Cisco Nexus 1000V VEM Software Installation and Upgrade Guide, Release 4.2(1) SV1(4a)
Available Languages
Table Of Contents
Cisco Nexus 1000V VEM Software Installation and Upgrade Guide, Release 4.2(1)SV1(4a)
Information About the Virtual Ethernet Module
Introduction to Cisco Nexus 1000V and the Virtual Ethernet Module
Prerequisites for Installing VEM Software
Choosing a VEM Software Upgrade or Installation Procedure
Upgrading the ESX/ESXi Host With VEM Software Installed Using VUM
Upgrading from VMware Release 4.0/4.1 to VMware Release 5.0.0
Upgrading the vCenter Update Manager
Verification After the Upgrade
Upgrading to VMware ESXi 5.0 Patch 01
Upgrading a VMware ESXi 5.0 Stateful Host to VMware ESXi 5.0 Patch 01
Upgrading a VMware ESXi 5.0 Stateless Host to VMware ESXi 5.0 Patch 01
Installing ESXi 5.0.0 Host Software Using the CLI
Installing or Upgrading the VEM Software Using the VUM
Installing or Upgrading the VEM Software Using the CLI
Installing a VEM on a Stateless ESXi Host
Information About a Stateless ESXi Host
Adding the Cisco Nexus 1000V to an ESXi Image Profile
Installing the VEM Software on an ESXi Stateless Host Using esxcli
Uninstalling the VEM Software on an ESXi Stateless Host Using esxcli
Installing the VEM Software on an ESXi Stateless Host Using VUM
Obtaining Documentation and Submitting a Service Request
Cisco Nexus 1000V VEM Software Installation and Upgrade Guide, Release 4.2(1)SV1(4a)
Revised: September 13, 2011OL-21656-A1This document describes how to install and upgrade the Cisco Nexus 1000V Virtual Ethernet Module (VEM) software on a VMware ESX/ESXi 4.0.0, ESX/ESXi 4.1.0, or ESXi 5.0.0 server.
This document includes the following sections:
•
Information About the Virtual Ethernet Module
•
Prerequisites for Installing VEM Software
•
Choosing a VEM Software Upgrade or Installation Procedure
•
Upgrading the ESX/ESXi Host With VEM Software Installed Using VUM
•
Upgrading from VMware Release 4.0/4.1 to VMware Release 5.0.0
•
Upgrading to VMware ESXi 5.0 Patch 01
•
Installing ESXi 5.0.0 Host Software Using the CLI
•
Installing or Upgrading the VEM Software Using the VUM
•
Installing or Upgrading the VEM Software Using the CLI
•
Installing a VEM on a Stateless ESXi Host
•
Obtaining Documentation and Submitting a Service Request, page 47
Audience
This document is intended for use by experienced server administrators who configure and maintain server software. Table 1 compares the roles of the network administrator and server administrator.
This document includes instructions for installing new VEM software as a fresh install or after upgrading the VSM software to a new version.
To install the Virtual Supervisor Module (VSM), see the following document:
Cisco Nexus 1000V Software Installation Guide, Release 4.2(1)SV1(4a)
For detailed information about upgrading the software on the VSM and VEM, see the following document:
Cisco Nexus 1000V Software Upgrade Guide, Release 4.2(1)SV1(4a)
Information About the Virtual Ethernet Module
This section provides information about the VEM and includes the following topics:
•
Introduction to Cisco Nexus 1000V and the Virtual Ethernet Module
Introduction to Cisco Nexus 1000V and the Virtual Ethernet Module
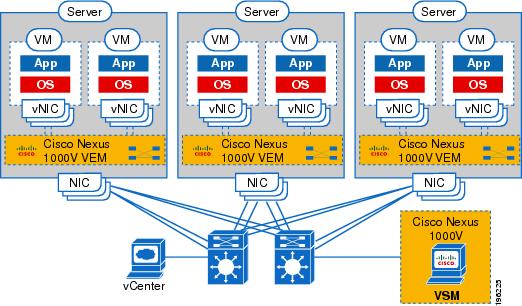
The Cisco Nexus 1000V is compatible with any upstream physical access layer switch that is Ethernet standard compliant, including the Catalyst 6500 series switch, Cisco Nexus switches, and switches from other network vendors. The Cisco Nexus 1000V is compatible with any server hardware listed in the VMware Hardware Compatibility List (HCL).
Cisco and VMware jointly designed APIs that produced the Cisco Nexus 1000V. The Cisco Nexus 1000V is a distributed virtual switch solution that is fully integrated within the VMware virtual infrastructure, including VMware vCenter for the virtualization administrator. This solution offloads the configuration of the virtual switch and port groups to the network administrator to enforce a consistent data center network policy.
The Cisco Nexus 1000V has the following components that can virtually emulate a 66-slot modular Ethernet switch with redundant supervisor functions:
•
Virtual Ethernet module (VEM) data plane—Each hypervisor is embedded with one VEM, which is a lightweight software component that replaces the virtual switch by performing the following functions:
–
Advanced networking and security
–
Switching between directly attached virtual machines
–
Uplinking to the rest of the network

Note
Only one version of VEM can be installed on an ESX/ESXi host at any given time.
•
Virtual supervisor module (VSM) control plane—The VSM is a virtual appliance that can be installed in either a standalone or active/standby HA pair. The VSM, with the VEMs that is controls, performs the following functions for the Cisco Nexus 1000V system.

Note
We recommend an active/standby HA pair configuration.
–
Configuration
–
Management
A single VSM can manage up to 64 VEMs.
–
Monitoring
–
Diagnostics
–
Integration with VMware vCenter
Active-standby VSMs increase high availability
In the Cisco Nexus 1000V, traffic is switched between virtual machines locally at each VEM instance. Each VEM also interconnects the local virtual machine with the rest of the network through the upstream access-layer network switch (blade, top-of-rack, end-of-row, and so forth). The VSM runs the control plane protocols and configures the state of each VEM accordingly, but it never forwards packets.
In the Cisco Nexus 1000V, the module slots are for the primary module 1 and secondary module 2. Either module can act as active or standby. The first server or host is automatically assigned to Module 3. The Network Interface Card (NIC) ports are 3/1 and 3/2 (vmnic0 and vmnic1 on the ESX/ESXi host). The ports to which the virtual NIC interfaces connect are virtual ports on the Cisco Nexus 1000V where they are assigned a global number.
Figure 1 shows an example of the Cisco Nexus 1000V distributed architecture.
Figure 1 Cisco Nexus 1000V Distributed Switching Architecture
Obtaining the VEM Software
You can obtain the VEM software from the sources listed in Table 2.
Table 2 Obtaining VEM Software
VUM
The VMware vCenter Update Manager (VUM) obtains the VEM software from the VSM or from the VMware online portal. See the VMware and Cisco Nexus 1000V Software Compatibility table in the Cisco Nexus 1000V Compatibility Information, Release 4.2(1)SV1(4a), to identify which VEM bits are available on the VSM or posted on the VMware online portal.1
VSM
After the VSM has been installed as a VM, copy the file containing the VEM software from the VSM home page located at the following url:
http://VSM_IP_Address/
VMware
Download the ESXi and VC software from the VMware website.
Click Download Vmware vSphere 4 Enterprise Plus > Download
Download the VMware patches if you are utilizing VMware releases with patches.
Cisco
Download the VEM software from Cisco.com.
1 VMware vCenter Update Manager 4.0 does not list Cisco Nexus 1000V patches or updates, but you can add a Cisco Nexus 1000V patch source using the VMware knowledge base procedure located at the following url:
http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=1013134
VMware vCenter Server 4.0 Update 1 with VUM P02 and later versions do not have this limitation.
VMware Patch Releases
The Cisco Nexus 1000V VEM software is updated to support VMware patch releases and is available on both the VMware and Cisco software download websites. The Cisco Nexus 1000V software posted on these websites can be used for both installation and upgrade of the VEM for both the VMware Classic and VMware Embedded platforms.
For information about installing software on an ESX/ESXi host, see your VMware documentation.
For information about VEM software packages and compatibility, see the Cisco Nexus 1000V Compatibility Information, Release 4.2(1)SV1(4a).
Prerequisites for Installing VEM Software
Before installing the Cisco Nexus 1000V VEM software, you must know or do the following:

CautionIf the VMware vCenter Server is hosted on the same ESX/ESXi host as a Cisco Nexus 1000V VEM, a VUM-assisted upgrade on the host will fail. You should manually vMotion the vCenter Server VM to another host before you perform an upgrade.

Note
When you perform any VUM operation on hosts that are a part of a cluster, ensure that VMWare High Availability (HA), VMware Fault Tolerance (FT), and VMware Distributed Power Management (DPM) features are disabled for the entire cluster. Otherwise, VUM will fail to install the hosts in the cluster.
•
Before you perform a VEM upgrade, make sure that there are no active VMs running on the host. When you install the VMware patch ESX/ESXi400-201002001 and later on the host, it puts the host in maintenance mode when you perform a VEM upgrade. If you do not have and also use VMware vCenter Update Manager 4.0 Update 1 Patch 2, vCLI build 198790, and VSM Release 4.0(4)SV1(2) or later releases, in order to have a nondisruptive upgrade.
•
You must install VMware patch ESX/ESXi400-201002001 and later on the host and also use VMware vCenter Update Manager 4.0 Update 1 Patch 2, vCLI build 198790, and VSM Release 4.0(4)SV1(2) or later releases, in order to have a nondisruptive upgrade.
•
You have a copy of your VMware documentation available for installing software on a host.
•
You have already obtained a copy of the VEM software file from one of the sources listed in Table 2.
•
If you are installing the VEM software for the first time, you can install it before you install the VSM. However, you cannot verify and configure the VEM until after you install the VSM.
•
You have already downloaded the correct VEM software based on the current ESX/ESXi host patch level. For more information, see the Cisco Nexus 1000V Compatibility Information, Release 4.2(1)SV1(4a).
•
If you install the VEM software on an ESXi host before adding the host to a vSphere Server, you must reboot the host. The alternative is to add the host to vSphere Server first and then install the VEM software.
•
If you are installing the VEM software for the first time, you will not need any action by the server administrator because VUM automatically installs the VEM software.
•
If you use a proxy server to connect VUM to the Internet, you may need to disable the proxy before starting a VUM upgrade. In VMware versions before VUM Update 1, the proxy prevents VUM from communicating locally with the VSM. For this reason, automatic VEM upgrades might fail if the proxy is not disabled first.
•
On your upstream switches, you must have the following configuration.
–
On Catalyst 6500 Series Switches with Cisco IOS software:
(config-if) portfast trunk
or
(config-if) portfast edge trunk–
On Cisco Nexus 5000 Series Switches with Cisco NX-OS software:
(config-if) spanning-tree port type edge trunk•
On your upstream switches, we highly recommend that you globally enable the following:
–
Global BPDU Filtering
–
Global BPDU Guard
•
On your upstream switches where you cannot globally enable BPDU Filtering and BPDU Guard, we highly recommended that you enter the following commands:
–
(config-if) spanning-tree bpdu filter
–
(config-if) spanning-tree bpdu guard
•
For more information about configuring spanning tree, BPDU, or PortFast, see the documentation for your upstream switch.
Choosing a VEM Software Upgrade or Installation Procedure
This section describes how you can upgrade the ESX/ESXi host with the VEM software installed or install or upgrade the VEM software:
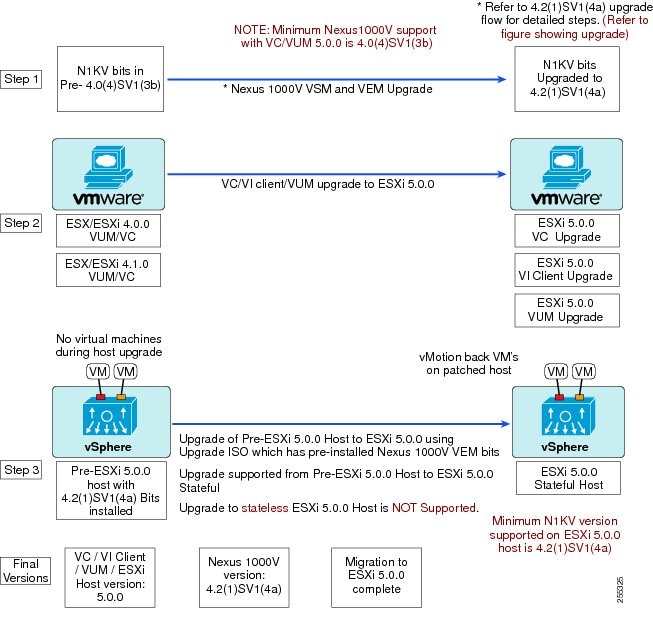
The following three diagrams depict the recommended workflows depending on the version of Cisco Nexus 1000V software you have installed. These workflows are for stateful ESXi hosts. For information on stateless ESXi hosts, see Installing a VEM on a Stateless ESXi Host.
Figure 2 Workflow with Cisco Nexus 1000V 4.2(1)SV1(4a) Installed
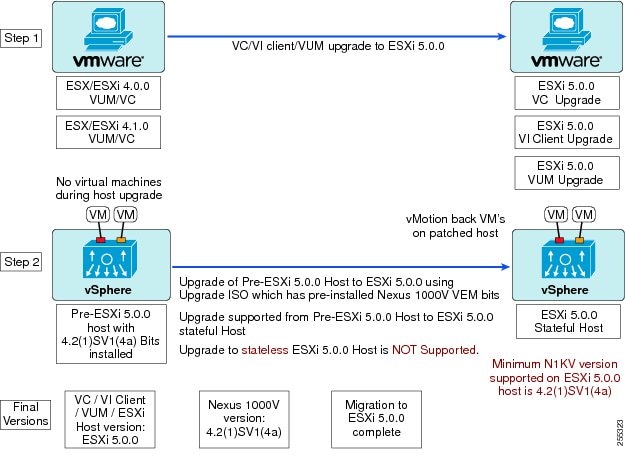
Figure 3 Workflow with Cisco Nexus 1000V 4.0(4)SV1(3b/3c) or 4.2(1)SV1(4) Installed
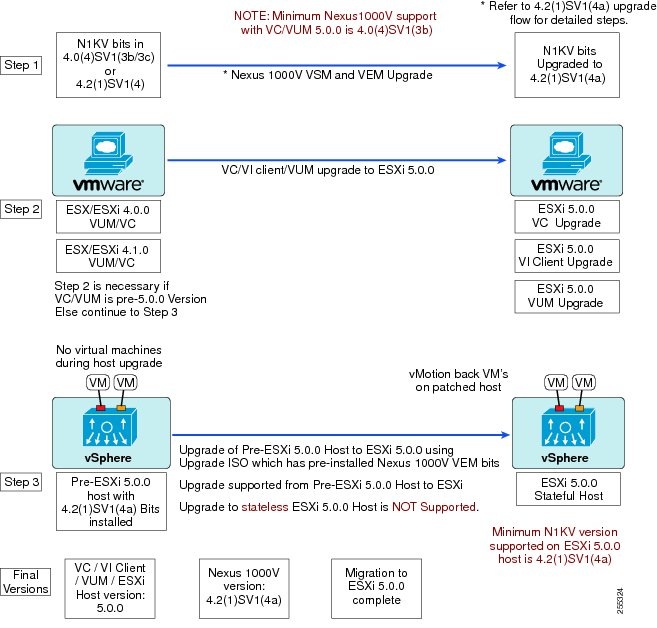
Figure 4 Workflow with a Cisco Nexus 1000V Version Prior to 4.0(4)SV1(3b) Installed
There are two possible use cases:
•
Upgrading the ESX/ESXi host with VEM software installed
–
If you are using VUM to upgrade the host, you must create a host patch baseline and include the appropriate VMware patch or update bulletins and the corresponding Cisco Nexus 1000V VEM bulletin in the baseline. You can then upgrade the host by applying the baseline to the host and remediating. To determine which VUM upgrade procedure you should follow, see the "Upgrading the ESX/ESXi Host With VEM Software Installed Using VUM" section.
–
If you are using the CLI, enter the vihostupdate command or the esxupdate command. For more information, see the "Installing ESXi 5.0.0 Host Software Using the CLI" section.
•
Installing or upgrading the VEM software
–
If you are using VUM, the Cisco Nexus 1000V VEM software is installed automatically when the host is added to the Cisco Nexus 1000V Distributed Virtual Switch (DVS). When VEM upgrades are triggered from the VSM, the VEM software is automatically upgraded on the host. To determine which VUM upgrade procedure you should follow, see the "Installing or Upgrading the VEM Software Using the VUM" section.
–
If you are using the CLI, enter the vihostupdate command or the esxupdate command. For more information, see the "Installing or Upgrading the VEM Software Using the CLI" section.
Upgrading the ESX/ESXi Host With VEM Software Installed Using VUM

CautionIf removable media is still connected, for example, if you have installed the VSM by using the ISO image and forgot to remove the media, then host movement to maintenance mode fails and the VUM upgrade fails.
This section describes the procedures for installing and upgrading from, VMware Release 4.0.0/4.1.0 to VMware Release 5.0.0.
•
Upgrading from VMware Release 4.0/4.1 to VMware Release 5.0.0
Upgrading from VMware Release 4.0/4.1 to VMware Release 5.0.0
You can use this procedure to upgrade from VMware Release 4.0/4.1 to VMware Release 5.0.0.
Upgrading your ESX infrastructure to VMware Release 5.0.0 when Cisco Nexus 1000V is installed requires you to upgrade in the following order:
1.
Upgrade the VSMs and VEMs to Release 4.2(1)SV1(4a).
2.
Upgrade the VMware vCenter Server to VMware Release 5.0.0.
3.
Upgrade the VMware Update Manager to VMware Release 5.0.0.
4.
Upgrade your ESX hosts to VMware Release 5.0.0 with a custom ESXi image that includes the VEM bits.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•
ESXi 5.0.0 vCenter Server and ESXi 5.0.0 Update Manager
•
Download the upgrade ISO file containing the ESXi 5.0.0 bits and the Cisco Nexus 1000V Release 4.2(1)SV1(4a) bits.
•
Consult the Cisco Nexus 1000V Compatibility Information, Release 4.2(1)SV1(4a) document to determine the correct VIB Version, VEM Bundle, Host Build, vCenter Server, and Update Manager versions.
•
Upgrading the ESX/ESXi hosts consists of the following procedures:
–
Upgrading the vCenter Update Manager
–
Augmenting the Customized ISO
Upgrading the vCenter Server
This procedure shows you how to upgrade the vCenter Server to VMware ESXi 5.0.0.

Note
This is an overview procedure. For specific information, refer to the VMWare documentation.
Step 1
Navigate to the VMware vSphere 5.0.0 installation file.

Note
If you have the ISO image, you should mount it on the host.
Figure 5 Autorun Window
Step 2
Double-click autorun.
Step 3
Click vCenter Server and click Install.
Step 4
Select a language and click OK.
The Installation Wizard opens.
Step 5
Click Next.
Step 6
In the Patent Agreement window, click Next.
The License Agreement window opens. See Figure 6.
Figure 6 License Agreement Window
Step 7
Click the I agree to the terms in the license agreement radio button.
Step 8
Click Next.
Step 9
In the Database Options screen, click Next.
The Database Upgrade Warning screen opens. See Figure 7.
Figure 7 Database Upgrade Warning Screen
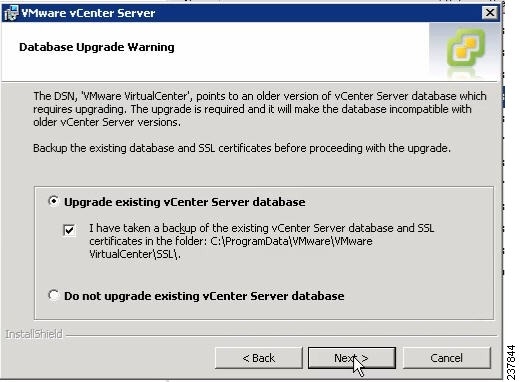
Step 10
Click the Upgrade existing vCenter Server database radio button and check the I have taken a backup of the existing vCenter Server database and SSL certificates in the folder: C:\ProgramData\VMware\VMware VirtualCenter\SSL\. check box.
Step 11
From the Windows Start Menu, click Run.
The Run dialog box opens.
Step 12
Enter the name of the folder that contains the vCenter Server database and click OK.
Step 13
Drag a copy of the parent folder (SSL) to the Desktop as a backup.
Step 14
Return to the installer program.
Step 15
Click Next.
Step 16
In the vCenter Agent Upgrade window, click the Automatic radio button.
Step 17
Click Next.
The vCenter Server Service screen opens. See Figure 8.
Figure 8 VMware vCenter Server Service Screen
Step 18
Check the Use SYSTEM Account check box.
Step 19
Click Next.
The Configure Ports screen opens. See Figure 9.
Figure 9 Configure Ports Screen
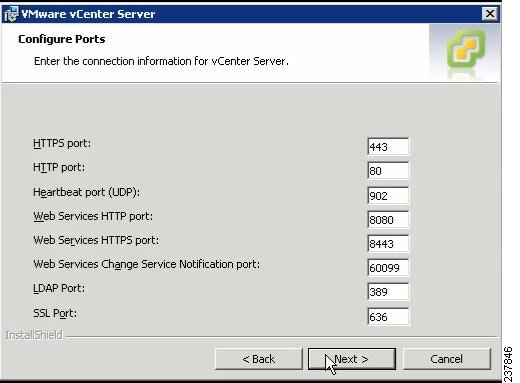
Step 20
Review the port settings and click Next.
The vCenter Server JVM Memory screen opens. See Figure 10.
Figure 10 vCenter Server JVM Memory Screen
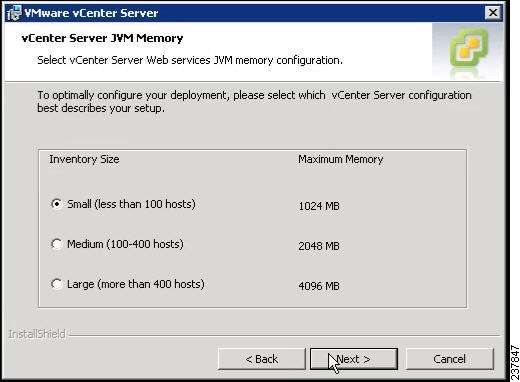
Step 21
Based on the number of hosts, click the appropriate memory radio button.
Step 22
Click Next.
The Ready to Install the Program screen opens. See Figure 11.
Figure 11 Ready to Install the Program Screen
Step 23
Click Install.
The Installation Completed screen appears. See Figure 12.
Figure 12 Installation Completed Screen
Step 24
Click Finish.
This completes the upgrade of the vCenter Server.
Step 25
Upgrade the VMware vSphere Client to ESXi 5.0.0.
Step 26
Open the VMware vSphere Client.
Step 27
From the Help menu, choose About VMware vSphere.
Step 28
Confirm that the vSphere Client and the VMware vCenter Server are both version VMware 5.0.0
Step 29
Click OK, and exit the VMware vSphere Client.
Upgrading the vCenter Update Manager
Step 1
On the local drive, double-click VMware-UpdateManager as seen in Figure 5.
Step 2
Select a language and click OK.
The Update Manager Installer opens.
Step 3
Click OK to upgrade to 5.0.0.
Figure 13 Welcome
Step 4
Click Next to begin.
Step 5
Click Next at the Patent Agreement.
Step 6
Click the I agree to the terms in the license agreement radio button.
Step 7
Click Next.
The vCenter Server Information screen opens. See Figure 14.
Figure 14 vCenter Server Information Screen
Step 8
In the VMware vCenter Server Information area, verify the IP address and Username.
Step 9
In the Password field, enter your password.
Step 10
Click Next.
The Database Information screen opens. See Figure 15.
Figure 15 Database Information Screen
Step 11
Click Next.
The Database Upgrade screen opens. See Figure 16.
Figure 16 Database Upgrade Screen
Step 12
Click the Yes, I want to upgrade my Update Manager database radio button.
Step 13
Click Next.
Step 14
Verify the Update Manager port settings.
Step 15
Click Next.
Step 16
Verify the Proxy Settings.
Step 17
Click Next.
Step 18
Click Install to begin the upgrade.
Step 19
Click OK to acknowledge that a reboot will be required to complete the setup.
Step 20
During the upgrade, the vSphere Client is disconnected. Click Cancel for the attempt to reconnect.
Step 21
Click OK in the Server Connection Invalid dialog box.
Step 22
Click Finish.
Step 23
Reboot the VUM/vCenter server.
The Shut Down Windows dialog box opens. See Figure 17
Figure 17 Shut Down Windows Dialog Box
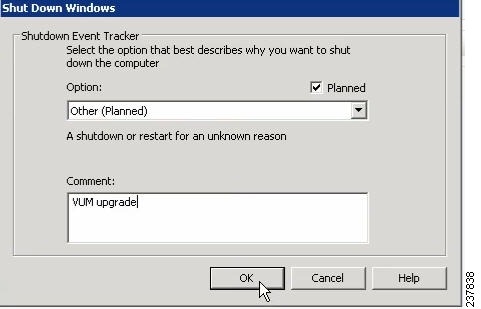
Step 24
From the Option drop-down list, choose Other (Planned), enter a value in the comment field, and click OK.
Step 25
After the system has rebooted, browse to the C:\ProgramData\VMware\VMware Update Manager\Logs\ folder.
Step 26
Open the vmware-vum-server-log4cpp file.
Step 27
From the VMware vCenter Server's Plug-in menu, select Manage Plug-ins.
Step 28
Under Available Plug-ins, click Download and Install for VMware vSphere Update Manager Extension.
The update of the VMware Update Manager is complete.
Augmenting the Customized ISO
If the ESXi host that is being upgrade to VMware 5.0.0 needs any Async drivers that are not already in VMware 5.0.0, refer to the respective vendor's documentation for the drivers and the procedure to update the customized ISO.
If you are using a QLogic NIC, download the driver to include in the customized ISO for that specific NIC.
Upgrading the ESXi Hosts
Step 1
In the vSphere Client, click Home
Step 2
Click the Update Manager tab.
Figure 18 ESXi Images Tab
Step 3
Click the ESXi Image tab.
Figure 19 Select ESXi Image Window
Step 4
Click the Import ESXi Image link in the ESXi Image window.
Step 5
Click the Browse button and navigate to the customized upgrade ISO image.
Step 6
Select the upgrade file and click Open.
The Select ESXi Image screen opens. See Figure 20.
Figure 20 Select ESXi Image Screen
Step 7
To import the ISO file, click Next.
The Upload Progress opens. See Figure 21.
Figure 21 Upload Progress Screen
Step 8
Click Next.
The Upload Complete screen opens. See Figure 22.
Figure 22 Upload Complete Screen
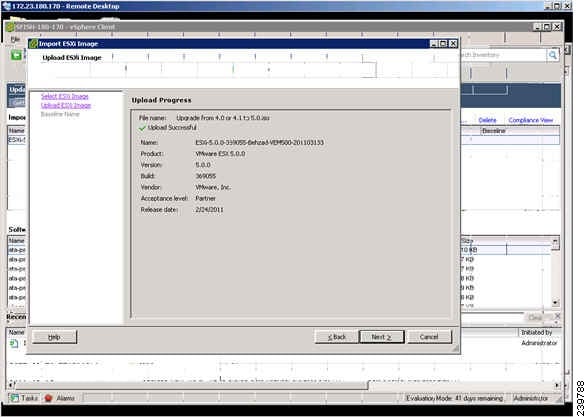
Step 9
When the upgrade ISO file is uploaded, click Next.
The Baseline Name screen opens. See Figure 23.
Figure 23 Baseline Name Screen
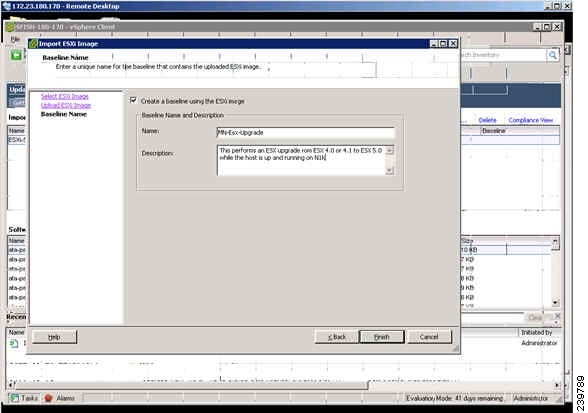
Step 10
In the Name field, enter a Name for the baseline and an optional description.
Step 11
Click Finish.
Figure 24 Update Manager Window
Step 12
Select the host or cluster to upgrade and click the Update Manager tab.
Step 13
Click Attach.
The Attach Baseline or Group window opens. See Figure 25.
Figure 25 Attach Baseline or Group Window
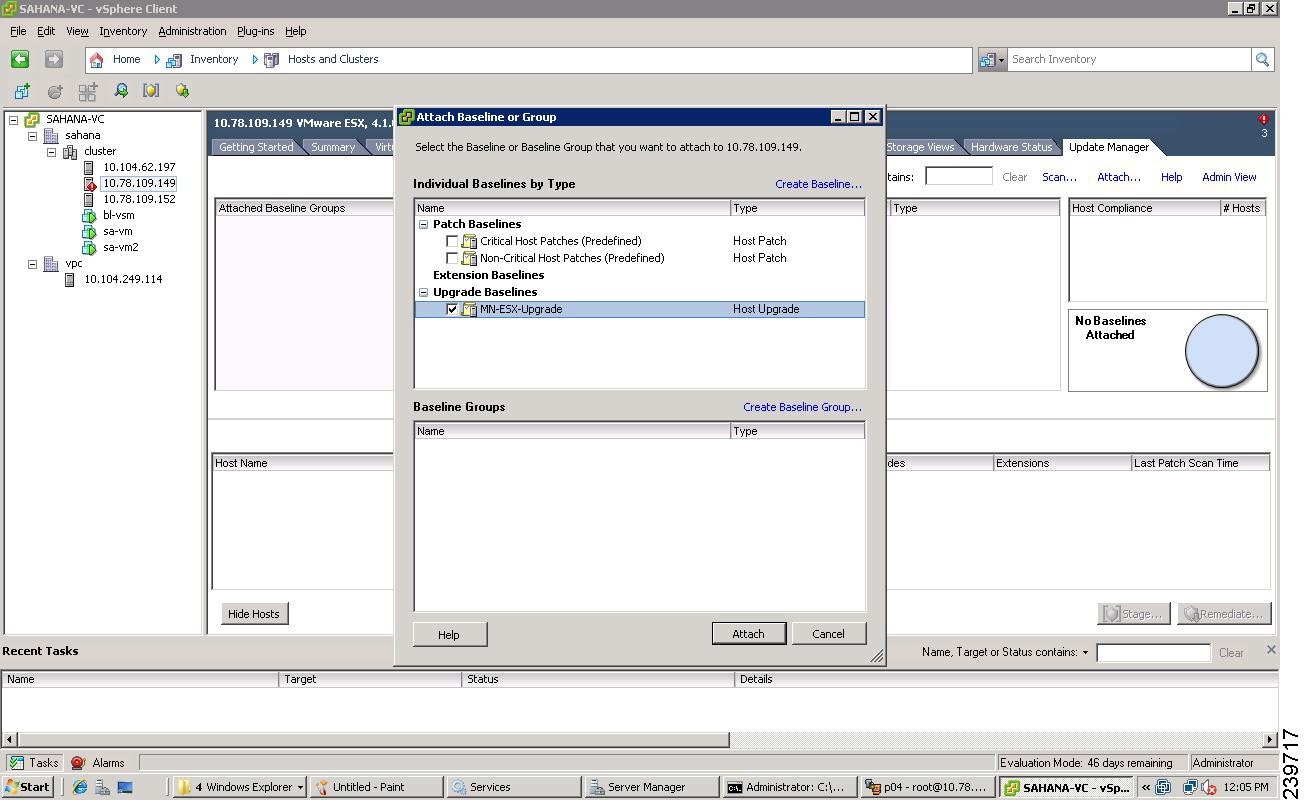
Step 14
Check the MN-ESX-Upgrade check box.
Step 15
Click Attach.
The Confirm Scan window opens. See Figure 26.
Figure 26 Confirm Scan Window
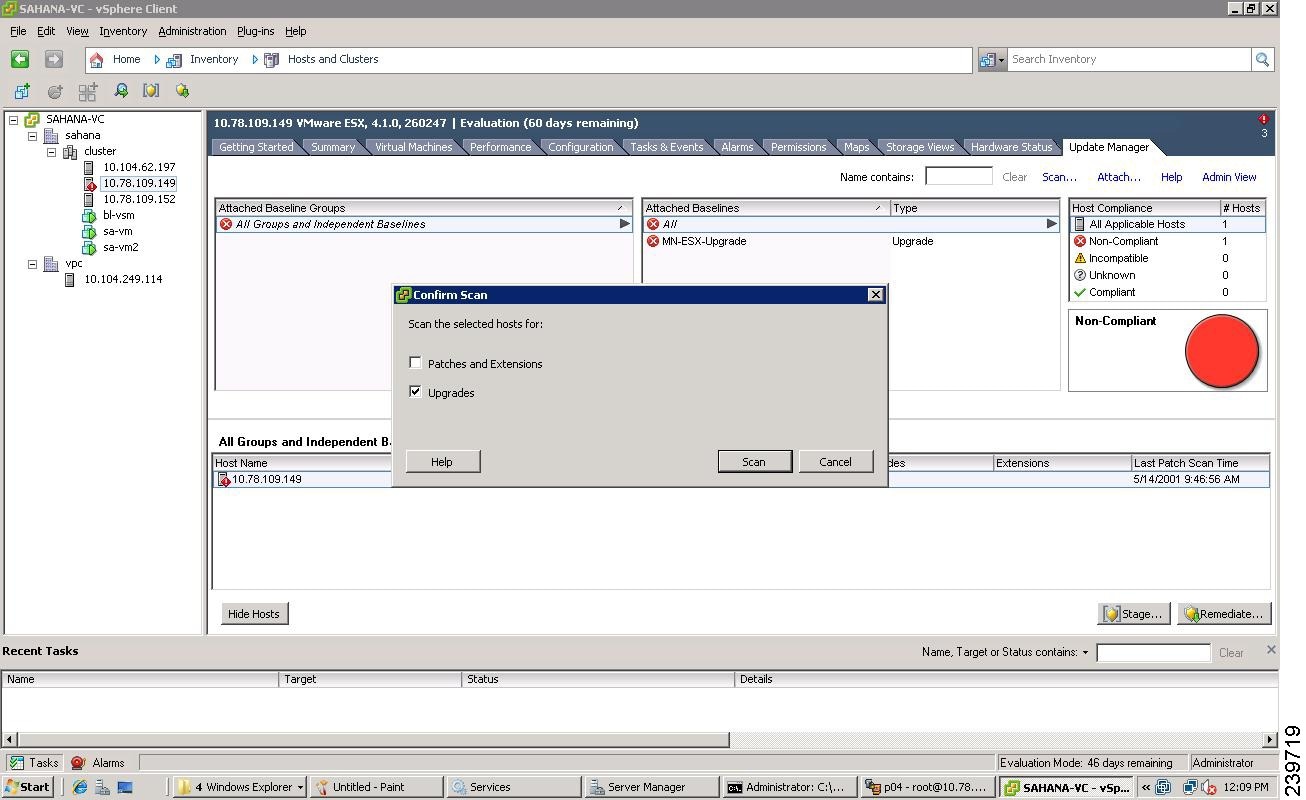
Step 16
Click Scan.
After the scan, the baseline will display non-compliant.
Figure 27 Upgrade Details Window

Step 17
If the Compliance State has a value of Incompatible, reboot the host with the baseline attached.
After the reboot, the Compliance State will have a value of Non-Compliant.
Figure 28 Upgrade Details Window
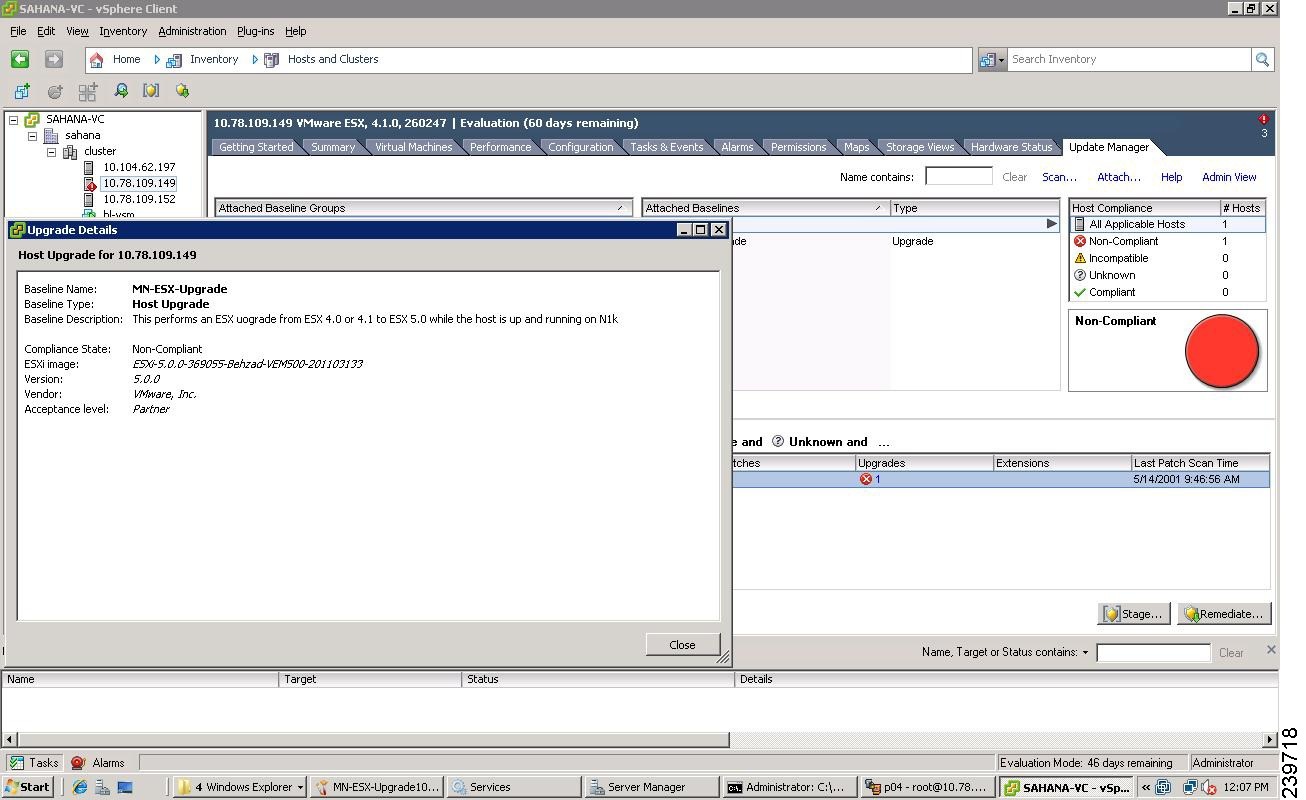
Step 18
When you are finished viewing the upgrade details, click Close.
Step 19
Verify that all hosts are Non-Compliant.
Step 20
Click Remediate.
The Remediate Selection screen opens. See Figure 29.
Figure 29 Remediate Selection Screen
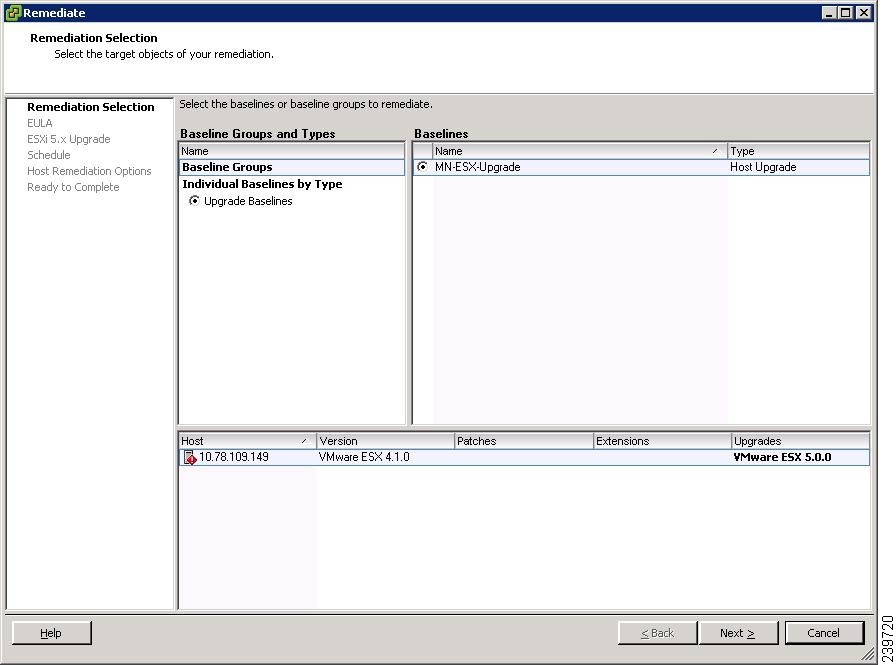
Step 21
Click Next.
The EULA screen opens. See Figure 30.
Figure 30 EULA Screen

Step 22
Check the I accept the terms and license agreement check box.
Step 23
Click Next.
Step 24
In the ESXi 5.x Upgrade window, click Next.
Figure 31 Schedule Window
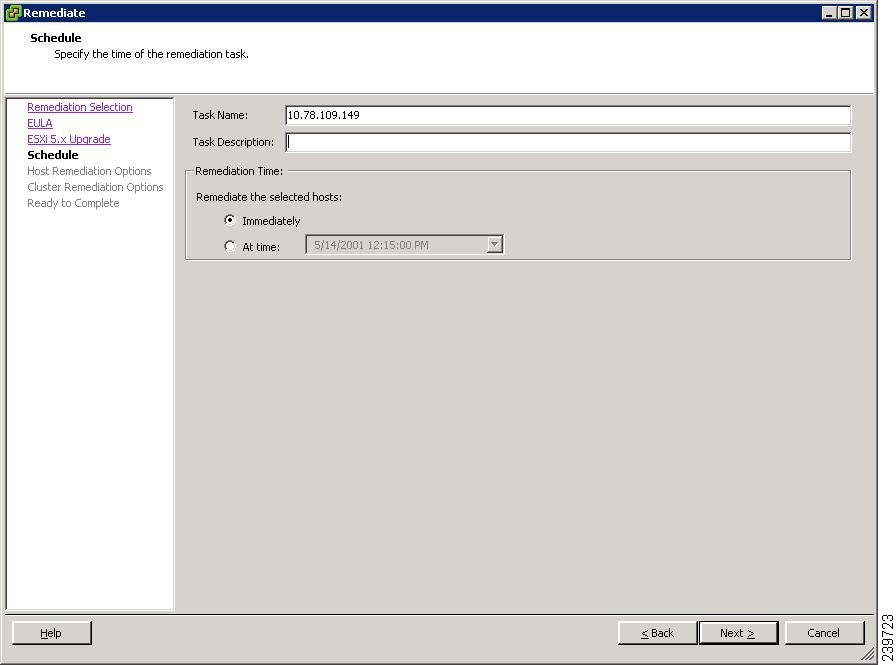
Step 25
Click Next.
The Host Remediation Options screen opens. See Figure 32.
Figure 32 Host Remediation Options Window
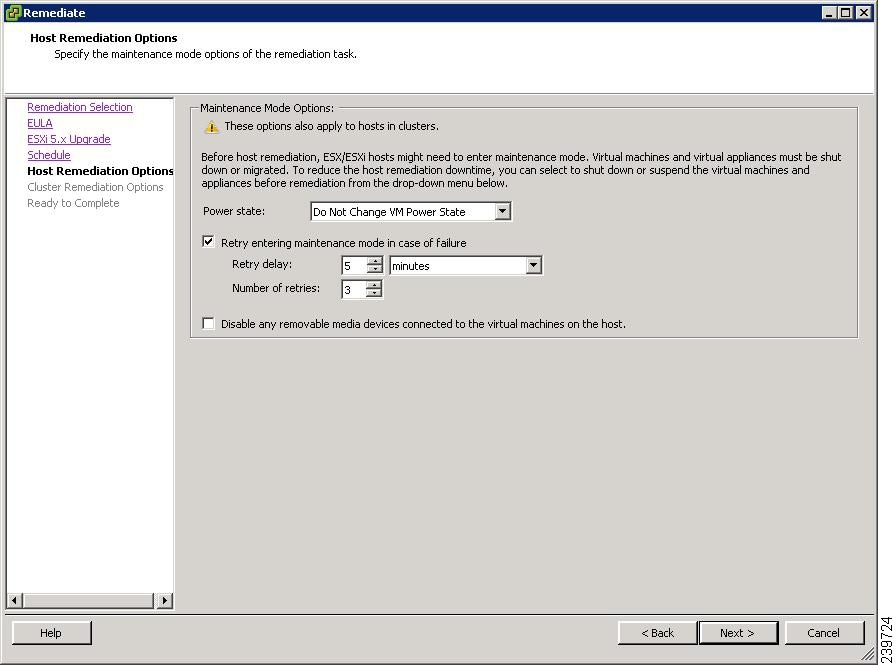
Step 26
Check the Disable any removable media devices connected to the virtual machines on the host check box.
Step 27
Click Next.
The Cluster Remediation Options screen opens. See Figure 33.
Figure 33 Cluster Remediation Options Screen
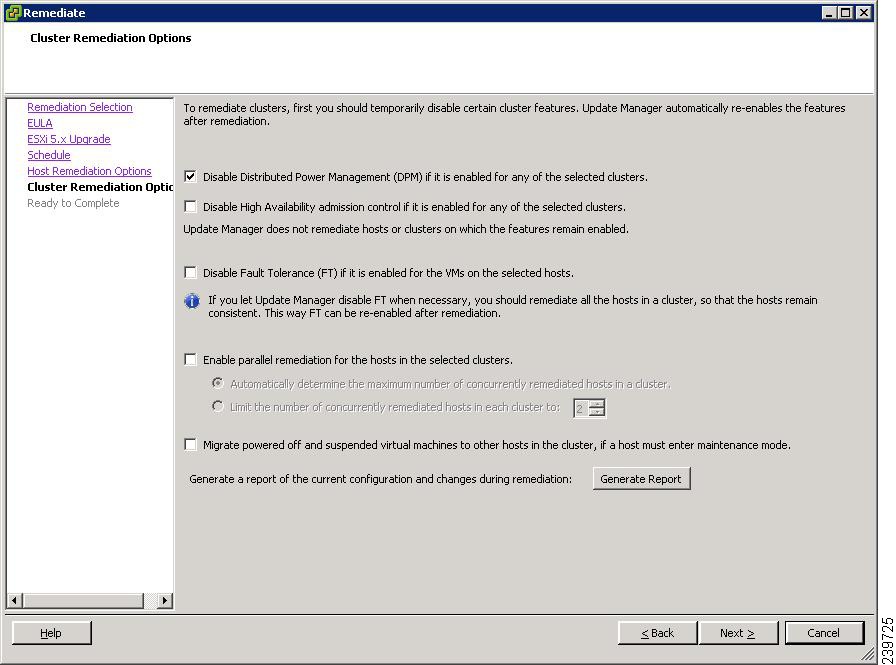
Step 28
In the Cluster Remediation Options window, check all check boxes.
Step 29
Click Next.
The Ready to Complete screen opens. See Figure 34.
Figure 34 Ready to Complete Screen
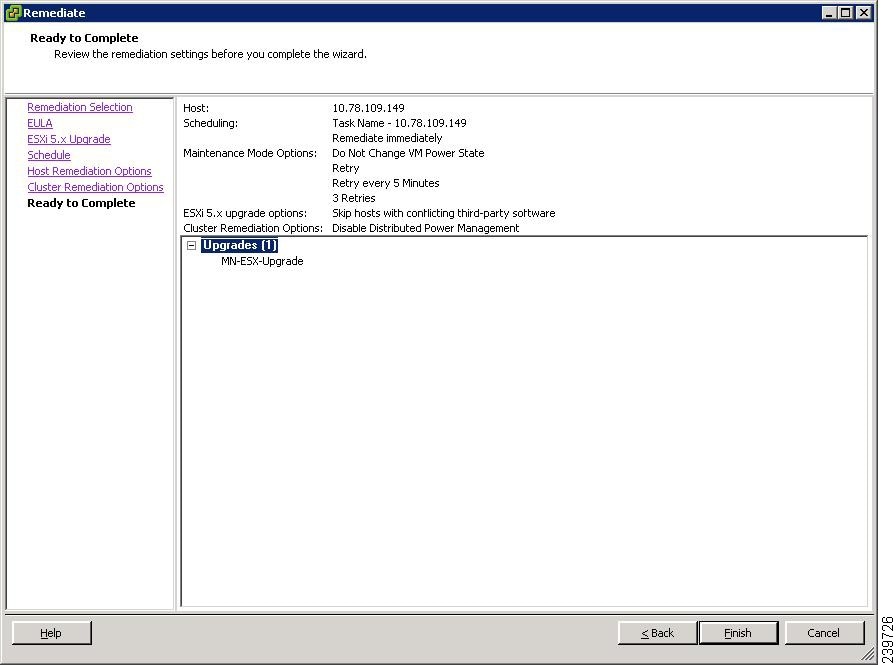
Step 30
Click Finish to begin the remediation.
Step 31
To check the host versions, click each host in the left-hand pane and confirm that 5.0.0 appears in the top-left corner of the right-hand pane and that the version information matches the contents of the Cisco Nexus 1000V Compatibility Information, Release 4.2(1)SV1(4a).
Step 32
The upgrade can also be confirmed by running the show module command on the VSM and observing that the VEMs are on the correct build.
The upgrade is complete.
Verification After the Upgrade
Step 1
To verify the build number on the ESXi host, run the following commands:
~ # vmware -vVMware ESXi 5.0.0 build-469512Step 2
To verify the upgrade on the Cisco Nexus 1000V, run the following commands:
switch# show moduleN1KV-VSM# show modMod Ports Module-Type Model Status--- ----- -------------------------------- ------------------ ------------1 0 Virtual Supervisor Module Nexus1000V active *2 0 Virtual Supervisor Module Nexus1000V ha-standby3 248 Virtual Ethernet Module NA okMod Sw Hw--- --------------- ------1 4.2(1)SV1(4a) 0.02 4.2(1)SV1(4a) 0.03 4.2(1)SV1(4a) 3.0Mod MAC-Address(es) Serial-Num--- -------------------------------------- ----------1 00-19-07-6c-5a-a8 to 00-19-07-6c-62-a8 NA2 00-19-07-6c-5a-a8 to 00-19-07-6c-62-a8 NA3 02-00-0c-00-09-00 to 02-00-0c-00-09-80 NAMod Server-IP Server-UUID Server-Name--- --------------- ------------------------------------ --------------------1 10.104.245.152 NA NA2 10.104.245.152 NA NA3 10.104.245.140 42064d20-4e52-62d1-e0ee-0b14be4388d6 mn-esxi-5.0-statefull* this terminal session
Upgrading to VMware ESXi 5.0 Patch 01
You can use the following procedures to upgrade a stateful or stateless host to ESXi 5.0 Patch 01.
This section includes the following topics:
•
Upgrading a VMware ESXi 5.0 Stateful Host to VMware ESXi 5.0 Patch 01
•
Upgrading a VMware ESXi 5.0 Stateless Host to VMware ESXi 5.0 Patch 01
Upgrading a VMware ESXi 5.0 Stateful Host to VMware ESXi 5.0 Patch 01
You can use this procedure to upgrade a VMware ESXi 5.0 GA stateful host connected to a Cisco Nexus 1000V, Release 4.2(1)SV1(4a) DVS to VMware ESXi 5.0 Patch 01 by using the esxcli command.
Step 1
Copy the ESXi 5.0 Patch 01 bundle (ESXi500-201109001.zip) to the host and enter the following command.
~ # esxcli software vib update -d /vmfs/volumes/newnfs/MN-patch01/ESXi500-201109001.zipInstallation ResultMessage: The update completed successfully, but the system needs to be rebooted for the changes to be effective.Reboot Required: trueVIBs Installed: VMware_bootbank_esx-base_5.0.0-0.3.474610, VMware_locker_tools-light_5.0.0-0.3.474610VIBs Removed: VMware_bootbank_esx-base_5.0.0-0.0.469512, VMware_locker_tools-light_5.0.0-0.0.469512VIBs Skipped: VMware_bootbank_ata-pata-amd_0.3.10-3vmw.500.0.0.469512, VMware_bootbank_ata-pata-atiixp_0.4.6-3vmw.500.0.0.469512,<========================================================================================= ===================>VMware_bootbank_scsi-qla4xxx_5.01.03.2-3vmw.500.0.0.469512, VMware_bootbank_uhci-usb-uhci_1.0-3vmw.500.0.0.469512
Upgrading a VMware ESXi 5.0 Stateless Host to VMware ESXi 5.0 Patch 01
You can use this procedure to upgrade a VMware ESXi 5.0 stateless host connected to a Cisco Nexus 1000V, Release 4.2(1)SV1(4a) DVS to VMware ESXi 5.0 Patch 01 by using the vSphere Auto Deploy PowerCLI.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•
The ESXi 5.0 GA stateless host should be connected to a Cisco Nexus 1000V Release 4.2(1)SV1(4a) DVS with a host profile attached in the vCenter Server.
•
The Host Profile Compliance should be Compliant.
•
The Answer File Status should be Complete.
For this example, the host has a rule defined with the following values in the PowerCLI:
Name : sans2-216
PatternList : {mac=c4:7d:4f:7c:a4:64}
ItemList : {mn-ga-n1k-bl1}
Where mn-ga-n1k-bl1 is an image profile containing the VMware ESXi 5.0 GA package,the VMware-fdm vib, and the Cisco Nexus 1000V vib :
VMware ESXi 5.0 GA package : ESXi-5.0.0-469512-standard
VMware-fdm vib : vSphere-HA-depot.zip
Cisco Nexus 1000V vib : VEM500-201108271.zip
Step 1
Use the PowerCLI to create an image profile for ESXi 5.0 Patch 01.
The ItemList mn-patch01-n1k-bl1 should contain the following:
–
ESXi 5.0 patch01 : ESXi-5.0.0-20110904001-standard
–
VMware-fdm vib : vSphere-HA-depot.zip
–
Cisco Nexus 1000V vib : VEM500-201108271.zip
–
Other required drivers
Step 2
Store the package to the image1 variable.
PowerCLI C:\> $image1 = Get-EsxImageProfile -Name mn-patch01-n1k-bl1Step 3
Replace the package.
PowerCLI C:\> Copy-DeployRule sans2-216 -ReplaceItem $image1Downloading esx-base 5.0.0-0.3.474610Download finished, uploading to AutoDeploy...Upload finished.Downloading tools-light 5.0.0-0.3.474610Download finished, uploading to AutoDeploy...Upload finished.Warning: Image Profile mn-patch01-n1k-bl1 contains one or more software packages that are not stateless-ready. You may experience problems when usingthis profile with Auto Deploy.Name : sans2-216PatternList : {mac=c4:7d:4f:7c:a4:64}ItemList : {mn-patch01-n1k-bl1}Step 4
Check for compliance ,
PowerCLI C:\> Test-DeployRuleSetCompliance sans2-216.cisco.comVMHost ItemList------ --------sans2-216.cisco.com {Non-compliant: mn-ga-n1k-bl1 != mn-patch01-n1k...The image is non-compliant.
Step 5
Store the output of the Test-DeployRuleSetCompliance command to the $tr variable.
PowerCLI C:\> $tr = Test-DeployRuleSetCompliance sans2-216.cisco.com------------------------------------------------------------------------------------------Step 6
Remove the non-compliant state.
PowerCLI C:\> Repair-DeployRuleSetCompliance $trStep 7
Check for compliance.
PowerCLI C:\> Test-DeployRuleSetCompliance sans2-216.cisco.comVMHost ItemList------ --------sans2-216.cisco.com {}Step 8
Reboot the host.
The host is upgraded to VMware ESXi 5.0 Patch 01.
Installing ESXi 5.0.0 Host Software Using the CLI
You can use this procedure to upgrade an ESXi host by installing a VMware patch or update with the compatible Cisco Nexus 1000V VEM software.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•
If you are using vCLI:
–
You have downloaded and installed the VMware vCLI. For information about installing vCLI, see the VMware vCLI documentation.
–
You are logged in to the remote host when vCLI is installed.

Note
The vSphere Command-Line Interface (vSphere CLI) command set allows you to enter common system administration commands against ESXi systems from any machine with network access to those systems. You can also enter most vSphere CLI commands against a vCenter Server system and target any ESXi system that the vCenter Server system manages. vSphere CLI commands are especially useful for ESXi hosts because ESXi does not include a service console.
•
If you are using the esxupdate command:
–
You are logged in to the ESX host.
•
Check the Cisco Nexus 1000V Compatibility Information, Release 4.2(1)SV1(4a), for compatible versions.
•
You have already copied the ESXi host software and VEM software installation file to the /tmp directory.
•
You know the name of the ESXi and VEM software file to be installed.
DETAILED STEPS
Step 1
Download the VEM bits and copy them to the local host.
Step 2
Determine the upgrade method that you want to use.
•
If you are using vCLI, enter the esxcli command and install the ESXi and VEM software simultaneously.

Note
When using the esxcli software vib install command, you must log in to each host and enter the command. ESXi 5.0.0 expects the VIB to be in the /var/log/vmware directory if the absolute path is not specified.
esxcli software vib install -v full-path-to-vibExample:# esxcli software vib install -v /tmp/cross_cisco-vem-v131-4.2.1.1.4.1.0-3.0.5.vibInstallation ResultMessage: Operation finished successfully.Reboot Required: falseVIBs Installed: Cisco_bootbank_cisco-vem-v131-esx_4.2.1.1.4.1.0-3.0.5VIBs Removed:VIBs Skipped:This command loads the software manually onto the host, loads the kernel modules, and starts the VEM Agent on the running system.
Step 3
Verify that the installation was successful.
[root@serialport tmp]# vmware -vVMware ESXi 5.0.0 build-469512# esxcli software vib list | grep ciscocisco-vem-v131-esx 4.2.1.1.4.1.0-3.0.5 Cisco PartnerSupported 2011-08-20~ # vem status -vPackage vssnet-esx4.1.2-00000-releaseVersion 4.2.1.1.4.1.0-1.11.1Build 1Date Wed Jul 27 04:42:14 PDT 2011Number of PassThru NICs are 0VEM modules are loadedSwitch Name Num Ports Used Ports Configured Ports MTU UplinksvSwitch0 128 2 128 1500 vmnic4DVS Name Num Ports Used Ports Configured Ports MTU Uplinksvsm-tec-mn-p 256 15 256 1500 vmnic5,vmnic2Number of PassThru NICs are 0VEM Agent (vemdpa) is running# vem version -vNumber of PassThru NICs are 0Running esx version -236512 x86_64VEM Version: 4.2.1.1.4.1.0-1.11.1VSM Version: 4.2(1)SV1(4a)System Version: VMware ESXi 5.0.0 Releasebuild-469512
Note
If the VEM Agent is not running, see the Cisco Nexus 1000V Troubleshooting Guide, Release 4.2(1)SV1(4a).
Step 4
Verify that the VEM has been upgraded by entering the following command from the VSM:
switch# show moduleMod Ports Module-Type Model Status--- ----- -------------------------------- ------------------ ------------1 0 Virtual Supervisor Module Nexus1000V active *2 0 Virtual Supervisor Module Nexus1000V ha-standby3 248 Virtual Ethernet Module NA ok4 248 Virtual Ethernet Module NA okMod Sw Hw--- ---------------- ------------------------------------------------1 4.2(1)SV1(4a) 0.02 4.2(1)SV1(4a) S0.03 4.2(1)SV1(4a) VMware ESXi 5.0.0 Releasebuild-381646 (3.0)4 4.2(1)SV1(4a) VMware ESXi 5.0.0 Releasebuild-381646 (3.0)Mod MAC-Address(es) Serial-Num--- -------------------------------------- ----------1 0
Note
The highlighted text in the previous command output confirms that the upgrade was successful.
Step 5
Do one of the following:
•
If the installation was successful, you do nothing because the installation procedure is complete.
•
If not, see the Recreating the Cisco Nexus 1000V Installation section in Cisco Nexus 1000V Troubleshooting Guide, Release 4.2(1)SV1(4a).
You have completed this procedure.
Installing or Upgrading the VEM Software Using the VUM

CautionIf removable media is still connected to the host, for example, if you have installed the VSM by using an ISO image and forgot to remove the media, then host movement to maintenance mode fails and the VUM upgrade fails.
When installing or upgrading the VEM software, VMware Update Manager (VUM) automatically selects the correct VEM software to be installed on the host.
VEM software is installed on the host in one of the following procedures:
•
When upgrading the VEM software, the VUM operation is initiated when the network administrator executes the vmware vem upgrade proceed command.
•
VUM operation is initiated when the server administrator adds a new host to the Cisco Nexus 1000V DVS.

Note
Make sure you read the "Prerequisites for Installing VEM Software" section to ensure that the VUM operation proceeds without failure.
–
If you are using VUM, the Cisco Nexus 1000V VEM software is installed automatically when the host is added to the Cisco Nexus 1000V DVS. When VEM upgrades are triggered from the VSM, the VEM software automatically upgrades on the host. To determine which VUM upgrade procedure you should follow, see the "Installing or Upgrading the VEM Software Using the VUM" section.
Installing or Upgrading the VEM Software Using the CLI
You can use this procedure to install the Cisco Nexus 1000V VEM software on an ESXi host.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•
If you are using vCLI:
–
You have downloaded and installed the VMware vCLI. For information about installing vCLI, see the VMware vCLI documentation.
–
You are logged in to the remote host where vCLI is installed.

Note
The vSphere Command-Line Interface (vCLI) command set allows you to enter common system administration commands against ESXi systems from any machine with network access to those systems. You can also enter most vCLI commands against a vCenter Server system and target any ESXi system that the vCenter Server system manages. vCLI commands are especially useful for ESXi hosts because ESXi does not include a service console.
•
If you are using the esxupdate command:
–
You are logged in to the ESX host.
•
Check the Cisco Nexus 1000V Compatibility Information, Release 4.2(1)SV1(4a) for compatible versions.
•
You have already copied the VEM software installation file to the /tmp directory.
•
You know the name of the VEM software file to be installed.
PROCEDURE
Step 1
Go to the directory where the new VEM software was copied.
[root@serialport -]# cd tmp[root@serialport tmp]#Step 2
Determine the upgrade method that you want to use and enter the appropriate command:
•
If you are using vCLI, enter the vihostupdate command and install the ESX/ ESXi and VEM software simultaneously.
•
If you are on an ESXi host running ESXi 4.0 or 4.1, enter one of the following commands:
vihostupdate --install --bundle [path to Cisco updated VEM offline bundle]" --server [vsphere host IP address]
Note
Put the host in maintenance mode before you enter the following command.
[root@serialport tmp]# vihostupdate --install --bundle VEM400-201107401.zip --server 192.0.2.0Enter username: rootEnter password:Please wait installation in progress ...The update completed successfully, but the system needs to be rebooted for the changes to be effective.[root@serialport tmp]#•
If you are using the esxupdate command, from the ESX host /tmp directory, install the VEM software as shown in the following example:

Note
When using the esxupdate command, you must log in to each host and enter the following command.
esxupdate -b [VMware offline update bundle] updateThis command loads the software manually onto the host, loads the kernel modules, and starts the VEM Agent on the running system.
Step 3
To display values with which to compare to Cisco Nexus 1000V Compatibility Information, Release 4.2(1)SV1(4a) enter the following commands:
[root@serialport tmp]# vmware -vVMware ESXi 5.0.0 build-469512The highlighted text shows the upgraded Cisco VEM.
root@serialport tmp]# esxupdate query-----Bulletin ID----- -----Installed----- ----------Summary----------ESXi400-Update01 2011-07-28T14:30:58 VMware ESXi 4.0 Update 1VEM400-201107273451115-BG 2011-07-28T14:48:36 Cisco Nexus 1000V 4.2(1)SV1(4a)[root@host212 ~]# vem status -vPackage vssnet-esx4.1.0-00000-releaseVersion 4.2.1.1.4.1.0-1.9.1Build 1Date Wed Jul 27 04:42:14 PDT 2011Number of PassThru NICs are 0VEM modules are loadedSwitch Name Num Ports Used Ports Configured Ports MTU UplinksvSwitch0 32 2 32 1500 vmnic0DVS Name Num Ports Used Ports Configured Ports Uplinksbyru-215 256 56 256 vmnic2,vmnic1Number of PassThru NICs are 0VEM Agent (vemdpa) is running[root@host212 ~]# vem version -vNumber of PassThru NICs are 0Running esx version -208167 x86_64VEM Version: 4.2.1.1.4.1.0-1.9.1VSM Version: 4.2(1)SV1(4a)System Version: VMware ESX 4.0.0 Releasebuild-208167Step 4
To display that the VEMs were upgraded, enter the following commands from the VSM.
switch# show moduleMod Ports Module-Type Model Status--- ----- -------------------------------- ------------------ ------------1 0 Virtual Supervisor Module Nexus1000V active *2 0 Virtual Supervisor Module Nexus1000V standby3 248 Virtual Ethernet Module NA okMod Sw Hw--- --------------- ------1 4.0(4)SV1(4a) 0.02 4.0(4)SV1(4a) 0.03 4.2(1)SV1(4a) VMware ESXi 4.0.0 build-208167 (1.9)Mod MAC-Address(es) Serial-Num--- -------------------------------------- ----------1 00-19-07-6c-5a-a8 to 00-19-07-6c-62-a8 NA4 02-00-0c-00-04-00 to 02-00-0c-00-04-80 NAMod Server-IP Server-UUID Server-Name--- --------------- ------------------------------------ --------------------1 10.104.62.220 NA NA4 10.104.62.217 3fa746d4-de2f-11de-bd5d-c47d4f7ca460 visor
Note
The highlighted text in the previous command output confirms that the upgrade was successful.
Step 5
Do one of the following:
•
If the installation was successful, the installation procedure is complete.
•
If the installation was not successful, see the "Recreating the Cisco Nexus 1000V Installation" section in the Cisco Nexus 1000V Troubleshooting Guide, Release 4.2(1)SV1(4a).
You have completed this procedure.
Installing a VEM on a Stateless ESXi Host
This section includes the following topics:
•
Information About a Stateless ESXi Host
•
Adding the Cisco Nexus 1000V to an ESXi Image Profile
•
Installing the VEM Software on an ESXi Stateless Host Using esxcli
•
Uninstalling the VEM Software on an ESXi Stateless Host Using esxcli
•
Installing the VEM Software on an ESXi Stateless Host Using VUM
Information About a Stateless ESXi Host

Note
A stateless deployment's PXE VLAN should be the same of the native VLAN, the management VLAN, and the system VLAN.
VMware vSphere 5.0.0 introduces the VMware Auto Deploy feature which provides the infrastructure for loading the ESXi image directly into the host's memory. If a host is configured for Auto Deploy, it does not store the image state. Instead, the image is loaded from the Auto Deploy server for every boot. A host that gets its image from an Auto Deploy server is defined as a stateless host. In this context, the image with which the host boots is identified as the image profile.
An image profile is a collection of vSphere Installation Bundles (VIBs) required for the host to operate and the image profile includes base VIBs from VMware and additional VIBs from partners.
On a stateless host, VEM software can be installed or upgraded using either the VUM or CLI.
In addition, the new or modified VEM module should also be bundled in the Image Profile from which the stateless host boots. Without this, the VEM module will not be persisted across reboot of the stateless host.
When entering the esxcli software vib install command on an ESXi 5.0.0 host, the following message displays:
Message: WARNING: Only live system was updated, the change is not persistent.
The following procedure describes how to bundle the VEM into the Image Profile and how to upgrade existing VEMs in the image profile.
For a more detailed description of the VMware Auto Deploy Infrastructure and Stateless boot process, see the "Installing ESXi using VMware Auto Deploy" chapter of the vSphere Installation and Setup, vSphere 5.0.0 document.
Adding the Cisco Nexus 1000V to an ESXi Image Profile
This section describes how to add a Cisco Nexus 1000V to an ESXi Image Profile.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•
Install and set up the VMware Auto Deploy server. See the vSphere Installation and Setup, vSphere 5.0.0 document.
•
Install the VMware PowerCLI on a Windows platform. This is required for bundling the VEM module into the image profile. For more information, see the vSphere PowerCLI Installation Guide.
•
On the same Windows platform, where VMware PowerCLI is installed:.
–
Download the image profile offline bundle, which is a .zip file, to a local file path.
–
Download the VEM offline bundle, which is a .zip file, to a local file path.

Note
In the following procedure, the image profile bundle is available as C:\ESXi-5.0.0-depot.zip and the VEM bundle is available as C:\VEM500-20110822140-BG.zip.
Step 1
Start the VMWare PowerCLI application.
Step 2
Connect to vCenter Server.
[vSphere PowerCLI] > Connect-VIServer 192.0.2.1 -User Administrator -Password XXXXXStep 3
Load the image profile offline bundle.

Note
Each image profile bundle can include multiple image profiles.
[vSphere PowerCLI] > Add-ESXSoftwareDepot c:\vmware-ESXi-5.0.0-depot.zipStep 4
List the image profiles.
[vSphere PowerCLI] > Get-EsxImageProfileName Vendor Last Modified---- ------ -------------ESXi-5.0.0-standard VMware, Inc. 2/25/2011 9:42:21 PMESXi-5.0.0-no-tools VMware, Inc. 2/25/2011 9:42:21 PMStep 5
Choose the image profile into which the VEM is to be bundled from the output of the Get-EsxImageProfile command.

Note
The image profiles will generally be in READONLY format. You need to clone the image profile before adding VEM module into it.
[vSphere PowerCLI] > New-EsxImageProfile -CloneProfile ESXi-5.0.0-standard -Name n1kv-Image
Note
The n1kv-Image is the cloned image profile of ESXi-5.0.0-standard.
Step 6
Load the Cisco Nexus 1000V VEM offline bundle.

Note
The offline bundle is a zip file which includes the n1kv-vib file.
[vSphere PowerCLI] > Add-EsxSoftwareDepot C:\VEM500-20110822140-BG.zipStep 7
Enter the following command to confirm that the n1kv-vib package is loaded.
[vSphere PowerCLI] > Get-EsxSoftwarePackage -Name cisco*Name Version Vendor Release---- ------- ------ -----------cisco-vem-v131-esx 4.2.1.1.3.24.0-3.0.8 Cisco 8/22/2011.Step 8
Bundle the n1kv-package into the cloned image profile.
[vSphere PowerCLI] > Add-EsxSoftwarePackage -ImageProfile n1kv-Image -SoftwarePackage cisco-vem-v131-esxStep 9
List all the VIBs in the cloned image profile by entering the following command:
[vSphere PowerCLI]> $img = Get-EsxImageProfile n1kv-Image[vSphere PowerCLI]> $img.vibListName Version Vendor Release Date---- ------- ------ ------------scsi-bnx2i 1.9.1d.v50.1-3vmw.500.0.0.4... VMware 6/22/2011...net-s2io 2.1.4.13427-3vmw.500.0.0.43... VMware 6/22/2011...net-nx-nic 4.0.557-3vmw.500.0.0.434219 VMware 6/22/2011...scsi-aic79xx 3.1-5vmw.500.0.0.434219 VMware 6/22/2011...sata-ata-piix 2.12-4vmw.500.0.0.434219 VMware 6/22/2011...net-e1000e 1.1.2-3vmw.500.0.0.434219 VMware 6/22/2011...net-forcedeth 0.61-2vmw.500.0.0.434219 VMware 6/22/2011...tools-light 5.0.0-0.0.434219 VMware 6/22/2011...ipmi-ipmi-msghandler 39.1-4vmw.500.0.0.434219 VMware 6/22/2011...scsi-aacraid 1.1.5.1-9vmw.500.0.0.434219 VMware 6/22/2011...net-be2net 4.0.88.0-1vmw.500.0.0.434219 VMware 6/22/2011...sata-ahci 3.0-6vmw.500.0.0.434219 VMware 6/22/2011...ima-qla4xxx 2.01.07-1vmw.500.0.0.434219 VMware 6/22/2011...ata-pata-sil680 0.4.8-3vmw.500.0.0.434219 VMware 6/22/2011...scsi-ips 7.12.05-4vmw.500.0.0.434219 VMware 6/22/2011...scsi-megaraid-sas 4.32-1vmw.500.0.0.434219 VMware 6/22/2011...scsi-mpt2sas 06.00.00.00-5vmw.500.0.0.43... VMware 6/22/2011...net-cnic 1.10.2j.v50.7-2vmw.500.0.0.... VMware 6/22/2011...ipmi-ipmi-si-drv 39.1-4vmw.500.0.0.434219 VMware 6/22/2011...esx-base 5.0.0-0.0.434219 VMware 6/22/2011...ata-pata-serverworks 0.4.3-3vmw.500.0.0.434219 VMware 6/22/2011...scsi-mptspi 4.23.01.00-5vmw.500.0.0.434219 VMware 6/22/2011...net-bnx2x 1.61.15.v50.1-1vmw.500.0.0.... VMware 6/22/2011...ata-pata-hpt3x2n 0.3.4-3vmw.500.0.0.434219 VMware 6/22/2011...sata-sata-sil 2.3-3vmw.500.0.0.434219 VMware 6/22/2011...scsi-hpsa 5.0.0-17vmw.500.0.0.434219 VMware 6/22/2011...block-cciss 3.6.14-10vmw.500.0.0.434219 VMware 6/22/2011...net-tg3 3.110h.v50.4-4vmw.500.0.0.4... VMware 6/22/2011...net-igb 2.1.11.1-3vmw.500.0.0.434219 VMware 6/22/2011...ata-pata-amd 0.3.10-3vmw.500.0.0.434219 VMware 6/22/2011...ata-pata-via 0.3.3-2vmw.500.0.0.434219 VMware 6/22/2011...net-e1000 8.0.3.1-2vmw.500.0.0.434219 VMware 6/22/2011...scsi-adp94xx 1.0.8.12-6vmw.500.0.0.434219 VMware 6/22/2011...scsi-lpfc820 8.2.2.1-18vmw.500.0.0.434219 VMware 6/22/2011...scsi-mptsas 4.23.01.00-5vmw.500.0.0.434219 VMware 6/22/2011...ata-pata-cmd64x 0.2.5-3vmw.500.0.0.434219 VMware 6/22/2011...sata-sata-svw 2.3-3vmw.500.0.0.434219 VMware 6/22/2011...misc-cnic-register 1.1-1vmw.500.0.0.434219 VMware 6/22/2011...ipmi-ipmi-devintf 39.1-4vmw.500.0.0.434219 VMware 6/22/2011...sata-sata-promise 2.12-3vmw.500.0.0.434219 VMware 6/22/2011...sata-sata-nv 3.5-3vmw.500.0.0.434219 VMware 6/22/2011...cisco-vem-v131-esx 4.2.1.1.3.24.0-3.0.8 Cisco 6/30/2011...Step 10
Export the image profile to a depot file for future use.
[vSphere PowerCLI] > Export-EsxImageProfile -ImageProfile n1kv-Image -FilePath C:\n1kv-Image.zip -ExportToBundle.Step 11
Set up the rule for the host to boot with this image profile.

Note
Any of the host parameters, such as MAC address, IPV4 IP address, or domain-name, can be used to associate an image profile with the host.
[vSphere PowerCLI] > New-deployrule -item $img -name rule-test -Pattern "mac=00:50:56:b6:03:c1"[vSphere PowerCLI] > Add-DeployRule -DeployRule rule-testStep 12
Display the configured rule to make sure the correct image profile is associated with the host.
[vSphere PowerCLI] > Get-DeployRuleSetName : rule-testPatternList : {mac=00:50:56:b6:03:c1}ItemList : {n1kv-Image}Step 13
Reboot the host.
The host contacts the Auto-Deploy server and presents the host boot parameters. The Auto Deploy server checks the rules to find the image profile associated with this host. The Auto Deploy server loads the image to the host's memory and the host boots from it.
Installing the VEM Software on an ESXi Stateless Host Using esxcli
The following procedure shows you how to install the VEM software by using the esxcli command.
Step 1
Display the VMware version and build number.
~ # vmware -vVMware ESXi 5.0.0 build-441354~ #~ # vmware -lVMware ESXi 5.0.0 GAStep 2
Log in to the ESXi stateless host.
Step 3
Copy the offline bundle to the host.
~ # esxcli software vib install -d /vmfs/volumes/newnfs/MN-VEM/VEM500-20110728153-BG-release.zipInstallation ResultMessage: WARNING: Only live system was updated, the change is not persistent.Reboot Required: falseVIBs Installed: Cisco_bootbank_cisco-vem-v131-esx_4.2.1.1.4.1.0-3.0.5VIBs Removed:VIBs Skipped:
Note
If the host is an ESXi 5.0.0 stateful host, the "Message: Operation finished successfully" line appears.
Step 4
Verify that the VIB has installed.
~ # esxcli software vib list | grep ciscocisco-vem-v131-esx 4.2.1.1.4.1.0-3.0.5 Cisco PartnerSupported 2011-08-18Step 5
Check that the VEM agent is running.
~ # vem status -vPackage vssnet-esxmn-ga-releaseVersion 4.2.1.1.4.1.0-3.0.5Build 5Date Thu Jul 28 01:37:10 PDT 2011Number of PassThru NICs are 0VEM modules are loadedSwitch Name Num Ports Used Ports Configured Ports MTU UplinksvSwitch0 128 4 128 1500 vmnic4Number of PassThru NICs are 0VEM Agent (vemdpa) is runningStep 6
Display the VEM version, VSM version, and ESXi version.
~ # vemcmd show versionVEM Version: 4.2.1.1.4.1.0-3.0.5VSM Version:System Version: VMware ESXi 5.0.0 Releasebuild-441354Step 7
Display the ESXi version and details about pass-through NICs.
~ # vem version -vNumber of PassThru NICs are 0Running esx version -441354 x86_64VEM Version: 4.2.1.1.4.1.0-3.0.5VSM Version:System Version: VMware ESXi 5.0.0 Releasebuild-441354Step 8
Add the host to the DVS by using the vCenter Server.
Step 9
Enter the show module command on the VSM.
switch# show moduleMod Ports Module-Type Model Status--- ----- -------------------------------- ------------------ ------------1 0 Virtual Supervisor Module Nexus1000V active *2 0 Virtual Supervisor Module Nexus1000V ha-standby3 248 Virtual Ethernet Module NA okMod Sw Hw--- ---------------- ------------------------------------------------1 4.2(1)SV1(4a) 0.02 4.2(1)SV1(4a) 0.03 4.2(1)SV1(4a) VMware ESXi 5.0.0 Releasebuild-441354 (3.0)Mod MAC-Address(es) Serial-Num--- -------------------------------------- ----------1 00-19-07-6c-5a-a8 to 00-19-07-6c-62-a8 NA2 00-19-07-6c-5a-a8 to 00-19-07-6c-62-a8 NA3 02-00-0c-00-03-00 to 02-00-0c-00-03-80 NAMod Server-IP Server-UUID Server-Name--- --------------- ------------------------------------ --------------------1 10.104.62.227 NA NA2 10.104.62.227 NA NA3 10.104.62.216 3fa746d4-de2f-11de-bd5d-c47d4f7ca460 sans2-216.cisco.com
Uninstalling the VEM Software on an ESXi Stateless Host Using esxcli
The following procedure shows you how to uninstall the VEM software by using the esxcli command.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•
Make sure that the host is not currently a part of any DVS by removing all of the following active ports from the DVS:
–
VMware kernel NICs
–
Virtual switch interfaces
–
Virtual NICs
· You are logged in to the ESXi host remotely by using secure shell (SSH).
Step 1
Put the host in maintenance mode.
Step 2
Enter the following command to remove the VIB.
~ # esxcli software vib remove -n cisco-vem-v131-esxRemoval ResultMessage: WARNING: Only live system was updated, the change is not persistent.Reboot Required: falseVIBs Installed:VIBs Removed: Cisco_bootbank_cisco-vem-v131-esx_4.2.1.1.4.1.0-3.0.5VIBs Skipped:
Note
If the host is an ESXi 5.0.0 stateful host, the "Message: Operation finished successfully" line appears.
Installing the VEM Software on an ESXi Stateless Host Using VUM
The following procedure shows you how to install the VEM software using VUM.
BEFORE YOU BEGIN
•
Make sure the VUM patch repository has VEM software downloaded.
Step 1
In the vCenter Server, choose Home > Update Manager > Configuration > ESX host/Cluster settings.
The ESX Host/Cluster Settings window opens. See Figure 35.
Figure 35 ESX Host/Cluster Settings WIndow
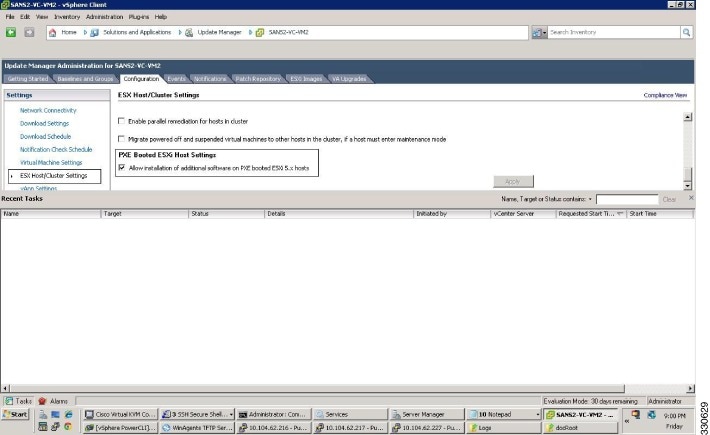
Step 2
Check the PXE Booted ESXi Host Settings check box.
Step 3
Add the host to the DVS by using the vCenter Server.
Available Documents
This section lists the documents used with the Cisco Nexus 1000V and available on Cisco.com at the following url:
http://www.cisco.com/en/US/products/ps9902/tsd_products_support_series_home.html
General Information
Cisco Nexus 1000V Documentation Roadmap, Release 4.2(1)SV1(4a)
Cisco Nexus 1000V Release Notes, Release 4.2(1)SV1(4a)
Cisco Nexus 1000V Compatibility Information, Release 4.2(1)SV1(4a)
Cisco Nexus 1010 Management Software Release Notes, Release 4.2(1)SP1(3)
Install and Upgrade
Cisco Nexus 1000V Virtual Supervisor Module Software Installation Guide, Release 4.2(1)SV1(4a)
Cisco Nexus 1000V Software Upgrade Guide, Release 4.2(1)SV1(4a)
Cisco Nexus 1000V VEM Software Installation and Upgrade Guide, Release 4.2(1)SV1(4a)
Cisco Nexus 1010 Virtual Services Appliance Hardware Installation Guide
Cisco Nexus 1010 Software Installation and Upgrade Guide, Release 4.2(1)SP1(3)
Configuration Guides
Cisco Nexus 1000V License Configuration Guide, Release 4.2(1)SV1(4a)
Cisco Nexus 1000V Getting Started Guide, Release 4.2(1)SV1(4a)
Cisco Nexus 1000V High Availability and Redundancy Configuration Guide, Release 4.2(1)SV1(4)
Cisco Nexus 1000V Interface Configuration Guide, Release 4.2(1)SV1(4a)
Cisco Nexus 1000V Layer 2 Switching Configuration Guide, Release 4.2(1)SV1(4)
Cisco Nexus 1000V Port Profile Configuration Guide, Release 4.2(1)SV1(4a)
Cisco Nexus 1000V Quality of Service Configuration Guide, Release 4.2(1)SV1(4)
Cisco Nexus 1000V Security Configuration Guide, Release 4.2(1)SV1(4a)
Cisco Nexus 1000V System Management Configuration Guide, Release 4.2(1)SV1(4a)
Cisco Nexus 1010 Software Configuration Guide, Release 4.2(1)SP1(3)
Programming Guide
Cisco Nexus 1000V XML API User Guide, Release 4.2(1)SV1(4)
Reference Guides
Cisco Nexus 1000V Command Reference, Release 4.2(1)SV1(4)
Cisco Nexus 1000V MIB Quick Reference
Cisco Nexus 1010 Command Reference, Release 4.2(1)SP1(3)
Troubleshooting and Alerts
Cisco Nexus 1000V Troubleshooting Guide, Release 4.2(1)SV1(4a)
Cisco Nexus 1000V Password Recovery Guide
Cisco NX-OS System Messages Reference
Virtual Security Gateway Documentation
Cisco Virtual Security Gateway for Nexus 1000V Series Switch
Virtual Network Management Center
Cisco Virtual Network Management Center
Network Analysis Module Documentation
Cisco Prime Network Analysis Module Software Documentation Guide, 5.1
Cisco Prime Network Analysis Module (NAM) for Nexus 1010 Installation and Configuration Guide, 5.1
Cisco Prime Network Analysis Module Command Reference Guide 5.1
Cisco Prime Network Analysis Module Software 5.1 Release Notes
Cisco Prime Network Analysis Module Software 5.1 User Guide
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, submitting a service request, and gathering additional information, see the monthly What's New in Cisco Product Documentation, which also lists all new and revised Cisco technical documentation, at:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Subscribe to the What's New in Cisco Product Documentation as a Really Simple Syndication (RSS) feed and set content to be delivered directly to your desktop using a reader application. The RSS feeds are a free service and Cisco currently supports RSS Version 2.0.
This document is to be used in conjunction with the documents listed in the section.
Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1005R)
Internet Protocol (IP) addresses used in this document are for illustration only. Examples, command display output, and figures are for illustration only. If an actual IP address appears in this document, it is coincidental.
© 2009-2011 Cisco Systems, Inc. All rights reserved.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback