Add Additional Ethernet Interfaces on the PGW Platform
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes procedures for how to add a second Ethernet interface (hme1) on the Cisco PGW platform.
Prerequisites
Requirements
Before you attempt this configuration, ensure that you meet these requirements:
-
Mitigate all IP issues.
-
Back up current configurations and the Cisco PGW database.
-
Schedule this process during a maintenance window (ensure sufficient time is available for configuration changes and system testing).
-
Any second IP interfaces required should be configured and validated on the gateway and Cisco Signaling Link Terminal (SLT) before you proceed to the Step-by-Step Instructions section of this document.
-
Mitigate all alarms.
Components Used
The information in this document is based on these software and hardware versions:
-
Cisco PGW version 9.3(2)
-
Netra T 1400/1405, Sunfire V120/Netra 120
-
Standard solution components
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
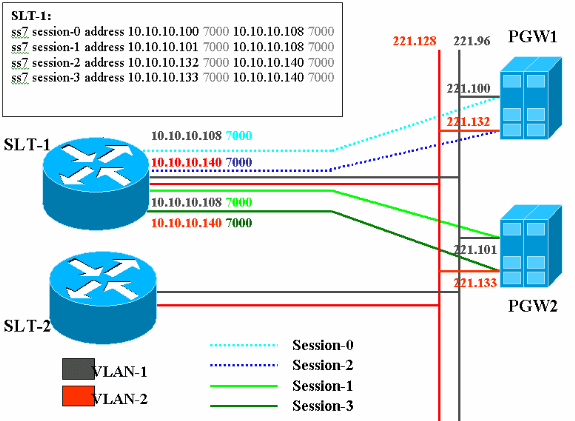
Network Diagram
This document uses the network setup shown in this diagram:
Conventions
For more information on document conventions, refer to the Cisco Technical Tips Conventions.
Background Theory
In this service configuration, four backhaul sessions are created, two on each Ethernet network. Only one of these sessions is active at a time and is determined by the Cisco PGW identification message, either SM_active or SM_standby. The sessions between the active Cisco PGW and the Cisco SLT are Session 0 and Session 2. If Session 0 and Session 2 are in-service, then one is active and the other standby. If Session 0 goes out-of-service, the Cisco PGW makes Session 2 active. Thereby, Session 2 provides redundancy for a backhaul communication path between the Cisco PGW and the Cisco SLT. The standby Cisco PGW has Session 1 and Session 3 established with the Cisco SLT, and both of these sessions are in the standby state.
When failover occurs between the active and the standby Cisco PGW, one of the sessions on the standby Cisco PGW becomes active. Upon recovery of the active Cisco PGW, Sessions 0 and 2 are in the standby state.
Add Additional Ethernet Interfaces on the PGW Platform
Step-by-Step Instructions
In this section, you are presented with the information to configure the features described in this document.
-
On the standby Cisco PGW (PGW2), add a second interface at the UNIX level.
The primary Ethernet interface is configured during the operating system installation. All additional Ethernet interfaces must be configured separately.
For more information, refer to the "Configuring Additional Ethernet Interfaces" section of Sun Solaris 8 Operating System Installation.
Note: For Ethernet interface information for each platform type, refer to "Table 2-2: Device Names on Supported Platforms" in Sun Solaris 8 Operating System Installation.
In order to configure additional Ethernet interfaces, perform these steps:
-
Add the IP address and hostname of the additional Ethernet interfaces to the /etc/hosts file with this command for each Ethernet port:
echo IP address <tab> Hostname-? >> /etc/hosts
Note: In sub-step A, the <tab> portion of the command you are instructed to enter is a reference to actually pressing the Tab key.
Note: The Hostname-? for hme1 is different than hme0, for example:
If the existing Cisco PGW hostname is U60-1, which normally correlates to hme0, then the entry made for hme1 would resemble this:
echo 10.10.10.132<tab>U60-2>>/etc/hosts
-
Create a new file named /etc/hostname.devicex, where device represents the Ethernet device type and x represents the interface instance. On the first and only line of the file, place the IP address or hostname for the additional Ethernet interfaces with this command for each Ethernet port:
echo 10.10.10.132 > /etc/hostname.hme1
Note: This example applies to a second Ethernet interface of hme1 and an IP address of 10.10.10.132.
-
Add a line to the /etc/netmasks file for each unique subnet of the interfaces that is added. Multiple subnets of the same network address must have individual lines in the /etc/netmasks file.
echo subnet address subnet mask >> /etc/netmasks
-
The machine has to be rebooted with a -r option to complete the configuration. Issue the reboot -- -r command.
-
When the machine finishes rebooting, log in as root and issue the ifconfig -a command. Verify that the new Ethernet interfaces appear in the output.
A screen similar to this is displayed:
lo0: flags=849<UP,LOOPBACK,RUNNING,MULTICAST> mtu 8232 inet 127.0.0.1 netmask ff000000 hme0: flags=863<UP,BROADCAST,NOTRAILERS,RUNNING,MULTICAST> mtu 1500 inet 172.24.235.53 netmask ffffff00 broadcast 172.24.235.255 ether 8:0:20:9a:76:6c hme1: flags=863<UP,BROADCAST,NOTRAILERS,RUNNING,MULTICAST> mtu 1500 inet 172.24.237.53 netmask ffffff00 broadcast 172.24.237.255 ether 8:0:20:9a:76:6c
Note: IP addresses are for demonstration purposes only. Actual addresses differ in each application.
-
-
Verify the second interface on the PGW2.
-
Verify that the PGW2 is in standby state with these commands:
-
rtrv-ne-health
-
rtrv-alms
-
rtrv-softw:all
-
-
Mitigate any issues before you proceed.
-
Ping from the first interface to the second interface on the PGW2.
-
Ping from the PGW1 to the new Ethernet interface hme1 on the PGW2.
-
Ensure that other equipment (such as the gateway and the Cisco SLT) can ping the second interface on the PGW2.
-
Ensure that hme interfaces are in full duplex mode with the ndd –get command.
For example:
/usr/sbin/ndd -get /dev/hme link_mode
-
0 - half duplex—This output means the interface is in half duplex mode.
-
1 - full duplex—This output means the interface in full duplex mode.
-
-
-
On the active Cisco PGW (PGW1), issue the sw-over::confirm command.
Ensure that the previous standby PGW2 is in the active state and the previous PGW1 is in the standby state. Alarms and issues need to be mitigated on both Cisco PGWs before you proceed.
-
On the PGW1 (standby), shut down the Cisco PGW application software with the /etc/init.d/CiscoMGC stop command. Add the second interface at the UNIX level.
For more information, refer to the "Configuring Additional Ethernet Interfaces" section of Sun Solaris 8 Operating System Installation.
Note: For Ethernet interface information for each platform type, refer to "Table 2-2: Device Names on Supported Platforms" in theSun Solaris 8 Operating System Installation.
In order to configure additional Ethernet interfaces, perform these steps:
-
Add the IP address and hostname of the additional Ethernet interfaces to the /etc/hosts file with this command for each Ethernet port:
echo IP address <tab> Hostname-? >> /etc/hosts
Note: The Hostname-? for hme1 is different than that for hme0, for example:
If the existing Cisco PGW hostname is U61-1, which normally correlates to hme0, then the entry made for hme1 would be similar to this:
echo 10.10.10.133<tab>U61-2>>/etc/hosts
-
Create a new file named /etc/hostname.devicex, where device represents the Ethernet device type and x represents the interface instance. On the first and only line of the file, place the IP address or hostname for the additional Ethernet interfaces with this command for each Ethernet port:
echo 10.10.10.133> /etc/hostname.hme1
Note: This example applies to a second Ethernet interface of hme1 and an IP address of 10.10.10.133.
-
Add a line to the /etc/netmasks file for each unique subnet of the interfaces added. Multiple subnets of the same network address must have individual lines in the /etc/netmasks file (if required).
echo subnet address subnet mask >> /etc/netmasks
-
The machine must be rebooted with a -r option to complete the configuration. Issue the reboot -- -r command.
-
When the machine has rebooted, log in as root and issue the ifconfig -a command. Verify that the new Ethernet interfaces appear in the output.
A screen similar to this is displayed:
lo0: flags=849<UP,LOOPBACK,RUNNING,MULTICAST> mtu 8232 inet 127.0.0.1 netmask ff000000 hme0: flags=863<UP,BROADCAST,NOTRAILERS,RUNNING,MULTICAST> mtu 1500 inet 172.24.235.53 netmask ffffff00 broadcast 172.24.235.255 ether 8:0:20:9a:76:6c hme1: flags=863<UP,BROADCAST,NOTRAILERS,RUNNING,MULTICAST> mtu 1500 inet 172.24.237.53 netmask ffffff00 broadcast 172.24.237.255 ether 8:0:20:9a:76:6c
-
-
Verify the second interface on the PGW1 by following these steps:
-
Ping from the first interface to the second interface on the PGW1.
-
Ping from the PGW2 to the new Ethernet interface hme1 on the PGW1.
-
Ensure that other equipment (such as the gateway and the Cisco SLT) can ping to the second interface.
-
Ensure that hme interfaces are in full duplex mode with the ndd –get command.
-
Mitigate any issues before you proceed.
-
-
Populate XECfgParm.dat on the PGW1 (standby).
-
Populate the second IP address fields in XECfgParm.dat:
*.ipAddrLocalA = 10.10.10.100 # MIGRATED *.ipAddrLocalB = 10.10.10.132 # MIGRATED !--- Populate the field above. *.ipAddrPeerA = 10.10.10.101 # MIGRATED *.ipAddrPeerB = 10.10.10.133 # MIGRATED !--- Populate the field above. *.IP_Addr1 = 10.10.10.100 # MIGRATED *.IP_Addr2 = 10.10.10.132 # MIGRATED !--- Populate the field above. *.IP_Addr3 = 0.0.0.0 # MIGRATED *.IP_Addr4 = 0.0.0.0 # MIGRATED foverd.ipLocalPortA = 1051 # MIGRATED foverd.ipPeerPortA = 1052 # MIGRATED foverd.ipLocalPortB = 1053 # MIGRATED foverd.ipPeerPortB = 1054 # MIGRATED
-
Restart the Cisco PGW application on the PGW1 with the /etc/init.d/CiscoMGC start command.
-
Verify that the PGW1 is in the standby state with these commands:
-
Rtrv-ne-health
-
Rtrv-alms
-
Rtrv-softw:all
-
-
Mitigate any issues before you proceed.
-
-
Make the Cisco PGW1 active with the Sw-over::confirm command.
-
Ensure the PGW1 is active and the PGW2 is in the standby state with these commands:
-
Rtrv-ne-health
-
Rtrv-alms
-
Rtrv-softw:all
-
-
Mitigate any issues before you proceed.
-
-
On the PGW2 (standby), shut down the Cisco PGW application software with the /etc/init.d/CiscoMGC stop command.
-
Populate XECfgParm.dat on the PGW2 (standby).
-
Populate the second IP address fields in XECfgParm.dat:
*.ipAddrLocalA = 10.10.10.101 # MIGRATED *.ipAddrLocalB = 10.10.10.133 # MIGRATED !--- Populate the field above. *.ipAddrPeerA = 10.10.10.100 # MIGRATED *.ipAddrPeerB = 10.10.10.132 # MIGRATED !--- Populate the field above. *.IP_Addr1 = 10.10.10.101 # MIGRATED *.IP_Addr2 = 10.10.10.133 # MIGRATED !--- Populate the field above. *.IP_Addr3 = 0.0.0.0 # MIGRATED *.IP_Addr4 = 0.0.0.0 # MIGRATED foverd.ipLocalPortA = 1051 # MIGRATED foverd.ipPeerPortA = 1052 # MIGRATED foverd.ipLocalPortB = 1053 # MIGRATED foverd.ipPeerPortB = 1054 # MIGRATED
-
Restart the Cisco PGW application on the PGW2 with the /etc/init.d/CiscoMGC start command.
-
-
Ensure the PGW1 is active and the PGW2 is in the standby state. (At this point the IP interfaces have been added and XECfgParm.dat has been populated.)
-
Issue these commands:
-
Rtrv-ne-health
-
Rtrv-alms
-
Rtrv-softw:all
-
-
Mitigate any issues before you proceed.
-
-
Add additional session sets on Cisco SLT.
An example is shown here:
ss7 session 2 address 10.10.10.132 7000 10.10.10.140 7000 session-set 0 ss7 session 3 address 10.10.10.133 7000 10.10.10.140 7000 session-set 0
-
Make Redundant Link Manager (RLM) changes in the gateways.
An example on one gateway is shown here (configuration additions in bold):
rlm group 0 server netra1 link address 10.10.10.100 source Loopback0 weight 1 link address 10.10.10.132 source Loopback0 weight 1 server netra2 link address 10.10.10.101 source Loopback0 weight 1 link address 10.10.10.133 source Loopback0 weight 1 ! rlm group 1 protocol rlm port 3002 server netra1 link address 10.10.10.100 source Loopback0 weight 1 link address 10.10.10.132 source Loopback0 weight 1 server netra2 link address 10.10.10.101 source Loopback0 weight 1 link address 10.10.10.133 source Loopback0 weight 1
-
Make configuration changes on the PGW1 (active).
Follow these steps:
-
Verify that you are on the active Cisco PGW.
-
Make sure the standby box is in the standby state.
-
Mitigate all alarms.
-
Start a provisioning session with the mml>prov-sta::srcver=”active”,dstver=”config_123” command.
-
Add an Ethernet interface card.
For more information, refer to the "Adding an Ethernet Interface" section of Adding Components with MML.
An example is shown here:
prov-add:ENETIF:NAME="eth-itf1",DESC="interface for the 2nd ethernet card in sc2200",CARD="eth-card-1"
-
Add IP_ADDR 2 information in session sets.
For more information, refer to the "Adding a Session Set" section of Adding Components with MML.
Note: Review the notes for how to add a session set for IP_ADDR 2. The Man-Machine Language (MML) commands in the link are for one IP address only.
An example is shown here:
prov-ed:SESSIONSET:Name="c7sset3",IPADDR2="IP_Addr2",PEERADDR2="10.10.10.140", NEXTHOP2="0.0.0.0",NETMASK2="255.255.255.255" prov-ed:SESSIONSET:Name="c7sset4",IPADDR2="IP_Addr2",PEERADDR2="10.10.10.141", NEXTHOP2="0.0.0.0",NETMASK2="255.255.255.255"
-
Add the second IP link with IP Addr 2 for all applicable gateways.
An example is shown here:
prov-add:IPLNK:NAME="iplk-csc504-origB",DESC="orig Link B between csc504 and sc2200",SVC="csc504-rlm-orig",IF="eth-itf1",IPADDR="IP_Addr2",PORT=3001, PEERADDR="10.10.11.4",PEERPORT=3001,PRI=2,NEXTHOP="0.0.0.0",NETMASK="255.255.255.255" prov-add:IPLNK:NAME="iplk-csc504-termB",DESC="term Link B between csc504 and sc2200",SVC="csc504-rlm-term",IF="eth-itf1",IPADDR="IP_Addr2",PORT=3003,PEERADDR="10.10.11.4", PEERPORT=3003,PRI=2,NEXTHOP="0.0.0.0",NETMASK="255.255.255.255"
-
-
-
Deploy a provisioning session with the prov-dply command.
-
Verify through MML that the session sets and IPLNKs added with IP_Addr 2 are in the IS state and have taken effect.
Set C7IPLNK to IS, and verify the final configuration with these MML commands:
-
Rtrv-ne-health
-
Rtrv-softw:all
-
Rtrv-alms
-
Rtrv-c7lnk:all
-
Rtrv-iplnk:all
-
Rtrv-dest:all
-
Rtrv-tc:all
-
Verify
There is currently no verification procedure available for this configuration.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
For troubleshooting information, refer to the Solution Troubleshooting Guide.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
04-Dec-2006 |
Initial Release |
 Feedback
Feedback