- Overview
- Tools
- Installation
- Licenses
- High Availability
- VSM and VEM Modules
- Ports
- Port Profiles
- Port Channels and Trunking
- Layer 2 Switching
- VLAN
- Private VLAN
- NetFlow
- ACL
- Quality of Service
- SPAN
- Multicast IGMP
- DHCP, DAI, and IPSG
- System
- Network Segmentation Manager
- Ethanalyzer
- Before Contacting Technical Support
Cisco Nexus 1000V for Microsoft Hyper-V Troubleshooting Guide, Release 5.2(1)SM1(5.1)
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- January 31, 2012
Chapter: Layer 2 Switching
Layer 2 Switching
This chapter describes how to identify and resolve problems that relate to Layer 2 switching.
Information About Layer 2 Ethernet Switching
The Cisco Nexus 1000V provides a distributed, Layer 2 virtual switch that extends across many virtualized hosts.
It consists of two components:
- Virtual Supervisor Module (VSM), which is also known as the control plane (CP), acts as the supervisor and contains the Cisco CLI, configuration, and high-level features.
- Virtual Ethernet Module (VEM), which is also known as the data plane (DP), acts as a line card and runs in each virtualized server to handle packet forwarding and other localized functions.
Port Model
This section describes the following port perspectives:
Viewing Ports from the VEM
The Cisco Nexus 1000V differentiates between virtual and physical ports on each of the VEMs. Figure 10-1 shows how ports on the Cisco Nexus 1000V switch are bound to physical and virtual Microsoft Hyper-V ports within a VEM.
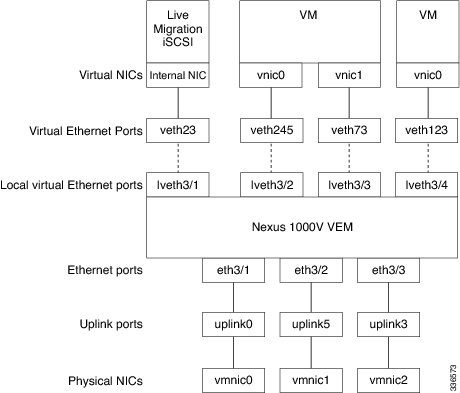
On the virtual side of the switch, three layers of ports are mapped together:
- Virtual NICs—There are two types of Virtual NICs. The virtual NIC (vnic) is part of the VM and represents the physical port of the host that is plugged into the switch. Internal NICs are used by the hypervisor for internal purposes. Each type maps to a vEth port within the Cisco Nexus 1000V.
- Virtual Ethernet Ports (VEth)—A vEth port is a port on the Cisco Nexus 1000V distributed virtual switch. The Cisco Nexus 1000V has a flat space of vEth ports 0..N. The virtual cable plugs into these vEth ports that are moved to the host that is running the VM.
vEth ports are assigned to port groups.
- Local virtual Ethernet ports (lveth)—Each host has a number of local vEth ports. These ports are dynamically selected for vEth ports that are needed on the host.
These local ports do not move and you can address them by the module-port number method.
Each physical NIC is represented by an interface called a vmnic. The vmnic number is allocated during Microsoft Hyper-V installation, or when a new physical NIC is installed, and remains the same for the life of the host.
Each uplink port on the host represents a physical interface. The port acts like an local vEth port, but because physical ports do not move between hosts, the mapping is 1:1 between an uplink port and a vmnic.
Each physical port that is added to the Cisco Nexus 1000V switch appears as a physical Ethernet port, just as it would on a hardware-based switch.
The uplink port concept is handled entirely by the hypervisor and is used to associate port configuration with vmnics. There is no fixed relationship between the uplink number and vmnic number, and the uplink and the vmnic numbers can be different on different hosts and can change throughout the life of the host. On the VSM, the Ethernet interface number, such as ethernet 2/4, is derived from the vmnic number, not the uplink number.
Viewing Ports from the VSM
Figure 10-2 shows the VSM view of the ports.
Port Types
The following types of ports are available:
–![]() vNICs of a Virtual Machine on the hypervisor.
vNICs of a Virtual Machine on the hypervisor.
–![]() Internal NICs on the hypervisor.
Internal NICs on the hypervisor.
- eths (physical Ethernet interfaces)—Correspond to the physical NICs on the hypervisor.
- Po (port channel interfaces)—The physical NICs of a hypervisor can be bundled into a logical interface. This logical bundle is referred to as a port channel interface.
For more information about Layer 2 switching, see the Cisco Nexus 1000V for Microsoft Hyper-V Layer 2 Switching Configuration Guide, Release 5.2(1)SM1(5.1) .
Problems with Layer 2 Switching
This section describes how to troubleshoot Layer 2 problems and lists troubleshooting commands. This section includes the following topics:
- Verifying a Connection Between VEM Ports
- Verifying a Connection Between VEMs
- Isolating Traffic Interruptions
Verifying a Connection Between VEM Ports
Step 1![]() View the state of the VLANs associated with the port by entering the show vlan command on the VSM. If the VLAN associated with a port is not active, the port might be down. In this case, you must create the VLAN and activate it.
View the state of the VLANs associated with the port by entering the show vlan command on the VSM. If the VLAN associated with a port is not active, the port might be down. In this case, you must create the VLAN and activate it.
Step 2![]() To see the state of the port on the VSM, enter the show interface brief command.
To see the state of the port on the VSM, enter the show interface brief command.
Step 3![]() Display the ports that are present on the VEM, their local interface indices, VLAN, type (physical or virtual), CBL state, port mode, and port name by entering the module vem module-number execute vemcmd show port command.
Display the ports that are present on the VEM, their local interface indices, VLAN, type (physical or virtual), CBL state, port mode, and port name by entering the module vem module-number execute vemcmd show port command.
The key things to look for in the output are as follows:
- State of the port.
- CBL.
- Mode.
- Attached device name.
- The LTL of the port that you are trying to troubleshoot. It will help you identify the interface quickly in other VEM commands where the interface name is not displayed.
- Make sure that the state of the port is up. If not, verify the configuration of the port on the VSM.
Step 4![]() View the VLANs and their port lists on a particular VEM by entering the module vem module-number execute vemcmd show bd command.
View the VLANs and their port lists on a particular VEM by entering the module vem module-number execute vemcmd show bd command.
If you are trying to verify that a port belongs to a particular VLAN, make sure that you see the port name or LTL in the port list of that VLAN.
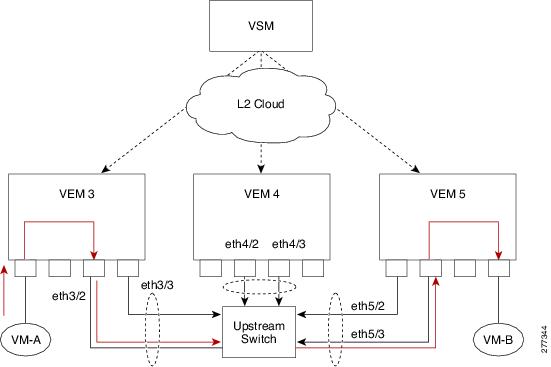
Verifying a Connection Between VEMs
Step 1![]() Check if the VLAN associated with the port is created on the VSM by entering the show vlan command.
Check if the VLAN associated with the port is created on the VSM by entering the show vlan command.
Step 2![]() Check if the ports are up in the VSM by entering the show interface brief command.
Check if the ports are up in the VSM by entering the show interface brief command.
Step 3![]() Check if the CBL state of the two ports is set to the value of 1 for forwarding (active) by entering the module vem 3 execute vemcmd show port command on the VEM.
Check if the CBL state of the two ports is set to the value of 1 for forwarding (active) by entering the module vem 3 execute vemcmd show port command on the VEM.
Step 4![]() Check if the two vEth ports are listed in the flood list of the VLAN to which they are trying to communicate by entering the module vem 3 execute vemcmd show bd command on the VEM.
Check if the two vEth ports are listed in the flood list of the VLAN to which they are trying to communicate by entering the module vem 3 execute vemcmd show bd command on the VEM.
Step 5![]() Verify that the uplink switch to which the VEMs are connected is carrying the VLAN to which the ports belong.
Verify that the uplink switch to which the VEMs are connected is carrying the VLAN to which the ports belong.
Step 6![]() Find the port on the upstream switch to which the physical NIC (that is supposed to be carrying the VLAN) on the VEM is connected to.
Find the port on the upstream switch to which the physical NIC (that is supposed to be carrying the VLAN) on the VEM is connected to.
The PNIC (Eth 5/2) is connected to swordfish-6k-2 on port Gig1/38.
Step 7![]() Log in to the upstream switch and make sure the port is configured to allow the VLAN that you are looking for.
Log in to the upstream switch and make sure the port is configured to allow the VLAN that you are looking for.
As this output shows, VLANs 1, 60 to 69 and 231 to 233 are allowed on the port. If a particular VLAN is not in the allowed VLAN list, make sure to add it to the allowed VLAN list of the port.
Isolating Traffic Interruptions
Step 1![]() In the output of the show port-profile name command, verify the following information:
In the output of the show port-profile name command, verify the following information:
- The control and packet VLANs that you configured are present (in the example, these VLANs are 3002 and 3003)
- If the physical NIC in your configuration carries the VLAN for VM, that VLAN is also present in the allowed VLAN list.
Step 2![]() Verify that the Ethernet interface is up by entering the ifconfig –a command inside the VM.
Verify that the Ethernet interface is up by entering the ifconfig –a command inside the VM.
If not, consider deleting that NIC from the VM, and adding another NIC.
Step 3![]() Using any sniffer tool, verify that ARP requests and responses are received on the VM interface.
Using any sniffer tool, verify that ARP requests and responses are received on the VM interface.
Step 4![]() On the upstream switch, look for the association between the IP and MAC address by entering these commands:
On the upstream switch, look for the association between the IP and MAC address by entering these commands:
This example shows how to debug the Address Resolution Protocol (ARP):
This example shows how to display ARP:
Layer 2 Switching Troubleshooting Commands
You can use the commands in this section to troubleshoot problems related to the Layer 2 MAC address configuration.
|
|
|
|---|---|
Displays the MAC address table to verify all MAC addresses on all VEMs controlled by the VSM. |
|
Displays the interface on which the MAC address specified is learned or configured. |
|
Displays the static MAC address of vEthernet interfaces in case a VEM physical port learns a dynamic MAC address and the packet source is in another VEM on the same VSM. |
|
show vlan [ all-ports | brief | id vlan-id | name name | dot1q tag native ] |
Displays VLAN information as specified. See Example 10-4 on page 10-9 . |
Displays a table of interface states. |
|
On the VEM, displays the port state on a particular VEM. |
|
For the specified VEM, displays its VLANs and their port lists . |
|
For the specified VEM, displays the VLAN state on a trunk port. |
|
For the specified VEM, displays the VLAN forwarding table for a specified VLAN. |
|
Displays the MAC addresses and the burn-in MAC address for an interface. |
Example 10-1 show mac address-table command

Note The Cisco Nexus 1000V MAC address table does not display multicast MAC addresses.

Tip Module indicates the VEM on which this MAC address is seen.
The N1KV Internal Port refers to an internal port that is created on the VEM. This port is used for control and management of the VEM and is not used for forwarding packets.
Example 10-2 show mac address-table address command

Tip This command shows all interfaces on which a MAC address is learned dynamically.
In this example, the same MAC address appears on Eth3/3 and Eth4/3.
Total MAC Addresses: 1
Example 10-3 show mac address-table static | inc veth command
Example 10-4 show vlan command

Tip This command shows the state of each VLAN that is created on the VSM.
Example 10-5 show interface brief command
Example 10-6 module vem module-number execute vemcmd show port command

Tip Look for the state of the port.
Example 10-7 module vem module-number execute vemcmd show bd command

Tip If a port belongs to a particular VLAN, the port name or LTL should be in the port list for the VLAN.
BD 1, vdc 1, vlan 1, 2 ports
Portlist:
16 vmnic1
17 vmnic2
Portlist:
BD 110, vdc 1, vlan 110, 1 ports
Portlist:
16 vmnic1
Portlist:
16 vmnic1
Portlist:
16 vmnic1
Portlist:
16 vmnic1
Portlist:
16 vmnic1
Portlist:
10 l22
16 vmnic1
Example 10-8 module vem module-number execute vemcmd show trunk command

Tip If a VLAN is active on a port, its CBL state should be 1.
If a VLAN is blocked, its CBL state is 0.
Example 10-9 module vem module-number execute vemcmd show l2 command
Dynamic MAC 00:50:56:bb:49:d9 LTL 16 timeout 0
Dynamic MAC 00:02:3d:42:e3:03 LTL 10 timeout 0
n1000v#
Troubleshooting Microsoft NLB Unicast Mode
Microsoft Network Load Balancing (MS-NLB) is a clustering technology offered by Microsoft as part of the Windows server operating systems. Clustering enables a group of independent servers to be managed as a single system for higher availability, easier manageability, and greater scalability.
For more information about MS-NLB, see the following URL:
http://technet.microsoft.com/en-us/library/bb742455.aspx

Note![]() Access to third-party websites identified in this document is provided solely as a courtesy to customers and others. Cisco Systems, Inc. and its affiliates are not in any way responsible or liable for the functioning of any third-party website, or the download, performance, quality, functioning or support of any software program or other item accessed through the website, or any damages, repairs, corrections or costs arising out of any use of the website or any software program or other item accessed through the website. Cisco's End User License Agreement does not apply to the terms and conditions of use of a third-party website or any software program or other item accessed through the website.
Access to third-party websites identified in this document is provided solely as a courtesy to customers and others. Cisco Systems, Inc. and its affiliates are not in any way responsible or liable for the functioning of any third-party website, or the download, performance, quality, functioning or support of any software program or other item accessed through the website, or any damages, repairs, corrections or costs arising out of any use of the website or any software program or other item accessed through the website. Cisco's End User License Agreement does not apply to the terms and conditions of use of a third-party website or any software program or other item accessed through the website.
Limitations and Restrictions
A syslog is generated if one of the following configurations exists when you try to disable automatic static MAC learning for MS-NLB because they do not support this feature:
Disabling Automatic Static MAC Learning on vEthernet Interfaces
You must disable automatic static MAC learning before you can successfully configure NLB on a vEthernet (vEth) interface.
In interface configuration mode, enter these commands:
In port profile configuration mode, enter these commands:
Checking the Status on a VSM
If the NLB unicast mode configuration does not function, check the status of the Virtual Supervisor Module (VSM).
Confirm that no mac auto-static-learn is listed in the vEth and/or port profile configurations.
This example shows how to generate the VSM status in the interface configuration mode:
This example shows how to generate the VSM status in the port profile configuration:
Checking the Status on a VEM
If the NLB unicast mode configuration does not function, check the status of the Virtual Ethernet Module (VEM). Check the following:
- Confirm that the MS-NLB vEthernet interfaces are disabled.
- Confirm that the MS-NLB shared-MAC address (starting with 02:BF) is not listed in the layer 2 (L2) MAC table.
This example shows how to generate the VSM status:
This example shows how to generate the Layer 2 MAC address table for VLAN 59:
Bridge domain 15 brtmax 4096, brtcnt 6, timeout 300
VLAN 59, swbd 59, ""
Flags: P - PVLAN S - Secure D - Drop
Configuring UUFB to Block Unwanted MS-NLB Traffic
When MS NLB VMs have more than one port on the same subnet, a request is flooded, which causes both ports to receive it. The server cannot manage this situation.
A workaround for this situation is to enable unknown unicast flood blocking (UUFB).
Enabling UUFB
This example shows how to enable UUFB. After you enter the commands in the example, press Ctrl-Z.
This configuration conceals the requests from the non-NLB ports and allows the system to function as expected.
Disabling UUFB for VMs That Use Dynamic MAC Addresses
Issues might occur for VMs that use dynamic MAC addresses. For ports that host these types of VMs, disable UUFB.
This example shows how to disable UUFB:
 Feedback
Feedback