TLS Handshake Failure on the VCS Web Interface
Available Languages
Introduction
The Cisco Video Communication Server (VCS) uses client certificates for the authentication and authorization process. This feature is extremely useful for some environments, because it allows an added layer of security and can be used for single sign on purposes. However, if incorrectly configured, it can lock administrators out of the VCS web interface.
The steps in this document are used to disable Client certificate-based security on the Cisco VCS.
Problem
If Client certificate-based security is enabled on a VCS, and is incorrectly configured, users might not be able to access the VCS web interface. Attempts to access the web interface are met with a Transport Layer Security (TLS) handshake failure.
This is the configuration change that triggers the issue:
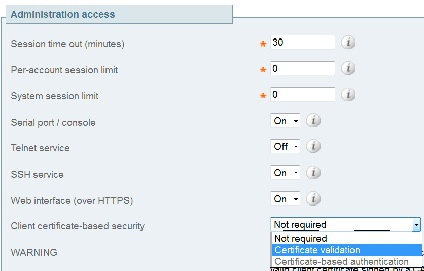
Solution
Complete these steps in order to disable Client certificate-based security and return the system to a state where administrators are able to access the web interface of the VCS:
- Connect to the VCS as root via Secure Shell (SSH).
- Enter this command as root in order to hard-code Apache to never use Client certificate-based security:
echo "SSLVerifyClient none" > /tandberg/persistent/etc/opt/apache2/ssl.d/removecba.conf
- You must restart the VCS in order for this configuration change to take effect. When you are ready to restart the VCS, enter these commands:
tshell
xcommand restart - Once the VCS reloads, Client certificate-based security is disabled. However, it is not disabled in a desirable way. Log in to the VCS with a read-write admin account. Navigate to System > System page on the VCS.
On the system administration page of the VCS, ensure that Client certificate-based security is set to "Not required":
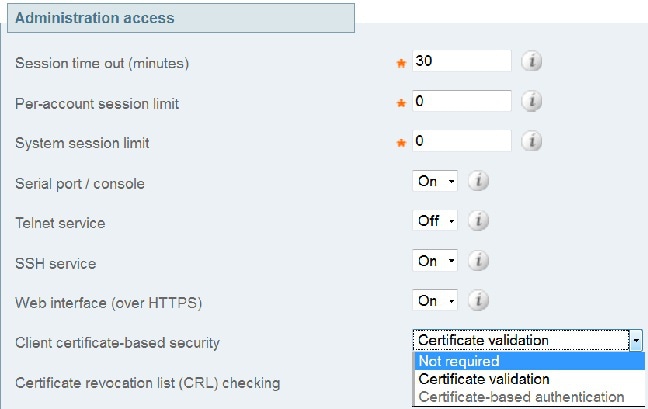
Once this change is made, save the changes. - Once complete, enter this command as root in SSH in order to reset Apache back to normal:
rm /tandberg/persistent/etc/opt/apache2/ssl.d/removecba.conf
- Restart the VCS one more time in order to verify that the procedure worked. Now that you have web access, you can restart the VCS from the web interface under Maintenance > Restart.
Congratulations! Your VCS now runs with Client cerificate-based security disabled.
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
09-Aug-2013 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)


 Feedback
Feedback