Cisco Nexus 1000v Network Segmentation Manager Configuration Guide, Release 4.2(1)SV1(5.1)
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- January 31, 2012
Chapter: Configuring Network Segmentation Manager
- Information About Network Segmentation Manager
- Prerequisites
- Guidelines and Limitations
- Default Settings
- Network Segmentation Manager Configuration Process
- Verifying the NSM Configuration
- Configuration Examples for Network Segmentation Manager
- Changing a Port Profile Associated with a Network Segmentation Policy
- Changing the Network Segmentation Policy Associated with a Network.
- Feature History for Network Segmentation Manager
Configuring Network Segmentation Manager
This chapter describes how to configure the Network Segmentation Manager and includes the following sections:
•![]() Network Segmentation Manager Configuration Process
Network Segmentation Manager Configuration Process
•![]() Verifying the NSM Configuration
Verifying the NSM Configuration
•![]() Configuration Examples for Network Segmentation Manager
Configuration Examples for Network Segmentation Manager
•![]() Changing a Port Profile Associated with a Network Segmentation Policy
Changing a Port Profile Associated with a Network Segmentation Policy
•![]() Changing the Network Segmentation Policy Associated with a Network.
Changing the Network Segmentation Policy Associated with a Network.
•![]() Feature History for Network Segmentation Manager
Feature History for Network Segmentation Manager
Information About Network Segmentation Manager
For more information, see the Information About Network Segmentation Manager.
Prerequisites
Network Segmentation Manager has the following prerequisites:
•![]() You have installed the Cisco Nexus 1000V software and configured the following using the Cisco Nexus 1000V Software Installation Guide, Release 4.2(1)SV1(5.1).
You have installed the Cisco Nexus 1000V software and configured the following using the Cisco Nexus 1000V Software Installation Guide, Release 4.2(1)SV1(5.1).
•![]() You have a vCenter Server 4.1 or 5.0 configured in vCloud Director 1.5 and vShield Manager 5.
You have a vCenter Server 4.1 or 5.0 configured in vCloud Director 1.5 and vShield Manager 5.
•![]() You have associated a vShield Manager with every vCenter Server.
You have associated a vShield Manager with every vCenter Server.
•![]() You have created an organization in vCloud Director.
You have created an organization in vCloud Director.
•![]() You have created provider and organization vDC in vCloud Director.
You have created provider and organization vDC in vCloud Director.
•![]() Ensure that Virtual Supervisor Module (VSM) has an active SVS connection.
Ensure that Virtual Supervisor Module (VSM) has an active SVS connection.
•![]() Ensure that Virtual Supervisor Module (VSM)- Virtual Ethernet Module (VEM) connectivity is functioning.
Ensure that Virtual Supervisor Module (VSM)- Virtual Ethernet Module (VEM) connectivity is functioning.
•![]() You have added hosts to Cisco Nexus 1000V.
You have added hosts to Cisco Nexus 1000V.
•![]() Ensure that the user specified for NSM on vShield Manager is a network administrator.
Ensure that the user specified for NSM on vShield Manager is a network administrator.
Guidelines and Limitations
Network Segmentation feature has the following configuration guidelines and limitations:
•![]() You must enable the VLANs that are going to be used through NSM and add them to the uplink.
You must enable the VLANs that are going to be used through NSM and add them to the uplink.
•![]() Ensure that the infrastructure has port 443 open.
Ensure that the infrastructure has port 443 open.
•![]() You must enable feature http-server in order to allow web service communication.
You must enable feature http-server in order to allow web service communication.
•![]() You must enable the segmentation feature in order to use NSM for Virtual Extensible Local Area Network (VXLAN) via vCloud Director. In a network segmentation policy, VXLAN is used for a segmentation policy. See the Cisco Nexus 1000V VXLAN Configuration Guide, Release 4.2(1)SV1(5.1).
You must enable the segmentation feature in order to use NSM for Virtual Extensible Local Area Network (VXLAN) via vCloud Director. In a network segmentation policy, VXLAN is used for a segmentation policy. See the Cisco Nexus 1000V VXLAN Configuration Guide, Release 4.2(1)SV1(5.1).
Default Settings
Table 2-1 lists the default settings for network segmentation policies.
|
|
|
|---|---|
VLAN policy (port-profile template) |
default_vlan_template |
segmentation policy (port-profile template) |
default_segmentation_template |

Note ![]() If a network creation request comes with a tenant ID and backing type that does not match a network segmentation policy, the default_vlan_template or default_segmentation_template is used during network creation from vCloud Director. In a network segmentation policy, VXLAN is used for a segmentation policy. For more information, see the Cisco Nexus 1000V VXLAN Configuration Guide, Release 4.2(1)SV1(5.1). If required, you can add additional policies to the default NSM template.
If a network creation request comes with a tenant ID and backing type that does not match a network segmentation policy, the default_vlan_template or default_segmentation_template is used during network creation from vCloud Director. In a network segmentation policy, VXLAN is used for a segmentation policy. For more information, see the Cisco Nexus 1000V VXLAN Configuration Guide, Release 4.2(1)SV1(5.1). If required, you can add additional policies to the default NSM template.
Network Segmentation Manager Configuration Process
The following section guides you through the NSM configuration process. See Figure 2-1. After completing each procedure, return to this section to make sure that you have completed all required procedures in the correct sequence.
Figure 2-1 Network Segmentation Manager Configuration Process
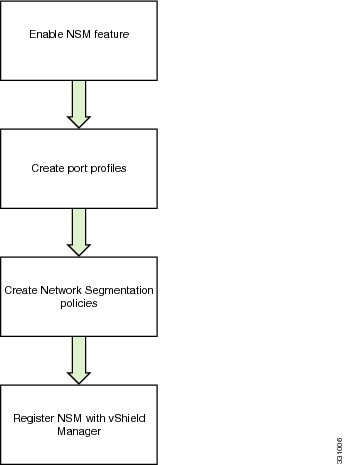
Step 1 ![]() Enable the NSM feature using the "Enabling the NSM Feature" section.
Enable the NSM feature using the "Enabling the NSM Feature" section.
Step 2 ![]() Create a port profile for network segmentation policies using the "Creating a Port Profile for Network Segmentation Policies" section.
Create a port profile for network segmentation policies using the "Creating a Port Profile for Network Segmentation Policies" section.
Step 3 ![]() Create network segmentation policies using the "Creating Network Segmentation Policies" section.
Create network segmentation policies using the "Creating Network Segmentation Policies" section.
Step 4 ![]() Register NSM with vShield Manager using the "Registering vShield Manager with Network Segmentation Manager" section.
Register NSM with vShield Manager using the "Registering vShield Manager with Network Segmentation Manager" section.
Enabling the NSM Feature
You can enable the NSM feature in Cisco Nexus 1000V.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in EXEC mode.
You are logged in to the CLI in EXEC mode.
SUMMARY STEPS
1. ![]() configure terminal
configure terminal
2. ![]() feature network-segmentation-manager
feature network-segmentation-manager
3. ![]() (Optional) show network-segment manager switch
(Optional) show network-segment manager switch
DETAILED STEPS
EXAMPLES
This example shows how to enable the NSM feature:
n1000v# configure terminal
n1000v(config)# feature network-segmentation-manager
n1000v# show network-segment manager switch
switch: default_switch
state: enabled
dvs-uuid: d4 e7 12 50 89 db 3b c4-8d 4d 4c 36 ca 1c d1 f0
dvs-name: nexus1000v
mgmt-srv-uuid: 087F202C-8937-4F1E-8676-6F714C1AB96C
reg status: unregistered
last alert: - seconds ago
connection status: disconnected
Creating a Port Profile for Network Segmentation Policies
You can create a port profile that contains policies such as QoS, ACLs, and so on for network segmentation policies in Cisco Nexus 1000V.
For more information on port profiles, see the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1).
For more information on QoS, see the Cisco Nexus 1000V Quality of Service Configuration Guide, Release 4.2(1)SV1(5.1).
For more information on ACL, see the Cisco Nexus 1000V Security Configuration Guide, Release 4.2(1)SV1(5.1).
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in EXEC mode.
You are logged in to the CLI in EXEC mode.
•![]() The VSM is connected to vCenter Server.
The VSM is connected to vCenter Server.
•![]() The NSM feature is enabled.
The NSM feature is enabled.
SUMMARY STEPS
1. ![]() configure terminal
configure terminal
2. ![]() port-profile [type vethernet] name
port-profile [type vethernet] name
3. ![]() no shutdown
no shutdown
4. ![]() state enabled
state enabled
5. ![]() (Optional) show running-config port-profile name
(Optional) show running-config port-profile name
DETAILED STEPS
EXAMPLES
This example shows how to create a segmentation type port profile:
n1000v# configure terminal
n1000v(config)# port-profile type vethernet ABC_profile_segmentation
n1000v(config-port-prof)# no shutdown
n1000v(config-port-prof)# state enabled
n1000v(config-port-prof)# show running-config port-profile ABC_profile_segmentation
!Command: show running-config port-profile ABC_profile_segmentation
!Time: Thu Dec 1 19:58:44 2011
version 4.2(1)SV1(5.1)
port-profile type vethernet ABC_profile_segmentation
no shutdown
state enabled
Creating Network Segmentation Policies
Network segmentation policies are a set of policies that are inherited on a port profile that is created as a result of a network. The policy type can be either VLAN or Segmentation. This policy type corresponds to the network pool type in the vCloud Director. VLAN network segmentation policies are used for networks created from VLAN-backed network pools and Segmentation network segmentation policies are used for networks created from network isolation-backed network pools.
The network segmentation policies also contains a tenant ID and a reference to a port profile that may contain other policies for features such as QoS, ACL, and so on. Each tenant ID is unique and can be associated with only one Segmentation and one VLAN network segmentation policy. The tenant ID correlates to the Organization Universally Unique Identifier (UUID) in the vCloud Director. For more information on retrieving the organization UUID from VMware vCloud Director, see http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=2012943

Note ![]() If a network segmentation policy with a tenant ID is not created, the default_vlan_template or default_segmentation_template is used during network creation from vCloud Director. In a network segmentation policy, VXLAN is used for a segmentation policy. For more information, see the Cisco Nexus 1000V VXLAN Configuration Guide, Release 4.2(1)SV1(5.1).
If a network segmentation policy with a tenant ID is not created, the default_vlan_template or default_segmentation_template is used during network creation from vCloud Director. In a network segmentation policy, VXLAN is used for a segmentation policy. For more information, see the Cisco Nexus 1000V VXLAN Configuration Guide, Release 4.2(1)SV1(5.1).
You can create network segmentation policies.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in EXEC mode.
You are logged in to the CLI in EXEC mode.
•![]() The NSM feature is enabled.
The NSM feature is enabled.
•![]() You know the tenant IDs for tenants that require non default network segmentation policies. The tenant IDs for network segment policies can be found on vCloud Director. It is located in the address bar of the browser when viewing an organization.
You know the tenant IDs for tenants that require non default network segmentation policies. The tenant IDs for network segment policies can be found on vCloud Director. It is located in the address bar of the browser when viewing an organization.
In the following example,
https://[VCloud_director_IP]/cloud/#/vAppListPage?org=91e87e80-e18b-460f-a761-b978c0d28aea
the tenant ID is "91e87e80-e18b-460f-a761-b978c0d28aea"
•![]() You must create the port profiles with all the required feature port profiles before importing them to the network segmentation policy. To create a port profile, see the "Creating a Port Profile for Network Segmentation Policies" section.
You must create the port profiles with all the required feature port profiles before importing them to the network segmentation policy. To create a port profile, see the "Creating a Port Profile for Network Segmentation Policies" section.
•![]() You have knowledge about port profile inheritance. See the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1).
You have knowledge about port profile inheritance. See the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1).
SUMMARY STEPS
1. ![]() configure terminal
configure terminal
2. ![]() network-segment policy name
network-segment policy name
3. ![]() description description
description description
4. ![]() type {segmentation | VLAN}
type {segmentation | VLAN}
5. ![]() id {vCloud Director Organization tenant-id}
id {vCloud Director Organization tenant-id}
6. ![]() import port-profile name
import port-profile name
7. ![]() (Optional) show running-config network-segment policy
(Optional) show running-config network-segment policy
DETAILED STEPS
EXAMPLES
This example shows how to create a NSM policy for ABC Inc for VXLAN networks:
n1000v# configure terminal
n1000v(config)# network-segment policy abc-policy-vxlan
n1000v(config-network-segment-policy)# description network segmentation policy for ABC for VXLAN networks
n1000v(config-network-segment-policy)# type segmentation
n1000v(config-network-segment-policy)# id f5dcf127-cdb0-4bdd-8df5-9515d6dc8170
n1000v(config-network-segment-policy)# import port-profile ABC_profile_segmentation
n1000v(config-network-segment-policy)#show running-config network-segment policy abc-policy-vxlan
!Command: show running-config network-segment policy abc-policy-vxlan
!Time: Fri Aug 26 18:34:50 2011
version 4.2(1)SV1(5.1)
feature network-segmentation-manager
network-segment policy abc-policy-vxlan
description network segmentation policy for ABC for VXLAN networks
id f5dcf127-cdb0-4bdd-8df5-9515d6dc8170
type segmentation
import port-profile port-profile ABC_profile_segmentation
This example shows how to create a NSM policy for ABC Inc for VLAN networks:
n1000v# configure terminal
n1000v(config)# network-segment policy abc-policy-vlan
n1000v(config-network-segment-policy)# description network segmentation policy for ABC for
VLAN networks
n1000v(config-network-segment-policy)# type vlan
n1000v(config-network-segment-policy)# id f5dcf127-cdb0-4bdd-8df5-9515d6dc8170
n1000v(config-network-segment-policy)# import port-profile ABC_profile_vlan
n1000v(config-network-segment-policy)#

Note ![]() As a best practice, if a tenant specific policy is defined through network segmentation policies, you should define it for both segmentation and VLAN types.
As a best practice, if a tenant specific policy is defined through network segmentation policies, you should define it for both segmentation and VLAN types.
Registering vShield Manager with Network Segmentation Manager
You can use this procedure to register VMware vShield Manager with NSM.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to vShield Manager.
You are logged in to vShield Manager.
•![]() The vShield Manager is connected to vCenter Server.
The vShield Manager is connected to vCenter Server.
•![]() The NSM feature is enabled.
The NSM feature is enabled.
•![]() You know the range of multicast addresses.
You know the range of multicast addresses.
•![]() You know the segment ID pool.
You know the segment ID pool.
•![]() Ensure that the segment ID range allocated to vShield Manager does not overlap with other instances in the network or VXLANs used on the Cisco Nexus 1000V.
Ensure that the segment ID range allocated to vShield Manager does not overlap with other instances in the network or VXLANs used on the Cisco Nexus 1000V.
•![]() Ensure that the user specified for NSM on vShield Manager is a network administrator.
Ensure that the user specified for NSM on vShield Manager is a network administrator.
DETAILED STEPS
Step 1 ![]() In the vShield Manager, navigate to the Settings and Report window.
In the vShield Manager, navigate to the Settings and Report window.
Step 2 ![]() In the Setting and Reports pane, click Configuration.
In the Setting and Reports pane, click Configuration.
Step 3 ![]() Click Networking. The Edit Settings window opens.
Click Networking. The Edit Settings window opens.
Step 4 ![]() Enter the segment ID pool. The segment ID pool should be greater than 4097.
Enter the segment ID pool. The segment ID pool should be greater than 4097.
Step 5 ![]() Enter the multicast address range.
Enter the multicast address range.
Step 6 ![]() Click OK.
Click OK.
Step 7 ![]() In the vShield Manager, navigate to the External Switch Providers window.
In the vShield Manager, navigate to the External Switch Providers window.
Step 8 ![]() Click Add Switch Provider. The External Switch Provider window opens.
Click Add Switch Provider. The External Switch Provider window opens.
Step 9 ![]() Enter the name of the switch.
Enter the name of the switch.
Step 10 ![]() Enter the NSM API service URL (https://Cisco-VSM-IP-Address/n1k/services/NSM).
Enter the NSM API service URL (https://Cisco-VSM-IP-Address/n1k/services/NSM).
Step 11 ![]() Enter the network administrator username and password.
Enter the network administrator username and password.
Step 12 ![]() Accept the SSL thumbprint.
Accept the SSL thumbprint.
Step 13 ![]() In the External Switch Providers window, a green check mark in the Status column indicates that the connection between vShield Manager and NSM is established.
In the External Switch Providers window, a green check mark in the Status column indicates that the connection between vShield Manager and NSM is established.
Step 14 ![]() You can verify the registration of the vShield Manager with NSM by entering the following command on the Cisco Nexus 1000V CLI:
You can verify the registration of the vShield Manager with NSM by entering the following command on the Cisco Nexus 1000V CLI:
n1000v# show network-segment manager switch
switch: default_switch
state: enabled
dvs-uuid: d4 e7 12 50 89 db 3b c4-8d 4d 4c 36 ca 1c d1 f0
dvs-name: nexus1000v
mgmt-srv-uuid: 087F202C-8937-4F1E-8676-6F714C1AB96C
reg status: registered
last alert: 30 seconds ago
connection status: connected
Unregistering vShield Manager with Network Segmentation Manager
You can use this procedure to unregister VMware vShield Manager with NSM.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to vShield Manager.
You are logged in to vShield Manager.
•![]() The vShield Manager is registered with NSM.
The vShield Manager is registered with NSM.
DETAILED STEPS
Step 1 ![]() In the vShield Manager, navigate to the Settings and Report window.
In the vShield Manager, navigate to the Settings and Report window.
Step 2 ![]() In the Setting and Reports pane, click Configuration.
In the Setting and Reports pane, click Configuration.
Step 3 ![]() Click Networking. The Edit Settings window opens.
Click Networking. The Edit Settings window opens.
Step 4 ![]() In the External Switch Providers pane, click the Delete link for the switch you wish to unregister.
In the External Switch Providers pane, click the Delete link for the switch you wish to unregister.
Step 5 ![]() You can verify that the vShield Manager has been unregistered by entering the following command on the Cisco Nexus 1000V CLI:
You can verify that the vShield Manager has been unregistered by entering the following command on the Cisco Nexus 1000V CLI:
n1000v# show network-segment manager switch
switch: default_switch
state: enabled
dvs-uuid: ff 05 32 50 5b d5 db fe-da 48 70 e1 0f bd ae 43
dvs-name: cinquedia-vsm
mgmt-srv-uuid: 35B101C8-DE9B-42F9-BE85-284DD679367D
reg status: unregistered
last alert: - seconds ago
connection status: disconnected
Verifying the NSM Configuration
To display NSM configuration information, perform one of the following tasks:
For detailed information about the fields in the output from these commands, refer to the Cisco Nexus 1000V Command Reference, Release 4.2(1)SV1(5.1).
Configuration Examples for Network Segmentation Manager
The following example shows how to configure Network Segmentation Manager feature:
Step 1 ![]() Enable Network Segmentation Manager.
Enable Network Segmentation Manager.
n1000v# configure terminal
n1000v(config)# feature network-segmentation-manager
Step 2 ![]() Create a port profiles for segmentation and VLAN policies.
Create a port profiles for segmentation and VLAN policies.
n1000v# configure terminal
n1000v(config)# port-profile type vethernet ABC_profile_segmentation
n1000v(config-port-prof)# no shutdown
n1000v(config-port-prof)# state enabled
n1000v# configure terminal
n1000v(config)# port-profile type vethernet ABC_profile_vlan
n1000v(config-port-prof)# no shutdown
n1000v(config-port-prof)# state enabled
Step 3 ![]() Create a NSM Policy
Create a NSM Policy
n1000v# configure terminal
n1000v(config)# network-segment policy abc-policy-vxlan
n1000v(config-network-segment-policy)# description network segmentation policy for ABC for VXLAN networks
n1000v(config-network-segment-policy)# type segmentation
n1000v(config-network-segment-policy)# id f5dcf127-cdb0-4bdd-8df5-9515d6dc8170
n1000v(config-network-segment-policy)# import port-profile ABC_profile_segmentation
n1000v#configure terminal
n1000v(config)# network-segment policy abc-policy-vlan
n1000v(config-network-segment-policy)# description network segmentation policy for ABC for
VLAN networks
n1000v(config-network-segment-policy)# type vlan
n1000v(config-network-segment-policy)# id f5dcf127-cdb0-4bdd-8df5-9515d6dc8170
n1000v(config-network-segment-policy)# import port-profile ABC_profile_vlan
Step 4 ![]() Verify the configuration.
Verify the configuration.
n1000v# configure terminal
n1000v(config)# show running-config network-segment policy abc-policy-vxlan
!Command: show running-config network-segment policy abc-policy-vxlan
!Time: Fri Aug 26 18:34:50 2011
version 4.2(1)SV1(5.1)
feature network-segmentation-manager
network-segment policy abc-policy-vxlan
description network segmentation policy for ABC for VXLAN networks
id f5dcf127-cdb0-4bdd-8df5-9515d6dc8170
type segmentation
import port-profile port-profile ABC_profile_segmentation
Changing a Port Profile Associated with a Network Segmentation Policy
During a network creation in the vCloud Director, network segmentation policies are created on the NSM and these network segmentation policies are inherited on a port profile. In order to associate a different port profile with the deployed network, you can change the port profile associated with the network segmentation policy.
To change the port profile associated with the network segmentation policy perform the following steps:
Step 1 ![]() Identify all the networks associated with the network segmentation policy. For more information, see Identifying the Networks Associated with the Network Segmentation Policy.
Identify all the networks associated with the network segmentation policy. For more information, see Identifying the Networks Associated with the Network Segmentation Policy.
Step 2 ![]() Manually remove the inheritance for the existing port profile. See section "Removing Inherited Policies from a Port Profile" in the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1) for more information.
Manually remove the inheritance for the existing port profile. See section "Removing Inherited Policies from a Port Profile" in the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1) for more information.
Step 3 ![]() Manually inherit the new port profile that will be associated with the network segmentation policy. See section "Inheriting a Configuration from a Port Profile" in the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1) for more information.
Manually inherit the new port profile that will be associated with the network segmentation policy. See section "Inheriting a Configuration from a Port Profile" in the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1) for more information.
Step 4 ![]() Update the network segmentation policy. For more information, see Updating the Network Segmentation Policy
Update the network segmentation policy. For more information, see Updating the Network Segmentation Policy
Identifying the Networks Associated with the Network Segmentation Policy
You can identify the networks associated with the network segmentation policy.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in configuration mode.
You are logged in to the CLI in configuration mode.
•![]() The NSM feature is enabled.
The NSM feature is enabled.
SUMMARY STEPS
1. ![]() configure terminal
configure terminal
2. ![]() show network-segment policy usage
show network-segment policy usage
DETAILED STEPS
EXAMPLES
This example shows how to identify the networks associated with a network segmentation policy:
n1000v(config)# show network-segment policy usage
network-segment policy default_segmentation_template
dvs.VCDVSint-org-cn2-e46e9686-2327-49df-ad5c-a3f89c00cfb8
network-segment policy default_vlan_template
network-segment policy abc-policy-vxlan
dvs.VCDVSint-org-nexus-6141babd-bdc8-4e86-8f16-1ac786fb377f
network-segment policy abc-policy-vlan
Updating the Network Segmentation Policy
You can update a network segmentation policy.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in EXEC mode.
You are logged in to the CLI in EXEC mode.
•![]() The NSM feature is enabled.
The NSM feature is enabled.
•![]() You know the tenant IDs for tenants that require non default network segmentation policies.
You know the tenant IDs for tenants that require non default network segmentation policies.
•![]() You must create the port profiles with all the required feature port profiles before importing them to the network segmentation policy. To create a port profile, see the Creating a Port Profile for Network Segmentation Policies.
You must create the port profiles with all the required feature port profiles before importing them to the network segmentation policy. To create a port profile, see the Creating a Port Profile for Network Segmentation Policies.
•![]() You have knowledge about port profile inheritance. See the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1).
You have knowledge about port profile inheritance. See the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1).
SUMMARY STEPS
1. ![]() configure terminal
configure terminal
2. ![]() network-segment policy name
network-segment policy name
3. ![]() import port-profile name force
import port-profile name force
4. ![]() (Optional) show run network-segment policy
(Optional) show run network-segment policy
DETAILED STEPS
EXAMPLES
This example shows how to update the network segmentation policy:
n1000v# configure terminal
n1000v(config)# show running-config network-segment policy abc-policy-vxlan
network-segment policy abc-policy-vxlan
description network segmentation policy for ABC for VXLAN networks
type segmentation
id f5dcf127-cdb0-4bdd-8df5-9515d6dc8170
import port-profile ABC_profile_segmentation
n1000v(config)# network-segment policy abc-policy-vxlan
n1000v(config-network-segment-policy)# import port-profile ABC_profile_segmentation_new
force
n1000v(config)# show running-config network-segment policy abc-policy-vxlan
network-segment policy abc-policy-vxlan
description network segmentation policy for ABC for VXLAN networks
type segmentation
id f5dcf127-cdb0-4bdd-8df5-9515d6dc8170
import port-profile ABC_profile_segmentation_new
Changing the Network Segmentation Policy Associated with a Network.
During a network creation in the vCloud Director, network segmentation policies are created on the NSM. In order to use other non default policies for any new or old networks associated with an Organization vDC in the vCloud Director, you must change the network segmentation policy associated with a network.
To change the network segmentation policy associated with a network, perform the following steps:
Step 1 ![]() Identify all the networks that need to be migrated. For more information, see Identifying the Networks.
Identify all the networks that need to be migrated. For more information, see Identifying the Networks.
Step 2 ![]() Manually remove the inheritance of the port profile associated with the network segmentation policy from the network. See section "Removing Inherited Policies from a Port Profile" in the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1) for more information.
Manually remove the inheritance of the port profile associated with the network segmentation policy from the network. See section "Removing Inherited Policies from a Port Profile" in the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1) for more information.
Step 3 ![]() Manually inherit the new port profile that will be associated with the network segmentation policy on the network. See section "Inheriting a Configuration from a Port Profile" in the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1) for more information.
Manually inherit the new port profile that will be associated with the network segmentation policy on the network. See section "Inheriting a Configuration from a Port Profile" in the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1) for more information.
Step 4 ![]() Migrate the networks from the default network segmentation policy to the non default network segmentation policy. For more information, see Migrating Networks to Non Default Network Segmentation Policy.
Migrate the networks from the default network segmentation policy to the non default network segmentation policy. For more information, see Migrating Networks to Non Default Network Segmentation Policy.
Identifying the Networks
You can identify the networks that have to be migrated.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in configuration mode.
You are logged in to the CLI in configuration mode.
•![]() The NSM feature is enabled.
The NSM feature is enabled.
SUMMARY STEPS
1. ![]() configure terminal
configure terminal
2. ![]() show network-segment network
show network-segment network
DETAILED STEPS
EXAMPLES
This example shows you how to display the networks associated with a network segmentation policy:
n1000v(config)# show network-segment network
network dvs.VCDVSint-org-cn2-e46e9686-2327-49df-ad5c-a3f89c00cfb8
tenant id: 2b4ca1b2-ba8e-456c-b772-a4730af16e2e
network-segment policy: default_segmentation_template
segment id: 4107
multicast ip: 225.0.0.1
network dvs.VCDVSint-org-nexus-6141babd-bdc8-4e86-8f16-1ac786fb377f
tenant id: 91e87e80-e18b-460f-a761-b978c0d28aea
network-segment policy: seg-template-nexus-org
segment id: 4108
multicast ip: 225.0.0.2
n100v(config)#
Migrating Networks to Non Default Network Segmentation Policy
You can migrate the networks from the default network segmentation policy to the non default network segmentation policy.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in EXEC mode.
You are logged in to the CLI in EXEC mode.
•![]() The NSM feature is enabled.
The NSM feature is enabled.
•![]() You know the tenant IDs for tenants that require non default network segmentation policies.
You know the tenant IDs for tenants that require non default network segmentation policies.
•![]() You have knowledge about port profile inheritance. See the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1).
You have knowledge about port profile inheritance. See the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1).
SUMMARY STEPS
1. ![]() configure terminal
configure terminal
2. ![]() network-segment policy migrate id isolation_id type nw_type dest-policy policy
network-segment policy migrate id isolation_id type nw_type dest-policy policy
3. ![]() (Optional) show network-segment network
(Optional) show network-segment network
DETAILED STEPS
EXAMPLES
This example shows you how to migrate networks to non default segmentation policy:
n1000v(config)# show network-segment network
network dvs.VCDVStenantid_vlan-74e36255-e588-4357-8abe-15d2cc7feaec
tenant id: da5c49a8-dd1b-4326-9da0-3c5e6a2c1b87
network-segment policy: default_segmentation_template
segment id: 4107
multicast ip: 225.0.0.1
n1000v(config)# network-segment policy migrate id da5c49a8-dd1b-4326-9da0-3c5e6a2c1b87
type segmentation dest-policy org_seg

Note ![]() In case a warning appears then, first manually remove the inheritance of the port profile associated with the network segmentation policy from the network. See section "Removing Inherited Policies from a Port Profile" in the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1) for more information. Then, manually inherit the new port profile that will be associated with the network segmentation policy on the network. See section "Inheriting a Configuration from a Port Profile" in the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1) for more information.
In case a warning appears then, first manually remove the inheritance of the port profile associated with the network segmentation policy from the network. See section "Removing Inherited Policies from a Port Profile" in the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1) for more information. Then, manually inherit the new port profile that will be associated with the network segmentation policy on the network. See section "Inheriting a Configuration from a Port Profile" in the Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(5.1) for more information.
n1000v(config)#show network-segment network
network dvs.VCDVStenantid_vlan-74e36255-e588-4357-8abe-15d2cc7feaec
tenant id: da5c49a8-dd1b-4326-9da0-3c5e6a2c1b87
network-segment policy: org_seg
segment id: 4107
multicast ip: 225.0.0.1
Feature History for Network Segmentation Manager
Table 2-2 lists the release history for this feature. Only features that were introduced or modified in Release 4.2(1)SV1(5.1) or a later release appear in the table.
|
|
|
|
|---|---|---|
Network Segmentation Manager |
4.2(1)SV1(5.1) |
Introduced the Network Segmentation Manager (NSM) feature. |
 Feedback
Feedback