Cisco Nexus Virtual Services Appliance Software Installation and Upgrade Guide, Release 4.2(1)SP1(5.1)
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- September 14, 2012
Chapter: Installing Cisco Nexus Virtual Services Appliance
- Information About Software Install
- Prerequisites
- Guidelines and Limitations
- Cisco Host Upgrade Utility Information
- Gathering Information About the Management Software
Cisco Nexus Virtual Services Appliance Software Installation
This chapter describes how to install the Cisco Nexus Virtual Services Appliance software, and includes the following sections:
- Information About Software Install
- Prerequisites
- Guidelines and Limitations
- Cisco Host Upgrade Utility Information
- Gathering Information About the Management Software
- Setting up the Primary Cisco Nexus Virtual Services Appliance
- Setting up the Secondary Cisco Nexus Virtual Services Appliance
- Example for Network Uplink Configuration
- Verifying the Cisco Nexus Virtual Services Appliance Configuration
- Getting Started With Cisco Nexus Virtual Services Appliance
- Feature History for Software Installation

Note![]() For information about upgrading Cisco Nexus 1000V software on a VSB, see theCisco Nexus 1000V Software Installation and Upgrade Guide, Release 4.2(1)SV1(5.2).
For information about upgrading Cisco Nexus 1000V software on a VSB, see theCisco Nexus 1000V Software Installation and Upgrade Guide, Release 4.2(1)SV1(5.2).
For an overview of the Cisco Nexus Virtual Services Appliance product family and procedures for configuring the software after it is installed, see the Cisco Nexus Virtual Services Appliance Software Configuration Guide, Release 4.2(1)SP1(5.1) .
Information About Software Install
Cisco Nexus Virtual Services Appliance software is pre installed as an ISO image. Use this procedure to install the Cisco Nexus Virtual Services Appliance software. The installation involves the following steps:
Step 1![]() Verify that you have the correct Cisco Integrated Management Controller (CIMC) software installed. See Verifying the CIMC Software Version.
Verify that you have the correct Cisco Integrated Management Controller (CIMC) software installed. See Verifying the CIMC Software Version.
Step 2![]() Gather information about Management Software. See Gathering Information About the Management Software.
Gather information about Management Software. See Gathering Information About the Management Software.
Step 3![]() Set up primary Cisco Nexus 1010 or Cisco Nexus 1010-X. See Setting up the Primary Cisco Nexus Virtual Services Appliance
Set up primary Cisco Nexus 1010 or Cisco Nexus 1010-X. See Setting up the Primary Cisco Nexus Virtual Services Appliance
Step 4![]() Set up the secondary Cisco Nexus 1010 or Cisco Nexus 1010-X. See Setting up the Secondary Cisco Nexus Virtual Services Appliance.
Set up the secondary Cisco Nexus 1010 or Cisco Nexus 1010-X. See Setting up the Secondary Cisco Nexus Virtual Services Appliance.
Prerequisites
Before installing Cisco Nexus Virtual Services Appliance Release 4.2(1)SP1(5.1), you must know or do the following:

Note![]() It is a recommended Cisco best practice to upgrade the firmware using the Cisco Host Upgrade Utility. Failing to do so might result in network setup failure and/or system reboots. When using the HUU upgrade menu, choose the option to upgrade the CIMC, BIOS, and all other components of the hardware. For information on the Cisco Host Upgrade Utility, seeCisco Host Upgrade Utility Information.
It is a recommended Cisco best practice to upgrade the firmware using the Cisco Host Upgrade Utility. Failing to do so might result in network setup failure and/or system reboots. When using the HUU upgrade menu, choose the option to upgrade the CIMC, BIOS, and all other components of the hardware. For information on the Cisco Host Upgrade Utility, seeCisco Host Upgrade Utility Information.
–![]() Version 1.4(3s)4 for the Cisco Nexus 1010 product family.
Version 1.4(3s)4 for the Cisco Nexus 1010 product family.
- Use the procedure described in Verifying the CIMC Software Version, to verify that you have the appropriate CIMC version installed.

Note • For firmware releases prior to version 1.4(3), the Cisco Host Upgrade Utility does not support Cisco Nexus 1010 and Cisco Nexus 1010-X. In such cases, use the Cisco Nexus Virtual Services Appliance CIMC GUI to manually update to CIMC version 1.4(3), and then use the Cisco Host Upgrade Utility to upgrade to firmware version 1.4(3s)4.
–![]() Upgrade to the latest CIMC version using the manual procedure in the Cisco UCS C-Series Servers Integrated Management Controller CLI Configuration Guide, Release 1.4.
Upgrade to the latest CIMC version using the manual procedure in the Cisco UCS C-Series Servers Integrated Management Controller CLI Configuration Guide, Release 1.4.
–![]() Upgrade the BIOS firmware version using the manual procedure in the Cisco UCS C-Series Rack-Mount Server BIOS Upgrade Guide.
Upgrade the BIOS firmware version using the manual procedure in the Cisco UCS C-Series Rack-Mount Server BIOS Upgrade Guide.
Guidelines and Limitations
Follow these guidelines and limitations when setting up the Cisco Nexus Virtual Services Appliance product family:
- The domain ID must be unique within the VLAN.
- If other Cisco Nexus Virtual Services Appliances or Cisco Nexus 1000Vs are in the same VLAN, then the domain ID must also be unique across all of them.
- When setting up the software, you configure the uplink type for your system. Once you configure an uplink type, the only way to modify it is to reload the software.
- The HA standalone role is not supported for the Cisco Nexus Virtual Services Appliance.
- Cisco Nexus Virtual Services Appliance is not supported in the non HA mode.
- It is a recommended Cisco best practice to configure a primary Cisco Nexus Virtual Services Appliance with a secondary backup. Although you can configure a primary Cisco Nexus Virtual Services Appliance without a secondary backup, this configuration in a production environment is not supported.
- It is recommended to configure the same domain ID, uplink type, control VLAN, management VLAN, control uplink, management uplink for both primary and secondary Cisco Nexus Virtual Services Appliances.
- The pairing of the Cisco Nexus Virtual Services Appliance must match the hardware platform.You cannot pair a Cisco Nexus 1010 with Cisco Nexus 1010-X.
Cisco Host Upgrade Utility Information
The Cisco Host Upgrade Utility (HUU) is a tool that you can use to upgrade the firmware on one or multiple Cisco UCS C-Series servers. The HUU detects the current version of the following components you have already installed, and guides you to upgrade them to the latest version:
- Cisco Integrated Management Controller (CIMC)
- System BIOS
- LAN on motherboard (LOM)
- RAID controllers
- Cisco UCS P81E Virtual Interface Card (VIC)
- Cisco UCS VIC 1225
- Cisco UCS VIC 1225-T
- Network adapters
You can obtain information about the minimum required version of the Cisco HUU, and how to download the HUU iso from the following sources:
- For Cisco Nexus 1010 product family, see the Cisco Host Upgrade Utility Release 1.4(3) Quick Start Guide.
You must use the instructions provided in the HUU documentation to upgrade the firmware before you install the Cisco Nexus Virtual Services Appliance 4.2(1)SP1(5.1).

Verifying the CIMC Software Version
Use this procedure to verify that you have CIMC software Version 1.2.1(b) or higher installed on your Cisco Nexus Virtual Services Appliance.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
- You must have CIMC software Version 1.2.1(b) or higher installed.
- If CIMC software Version 1.2.1(b) or higher is installed, you will see the product ID N1K-C1010 on Cisco Nexus 1010 or the product ID N1K-C1010-X on Cisco Nexus 1010-X in the output of the show hardware command. This procedure includes steps for this verification.
- You are logged in to the Cisco Nexus Virtual Services Appliance from the CLI or a Web browser.
Step 1![]() From the Cisco Nexus Virtual Services Appliance do one of the following to display the product ID (PID):
From the Cisco Nexus Virtual Services Appliance do one of the following to display the product ID (PID):
- From the CLI, view the output of the show hardware command.
Look in the Switch Hardware ID information for the PID. - From a WEB browser, open the Server Summary window and view the server properties. See Figure 2-1 for an example.
Figure 2-1 CIMC Window with Product ID (PID)
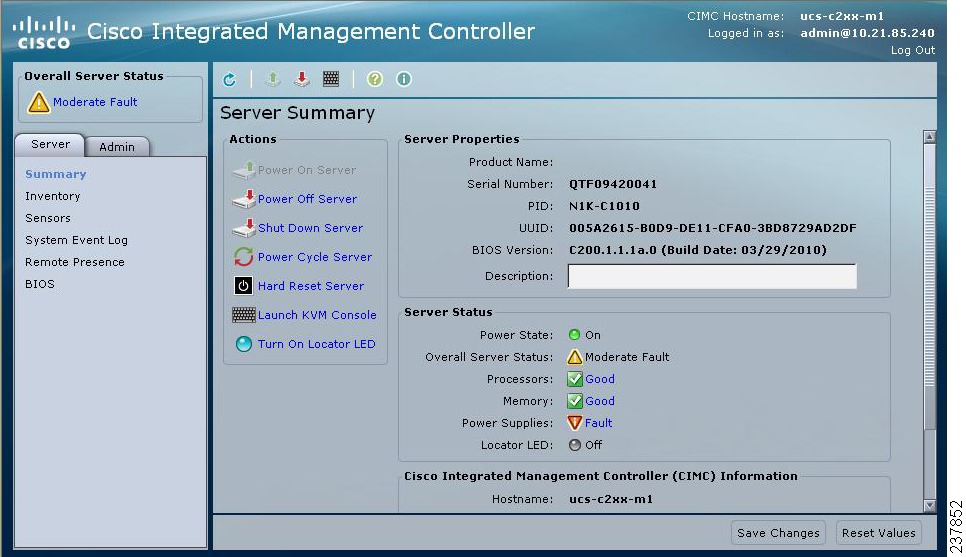
Step 2![]() Do one of the following:
Do one of the following:
- If the PID displayed is N1K-C1010 on Cisco Nexus 1010 or N1K-C1010-X on Cisco Nexus 1010-X, you can proceed with the install or upgrade to Cisco Nexus Virtual Services Appliance Release 4.2(1)SP1(5.1).
- If the PID displayed is not N1K-C1010 on Cisco Nexus 1010 or N1K-C1010-X on Cisco Nexus 1010-X, do not install or upgrade to Release 4.2(1)SP1(5.1). Instead you must replace the Cisco Nexus Virtual Services Appliance using the RMA process. See Replacing a Cisco Nexus Virtual Services Appliance.
Gathering Information About the Management Software
Before you begin the installation, you will need the following information for your Cisco Nexus Virtual Services Appliance:
Administrator Credentials
When you set up the system software, you are required to create an administrator password. Table 2-1 lists password strength guidelines:
|
|
|
|---|---|
HA Redundancy Role
The Cisco Nexus Virtual Services Appliance product family is provided in redundant pairs for high availability. When setting up the device, you configure a high availability role—primary or secondary. Table 2-2 describes these roles.

Note![]() The HA standalone role is not supported for the Cisco Nexus Virtual Services Appliance product family. Cisco Nexus Virtual Services Appliance is not supported in a non HA mode.
The HA standalone role is not supported for the Cisco Nexus Virtual Services Appliance product family. Cisco Nexus Virtual Services Appliance is not supported in a non HA mode.
HA Redundancy States
Table 2-3 describes the HA redundancy states.
Domain ID
The primary and secondary Cisco Nexus Virtual Services Appliances use the domain ID to identify each other. The Cisco Nexus Virtual Services Appliances must be in the same switching domain, and share the same management IP address.
Network Uplinks
Cisco Nexus Virtual Services Appliance product family supports two types of network uplink configurations to connect to the network.
- Flexible Network Uplink: Flexible network configuration offers complete flexibility to connect the Cisco Nexus Virtual Services Appliance product family to the network and allows you to achieve a maximum of six uplinks.
- Static Network Uplink :In a static network configuration, the Cisco Nexus Virtual Services Appliance product family is connected to the network using four fixed network uplink configurations. See Network Uplink Types.
As a result you can connect your system to the network using one of the following five supported uplink types.
- One uplink
- Two uplinks with common management and control traffic
- Two uplinks with common control and data traffic
- Three uplinks
- Flexible network uplink

Note Once you configure an uplink type, the only way to modify it is to reload the software.
See the Cisco Nexus Virtual Services Appliance Software Configuration Guide, Release 4.2(1)SP1(5.1) for more information about network uplink types.
During the installation of Cisco Nexus Virtual Services Appliance product family you can setup the flexible network uplink type or the static network uplink uplink type. If you modify the uplink type, a reload is required each time the uplink type is modified for it to take effect.
See the Cisco Nexus Virtual Services Appliance Software Configuration Guide, Release 4.2(1)SP1(5.1) for information about migrating the network uplink types.
Table 2-4 Table 2-4 shows the four supported network uplink types and the ports that carry each type of VLAN traffic.
|
|
|
|
|
|---|---|---|---|
VLANs
Control, and management VLANs are used by the Cisco Nexus Virtual Services Appliance product family for management and communication with its virtual service blades. These VLANs are added as a part of the initial setup of the management software. Control and packet VLANs are also added to each virtual service blade when it is created. The management VLAN is inherited from the Cisco Nexus Virtual Services Appliance product family by each virtual service blade.
If you modify a control, packet, or management VLAN on the Cisco Nexus Virtual Services Appliance product family , the change is effective immediately. A reload is required to effect the change of control and management VLAN on Cisco Nexus Virtual Services Appliance. However, for service continuity, you must configure the same control and packet VLANs on the hosted VSMs. Otherwise the Cisco Nexus Virtual Services Appliance loses communication with its VSMs.
Management VLAN
The management VLAN is the VLAN that forwards traffic for the management port of the Cisco Nexus Virtual Services Appliance. If your virtual service blade uses the management class of traffic, it inherits the management VLAN from the Cisco Nexus Virtual Services Appliance.
The management VLAN is used by the outside world to reach the Cisco Nexus Virtual Services Appliance management 0 interface.
The Cisco Nexus Virtual Services Appliance and its hosted Cisco Nexus 1000 VSMs share the same management VLAN in static topology. Unlike the control and packet VLANs which are set when a VSB is created, the management VLAN is inherited. In a static topology, the management VLAN on a VSB cannot be changed. Since the management VLAN is inherited from the Cisco Nexus Virtual Services Appliance, if you change management VLAN for Cisco Nexus Virtual Services Appliance, then the change is applied to both the Cisco Nexus Virtual Services Appliance and all of its hosted Cisco Nexus 1000 VSMs in next reload.
However, this constraint does not exist in flexible topology and the management VLAN of a VSB can be different from the Cisco Nexus Virtual Services Appliance host.
Control VLAN
The control VLAN is a Layer 2 interface used for communication between the redundant Cisco Nexus Virtual Services Appliances. This interface handles low-level control packets such as heartbeats as well as any configuration data that needs to be exchanged between the Cisco Nexus 1010s.
Setting up the Primary Cisco Nexus Virtual Services Appliance
You can use this procedure to set up the management software for the following:
It is a recommended Cisco best practice to configure a primary Cisco Nexus Virtual Services Appliance with a secondary backup. Although you can configure a primary Cisco Nexus Virtual Services Appliance without a secondary backup, this configuration in a production environment is not supported.
BEFORE YOU BEGIN
–![]() HA role (primary or secondary)
HA role (primary or secondary)
If you do not specify an HA role, then the role is configured as primary.
–![]() Management 0 IP address
Management 0 IP address
This is the IP address of the management interface that appears as the mgmt0 port on the appliance.
DETAILED STEPS
Step 1![]() Use one of the following methods to log in to the Cisco Nexus Virtual Services Appliance.
Use one of the following methods to log in to the Cisco Nexus Virtual Services Appliance.
The setup wizard starts automatically.
---- System Admin Account Setup ----
Enter the password for "admin":
Confirm the password for "admin":
---- System Admin Account Setup ----
Enter the password for "admin":
Confirm the password for "admin":
Step 2![]() When asked, enter and confirm the Administrator password.
When asked, enter and confirm the Administrator password.
---- System Admin Account Setup ---- Confirm the password for
Enter the password for "admin":
"admin":
Step 3![]() When asked, enter the HA role. If you do not specify a role, then primary is assigned.
When asked, enter the HA role. If you do not specify a role, then primary is assigned.
Enter HA role[primary/secondary]: primary

Note The HA standalone role is not supported for the Cisco Nexus Virtual Services Appliance product family. Cisco Nexus Virtual Services Appliance is not supported in a non HA mode
Step 4![]() When asked, enter the uplink type.To specify static network uplink, enter a value from 1-4. To specify flexible network uplink, enter the value 5.
When asked, enter the uplink type.To specify static network uplink, enter a value from 1-4. To specify flexible network uplink, enter the value 5.

Note Once you configure an uplink type, the only way to modify it is to reload the software.
Step 5![]() When asked, enter the VLAN ID for the control VLAN.
When asked, enter the VLAN ID for the control VLAN.
Step 6![]() When asked, enter control uplink.
When asked, enter control uplink.
Step 7![]() When asked, enter the domain ID.
When asked, enter the domain ID.
Step 8![]() When asked, enter the VLAN ID for the management VLAN.
When asked, enter the VLAN ID for the management VLAN.
Step 9![]() When asked, enter management uplink.
When asked, enter management uplink.
Step 10![]() When you have completed this process, the Cisco Nexus Virtual Services Appliance software saves the configuration and automatically reboots to configure the network uplinks.
When you have completed this process, the Cisco Nexus Virtual Services Appliance software saves the configuration and automatically reboots to configure the network uplinks.
The new configuration is saved into nonvolatile storage, after which the running and the startup copies of the configuration are identical.
After reboot, the default static or flexible topology will be configured. See Figure 2-2 for default flexible network uplink configuration. For more information, see the Cisco Nexus Virtual Services Appliance Software Configuration Guide, Release 4.2(1)SP1(5.1) .
Figure 2-2 Default Flexible Network Uplink Configuration without vPC /VSS
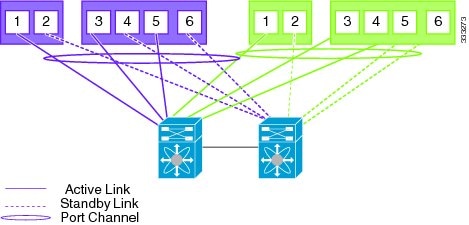
Figure 2-3 Default Flexible Network Uplink Configuration with vPC /VSS

Step 11![]() When asked if you want to enter the basic configuration dialog, respond yes .
When asked if you want to enter the basic configuration dialog, respond yes .
Step 12![]() When asked to create another Login account, answer no .
When asked to create another Login account, answer no .
Create another login account (yes/no) [n]: no
Step 13![]() When asked to configure a read-only SNMP community string, answer no .
When asked to configure a read-only SNMP community string, answer no .
Configure read-only SNMP community string (yes/no) [n]: no
Step 14![]() When asked to configure a read-write SNMP community string, answer no .
When asked to configure a read-write SNMP community string, answer no .
Configure read-write SNMP community string (yes/no) [n]:
Step 15![]() Enter a name for the appliance.
Enter a name for the appliance.
Step 16![]() When asked to configure out-of-band management, answer yes and then enter the management 0 IPv4/IPv6 address.
When asked to configure out-of-band management, answer yes and then enter the management 0 IPv4/IPv6 address.
This is the IP address of the management interface that appears as the mgmt0 port on the appliance.
Continue with Out-of-band (mgmt0) management configuration? [yes/no] [y]: yes
Mgmt0 IP address type V4/V6? (V4): V4
Step 17![]() When asked to configure the default gateway, answer yes .
When asked to configure the default gateway, answer yes .
Configure the default-gateway: (yes/no) [y]: yes
IPv4 address of the default gateway: 45.45.45.1
Step 18![]() When asked to configure advanced IP options, answer no .
When asked to configure advanced IP options, answer no .
Configure Advanced IP options (yes/no)? [n]: no
Step 19![]() When asked to enable the Telnet service, answer
When asked to enable the Telnet service, answer no .
Enable the telnet service? (yes/no) [y]: no
Step 20![]() When asked to enable the SSH service, answer yes and then enter the key type and number of key bits.
When asked to enable the SSH service, answer yes and then enter the key type and number of key bits.
Enable the ssh service? (yes/no) [y]: yes
Type of ssh key you would like to generate (dsa/rsa) : rsa
Number of key bits <768-2048> : 1024
Step 21![]() When asked to enable the HTTP server, answer yes
When asked to enable the HTTP server, answer yes
Step 22![]() When asked to configure the NTP server, answer no .
When asked to configure the NTP server, answer no .
The configuration is summarized.
Configure NTP server? (yes/no) [n]: no
Step 23![]() Do one of the following:
Do one of the following:
- If you do not want to edit the configuration answer no and continue with the next step.
- If you want to edit the configuration, answer yes and return to Step 12 to revisit each command.
Step 24![]() When asked to use and save this configuration, answer yes .
When asked to use and save this configuration, answer yes .

Use this configuration and save it? (yes/no) [y]: yes
The new configuration is saved into nonvolatile storage, after which the running and the startup copies of the configuration are identical.

Note You can use the setup routine to update the configuration done in Step 12 through Step 24 at any time by entering the setup command in EXEC mode. Once setup begins, press Enter to skip a command. Use ctrl-c to skip the remaining commands.
Step 25![]() You have completed this procedure. You can verify the configuration using the following command:
You have completed this procedure. You can verify the configuration using the following command:
Setting up the Secondary Cisco Nexus Virtual Services Appliance
You can use this procedure to set up the management software for the secondary Cisco Nexus Virtual Services Appliance in a redundant pair.
It is recommended to configure the same domain ID, uplink type, control VLAN, management VLAN, control uplink, management uplink for both primary and secondary Cisco Nexus Virtual Services Appliances.
DETAILED STEPS
Step 1![]() When asked, enter and confirm the Administrator password.
When asked, enter and confirm the Administrator password.
---- System Admin Account Setup ---- Confirm the password for
Enter the password for "admin":
"admin":
Step 2![]() When asked, enter the HA role.
When asked, enter the HA role.
Enter HA role[primary/secondary]: secondary
Step 3![]() When asked, enter the uplink type.
When asked, enter the uplink type.

Note Once you configure an uplink type, the only way to modify it is to reload the software.
Step 4![]() When asked, enter the VLAN ID for the control VLAN.
When asked, enter the VLAN ID for the control VLAN.
Step 5![]() When asked, enter control uplink type.
When asked, enter control uplink type.
Step 6![]() When asked, enter the domain ID.
When asked, enter the domain ID.
Step 7![]() When asked, enter the VLAN ID for the management VLAN.
When asked, enter the VLAN ID for the management VLAN.
Step 8![]() When asked, enter management uplink type.
When asked, enter management uplink type.
The following things occur on the switch:
- The new configuration is saved into nonvolatile storage, after which the running and the startup copies of the configuration are identical.
- The system reboots to configure the network uplinks.
- The system restarts and synchronizes its configuration with the primary Cisco Nexus 1000V.
Step 9![]() You have completed this procedure. You can verify the configuration using the following command:
You have completed this procedure. You can verify the configuration using the following command:
Example for Network Uplink Configuration
The following example shows how to configure flexible network uplink configuration during installation:
The following example shows how to configure static network uplink configuration during installation:
Verifying the Cisco Nexus Virtual Services Appliance Configuration
To verify the Cisco Nexus Virtual Services Appliance configuration, use the following commands:
|
|
|
|---|---|
Displays the Cisco Nexus Virtual Services Appliance running configuration. See Example 2-1 on page 2-19 . |
|
Displays the redundancy state (active or standby) and the redundancy role (primary or secondary) for the Cisco Nexus Virtual Services Appliances. See Example 2-2 on page 2-21 . |
|
Displays the domain information for the Cisco Nexus Virtual Services Appliance: See Example 2-3 on page 2-21 . |
|
Displays uplink connectivity for the active or standby Cisco Nexus Virtual Services Appliance. See Example 2-4 on page 2-21 . |
Example 2-1 Setup Configuration
This example shows how to display and verify the Cisco Nexus Virtual Services Appliance setup configuration:
Example 2-4 CDP neighbors (standby)
Getting Started With Cisco Nexus Virtual Services Appliance
After you complete the software installation, you can configure the Cisco Nexus Virtual Services Appliance product family. See the Cisco Nexus Virtual Services Appliance Software Configuration Guide, Release 4.2(1)SP1(5.1) for more information
The following are the basic steps in the software configuration process.
Step 1![]() Configuring port channels for flexible network uplink. Use this procedure to configure port channels after you set up the flexible network uplink type.
Configuring port channels for flexible network uplink. Use this procedure to configure port channels after you set up the flexible network uplink type.
Step 2![]() Setting up remote management. Use this procedure to set up remote management in your startup configuration for use in recovering an unreachable Cisco Nexus Virtual Services Appliance.
Setting up remote management. Use this procedure to set up remote management in your startup configuration for use in recovering an unreachable Cisco Nexus Virtual Services Appliance.
Step 3![]() Do one of the following to add a service blades to the new Cisco Nexus Virtual Services Appliance :
Do one of the following to add a service blades to the new Cisco Nexus Virtual Services Appliance :
- Create a new virtual service blade.
- Migrate an existing VSM from a VM to the Cisco Nexus Virtual Services Appliance.
Feature History for Software Installation
This section provides the software installation and upgrade release history.
|
|
|
|
|---|---|---|
 Feedback
Feedback