BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
Available Languages
Table Of Contents
BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
Prerequisites for BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
Restrictions for BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
Information About BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
How to Configure BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
Configuring a PE Router to Support BGP NSR with SSO
Configuring a Peer to Support BGP NSR with SSO
Configuring a Peer Group to Support BGP NSR with SSO
Configuring Support for BGP NSR with SSO in a Peer Session Template
Verifying BGP Support for NSR with SSO
Configuration Examples for BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
Configuring BGP NSR with SSO: Example
show ip bgp vpnv4 all sso summary
Feature Information for BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
First Published: March 20, 2006Last Updated: March 20, 2006The BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO) feature enables provider edge (PE) routers to maintain Border Gateway Protocol (BGP) state with customer edge (CE) routers and ensure continuous packet forwarding during a Route Processor (RP) switchover or during a planned In-Service Software Upgrade (ISSU) for a PE router. CE routers do not need to be Nonstop Forwarding (NSF)-capable or NSF-aware to benefit from BGP NSR capabilities on PE routers. Only PE routers need to be upgraded to support BGP NSR—no CE router upgrades are required. BGP NSR with SSO, thus, enables service providers to provide the benefits NSF with the additional benefits of NSR without requiring CE routers to be upgraded to support BGP graceful restart.
Finding Feature Information in This Module
Your Cisco IOS software release may not support all of the features documented in this module. To reach links to specific feature documentation in this module and to see a list of the releases in which each feature is supported, use the "Feature Information for BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)" section.
Finding Support Information for Platforms and Cisco IOS Software Images
Use Cisco Feature Navigator to find information about platform support and Cisco IOS software image support. Access Cisco Feature Navigator at http://www.cisco.com/go/fn. You must have an account on Cisco.com. If you do not have an account or have forgotten your username or password, click Cancel at the login dialog box and follow the instructions that appear.
Contents
•
Prerequisites for BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
•
Restrictions for BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
•
Information About BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
•
How to Configure BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
•
Configuration Examples for BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
Prerequisites for BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
•
This document assumes that your network is configured to run BGP.
•
This document assumes that Multiprotocol Layer Switching (MPLS) Layer 3 Virtual Private Networks (VPNs) are configured.
•
This document assumes that you are familiar NSF and SSO concepts and tasks.
Restrictions for BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
•
This feature is supported on Cisco 10000 Series Performance Routing Engines 2 (PRE2s) and Cisco 10000 Series Performance Routing Engines 3 (PRE3s) .
Information About BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
To configure BGP NSR with SS0, you should be familiar with the following concepts:
Overview of BGP NSR with SSO
Prior to the introduction of BGP NSR with SS0 in Cisco IOS Release 12.2(28)SB, BGP required that all neighboring devices participating in BGP NSF be configured to be either NSF-capable or NSF-aware (by configuring the devices to support the BGP graceful restart mechanism). BGP NSF, thus, required that all neighboring devices be upgraded to a version of Cisco IOS software that supports BGP graceful restart. However, in many MPLS VPN deployments, there are situations where PE routers engage in exterior BGP (eBGP) peering sessions with CE routers that do not support BGP graceful restart and cannot be upgraded to a software version that supports BGP graceful restart in the same time frame as the provider (P) routers.
BGP NSR with SSO provides a high availability (HA) solution to service providers whose PE routers engage in eBGP peering relationships with CE routers that do not support BGP graceful restart. BGP NSR works with SSO to synchronize BGP state information between the active and standby RP. SSO minimizes the amount of time a network is unavailable to its users following a switchover. When the BGP NSR with SSO feature is configured, in the event of an RP switchover, the PE router uses BGP NSR with SSO to maintain BGP state for eBGP peering sessions with CEs that are not NSF-aware (see Figure 1). Additionally, the BGP NSR with SSO feature dynamically detects NSF-aware peers and runs graceful restart with those CE routers. For eBGP peering sessions with NSF-aware peers and for internal BGP (iBGP) sessions with BGP Route Reflectors (RRs) in the service provider core, the PE uses NSF to maintain BGP state. BGP NSR with SSO, thus, enables service providers to provide the benefits of NSF with the additional benefits of NSR without requiring CE routers to be upgraded to support BGP graceful restart.
Figure 1 BGP NSR with SSO Operations During an RP Switchover
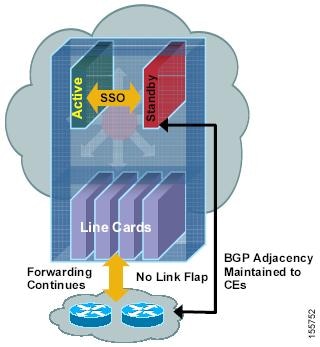
BGP NSR with SSO is supported in BGP peer, BGP peer group, and BGP session template configurations. To configure support for BGP NSR with SSO in BGP peer and BGP peer group configurations, use the neighbor ha-mode sso command in address family configuration mode for IPv4 VRF address family BGP peer sessions. To include support for Cisco BGP NSR with SSO in a peer session template, use the ha-mode sso command in session-template configuration mode.
Benefits of BGP NSR with SSO
•
Minimizes services disruptions—BGP NSR with SSO reduces impact on customer traffic during RP switchovers (scheduled or unscheduled events), extending HA deployments and benefits at the edge.
•
Enhances high-availability NSF and SSO deployment at the edge—BGP NSR with SSO allows incremental deployment by upgrading the provider edge with the NSR capability so that customer-facing edge routers are synchronized automatically and no coordination or NSF awareness is needed with the customer side Cisco or third-party customer edge routers. The BGP NSR feature dynamically detects NSF-aware peers and runs graceful restart with those CE routers.
•
Provides transparent route convergence—BGP NSR with SSO eliminates route flaps by keeping BGP state on both active and standby RPs and ensures continuous packet forwarding with minimal packet loss during RP failovers.
How to Configure BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
This section contains the following procedures:
•
Configuring a PE Router to Support BGP NSR with SSO (required)
•
Verifying BGP Support for NSR with SSO (optional)
Configuring a PE Router to Support BGP NSR with SSO
Perform this task to enable a PE router to maintain BGP state with CE routers and ensure continuous packet forwarding during a RP switchover or during a planned ISSU. BGP NSR with SSO enables service providers to provide the benefits NSF with the additional benefits of NSR without requiring CE routers to be upgraded to support BGP graceful restart.
BGP NSR with SSO is supported in BGP peer, BGP peer group, and BGP session template configurations. Perform one of the following tasks in this section on a PE router, depending on whether you want to configure support for BGP NSR with SSO in a peer, a peer group, or a session template configuration:
•
Configuring a Peer to Support BGP NSR with SSO
•
Configuring a Peer Group to Support BGP NSR with SSO
•
Configuring Support for BGP NSR with SSO in a Peer Session Template
Prerequisites
•
These tasks assume that you are familiar with BGP peer, BGP peer group, and BGP session template concepts. For more information, see the "Configuring a Basic BGP Network" chapter in the
Cisco IOS IP Routing Configuration Guide, Release 12.4.•
The active and standby RP must be in SSO mode. For information about configuring SSO mode, see the "Configuring SSO" task in the Stateful Switchover document.
•
Graceful restart should be enabled on the PE router. For more information about configuring graceful restart, see the "BGP Nonstop Forwarding (NSF) Awareness" document.

Note
We recommend that you enable graceful restart on all BGP peers in the provider core that participate in BGP NSF.
•
CE routers must support the route refresh capability. For more information, refer to the "BGP" part of the Cisco IOS IP Configuration Guide, Release 12.4.
Restrictions
•
This feature is supported only on Cisco 10000 Series PRE2s and Cisco 10000 Series PRE3s.
Configuring a Peer to Support BGP NSR with SSO
Perform this task on a PE router if you want to configure a BGP peer to support BGP NSR with SSO.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
router bgp autonomous-system-number
4.
bgp graceful-restart [restart-time seconds] [stalepath-time seconds]
5.
address-family ipv4 vrf vrf-name
6.
neighbor ip-address remote-as autonomous-system-number
7.
neighbor ip-address ha-mode sso
8.
neighbor ip-address activate
9.
end
10.
show ip bgp vpnv4 all sso summary
DETAILED STEPS
Step 1
enable
Example:Router> enable
Enables privileged EXEC mode.
•
Enter your password if prompted.
Step 2
configure terminal
Example:Router# configure terminal
Enters global configuration mode.
Step 3
router bgp autonomous-system-number
Example:Router(config)# router bgp 40000
Enters router configuration mode for the specified routing process.
Step 4
bgp graceful-restart [restart-time seconds] [stalepath-time seconds]
Example:Router(config-router)# bgp graceful-restart
Enables the BGP graceful restart capability and BGP NSF awareness.
•
If you enter this command after the BGP session has been established, you must restart the session for the capability to be exchanged with the BGP neighbor.
•
Use this command on the restarting router and all of its peers (NSF-capable and NSF-aware).
Step 5
address-family ipv4 vrf vrf-name
Example:Router(config-router)# address-family ipv4 vrf test
Enters address family configuration mode for IPv4 VRF address family sessions.
•
The vrf keyword and vrf-name argument specify that IPv4 VRF instance information will be exchanged.
Note
Only the syntax necessary for this task is displayed. For more details, see the Cisco IOS IP Routing: BGP Command Reference.
Step 6
neighbor ip-address remote-as autonomous-system-number
Example:Router(config-router-af)# neighbor 192.168.1.1 remote-as 45000
Adds the IP address of the neighbor in the specified autonomous system to the IPv4 multiprotocol BGP neighbor table of the local router.
Step 7
neighbor ip-address ha-mode sso
Example:Router(config-router-af)# neighbor 192.168.1.1 ha-mode sso
Configures the neighbor to support BGP NSR with SSO.
Step 8
neighbor ip-address activate
Example:Router(config-router-af)# neighbor testgroup activate
Enables the neighbor to exchange prefixes for the IPv4 address family with the local router.
Note
By default, neighbors that are defined using the neighbor remote-as command in router configuration mode exchange only unicast address prefixes.
Step 9
end
Example:Router(config-router-af)# end
Exits address family configuration mode and enters privileged EXEC mode.
Step 10
show ip bgp vpnv4 all sso summary
Example:Router# show ip bgp vpnv4 all sso summary
(Optional) Displays the number of BGP neighbors that are in SSO mode.
Configuring a Peer Group to Support BGP NSR with SSO
Perform this task on a PE router if you want to configure a BGP peer group to support BGP NSR with SSO.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
router bgp autonomous-system-number
4.
bgp graceful-restart [restart-time seconds] [stalepath-time seconds]
5.
address-family ipv4 vrf vrf-name
6.
neighbor peer-group-name peer-group
7.
neighbor ip-address remote-as autonomous-system-number
8.
neighbor ip-address peer-group peer-group-name
9.
neighbor peer-group-name ha-mode sso
10.
neighbor peer-group-name activate
11.
end
12.
show ip bgp vpnv4 all sso summary
DETAILED STEPS
Step 1
enable
Example:Router> enable
Enables privileged EXEC mode.
•
Enter your password if prompted.
Step 2
configure terminal
Example:Router# configure terminal
Enters global configuration mode.
Step 3
router bgp autonomous-system-number
Example:Router(config)# router bgp 40000
Enters router configuration mode for the specified routing process.
Step 4
bgp graceful-restart [restart-time seconds] [stalepath-time seconds]
Example:Router(config-router)# bgp graceful-restart
Enables the BGP graceful restart capability and BGP NSF awareness.
•
If you enter this command after the BGP session has been established, you must restart the session for the capability to be exchanged with the BGP neighbor.
•
Use this command on the restarting router and all of its peers (NSF-capable and NSF-aware).
Step 5
address-family ipv4 vrf vrf-name
Example:Router(config-router)# address-family ipv4 vrf cisco
Specifies the IPv4 address family and enters address family configuration mode.
•
The vrf keyword and vrf-name argument specify that IPv4 VRF instance information will be exchanged.
Note
Only the syntax necessary for this task is displayed. For more details, see the Cisco IOS IP Routing Protocols Command Reference.
Step 6
neighbor peer-group-name peer-group
Example:Router(config-router-af)# neighbor testgroup peer-group
Creates a BGP peer group.
Step 7
neighbor ip-address remote-as autonomous-system-number
Example:Router(config-router-af)# neighbor 192.168.1.1 remote-as 45000
Adds the IP address of the neighbor in the specified autonomous system to the IPv4 multiprotocol BGP neighbor table of the local router.
Step 8
neighbor ip-address peer-group peer-group-name
Example:Router(config-router-af)# neighbor 192.168.1.1 peer-group testgroup
Assigns the IP address of a BGP neighbor to a BGP peer group.
Step 9
neighbor peer-group-name ha-mode sso
Example:Router(config-router-af)# neighbor 192.168.1.1 ha-mode sso
Configures the BGP peer group to support BGP NSR with SSO.
Step 10
neighbor peer-group-name activate
Example:Router(config-router-af)# neighbor testgroup activate
Enables the neighbor to exchange prefixes for the IPv4 address family with the local router.
Step 11
end
Example:Router(config-router-af)# end
Exits address family configuration mode and returns to global configuration mode.
Step 12
show ip bgp vpnv4 all sso summary
Example:Router# show ip bgp vpnv4 all sso summary
(Optional) Displays the number of BGP neighbors that are in SSO mode.
Configuring Support for BGP NSR with SSO in a Peer Session Template
Perform this task on a PE router if you want to configure support for BGP NSR with SSO in a BGP peer session template.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
router bgp autonomous-system-number
4.
template peer-session session-template-name
5.
ha-mode sso
6.
exit-peer-session
7.
end
8.
show ip bgp template peer-session [session-template-name]
DETAILED STEPS
What to Do Next
After the peer session template is created, the configuration of the peer session template can be inherited by or applied to another peer session template with the inherit peer-session or neighbor inherit peer-session command.
For more information about configuring peer session templates, see the "Configuring a Basic BGP Network" chapter in the Cisco IOS IP Routing Configuration Guide, Release 12.4.
Verifying BGP Support for NSR with SSO
Perform this optional task to verify BGP NSR with SSO support.
SUMMARY STEPS
1.
enable
2.
show ip bgp vpnv4 all sso summary
3.
show ip bgp vpnv4 all neighbors
DETAILED STEPS
Step 1
enable
Enables privileged EXEC mode. Enter your password if prompted.
Router> enableStep 2
show ip bgp vpnv4 all sso summary
This command is used to display the number of BGP neighbors that are in SSO mode.
The following is sample output from the show ip bgp vpnv4 all sso summary command:
Router# show ip bgp vpnv4 all sso summaryStateful switchover support enabled for 40 neighborsStep 3
show ip bgp vpnv4 all neighbors
This command displays VPN address information from the BGP table.
The following is sample output from the show ip bgp vpnv4 all neighbors command. The "Stateful switchover support" field indicates whether SSO is enabled or disabled. The "SSO Last Disable Reason" field displays information about the last BGP session that lost SSO capability.
Router# show ip bgp vpnv4 all neighbors 10.3.3.3BGP neighbor is 10.3.3.3, vrf vrf1, remote AS 3, external linkInherits from template 10vrf-session for session parametersBGP version 4, remote router ID 10.1.105.12BGP state = Established, up for 04:21:39Last read 00:00:05, last write 00:00:09, hold time is 30, keepalive interval is 10 secondsConfigured hold time is 30, keepalive interval is 10 secondsMinimum holdtime from neighbor is 0 secondsNeighbor capabilities:Route refresh: advertised and received(new)Address family IPv4 Unicast: advertised and receivedStateful switchover support enabledMessage statistics:InQ depth is 0OutQ depth is 0Sent RcvdOpens: 1 1Notifications: 0 0Updates: 1 4Keepalives: 1534 1532Route Refresh: 0 0Total: 1536 1537Default minimum time between advertisement runs is 30 secondsFor address family: VPNv4 UnicastTranslates address family IPv4 Unicast for VRF vrf1BGP table version 25161, neighbor version 25161/0Output queue size : 0Index 7, Offset 0, Mask 0x807 update-group memberInherits from template 10vrf-policyOverrides the neighbor AS with my AS before sending updatesOutbound path policy configuredRoute map for outgoing advertisements is Deny-CE-prefixesSent RcvdPrefix activity: ---- ----Prefixes Current: 10 50 (Consumes 3400 bytes)Prefixes Total: 10 50Implicit Withdraw: 0 0Explicit Withdraw: 0 0Used as bestpath: n/a 0Used as multipath: n/a 0Outbound InboundLocal Policy Denied Prefixes: -------- -------route-map: 150 0AS_PATH loop: n/a 760Total: 150 760Number of NLRIs in the update sent: max 10, min 10Address tracking is enabled, the RIB does have a route to 10.3.3.3Address tracking requires at least a /24 route to the peerConnections established 1; dropped 0Last reset neverTransport(tcp) path-mtu-discovery is enabledTCP session must be opened passivelyConnection state is ESTAB, I/O status: 1, unread input bytes: 0 Connection is ECN Disabled Local host: 10.0.21.1, Local port: 179 Foreign host: 10.0.21.3, Foreign port: 51205 Connection tableid (VRF): 1Enqueued packets for retransmit: 0, input: 0 mis-ordered: 0 (0 bytes)Event Timers (current time is 0x1625488):Timer Starts Wakeups NextRetrans 1746 210 0x0TimeWait 0 0 0x0AckHold 1535 1525 0x0SendWnd 0 0 0x0KeepAlive 0 0 0x0GiveUp 0 0 0x0PmtuAger 0 0 0x0DeadWait 0 0 0x0Linger 0 0 0x0iss: 2241977291 snduna: 2242006573 sndnxt: 2242006573 sndwnd: 13097irs: 821359845 rcvnxt: 821391670 rcvwnd: 14883 delrcvwnd: 1501SRTT: 300 ms, RTTO: 303 ms, RTV: 3 ms, KRTT: 0 msminRTT: 0 ms, maxRTT: 300 ms, ACK hold: 200 ms Status Flags: passive open, retransmission timeout, gen tcbs0x1000Option Flags: VRF id set, always push, md5Datagrams (max data segment is 4330 bytes):Rcvd: 3165 (out of order: 0), with data: 1535, total data bytes: 31824Sent: 3162 (retransmit: 210 fastretransmit: 0),with data: 1537, total databytes: 29300SSO Last Disable Reason: Application Disable (Active)Troubleshooting Tips
To troubleshoot BGP NSR with SSO, use the following commands in privileged EXEC mode, as needed:
•
debug ip bgp sso—Displays BGP-related SSO events or debugging information for BGP-related interactions between the active RP and the standby RP. This command is useful for monitoring or troubleshooting BGP sessions on a PE router during an RP switchover or during a planned ISSU.
•
debug ip tcp ha—Displays TCP HA events or debugging information for TCP stack interactions between the active RP and the standby RP. This is command is useful for troubleshooting SSO-aware TCP connections.
•
show tcp—Displays the status of TCP connections. The display output will display the SSO capability flag and will indicate the reason that the SSO property failed on a TCP connection.
•
show tcp ha connections—Displays connection-ID-to-TCP mapping data.
Configuration Examples for BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
This section contains the following configuration example:
•
Configuring BGP NSR with SSO: Example
Configuring BGP NSR with SSO: Example
Figure 2 illustrates a sample BGP NSR with SSO network topology, and the configuration examples that follow show configurations from three routers in the topology: the RR1 router, the PE router, and the CE-1 router.

Note
The configuration examples omit some of the configuration required for MPLS VPNs because the purpose of these examples is to illustrate the configuration of BGP NSR with SSO.
Figure 2 BGP NSR with SSO Example Topology
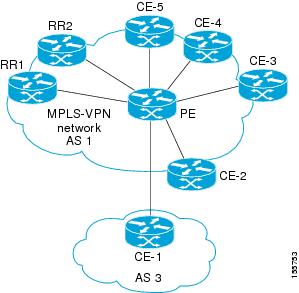
RR1 Configuration
The following example shows the BGP configuration for RR1 in Figure 2. RR1 is configured as a NSF-aware route reflector. In the event of an RP switchover, the PE router uses NSF to maintain the BGP state of the internal peering session with RR1.
!router bgp 1no synchronizationbgp log-neighbor-changesbgp graceful-restart restart-time 120bgp graceful-restart stalepath-time 360bgp graceful-restartneighbor 10.2.2.2 remote-as 1neighbor 10.2.2.2 update-source Loopback0no auto-summary!address-family vpnv4neighbor 10.2.2.2 activateneighbor 10.2.2.2 send-community bothneighbor 10.2.2.2 route-reflector-clientexit-address-family!PE Configuration
The following example shows the BGP NSR with SSO configuration for the PE router in Figure 2. The PE router is configured to support both NSF-awareness and the BGP NSR with SSO capability. In the event of an RP switchover, the PE router uses BGP NSR with SSO to maintain BGP state for the eBGP peering session with the CE-1 router, a CE router in this topology that is not NSF-aware, and uses NSF to maintain BGP state for the iBGP session with RR1. The PE router also detects if any of the other CE routers in the MPLS VPN network are NSF-aware and runs graceful restart with those CE routers.
!router bgp 2no synchronizationbgp log-neighbor-changesbgp graceful-restart restart-time 120bgp graceful-restart stalepath-time 360bgp graceful-restartneighbor 10.1.1.1 remote-as 1neighbor 10.1.1.1 update-source Loopback0no auto-summary!address-family vpnv4neighbor 10.1.1.1 activateneighbor 10.1.1.1 send-community bothexit-address-family!address-family ipv4 vrf ce-1neighbor 10.3.3.3 remote-as 3neighbor 10.3.3.3 ha-mode ssoneighbor 10.3.3.3 activateneighbor 10.3.3.3 as-overrideno auto-summaryno synchronizationexit-address-family!CE-1 Configuration
The following example shows the BGP configuration for CE-1 in Figure 2. The CE-1 router is configured as an external peer of the PE router. The CE-1 router is not configured to be NSF-capable or NSF-aware. The CE-1 router, however, does not need to be NSF-capable or NSF-aware to benefit from BGP NSR capabilities on the PE router nor does it need to be upgraded to support BGP NSR.
!router bgp 3neighbor 10.2.2.2 remote-as 1!Additional References
The following sections provide references related to configuring the BGP Support for NSR with SSO feature.
Related Documents
Standards
No new or modified standards are supported by this feature, and support for existing standards has not been modified by this feature.
—
MIBs
RFCs
Technical Assistance
Command Reference
This section documents new and modified commands.
•
show ip bgp vpnv4 all sso summary
debug ip bgp sso
To display Border Gateway Protocol (BGP)-related stateful switchover (SSO) events or debugging information for BGP-related interactions between the active Route Processor (RP) and the standby RP, use the debug ip bgp sso command in privileged EXEC mode. To disable debugging output, use the no form of this command.
debug ip bgp sso {events | transactions} [detail]
no debug ip bgp sso {events | transactions} [detail]
Syntax Description
Command Modes
Privileged EXEC
Command History
Usage Guidelines
The debug ip bgp sso command is used to display BGP-related SSO events or debugging information for BGP-related interactions between the active RP and the standby RP. This command is useful for monitoring or troubleshooting BGP sessions on a provider edge (PE) router during an RP switchover or during a planned In-Service Software Upgrade (ISSU).
Examples
The following is sample output from the debug ip bgp sso command with the events keyword. The following output indicates that the 10.34.32.154 BGP session is no longer SSO capable.
*Mar 28 02:29:43.526: BGPSSO: 10.34.32.154 reset SSO and decrement count
Tip
Use the show ip bgp vpnv4 all neighbors command to display the reason that the SSO-capable BGP session has been disabled.
The following is sample output from the debug ip bgp sso command with the transactions keyword. The following output shows an SSO notification indicating that the SSO capability is pending for 602 BGP neighbors. This notification is generated as the state between the active and standby RP is being synchronized during the bulk synchonization phase of SSO initialization. During this phase, the Transmission Control Blocks (TCBs) must be synchronized with the TCBs on the standby RP before SSO initialization is complete.
*Mar 28 02:32:12.102: BGPSSO: tcp sso notify pending for 602 nbrsdebug ip tcp ha
To display TCP high availabilty (HA) events or debugging information for TCP stack interactions between the active Route Processor (RP) and the standby RP, use the debug ip tcp ha command in privileged EXEC mode. To disable debugging output, use the no form of this command.
debug ip tcp ha {events | transactions} [detail]
no debug ip tcp ha {events | transactions} [detail]
Syntax Description
Command Modes
Privileged EXEC
Command History
Usage Guidelines
The debug ip tcp ha command is used to display TCP stateful switchover (SSO) events or debugging information for TCP stack interactions between the active RP and the standby RP. This is command is useful for troubleshooting SSO-aware TCP connections.
Use the debug ip tcp ha command with the transactions keyword to display failed TCP stack interactions between the active RP and standby RP. This form of the command displays failed TCP HA messages, RF redundancy-related client-application transactions, IPC client-application transactions, and In-Service Software Upgrade (ISSU) transactions.
Use the debug ip tcp ha command with the transactions and detail keywords to display successful TCP stack interactions between the active and standby RP. This form of the command displays successful TCP HA messages, RF redundancy-related client-application transactions, IPC client-application transactions, and ISSU transactions.
Use the debug ip tcp ha command with the events keyword to display TCP HA failures. This form of the command displays TCP HA failed encode or decode messages, system resources failures (such as memory allocation failures in the context of TCP HA), failed state changes, and failures that occur when SSO is enabled or disabled.
Use the debug ip tcp ha command with the events and detail keywords to display successful TCP HA operations and useful informational messages. This form of the command displays successful TCP encode or decode messages, state changes, and operations that occur when SSO is enabled or disabled.
Examples
The following is sample output from the debug ip tcp ha command with the transactions and detail keywords. The following output shows packet flow from the active to the standby RP for an established TCP SSO connection:
*Feb 19 23:28:23.324: TCPHA: Sending pkt msg, conn_id = 39, seq no = 2727115707*Feb 19 23:28:23.324: TCPHA: Sending pkt msg, conn_id = 396, seq no = 2959469308*Feb 19 23:28:23.324: TCPHA: Sending pkt msg, conn_id = 41, seq no = 1270243395*Feb 19 23:28:23.932: TCPHA: Sending pkt msg, conn_id = 42, seq no = 974255741*Feb 19 23:28:23.932: TCPHA: Sending pkt msg, conn_id = 475, seq no = 3059612402*Feb 19 23:28:24.544: TCPHA: Sending dummy pkt to standby; cid=109, size=19*Feb 19 23:28:42.976: TCPHA: Recd IPC msg len 24, type 3*Feb 19 23:28:42.976: TCPHA: Recd IPC msg len 24, type 3*Feb 19 23:28:43.172: TCPHA: Recd IPC msg len 79, type 2*Feb 19 23:28:43.172: TCPHA: Recd IPC msg len 79, typeneighbor ha-mode sso
To configure a Border Gateway Protocol (BGP) neighbor to support BGP Nonstop Routing (NSR) with stateful switchover (SSO), use the neighbor ha-mode sso command in the appropriate command mode. To remove the configuration, use the no form of this command.
neighbor ip-address ha-mode sso
no neighbor ip-address ha-mode sso
Syntax Description
Command Default
BGP NSR with SSO support is disabled.
Command Modes
Address family configuration
Session-template configurationCommand History
Usage Guidelines
The neighbor ha-mode sso command is used to configure a BGP neighbor to support BGP NSR with SSO. BGP NSR with SSO is disabled by default.
BGP NSR with SSO is supported in BGP peer, BGP peer group, and BGP session template configurations. To configure BGP NSR with SSO in BGP peer and BGP peer group configurations, use the neighbor ha-mode sso command in address family configuration mode for IPv4 VRF address family BGP peer sessions. To include support for Cisco BGP NSR with SSO in a peer session template, use the ha-mode sso command in session-template configuration mode.
Examples
The following example shows how to configure a BGP neighbor to support SSO:
Router(config-router-af)# neighbor 10.3.32.154 ha-mode ssoRelated Commands
show ip bgp vpnv4
Displays VPN address information from the BGP table.
show ip bgp vpnv4 all sso summary
Displays the number of BGP neighbors that support SSO.
show ip bgp vpnv4
To display Virtual Private Network Version 4 (VPNv4) address information from the Border Gateway Protocol (BGP) table, use the show ip bgp vpnv4 command in user EXEC or privileged EXEC mode.
show ip bgp vpnv4 {all | rd route-distinguisher | vrf vrf-name} [rib-failure] [ip-prefix/length [longer-prefixes]] [network-address [mask] [longer-prefixes]] [cidr-only] [community] [community-list] [dampened-paths] [filter-list] [flap-statistics] [inconsistent-as] [neighbors] [paths [line]] [peer-group] [quote-regexp] [regexp] [summary] [labels]
Syntax Description
Command Modes
User EXEC
Privileged EXECCommand History
Usage Guidelines
Use this command to display VPNv4 information from the BGP database. The show ip bgp vpnv4 all command displays all available VPNv4 information. The show ip bgp vpnv4 summary command displays BGP neighbor status. The show ip bgp vpnv4 all labels command displays explicit-null label information.
Examples
The following example shows output for all available VPNv4 information in a BGP routing table:
Router# show ip bgp vpnv4 allBGP table version is 18, local router ID is 10.14.14.14Status codes: s suppressed, d damped, h history, * valid, > best, i - internalOrigin codes: i - IGP, e - EGP,? - incompleteNetwork Next Hop Metric LocPrf Weight PathRoute Distinguisher: 1:101 (default for vrf vpn1)*>i10.6.6.6/32 10.0.0.21 11 100 0 ?*> 10.7.7.7/32 10.150.0.2 11 32768 ?*>i10.69.0.0/30 10.0.0.21 0 100 0 ?*> 10.150.0.0/24 0.0.0.0 0 32768 ?Table 1 describes the significant fields shown in the display.
The following example shows how to display a table of labels for NLRI prefixes that have a route distinguisher value of 100:1.
Router# show ip bgp vpnv4 rd 100:1 labelsNetwork Next Hop In label/Out labelRoute Distinguisher: 100:1 (vrf1)10.0.0.0 10.20.0.60 34/nolabel10.0.0.0 10.20.0.60 35/nolabel10.0.0.0 10.20.0.60 26/nolabel10.20.0.60 26/nolabel10.0.0.0 10.15.0.15 nolabel/26Table 2 describes the significant fields shown in the display.
The following example shows VPNv4 routing entries for the VRF named vpn1:
Router# show ip bgp vpnv4 vrf vpn1BGP table version is 18, local router ID is 10.14.14.14Status codes: s suppressed, d damped, h history, * valid, > best, i - internalOrigin codes: i - IGP, e - EGP,? - incompleteNetwork Next Hop Metric LocPrf Weight PathRoute Distinguisher: 1:101 (default for vrf vpn1)*>i10.6.6.6/32 10.0.0.21 11 100 0 ?*> 10.7.7.7/32 10.150.0.2 11 32768 ?*>i10.69.0.0/30 10.0.0.21 0 100 0 ?*> 10.150.0.0/24 0.0.0.0 0 32768 ?*> 10.0.0.1/32 10.150.0.2 11 32768 ?*>i10.0.0.3/32 10.0.0.21 11 100 0 ?Table 3 describes the significant fields shown in the display.
The following example shows attributes for network 10.22.22.0 that include multipaths and a best path:
Router# show ip bgp vpnv4 all 10.22.22.0BGP routing table entry for 10:1:10.22.22.0/24, version 50Paths:(6 available, best #1)Multipath:iBGPAdvertised to non peer-group peers:10.1.12.122210.22.7.8 (metric 11) from 10.11.3.4 (10.0.0.8)Origin IGP, metric 0, localpref 100, valid, internal, multipath, bestExtended Community:RT:100:1Originator:10.0.0.8, Cluster list:10.1.1.442210.22.1.9 (metric 11) from 10.11.1.2 (10.0.0.9)Origin IGP, metric 0, localpref 100, valid, internal, multipathExtended Community:RT:100:1Originator:10.0.0.9, Cluster list:10.1.1.22Table 4 describes the significant fields shown in the display.
The following example shows routes that BGP could not install in the VRF table:
Router# show ip bgp vpnv4 vrf xyz rib-failureNetwork Next Hop RIB-failure RIB-NH MatchesRoute Distinguisher: 2:2 (default for vrf bar)10.1.1.2/32 10.100.100.100 Higher admin distance No10.111.111.112/32 10.9.9.9 Higher admin distance YesTable 5 describes the significant fields shown in the display.
The following example shows the information displayed on the active and standby route processors when they are configured for MPLS VPN nonstop forwarding.
Table 6 describes the significant fields shown in the display.
The following example displays output, including the explicit-null label, from the show ip bgp vpnv4 all labels command on a CSC-PE router:
Router# show ip bgp vpnv4 all labelsNetwork Next Hop In label/Out labelRoute Distinguisher: 100:1 (v1)10.0.0.0/24 10.0.0.0 19/aggregate(v1)10.0.0.1/32 10.0.0.0 20/nolabel10.1.1.1/32 10.0.0.0 21/aggregate(v1)10.10.10.10/32 10.0.0.1 25/exp-null10.168.100.100/3210.0.0.1 23/exp-null10.168.101.101/3210.0.0.1 22/exp-nullTable 7 describes the significant fields shown in the display.
The following example displays separate router IDs for each VRF in the output from an image in Cisco IOS Release 12.2(33)SRA and later releases with the Per-VRF Assignment of BGP Router ID feature configured. The router ID is shown next to the VRF name.
Router# show ip bgp vpnv4 allBGP table version is 5, local router ID is 172.17.1.99Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,r RIB-failure, S StaleOrigin codes: i - IGP, e - EGP, ? - incompleteNetwork Next Hop Metric LocPrf Weight PathRoute Distinguisher: 1:1 (default for vrf vrf_trans) VRF Router ID 10.99.1.2*> 192.168.4.0 0.0.0.0 0 32768 ?Route Distinguisher: 42:1 (default for vrf vrf_user) VRF Router ID 10.99.1.1*> 192.168.5.0 0.0.0.0 0 32768 ?Table 8 describes the significant fields shown in the display.
Related Commands
show ip bgp vpnv4 all sso summary
To display information about Border Gateway Protocol (BGP) peers that support BGP Nonstop Routing (NSR) with stateful switchover (SSO), use the show ip bgp vpn4 sso summary command in privileged EXEC mode.
show ip bgp vpnv4 all sso summary
Syntax Description
This command has no arguments or keywords.
Command Modes
Privileged EXEC
Command History
Usage Guidelines
The show ip bgp vpnv4 all sso summary command is used to display the number of BGP neighbors that are in SSO mode.
Examples
The following is sample output from the show ip bgp vpnv4 all sso summary command:
Router# show ip bgp vpnv4 all sso summaryStateful switchover support enabled for 40 neighborsTable 9 describes the significant fields shown in the display.
Table 9 show ip bgp vpnv4 all sso summary Field Descriptions
Stateful Switchover support enabled for
Indicates the number of BGP neighbors that are in SSO mode.
Related Commands
show tcp
To display the status of Transmission Control Protocol (TCP) connections when Cisco IOS or Cisco IOS Software Modularity images re running, use the show tcp command in user EXEC or privileged EXEC mode.
show tcp [line-number] [tcb address]
Syntax Description
Command Modes
User EXEC
Privileged EXECCommand History
Examples
Example output varies between Cisco IOS software images and Cisco IOS Software Modularity software images. To view the appropriate output, choose one of the following sections:
•
Cisco IOS Software Modularity
Cisco IOS Software
The following is sample output that displays the status and option flags:
Router# show tcp...Status Flags: passive open, active open, retransmission timeout, app closedOption Flags: vrf id setIP Precedence value: 6...SRTT: 273 ms, RTTO: 490 ms, RTV: 217 ms, KRTT: 0 msminRTT: 0 ms, maxRTT: 300 ms, ACK hold: 200 msStatus Flags: active open, retransmission timeoutOption Flags: vrf id setIP Precedence value: 6Table 10 contains the types of flags, all possible command output enhancements, and descriptions. See Table 11 through Table 15 for descriptions of the other fields in the sample output.
The following is sample output from the show tcp command:
Router# show tcptty0, connection 1 to host ciderConnection state is ESTAB, I/O status: 1, unread input bytes: 0Local host: 172.31.232.17, Local port: 11184Foreign host: 172.31.1.137, Foreign port: 23Enqueued packets for retransmit: 0, input: 0, saved: 0Event Timers (current time is 67341276):Timer: Retrans TimeWait AckHold SendWnd KeepAliveStarts: 30 0 32 0 0Wakeups: 1 0 14 0 0Next: 0 0 0 0 0iss: 67317172 snduna: 67317228 sndnxt: 67317228 sndwnd: 4096irs: 1064896000 rcvnxt: 1064897597 rcvwnd: 2144 delrcvwnd: 0SRTT: 317 ms, RTTO: 900 ms, RTV: 133 ms, KRTT: 0 msminRTT: 4 ms, maxRTT: 300 ms, ACK hold: 300 msFlags: higher precedence, idle user, retransmission timeoutDatagrams (max data segment is 536 bytes):Rcvd: 41 (out of order: 0), with data: 34, total data bytes: 1596Sent: 57 (retransmit: 1), with data: 35, total data bytes: 55Table 11 describes the first five lines of output shown in the above display.

Note
Use the show tcp brief command to display information about the ECN-enabled connections.
The following line of output shows the current elapsed time according to the system clock of the local host. The time shown is the number of milliseconds since the system started.
Event Timers (current time is 67341276):The following lines of output display the number of times that various local TCP timeout values were reached during this connection. In this example, the local host re-sent data 30 times because it received no response from the remote host, and it sent an acknowledgment many more times because there was no data.
Timer: Retrans TimeWait AckHold SendWnd Keepalive GiveUp PmtuAgerStarts: 30 0 32 0 0 0 0Wakeups: 1 0 14 0 0 0 0Next: 0 0 0 0 0 0 0Table 12 describes the fields in the above lines of output.
The following lines of output display the sequence numbers that TCP uses to ensure sequenced, reliable transport of data. The local host and remote host each use these sequence numbers for flow control and to acknowledge receipt of datagrams.
iss: 67317172 snduna: 67317228 sndnxt: 67317228 sndwnd: 4096irs: 1064896000 rcvnxt: 1064897597 rcvwnd: 2144 delrcvwnd: 0Table 13 describes the fields shown in the display above.
The following lines of output display values that the local host uses to keep track of transmission times so that TCP can adjust to the network that it is using.
SRTT: 317 ms, RTTO: 900 ms, RTV: 133 ms, KRTT: 0 msminRTT: 4 ms, maxRTT: 300 ms, ACK hold: 300 msFlags: higher precedence, idle user, retransmission timeoutTable 14 describes the significant fields shown in the output above.

Note
For more information on the above fields, see Round Trip Time Estimation, P. Karn & C. Partridge, ACM SIGCOMM-87, August 1987.
The following lines of output display the number of datagrams that are transported with data.
Datagrams (max data segment is 536 bytes):Rcvd: 41 (out of order: 0), with data: 34, total data bytes: 1596Sent: 57 (retransmit: 1), with data: 35, total data bytes: 55Table 15 describes the significant fields shown in the last lines of the show tcp command output.
The following is sample output from the show tcp tcb command that displays detailed information by hexadecimal address about an ECN-enabled connection:
Router# show tcp tcb 0x62CD2BB8Connection state is LISTEN, I/O status: 1, unread input bytes: 0Connection is ECN enabledLocal host: 10.10.10.1, Local port: 179Foreign host: 10.10.10.2, Foreign port: 12000Enqueued packets for retransmit: 0, input: 0 mis-ordered: 0 (0 bytes)Event Timers (current time is 0x4F31940):Timer Starts Wakeups NextRetrans 0 0 0x0TimeWait 0 0 0x0AckHold 0 0 0x0SendWnd 0 0 0x0KeepAlive 0 0 0x0GiveUp 0 0 0x0PmtuAger 0 0 0x0DeadWait 0 0 0x0iss: 0 snduna: 0 sndnxt: 0 sndwnd: 0irs: 0 rcvnxt: 0 rcvwnd: 4128 delrcvwnd: 0SRTT: 0 ms, RTTO: 2000 ms, RTV: 2000 ms, KRTT: 0 msminRTT: 60000 ms, maxRTT: 0 ms, ACK hold: 200 msFlags: passive open, higher precedence, retransmission timeoutTCB is waiting for TCP Process (67)Datagrams (max data segment is 516 bytes):Rcvd: 6 (out of order: 0), with data: 0, total data bytes: 0Sent: 0 (retransmit: 0, fastretransmit: 0), with data: 0, total databytes: 0Cisco IOS Software Modularity
The following is sample output from the show tcp tcb command from a Software Modularity image:
Router# show tcp tcb 0x1059C10Connection state is ESTAB, I/O status: 0, unread input bytes: 0Local host: 10.4.2.32, Local port: 23Foreign host: 10.4.2.39, Foreign port: 11000VRF table id is: 0Current send queue size: 0 (max 65536)Current receive queue size: 0 (max 32768) mis-ordered: 0 bytesEvent Timers (current time is 0xB9ACB9):Timer Starts Wakeups Next(msec)Retrans 6 0 0SendWnd 0 0 0TimeWait 0 0 0AckHold 8 4 0KeepAlive 11 0 7199992PmtuAger 0 0 0GiveUp 0 0 0Throttle 0 0 0irs: 1633857851 rcvnxt: 1633857890 rcvadv: 1633890620 rcvwnd: 32730iss: 4231531315 snduna: 4231531392 sndnxt: 4231531392 sndwnd: 4052sndmax: 4231531392 sndcwnd: 10220SRTT: 84 ms, RTTO: 650 ms, RTV: 69 ms, KRTT: 0 msminRTT: 0 ms, maxRTT: 200 ms, ACK hold: 200 msKeepalive time: 7200 sec, SYN wait time: 75 secGiveup time: 0 ms, Retransmission retries: 0, Retransmit forever: FALSEState flags: noneFeature flags: NagleRequest flags: noneWindow scales: rcv 0, snd 0, request rcv 0, request snd 0Timestamp option: recent 0, recent age 0, last ACK sent 0Datagrams (in bytes): MSS 1460, peer MSS 1460, min MSS 1460, max MSS 1460Rcvd: 14 (out of order: 0), with data: 10, total data bytes: 38Sent: 10 (retransmit: 0, fastretransmit: 0), with data: 5, total data bytes: 76Header prediction hit rate: 72 %Socket states: SS_ISCONNECTED, SS_PRIVRead buffer flags: SB_WAIT, SB_SEL, SB_DEL_WAKEUPRead notifications: 4Write buffer flags: SB_DEL_WAKEUPWrite notifications: 0Socket status: 0Related Commands
show tcp ha connections
To display connection-ID-to-TCP mapping data, use the show tcp ha connections command in privileged EXEC mode.
show tcp ha connections
Syntax Description
This command has no arguments or keywords.
Command Modes
Privileged EXEC
Command History
Usage Guidelines
The show tcp ha connections command is used to display connection-ID-to-TCP mapping data.
Examples
The following is sample output from the show tcp ha connections command:
Router# show tcp ha connectionsSSO enabled for 40 connectionsTCB Local Address Foreign Address (state) Conn Id71EACE60 10.0.56.1.179 10.0.56.3.58671 ESTAB 3771EA9320 10.0.53.1.179 10.0.53.3.58659 ESTAB 3471EA35F8 10.0.41.1.179 10.0.41.3.58650 ESTAB 2271A21FE0 10.0.39.1.179 10.0.39.3.58641 ESTAB 2071EAA6E0 10.0.54.1.179 10.0.54.3.58663 ESTAB 3571EA2238 10.0.40.1.179 10.0.40.3.58646 ESTAB 2171EABAA0 10.0.55.1.179 10.0.55.3.58667 ESTAB 3671EAE710 10.0.28.1.179 10.0.28.3.58676 ESTAB 971EA2728 10.0.50.1.179 10.0.50.3.58647 ESTAB 31720541D8 10.0.49.1.179 10.0.49.3.58642 ESTAB 3071EAA1F0 10.0.44.1.179 10.0.44.3.58662 ESTAB 252180B3A8 10.0.33.1.179 10.0.33.3.58657 ESTAB 1471EAB5B0 10.0.45.1.179 10.0.45.3.58666 ESTAB 2621809FE8 10.0.32.1.179 10.0.32.3.58653 ESTAB 1371EA8E30 10.0.43.1.179 10.0.43.3.58658 ESTAB 2471EAD350 10.0.27.1.179 10.0.27.3.58672 ESTAB 82180A9C8 10.0.52.1.179 10.0.52.3.58655 ESTAB 332180A4D8 10.0.42.1.179 10.0.42.3.58654 ESTAB 2371EABF90 10.0.26.1.179 10.0.26.3.58668 ESTAB 771EA3AE8 10.0.51.1.179 10.0.51.3.58651 ESTAB 32720546C8 10.0.59.1.179 10.0.59.3.58643 ESTAB 40Table 16 describes the significant fields shown in the display.
Feature Information for BGP Support for Nonstop Routing (NSR) with Stateful Switchover (SSO)
Table 17 lists the release history for this feature.
Not all commands may be available in your Cisco IOS software release. For release information about a specific command, see the command reference documentation.
Cisco IOS software images are specific to a Cisco IOS software release, a feature set, and a platform. Use Cisco Feature Navigator to find information about platform support and Cisco IOS software image support. Access Cisco Feature Navigator at http://www.cisco.com/go/fn. You must have an account on Cisco.com. If you do not have an account or have forgotten your username or password, click Cancel at the login dialog box and follow the instructions that appear.

Note
Table 17 lists only the Cisco IOS software release that introduced support for a given feature in a given Cisco IOS software release train. Unless noted otherwise, subsequent releases of that Cisco IOS software release train also support that feature.

Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
© 2006 Cisco Systems, Inc. All rights reserved.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback