Jabber for Windows Crash Dump Analysis with the WinDbg Tool
Available Languages
Contents
Introduction
This document describes the procedure used in order to analyze the .dmp file that is created when the Cisco Jabber for Windows client crashes.
Prerequisites
Requirements
Cisco recommends that you have knowledge of Cisco Jabber for Windows.
Components Used
The information in this document is based on Cisco Jabber for Windows Version 9.x and Cisco Unified Personal Communicator (CUPC) Version 8.6.x.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Perform Crash Dump Analysis for Cisco Jabber for Windows
Use the WinDbg tool in order to perform crash dump analysis. Download the tool from the WinDbg website.
WinDbg Symbols Configuration
- In order to change the symbol path, navigate to File > Symbol File Path > Symbol Path.
- Paste this text into the window:
SRV*c:\websymbols*http://msdl.microsoft.com/download/symbols
- Click OK.
Crash Dump Analysis in WinDbg
- Start WinDbg.
- From the File menu, click Open Crash Dump.
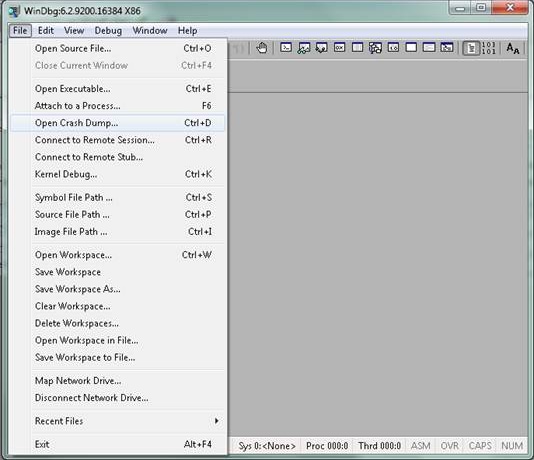
- Choose the .dmp (memory.dmp, user.dmp etc.) file, and click Open or drag and drop the .dmp file into WinDbg. This example uses the fulldump file.
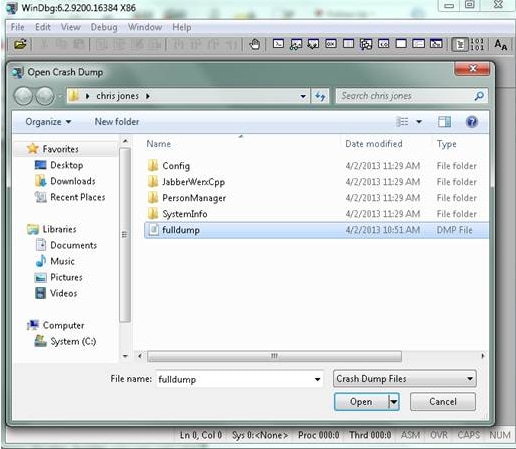
- In the command window at the bottom, enter !analyze - v, and press Enter.
- You can see the progress of the analysis on the bottom-left of the screen. In this image, the status is "BUSY."

This command performs an analysis with a fully verbose display of data and is useful in order to obtain more information. - In order to quit, enter q in the command window, and press Enter.
Here is an example of dump analyzer output:
> !analyze -v
<snip>
STACK_TEXT:
WARNING: Frame IP not in any known module. Following frames may be wrong.
02f4e80c 01457967 7ffdac00 00000104 02f4e86c 0x0
02f4e848 0145637d 00000001 02f4e86c 02f4ed58 wxvault+0x7967
02f4ea88 7c8138b7 7ffdac00 00000000 02f4eac8 wxvault+0x637d
02f4ed1c 009a436f 00b413b4 02f4ed58 00000000
kernel32!FindFirstFileA+0x3a
02f4edb8 00000000 00000000 00000000 00000000 CUPCK9+0x5a436f
STACK_COMMAND: ~8s; .ecxr ; kb
SYMBOL_STACK_INDEX: 1
SYMBOL_NAME: wxvault+7967
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: wxvault
IMAGE_NAME: wxvault.dll
DEBUG_FLR_IMAGE_TIMESTAMP: 450162c1
FAILURE_BUCKET_ID:
NULL_INSTRUCTION_PTR_c0000005_wxvault.dll!Unknown
BUCKET_ID:
APPLICATION_FAULT_NULL_INSTRUCTION_PTR_NULL_POINTER_READ_DETOURED_NULL_IP_
wxvault+7967
Examine the MODULE_NAME and the IMAGE_NAME. The information these provide, like wxvault.dll or CiscoJabber.exe, indicate what application caused the crash. In this case, the crash occurred because of issues with the Cisco Jabber.exe application and not with the user?s machine. A Google search shows that wxvault.dll is related to the DELL Embassy Trust Suite.
Send the Cisco Jabber Problem Report to the Cisco Technical Assistance Center in order to determine if the crash dump is related to a known defect that has a possible workaround.
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
14-Aug-2013 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)





 Feedback
Feedback