Cisco Nexus 7000 Series NX-OS Unicast Routing Configuration Guide, Release 4.x
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- September 15, 2010
Chapter: Configuring GLBP
Configuring GLBP
This chapter describes how to configure the Gateway Load Balancing Protocol (GLBP).
This chapter includes the following sections:
•![]() Licensing Requirements for GLBP
Licensing Requirements for GLBP
Information About GLBP
GLBP provides path redundancy for IP by sharing protocol and Media Access Control (MAC) addresses between redundant gateways. Additionally, GLBP allows a group of Layer 3 routers to share the load of the default gateway on a LAN. A GLBP router can automatically assume the forwarding function of another router in the group if the other router fails.
This section includes the following topics:
•![]() GLBP Virtual MAC Address Assignment
GLBP Virtual MAC Address Assignment
•![]() GLBP Virtual Gateway Redundancy
GLBP Virtual Gateway Redundancy
•![]() GLBP Virtual Forwarder Redundancy
GLBP Virtual Forwarder Redundancy
•![]() GLBP Load Balancing and Tracking
GLBP Load Balancing and Tracking
GLBP Overview
GLBP provides automatic gateway backup for IP hosts configured with a single default gateway on an IEEE 802.3 LAN. Multiple routers on the LAN combine to offer a single virtual first-hop IP gateway while sharing the IP packet forwarding load. Other routers on the LAN may act as redundant GLBP gateways that become active if any of the existing forwarding gateways fail.
GLBP performs a similar function to the Hot Standby Redundancy Protocol (HSRP) and the Virtual Router Redundancy Protocol (VRRP). HSRP and VRRP allow multiple routers to participate in a virtual group configured with a virtual IP address. These protocols elect one member as the active router to forward packets to the virtual IP address for the group. The other routers in the group are redundant until the active router fails.
GLBP performs an additional load balancing function that the other protocols do not provide. GLBP load balances over multiple routers (gateways) using a single virtual IP address and multiple virtual MAC addresses. GLBP shares the forwarding load among all routers in a GLBP group instead of allowing a single router to handle the whole load while the other routers remain idle. You configure each host with the same virtual IP address, and all routers in the virtual group participate in forwarding packets. GLBP members communicate between each other using periodic hello messages.
GLBP Active Virtual Gateway
GLBP prioritizes gateways to elect an active virtual gateway (AVG). If multiple gateways have the same priority, the gateway with the highest real IP address becomes the AVG. The AVG assigns a virtual MAC address to each member of the GLBP group. Each member is the active virtual forwarder (AVF) for its assigned virtual MAC address, forwarding packets sent to its assigned virtual MAC address.
The AVG also answers Address Resolution Protocol (ARP) requests for the virtual IP address. Load sharing is achieved when the AVG replies to the ARP requests with different virtual MAC addresses.

Note ![]() In Cisco NX-OS Release 4.1(2) and later, packets received on a routed port destined for the GLBP virtual IP address will terminate on the local router, regardless of whether that router is the active GLBP router or a redundant GLBP router. This includes ping and telnet traffic. Packets received on a Layer 2 (VLAN) interface destined for the GLBP virtual IP address will terminate on the active router.
In Cisco NX-OS Release 4.1(2) and later, packets received on a routed port destined for the GLBP virtual IP address will terminate on the local router, regardless of whether that router is the active GLBP router or a redundant GLBP router. This includes ping and telnet traffic. Packets received on a Layer 2 (VLAN) interface destined for the GLBP virtual IP address will terminate on the active router.
GLBP Virtual MAC Address Assignment
The AVG assigns the virtual MAC addresses to each member of the group. The group members request a virtual MAC address after they discover the AVG through hello messages. The AVG assigns the next MAC address based on the load-balancing algorithm selected (see the "GLBP Load Balancing and Tracking" section). A gateway that is assigned with a virtual MAC address by the AVG is the primary virtual forwarder. The other members of the GLBP group that learn the virtual MAC addresses from hello messages are secondary virtual forwarders.
GLBP Virtual Gateway Redundancy
GLBP provides virtual gateway redundancy. A member in a group can be in the active, standby, or listen state. GLBP uses a priority algorithm to elect one gateway as the AVG and elect another gateway as the standby virtual gateway. The remaining gateways go into the listen state. You can configure the GLBP priority on each gateway. If the GLBP priority is identical on multiple gateways, GLBP uses the gateway with the highest IP address as the AVG.
If an AVG fails, the standby virtual gateway assumes responsibility for the virtual IP address. GLBP elects a new standby virtual gateway from the gateways in the listen state.
GLBP Virtual Forwarder Redundancy
GLBP provides virtual forwarder redundancy. Virtual forwarder redundancy is similar to virtual gateway redundancy with an active virtual forwarder (AVF). If the AVF fails, a secondary virtual forwarder in the listen state assumes responsibility for the virtual MAC address. This secondary virtual forwarder is also a primary virtual forwarder for a different virtual MAC address. GLBP migrates hosts away from the old virtual MAC address of the failed AVF, using the following two timers.
•![]() Redirect timer—Specifies the interval during which the AVG continues to redirect hosts to the old virtual MAC address. When the redirect time expires, the AVG stops using the old virtual MAC address in ARP replies, although the secondary virtual forwarder continues to forward packets that were sent to the old virtual MAC address.
Redirect timer—Specifies the interval during which the AVG continues to redirect hosts to the old virtual MAC address. When the redirect time expires, the AVG stops using the old virtual MAC address in ARP replies, although the secondary virtual forwarder continues to forward packets that were sent to the old virtual MAC address.
•![]() Secondary hold timer—Specifies the interval during which the virtual MAC address is valid. When the secondary hold time expires, GLBP removes the virtual MAC address from all gateways in the GLBP group and load balances the traffic over the remaining AVFs. The expired virtual MAC address becomes eligible for reassignment by the AVG.
Secondary hold timer—Specifies the interval during which the virtual MAC address is valid. When the secondary hold time expires, GLBP removes the virtual MAC address from all gateways in the GLBP group and load balances the traffic over the remaining AVFs. The expired virtual MAC address becomes eligible for reassignment by the AVG.
GLBP uses hello messages to communicate the current state of the timers.
In Figure 18-1, router A is the AVG for a GLBP group and is responsible for the virtual IP address 192.0.2.1. Router A is also an AVF for the virtual MAC address 0007.b400.0101. Router B is a member of the same GLBP group and is designated as the AVF for the virtual MAC address 0007.b400.0102. Client 1 has a default gateway IP address of 192.0.2.1, the virtual IP address, and a gateway MAC address of 0007.b400.0101 that points to router A. Client 2 shares the same default gateway IP address but receives the gateway MAC address 0007.b400.0102 because router B is sharing the traffic load with router A.
Figure 18-1 GLBP Topology
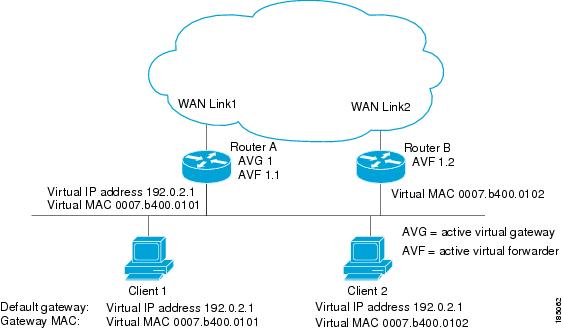
If router A becomes unavailable, client 1 does not lose access to the WAN because router B assumes responsibility for forwarding packets sent to the virtual MAC address of router A and for responding to packets sent to its own virtual MAC address. Router B also assumes the role of the AVG for the entire GLBP group. Communication for the GLBP members continues despite the failure of a router in the GLBP group.
GLBP Authentication
GLBP has three authentication types:
•![]() MD5 authentication
MD5 authentication
•![]() Plain text authentication
Plain text authentication
•![]() No authentication
No authentication
MD5 authentication provides greater security than plain text authentication. MD5 authentication allows each GLBP group member to use a secret key to generate a keyed MD5 hash that is part of the outgoing packet. At the receiving end, a keyed hash of an incoming packet is generated. If the hash within the incoming packet does not match the generated hash, the packet is ignored. The key for the MD5 hash can either be given directly in the configuration using a key string or supplied indirectly through a key chain.
You can also choose to use a simple password in plain text to authenticate GLBP packets, or choose no authentication for GLBP.
GLBP rejects packets in any of the following cases:
•![]() The authentication schemes differ on the router and in the incoming packet.
The authentication schemes differ on the router and in the incoming packet.
•![]() MD5 digests differ on the router and in the incoming packet.
MD5 digests differ on the router and in the incoming packet.
•![]() Text authentication strings differ on the router and in the incoming packet.
Text authentication strings differ on the router and in the incoming packet.
GLBP Load Balancing and Tracking
You can configure the following load-balancing methods for GLBP:
•![]() Round-robin—GLBP cycles through the virtual MAC addresses sent in ARP replies, load balancing the traffic across all the AVFs.
Round-robin—GLBP cycles through the virtual MAC addresses sent in ARP replies, load balancing the traffic across all the AVFs.
•![]() Weighted—AVG uses the advertised weight for an AVF to decide the load directed to the AVF. A higher weight means that the AVG directs more traffic to the AVF.
Weighted—AVG uses the advertised weight for an AVF to decide the load directed to the AVF. A higher weight means that the AVG directs more traffic to the AVF.
•![]() Host dependent—GLBP uses the MAC address of the host to determine which virtual MAC address to direct the host to use. This algorithm guarantees that a host gets the same virtual MAC address if the number of virtual forwarders does not change.
Host dependent—GLBP uses the MAC address of the host to determine which virtual MAC address to direct the host to use. This algorithm guarantees that a host gets the same virtual MAC address if the number of virtual forwarders does not change.
The default for IPv4 networks is round-robin. You can disable all load balancing for GLBP on an interface. If you do not configure load balancing, the AVG handles all traffic for the hosts while the other GLBP group members are in standby or listen mode.
You can configure GLBP to track an interface or routes and enable the secondary virtual forwarder to take over if a tracked link goes down. GLBP tracking uses weighted load-balancing to determine whether a GLBP group member acts as an AVF. You must configure the initial weighting values and optional thresholds to enable or disable this group member as an AVF. You can also configure the interface to track and the value that will reduce the interface's weighting if the interface goes down. When the GLBP group weighting drops below the lower threshold, the member is no longer an AVF and a secondary virtual forwarder takes over. When the weighting rises above the upper threshold, the member can resume its role as an AVF.
Figure 18-2 shows an example of GLBP tracking and weighting.
Figure 18-2 GLBP Object Tracking and Weighting
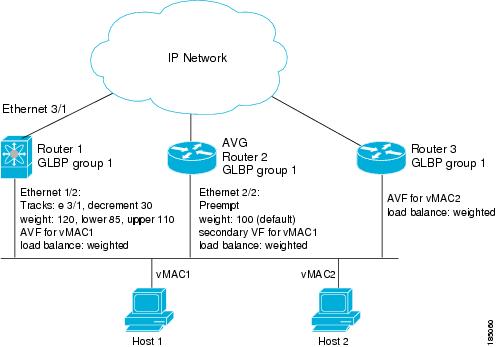
In Figure 18-2, the Ethernet 1/2 interface on router 1 is the gateway for host 1 (the AVF for virtual MAC address, vMAC1), while Ethernet 2/2 on router 2 acts as a secondary virtual forwarder for Host 1. Ethernet 1/2 tracks Ethernet 3/1, which is the network connection for router 1. If Ethernet 3/1 goes down, the weighting for Ethernet 1/2 drops to 90. Ethernet 2/2 on router 2 preempts Ethernet 1/2 and takes over as AVF because it has the default weighting of 100 and is configured to preempt the AVF.
See the "Configuring GLBP Weighting and Tracking" section for details about configuring weighting and tracking.
High Availability
GLBP supports stateful restarts and stateful switchover. A stateful restart occurs when the GLBP process fails and is restarted. Stateful switchover occurs when the active supervisor switches to the standby supervisor. Cisco NX-OS applies the run-time configuration after the switchover.
Virtualization Support
GLBP supports Virtual Routing and Forwarding instances (VRFs). VRFs exist within virtual device contexts (VDCs). By default, Cisco NX-OS places you in the default VDC and default VRF unless you specifically configure another VDC and VRF.
If you change the VRF membership of an interface, Cisco NX-OS removes all layer 3 configuration, including GLBP.
For more information, see the Cisco Nexus 7000 Series NX-OS Virtual Device Context Configuration Guide, Release 4.x and see Chapter 14, "Configuring Layer 3 Virtualization."
Licensing Requirements for GLBP
The following table shows the licensing requirements for this feature:
Prerequisites for GLBP
GLBP has the following prerequisites:
•![]() Globally enable the GLBP feature (see the "Enabling the GLBP Feature" section).
Globally enable the GLBP feature (see the "Enabling the GLBP Feature" section).
•![]() You can only configure GLBP on Layer 3 interfaces (see the Cisco Nexus 7000 Series NX-OS Interfaces Configuration Guide, Release 4.xCisco DCNM Interfaces Configuration Guide, Release 4.x).
You can only configure GLBP on Layer 3 interfaces (see the Cisco Nexus 7000 Series NX-OS Interfaces Configuration Guide, Release 4.xCisco DCNM Interfaces Configuration Guide, Release 4.x).
•![]() If you configure VDCs, install the Advanced Services license and enter the desired VDC (see the Cisco Nexus 7000 Series NX-OS Virtual Device Context Configuration Guide, Release 4.xCisco DCNM Virtual Device Context Configuration Guide, Release 4.x).
If you configure VDCs, install the Advanced Services license and enter the desired VDC (see the Cisco Nexus 7000 Series NX-OS Virtual Device Context Configuration Guide, Release 4.xCisco DCNM Virtual Device Context Configuration Guide, Release 4.x).
Guidelines and Limitations
GLBP has the following guidelines and limitations:
•![]() You should configure all customization options for GLBP on all GLBP member gateways before enabling a GLBP group by configuring a virtual IP address.
You should configure all customization options for GLBP on all GLBP member gateways before enabling a GLBP group by configuring a virtual IP address.
•![]() You must configure an IP address for the interface that you configure GLBP on and enable that interface before GLBP becomes active.
You must configure an IP address for the interface that you configure GLBP on and enable that interface before GLBP becomes active.
•![]() The GLBP virtual IP address must be in the same subnet as the interface IP address.
The GLBP virtual IP address must be in the same subnet as the interface IP address.
•![]() We recommend that you do not configure more than one first-hop redundancy protocol on the same interface.
We recommend that you do not configure more than one first-hop redundancy protocol on the same interface.
•![]() Cisco NX-OS removes all layer 3 configuration on an interface when you change the VDC, interface VRF membership, port channel membership, or when you change the port mode to layer 2.
Cisco NX-OS removes all layer 3 configuration on an interface when you change the VDC, interface VRF membership, port channel membership, or when you change the port mode to layer 2.
•![]() Cisco NX-OS does not support GLBP group configuration on interface secondary subnets.
Cisco NX-OS does not support GLBP group configuration on interface secondary subnets.
Configuring GLBP
This section includes the following topics:
•![]() Configuring GLBP Authentication
Configuring GLBP Authentication
•![]() Configuring GLBP Load Balancing
Configuring GLBP Load Balancing
•![]() Configuring GLBP Weighting and Tracking
Configuring GLBP Weighting and Tracking

Note ![]() If you are familiar with the Cisco IOS CLI, be aware that the Cisco NX-OS commands for this feature might differ from the Cisco IOS commands that you would use.
If you are familiar with the Cisco IOS CLI, be aware that the Cisco NX-OS commands for this feature might differ from the Cisco IOS commands that you would use.
Enabling the GLBP Feature
You must enable the GLBP feature before you can configure and enable any GLBP groups.
BEFORE YOU BEGIN
Ensure that you are in the correct VDC (or use the switchto vdc command).
DETAILED STEPS
To enable the GLBP feature, use the following command in global configuration mode:
|
|
|
|---|---|
feature glbp Example: switch(config)# feature glbp |
Enables GLBP. |
To disable the GLBP feature in a VDC and remove all associated configuration, use the following command in global configuration mode:
|
|
|
|---|---|
no feature glbp Example: switch(config)# no feature glbp |
Disables the GLBP feature in a VDC. |
Configuring GLBP Authentication
You can configure GLBP to authenticate the protocol using cleartext or an MD5 digest. MD5 authentication uses a key chain (see the Cisco Nexus 7000 Series NX-OS Security Configuration Guide, Release 4.x).
BEFORE YOU BEGIN
Ensure that you are in the correct VDC (or use the switchto vdc command).
Enable the GLBP feature (see the "Enabling the GLBP Feature" section).

Note ![]() You must configure the same authentication and keys on all members of the GLBP group.
You must configure the same authentication and keys on all members of the GLBP group.
SUMMARY STEPS
1. ![]() config t
config t
2. ![]() interface interface-type slot/port
interface interface-type slot/port
3. ![]() ip ip-address/length
ip ip-address/length
4. ![]() glbp group-number
glbp group-number
5. ![]() authentication text string
authentication text string
or
authentication md5 {key-chain key-chain | key-string {text | encrypted text}
6. ![]() ip [ip-address [secondary]]
ip [ip-address [secondary]]
7. ![]() show glbp [group group-number]
show glbp [group group-number]
8. ![]() copy running-config startup-config
copy running-config startup-config
DETAILED STEPS
The following example shows how to configure MD5 authentication for GLBP on Ethernet 1/2 after creating the key chain:
switch# config t
switch(config)# key chain glbp-keys
switch(config-keychain)# key 0
switch(config-keychain-key)# key-string 7 zqdest
switch(config-keychain-key) accept-lifetime 00:00:00 Jun 01 2008 23:59:59 Sep 12 2008
switch(config-keychain-key) send-lifetime 00:00:00 Jun 01 2008 23:59:59 Aug 12 2008
switch(config-keychain-key) key 1
switch(config-keychain-key) key-string 7 uaeqdyito
switch(config-keychain-key) accept-lifetime 00:00:00 Aug 12 2008 23:59:59 Dec 12 2008
switch(config-keychain-key) send-lifetime 00:00:00 Sep 12 2008 23:59:59 Nov 12 2008
switch(config)# interface ethernet 1/2
switch(config-if)# glbp 1
switch(config-if-glbp)# authenticate md5 key-chain glbp-keys
switch(config-if-glbp)# copy running-config startup-config
Configuring GLBP Load Balancing
You can configure GLBP to use load balancing based on round-robin, weighted, or host-dependent methods (see the "GLBP Load Balancing and Tracking" section).
To configure GLBP load balancing, use the following command in GLBP configuration mode:
|
|
|
|---|---|
load-balancing [host-dependent | round-robin | weighted] Example: switch(config-if-glbp)# load-balancing weighted |
Sets the GLBP load-balancing method. The default is round-robin. |
Configuring GLBP Weighting and Tracking
You can configure GLBP weighting values and object tracking to work with the GLBP weighted load-balancing method.
You can optionally configure the interface to preempt an AVF if the interface was originally assigned with the virtual MAC address or if this interface has a higher weight than the AVF.
BEFORE YOU BEGIN
Ensure that you are in the correct VDC (or use the switchto vdc command).
Enable the GLBP feature (see the "Enabling the GLBP Feature" section).
SUMMARY STEPS
1. ![]() config t
config t
2. ![]() track object-id interface interface-type number {ip routing | line-protocol}
track object-id interface interface-type number {ip routing | line-protocol}
3. ![]() track object-id ip route ip-prefix/length reachability
track object-id ip route ip-prefix/length reachability
4. ![]() interface interface-type slot/port
interface interface-type slot/port
5. ![]() ip ip-address/length
ip ip-address/length
6. ![]() glbp group-number
glbp group-number
7. ![]() weighting maximum [lower lower] [upper upper]
weighting maximum [lower lower] [upper upper]
8. ![]() weighting track object-number [decrement value]
weighting track object-number [decrement value]
9. ![]() forwarder preempt [delay minimum seconds]
forwarder preempt [delay minimum seconds]
10. ![]() ip [ip-address [secondary]]
ip [ip-address [secondary]]
11. ![]() show glbp interface-type number
show glbp interface-type number
12. ![]() copy running-config startup-config
copy running-config startup-config
DETAILED STEPS
The following example shows how to configure GLBP weighting and tracking on Ethernet 1/2:
switch# config t
switch(config)# track 2 interface ethernet 2/2 ip routing
switch(config)# interface ethernet 1/2
switch(config-if)# glbp 1
switch(config-if-glbp)# weighting 110 lower 95 upper 105
switch(config-if-glbp)# weighting track 2 decrement 20
switch(config-if-glbp)# copy running-config startup-config
Customizing GLBP
Customizing the behavior of GLBP is optional. Be aware that as soon as you enable a GLBP group by configuring a virtual IP address, that group is operational. If you enable a GLBP group before you customize GLBP, the router could take over control of the group and become the AVG before you finish customizing the feature. If you plan to customize GLBP, you should do so before enabling GLBP.
To customize GLBP, use the following commands in GLBP configuration mode:
Enabling a GLBP Group
You can configure the virtual IP address on an interface to enable the GLBP group. You must configure each gateway in the GLBP group with the same group number. The GLBP member can learn all other required parameters from another GLBP member.
BEFORE YOU BEGIN
Ensure that you are in the correct VDC (or use the switchto vdc command).
Enable the GLBP feature (see the "Enabling the GLBP Feature" section).
SUMMARY STEPS
1. ![]() config t
config t
2. ![]() interface interface-type slot/port
interface interface-type slot/port
3. ![]() ip ip-address/length
ip ip-address/length
4. ![]() glbp group-number
glbp group-number
5. ![]() ip [ip-address [secondary]]
ip [ip-address [secondary]]
6. ![]() show glbp [brief]
show glbp [brief]
7. ![]() copy running-config startup-config
copy running-config startup-config
DETAILED STEPS
The following example shows how to enable GLBP on Ethernet 1/2:
switch# config t
switch(config)# interface ethernet 1/2
switch(config-if)# glbp 1
switch(config-if-glbp)# ip 192.0.2.10
Verifying GLBP Configuration
To display GLBP configuration information, perform one of the following tasks:
GLBP Example Configuration
The following example enables GLBP on an interface, with MD5 authentication, interface tracking, and weighted load balancing:
key chain glbp-keys
key 0
key-string 7 zqdest
accept-lifetime 00:00:00 Jun 01 2008 23:59:59 Sep 12 2008
send-lifetime 00:00:00 Jun 01 2008 23:59:59 Aug 12 2008
key 1
key-string 7 uaeqdyito
accept-lifetime 00:00:00 Aug 12 2008 23:59:59 Dec 12 2008
send-lifetime 00:00:00 Sep 12 2008 23:59:59 Nov 12 2008
feature glbp
track 2 interface ethernet 2/2 ip
interface ethernet 1/2
ip address 192.0.2.2/8
glbp 1
authentication md5 key-chain glbp-keys
weighting 110 lower 95 upper 105
weighting track 2 decrement 20
ip 192.0.2.10
no shutdown
Default Settings
Table 18-1 lists the default settings for GLBP parameters.
Additional References
For additional information related to implementing GLBP, see the following sections:
Related Documents
Standards
|
|
|
|---|---|
No new or modified standards are supported by this feature, and support for existing standards has not been modified by this feature. |
— |
Feature History for GLBP
Table 18-2 lists the release history for this feature.
 Feedback
Feedback