|
Access
Control Enhancements
|
12.4(20)T
|
This
feature allows administrators to configure automatic authentication and
authorization for users. Users provide their username and password via the
gateway page URL and do not have to re-enter their usernames and passwords from
the login page. Authorization is enhanced to support more generic
authorization, including local authorization.
The
following commands were introduced by this feature:
aaa authentication
auto,
aaa
authorization list.
|
|
AnyConnect
Client Support
|
12.4(20)T
|
Effective
with this release, AnyConnect Client adds support for several client-side
platforms, such as Microsoft Windows, Apple-Mac, and Linux. The ability to
install AnyConnect in a standalone mode is also added. In addition, this
feature allows multiple SSL VPN client package files to be configured on a
gateway.
The
following command was modified by this feature:
webvpn install.
|
|
Application
ACL Support
|
12.4(11)T
|
This
feature provides administrators with the flexibility to fine-tune access
control at the application layer level.
The
following commands were introduced by this feature:
acl add error-msg,
error-url,
list.
|
|
Auto Applet
Download
|
12.4(9)T
|
This
feature provides administrators with the option of automatically downloading
the port-forwarding applet under the policy group.
The
following command was modified by this feature:
port-forward
(policy group).
|
|
Backend
HTTP Proxy
|
12.4(20)T
|
This
feature allows administrators to route user requests through a backend HTTP
proxy, providing more flexibility and control than routing through internal web
servers.
The
following command was added by this feature:
http
proxy-server.
|
|
Cisco
AnyConnect VPN Client
|
12.4(15)T
|
This
feature is the next-generation SSL VPN Client. The feature provides remote
users with secure VPN connections to the router platforms supported by SSL VPN
and to the Cisco 5500 Series Adaptive Security Appliances.
If you have
Cisco IOS releases before Release 12.4(15)T see
SSL VPN
Client GUI
and if you have Cisco IOS Release 12.4(15)T and later
releases, see
Cisco
AnyConnect VPN Client GUI.
The task
configurations in this document for tunnel mode apply to SVC and AnyConnect VPN
Client.
For more
information about the Cisco AnyConnect VPN Client feature, see the
Cisco AnyConnect VPN Client
Administrator Guide,
Release 2.4
and the
Release Notes for Cisco
AnyConnect VPN Client,
Release 2.4.
| Note
|
Many of
the features listed in the documents
Cisco
AnyConnect VPN Client Administrator Guide and
Release
Notes for Cisco AnyConnect VPN Client, Version 2.0
apply only to the Cisco ASA 5500 Series Adaptive
Security Appliances. For a list of features that do not currently apply to
other Cisco platforms, see the restriction in the
Cisco_AnyConnect_VPN_Client_
of this document.
|
|
|
Debug
Infrastructure
|
12.4(11)T
|
Updates to
the
webvpn debug
command provide administrators with the ability to turn debugging on for any
one user or group.
The
following keywords were introduced by this feature:
acl, entry sso,
verbose.
The
following keyword options were added for the
http keyword:
authentication ,
trace , and
verbose .
The
verbose
keyword option was added for the
citrix ,
cookie ,
tunnel , and
webservice
keywords.
The
port-forward
keyword was deleted and the
detail
keyword option for the
tunnel
keyword was deleted.
|
|
DTLS Support for IOS SSL VPN
|
15.1(2)T
|
The DTLS Support for IOS SSL VPN feature enables DTLS as a
transport protocol for the traffic tunneled through SSL VPN.
The following commands were introduced or modified:
debug webvpn dtls,
dtls port,
svc dtls .
|
|
Full-Tunnel CEF Support
|
12.4(20)T
|
This
feature provides better performance for full-tunnel packets.
|
|
GUI
Enhancements
|
12.4(15)T
|
These
enhancements provide updated examples and explanation of the Web VPN GUIs.
|
|
Internationalization
|
12.4(22)T
|
The
Internationalization feature provides multi-language support for SSL VPN
clients, such as Cisco Secure Desktop (CSD) and SSL VPN Client (SVC).
The
following commands were introduced:
browser-attribute import,
import language, webvpn create template.
|
|
Licensing
Support for Cisco IOS SSL VPNs
|
15.0(1)M
|
A license
count is associated with each counted license and the count indicates the
instances of the feature available for use in the system.
In Cisco
IOS Release 15.0(1)M, support was added for Cisco 880, Cisco 890, Cisco 1900,
Cisco 2900, and Cisco 3900 series routers.
The
following commands were introduced or modified:
debug webvpn license, show
webvpn license.
|
|
Max-user
Limit Message
|
12.4(22)T
|
This
error message is received when you try to log in to a Web VPN context and a
maximum limit has been reached.
|
|
Netegrity
Cookie-Based Single SignOn (SSO) Support
|
12.4(11)T
|
This
feature allows administrators to configure an SSO server that sets a SiteMinder
cookie in the browser of a user when the user initially logs in. The benefit of
this feature is that users are prompted to log in only a single time.
The
following commands were modified for this feature:
clear
webvpn
stats ,
debug
webvpn ,
show
webvpn
context ,
show
webvpn
policy , and
show
webvpn
stats .
The
following commands were added for this feature:
max-retry-attempts ,
request-timeout ,
secret-key ,
sso-server ,
and
web-agent-url .
|
|
NTLM
Authentication
|
12.4(9)T
|
This
feature provides NT LAN Manager (NTLM) authentication support.
The
following command was modified by this feature:
functions
|
|
Port-Forward Enhancements
|
12.4(11)T
|
This
feature provides administrators with more options for configuring HTTP proxy
and portal pages.
The
following commands were added for this feature:
acl ,
add ,
deny ,
error-msg ,
error-url ,
list , and
permit .
|
|
RADIUS
Accounting
|
12.4(9)T
|
This
feature provides for RADIUS accounting for SSL VPN sessions.
The
following command was added by this feature:
webvpn
aaa
accounting-list .
|
|
SSL VPN
|
12.4(6)T
|
This
feature enhances SSL VPN support in the Cisco IOS software. This feature
provides a comprehensive solution that allows easy access to a broad range of
web resources and web-enabled applications using native HTTP over SSL (HTTPS)
browser support. SSL VPN introduced three modes of SSL VPN access: clientless,
thin-client, and full-tunnel client support.
The
following command was introduced in Cisco IOS Release 12.4(15)T:
cifs-url-list
|
|
SSL VPN
Client-Side Certificate-Based Authentication
|
15.0(1)M
|
This
feature enables SSL VPN to authenticate clients based on the client’s AAA
username and password, and supports webvpn gateway authentication of clients
using AAA certificates.
The
following command was modified by this feature:
authentication
certificate ,
ca
trustpoint ,
match-certificate ,
svc
profile ,
username-prefill ,
webvpn
import
svc
profile .
|
|
SSL VPN
DVTI Support
|
15.1(1)T
|
The SSL
VPN DVTI Support feature adds DVTI support to the SSL VPN and hence enables
seamless interoperability with IP features, such as firewalls, NAT, ACL, and
VRF. This feature also provides DVTI support, which allows the configuration of
IP features on a per-tunnel basis.
The
following command was introduced or modified:
virtual-template .
|
|
SSL VPN MIB
|
15.5(2)T
|
The SSL VPN
MIB represents the Cisco implementation-specific attributes of a Cisco entity
that implements SSL VPN. The MIB provides operational information in Cisco’s
SSL VPN implementation by managing the SSLVPN, trap control, and notification
groups. For example, the SSL VPN MIB provides the number of active SSL tunnels
on the device.
In Cisco IOS Release 15.5(2)T, this feature was introduced on
Cisco 800 Integrated Services Routers, Cisco 3900 Integrated Services Routers,
and 3900E Series Integrated Services Routers.
|
|
SSL VPN Phase-4 Features
|
15.1(1)T
|
The SSL VPN Phase-4 Features feature provides the following
enhancements to the Cisco IOS SSL VPN:
-
ACL support for split tunneling
-
IP mask for IP pool address assignment
-
Undoing the renaming of AnyConnect or SVC Full Tunnel
Cisco package during installation on a Cisco IOS router
-
Adding per-user SSL VPN session statistics
-
Start Before Logon option for the Cisco IOS SSL VPN
headend
The following commands were introduced or modified:
show
webvpn
session ,
svc
address-pool ,
svc
module ,
svc
split .
|
|
Stateless
High Availability with Hot Standby Router Protocol (HSRP)
|
12.4(20)T
|
This
feature allows stateless failover to be applied to VPN routers by using HSRP.
The
following command was modified by this feature:
ip
address .
|
|
URL
Obfuscation
|
12.4(11)T
|
This
feature provides administrators with the ability to obfuscate, or mask,
sensitive portions of an enterprise URL, such as IP addresses, hostnames, or
port numbers.
The
following command was added by this feature:
mask-urls .
|
|
URL
Rewrite Splitter
|
12.4(20)T
|
This
feature allows administrators to selectively mangle requests to the gateway.
The
following commands were added by this feature:
host ,
ip ,
unmatched-action , and
url
rewrite .
|
|
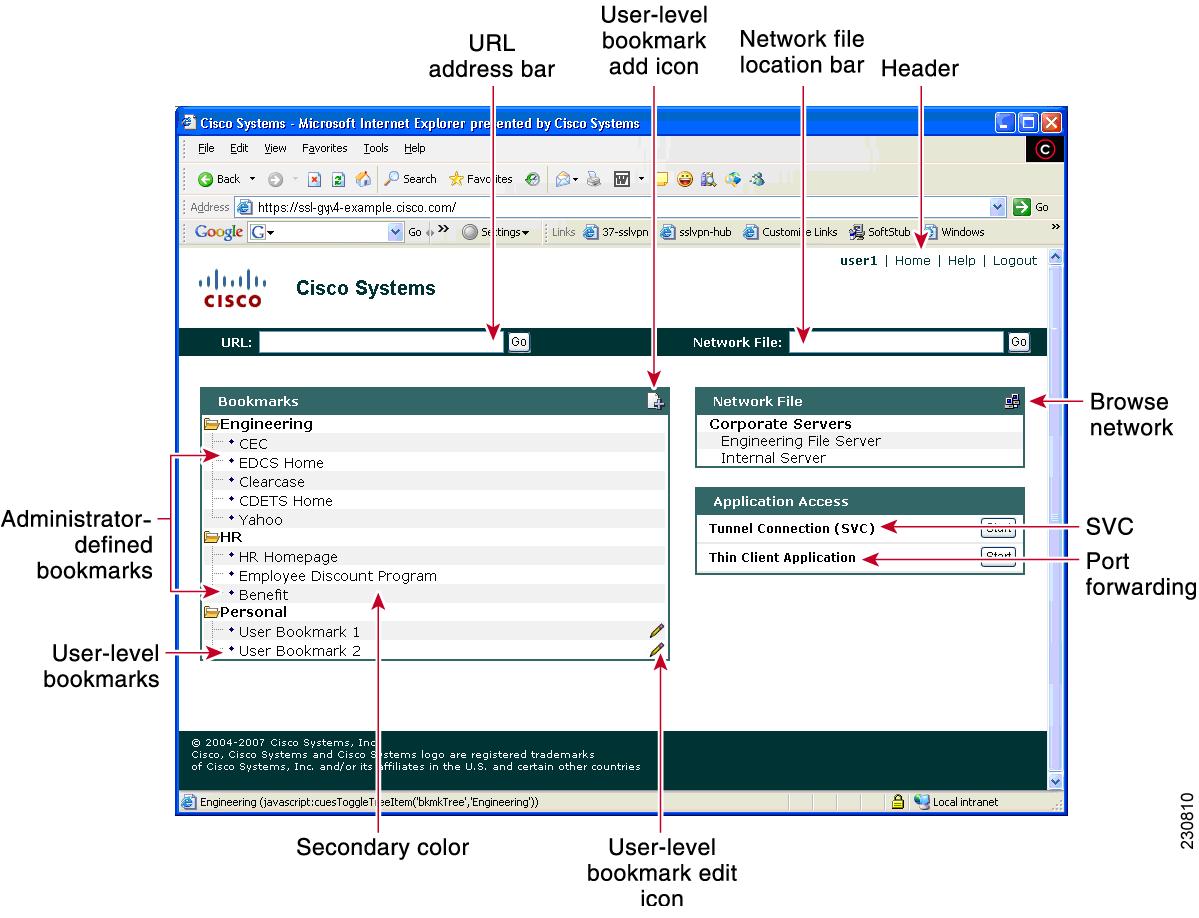
User-Level Bookmarking
|
12.4(15)T
|
This
feature allows a user to bookmark URLs while connected through an SSL VPN
tunnel.
The
following command was added by this feature:
user-profile
location .
|
|
Virtual
Templates
|
12.4(24)T1
|
A virtual
template enables SSL VPN to interoperate with IP features such as NAT,
firewall, and policy-based routing.
The
following command was introduced:
virtual-template .
|




 Feedback
Feedback