 interface and specifies the downstream VRF named D:
Router> enable Router# configure terminal Router(config)# interface virtual-template 1 Router(config-if)# ip vrf forwarding U downstream D Router(config-if)# ip unnumbered Loopback1
Configuring Scalable Hub-and-Spoke MPLS VPNs--Basic Configuration Example
In this example, local authentication is used; that is, the RADIUS server is not used.
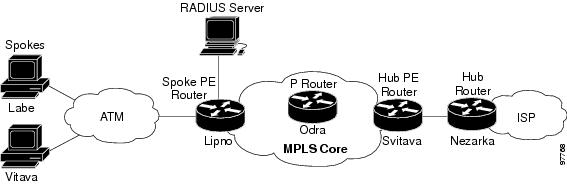
This example uses the hub-and-spoke topology shown in the figure below.
ip vrf D rd 1:8 route-target export 1:100 ! ip vrf U rd 1:0 route-target import 1:0 ! ip cef vpdn enable ! vpdn-group U accept-dialin protocol pppoe virtual-template 1 ! interface Loopback2 ip vrf forwarding U ip address 2.0.0.8 255.255.255.255 ! interface ATM2/0 description Mze ATM3/1/2 no ip address no atm ilmi-keepalive pvc 0/16 ilmi ! pvc 3/100 protocol pppoe ! pvc 3/101 protocol pppoe ! interface Virtual-Template1 ip vrf forwarding U downstream D ip unnumbered Loopback2 peer default ip address pool U-pool ppp authentication chap
Example
The following example shows how to connect two Point-to-Point Protocol over Ethernet (PPPoE) clients to a single VRF pair on the spoke PE router named Lipno. Although both PPPoE clients are configured in the same VRF, all communication occurs using the hub PE router. Half-duplex VRFs are configured on the spoke PE. The client configuration is downloaded to the spoke PE from the RADIUS server.
This example uses the hub-and-spoke topology shown in the figure above.
aaa new-model ! aaa group server radius R server 22.0.20.26 auth-port 1812 acct-port 1813 ! aaa authentication ppp default group radius aaa authorization network default group radius ! ip vrf D description Downstream VRF - to spokes rd 1:8 route-target export 1:100 ! ip vrf U description Upstream VRF - to hub rd 1:0 route-target import 1:0 ! ip cef vpdn enable ! vpdn-group U accept-dialin protocol pppoe virtual-template 1 ! interface Loopback2 ip vrf forwarding U ip address 2.0.0.8 255.255.255.255 ! interface ATM2/0 pvc 3/100 protocol pppoe ! pvc 3/101 protocol pppoe ! interface virtual-template 1 no ip address ppp authentication chap ! router bgp 1 no synchronization neighbor 100.0.0.34 remote-as 1 neighbor 100.0.0.34 update-source Loopback0 no auto-summary ! address-family vpnv4 neighbor 100.0.0.34 activate neighbor 100.0.0.34 send-community extended auto-summary exit-address-family ! address-family ipv4 vrf U no auto-summary no synchronization exit-address-family ! address-family ipv4 vrf D redistribute static no auto-summary no synchronization exit-address-family ! ip local pool U-pool 2.8.1.1 2.8.1.100 ip route vrf D 2.0.0.0 255.0.0.0 Null0 ! radius-server host 22.0.20.26 auth-port 1812 acct-port 1813 radius-server key cisco
Additional References
Related Documents
MIBs
Technical Assistance
|
Description |
Link |
|---|---|
|
The Cisco Technical Support website contains thousands of pages of searchable technical content, including links to products, technologies, solutions, technical tips, and tools. Registered Cisco.com users can log in from this page to access even more content. The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds. Access to most tools on the Cisco Support website requires a Cisco.com user ID and password. |
Feature Information for Configuring Scalable Hub-and-Spoke MPLS VPNs
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
| Table 1 | Feature Information for Configuring Scalable Hub-and-Spoke MPLS VPNs |
|
Feature Name |
Releases |
Feature Configuration Information |
|---|---|---|
|
MPLS VPN: Half Duplex VRF Support |
12.3(6) 12.3(11)T |
This feature ensures that VPN clients that connect to the same PE router at the edge of the MPLS VPN use the hub site to communicate. |
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.

 Feedback
Feedback