Cisco Prime Central 1.5.2 Quick Start Guide
Preface
This guide explains how to install Cisco Prime Central 1.5.2 .
The primary audience for this guide is network operations personnel and system administrators. This guide assumes that you are familiar with the following products and topics:
-
Basic internetworking terminology and concepts
-
Network topology and protocols
-
Microsoft Windows XP, Windows 7, and Windows 10
-
Red Hat Enterprise Linux (RHEL) administration
-
Oracle database administration
-
Telecommunication Management Network (TMN) architecture model
Related Documentation
See the .Cisco Prime Central 1.5.2 Documentation Overview
See also the documentation for the following suite components:
 Note |
We sometimes update the documentation after original publication. Therefore, you should review the documentation on Cisco.com for any updates. |
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, using the Cisco Bug Search Tool (BST), submitting a service request, and gathering additional information, see What's New in Cisco Product Documentation at:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Subscribe to What's New in Cisco Product Documentation, which lists all new and revised Cisco technical documentation, as an RSS feed and deliver content directly to your desktop using a reader application. The RSS feeds are a free service.
Installation Requirements
prime
This section explains what is required to install Prime Central 1.5.2 .
Prime Central Server Requirements
The following table lists the Prime Central server system requirements.
 Note |
The below mentioned requirements are for Small Scale deployments. For more information on the required network size for installation, see Prime Carrier Management Sizing guide. |
| Minimum Requirement | Notes |
|---|---|
|
Database |
|
|
One of the following:
|
|
|
Memory |
|
|
— |
|
Disk Space |
|
|
Prime Central:
|
— |
|
External database: 22 GB for the data files |
A data file is a physical file on disk that contains data structures such as tables and indexes. The optimal location is an external disk array (preferably RAID 10). The data files are created under the directory that you specify during installation. |
|
Embedded database:
|
Redo logs are files that contain records of changes made to data. Redo logs should not reside on the same disk as the data files. An archive log is a member of a redo log that has been archived by the Oracle database. Archive logs should not reside on the same disk as the data files. Archive logs can be applied to a database backup for media recovery. A backup file stores a copy of the database data, which can be used to reconstruct data. Backup files should not reside on the same disk as the data files. Data files, redo logs, archive logs, and backup files are created under the directories that you specify during installation. Your system administrator must:
|
|
Prime Central Fault Management:
|
— |
|
Upgrade from Prime Central 1.5.1 to 1.5.2: The server must have at least (size of the current installation directory + 7 GB) of free space in the folder where Prime Central 1.5.1 is installed. |
Example: If Prime Central 1.5.1 is installed in the /opt/primecentral folder and that folder is 10 GB, you must have at least 17 GB of free space in the /opt folder before upgrading. |
|
Upgrade from Prime Central Fault Management 1.5.1 to 1.5.2: The server must have at least (size of the current installation directory + 5 GB) of free space in the folder where Prime Central Fault Management 1.5.1 is installed. |
Example: If Prime Central Fault Management is installed in the /opt/primecentral/faultmgmt folder and that folder is 15 GB, you must have at least 20 GB of free space in the /opt/primecentral folder before upgrading. |
|
64-Bit Operating System Platform |
|
| Red Hat Enterprise Linux (RHEL) 5.8, 6.4, 6.5, or 6.7 |
|
|
Hardware |
|
|
One of the following:
|
Use the following minimum hardware resources for the individual Prime Central and Fault Management servers:
Before installing RHEL 6.5 or 6.7 with VMWARE ESXi 5.1 or VMWARE ESXi 5.5 5.1, 5.5, or 6.0 5.1, 5.5, 6.0, or KVM Hypervisor (version: qemu-kvm-0.12.1.2) for Prime Central, verify your hardware compatibility. See the Cisco UCS hardware compatibility list at http://www.cisco.com/web/techdoc/ucs/interoperability/matrix/matrix.html. |
|
Red Hat RPM Packages |
|
|
For Prime Central Fault Management, the installer automatically installs the Red Hat RPM Package Manager (RPM) packages listed here. |
If any of the RPM packages are missing, the Fault Management installer automatically installs them. No user intervention is required. |
|
For Prime Central, the following packages must be present in the system path:
|
The RPM packages should be installed along with RHEL. Refer RHEL installation procedure for more information. |
|
Red Hat Services and Components |
|
|
The following Red Hat services and components (usually present as part of the Red Hat installation) are required:
|
The RPM packages should be installed along with RHEL. Refer RHEL installation procedure for more information. |
Additional Requirements
-
If you are using any of the OpenSSL versions known to have the CVE-2014-0160 vulnerability (better-known as Heartbleed), please review and take the steps outlined in the OpenSSL Security Advisory [07 Apr 2014].
-
All systems must have access to the Prime Central server hostname.
-
Clocks must be synchronized on Prime Central and all attached Prime application servers.
-
When you install Prime Central, Prime Central Fault Management, or any suite components, Domain Name System (DNS) must be enabled on the hosts. Otherwise, Prime Central components cannot communicate, and clients cannot launch Prime Central.
If the hosts do not have DNS access, or if their hostnames are not registered in the DNS, you must add those hostnames (with the correct IP addresses) to your local hosts file (/etc/hosts on Linux; ${Windows}\System32\drivers\etc\hosts on Windows).
-
If DNS is not available, the Prime Central server and the Prime Central integration layer must include in their /etc/hosts file the following entries for Prime Network, Prime Optical, Prime Performance Manager, Prime Provisioning, :
application-IP-address fully-qualified-application-hostname application-hostname
For example, if Prime Optical is installed on the "my-server" workstation with IP address 209.165.200.225, the following entry must exist in the /etc/hosts file on the Prime Central portal and the Prime Central integration layer:
209.165.200.225 my-server.cisco.com my-server
Installed Red Hat RPM Packages
The following Red Hat RPM packages are installed by the Prime Central Fault Management installer.
|
compat-db.i386 |
libgcc.i386 |
|
compat-db.x86_64 |
libgcc.x86_64 |
|
compat-glibc.i386 |
libXft.i386 |
|
compat-glibc.x86_64 |
libXft.x86_64 |
|
compat-glibc-headers.x86_64 |
libXmu.i386 |
|
compat-libstdc++-296.i386 |
libXmu.x86_64 |
|
compat-libstdc++-33.i386 |
libXp.i386 |
|
compat-libstdc++-33.x86_64 |
libXp.x86_64 |
|
elfutils.x86_64 |
libXpm.i386 |
|
elfutils-libs.x86_64 |
libXpm.x86_64 |
|
gtk2.i386 |
libXtst.i386 |
|
gtk2.x86_64 |
libXtst.x86_64 |
|
gtk2-engines.i386 |
openmotif22.i386 |
|
gtk2-engines.x86_64 |
openmotif22.x86_64 |
|
kernel-headers.x86_64 |
pam.i386 |
|
ksh.x86_64 |
pam.x86_64 |
|
compat-db.i686 |
libXft.i686 |
|
compat-db.x86_64 |
libXft.x86_64 |
|
compat-glibc.x86_64 |
libXmu.i686 |
|
compat-libstdc++-296.i686 |
libXmu.x86_64 |
|
compat-libstdc++-33.i686 |
libXp.i686 |
|
compat-libstdc++-33.x86_64 |
libXp.x86_64 |
|
elfutils.x86_64 |
libXpm.i686 |
|
elfutils-libs.x86_64 |
libXpm.x86_64 |
|
gtk2.i686 |
libXtst.i686 |
|
gtk2.x86_64 |
libXtst.x86_64 |
|
gtk2-engines.i686 |
openmotif22.i686 |
|
gtk2-engines.x86_64 |
openmotif22.x86_64 |
|
kernel-headers.x86_64 |
pam.i686 |
|
ksh.x86_64 |
pam.x86_64 |
|
libgcc.i686 |
rpm-build.x86_64 |
|
libgcc.x86_64 |
Protocols and Ports of Prime Central Components
The following table lists the protocols and ports that Prime Central component uses.
| Port No. | Exposure | Protocol | Used by... | The system administrator should... |
|---|---|---|---|---|
|
Prime Central Portal |
||||
|
1107 |
Public |
SSH |
Internal services for SSH communication |
Apply a rate-limiting policy. |
|
1108 |
Public |
TCP |
Embedded Oracle database |
Apply a rate-limiting policy. |
|
1199 |
Private |
TCP |
RMI service |
Only allow access to this port from localhost. |
|
1521 |
Public |
TCP |
Oracle database server listener |
Apply a rate-limiting policy. |
|
8005 |
Private |
TCP |
Tomcat shutdown |
Only allow access to this port (or its equivalent) from the Prime Central portal, unless remote shutdown is required. |
|
8009 |
Private |
TCP |
Apache JServ Protocol (AJP) |
Disable this port if it is not in use. |
|
8090 |
Private |
TCP |
Discovery service |
Only allow access to this port from localhost. |
|
8443 |
Public |
TCP |
Default HTTPS port; subject to change during installation |
Apply a rate-limiting policy and make this port available to all users who need to access the Prime Central portal. |
|
Prime Central Integration Layer |
||||
|
1099–1103 |
Private |
TCP |
Karaf JMX RMI registry (Prime Central integration layer management) |
Allow a dynamic range from 1099 to the number of integration layer registrations; for example, 1103. Set aside a range of 10 ports. |
|
8101–8105 |
Private (localhost) |
TCP |
Karaf SSH shell |
Allow a dynamic range from 8101 to the number of integration layer registrations; for example 8105. Set aside a range of 10 ports. |
|
9020 |
Private/Public |
TCP |
Alarm management northbound interface (NBI) |
Only allow access to this port from localhost, unless alarm management NBI access is required. If so, enable access from the alarm management client machines and apply a rate-limiting policy. |
|
9110 |
Private/Public |
TCP |
Multi-Technology Operations System Interface (MTOSI) WS-SOAP NBI |
Only allow access to this port from localhost, unless MTOSI NBI access is required. If so, enable access from the MTOSI client machines and apply a rate-limiting policy. |
|
9220 |
Private/Public |
TCP |
3GPP NBI |
Only allow access to this port from localhost, unless 3GPP NBI access is required. If so, enable access from the 3GPP client machines and apply a rate-limiting policy. |
|
32768– 61000 |
Private/Public |
TCP |
Ephemeral ports |
Only allow access to this port from localhost, unless Prime Central uses a dual-server (distributed) installation. If so, enable access from the Prime Central portal and apply a rate-limiting policy. |
|
44444– 44448 |
Private |
TCP |
Karaf JMX RMI server (Prime Central integration layer management) |
Allow a dynamic range from 44444 to the number of integration layer registrations; for example 44448. Set aside a range of 10 ports. |
|
61615 |
Private/Public |
TCP |
Java Message Service (JMS) Secure Sockets Layer (SSL) transport |
Only allow access to this port from localhost, unless Prime Central uses a dual-server (distributed) installation with JMS SSL transport. If so, enable access from the Prime Central portal and apply a rate-limiting policy. |
|
61616 |
Private/Public |
TCP |
JMS NIO transport |
Only allow access to this port from localhost, unless Prime Central uses a dual-server (distributed) installation with JMS NIO transport. If so, enable access from the Prime Central portal and apply a rate-limiting policy. |
|
Fault Management Component |
||||
|
1162 |
Public |
TCP, UDP |
Fault Management |
Allow applications to use this port to send SNMP traps to the Prime Central Fault Management component. |
|
2000 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
4100 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
4200 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
4300 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
4400 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
5435 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
9043 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
9060 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
9080 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
16310 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
16311 |
Public |
TCP |
Fault Management |
Allow Prime Central to use this port to display the Alarm Browser and Alarm Report portlets. |
|
16312 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
16313 |
Public |
TCP |
Fault Management |
Allow the Prime Central integration layer to use this port to send user management and suite monitoring requests to the Prime Central Fault Management component. |
|
16314 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
16315 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
16316 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
16318 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
16320 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
16321 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
16322 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
16323 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
|
16324 |
Private |
TCP |
Fault Management |
Only allow access to this port from localhost. |
Port Exposure Categories
The ports listed in Prime Central Protocols and Ports belong to the following exposure categories:
-
Private—These ports should not be accessible from outside workstations. Administrators should restrict access to localhost (127.0.0.1). Administrators can use firewall software such as Linux iptables to implement access restrictions.
-
Public—These ports might need to be accessible from outside workstations. To protect against external security threats, administrators should restrict access to these ports to only those workstations that need explicit access. As additional precaution against denial of service (DoS) attacks, administrators should apply rate-limiting policies. Administrators can use firewall software such as Linux iptables to implement access restrictions and rate-limiting policies. Whenever possible, if the set of source addresses is known, restrict all other access.
-
In some cases, the packet source is not known ahead of time; for example, the HTTPS port that clients use to communicate with the Prime Central portal.
-
In some cases, the packet source is known ahead of time; for example, a distributed Prime Central installation, where the Prime Central portal must communicate with the Prime Central integration layer.
-
-
Ephemeral—These ports are similar to public ports, except that their port numbers are not fixed. Depending on the Prime Central deployment scenario, ephemeral ports might require public exposure. If so, administrators should restrict access to these ports to only those workstations that need explicit access. As additional precaution against denial of service (DoS) attacks, administrators should apply rate-limiting policies. Administrators can use firewall software such as Linux iptables to implement access restrictions and rate-limiting policies.
-
In some cases, the packet source is not known ahead of time; for example, the HTTPS port that clients use to communicate with the Prime Central portal.
-
In some cases, the packet source is known ahead of time; for example, a distributed Prime Central installation, where the Prime Central portal must communicate with the Prime Central integration layer.
-
-
Restricted—We recommend that administrators restrict access to all other ports. Administrators can use firewall software such as Linux iptables to implement access restrictions.
Sample Remediation Policy Script
The following sample script shows how a system administrator can implement a remediation policy by using the built-in Linux iptables firewall feature.
#!/bin/bash
FWCONF=/etc/init.d/iptables
FW=/sbin/iptables
#Start firewall
$FWCONF save
$FWCONF start
#Remove any previous rules:
$FW -F
$FW -X
$FW -P INPUT ACCEPT
$FW -P FORWARD ACCEPT
$FW -P OUTPUT ACCEPT
#Drop invalid packets
$FW -A INPUT -m state --state INVALID -j LOG --log-prefix "DROP INVALID " --log-ip-options --log-tcp-options
$FW -A INPUT -m state --state INVALID -j DROP
#Permit rules
#Allow local packets (category 1 packets)
$FW -A INPUT -i lo -j ACCEPT
#Allow icmp/esp/ah packets
$FW -A INPUT -p icmp --icmp-type any -j ACCEPT
$FW -A INPUT -p esp -j ACCEPT
$FW -A INPUT -p ah -j ACCEPT
#Allow any tcp traffic to port <allowed-port> with rate-limiting to <rate> packets/second (category 2a packets)
$FW -A INPUT -s 0/0 -d 0/0 -j ACCEPT --protocol tcp --dport <allowed-port> -m hashlimit --hashlimit
<rate>/second
#Allow tcp traffic from source address <source-IP> to a port <allowed-port> with rate-limiting to <rate>
packets/second (category 2b packets)
$FW -A INPUT -s <source-IP>/32 -d 0/0 -j ACCEPT --protocol tcp --dport <allowed-port> -m hashlimit --hashlimit
<rate>/second
#Allow any tcp traffic to ephemeral ports with rate-limiting to <rate> packets/second (category 3a packets)
$FW -A INPUT -p tcp --dport 32768:6100 -m hashlimit --hashlimit <rate>/second
#Allow tcp traffic from source address <source-IP> to ephemeral ports with rate-limiting to <rate>
packets/second (category 3b packets)
$FW -A INPUT -s <source-IP>/32 -p tcp --dport 32768:6100 -m hashlimit --hashlimit <rate>/second
#Allow established connections
$FW -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
$FW -A INPUT -p tcp --dport ssh -j ACCEPT
#Drop everything else (category 4 packets)
$FW -A INPUT -j DROP
#Save firewall rules.
$FWCONF saveEmbedded Database Requirements
An embedded database for use with Prime Central has the following requirements. These requirements are in addition to those in Prime Central Server Requirements .
You can install the embedded database on Red Hat Enterprise Linux (RHEL) 5.8 or 6.4 5.8, 6.4, 6.5, or 6.7. During the installation, the installer automatically installs the following RPM software packages:
|
binutils |
ksh |
|
compat-libstdc++-33-3.2.3 |
libaio |
|
elfutils-libelf |
libaio-devel |
|
elfutils-libelf-devel |
libgcc-4.1.2 |
|
gcc-4.1.2 |
libstdc++ |
|
gcc-c++-4.1.2 |
libstdc++-devel |
|
glibc-2.5 |
make |
|
glibc-common-2.5 |
numactl-devel |
|
glibc-devel-2.5 |
sysstat-7.0.2 |
|
glibc-headers-2.5 |
 Note |
To verify that all of the required RHEL 5.8 RPM packages are installed, enter the following command as the root user: # rpm -q binutils compat-libstdc++-33-3.2.3 elfutils-libelf elfutils-libelf-devel gcc-4.1.2 gcc-c++-4.1.2 glibc glibc-common glibc-devel glibc-headers ksh libaio libaio-devel libgcc-4.1.2 libstdc++ libstdc++-devel make numactl-devel sysstat-7.0.2 --qf '%{name}.%{arch}\n'|sort |
|
cloog-ppl-0.15.7-1.2.el6.x86_64.rpm |
libgcc-4.4.7-3.el6.i686.rpm |
|
compat-libcap1-1.10-1.x86_64.rpm |
libstdc++-devel-4.4.7-3.el6.x86_64.rpm |
|
compat-libstdc++-33-3.2.3-69.el6.x86_64.rpm |
libX11-1.5.0-4.el6.i686.rpm |
|
cpp-4.4.7-3.el6.x86_64.rpm |
libXau-1.0.6-4.el6.i686.rpm |
|
gcc-4.4.7-3.el6.x86_64.rpm |
libxcb-1.8.1-1.el6.i686.rpm |
|
gcc-c++-4.4.7-3.el6.x86_64.rpm |
libXext-1.3.1-2.el6.i686.rpm |
|
glibc-2.12-1.107.el6.i686.rpm |
libXi-1.6.1-3.el6.i686.rpm |
|
glibc-devel-2.12-1.107.el6.x86_64.rpm |
libXtst-1.2.1-2.el6.i686.rpm |
|
glibc-headers-2.12-1.107.el6.x86_64.rpm |
mpfr-2.4.1-6.el6.x86_64.rpm |
|
kernel-headers-2.6.32-358.el6.x86_64.rpm |
nss-softokn-freebl-3.12.9-11.el6.i686.rpm |
|
ksh-20100621-19.el6.x86_64.rpm |
ppl-0.10.2-11.el6.x86_64.rpm |
|
libaio-devel-0.3.107-10.el6.x86_64.rpm |
The following components (usually installed as part of Red Hat) must be present in the system path:
-
/bin/sh
-
/bin/tcsh
-
gunzip
-
perl 5.8.6 or later
-
tar
 Note |
To verify that all of the required RHEL 6.4 RPM packages are installed, enter the following command as the root user: # rpm -q cloog-ppl compat-libcap1 compat-libstdc++-33 cpp gcc gcc-c++ glibc glibc-devel glibc-headers kernel-headers ksh libaio-devel libgcc libstdc++-devel libX11 libXau libxcb libXext libXi libXtst mpfr nss-softokn-freebl ppl --qf '%{name}.%{arch}\n'|sort |
 Note |
To verify that all of the required RHEL 6.5 RPM packages are installed, enter the following command as the root user: # rpm -q cloog-ppl compat-libcap1 compat-libstdc++-33 cpp gcc gcc-c++ glibc glibc-devel glibc-headers kernel-headers ksh libaio-devel libgcc libstdc++-devel libX11 libXau libxcb libXext libXi libXtst mpfr nss-softokn-freebl ppl --qf '%{name}.%{arch}\n'|sort |
|
cloog-ppl-0.15.7-1.2.el6.x86_64.rpm |
libstdc++-devel-4.4.7-16.el6.x86_64.rpm |
|
compat-libstdc++-33-3.2.3-69.el6.x86_64.rpm |
libX11-1.6.0-6.el6.x86_64.rpm |
|
cpp-4.4.7-16.el6.x86_64.rpm |
libXau-1.0.6-4.el6.x86_64.rpm |
|
gcc-4.4.7-16.el6.x86_64.rpm |
libxcb-1.9.1-3.el6.x86_64.rpm |
|
gcc-c++-4.4.7-16.el6.x86_64.rpm |
libXext-1.3.2-2.1.el6.x86_64.rpm |
|
glibc-2.12-1.166.el6_7.7.x86_64.rpm |
libXi-1.7.2-2.2.el6.x86_64.rpm |
|
glibc-devel-2.12-1.166.el6_7.7.x86_64.rpm |
libXtst-1.2.2-2.1.el6.x86_64.rpm |
|
glibc-headers-2.12-1.166.el6_7.7.x86_64.rpm |
mpfr-2.4.1-6.el6.x86_64.rpm |
|
kernel-headers-2.6.32-573.el6.x86_64.rpm |
nss-softokn-freebl-3.14.3-22.el6_6.x86_64.rpm |
|
ksh-20120801-28.el6.x86_64.rpm |
ppl-0.10.2-11.el6.x86_64.rpm |
|
libaio-devel-0.3.107-10.el6.x86_64.rpm |
 Note |
To verify that all of the required RHEL 6.7 RPM packages are installed, enter the following command as the root user: # rpm -q cloog-ppl compat-libstdc++-33 cpp gcc gcc-c++ glibc glibc-devel glibc-headers kernel-headers ksh libaio-devel libstdc++-devel libX11 libXau libxcb libXext libXi libXtst mpfr nss-softokn-freebl ppl --qf '%{name}.%{arch}\n'|sort |
Database Memory
Installation Phase
For the installation phase, the database memory requirements are:
-
Swap space: 150 MB
-
RAM: At least 4 GB
Runtime Phase
For the runtime phase, the database swap space requirement is two times the size of RAM, up to 32 GB.
Ports and Files
The following ports and files are required:
-
Port 1108 must be available for SSH communication between the Prime Central owner and the database owner. The port must also be open on the embedded database server, if it is installed separately.
-
The /etc/hosts file must include the workstation’s local hostname and IP address.
Example of a correct entry in the /etc/hosts file:
127.0.0.1 localhost.localdomain localhost ::1 localhost6.localdomain6 localhost6 IP-address myserver.domain.com myserverExample of an incorrect entry in the /etc/hosts file (without the server IP address information):
127.0.0.1 localhost.localdomain localhost ::1 localhost6.localdomain6 localhost6 -
The hostname --fqdn command must return the hostname with the fully qualified domain name. For example:
sh-nv210-266.cisco.com -
The hostname command should return the non-fqdn hostname. For example:
sh-nv210-266If the output is not displayed as above, hostname can be configured either through /etc/sysconfig/network or through a CLI command:
-
Edit file /etc/sysconfig/network to add hostname details and then reboot the VM to make the changes permanent.
-
Use the command hostname <name> to make temporary changes.
-
-
The /etc/nsswitch.conf file must not have NIS or NIS+ for password, group, shadow, or services. For example:
passwd: files shadow: files group: files services: files
Dual-Server Installation
If you are installing the embedded database and Prime Central on separate servers, note the following additional prerequisites for the remote server:
-
Perl 5.8.6 or later must be installed on the root user.
-
The following ports must be available:
-
22 (the default SSH port)
-
1108 (for SSH communication between the Prime Central owner and the database owner)
-
1521
-
The installation script copies the Oracle installation files to the remote server under the home directory of the user connecting to the workstation via SSH. The home directory must have at least 4 GB of space available for the installation files. This is especially important if the home directory is root (/), because overconsumption might cause the server to crash.
Security
Prime Central connects to the database using an Oracle encryption feature. By default, connections between Prime Central and the embedded database are encrypted.
As Prime Central uses Oracle database, it is recommended to periodically check Oracle website (https://support.oracle.com) for any critical patch update that needs be installed to address any security alerts.
If you are using any of the OpenSSL versions, it is recommended to periodically check for the latest patches or upgraded versions using the advisories in order to fix security vulnerabilities.
Prime Central Client Browser Requirements
The following table lists the client browsers and the Citrix XenApp deployment that Prime Central 1.5.2 supports. You must enable cookies and caching in your browser. Mozilla Firefox is the recommended browser.
 Note |
|
| Certified Citrix Setup | Operating System | Mozilla Firefox Version | Microsoft Internet Explorer Version |
|---|---|---|---|
|
Citrix Presentation Server 4.5 XenApp 5.0, installed on a Windows 2003 (SP2) server |
Windows 7 and Windows 10 (32 and 64 bit) |
Firefox 30 and 38 Standard Edition |
Internet Explorer 9, 10 and 11 |
|
Firefox 38 Extended Support Release (ESR) |
Internet Explorer 9, 10 and 11 |
Supported Client JRE Versions
|
Platform |
Prime Central |
|---|---|
|
JRE 1.8 update 45 |
Yes |
 Note |
AGORA EMS supports JRE 1.6. So, for cross-launching from Prime Central , you need to install JRE 1.6 in the client windows machine. |
Component Version Requirements
Prime Central 1.5.2 Image (Electronic Copy) Signature Verification
Before installing electronic copy of signed Cisco Prime Central image (not USB), you need to verify the signature of an image file. Follow the below procedure to verify the same:
SUMMARY STEPS
- If you do not have openssl (supported version 0.9.8e or later) installed, download and install it. See http://www.openssl.org
- If you do not have python (supported python version is 2.7.4 or later) installed, download and install it. See https://www.python.org/
- Place the following files in a temporary directory after extracting from PrimeCentral152.zip :
- In the temporary directory, run the following command:
- If the result is:
DETAILED STEPS
| Step 1 |
If you do not have openssl (supported version 0.9.8e or later) installed, download and install it. See http://www.openssl.org |
||
| Step 2 |
If you do not have python (supported python version is 2.7.4 or later) installed, download and install it. See https://www.python.org/ |
||
| Step 3 |
Place the following files in a temporary directory after extracting from PrimeCentral152.zip :
|
||
| Step 4 |
In the temporary directory, run the following command: python IS_verify_bulkhash.pyc -e PRIMECENTRAL152.cer -i PrimeCentral152.img –s PrimeCentral152.img.signature -v dgst -sha512 |
||
| Step 5 |
If the result is: Downloading CA certificate from http://www.cisco.com/security/pki/certs/crcam2.cer ... Successfully downloaded and verified crcam2.cer. Downloading SubCA certificate from http://www.cisco.com/security/pki/certs/innerspace.cer ... Successfully downloaded and verified innerspace.cer. Successfully verified root, subca and end-entity certificate chain. Successfully verified the signature of PrimeCentral152.img using PRIMECENTRAL152.cer The image is successfully verified.
|
Extracting the PrimeCentral.img.isoPrime Central 1.5.2 Image
If you ordered Prime Central electronically, this section explains how to extract the Prime Central .iso image. (If you did not order Prime Central electronically, skip this section.)
 Note |
This procedure references the ImDisk utility, but you can choose any utility that opens .iso files. |
Procedure
| Step 1 |
Download and install the ImDisk utility for Windows. |
| Step 2 |
Do one of the following, depending on where you are installing Prime Central:
cd /mnt/ISO1.5.2 |
| Step 3 |
Go to the Control Panel and click ImDisk Virtual Disk Driver. |
| Step 4 |
|
| Step 5 |
Open the Computer folder and confirm that the drive is available. 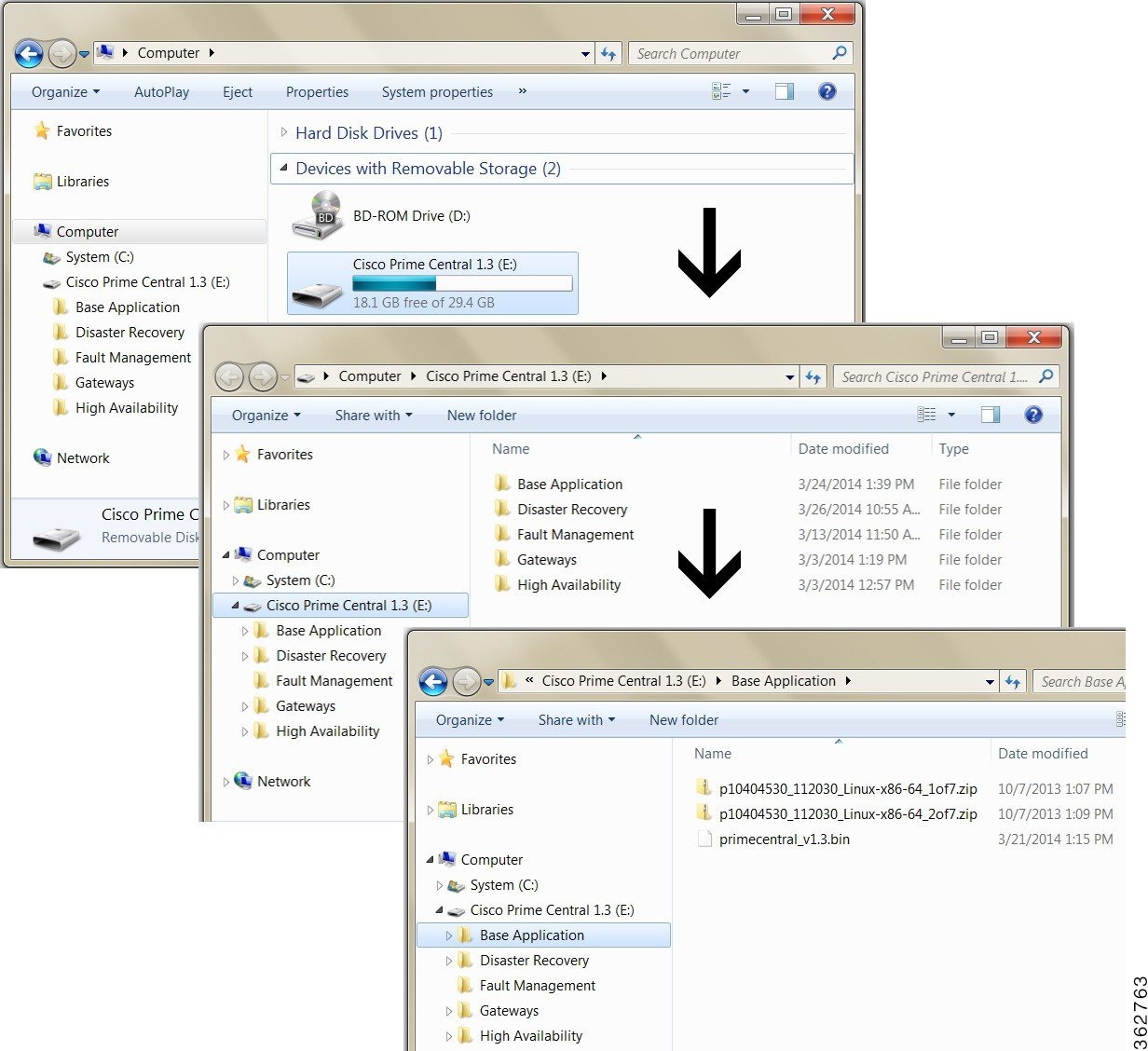 |
| Step 6 |
Continue to the relevant installation section: |
Installing Prime Central
You can install the following Prime Central 1.5.2 2.0 components on the same or separate servers:
-
Database—Can be installed as an external or an embedded Oracle 11gdatabase .
-
Prime Central portal—Provides a single sign-on and a multi-tenant common administrative interface for all applications within the suite.
-
Prime Central integration layer (IL)—Performs back-end mediation and enables information exchange between the various components
-
Fault Management—Locates, diagnoses, and reports network problems.
Installing Prime Central in a Single-Server Setup
Installing the database, Prime Central portal, and Prime Central integration layer on the same server is a two-part process:
-
Prepare the server for installation.
-
Install Prime Central.

Note
During the installation, the variables that you define must adhere to the constraints described in Pathname, Group Name, Username, and Password Constraints.
Preparing the Server for Installation
Before you install Prime Central, you must first connect to the server and, if using X server, verify the display settings.
To prepare the server for Prime Central installation:
Procedure
| Step 1 |
Use one of the following options to connect to the server where you want to install Prime Central:
|
| Step 2 |
As the root user, launch a terminal on the server where you want to install Prime Central. (If you logged in as a nonroot user, use su - to become the root user.) The C shell (csh) is recommended, but you can also use the Bash shell.
If you are using X server, continue to Step 3. If you are using VNC, skip to Step 5. |
| Step 3 |
Set the DISPLAY variable: setenv DISPLAY hostname-or-IP-address:0.0 |
| Step 4 |
Verify that the display is set correctly: echo $DISPLAY In the command output, you should see: hostname-or-IP-address:0.0 |
| Step 5 |
Set the ulimit value. If using a C shell, enter: limit descriptors 1048576 In the command output, you should see: If using a Bash shell, enter: ulimit -n 1048576 In the command output, you should see: |
| Step 6 |
(For an external database only; not applicable to an embedded database) If you are using a local or remote external database, create the following directory under ORACLE_HOME for the Prime Service Inventory (PSI) integration, and make the owner oracle: ORACLE_HOME/oradata/PSI |
| Step 7 |
Verify that the following Red Hat RPM packages are installed To verify the RHEL 5 RPM packages, enter:
To verify the RHEL 6 RPM packages, enter:
|
Installing Prime Central on the Server
Procedure
| Step 1 |
Insert the Cisco Prime Central 1.5.2 USB drive into the USB port and navigate to the Base Application folder, which contains the following files:
|
||
| Step 2 |
Use SSH to connect to the server. |
||
| Step 3 |
Copy the 3 files listed in Step 1 to the server. |
||
| Step 4 |
Change file permissions and ownership: chmod 755 * |
||
| Step 5 |
Run the installer: ./primecentral_v1.5.2.bin |
||
| Step 6 |
In the Welcome window, click Next.
|
||
| Step 7 |
In the License Agreement window, read the license agreement, click the I accept the terms of the License Agreement radio button, and click Next. |
||
| Step 8 |
In the Install Type window, click the Single-Server Install radio button; then, click Next. |
||
| Step 9 |
In the Validating Environment window, review the information for accuracy; then, click Next. |
||
| Step 10 |
In the Server Information window, confirm that the fully qualified domain name (FQDN) of the local server is correct; if not, enter the correct FQDN. (Be sure to use the hostname of the server where Prime Central will be mounted.) Then, click Next. |
||
| Step 11 |
In the Choose Install Folder window, specify where to install Prime Central. Then, click Next. The "o" (other or world) UNIX users must have at least execute permissions on the installation directory path. |
||
| Step 12 |
In the OS User Information window, provide the information required to create an OS user to start and stop processes. The username is primeusr and cannot be changed. Then, click Next. |
||
| Step 13 |
In the Admin User Information window, enter the password for the admin user who will be used for the first system login. The username is centraladmin and cannot be changed. Then, click Next. |
||
| Step 14 |
In the Install Mode window, specify one of the following installation modes:
|
||
| Step 15 |
In the Validating Port Configuration window, review the information for accuracy; then, click Next. |
||
| Step 16 |
In the Database Type window, specify one of the following database types; then, click Next: Embedded Database:
External Database: |
||
| Step 17 |
Verify that the information in the Pre-Installation Summary window is correct; then, click Install. It might take 30 minutes or longer to install Prime Central, depending on your system performance and whether you are using an embedded or external database. |
||
| Step 18 |
In the Install Complete window, click Done. If the installation fails, see Troubleshooting the Installation, and make sure to uninstall Prime Central before attempting new installation. For more information, see Uninstalling Prime Central. |
Explanation of Fields in the Embedded DB Information Window
The following table describes the required information for your local or remote embedded database.
| Field | Description |
|---|---|
|
Oracle User |
The default username is oracle. |
|
Oracle Home Directory |
The installer creates /export/home/oracle by default. If you want to use a different directory, choose one that is not already present on the server. |
|
Data Files Location |
The default is /export/home/oracle/oradata/primedb. |
|
Redo Files Location |
The default is /export/home/oracle/redo. |
|
Enable backups on the database |
Check this optional check box to enable backups on the Oracle database. |
|
Archive Log Location |
(Required if "Enable backups on the database" is checked) The default is /export/home/oracle/arch. |
|
Backup Destination |
(Required if "Enable backups on the database" is checked) The default is /export/home/oracle/backup. |
|
Install database on remote server |
Check this optional check box to install the embedded database on a remote server. The SSH user and password are used to establish an SSH connection between Prime Central and the remote database server. |
|
Remote SSH User |
(Required if "Install database on remote server" is checked) The remote SSH user's home directory cannot be the / directory. |
|
Remote SSH User Password |
(Required if "Install database on remote server" is checked) Enter the password for the remote SSH user. The password cannot contain a percent sign (%). |
|
Server IP Address |
Enter the IP address of the server where the database will be installed. |
|
Root Password |
Enter the root password for the server where the database will be installed. The password cannot contain following special characters (%, ^, $, *). |
Installing Prime Central in a Dual-Server Setup
Installing the Prime Central portal and Prime Central integration layer on separate servers—called a distributed or dual-server installation—is a three-part process:
-
Prepare both servers for installation.
-
Install the Prime Central portal.
-
Install the Prime Central integration layer.
 Note |
You must install the Prime Central portal before installing the Prime Central integration layer. During the installation, the variables that you define must adhere to the constraints described in Pathname, Group Name, Username, and Password Constraints. |
Preparing Both Servers for Installation
Before you install the Prime Central portal and the Prime Central integration layer on separate servers, you must first connect to each server and, if using X server, verify the display settings.
Do the following on both servers:
Procedure
| Step 1 |
Use one of the following options to connect to the server:
|
| Step 2 |
As the root user, launch a terminal on the server. (If you logged in as a nonroot user, enter the su - command to become the root user.) The C shell (csh) is recommended, but you can also use the Bash shell.
If you are using X server, continue to Step 3. If you are using VNC, skip to Step 5. |
| Step 3 |
Set the DISPLAY variable: setenv DISPLAY hostname-or-IP-address:0.0 |
| Step 4 |
Verify that the display is set correctly: echo $DISPLAY In the command output, you should see: |
| Step 5 |
Set the ulimit value. If using a C shell, enter: limit descriptors 1048576 In the command output, you should see: If using a Bash shell, enter: ulimit -n 1048576 In the command output, you should see: |
| Step 6 |
(For an external database only; not applicable to an embedded database) If you are using a local or remote external database, create the following directory under ORACLE_HOME for the PSI integration, and make the owner oracle: ORACLE_HOME/oradata/PSI download prePCInstallForExt12c.sh from the scripts folder in the Base Application folder (where images/primecentral_v1.5.2 .bin is located) Copy prePCInstallForExt12c.sh to ORACLE_HOME/network/admin and execute. |
| Step 7 |
Verify that the following Red Hat RPM packages are installed To verify the RHEL 5 RPM packages, enter:
|
Installing the Prime Central Portal
Procedure
| Step 1 |
Insert the Cisco Prime Central 1.5.2 USB drive into the USB port and navigate to the Base Application folder. |
||
| Step 2 |
Change file permissions and ownership: chmod 755 * |
||
| Step 3 |
From the Base Application folder, run the installer: ./primecentral_v1.5.2.bin |
||
| Step 4 |
In the Welcome window, click Next. |
||
| Step 5 |
In the License Agreement window, read the license agreement, click the I accept the terms of the License Agreement radio button, and click Next. |
||
| Step 6 |
In the Install Type window, click the Distributed Install radio button; then, click Next. |
||
| Step 7 |
In the Distributed Install Components window, click the Portal radio button; then, click Next. |
||
| Step 8 |
In the Validating Environment window, review the information for accuracy; then, click Next. |
||
| Step 9 |
In the Server Information window, confirm that the FQDN of the local server is correct; if not, enter the correct FQDN. Then, click Next. |
||
| Step 10 |
In the Choose Install Folder window, specify where to install the Prime Central portal. Then, click Next. The "o" (other or world) UNIX users must have at least execute permissions on the installation directory path. |
||
| Step 11 |
In the OS User Information window, provide the information required to create an OS user to start and stop processes. The username is primeusr and cannot be changed. Then, click Next. |
||
| Step 12 |
In the Admin User Information window, enter the password for the admin user who will be used for the first system login. The username is centraladmin and cannot be changed. Then, click Next. |
||
| Step 13 |
In the Install Mode window, specify one of the following installation modes:
|
||
| Step 14 |
In the Validating Port Configuration window, review the information for accuracy; then, click Next. |
||
| Step 15 |
In the Database Type window, specify one of the following database types; then, click Next: Embedded Database:
External Database: |
||
| Step 16 |
Verify that the information in the Pre-Installation Summary window is correct; then, click Install. It might take 30 minutes or longer to install Prime Central, depending on your system performance and whether you are using an embedded or external database. |
||
| Step 17 |
In the Install Complete window, click Done. If the installation fails, see Troubleshooting the Installation, and make sure to uninstall Prime Central before attempting new installation. For more information, see Uninstalling Prime Central. |
Installing the Prime Central Integration Layer
Procedure
| Step 1 |
Insert the Cisco Prime Central 1.5.2 USB drive into the USB port and navigate to the Base Application folder. |
| Step 2 |
Change file permissions and ownership: chmod 755 * |
| Step 3 |
From the Base Application folder, run the installer: ./primecentral_v1.5.2.bin |
| Step 4 |
In the Welcome window, click Next. |
| Step 5 |
In the License Agreement window, read the license agreement, click the I accept the terms of the License Agreement radio button, and click Next. |
| Step 6 |
In the Install Type window, click the Distributed Install radio button; then, click Next. |
| Step 7 |
In the Distributed Install Components window, click the Integration Layer radio button; then, click Next. |
| Step 8 |
In the Validating Environment window, review the information for accuracy; then, click Next. |
| Step 9 |
In the Database Information window, enter the following Prime Central database connection information; then, click Next:
|
| Step 10 |
To scale the integration layer to support multiple application instances and provide the option of high availability, Prime Central 1.5.2 uses a distributed integration layer architecture. In the Integration Layer Profile window, specify one or both of the following integration layer profiles:
|
| Step 11 |
In the Server Information window, confirm that the FQDN is correct; if not, enter the correct FQDN. Then, click Next. |
| Step 12 |
In the Choose Install Folder window, specify where to install the Prime Central integration layer. Then, click Next. The "o" (other or world) UNIX users must have at least execute permissions on the installation directory path. |
| Step 13 |
In the OS User Information window, provide the information required to create an OS user to start and stop processes. The username is primeusr and cannot be changed. Then, click Next. |
| Step 14 |
In the Install Mode window, specify one of the following installation modes:
|
| Step 15 |
In the Validating Port Configuration window, review the information for accuracy; then, click Next. |
| Step 16 |
Verify that the information in the Pre-Installation Summary window is correct; then, click Install. It might take 10 minutes or longer to install the Prime Central integration layer, depending on your system performance and whether you are using an embedded or external database. |
| Step 17 |
In the Install Complete window, click Done. If the installation fails, see Troubleshooting the Installation, and make sure to uninstall Prime Central before attempting new installation. For more information, see Uninstalling Prime Central. |
Pathname, Group Name, Username, and Password Constraints
During the Prime Central installation, the variables that you define must adhere to the constraints listed in the following table.
| Variable | Constraints |
|---|---|
|
Choose Install Folder Window |
|
|
Installation directory pathname |
The installation directory pathname cannot:
|
|
User Information Windows (OS User, Admin User, Prime Central Database User, Fault Management Application User) |
|
|
OS user group name |
The OS user group name must:
|
|
Fault management application username |
The Fault Management application username must:
|
|
All user passwords |
Except where noted, the following constraints apply to all user passwords:
|
Verifying the Prime Central Installation
Procedure
| Step 1 |
As the primeusr, log in to the Linux server with the primeusr password that you specified during the installation. |
| Step 2 |
Verify that the Prime Central portal is running: portalctl status In the output, you should see: |
| Step 3 |
Open a web browser and log in to the Prime Central portal at https://server-hostname:https-port-number, where:
|
| Step 4 |
Enter the username centraladmin and the admin user password that you specified during the installation. |
Checking the Prime Central Version
Procedure
| Step 1 |
As the primeusr, log in to the Prime Central server. |
||
| Step 2 |
On the command line, enter the version . The following is an example of the output of the version command:
|
Installing Prime Central Silently
You can install Prime Central without user interaction. In a silent installation, no messages or prompts appear on-screen, and interactive dialogs are not displayed. Information and answers that you would normally provide are read from a properties file.
A silent installation allows for unattended product installations based on the values that are provided in the silent installation properties file.
Procedure
| Step 1 |
As the root user, launch a terminal on the server where you want to silently install Prime Central. (If you logged in as a nonroot user, enter the su - command to become the root user.) The C shell (csh) is recommended. To start the C shell, enter: /bin/csh |
||
| Step 2 |
Insert the Cisco Prime Central 1.5.2 USB drive into the USB port and navigate to the local folder where the drive is mounted. |
||
| Step 3 |
Create an install.properties file based on the samples provided in Sample install.properties Files. Depending on the input that you provide, Prime Central will be installed in either a single-server setup or a dual-server (distributed) setup.
|
||
| Step 4 |
Save your changes to the install.properties file. |
||
| Step 5 |
Change file permissions: chmod 755 * |
||
| Step 6 |
Run the installer: ./primecentral_v1.5.2.bin -i silent -f install.properties The silent installation log files are available in the installation-directory/install/logs/ folder.
It is mandatory to verify the log files for any errors before proceeding further. |
Sample install.properties Files
The following examples show a typical install.properties file for each of the following scenarios:
-
Example 1: Installing Prime Central in a Single-Server Setup with a Local Embedded Database
-
Example 2: Installing Prime Central in a Single-Server Setup with a Remote Embedded Database
-
Example 3: Installing Prime Central in a Single-Server Setup with an External Database
-
Example 4: Installing the Prime Central Portal in a Dual-Server Setup with a Local Embedded Database
-
Example 6: Installing the Prime Central Portal in a Dual-Server Setup with an External Database
-
Example 7: Installing the Prime Central Integration Layer in a Dual-Server Setup
 Caution |
The values shown in the following examples are for illustrative purposes only. Be careful to enter actual values that are appropriate for your operating environment. |
Example 1: Installing Prime Central in a Single-Server Setup with a Local Embedded Database
Installer_UI=silent
########## Basic ##########
USER_INSTALL_DIR=/opt/primecentral
SUITEFW_INSTALL_TYPE=Single-Server Install
SUITEFW_DISTRIBUTED_INSTALL_TYPE=
SUITEFW_BOTH_SERVER_HOSTNAME=prime-dev.cisco.com
########## OS User (primeusr is fixed, do not change it) ##########
SUITEFW_OS_USER=primeusr
SUITEFW_OS_GROUP=primegrp
SUITEFW_OS_PASSWD=Admin123~
SUITEFW_OS_TYPE=Linux
########## Application Admin user (centraladmin) password ###
SUITEFW_ADMIN_USER_PASSWD=Admin123~
########## DATABASE ##########
SUITEFW_DB_TYPE=Embedded Database
### Database User (primedba is fixed. do not change it) ###
SUITEFW_DB_USER=primedba
SUITEFW_DB_USER_PASSWD=Admin123~
### External Database
SUITEFW_DB_HOST_IP_ADDRESS=
SUITEFW_DB_SYSTEM_PASSWD=
SUITEFW_DB_SYSTEM_USER=system
SUITEFW_DB_PORT=1521
SUITEFW_DB_SID=
SUITEFW_DBF_FILES_DIR=
### Embedded Database
SUITEFW_EMBEDDED_REMOTE=0
SUITEFW_EMBEDDED_ROOT_PASSWD=poPPee
SUITEFW_EMBEDDED_HOST_IP=209.165.201.30
SUITEFW_EMBEDDED_DBPROFILE=2
SUITEFW_EMBEDDED_SMTP=self
SUITEFW_EMBEDDED_SSH_USER=
SUITEFW_EMBEDDED_SSH_USER_PASSWORD=
SUITEFW_EMBEDDED_ORACLE_HOME=/export/home/oracle
SUITEFW_EMBEDDED_ORACLE_USER=oracle
SUITEFW_EMBEDDED_DATAFILES=/export/home/oracle/oradata/primedb
SUITEFW_EMBEDDED_REDO=/export/home/oracle/redo
SUITEFW_EMBEDDED_BACKUP=1
SUITEFW_EMBEDDED_ARCHIVE=/export/home/oracle/arch
SUITEFW_EMBEDDED_BACKUP_DEST=/export/home/oracle/backup
########## Install Mode ##########
SUITEFW_BOTH_INSTALL_MODE=Simple Install
### Portal
SUITEFW_PORTAL_HTTPS_PORT=8443
SUITEFW_PORTAL_HTTP_PORT=8080
SUITEFW_PORTAL_AJP_PORT=8009
SUITEFW_PORTAL_SHUTDOWN_PORT=8005
### IL
SUITEFW_IL_MTOSI_PORT=9110
SUITEFW_IL_CONNECTION_TRANSPORTTYPE=nio
SUITEFW_IL_CONNECTION_PORT=61616
SUITEFW_IL_NIO_TRANSPORT_PORT=61616
SUITEFW_IL_SSL_TRANSPORT_PORT=61615
SUITEFW_IL_NIO_TRANSPORT_FAILOVER_PORT=61614
SUITEFW_IL_REQUEST_TIMEOUT=135000
SUITEFW_IL_3GPP_PORT=9220
SUITEFW_IL_ALARM_MGMT_PORT=9020
SUITEFW_IL_RECONNECT_DELAY=10
### IL Profiles
# needed for distributed - IL
#SUITEFW_IL_PROFILES=PC-IL-JMS PC-IL-CORE
#### RPM VERIFICATION ######
SUITEFW_OVERRIDE_RPM_STATUS=Example 2: Installing Prime Central in a Single-Server Setup with a Remote Embedded Database
Installer_UI=silent
########## Basic ##########
USER_INSTALL_DIR=/opt/primecentral
SUITEFW_INSTALL_TYPE=Single-Server Install
SUITEFW_DISTRIBUTED_INSTALL_TYPE=
SUITEFW_BOTH_SERVER_HOSTNAME=prime-dev.cisco.com
########## OS User (primeusr is fixed, do not change it) ##########
SUITEFW_OS_USER=primeusr
SUITEFW_OS_GROUP=primegrp
SUITEFW_OS_PASSWD=Admin123~
SUITEFW_OS_TYPE=Linux
########## Application Admin user (centraladmin) password ###
SUITEFW_ADMIN_USER_PASSWD=Admin123~
########## DATABASE ##########
SUITEFW_DB_TYPE=Embedded Database
### Database User (primedba is fixed. do not change it) ###
SUITEFW_DB_USER=primedba
SUITEFW_DB_USER_PASSWD=Admin123~
### External Database
SUITEFW_DB_HOST_IP_ADDRESS=
SUITEFW_DB_SYSTEM_PASSWD=
SUITEFW_DB_SYSTEM_USER=system
SUITEFW_DB_PORT=1521
SUITEFW_DB_SID=
SUITEFW_DBF_FILES_DIR=
### Embedded Database
SUITEFW_EMBEDDED_REMOTE=1
SUITEFW_EMBEDDED_ROOT_PASSWD=poPPee123
SUITEFW_EMBEDDED_HOST_IP=209.165.200.254
SUITEFW_EMBEDDED_DBPROFILE=2
SUITEFW_EMBEDDED_SMTP=self
SUITEFW_EMBEDDED_SSH_USER=test
SUITEFW_EMBEDDED_SSH_USER_PASSWORD=Admin123~
SUITEFW_EMBEDDED_ORACLE_HOME=/export/home/oracle
SUITEFW_EMBEDDED_ORACLE_USER=oracle
SUITEFW_EMBEDDED_DATAFILES=/export/home/oracle/oradata/primedb
SUITEFW_EMBEDDED_REDO=/export/home/oracle/redo
SUITEFW_EMBEDDED_BACKUP=1
SUITEFW_EMBEDDED_ARCHIVE=/export/home/oracle/arch
SUITEFW_EMBEDDED_BACKUP_DEST=/export/home/oracle/backup
########## Install Mode ##########
SUITEFW_BOTH_INSTALL_MODE=Simple Install
### Portal
SUITEFW_PORTAL_HTTPS_PORT=8443
SUITEFW_PORTAL_HTTP_PORT=8080
SUITEFW_PORTAL_AJP_PORT=8009
SUITEFW_PORTAL_SHUTDOWN_PORT=8005
### IL
SUITEFW_IL_MTOSI_PORT=9110
SUITEFW_IL_CONNECTION_TRANSPORTTYPE=nio
SUITEFW_IL_CONNECTION_PORT=61616
SUITEFW_IL_NIO_TRANSPORT_PORT=61616
SUITEFW_IL_SSL_TRANSPORT_PORT=61615
SUITEFW_IL_NIO_TRANSPORT_FAILOVER_PORT=61614
SUITEFW_IL_REQUEST_TIMEOUT=135000
SUITEFW_IL_3GPP_PORT=9220
SUITEFW_IL_ALARM_MGMT_PORT=9020
SUITEFW_IL_RECONNECT_DELAY=10
### IL Profiles
# needed for distributed - IL
#SUITEFW_IL_PROFILES=PC-IL-JMS PC-IL-CORE
#### RPM VERIFICATION ######
SUITEFW_OVERRIDE_RPM_STATUS=Example 3: Installing Prime Central in a Single-Server Setup with an External Database
Installer_UI=silent
########## Basic ##########
USER_INSTALL_DIR=/opt/primecentral
SUITEFW_INSTALL_TYPE=Single-Server Install
SUITEFW_DISTRIBUTED_INSTALL_TYPE=
SUITEFW_BOTH_SERVER_HOSTNAME=prime-dev.cisco.com
########## OS User (primeusr is fixed, do not change it) ##########
SUITEFW_OS_USER=primeusr
SUITEFW_OS_GROUP=primegrp
SUITEFW_OS_PASSWD=Admin123~
SUITEFW_OS_TYPE=Linux
########## Application Admin user (centraladmin) password ###
SUITEFW_ADMIN_USER_PASSWD=Admin123~
########## DATABASE ##########
SUITEFW_DB_TYPE=External Database
### Database User (primedba is fixed. do not change it) ###
SUITEFW_DB_USER=primedba
SUITEFW_DB_USER_PASSWD=Admin123~
### External Database
SUITEFW_DB_HOST_IP_ADDRESS=209.165.200.225
SUITEFW_DB_SYSTEM_PASSWD=manager
SUITEFW_DB_SYSTEM_USER=system
SUITEFW_DB_PORT=1521
SUITEFW_DB_SID=service-name
SUITEFW_DBF_FILES_DIR=/export/home/oracle/prime_test
SUITEFW_EMBEDDED_ORACLE_HOME=/export/home/oracle
########## Install Mode ##########
SUITEFW_BOTH_INSTALL_MODE=Simple Install
### Portal
SUITEFW_PORTAL_HTTPS_PORT=8443
SUITEFW_PORTAL_HTTP_PORT=8080
SUITEFW_PORTAL_AJP_PORT=8009
SUITEFW_PORTAL_SHUTDOWN_PORT=8005
### IL
SUITEFW_IL_MTOSI_PORT=9110
SUITEFW_IL_CONNECTION_TRANSPORTTYPE=nio
SUITEFW_IL_CONNECTION_PORT=61616
SUITEFW_IL_NIO_TRANSPORT_PORT=61616
SUITEFW_IL_SSL_TRANSPORT_PORT=61615
SUITEFW_IL_NIO_TRANSPORT_FAILOVER_PORT=61614
SUITEFW_IL_REQUEST_TIMEOUT=135000
SUITEFW_IL_3GPP_PORT=9220
SUITEFW_IL_ALARM_MGMT_PORT=9020
SUITEFW_IL_RECONNECT_DELAY=10
### IL Profiles
# needed for distributed - IL
#SUITEFW_IL_PROFILES=PC-IL-JMS PC-IL-CORE
#### RPM VERIFICATION ######
SUITEFW_OVERRIDE_RPM_STATUS=Example 4: Installing the Prime Central Portal in a Dual-Server Setup with a Local Embedded Database
Installer_UI=silent
######### Basic ##########
USER_INSTALL_DIR=/opt/primecentral
SUITEFW_INSTALL_TYPE=Distributed Install
SUITEFW_DISTRIBUTED_INSTALL_TYPE=Portal
SUITEFW_BOTH_SERVER_HOSTNAME=prime-dev.cisco.com
########## OS User (primeusr is fixed, do not change it) ##########
SUITEFW_OS_USER=primeusr
SUITEFW_OS_GROUP=primegrp
SUITEFW_OS_PASSWD=Admin123~
SUITEFW_OS_TYPE=Linux
########## Application Admin user (centraladmin) password ###
SUITEFW_ADMIN_USER_PASSWD=Admin123~
########## DATABASE ##########
SUITEFW_DB_TYPE=Embedded Database
### Database User (primedba is fixed. do not change it) ###
SUITEFW_DB_USER=primedba
SUITEFW_DB_USER_PASSWD=Admin123~
### External Database
SUITEFW_DB_HOST_IP_ADDRESS=
SUITEFW_DB_SYSTEM_PASSWD=
SUITEFW_DB_SYSTEM_USER=system
SUITEFW_DB_PORT=1521
SUITEFW_DB_SID=
SUITEFW_DBF_FILES_DIR=
### Embedded Database
SUITEFW_EMBEDDED_REMOTE=0
SUITEFW_EMBEDDED_ROOT_PASSWD=poPPee
SUITEFW_EMBEDDED_HOST_IP=209.165.201.30
SUITEFW_EMBEDDED_DBPROFILE=2
SUITEFW_EMBEDDED_SMTP=self
SUITEFW_EMBEDDED_SSH_USER=
SUITEFW_EMBEDDED_SSH_USER_PASSWORD=
SUITEFW_EMBEDDED_ORACLE_HOME=/export/home/oracle
SUITEFW_EMBEDDED_ORACLE_USER=oracle
SUITEFW_EMBEDDED_DATAFILES=/export/home/oracle/oradata/primedb
SUITEFW_EMBEDDED_REDO=/export/home/oracle/redo
SUITEFW_EMBEDDED_BACKUP=1
SUITEFW_EMBEDDED_ARCHIVE=/export/home/oracle/arch
SUITEFW_EMBEDDED_BACKUP_DEST=/export/home/oracle/backup
########## Install Mode ##########
SUITEFW_BOTH_INSTALL_MODE=Simple Install
### Portal
SUITEFW_PORTAL_HTTPS_PORT=8443
SUITEFW_PORTAL_HTTP_PORT=8080
SUITEFW_PORTAL_AJP_PORT=8009
SUITEFW_PORTAL_SHUTDOWN_PORT=8005
### IL
SUITEFW_IL_MTOSI_PORT=9110
SUITEFW_IL_CONNECTION_TRANSPORTTYPE=nio
SUITEFW_IL_CONNECTION_PORT=61616
SUITEFW_IL_NIO_TRANSPORT_PORT=61616
SUITEFW_IL_SSL_TRANSPORT_PORT=61615
SUITEFW_IL_NIO_TRANSPORT_FAILOVER_PORT=61614
SUITEFW_IL_REQUEST_TIMEOUT=135000
SUITEFW_IL_3GPP_PORT=9220
SUITEFW_IL_ALARM_MGMT_PORT=9020
SUITEFW_IL_RECONNECT_DELAY=10
### IL Profiles
# needed for distributed - IL
#SUITEFW_IL_PROFILES=PC-IL-JMS PC-IL-CORE
#### RPM VERIFICATION ######
SUITEFW_OVERRIDE_RPM_STATUS=Example 5: Installing the Prime Central Portal in a Dual-Server Setup with a Remote Embedded Database
Installer_UI=silent
########## Basic ##########
USER_INSTALL_DIR=/opt/primecentral
SUITEFW_INSTALL_TYPE=Distributed Install
SUITEFW_DISTRIBUTED_INSTALL_TYPE=Portal
SUITEFW_BOTH_SERVER_HOSTNAME=prime-dev.cisco.com
########## OS User (primeusr is fixed, do not change it) ##########
SUITEFW_OS_USER=primeusr
SUITEFW_OS_GROUP=primegrp
SUITEFW_OS_PASSWD=Admin123~
SUITEFW_OS_TYPE=Linux
########## Application Admin user (centraladmin) password ###
SUITEFW_ADMIN_USER_PASSWD=Admin123~
########## DATABASE ##########
SUITEFW_DB_TYPE=Embedded Database
### Database User (primedba is fixed. do not change it) ###
SUITEFW_DB_USER=primedba
SUITEFW_DB_USER_PASSWD=Admin123~
### External Database
SUITEFW_DB_HOST_IP_ADDRESS=
SUITEFW_DB_SYSTEM_PASSWD=
SUITEFW_DB_SYSTEM_USER=system
SUITEFW_DB_PORT=1521
SUITEFW_DB_SID=
SUITEFW_DBF_FILES_DIR=
### Embedded Database
SUITEFW_EMBEDDED_REMOTE=1
SUITEFW_EMBEDDED_ROOT_PASSWD=poPPee123
SUITEFW_EMBEDDED_HOST_IP=209.165.200.254
SUITEFW_EMBEDDED_DBPROFILE=2
SUITEFW_EMBEDDED_SMTP=self
SUITEFW_EMBEDDED_SSH_USER=test
SUITEFW_EMBEDDED_SSH_USER_PASSWORD=Admin123~
SUITEFW_EMBEDDED_ORACLE_HOME=/export/home/oracle
SUITEFW_EMBEDDED_ORACLE_USER=oracle
SUITEFW_EMBEDDED_DATAFILES=/export/home/oracle/oradata/primedb
SUITEFW_EMBEDDED_REDO=/export/home/oracle/redo
SUITEFW_EMBEDDED_BACKUP=1
SUITEFW_EMBEDDED_ARCHIVE=/export/home/oracle/arch
SUITEFW_EMBEDDED_BACKUP_DEST=/export/home/oracle/backup
########## Install Mode ##########
SUITEFW_BOTH_INSTALL_MODE=Simple Install
### Portal
SUITEFW_PORTAL_HTTPS_PORT=8443
SUITEFW_PORTAL_HTTP_PORT=8080
SUITEFW_PORTAL_AJP_PORT=8009
SUITEFW_PORTAL_SHUTDOWN_PORT=8005
### IL
SUITEFW_IL_MTOSI_PORT=9110
SUITEFW_IL_CONNECTION_TRANSPORTTYPE=nio
SUITEFW_IL_CONNECTION_PORT=61616
SUITEFW_IL_NIO_TRANSPORT_PORT=61616
SUITEFW_IL_SSL_TRANSPORT_PORT=61615
SUITEFW_IL_NIO_TRANSPORT_FAILOVER_PORT=61614
SUITEFW_IL_REQUEST_TIMEOUT=135000
SUITEFW_IL_3GPP_PORT=9220
SUITEFW_IL_ALARM_MGMT_PORT=9020
SUITEFW_IL_RECONNECT_DELAY=10
### IL Profiles
# needed for distributed - IL
#SUITEFW_IL_PROFILES=PC-IL-JMS PC-IL-CORE
#### RPM VERIFICATION ######
SUITEFW_OVERRIDE_RPM_STATUS=Example 6: Installing the Prime Central Portal in a Dual-Server Setup with an External Database
Installer_UI=silent
########## Basic ##########
USER_INSTALL_DIR=/opt/primecentral
SUITEFW_INSTALL_TYPE=Distributed Install
SUITEFW_DISTRIBUTED_INSTALL_TYPE=Portal
SUITEFW_BOTH_SERVER_HOSTNAME=prime-dev.cisco.com
########## OS User (primeusr is fixed, do not change it) ##########
SUITEFW_OS_USER=primeusr
SUITEFW_OS_GROUP=primegrp
SUITEFW_OS_PASSWD=Admin123~
SUITEFW_OS_TYPE=Linux
########## Application Admin user (centraladmin) password ###
SUITEFW_ADMIN_USER_PASSWD=Admin123~
########## DATABASE ##########
SUITEFW_DB_TYPE=External Database
### Database User (primedba is fixed. do not change it) ###
SUITEFW_DB_USER=primedba
SUITEFW_DB_USER_PASSWD=Admin123~
### External Database
SUITEFW_DB_HOST_IP_ADDRESS=209.165.200.225
SUITEFW_DB_SYSTEM_PASSWD=manager
SUITEFW_DB_SYSTEM_USER=system
SUITEFW_DB_PORT=1521
SUITEFW_DB_SID=service-name
SUITEFW_DBF_FILES_DIR=/export/home/oracle/prime_test
SUITEFW_EMBEDDED_ORACLE_HOME=/export/home/oracle
########## Install Mode ##########
SUITEFW_BOTH_INSTALL_MODE=Simple Install
### Portal
SUITEFW_PORTAL_HTTPS_PORT=8443
SUITEFW_PORTAL_HTTP_PORT=8080
SUITEFW_PORTAL_AJP_PORT=8009
SUITEFW_PORTAL_SHUTDOWN_PORT=8005
### IL
SUITEFW_IL_MTOSI_PORT=9110
SUITEFW_IL_CONNECTION_TRANSPORTTYPE=nio
SUITEFW_IL_CONNECTION_PORT=61616
SUITEFW_IL_NIO_TRANSPORT_PORT=61616
SUITEFW_IL_SSL_TRANSPORT_PORT=61615
SUITEFW_IL_NIO_TRANSPORT_FAILOVER_PORT=61614
SUITEFW_IL_REQUEST_TIMEOUT=135000
SUITEFW_IL_3GPP_PORT=9220
SUITEFW_IL_ALARM_MGMT_PORT=9020
SUITEFW_IL_RECONNECT_DELAY=10
### IL Profiles
# needed for distributed - IL
#SUITEFW_IL_PROFILES=PC-IL-JMS PC-IL-CORE
#### RPM VERIFICATION ######
SUITEFW_OVERRIDE_RPM_STATUS=Example 7: Installing the Prime Central Integration Layer in a Dual-Server Setup
Installer_UI=silent
########## Basic ##########
USER_INSTALL_DIR=/opt/primecentral
SUITEFW_INSTALL_TYPE=Distributed Install
SUITEFW_DISTRIBUTED_INSTALL_TYPE=Integration Layer
SUITEFW_BOTH_SERVER_HOSTNAME=prime-dev.cisco.com
########## OS User (primeusr is fixed, do not change it) ##########
SUITEFW_OS_USER=primeusr
SUITEFW_OS_GROUP=primegrp
SUITEFW_OS_PASSWD=Admin123~
SUITEFW_OS_TYPE=Linux
########## Application Admin user (centraladmin) password ###
SUITEFW_ADMIN_USER_PASSWD=Admin123~
########## DATABASE ##########
SUITEFW_DB_TYPE=External Database
### Database User (primedba is fixed. do not change it) ###
SUITEFW_DB_USER=primedba
SUITEFW_DB_USER_PASSWD=Admin123~
### External Database
SUITEFW_DB_HOST_IP_ADDRESS=198.51.100.1
SUITEFW_DB_SYSTEM_PASSWD=Admin123~
SUITEFW_DB_SYSTEM_USER=primedba
SUITEFW_DB_PORT=1521
SUITEFW_DB_SID=service-name
SUITEFW_DBF_FILES_DIR=/export/home/oracle/prime_test
SUITEFW_EMBEDDED_ORACLE_HOME=/export/home/oracle
### Portal
SUITEFW_PORTAL_HTTPS_PORT=8443
SUITEFW_PORTAL_HTTP_PORT=8080
SUITEFW_PORTAL_AJP_PORT=8009
SUITEFW_PORTAL_SHUTDOWN_PORT=8005
### IL
SUITEFW_IL_MTOSI_PORT=9110
SUITEFW_IL_CONNECTION_TRANSPORTTYPE=nio
SUITEFW_IL_CONNECTION_PORT=61616
SUITEFW_IL_NIO_TRANSPORT_PORT=61616
SUITEFW_IL_SSL_TRANSPORT_PORT=61615
SUITEFW_IL_NIO_TRANSPORT_FAILOVER_PORT=61614
SUITEFW_IL_REQUEST_TIMEOUT=135000
SUITEFW_IL_3GPP_PORT=9220
SUITEFW_IL_ALARM_MGMT_PORT=9020
SUITEFW_IL_RECONNECT_DELAY=10
### IL Profiles
# needed for distributed - IL
SUITEFW_IL_PROFILES=PC-IL-JMS PC-IL-CORE
#### RPM VERIFICATION ######
SUITEFW_OVERRIDE_RPM_STATUS=Verifying the Silent Installation
Procedure
| Step 1 |
Open a web browser and log in to the Prime Central portal at https://server-hostname:https-port-number, where:
|
| Step 2 |
Enter the username centraladmin and the admin user password that you specified for the silent installation. If you cannot log in to the Prime Central portal, check the silent installation log files in the installation-directory/install/logs/ folder. If the installation failed, the log files contain errors and exceptions that you can use for troubleshooting. |
Installing Prime Central Fault Management
Installing the Prime Central Fault Management component—which has its own installation DVD and installation binary—is a two-part process:
-
Prepare the server for installation.
-
Install the Prime Central Fault Management component.

Note
During the installation, the variables that you define must adhere to the constraints described in Pathname, Group Name, Username, and Password Constraints.
Preparing the Server for Installation
Before you install the Prime Central Fault Management component, you must first connect to the server and, if using X server, verify the display settings.
Procedure
| Step 1 |
Use one of the following options to connect to the server where you want to install Prime Central Fault Management:
|
| Step 2 |
As the root user, launch a terminal on the server where you want to install Prime Central Fault Management. The C shell (csh) is recommended. To start the C shell, enter: /bin/csh If you are using X server, continue to the next step. If you are using VNC, you are finished; continue to Installing Prime Central Fault Management on the Server. |
| Step 3 |
Set the DISPLAY variable: setenv DISPLAY hostname-or-IP-address:0.0 |
| Step 4 |
Verify that the display is set correctly: echo $DISPLAY In the command output, you should see: |
| Step 5 |
If the hosts do not have DNS access, or their hostnames are not registered in the DNS, update the /etc/hosts file on the server: # IP-address FQDN hostname For example: |
| Step 6 |
Save the /etc/hosts file. |
| Step 7 |
Run the following tests: # hostname -a fm-server # hostname -f fm-server.cisco.com # hostname -i 192.168.1.170 # ipcalc -h 192.168.1.170 HOSTNAME=fm-server.cisco.com If any of the tests return incorrect results, check the /etc/hosts file for typos. Check also the /etc/sysconfig/network file and verify that the HOSTNAME entry contains your server's FQDN (fm-server.cisco.com in this example). |
| Step 8 |
Move (or remove) all *.log files from the /tmp folder. |
| Step 9 |
Before installing Prime Central Fault Management on a RHEL 6.4, 6.5, 6.7, or 6.8 server, make sure that the numactl-devel RPM package is not installed. To uninstall it: |
| Step 10 |
Verify that the Red Hat RPM packages listed here are installed.
|
Installing Prime Central Fault Management on the Server
Procedure
| Step 1 |
Insert the Cisco Prime Central 1.5.2 USB, navigate to the Fault Management folder, and locate the FM 1.5.2 Build.tar.gz file. |
||
| Step 2 |
Use SSH to connect to the server. |
||
| Step 3 |
Copy the FM 1.5.2 Build.tar.gz file to the server. |
||
| Step 4 |
Distribute the file: |
||
| Step 5 |
Run the installer: ./primefm_v1.5.2.bin |
||
| Step 6 |
In the Introduction window, click Next. |
||
| Step 7 |
In the License Agreement window, read the license agreement, click the I accept the terms of the License Agreement radio button, and click Next. |
||
| Step 8 |
In the Environment Validation window, review the information for accuracy; then, click Next. |
||
| Step 9 |
In the Server Information window, confirm that the FQDN is correct; if not, enter the correct FQDN. Then, click Next. |
||
| Step 10 |
In the UNIX OS User Information window, provide the information required to create a UNIX OS user to start and stop processes; then, click Next.
|
||
| Step 11 |
In the App User Information window, enter the username and password for the Prime Central Fault Management application user; then, click Next. |
||
| Step 12 |
In the Database Information window, enter the following database connection information; then, click Next:
|
||
| Step 13 |
In the Choose Install Folder window, specify where to install the Fault Management server; then, click Next. The installation directory defaults to /opt/primeusr/faultmgmt. |
||
| Step 14 |
In the Install Mode window, specify one of the following installation modes:
|
||
| Step 15 |
Verify that the information in the Pre-Installation Summary window is correct; then, click Install. |
||
| Step 16 |
Confirm that both the Prime Central portal and the Prime Central integration layer are running on the Prime Central server. It might take 90 minutes or longer to install Prime Central Fault Management, depending on your system performance. |
||
| Step 17 |
Verify that the Red Hat RPM packages listed under Installed Red Hat RPM Packages table are installed.
|
||
| Step 18 |
In the Install Complete window, click Done. The installation log files are available in the installation-directory/install/logs/ folder. |
||
| Step 19 |
Complete the installation by logging into the Prime Central integration layer as the primeusr and entering the following commands to restart it: |
Configuring Mail Service for Alarm Reports
After successful installation of Fault Management, configure mail service for receiving alarm reports.
Procedure
| Step 1 |
Go to ~/faultmgmt/tipv2Components/TCRComponent/cognos/configuration folder. |
| Step 2 |
Open cogstartup.xml file in vi editor. |
| Step 3 |
Scroll down to the below parameters: |
| Step 4 |
Replace mailserver with localhost. |
| Step 5 |
Save the file and close it. |
| Step 6 |
Restart Prime Central Fault Management TIP component, by logging in as primeusr: |
Installing Prime Central Fault Management Silently
Procedure
| Step 1 |
As the root user, launch a terminal on the server where you want to silently install Prime Central Fault Management. The C shell (csh) is recommended. To start the C shell, enter: /bin/csh |
||||
| Step 2 |
Insert the Cisco Prime Central 1.5.2 USB drive into the USB port and navigate to the local folder where the drive is mounted. |
||||
| Step 3 |
Create a PrimeFM_install.properties file based on the sample provided in Sample PrimeFM_install.properties File. The silent properties file is the same whether you are installing the Fault Management component on the same server as Prime Central, or on a separate server. If you are installing the Fault Management component on the same server as Prime Central, the OS user primeusr is already created. Therefore, when you create the PrimeFM_install.properties file, be sure to enter the correct password for the OS user primeusr.
|
||||
| Step 4 |
Save your changes to the PrimeFM_install.properties file. |
||||
| Step 5 |
Change file permissions: chmod 755 * |
||||
| Step 6 |
Run the installer: ./primefm_v1.5.2.bin -i silent -f PrimeFM_install.properties The silent installation log files are available in the installation-directory/install/logs/ folder. It is mandatory to verify the log files for any errors before proceeding further. |
Sample PrimeFM_install.properties File
The following example shows a typical PrimeFM_install.properties file for Prime Central Fault Management.
 Caution |
The values shown in the following example are for illustrative purposes only. Be careful to enter actual values that are appropriate for your operating environment. |
Note the following:
-
For the PRIMEFM_OS_USER parameter, the value primeusr is fixed; do not change it.
-
For the PRIMEFM_OS_GROUP and PRIMEFM_PA_GROUP parameters, the value ncoadmin is fixed; do not change it.
-
For the PRIMEFM_INSTALL_TYPE parameter, if you enter Simple Install, the default port values will be used. If you want to use different ports, enter Advanced Install.
Sample PrimeFM_install.properties File when Installing Prime Central Fault Management
##########User Information########### PRIMEFM_OS_USER=primeusr PRIMEFM_OS_GROUP=ncoadmin PRIMEFM_OS_PASSWD=Prime123@ PRIMEFM_PA_USER=primefm_pa PRIMEFM_PA_GROUP=ncoadmin PRIMEFM_PA_PASSWD=Prime123@ PRIMEFM_APP_USER=primefm PRIMEFM_APP_USER_PASSWD=Prime123@ # Fully qualified hostname of the FM Server PRIMEFM_SERVER_HOSTNAME=fm-server.cisco.com #########Prime Central Database Information########## PRIMEFM_DB_HOST_IP_ADDRESS=209.165.200.225 PRIMEFM_DB_PORT=1521 PRIMEFM_DB_SID=primedb PRIMEFM_DB_SYSTEM_USER=primedba PRIMEFM_DB_SYSTEM_PASSWD=Prime123@ ##########User Install Directory######### USER_INSTALL_DIR=/opt/primecentral/faultmgmt ##########Install Type########## PRIMEFM_INSTALL_TYPE=Simple Install #########Port Information############## PRIMEFM_DB_SERVER_PORT=4100 PRIMEFM_GATEWAY_PORT=4300 PRIMEFM_PROXY_PORT=4400 PRIMEFM_PROCESS_AGENT_PORT=4200 PRIMEFM_SNMP_PROBE_PORT=1162 PRIMEFM_WEB_SERVER_PORT=16310 PRIMEFM_CORR_HTTP_PORT=9080 PRIMEFM_CORR_ADMIN_PORT=9060 PRIMEFM_CORR_DB_PORT=5435 PRIMEFM_CORR_CLI_PORT=2000 PRIMEFM_WEB_SERVER_SOAP_PORT=16313 PRIMEFM_PN_GATEWAY_PORT=6081 ##########Disaster Recovery########## # Options: 'Regular' or 'DR' PRIMEFM_INSTALL_MODE=Regular # Run the 'list' command on PC server and find the id value for cfm type # Use a value of 0 for Regular mode. Use a positive value for DR mode. PRIMEFM_CFM_ID=0 #### RPM VERIFICATION ###### PRIMEFM_OVERRIDE_RPM_STATUS=
Manually Registering Fault Management to Retrieve Alarm Data
If an application is integrated with Prime Central but is not up and running when the Fault Management component is installed, you must manually register with the application if you want to receive alarms immediately. (Within 10 minutes of the Fault Management installation, an automatic cron job starts alarm retrieval.)
To bypass the 10-minute waiting period and begin receiving alarms immediately:
Procedure
| Step 1 |
As the primeusr, log in to the Prime Central Fault Management server. |
||
| Step 2 |
After the application is integrated with Prime Central, go to the installation-directory /prime_integrator/scripts folder and enter: ./DMRegistration.sh
|
Installing the Gateways Used with Prime Central
You can install IBM Tier 1 and Tier 2 gateways that are available for use with Prime Central through a separately purchased license. The gateways have their own installation binary. The installation procedure for the following gateways is mentioned below:
 Note |
The following steps do not apply to the data source adaptors (DSAs) that are included in the Prime Central base application. |
Procedure
| Step 1 |
Insert the Cisco Prime Central 1.5.2 USB drive into the USB port, navigate to the Gateways folder, and unzip the PC_Gateways.zip file. |
| Step 2 |
From the list of files displayed in the PC_Gateways/Tier1 or PC_Gateways/Tier2 folder, copy the desired file to the workstation on which you want to install the gateway. |
| Step 3 |
Uncompress (unzip) the file: gunzip filename |
| Step 4 |
Extract the .tar archive contents: tar -xvf filename |
| Step 5 |
Open the README.txt file that is packaged with the gateway and follow the gateway installation steps. |
Troubleshooting the Installation
If your Prime Central installation fails, you can check the log files to locate the problem and take the appropriate action.
Procedure
| Step 1 |
Check the following log files in the installation-directory/install/logs/ folder:
|
| Step 2 |
Uninstall Prime Central as explained in Uninstalling Prime Central. |
| Step 3 |
Restart the installation. |
Prime Central Log Files
| Log File | Description | ||
|---|---|---|---|
|
CreateOSGroup.log |
Output and errors during OS user and group creation. |
||
|
CreateOSUser.log |
|||
|
dbPasswdEncryption.log |
Output and errors during the database and admin user password encryption process. |
||
|
DBUserAction.log |
Output and errors during database user and schema creation. |
||
|
ExitCode.log |
Exit codes for important installation actions. You can determine installation status from the exit codes. |
||
|
insertESB-PC-IL-COMMON.log |
Output and errors while persisting Prime Central integration layer information to the suite database. |
||
|
insertESB-PC-IL-CORE.log |
|||
|
insertESB-PC-IL-JMS.log |
|||
|
insertESB.log |
Output and errors while persisting Prime Central portal information to the suite database. |
||
|
insertPortal.log |
|||
|
installESB-PC-IL-CORE.log |
Output and errors during the Prime Central integration layer installation. |
||
|
installESB-PC-IL-JMS.log |
|||
|
installXMP.log |
Output and errors during XMP installation. |
||
|
prime_embedded_oracle.log |
Embedded database installation information.
|
||
|
primecentral_uninstall.log |
Uninstallation console output that is saved to /tmp. |
||
|
psiintegration.log |
Output and errors during the PSI integration. |
||
|
startXMP.log |
Output and errors during XMP startup. If an error is noted during XMP startup, check the installation-directory/XMP_Platform/logs/Startup.log file.
|
||
|
UNINSTALL_LOG_time-stamp |
Uninstallation information that is time stamped and saved in /var/adm/Cisco/uninstall; for example, /var/adm/Cisco/uninstall/UNINSTALL_LOG_102711-123237. |
Troubleshooting the Prime Central Installation
The following table offers additional troubleshooting steps to help solve installation-related problems.
| Problem | Solution |
|---|---|
|
An embedded database installation fails with the following error in the installation-directory /local/scripts/prime_embedded_oracle.log file: If you try to remove the oracle user manually, the following errors are generated: |
In the /etc/nsswitch.conf file, remove the nis entry from passwd, shadow, group, and services. Then, remove the oracle user. |
|
The installation validation fails with an insufficient disk space error, even though the disk partition used to create the installation directory has more than 20 GB of free space. |
Do the following:
|
|
An embedded database installation fails with the following errors in the installation-directory /local/scripts/prime_embedded_oracle.log file: |
Verify that the available free memory on the system meets the Oracle installation requirements. |
|
An embedded database installation fails with the following error in the installation-directory /local/scripts/prime_embedded_oracle.log file: |
Verify that the available disk space meets the Oracle installation requirements. |
|
An embedded database installation fails with the following errors in the installation-directory /local/scripts/prime_embedded_oracle.log file: |
Verify that the /etc/hosts format is correct; for example: |
|
An embedded database installation fails with the following errors in the installation-directory /local/scripts/prime_embedded_oracle.log file: |
Verify that your system meets the requirements listed in Embedded Database Requirements. |
|
Database connection errors are generated while installing the Prime Central integration layer in a dual-server setup. |
Do the following:
|
|
An embedded database installation fails with the following errors in the installation-directory /local/scripts/prime_embedded_oracle.log file: |
Verify that the correct Oracle system packages are installed in libaio-devel, libaio, and glibc-devel. For example, this problem occurs if glibc-devel-2.5.49 (x86_64) is not installed on the x86_64 system. To verify that the correct Oracle system packages are installed, enter: rpm -qa --queryformat "%{NAME}-%{VERSION}.%{RELEASE} (%{ARCH})\n" | sort > /tmp/rpmlist.txt |
|
The Prime Central installation quits with an error message about viewing the prime_embedded_oracle.log file on both the local and remote machines. However, no log files exist at the specified locations. |
Look at the primecentral_install.log file for exceptions or errors that relate to zip, unzip, or open files. (The primecentral_install.log file is located under /tmp/ or installation-directory /install/logs/.) The root cause of this problem is that the ulimit value was not set to ulimit -n 1048576. |
|
An embedded database installation fails because the /etc/oratab file contains an extra user at the bottom of the file, as shown in the following example: |
Verify that the /etc/oratab file does not contain any users except for the primedb user. (Because the installation failed, the primedb user might not be present.) If /etc/oratab contains any user other than the primedb user, delete the extra user. Then, rerun the installation. |
|
The Prime Central installation fails after installing the database. As part of the failed installation, the installer copies the /var/.com.zerog.registry.xml file to the system. If you later try to reinstall Prime Central, the presence of the /var/.com.zerog.registry.xml file prevents you from performing any subsequent installations. |
Do the following:
|
|
While registering an application with Prime Central, you receive error messages similar to the following: |
Add the entry dns next to “hosts:” in the /etc/nsswitch.conf file. |
|
Installation of the Fault Management component fails. |
Review the installation log files in the installation-directory/install/logs folder:
If Impact failed, this typically indicates that either the FQDN of the Fault Management server was not entered during the installation process or the FQDN of the Fault Management server was incorrectly entered in DNS or the /etc/hosts file. If TCR failed, this typically indicates that an RPM is missing. Verify that all of the required RPMs have been installed. |
|
|
Remove the numactl-devel RPM package:
You will
also need to delete the
|
|
|
Add the following environment variable to your session prior to running the installation binary: export _JAVA_OPTIONS="-Xms128m -Xmx512m" If the error still appears, try doubling the Xmx value. |
|
Prime Central/ Fault Management installation fails because of RPM installation error as in /opt/primecentral/install/logs/installUtils.log : |
Configuring Prime Carrier Management Suite Scale Setup
Before starting the integration process, perform the Prime Carrier Management suite scale setup.
 Note |
The following steps are applicable only to Extremely Large scale setups. |
Procedure
| Step 1 |
Switch to Oracle User: su - oracle |
| Step 2 |
Login to sql prompt as sysdba: sqlplus / as sysdba |
| Step 3 |
Enter the following query @ sql prompt: alter system set sga_max_size=8G scope=spfile; |
| Step 4 |
Come out of sql prompt and oracle user using exit command. |
| Step 5 |
Switch to the primeusr to restart emdbctl and portalctl (Oracle Database) with the following commands: su - primeusr portalctl stop emdbctl --stop emdbctl --start portalctl start |
| Step 6 |
Come out of primeusr user using exit command. |
| Step 7 |
Switch again to Oracle User to increase db_cache size: su - oracle |
| Step 8 |
Login to sql prompt as sysdba: sqlplus / as sysdba |
| Step 9 |
Enter the following query @ sql prompt: alter system set db_cache_size=4G; |
| Step 10 |
Come out of sql prompt and oracle user using exit command. |
Configuring Applications as Suite Components
You can integrate an existing installation of the following applications with Prime Central:
-
Cisco InTracer
-
Prime Network, including the Prime Network integration layer
-
Prime Optical, including the Prime Optical integration layer
-
Prime Performance Manager
-
Prime Provisioning
-
Agora-NG
This section assumes that you have already installed the application in standalone mode, and now you want it to join the Prime Carrier Management suite.
Integration Process
When you install an individual application, it contains the following files, which the Prime Central portal and Prime Central integration layer require to identify and route to the application:
-
DMIntegrator.sh—Wrapper script to invoke the API to register the application with the Prime Central platform.
-
DMIntegrator.tar—Tar bundle that contains the libraries required to register the application.
The application integration (also known as registration) process is as follows:
-
The DMIntegrator.sh and DMIntegrator.tar files integrate the application with Prime Central. (These files are bundled with the application installers.)
-
The DMIntegrator.prop file is generated when the application is installed. (This file contains information to populate the application in the Prime Central database and is provided as input to the DMIntegrator.sh script.)
-
The DMIntegrator.sh script runs in interactive or silent mode:
-
Interactive mode—You are prompted for database information such as username, password, IP address, service name, and so on.
-
Silent mode—Database information is passed as CLI arguments to the DMIntegrator.sh script.
These modes are useful for both:
-
Standalone application integration
-
Seamless installation as a suite component
-
-
The DMIntegrator.sh script calls the DMSwitchToSuite.sh script, which switches between the standalone application installer and the integrated application installer.
-
The application installer installs the application in either standalone or integrated mode. In integrated mode, the application installer calls the DMIntegrator.sh script to make the integration seamless.
Note the following:
-
Once Prime Provisioning is integrated with Prime Central, it cannot be reverted to standalone mode, even after unregistering Prime Provisioning.
-
The DMIntegrator.sh, DMIntegrator.tar, and DMIntegrator.prop files reside in the application-installation-directory/prime_integrator/ folder on the application server.
-
The DMIntegrator.sh file generates the following output, which is available in the application-installation-directory/prime_integrator/ folder:
-
datasource.properties—Contains connection information for the Prime Central database; the password is encrypted.
-
dmid.xml—Contains a unique ID that the application uses to update its information in the Prime Central database.
-
pc.xml—Contains the name of the Prime Central server with which the application integrates.
-
-
If Prime Network is installed on an IPv6-only gateway, you cannot integrate it with Prime Central.
Contents of the DMIntegrator.prop File
The DMIntegrator.prop file is generated by entering environment values for each application. The file contains the following name-value pairs:
TYPE={cfm | cit | ful | net | opt | ppm}
DISPLAY={Fault Management | CIT | Prime Network | Prime Optical | Prime Performance Manager |
Prime Provisioning}
HOSTNAME=
DESCRIPTION=
VERSION=
PATCH=
DB_VERSION=
DB_LOCATION=
DB_SID=
DB_PORT=
DB_TYPE=
INSTALL_DATE_TIME=
INSTALL_LOCATION=
OS_USERNAME=
SWITCH_TO_SUITE_LOC=
PROTOCOL_PORT_PAIR=<name:value,name:value,name:value,...>
BUILD_NUMBER=
where:
-
DISPLAY is the application.
-
SWITCH_TO_SUITE_LOC is the location of the DMSwitchToSuite.sh script on the application.
-
PROTOCOL_PORT_PAIR is a comma-separated pair of protocols and ports relevant to the application.
-
BUILD_NUMBER is the build number of the installed application.
DMIntegrator.sh Script Usage
The DMIntegrator.sh script shows the following usage:
./DMIntegrator.sh [-n] prop-file server-hostname service-name db-user db-password db-port
./DMIntegrator.sh [-a] prop-file server-hostname service-name db-user db-password db-port
./DMIntegrator.sh [-i] prop-file
where:
-
-n is for noninteractive, single application instance registration
-
-a is for noninteractive, multiple application instance registration
-
-i is for interactive mode for both single and multiple application instance registration
When multiple instances of Prime Network are integrated with Prime Central, they all must be the same version.
For example:
./DMIntegrator.sh -a DMIntegrator.prop db-server db-sid db-user db-password db-port
where:
-
db-server—Prime Central database server hostname or IP address.
-
db-sid—Prime Central database service name (primedb for an embedded database; user provided for an external database).
-
db-user—Prime Central database user (primedba for an embedded or external database).
-
db-password—Prime Central database user password.
-
db-port—Prime Central database port number (1521 for an embedded database; user provided for an external database).
 Note |
The DMIntegrator.sh script output is available in the DMIntegrator.log file. |
Integrating Cisco InTracer with Prime Central
Procedure
| Step 1 |
As the application user, shut down Cisco InTracer. |
| Step 2 |
Verify that the JAVA_HOME environment variable points to Java 1.7, which the DMIntegrator.sh script requires. |
| Step 3 |
Verify that the /usr/bin/scp secure copy tool is present on the Cisco InTracer server. |
| Step 4 |
Under the Cisco InTracer home folder, create a prime_integrator folder (if it does not already exist) and copy the following files to it:
|
| Step 5 |
Verify that permissions are correct. |
| Step 6 |
Run the DMIntegrator.sh script. (For usage details, see DMIntegrator.sh Script Usage.) $ ./DMIntegrator.sh |
| Step 7 |
As the primeusr user, log in to the Prime Central integration layer and restart it: |
| Step 8 |
Start Cisco InTracer. |
| Step 9 |
After Cisco InTracer is integrated with Prime Central, use the Prime Central portal to create new users, even if they already existed in standalone mode. |
Integrating Prime Network with Prime Central
Procedure
| Step 1 |
As the application user, shut down Prime Network: networkctl stop |
||
| Step 2 |
Enter: cd $PRIME_NETWORK_HOME/Main ; runRegTool.sh localhost set suite-integ/enabled true
|
||
| Step 3 |
Verify that the JAVA_HOME environment variable points to Java 1.7 (or 1.8 for Prime Network 4.3 or Prime Network 4.3.1), which the DMIntegrator.sh script requires: java –version |
||
| Step 4 |
Verify that the correct value is configured for the HOSTNAME object in the DMIntegrator.prop file.
|
||
| Step 5 |
Run the DMIntegrator.sh script. ./DMIntegrator.sh -a DMIntegrator.prop Prime-Central-DB-hostname db-SID db-user db-password port |
||
| Step 6 |
Start Prime Network: networkctl start |
||
| Step 7 |
Restart the Prime Central integration layer so that it recognizes the recently added Prime Network server: itgctl stop itgctl start |
||
| Step 8 |
Now that Prime Network is integrated with Prime Central, you must also integrate the Prime Network integration layer. Continue to Integrating the Prime Network Integration Layer with Prime Central. |
||
| Step 9 |
After Prime Network is integrated with Prime Central, use the Prime Central portal to create new users, even if they already existed in standalone mode (or provide PN scope to the users). To provide Prime Network scope to users, see the topic "Creating New Device Scopes to Control Device Access" in the Cisco Prime Network 5.1 Administrator Guide, Chapter 6, "Controlling Device Access and Authorization Using Device Scopes." |
Integrating the Prime Network Integration Layer with Prime Central
Procedure
| Step 1 |
As the Prime Network user, log in to the Prime Network gateway: ssh root@ Prime-Network-host-IP-address su - prime
|
||
| Step 2 |
Disable the Prime Network integration layer health checker by entering the following command on the Prime Network gateway server: $PRIMEHOME/local/scripts/il-watch-dog.sh disable |
||
| Step 3 |
Stop the Prime Network integration layer: $PRIMEHOME/bin/itgctl stop |
||
| Step 4 |
Change directories to the $PRIMEHOME/integration directory: cd $PRIMEHOME/integration |
||
| Step 5 |
Run the DMIntegrator script. ./DMIntegrator.sh -a ILIntegrator.prop Prime-Central-DB-hostname db-SID db-user db-password port |
||
| Step 6 |
Reload the user profile: source $HOME/.cshrc |
||
| Step 7 |
Enable the Prime Network integration layer health checker by entering the following command on the Prime Network gateway server: $PRIMEHOME/local/scripts/il-watch-dog.sh enable |
||
| Step 8 |
Start the Prime Network integration layer: $PRIMEHOME/bin/itgctl start |
||
| Step 9 |
If you install a Prime Network instance after Prime Performance Manager is integrated with Prime Central, enter the following commands in Prime Performance Manager GW server to integrate Prime Performance Manager with Prime Network: /opt/CSCOppm-gw/bin/sgmInventoryImportUtility.sh -installCrossLaunchPoints /opt/CSCOppm-gw/bin/sgmInventoryImportUtility.sh -installTrapSupport |
Integrating Prime Network in a High Availability Configuration with Prime Central
Procedure
| Step 1 |
As the application user, shut down Prime Network. |
||
| Step 2 |
Verify that the JAVA_HOME environment variable points to Java 1.7 (or 1.8 for Prime Network 4.3) or 1.8 for Prime Network 4.3.1 , , which the DMIntegrator.sh script requires. |
||
| Step 3 |
Verify that the /usr/bin/scp secure copy tool is present on the Prime Network server. |
||
| Step 4 |
Under the Prime Network home folder, create a prime_integrator folder (if it does not already exist) and copy the following files to it:
|
||
| Step 5 |
Verify that permissions are correct. |
||
| Step 6 |
On the client workstation, repeat the preceding step. If you are using a Windows workstation, use the C:\Windows\system32\drivers\etc\hosts file. |
||
| Step 7 |
Run the DMIntegrator.sh script. ./DMIntegrator.sh -a DMIntegrator.prop Prime-Central-DB-hostname db-SID db-user db-password port
|
||
| Step 8 |
As the Prime Network user, run the jars script: |
||
| Step 9 |
If you are reintegrating the same Prime Network instance with a different COM-URI, you must restart the Prime Central portal. (The COM-URI is the Prime Network identifier and can be found in the Prime Central portal > Suite Monitoring portlet.) To do so, log in to the Prime Central portal as the primeusr user and enter: portalctl stop portalctl start |
||
| Step 10 |
Start Prime Network. |
||
| Step 11 |
After Prime Network is integrated with Prime Central, use the Prime Central portal to create new users, even if they already existed in standalone mode. |
Integrating the Prime Network Integration Layer in a High Availability Configuration with Prime Central
Prime Central supports integration with the Prime Network integration layer in the following high availability configurations:
-
Local redundancy only, which uses two active local servers for automatic failover.
-
Geographical disaster recovery only, which uses a server at a remote geographical site for a full disaster recovery.
Complete the integration procedure specific to the configuration you have in place.
Local Redundancy Configuration
Procedure
| Step 1 |
As the root user, log in to the Prime Network primary cluster node. |
||
| Step 2 |
Freeze the “ana” service: clusvcadm -Z ana |
||
| Step 3 |
Switch users to the Prime Network Gateway application user: su – anauser |
||
| Step 4 |
Stop the Prime Network integration layer: $PRIMEHOME/bin/itgctl stop |
||
| Step 5 |
Change to the $PRIMEHOME/integration directory: cd $PRIMEHOME/integration |
||
| Step 6 |
Open the ILIntegrator.prop file: vi $PRIMEHOME/integration/ILIntegrator.prop |
||
| Step 7 |
Change the HOSTNAME value to ana-cluster-ana. |
||
| Step 8 |
Run the DMIntegrator.sh script. ./DMIntegrator.sh -a ILIntegrator.prop Prime-Central-database-server service-namedb-user db-password db-port where Prime-Central-database-server is the server’s hostname or IP address.
|
||
| Step 9 |
Reload the user profile: source $HOME/.cshrc |
||
| Step 10 |
Start the Prime Network Integration layer: $PRIMEHOME/bin/itgctl start |
||
| Step 11 |
As the root user, unfreeze the “ana” service: clusvcadm -U ana |
||
| Step 12 |
If you install a Prime Network instance after Prime Performance Manager is integrated with Prime Central, enter the following commands in Prime Performance Manager GW server to integrate Prime Performance Manager with Prime Network: /opt/CSCOppm-gw/bin/sgmInventoryImportUtility.sh -installCrossLaunchPoints /opt/CSCOppm-gw/bin/sgmInventoryImportUtility.sh -installTrapSupport |
Geographical Disaster Recovery Configuration
Complete the following procedures for both the primary and geographical disaster recovery Prime Network servers.
Configuring the Primary Server
Procedure
| Step 1 |
As the root user, log in to the primary Prime Network primary server: ssh root@ server where server is the primary server’s hostname or IP address. |
| Step 2 |
Switch users to the Prime Network application user: su – username |
| Step 3 |
Disable the Prime Network integration layer health monitor and stop the Prime Network integration layer: $PRIMEHOME/local/scripts/il-watch-dog.sh disableandstop |
| Step 4 |
Change to the $PRIMEHOME/integration directory: cd $PRIMEHOME/integration |
| Step 5 |
Run the DMIntegrator.sh script. ./DMIntegrator.sh -a ILIntegrator.prop Prime-Central-database-server service-name db-user db-password db-port where Prime-Central-database-server is the server’s hostname or IP address. |
| Step 6 |
Reload the user profile: source $HOME/.cshrc |
| Step 7 |
Run the itgctl list command to obtain the Prime Network integration layer’s instance ID value. You will need this for Step 8 of the Configuring the Geographical Disaster Recovery Server procedure. |
| Step 8 |
Enable the Prime Network integration layer health monitor: $PRIMEHOME/local/scripts/il-watch-dog.sh enable |
| Step 9 |
Start the Prime Network Integration layer: $PRIMEHOME/bin/itgctl start |
Configuring the Geographical Disaster Recovery Server
Procedure
| Step 1 |
As the root user, log in to the geographical disaster recovery Prime Network server: ssh root@ server where server is the geographical disaster recovery server’s hostname or IP address. |
| Step 2 |
Change to the /var/adm/cisco/prime-network/scripts/ha/rsync directory: cd /var/adm/cisco/prime-network/scripts/ha/rsync |
| Step 3 |
Rename the rsync_exclude_pnil_cfg.txt file: mv rsync_exclude_pnil_cfg.txt rsync_exclude_pnil_cfg.txt.org |
| Step 4 |
Switch users to the Prime Network application user: su – username |
| Step 5 |
Disable the Prime Network integration layer health monitor and stop the Prime Network integration layer: $PRIMEHOME/local/scripts/il-watch-dog.sh disableandstop |
| Step 6 |
Change to the $PRIMEHOME/integration directory: cd $PRIMEHOME/integration |
| Step 7 |
Open the ILIntegrator.prop file: vi $PRIMEHOME/integration/ILIntegrator.prop |
| Step 8 |
Change the HOSTNAME value to the standby Prime Network geographical disaster recovery server’s hostname. |
Integrating Prime Optical and the Prime Optical Integration Layer with Prime Central
Procedure
| Step 1 |
As the application user, shut down Prime Optical: opticalctl stop |
||
| Step 2 |
Under the application home folder, change directories to the /bin directory: cd /opt/CiscoTransportManagerServer/bin |
||
| Step 3 |
Run the CPOIntegrator.sh script: CPOIntegrator.sh -a prop-file server-hostname service-name db-user db-password port-number For example: CPOIntegrator.sh -a DMIntegrator.prop prime-server primedb primedba Test456@ 1521
|
||
| Step 4 |
Start Prime Optical: opticalctl start |
Integrating Prime Performance Manager with Prime Central
 Tip |
Integrate Prime Performance Manager with Prime Central after you integrate the Fault Management component and each instance of Prime Network with Prime Central. |
Procedure
| Step 1 |
As the root user, log in to the Prime Performance Manager gateway server and navigate to the Prime-Performance-Manager-gateway-installation-directory /bin directory. |
| Step 2 |
Enter: ./ppm primecentralintegration |
| Step 3 |
Enter the appropriate responses at the prompts:
|
| Step 4 |
Restart Prime Performance Manager for the changes to take effect. |
| Step 5 |
As the primeusr user, log in to the Prime Central integration layer and restart it: itgctl stop itgctl start |
| Step 6 |
If you are reintegrating Prime Performance Manager after a previous integration, you must unregister it from Prime Central before you reintegrate it. See Unregistering Prime Performance Manager. |
| Step 7 |
If remote units are connected to the gateway, complete the below steps to enable SSL on remote units: |
| Step 8 |
After Prime Performance Manager is integrated with Prime Central, use the Prime Central portal to create new users. (Any users that existed before the integration are removed during the integration.) |
| Step 9 |
If you install a Prime Network instance after Prime Performance Manager is integrated with Prime Central, enter the following commands to integrate Prime Performance Manager with Prime Network: /opt/CSCOppm-gw/bin/sgmInventoryImportUtility.sh -installCrossLaunchPoints /opt/CSCOppm-gw/bin/sgmInventoryImportUtility.sh -installTrapSupport |
| Step 10 |
If Prime Performance Manager is configured to send alarms directly to the Prime Central Fault Management server, verify that an upstream OSS host is configured correctly in the System Event Editor of Prime Performance Manager. |
| Step 11 |
If you install the Fault Management component after Prime Performance Manager is integrated with Prime Central, enter the following command and select Fault Management as the trap destination to integrate it with Prime Performance Manager: ./ppm setpctrapdestination For example: |
Integrating Prime Provisioning with Prime Central
Procedure
| Step 1 |
As the application user, shut down Prime Provisioning. ./prime.sh stop |
| Step 2 |
Set the Prime Provisioning environment: ./prime.sh shell |
| Step 3 |
Run the DMIntegrator.sh script. (For usage details, see DMIntegrator.sh Script Usage.) $ ./DMIntegrator.sh |
| Step 4 |
As the primeusr user, log in to the Prime Central integration layer and restart it: |
| Step 5 |
If you are reintegrating Prime Provisioning with a different COM-URI, you must restart the Prime Central portal. (The COM-URI is the Prime Provisioning identifier and can be found in the Prime Central portal > Suite Monitoring portlet.) To do so, log in to the Prime Central portal as the primeusr user and enter: portalctl stop portalctl start |
| Step 6 |
Start Prime Provisioning. As Prime Provisioning user, log in to the Prime Provisioning
server and run:
./prime.sh start |
| Step 7 |
After Prime Provisioning is integrated with Prime Central, use the Prime Central portal to create new users, even if they already existed in standalone mode. |
Integrating Cisco ME 4600 Series Agora-NG with Prime Central
Procedure
| Step 1 |
Log in to the Agora-NG server as the user agorang. |
| Step 2 |
Enter the following commands: ~$ cd share/primecentral ~/share/primecentral$ bash DMIntegrator.sh -n DMIntegrator.prop pc-server pc-db-sid pc-db-user pc-db-password pc-db-port ~/share/primecentral$ agorang restart where:
Once Agora-NG restarts, integration with Prime Central is complete. |
Integrating Cisco Broadband Access Center (BAC) with Prime Central
Before you integrate Cisco BAC with Prime Central, we recommend that you first install Cisco BAC’s Regional Distribution Unit (RDU) and Device Provisioning Engine (DPE) components.
To integrate Cisco Broadband Access Center (BAC) with Prime Central, refer to the procedure in section Integrating Serving Node with Prime Central Active Server in the Cisco RAN Management System Installation Guide, Release 5.1.
For AP Boot Notification Alarm configuration, refer to the section Configuring SNMP Trap for CPEs in the Cisco Broadband Access Center 3.10 Administrator Guide.
Integrating RAN Management System (RMS) with Prime Central
The 'configure_fm_server.sh' script is used to integrate Cisco RMS with the Prime Central NMS for fault notification. This script allows the registration of the Domain Manager for RMS in the Prime Central NMS. Prime Central allows the receipt of SNMP traps from RMS only if DM registration for RMS is completed
The 'configure_fm_server.sh' script:
-
Accepts the following NMS interface details and updates the FMServer.properties file (for FM Server) and /etc/snmp/snmpd.conf (for snmp)
. -
NMS interface IP address, port number (162 or 1162), community string, supported SNMP version (v1 or v2c)
. -
Adds the ip tables rules to allow the SNMP traps to be notified to the specified NMS interfaces
Subsequently, during deployment the script prompts you to specify whether one of the configured NMS is Prime Central. If it is Prime Central, the script accepts the Prime Central database server details such as, Prime Central DB server IP, DB server listening port, DB user credentials (user-ID and password), and registers the Domain Manger for RMS in Prime Central.
To integrate RAN Management System (RMS) with Prime Central, refer to the procedure in section Integrating FM, PMG, LUS, and RDU Alarms on Central Node with Prime Central NMS in the Cisco RAN Management System Installation Guide, Release 5.1.
Integrating Cisco Prime Access Registrar (CPAR) with Prime Central
Procedure
| Step 1 |
From the Fault Source Management portlet, click Add to add the Fault Source details. The
Add New
Fault Source dialog box appears.
|
||
| Step 2 |
Enter the Fault Source Type from the drop-down as CAR and specify the Fault Source details in the appropriate fields. |
||
| Step 3 |
Click OK. For more Information about how to add a Fault Source and the field descriptions, refer to the section Adding a Fault Source in the
Prime Central 1.5.2 User Guide
e.
|
Configuring Prime Central as Trap Listener in CPAR to Receive Traps
Procedure
| Step 1 |
Login to CPAR server. |
||
| Step 2 |
Go to CPAR installation directory and change it to /ucd-snmp/share/snmp directory. |
||
| Step 3 |
Add the following command to snmpd.conf file. trap2sink <<ip-addr-FM-Server>> public <FM-port>
|
||
| Step 4 |
To reflect the changes, enter the following command for restarting the CPAR server: cd <CPAR installation directory>/bin ./arserver restart |
||
| Step 5 |
Check if the following options, in the path /radius/advanced/snmp (in aregcmd prompt), are enabled: enabled = true masteragent = true |
||
| Step 6 |
If the above options are not enabled, perform the following steps to enable these options: |
Integrating Cisco Prime Network Registrar (CPNR) with Prime Central
Procedure
| Step 1 |
From the Fault Source Management portlet, click Add to add the Fault Source details. The
Add New
Fault Source dialog box appears.
|
| Step 2 |
Enter the Fault Source Type from the drop-down as CNR and specify the Fault Source details in the appropriate fields. |
| Step 3 |
Click OK. For more Information about how to add a Fault Source and the field descriptions, refer to the section Adding a Fault Source in the Cisco Prime Central 1.5.2 User Guide. .. After the CPNR Fault Source is added, CPNR is registered with Prime Central as a domain manager instance. |
Configuring Prime Central as Trap Listener in CPNR to Receive Traps
Procedure
| Step 1 |
Login to CPNR server. |
||
| Step 2 |
Go to CPNR installation directory and change it to /local/usrbin directory. |
||
| Step 3 |
Enter the following command: ./nrcmd |
||
| Step 4 |
Provide the CPNR user credentials. The
nrcmd prompt
appears
|
||
| Step 5 |
Execute the following command to add an FM server as a trap recipient for CPNR: nrcmd> trap-recipient <name> create
ip-addr=<ip-addr-FM-Server> port-number=<portnumber of FM
server
|
||
| Step 6 |
To reflect the changes, enter the following command for restarting the SNMP server: nrcmd > snmp stop nrcmd > snmp start |
Integrating SpiderNet with Prime Central
Procedure
| Step 1 |
From the Fault Source Management portlet, click Add to add the Fault Source details. The
Add New
Fault Source dialog box appears.
|
||
| Step 2 |
Enter the Fault Source Type from the drop-down as SpiderCloud and specify the Fault Source details in the appropriate fields. |
||
| Step 3 |
Click OK. For more Information about how to add a Fault Source and the field descriptions, refer to the section Adding a Fault Source in the
Prime Central 1.5.2 User Guide.
|
Configuring Prime Central as Trap Listener in SpiderNet to Receive Traps
Procedure
| Step 1 |
Login to SpiderNet server GUI. |
| Step 2 |
Create a SNMP Managers Group:
|
| Step 3 |
Configure Events:
|
| Step 4 |
Configure a Trap Target:
|
Upgrading Prime Central
You can upgrade from Prime Central 1.5.1 to 1.5.2 . The upgrade does the following automatically:
- Backs up the embedded database, if present.
- Stops the Prime Central portal and Prime Central integration layer.
- Backs up the previous installation directory.
- Upgrades the Prime Central portal and Prime Central integration layer.
- Starts the Prime Central portal and Prime Central integration layer.
 Note |
You must upgrade Prime Central before upgrading the Fault Management component. DB files (datafiles, arch, backup, redo) cannot be located directly in a partition and should be under directory. Scenarios with any DB file directly on partition will fail the upgrade and require pre-work to be done. |
Before You Begin
-
If you are using an external database, you must back it up manually.
-
If you are installing portal and integration layer on different servers, you must stop the integration layer manually before upgrade.
-
If you are using an embedded (local or remote) database, we recommend (but not require) that you back it up manually before upgrading.
- The upgrade steps are the same for both single- and dual-server setups. In a dual-server setup, complete the following procedure on the Prime Central portal server first; then, repeat the procedure on the Prime Central integration layer server.
Upgrading from Prime Central 1.5.2 to
Procedure
| Step 1 |
Use one of the following options to connect to the server where you want to upgrade Prime Central:
|
| Step 2 |
As the root user, launch a terminal on the server where you want to upgrade Prime Central. (If you logged in as a nonroot user, use su - to become the root user.) The C shell (csh) is recommended. To start the C shell, enter: /bin/csh If you are using X server, continue to the next step. If you are using VNC, skip to Step 5. |
| Step 3 |
Set the DISPLAY variable: setenv DISPLAY hostname-or-IP-address:0.0 |
| Step 4 |
Verify that the display is set correctly: echo $DISPLAY In the command output, you should see: hostname-or-IP-address:0.0 |
| Step 5 |
Insert the Cisco Prime Central 1.5.2 USB drive into the USB port and navigate to the local folder where the drive is mounted.Base Application folder, which contains the following files:
|
| Step 6 |
Take backup of /var/.com.zerog.registry.xml file as /var/.com.zerog.registry.xml_backup_for_1.4.1 /var/.com.zerog.registry.xml_backup_for_1.5.1 |
| Step 7 |
Change file permissions and ownership: chmod 755 * |
| Step 8 |
Begin the upgrade: ./primecentral_v1.5.1.bin ./primecentral_v1.5.2.bin |
| Step 9 |
In the Welcome window, click Next. If you are upgrading to Prime Central 1.5.2 on the same server where the earlier Prime Central version was installed, the following dialog box is displayed: A previous installation exists on the system. Do you want to directly upgrade from 1.5.3.0 to 2.1.0.0? |
| Step 10 |
Click OK. If you are using an external database, the following dialog box is displayed: You must back up the database manually before continuing. |
| Step 11 |
Confirm that your database backup succeeded; then, click Continue. |
| Step 12 |
In the Advanced Configuration window, make any desired changes to the port numbers, timeout value, or reconnect delay; then, click Install. |
| Step 13 |
In the Upgrade Complete window, click Done. It might take 20 to 3040 to 5040 to 50 minutes or longer to complete the upgrade, depending on your system performance and whether you are using an embedded or external database. The log files are available in installation-directory /install/logs and installation-directory /upgrade/ /upgrade.log. The log files are available in:
|
| Step 14 |
Take backup of embedded database after the upgrade. For Backup and Restore, refer to the section Backing Up and Restoring the Embedded Database. |
Upgrading Prime Central Silently from 1.5.3 to 2.0.0
You can upgrade Prime Central without user interaction. In a silent upgrade, no messages or prompts appear on-screen, and interactive dialogs are not displayed. Information and answers that you would normally provide are read from a properties file.
A silent upgrade allows for unattended product upgrades based on the values that are provided in the properties file.
 Note |
The silent upgrade steps are the same for both single- and dual-server setups. In a dual-server setup, complete the following procedure on the Prime Central portal server first; then, repeat the procedure on the Prime Central integration layer server. |
Procedure
| Step 1 |
As the root user, launch a terminal on the server where you want to silently upgrade to Prime Central 1.5.2 . (If you logged in as a nonroot user, enter the su - command to become the root user.) The C shell (csh) is recommended. To start the C shell, enter: /bin/csh |
| Step 2 |
Insert the Cisco Prime Central 1.5.2 USB drive into the USB port and navigate to the local folder where the drive is mounted. |
| Step 3 |
Change file permissions: chmod 755 * |
| Step 4 |
If you are upgrading an external database, add the following property (with the oracle home directory as the value) to the install.properties file: SUITEFW_EMBEDDED_ORACLE_HOME=/export/home/oracle |
| Step 5 | |
| Step 6 |
Begin the silent upgrade: ./primecentral_v1.5.2.bin -i silent -f install.properties |
| Step 7 |
(Optional) The silent upgrade uses the following default values for the request timeout, 3GPP port, alarm management port, and reconnect delay. You can change these values as desired: When the silent upgrade completes, the log files are available in installation-directory /install/logs and installation-directory /upgrade/ 1.5.1.0-1.5.2.0 /upgrade.log. If the upgrade fails, make sure to verify the log files. If an upgrade is necessary, only then perform the rollback procedure from Prime Central 1.5.2 to Prime Central 1.5.1, and then try the upgrade again. If the upgrade fails, make sure to verify the log files. If an upgrade is necessary, only then perform the rollback procedure from Prime Central 1.5.2 , and then try the upgrade again. |
| Step 8 |
(Applicable for external database only and if Prime Central upgrade is successful) If you are using an external database, remove the following directory under ORACLE_HOME which was created for Prime Central installation: ORACLE_HOME/oradata/PSI |
Verifying the Upgrade
To verify the upgrade, log in to the Prime Central server as the primeusr and enter:
version
The output should show:
# version
Running Integration Layer(PC-IL-CORE,PC-IL-JMS) + Platform (v 1.3.0.0 1.5.2 (build number)) with Patch(0.0.0.0)Reverting to Prime Central 1.5.1
After upgrading to Prime Central 1.5.2 , you may find the need to revert to the previous version. To do so, complete the following procedure.
 Note |
By default the primeusr home folder is /opt/primecentral. If your primeusr home folder is different, specify that folder instead. |
Procedure
| Step 1 |
Confirm that the /opt/primecentral_1.5.1.0 _backup folder was created during upgrade from Prime Central 1.5.1 to Prime Central 1.5.2 .
|
||
| Step 2 |
Change ownership of the /opt/primecentral_1.5.1.0 _backup folder: chown –R primeusr:ncoadmin /opt/primecentral_1.5.1.0_backup |
||
| Step 3 |
Stop all Prime Central processes: su - primeusr itgctl stop portalctl stop exit For distributed server environment (portal and IL are in different servers):
|
||
| Step 4 |
Move the primecentral folder to the tmp folder: mv /opt/primecentral/ /tmp/primecentral |
||
| Step 5 |
Rename the /opt/primecentral_ 1.5.1.0 _backup folder: mv /opt/primecentral_1.5.1.0_backup/ /opt/primecentral |
||
| Step 6 |
Restore the /var/.com.zerog.registry.xml file with the backup file: /var/.com.zerog.registry.xml_backup_for_1.5.1 /var/.com/zerog.registry.xml_backup_for_2.1.0 that was created during Prime Central upgrade process. Execute the below commands:
Execute the below commands:
|
||
| Step 7 |
To find the exact time to restore database, back to the timestamp before upgrade. Login to the database as sysdba and execute the below query to get the RMAN backup history: SELECT status, to_char(START_TIME,'mm/dd/yy hh24:mi') start_time, to_char(END_TIME,'mm/dd/yy hh24:mi') end_time FROM V$RMAN_BACKUP_JOB_DETAILS ORDER BY end_time DESC; |
||
| Step 8 |
Change the permissions of ssh key files as below: For primeusr user: su - primeusr cd ~/local/prime_secured chmod 600 id_dsa id_dsa.pub authorized_keys For oracle user: su - [oracle_user] cd ~/prime_secured chmod 600 id_dsa id_dsa.pub authorized_keys |
||
| Step 9 |
Restore database (from the backup taken before upgrading to Prime Central 1.5.3 ) If it is embedded database: su - primeusr emdbctl --restore
Database restore log location: /export/home/oracle/prime_logs/restore***_***.log If it is External database:
|
||
| Step 10 |
Start all Prime Central processes: su - primeusr itgctl start portalctl start exit For distributed server environment (portal and IL are in different servers):
|
||
| Step 11 |
Execute this step only if it is distributed server environment (portal and IL are in different servers): Repeat the above steps 1 to 6 in IL server. |
Upgrading to Prime Central Fault Management 1.5.2
You can upgrade from Prime Central Fault Management 1.5.1 to 1.5.2 . For Prime Central Fault Management servers that just meet the minimum server requirements specified in this guide, you must update the timeout value in the soap.client.props file before upgrading. Do the following:
-
Enter the following commands:
# su - primeusr
# vim ~/faultmgmt/tipv2/profiles/TIPProfile/properties/soap.client.props
-
Change the value of the com.ibm.SOAP.requestTimeout parameter to 3600.

Note
The default value set on the server is 600.
Make sure that the Prime Central Fault Management service is up before starting with the Fault Management upgrade. For example, fmctl status .
Procedure
| Step 1 |
Move (or remove) all *.log files from the /tmp folder. For example, rm /tmp/*.log |
||
| Step 2 |
Use one of the following options to connect to the server where you want to upgrade Prime Central Fault Management:
|
||
| Step 3 |
As the root user, launch a terminal on the server where you want to upgrade Prime Central Fault Management. (If you logged in as a nonroot user, use su - to become the root user.) The C shell (csh) is recommended. To start the C shell, enter: /bin/cshIf you are using X server, continue to the next step. If you are using VNC, skip to Step 7. |
||
| Step 4 |
Set the DISPLAY variable: setenv DISPLAY hostname-or-IP-address:0.0 |
||
| Step 5 |
Verify that the display is set correctly: echo $DISPLAY In the command output, you should see: hostname-or-IP-address:0.0 |
||
| Step 6 |
Take backup of /var/.com.zerog.registry.xml file as /var/.com.zerog.registry.xml_backup_for_1.4.1 /var/.com.zerog.registry.xml_backup_for_1.5.1 For example, cp /var/.com.zerog.registry.xml /var/.com.zerog.registry.xml_backup_for_151 |
||
| Step 7 |
Execute the following commands to take debackup of netcool components deployment engine: su - primeusr cd .acsi_primeusr/bin setenv ./de_backupdb
-bfile <backupfile_full_path>
|
||
| Step 8 |
Log in as root user. |
||
| Step 9 |
Insert the Cisco Prime Central 1.5.2 USB drive into the USB port and navigate to the local folder where the drive is mounted. |
||
| Step 10 |
Copy the FM1.5.2 Build.tar.gz file to the server. |
||
| Step 11 |
Distribute the file: # tar -zxf FM1.5.2Build.tar.gz # cd Disk1/InstData/VM # chmod 755 primefm_v1.5.2.bin |
||
| Step 12 |
From the Fault Management folder, begin the upgrade: ./primefm_v1.5.2.bin |
||
| Step 13 |
In the Introduction window, click Next. If you are upgrading to Prime Central Fault Management 1.5.2 on the same server where 1.2 1.5.1 was installed, the following message is displayed: A previous installation exists on the system. Do you want to directly upgrade from 1.5.3.0 to 2.1.0.0?
|
||
| Step 14 |
Click OK to proceed with the upgrade. |
||
| Step 15 |
Verify that the information in the Pre-Installation Summary window is correct; then, click Install. The upgrade process is automatic and requires no user input. |
||
| Step 16 |
In the Upgrade Complete window, click Done. It might take 90 minutes or longer to upgrade Prime Central Fault Management, depending on your system performance. The log files are available in the installation-directory /faultmgmt/upgrade/ 1.5.1.0-1.5.2.0 /logs folder. |
||
| Step 17 |
During the upgrade, if any components fail to start, do the following as the primeusr user: |
Upgrading Prime Central Fault Management Silently from 1.5.3 to 2.0.0
You can upgrade Prime Central Fault Management without user interaction. In a silent upgrade, no messages or prompts appear on-screen, and interactive dialogs are not displayed. Information and answers that you would normally provide are read from a properties file.
Procedure
| Step 1 |
As the root user, launch a terminal on the server where you want to silently upgrade to Prime Central Fault Management 1.5.2 . (If you logged in as a nonroot user, enter the su - command to become the root user.) The C shell (csh) is recommended. To start the C shell, enter: /bin/csh |
| Step 2 |
Take backup of /var/.com.zerog.registry.xml file as /var/.com.zerog.registry.xml_backup_for_1.5.1 |
| Step 3 |
Take backup of /var/.com.zerog.registry.xml file as |
| Step 4 |
Insert the Cisco Prime Central 1.5.2 USB drive into the USB port and navigate to the local folder where the drive is mounted. |
| Step 5 |
Copy the FM 1.5.2 Build.tar.gz file to the server. |
| Step 6 |
Distribute the file: # tar -zxf FM1.5.2Build.tar.gz # cd Disk1/InstData/VM # chmod 755 primefm_v1.5.2.bin # chmod 755 primefm_v1.5.3.bin |
| Step 7 |
From the Fault Management folder, begin the silent upgrade: ./primefm_v.1.5.2.bin -i silent -f fm-install.properties For example, if your silent properties file is named PrimeFM_install.properties, enter: ./primefm_v1.5.2.bin -i silent -f PrimeFM_install.properties The silent upgrade log files are available in the installation-directory /faultmgmt/upgrade/ 1.5.1.0-1.5.2.0 /logs folder. |
| Step 8 |
During the upgrade, if any components fail to start, do the following as the primeusr user: |
Reverting to Prime Central Fault Management 1.5.1
After upgrading to Prime Central Fault Management 1.5.2 , you may find the need to revert to the previous version. To do so, complete the following procedure.
 Note |
By default the primeusr home folder is /opt/primeusr. If your primeusr home folder is different, specify that folder instead. |
Procedure
| Step 1 |
Confirm that the faultmgmt_ 1.5.1.0 _backup folder was created.
|
||
| Step 2 |
Stop all Fault Management processes: su - primeusr fmctl stop exit (As the root user) pkill nco_pad |
||
| Step 3 |
Move the faultmgmt folder to the tmp folder: su - primeusr mv ~/faultmgmt /tmp/faultmgmt |
||
| Step 4 |
Move the faultmgmt_ 1.5.1.0 _backup folder to the faultmgmt folder: su - primeusr mv ~/faultmgmt_1.4.0.0_backup/faultmgmt ~/ mv ~/faultmgmt_1.5.1.0_backup/faultmgmt ~/ |
||
| Step 5 |
Restore debackup obtained before the upgrade: cd .acsi_primeusr/bin setenv ./de_restoredb -bfile <backupfile_full_path> |
||
| Step 6 |
Open the .cshrc file: su - primeusr vi ~/.cshrc Find the following line and change jre 1.8 to jre 1.7: setenv JAVA_HOME "$PRIMEFMHOME/utils/${OSTYPE}/jre1.8/" |
||
| Step 7 |
As the root user, start the nco_pad process: For example: For example: cd /opt/primeusr/faultmgmt/omnibus/bin ./nco_pad |
||
| Step 8 |
Perform the below mentioned steps:
As a root user, execute the below commands: su - primeusr itgctl stop itgctl start |
||
| Step 9 |
Perform the below mentioned steps:
As a root user, execute the below commands: su - primeusr itgctl stop itgctl start |
||
| Step 10 |
Reintegrate Fault Management with Prime Central: su - primeusr fmctl integrate |
||
| Step 11 |
Restore the /var/.com.zerog.registry.xml file with the backup file: /var/.com.zerog.registry.xml_backup_for_1.5.1 that was created during Prime Central Fault Management upgrade process. Execute below
commands:
|
||
| Step 12 |
Restore the /var/.com.zerog.registry.xml file with the backup file: /var/.com.zerog.registry.xml_backup_for_1.5.2 that was created during Prime Central Fault Management upgrade process. Execute below commands:
|
Upgrading RHEL Operating System
The Operating System (OS) upgrade procedure supports Prime Central 1.5.1 customers to perform upgrade of Operating System from RHEL 5.8 to 6.5 and inline upgrade from RHEL 5.8 or 6.5 to 6.7, 6.5.or 6.7 to 6.8.. For more information, refer the Cisco Prime Central RHEL Operating System Upgrade guide.
Uninstalling Prime Central
You can use the GUI to uninstall the various Prime Central components, or you can uninstall them silently.
Uninstalling Prime Central in an Embedded Database Configuration
If you installed an embedded database, it is uninstalled automatically when you uninstall Prime Central.
The following procedure removes all files from the installation directory. This procedure also removes the database and its contents. Database backups are not removed if they reside in a different directory from the installation directory.
If you upgrade Prime Central and then uninstall it, the /opt/primecentral_backup_ 1.5.2 folder is removed during uninstallation.
 Note |
If you installed the Fault Management component in the same directory as Prime Central, you must uninstall the Fault Management component before uninstalling Prime Central. See Uninstalling Prime Central Fault Management. |
Procedure
| Step 1 |
Depending on how you installed Prime Central, use one of the following options to connect to the server where you want to uninstall Prime Central:
|
| Step 2 |
As the root user, launch a terminal on the server where you want to uninstall Prime Central. (If you logged in previously as a nonroot user, enter the su - command to become the root user.) |
| Step 3 |
Enter: cd /var/adm/cisco/uninstall/Uninstall_Prime_Central/ ./Uninstall_Prime_Central |
| Step 4 |
Verify that the information in the Uninstall Prime Central window is correct; then, click Uninstall. |
| Step 5 |
In the Uninstall Complete window, click Done. The uninstallation log files are available at /var/adm/cisco/uninstall/UNINSTALL_LOG_time-stamp. |
Uninstalling Prime Central in an External Database Configuration
In a dual-server setup, you must uninstall the Prime Central integration layer before uninstalling the Prime Central portal. Perform the following steps on the integration layer server first; then, repeat them on the Prime Central portal server.
If you installed the Fault Management component in the same directory as Prime Central, you must uninstall the Fault Management component before uninstalling Prime Central. See Uninstalling Prime Central Fault Management.
Procedure
| Step 1 |
Depending on how you installed Prime Central, use one of the following options to connect to the server where you want to uninstall Prime Central:
|
| Step 2 |
As the root user, launch a terminal on the server where you want to uninstall Prime Central. (If you logged in previously as a nonroot user, enter the su - command to become the root user.) |
| Step 3 |
Enter: cd /var/adm/cisco/uninstall/Uninstall_Prime_Central/ ./Uninstall_Prime_Central |
| Step 4 |
Verify that the information in the Uninstall Prime Central window is correct; then, click Next. |
| Step 5 |
In the Database Information window, enter the database system password and confirm the following information for your preinstalled Oracle database server. Except for the password, the values are prepopulated with the information that you entered during installation:
|
| Step 6 |
Click Uninstall. |
| Step 7 |
In the Uninstall Complete window, click Done. The uninstallation log files are available at /var/adm/cisco/uninstall/UNINSTALL_LOG_time-stamp. |
Uninstalling Prime Central Silently
Procedure
| Step 1 |
Navigate to the /var/adm/cisco/uninstall/Uninstall_Prime_Central directory. The uninstall folder contains the installvariables.properties file. |
| Step 2 |
Run the silent uninstallation: ./Uninstall_Prime_Central -i silent The uninstallation log files are available at /var/adm/cisco/uninstall/UNINSTALL_LOG_time-stamp. |
Uninstalling Prime Central Fault Management
When you uninstall the Fault Management component, its subcomponents (except for the backup folder) are also uninstalled.
Procedure
| Step 1 |
Depending on how you installed the Fault Management component, use one of the following options to connect to the server where you want to uninstall Prime Central:
|
| Step 2 |
As the root user, launch a terminal on the server where you want to uninstall Prime Central Fault Management. (If you logged in previously as a nonroot user, enter the su - command to become the root user.) |
| Step 3 |
Enter: cd /var/adm/cisco/uninstall/Uninstall_Prime_Central_Fault_Management ./Uninstall_Prime_Central_Fault_Management |
| Step 4 |
Verify that the information in the Uninstall Prime Central Fault Management window is correct; then, click Uninstall. |
| Step 5 |
In the Uninstall Complete window, click Done. The uninstallation log files are available at /var/adm/cisco/uninstall/PrimeFM-uninstall.log-time-stamp and /tmp/primefm_uninstall.log. |
| Step 6 |
If the Fault Management uninstallation hangs without creating a log file, the RSA key entry might be missing from the ~/.ssh/known_hosts file. Do the following to generate the RSA key and add it to the server: |
| Step 7 |
Remove Prime Central Fault Management from the Prime Central portal:
|
| Step 8 |
As the primeusr user, log in to the Prime Central integration layer and restart it: itgctl stop itgctl start |
Uninstalling Prime Central Fault Management Silently
Procedure
| Step 1 |
Navigate to the /var/adm/cisco/uninstall/Uninstall_Prime_Central_Fault_Management directory. The uninstall folder contains the installvariables.properties file. |
| Step 2 |
Run the silent uninstallation: ./Uninstall_Prime_Central_Fault_Management -i silent The uninstallation log files are available at /var/adm/cisco/uninstall/PrimeFM-uninstall.log-time-stamp and /tmp/primefm_uninstall.log. |
| Step 3 |
Remove Prime Central Fault Management from the Prime Central portal:
|
| Step 4 |
As the primeusr user, log in to the Prime Central integration layer and restart it: itgctl stop itgctl start |
Unregistering an Application from Prime Central
You can completely unregister an application from Prime Central.
 Note |
|
Unregistering Cisco InTracer
Procedure
| Step 1 |
On the Cisco InTracer server, do the following: |
| Step 2 |
On the Prime Central portal, do the following: |
| Step 3 |
As the primeusr user, log in to the Prime Central integration layer and restart it: |
Unregistering Prime Network
Procedure
| Step 1 |
On the Prime Network gateway server, do the following: |
| Step 2 |
On the Prime Central portal, do the following: |
| Step 3 |
As the primeusr user, log in to the Prime Central integration layer and restart it: itgctl stop itgctl start |
Unregistering the Prime Network Integration Layer
In a suite environment, it is not recommended to unregister the Prime Network integration layer. However, if you must unregister (for troubleshooting, for example), complete the following steps:
Procedure
| Step 1 |
Remove the Prime Network integration layer from the Prime Central portal:
|
| Step 2 |
Disable the Prime Network integration layer health checker: |
| Step 3 |
Stop the Prime Network integration layer: itgctl stop |
| Step 4 |
Delete the dmid.xml file: rm $PRIMEHOME/integration/dmid.xml Unregistering the Prime Network integration layer is a temporary measure. When troubleshooting is complete, reintegrate the Prime Central integration layer to restore normal operation in a suite environment and allow other applications to resume communication with Prime Network. |
Unregistering Prime Optical
Procedure
| Step 1 |
On the Prime Optical server, enter: opticalctl stop |
| Step 2 |
On the Prime Central portal, do the following: |
| Step 3 |
As the primeusr user, log in to the Prime Central integration layer and restart it: |
Unregistering the Prime Optical Integration Layer
Procedure
| Step 1 |
From the Prime Central menu, choose . |
| Step 2 |
In the Suite Monitoring portlet, click the Prime Central tab. |
| Step 3 |
Click the Prime Optical Integration Layer radio button and click Remove. |
| Step 4 |
At the confirmation prompt, click OK. |
Unregistering Prime Performance Manager
Procedure
| Step 1 |
As the root user, log in to the Prime Performance Manager gateway server and navigate to the Prime-Performance-Manager-gateway-installation-directory/bin directory. |
||
| Step 2 |
Enter: ./ppm primecentralintegration remove
The
system prompts to restart Prime Performance Manager.
|
||
| Step 3 |
Restart Prime Performance Manager for the changes to take effect. |
||
| Step 4 |
On the Prime Central portal, do the following:
|
||
| Step 5 |
As the primeusr user, log in to the Prime Central integration layer and restart it: |
Unregistering Prime Provisioning
Procedure
| Step 1 |
On the Prime Central portal, do the following: |
| Step 2 |
Navigate to the Prime Provisioning installation directory and restart the Prime Provisioning server: |
| Step 3 |
As the primeusr user, log in to the Prime Central integration layer and restart it: |
| Step 4 |
Login to Prime Provisioning server and navigate to the directory where Prime Provisioning is installed. |
| Step 5 |
Navigate to <INSTALL_DIR>/prime_integrator directory and delete dmid.xml. |
Unregistering Cisco ME 4600 Series Agora-NG
Procedure
| Step 1 |
On the Agora-NG server, run the following command: $ rm /opt/ptin/agorang/share/primecentral/dmid.xml |
| Step 2 |
SSH to the Prime Central server. |
| Step 3 |
Enter: su – primeusr |
| Step 4 |
Run the list command and find the ID value assigned to the Agora-NG server. You will need this for Step 6. |
| Step 5 |
Enter the following commands: cd ~/install/scripts ./dmRemoveUtil |
| Step 6 |
Enter the centraladmin user’s username and password, as well as the Agora-NG server’s ID value you found in Step 4. |
Unregistering Cisco BAC
Procedure
| Step 1 |
SSH to the Prime Central server. |
| Step 2 |
Enter: su – primeusr |
| Step 3 |
Run the list command and find the ID value assigned to the Cisco BAC server. You will need this for Step 5. |
| Step 4 |
Enter the following commands: cd ~/install/scripts ./dmRemoveUtil |
| Step 5 |
Enter the centraladmin user’s username and password, as well as the Cisco BAC server’s ID value you found in Step 3. |
| Step 6 |
On the Cisco BAC server, run the following command to remove the trap sender: home-directory/snmp/bin/snmpAgentCfgUtil.sh delete host FM-server where:
|
| Step 7 |
Unregistering RMS from Prime Central
To rerun the Cisco RMS integration with Prime Central on the Central node, complete the procedures listed in this section. It is mandatory to unregister Cisco RMS with Prime Central NMS before the rerun:
-
Disabling SNMP Traps Notification to Prime Central NMS Interface
-
Cleaning up Files on Central Node
-
Unregistering RMS Data Manager from Prime Central
Disabling SNMP Traps Notification to Prime Central NMS Interface
Follow these steps to disable SNMP traps notifications to the Prime Central NMS interface on the Cisco RMS Central node:
Procedure
| Step 1 |
Log in to the Central node and run the following commands.
Example:
|
| Step 2 |
Enter the number of SNMP managers to be configured as ' 0 ' to deregister the PC NMS interface. This will disable the SNMP traps notification. The script execution output log is displayed as follows: Example
|
Cleaning Up Files On Central Node
To clean up the files on the Central node, that was generated from the earlier Prime Central integration procedure, complete the following steps:
Procedure
| Step 1 |
Go to the directory
|
||
| Step 2 |
Enter
|
||
| Step 3 |
Enter It is recommended to restart [Stop and Start] the SNMP agent. For example, enter /etc/init.d # ./snmpd restart.
|
Unregistering RMS Data Manager from Prime Central
Unregister RMS Data Manager from Prime Central, which was used to integrate RMS with Prime Central earlier
Procedure
| Step 1 |
Log in to the Prime Central server using ssh with 'root' user ID and its password. |
||
| Step 2 |
Enter |
||
| Step 3 |
Execute the list command to find the ID value assigned to the RMS host (Central node host name). |
||
| Step 4 |
Enter
|
||
| Step 5 |
Enter
|
||
| Step 6 |
Log out from the Prime Central server. |
Unregistering Cisco Prime Access Registrar (CPAR) from Prime Central
Procedure
| Step 1 |
From the Fault Source Management portlet, select the CPAR domain manager you want to remove. |
| Step 2 |
Click Delete. |
| Step 3 |
On the CPAR server, to remove Prime Central trap recipient, delete the Prime Central entry from the following configuration file:
|
| Step 4 |
Enter the following command to restart the CPAR server to reflect the changes:
|
Unregistering Cisco Prime Network Registrar (CPNR) from Prime Central
Procedure
| Step 1 |
From the Fault Source Management portlet, select the CPNR domain manager you want to remove. |
| Step 2 |
Click Delete. After
the CPNR fault source is deleted, CPNR domain manager instance is De-Registered
with Prime Central.
|
| Step 3 |
On the CPNR server, to remove prime central trap recipient execute the following command:
/opt/nwreg2/local/usrbin/nrcmd -s
The
|
Unregistering SpiderNet from Prime Central
Procedure
| Step 1 |
From the Fault Source Management portlet, select the SpiderNet domain manager you want to remove. |
| Step 2 |
Click Delete. |
| Step 3 |
Login to SpiderNet GUI. |
| Step 4 |
On the SpiderNet server, to remove Prime Central trap recipient, delete the Prime Central SNMP Manager Group:
|
Next Steps
You can start and stop the Prime Central components and set up a backup schedule.
Starting and Stopping the Prime Central Components
As the primeusr, enter the commands shown in the following table to start and stop the various Prime Central components.
| Action | Command | ||
|---|---|---|---|
|
Prime Central Portal |
|||
|
Start |
portalctl start |
||
|
Stop |
portalctl stop |
||
|
Restart |
portalctl stop portalctl start
|
||
|
Obtain status |
portalctl status |
||
|
Enable debug logging |
portalctl start log
|
||
|
Prime Central Integration Layer |
|||
|
Start |
itgctl start |
||
|
Stop |
itgctl stop |
||
|
Restart |
itgctl stop itgctl start
|
||
|
Obtain status |
itgctl status |
||
|
List instances |
itgctl list
|
||
|
Fault Management |
|||
|
Start |
fmctl start |
||
|
Stop |
fmctl stop |
||
|
Obtain status |
fmctl status |
||
|
Restart |
fmctl restart |
||
|
Integrate with Prime Central |
fmctl integrate |
||
|
Synchronize with one or more Domain Managers |
fmctl resync |
||
|
Configimpact |
fmctl configimpact <centraladmin
pwd>
|
||
|
Impact |
fmctl <start/stop/restart> impact |
||
|
OMNI bus and Common Reporting |
fmctl <start/stop/restart> tip |
||
|
Registration with Domain Manager |
fmctl <start/stop/restart> registration |
||
Backing Up and Restoring the Embedded Database
As the primeusr user, enter the commands shown in the following table to back up and restore the Prime Central embedded database.
| Action | Command |
|---|---|
|
Start |
emdbctl --start |
|
Stop |
emdbctl --stop |
|
Enable backups |
emdbctl --enable_backup |
|
Back up the database |
emdbctl --backup |
|
Restore the database |
emdbctl --restore |
|
Obtain database status |
emdbctl --db_status |
Note the following:
-
These commands should be run only on the server where the Prime Central portal is installed with an embedded Oracle database.
-
Shut down the Prime Central portal and the Prime Central integration layer before restoring the database. Restart them after the database restore is complete.
-
By default, the option to enable backups is checked during installation. If you uncheck it during installation but later decide to enable automatic backups, you must enter the emdbctl --enable_backup command to do so.
-
An automatic backup runs daily at 4:00 a.m. A full backup runs every Saturday; incremental backups run on all other days.
-
By default, Prime Central saves eight database backups to ORACLE_HOME/backup. Your system administrator must back up the database backups and archive directories to tape daily.
-
The emdbctl --restore command prompts you to enter a date and time to restore a database backup. The format is MM-DD-YYYY HH:MI; for example, 07-30-2013 03:34. If you enter a date in the wrong format, or if the backup cannot be restored for the date and time entered, the database will instead be restored to the most recent possible date and time.
-
The emdbctl --restore should not be used in HA/GEO setup as it may break the HA configuration.
Backing Up and Restoring the Fault Management Database
Prime Central Fault Management alarms are stored in the Fault Management database. These same alarms are also forwarded and stored on the Prime Central Oracle database. Both the Prime Central and Fault Management databases are automatically backed up daily. By default, the Fault Management backups are saved in $NCHOME/omnibus/backup/NCOMS/. You can create a cron job that periodically copies the backups to an offsite location.
If a manual backup is required, you can back up and restore the data manually.
Backing Up the Fault Management Database Manually
Procedure
| Step 1 |
Log in to the Fault Management server and then stop it: fmctl stop |
| Step 2 |
Choose a backup location within the primeusr directory structure (for example, ~/omnibus-backup/): mkdir -p backup-location/db cp -r $NCHOME/omnibus/db/NCOMS/* backup-location/db |
| Step 3 |
Back up the miscellaneous files, if they were changed manually: mkdir -p backup-location/misc cp -r $NCHOME/omnibus/etc backup-location/misc |
| Step 4 |
Back up the log files: cp -r $NCHOME/omnibus/log backup-location/misc |
| Step 5 |
Start the Fault Management server: fmctl start |
Restoring the Fault Management Database Manually
Procedure
| Step 1 |
Stop the Fault Management server: fmctl stop |
||
| Step 2 |
Restore the previously saved database files: rm -rf $NCHOME/omnibus/db/NCOMS/* cp backup-location/db/* $NCHOME/omnibus/db/NCOMS |
||
| Step 3 |
Restore the miscellaneous files, if they were backed up: cp -r backup-location/misc/etc $NCHOME/omnibus
|
||
| Step 4 |
Start the Fault Management server: fmctl start |
 Feedback
Feedback