Cisco Nexus 1010 Software Configuration Guide, Release 4.2(1)SP1(4)
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- February 20, 2012
Chapter: Overview
- Information About Cisco Nexus 1010 Product Family
- Comparison with a Virtual Machine
- Cisco Integrated Management Controller
- Virtual Service Blades
- Uplinks
- Traffic Classification
- Options for Connecting to the Network
- Topology 5: Flexible Network Uplink Configuration
- Topology 1: Single Uplink
- Topology 2: Two Uplinks—1) Management and Control and 2) Data
- Topology 3: Two Uplinks—1) Management and 2) Control and Data
- Topology 4: Three Uplinks—1) Management, 2) Control, and 3) Data
Overview
This chapter describes the Cisco Nexus 1010 product family and hosted virtual service blades. This chapter includes the following sections:
•![]() Information About Cisco Nexus 1010 Product Family
Information About Cisco Nexus 1010 Product Family
•![]() Comparison with a Virtual Machine
Comparison with a Virtual Machine
•![]() Cisco Integrated Management Controller
Cisco Integrated Management Controller
Information About Cisco Nexus 1010 Product Family
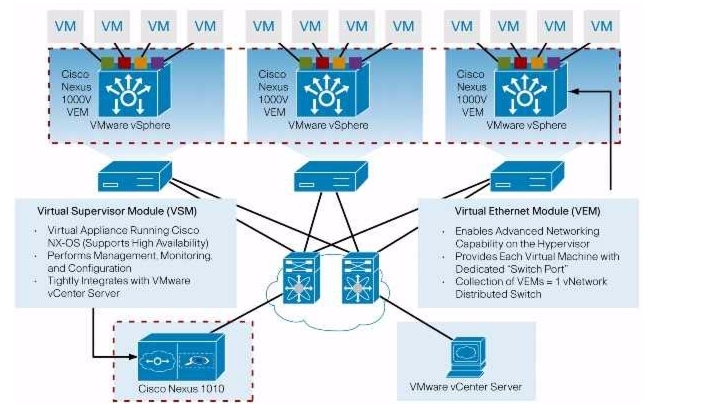
The Cisco Nexus 1010 product family includes Cisco Nexus 1010 and Cisco Nexus 1010-X. The Cisco Nexus 1010 product family are networking appliances that can hosts up to six Cisco Nexus 1000V virtual service blades (VSBS) on Cisco Nexus 1010 and upto ten Cisco Nexus 1000V virtual service blades (VSBS) on Cisco Nexus 1010-X. Cisco Nexus 1010 product family supports VSBs like Cisco Nexus 1000V Virtual Supervisor Module (VSM), Network Analysis Module (NAM), Virtual Security Gateway(VSG), and Data Center Network Management Module (DCNM).
The Cisco Nexus 1010 and Cisco Nexus 1010-X provides dedicated hardware for the VSM. VSMs that were hosted on VMware virtual machines can now be hosted on a Cisco Nexus 1010 or Cisco Nexus 1010-X appliance. This allows you to install and manage the VSM like a standard Cisco switch. The services (VSM, VSG,DCNM, or NAM) managed by the Cisco Nexus 1010 product family are called virtual service blades (VSBs). For more information about VSBs, see the "Virtual Service Blades" section.
Figure 1-1 shows how the Cisco Nexus 1010 hosts a Cisco Nexus 1000V VSM and its VEMs in your network.
Figure 1-1 Cisco Nexus 1010 Virtual Services Appliance Architecture
Cisco Nexus 1010 High Availability
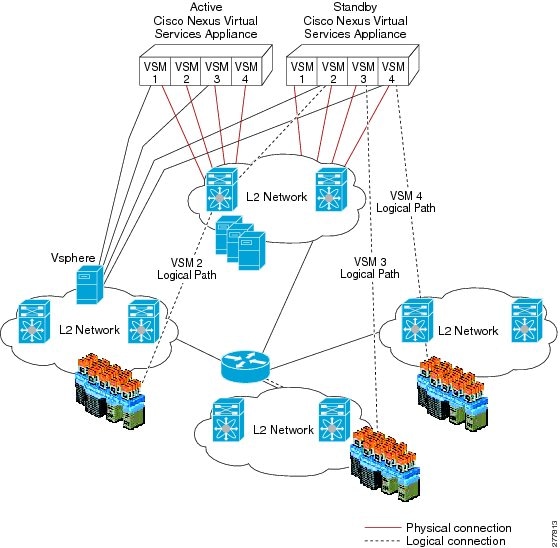
Cisco Nexus 1010 supports High Availability. Two Cisco Nexus 1010 can form a HA pair to provide high availability. If control connectivity is lost for the Cisco Nexus 1010, but management connectivity is preserved, the active Cisco Nexus 1010 reloads the standby once. The standby comes up in wait state until control connectivity is restored. In a HA pair, the active and standby Cisco Nexus 1010 uses control connectivity to synchronize data.
Cisco Nexus 1010 supports the following two forms of high availability concurrently:
•![]() Active-Standby in Management Deployment: The active Cisco Nexus 1010 is reachable over the network and majority of the commands are supported only on the active Cisco Nexus 1010. Standby Cisco Nexus 1010 is not reachable over the IP network, but can be accessed through the active Cisco Nexus 1010 or directly through serial connection.
Active-Standby in Management Deployment: The active Cisco Nexus 1010 is reachable over the network and majority of the commands are supported only on the active Cisco Nexus 1010. Standby Cisco Nexus 1010 is not reachable over the IP network, but can be accessed through the active Cisco Nexus 1010 or directly through serial connection.
•![]() Active-Active in VSB Deployment: When you deploy a VSB on Cisco Nexus 1010, you can deploy the VSB on either the active or the standby Cisco Nexus 1010 and the VSBs can be active on both the active and standby Cisco Nexus 1010. This helps balance the distribution of traffic as well as reduce the potential fault domain.
Active-Active in VSB Deployment: When you deploy a VSB on Cisco Nexus 1010, you can deploy the VSB on either the active or the standby Cisco Nexus 1010 and the VSBs can be active on both the active and standby Cisco Nexus 1010. This helps balance the distribution of traffic as well as reduce the potential fault domain.
Figure 1-2 shows the HA components and the communication links between them.
Figure 1-2 Cisco Nexus 1010 HA Components and Communication Links
Comparison with a Virtual Machine
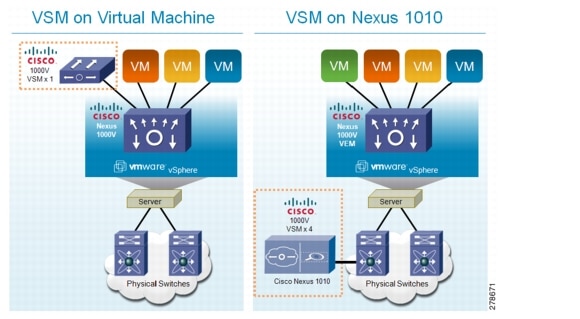
Table 1-1 compares running a VSM on a Cisco Nexus 1010 with running a VSM on a virtual machine.
|
|
|
|
|
|---|---|---|---|
Host (ESX or ESXi) Management Capacity |
64 |
3841 |
6402 |
VSM with Cisco NX-OS high availability |
Yes |
Yes |
Yes |
VEM running on vSphere 4 Enterprise Plus |
Yes |
Yes |
Yes |
Cisco Nexus 1000 features and scalability |
Yes |
Yes |
Yes |
Software-only switch |
Yes |
No |
No |
Dedicated services appliance, such as Cisco NAM |
No |
Yes |
Yes |
Installation like a standard Cisco switch |
No |
Yes |
Yes |
Network Team manages the switch hardware |
No |
Yes |
Yes |
1 64 hosts per VSM X 4 VSMs 2 64 hosts per VSM X 4 VSMs |
Figure 1-3 compares running a VSM on a Cisco Nexus 1010 with running a VSM on a virtual machine.
Figure 1-3 VM and Cisco Nexus 1010 Comparison
Cisco Integrated Management Controller
The Cisco Integrated Management Controller (CIMC) is a software interface included with the Cisco Nexus 1010. CIMC allows you to configure serial over LAN (SoL) access and set up remote management in the event the device becomes unreachable. For more information about remote management, see the Cisco Nexus 1010 Software Installation and Upgrade Guide, Release 4.2(1)SP1(4).
When installing the Cisco Nexus 1010 or Cisco Nexus 1010-X, you have the option to configure the CIMC interface. To configure the CIMC software while installing the Cisco Nexus 1010, see the Cisco Nexus 1010 Virtual Services Appliance Hardware Installation Guide.
Virtual Service Blades
The services (VSM, NAM, VSG, DCNM) hosted, created, and managed by the Cisco Nexus 1010 product family are called virtual service blades (VSBs). Cisco Nexus 1010 can hosts up to six virtual service blades (VSBs) and Cisco Nexus 1010-X can host upto 10 VSBs.
VSBs are created using ISO or OVA image files found in the Cisco Nexus 1010 bootflash repository. The ISO defines the following for a VSB:
•![]() Required number of interfaces
Required number of interfaces
•![]() Required hard disk emulation
Required hard disk emulation
•![]() Disk and RAM defaults
Disk and RAM defaults
•![]() Type of virtual service blade
Type of virtual service blade
–![]() VSM
VSM
–![]() NAM
NAM
–![]() VSG
VSG
–![]() DCNM
DCNM
For more information about VSBs, see the "Configuring Virtual Service Blades" section.
Weighting Matrix to determine maximum capacity of various VSBs on the Cisco Nexus 1010 product family.
|
|
|
|
|
|
|
|---|---|---|---|---|---|
Cisco Nexus 1010 |
1 |
1 |
2 |
2 |
<=6 |
Cisco Nexus 1010-X |
1 |
1 |
2 |
2 |
<=10 |
Example Cisco Nexus 1010 configurations using the weighting matrix:
•![]() 6 VSMs
6 VSMs
•![]() 6 VSGs
6 VSGs
•![]() 3 VSMs, 3 VSGs
3 VSMs, 3 VSGs
•![]() 1 VSM, 1 VSG, 1 NAM, 1 DCNM
1 VSM, 1 VSG, 1 NAM, 1 DCNM
Example Cisco Nexus 1010-X configurations using the weighting matrix:
•![]() 10 VSMs
10 VSMs
•![]() 10 VSGs
10 VSGs
•![]() 5 VSMs, 5 VSGs
5 VSMs, 5 VSGs
•![]() 3 VSMs, 3 VSG, 1 NAM, 1 DCNM
3 VSMs, 3 VSG, 1 NAM, 1 DCNM
Uplinks
This section describes the uplinks that you connected during your installation of the hardware. For more information about these connections and the prerequisites for the switches that are upstream from your Cisco Nexus 1010, see the Cisco Nexus 1010 Virtual Services Appliance Hardware Installation Guide.
This section includes the following topics:
•![]() Options for Connecting to the Network
Options for Connecting to the Network
•![]() Topology 5: Flexible Network Uplink Configuration
Topology 5: Flexible Network Uplink Configuration
•![]() Topology 2: Two Uplinks—1) Management and Control and 2) Data
Topology 2: Two Uplinks—1) Management and Control and 2) Data
•![]() Topology 3: Two Uplinks—1) Management and 2) Control and Data
Topology 3: Two Uplinks—1) Management and 2) Control and Data
•![]() Topology 4: Three Uplinks—1) Management, 2) Control, and 3) Data
Topology 4: Three Uplinks—1) Management, 2) Control, and 3) Data
Traffic Classification
Table 1-2 lists and describes the classes of network traffic carried on the Cisco Nexus 1010 uplinks:
Options for Connecting to the Network
Table 1-3 describes the available uplink configurations.
You choose the type of uplink for your network using the "Setting Up the Management Software" procedure.

Note ![]() Once you configure an uplink type, the only way to modify it is to reload the software.
Once you configure an uplink type, the only way to modify it is to reload the software.
Topology 5: Flexible Network Uplink Configuration
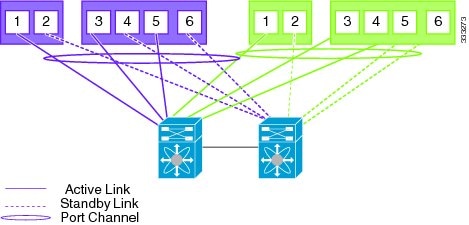
Flexible network configuration offers complete flexibility to connect Cisco Nexus 1010 or Cisco Nexus 1010-X to the network, and allowing flexible deployment of the VSBs on the Cisco Nexus 1010 product family. Flexible configuration thus enables appropriate traffic segregation policies like VSB traffic segregation. The default flexible network uplink configuration is the basic configuration with each physical port acting as an individual uplink. See Figure 1-4. You can then make changes to the default configuration by adding ports to a port channel or by assigning uplinks to a VSB interface.
For more information on flexible network uplink configuration, see Flexible Network Uplink Configuration.
Figure 1-4 Topology 5: Without vPC or VSS
(Default)
Figure 1-5
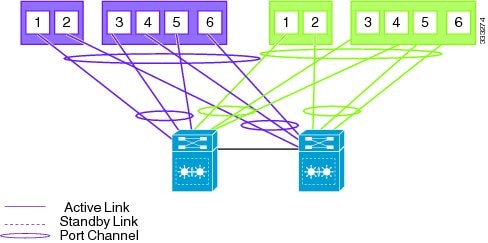
Topology 5: With vPC or VSS (Default)
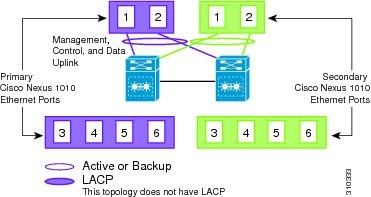
Topology 1: Single Uplink
In this topology, your Cisco Nexus 1010 pair connects to your network in two uplinks as shown in the following figures:
•![]() Figure 1-6, without vPC or VSS
Figure 1-6, without vPC or VSS
•![]() Figure 1-7, with vPC or VSS
Figure 1-7, with vPC or VSS
For detailed information about connecting uplinks, see the Cisco Nexus 1010 Virtual Services Appliance Hardware Installation Guide.
Figure 1-6 Topology 1: Single Uplink Without vPC or VSS
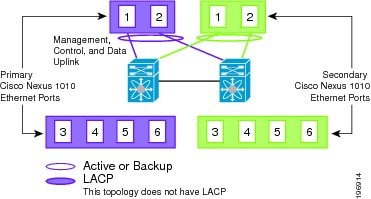
Figure 1-7 Topology 1: Single Uplink With vPC or VSS
Topology 2: Two Uplinks—1) Management and Control and 2) Data
In topology 2, six Gigabit Ethernet ports on each Cisco Nexus 1010 create two uplinks. The ports in each Cisco Nexus 1010 internally form a port channel and network traffic is load balanced based on the source MAC algorithm.
LACP must be configured on the upstream switches connecting to ports 3, 4, 5, and 6.
In topology 2, your Cisco Nexus 1010 pair connects to your network in two uplinks as shown in the following figures:
•![]() Figure 1-8, without vPC or VSS
Figure 1-8, without vPC or VSS
•![]() Figure 1-9, with vPC or VSS
Figure 1-9, with vPC or VSS
For detailed information about connecting uplinks, see the Cisco Nexus 1010 Virtual Services Appliance Hardware Installation Guide.
Figure 1-8 Topology 2: Two Uplinks Without vPC or VSS—
1) Management and Control Uplink, and 2) Data Uplink
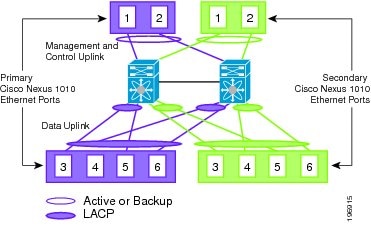
Figure 1-9 Topology 2: Two Uplinks With vPC or VSS—
1) Management and Control Uplink, and 2) Data Uplink
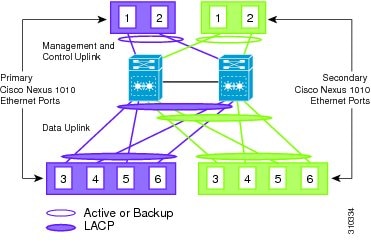
Topology 3: Two Uplinks—1) Management and 2) Control and Data
In topology 3, the ports in each Cisco Nexus 1010 internally form a port channel and network traffic is load balanced based on the source MAC algorithm.
LACP must be configured on the upstream switches connecting to ports 3, 4, 5, and 6.
In topology 3, your Cisco Nexus 1010 pair connects to your network in two uplinks as shown in the following figures:
•![]() Figure 1-10, without vPC or VSS
Figure 1-10, without vPC or VSS
•![]() Figure 1-11, with vPC or VSS
Figure 1-11, with vPC or VSS
For detailed information about connecting uplinks, see the Cisco Nexus 1010 Virtual Services Appliance Hardware Installation Guide.
Figure 1-10 Topology 3: Two Uplinks Without vPC or VSS—
1) Management Uplink, and 2) Control and Data Uplink
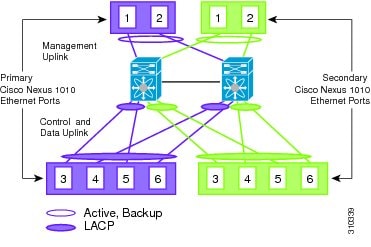
Figure 1-11 Topology 3: Two Uplinks With vPC or VSS—
1) Management Uplink, and 2) Control and Data Uplink

Topology 4: Three Uplinks—1) Management, 2) Control, and 3) Data
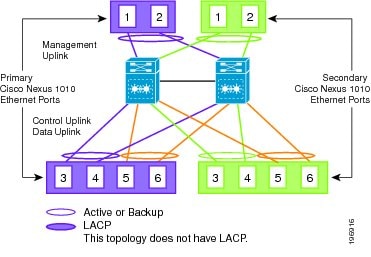
In topology 4, six Gigabit Ethernet ports on each Cisco Nexus 1010 create three uplinks as shown in one of the following figures:
•![]() Figure 1-12, without vPC or VSS
Figure 1-12, without vPC or VSS
•![]() Figure 1-13, with vPC or VSS
Figure 1-13, with vPC or VSS
For detailed information about connecting uplinks, see the Cisco Nexus 1010 Virtual Services Appliance Hardware Installation Guide.
Figure 1-12 Topology 4: Three Uplinks Without vPC or VSS
1) Management, 2) Control, and 3) Data
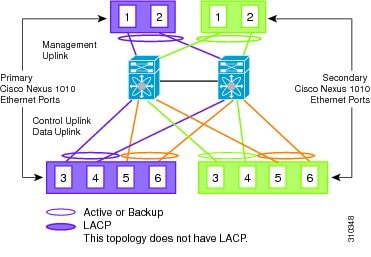
Figure 1-13 Topology 4: Three Uplinks With vPC or VSS
1) Management, 2) Control, and 3) Data
 Feedback
Feedback