Configure the Cisco VPN 3000 Series Concentrators to Support the NT Password Expiration Feature with the RADIUS Server
Available Languages
Contents
Introduction
This document includes step-by-step instructions on how to configure the Cisco VPN 3000 Series Concentrators to support the NT Password Expiration feature using the RADIUS server.
Refer to VPN 3000 RADIUS with Expiry Feature Using Microsoft Internet Authentication Server in order to learn more about the same scenerio with the Internet Authentication Server (IAS).
Prerequisites
Requirements
-
If your RADIUS server and NT Domain Authentication server are on two separate machines, make sure that you have established IP connectivity between the two machines.
-
Make sure that you have established IP connectivity from the concentrator to the RADIUS server. If the RADIUS server is towards the public interface, don't forget to open up the RADIUS port on the Public Filter.
-
Ensure that you can connect to the concentrator from the VPN client using the Internal User Database. If this is not configured, please refer to Configuring IPSec - Cisco 3000 VPN Client to VPN 3000 Concentrator.
Note: The Password expiration feature cannot be used with Web VPN or SSL VPN clients.
Components Used
This configuration was developed and tested using the software and hardware versions below.
-
VPN 3000 Concentrator Software Version 4.7
-
VPN Client Release 3.5
-
Cisco Secure for NT (CSNT) version 3.0 Microsoft Windows 2000 Active Directory Server for User Authentication
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Network Diagram
This document uses this network setup:
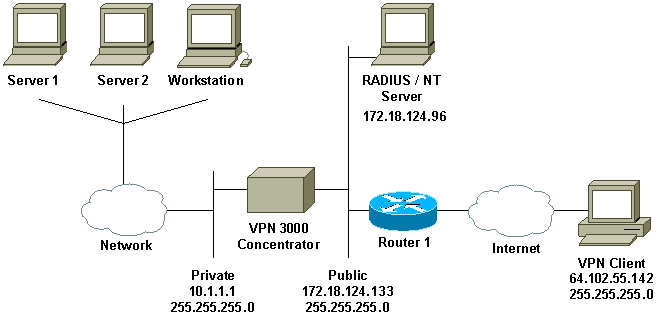
Diagram Notes
-
The RADIUS server in this configuration is on the public interface. If this is the case with your specific setup, please create two rules in your public filter to allow RADIUS traffic to enter and leave the concentrator.
-
This configuration shows CSNT software and NT Domain Authentication Services running on the same machine. These elements can be run on two separate machines if required by your configuration.
Configuring the VPN 3000 Concentrator
Group Configuration
-
To configure the group to accept the NT Password Expiration Parameters from the RADIUS Server, go to Configuration > User Management > Groups, select your group from the list, and click Modify Group. The example below shows how to modify a group named "ipsecgroup."
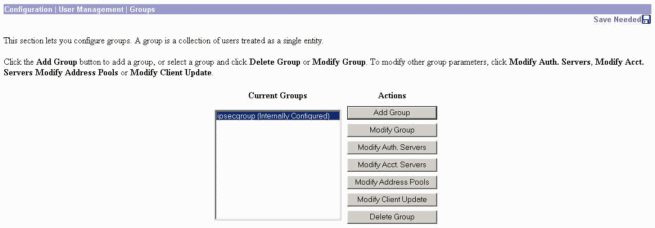
-
Go to the IPSec tab, make sure that RADIUS with Expiry is selected for the Authentication attribute.
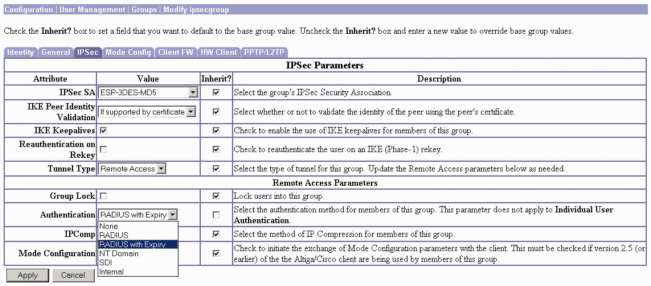
-
If you want this feature to be enabled on the VPN 3002 Hardware Clients, go to the HW Client tab, make sure that Require Interactive Hardware Client Authentication is enabled, then click Apply.
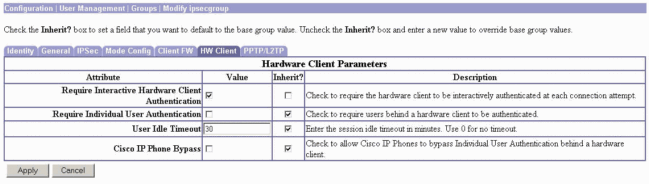
RADIUS Configuration
-
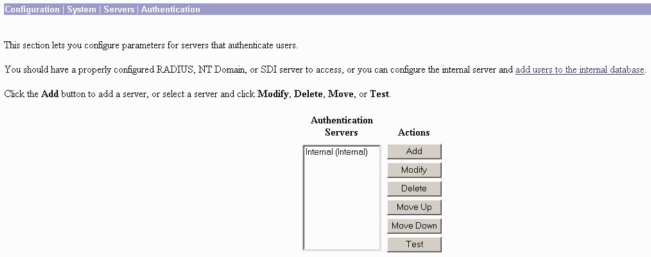
To configure the RADIUS server settings on the concentrator, go to Configuration > System > Servers > Authentication > Add.
-
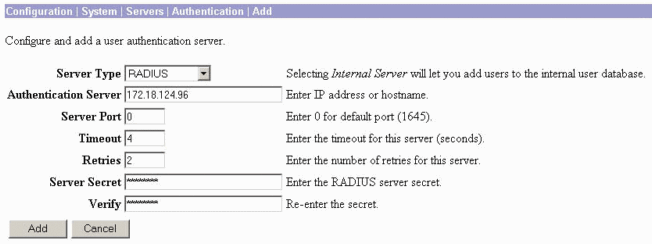
On the Add screen, type in the values that correspond to the RADIUS server and click Add.
The example below uses the following values.
Server Type: RADIUS
Authentication Server: 172.18.124.96
Server Port = 0 (for default of 1645)
Timeout = 4
Reties = 2
Server Secret = cisco123
Verify: cisco123
Configuring the Cisco Secure NT RADIUS Server
Configuring an Entry for the VPN 3000 Concentrator
-
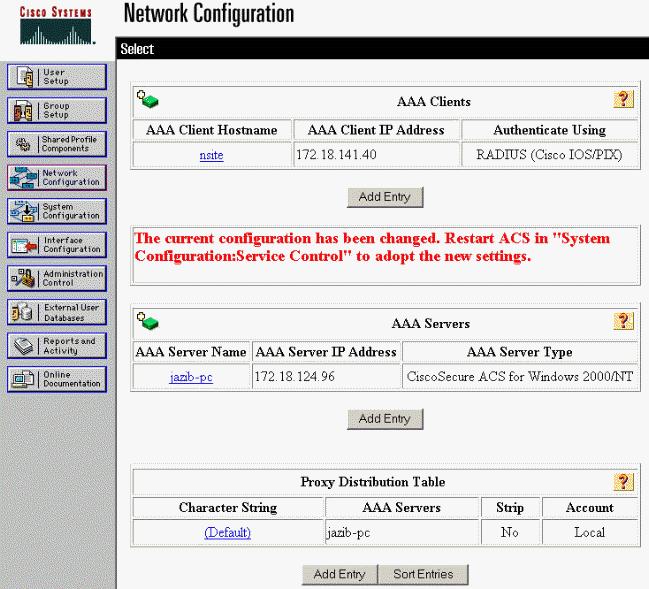
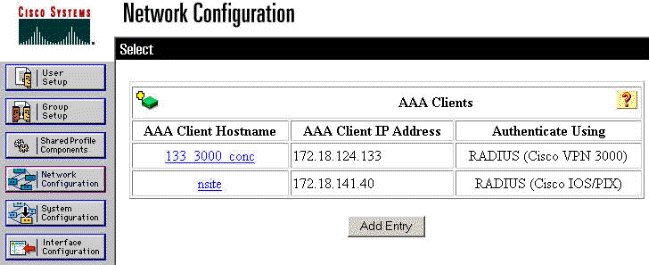
Log into CSNT and click Network Configuration in the left panel. Under "AAA Clients," click Add Entry.
-
On the "Add AAA Client" screen, type in the appropriate values to add the concentrator as the RADIUS Client, then click Submit + Restart.
The example below uses the following values.
AAA Client Hostname = 133_3000_conc
AAA Client IP Address = 172.18.124.133
Key = cisco123
Authenticate using = RADIUS (Cisco VPN 3000)
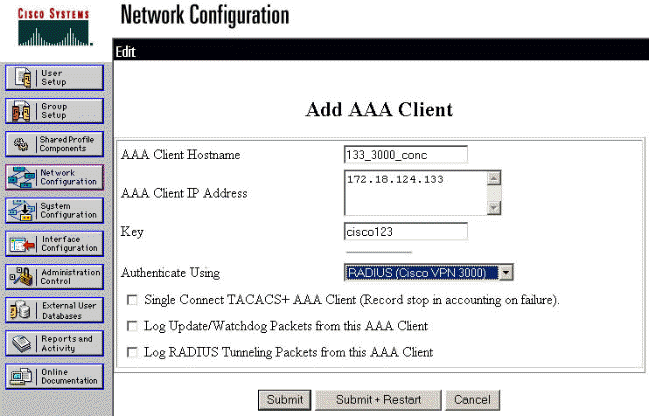
An entry for your 3000 concentrator will appear under the "AAA Clients" section.
Configuring the Unknown User Policy for NT Domain Authentication
-
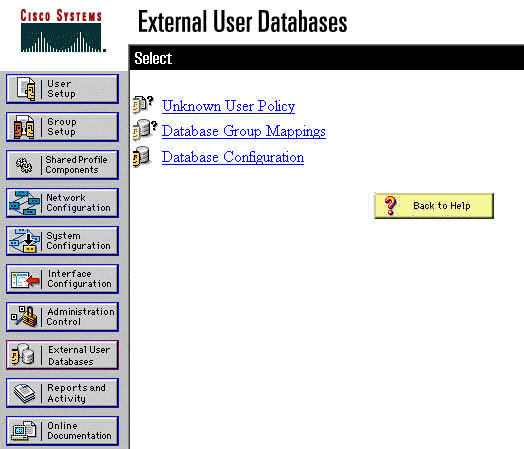
To configure User Authentication on the RADIUS server as a part of the Unknown User Policy, click External User Database in the left panel, then click the link for Database Configuration.
-
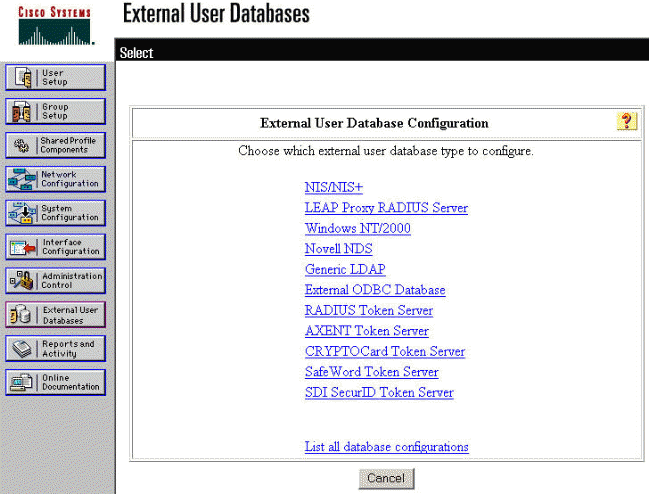
Under "External User Database Configuration," click Windows NT/2000.
-
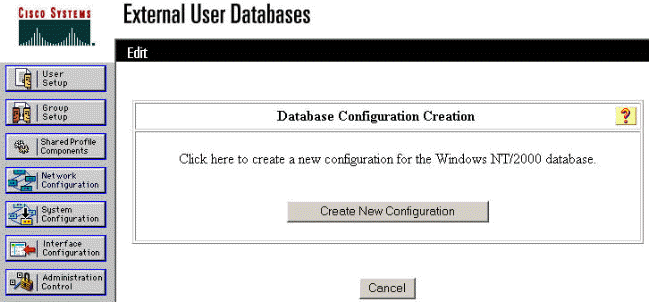
On the "Database Configuration Creation" screen, click Create New Configuration.
-
When prompted, type a name for the NT/2000 Authentication and click Submit. The example below shows the name "Radius/NT Password Expiration."
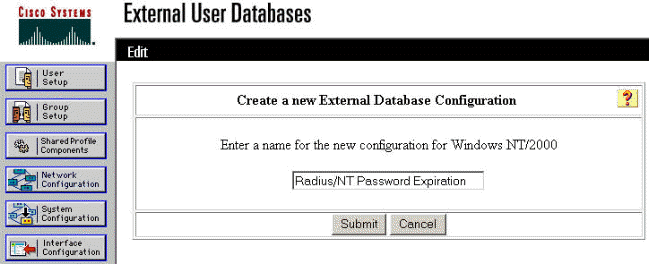
-
Click Configure to configure the Domain Name for User Authentication.
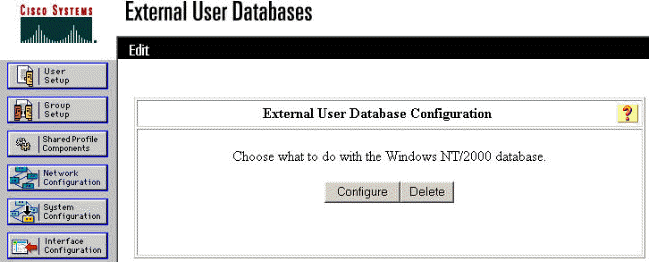
-
Select your NT domain from the "Available Domains," then click the right-arrow button to add it to the "Domain List." Under "MS-CHAP Settings," ensure that the options for Permit password changes using MS-CHAP version 1 and version 2 are selected. Click Submit when you are done.
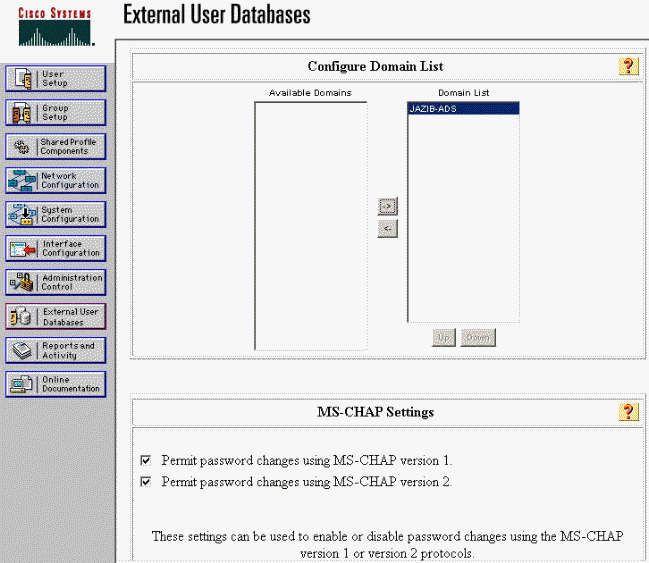
-
Click External User Database in the left panel, then click the link for Database Group Mappings (as seen in this example). You should see an entry for your previously configured external database. The example below shows an entry for "Radius/NT Password Expiration," the database that we just configured.
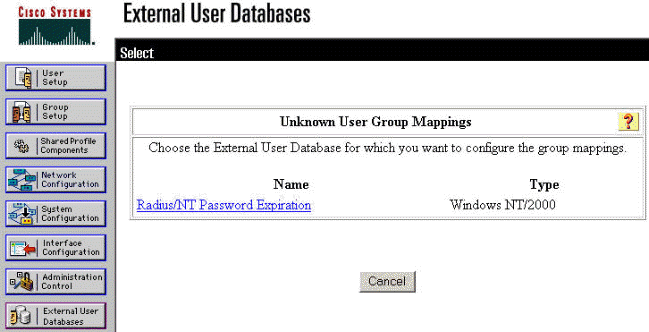
-
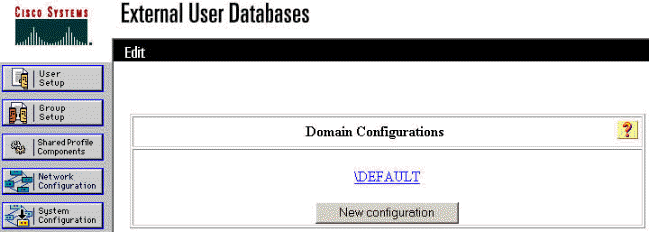
On the "Domain Configurations" screen, click New configuration to add the domain configurations.
-
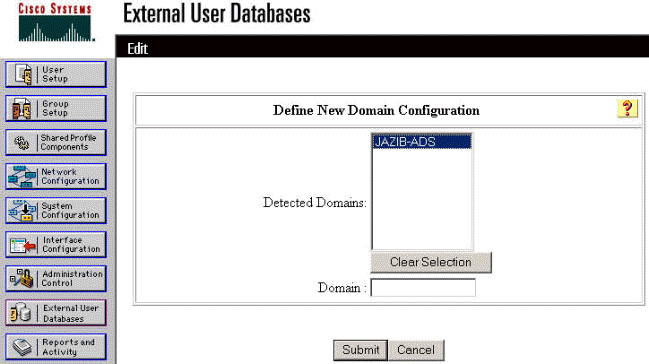
Select your domain from the list of "Detected Domains" and click Submit. The example below shows a domain named "JAZIB-ADS."
-
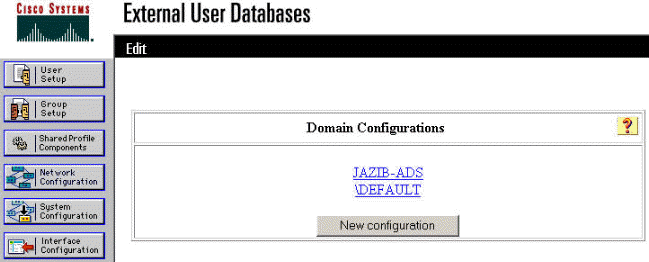
Click on your domain name to configure the group mappings. This example shows the domain "JAZIB-ADS."
-
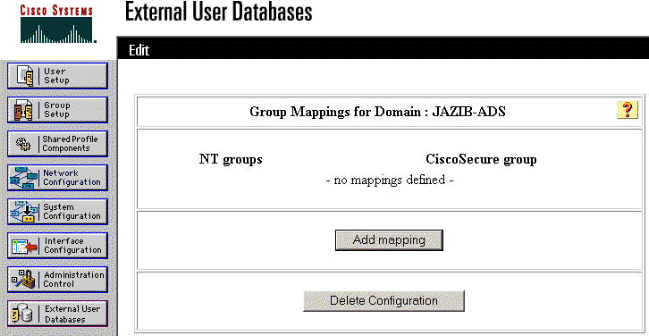
Click Add mapping to define the group mappings.
-
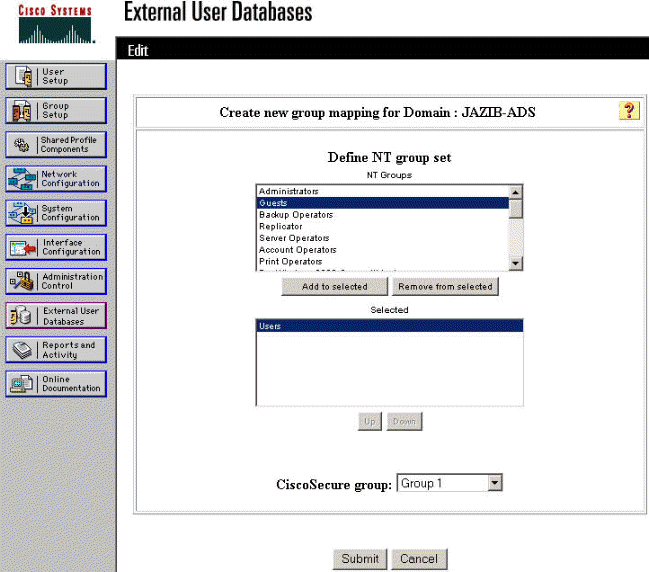
On the "Create new group mapping" screen, map the group on the NT domain to a group on the CSNT RADIUS server, then click Submit.. The example below maps the NT group "Users" to the RADIUS group "Group 1."
-
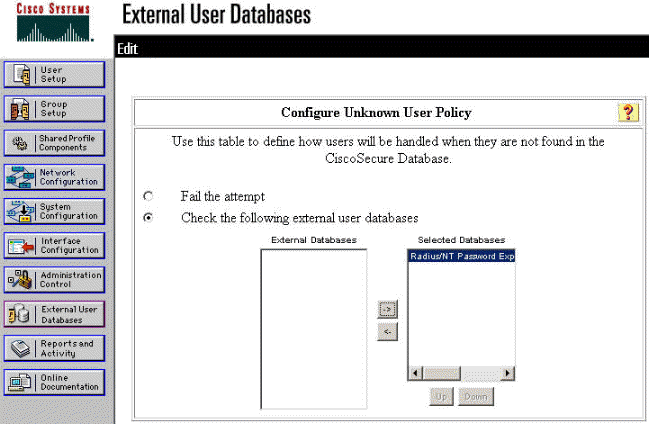
Click External User Database in the left panel, then click the link for Unknown User Policy (as seen in this example). Make sure that the option for Check the following external user databases is selected. Click the right-arrow button to move the previously configured external database from the list of "External Databases" to the list of "Selected Databases."
Testing the NT/RADIUS Password Expiration Feature
The concentrator offers a function to test RADIUS authentication. To test this feature properly, make sure that you follow these steps carefully.
Testing RADIUS Authentication
-
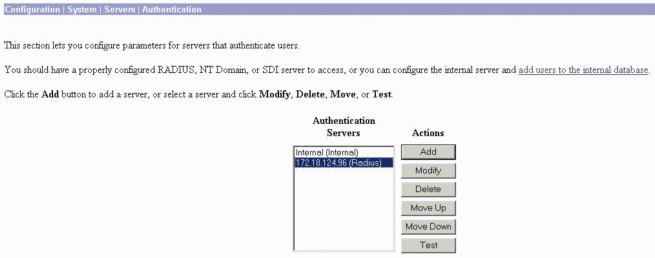
Go to Configuration > System > Servers > Authentication. Select your RADIUS server and click Test.
-
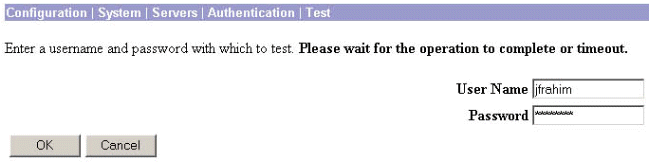
When prompted, type your NT domain user name and password, and then click OK. The example below shows user name "jfrahim" configured on the NT domain server with "cisco123" as the password.
-
If your authentication is set up properly, you should get a message stating "Authentication Successful."

If you receive any message other than the one shown above, there is some configuration or connection problem. Please repeat the configuration and testing steps outlined in this document to ensure that all settings were made properly. Also check the IP connectivity between your devices.
Actual NT Domain Authentication Using RADIUS Proxy to Test the Password Expiration Feature
-
If the user is already defined on the domain server, modify the properties so that the user will be prompted to change the password at the next logon. Go to the "Account" tab of the user's properties dialog box, select the option for User must change password at next logon, then click OK.
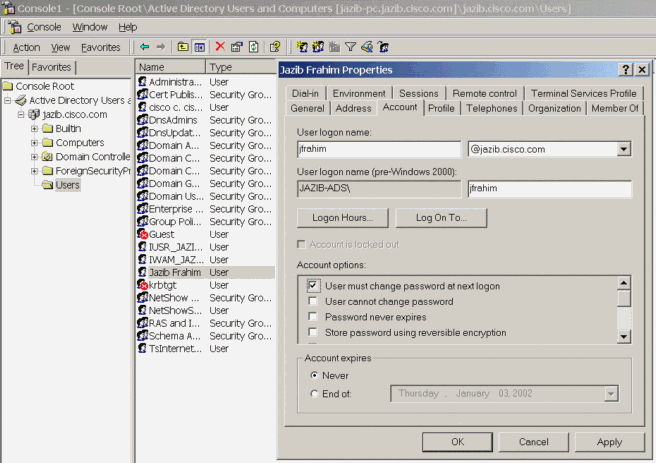
-
Launch the VPN client, then try to establish the tunnel to the concentrator.
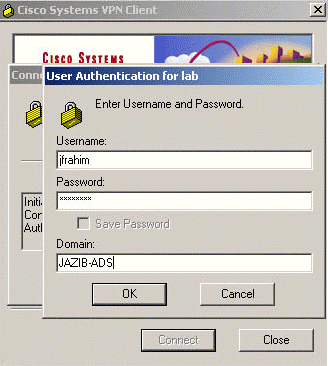
-
During User Authentication, you should be prompted to change the password.
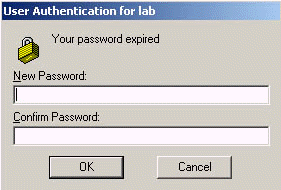
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
19-Jan-2006 |
Initial Release |


























 Feedback
Feedback