Introduction
This document describes a common problem encountered when you configure Cisco Cloud Web Security (CWS) (previously known as ScanSafe) on Cisco Adaptive Security Appliances (ASAs) Versions 9.0 and later.
With CWS, the ASA transparently redirects selected HTTP and HTTPS to a CWS proxy server. Administrators have the ability to allow, block, or warn end-users in order to protect them from malware with the appropriate configuration of security policies on the CWS portal.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these configurations:
- Cisco ASAs via CLI and/or Adaptive Security Device Manager (ASDM)
- Cisco Cloud Web Security on Cisco ASAs
Components Used
The information in this document is based on Cisco ASAs.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Network Diagram
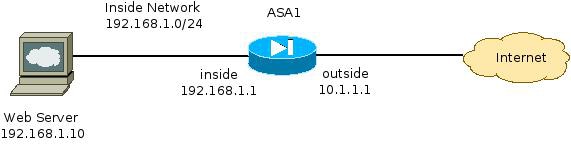
Problem
A common problem encountered when you configure Cisco CWS on the ASA occurs when the internal web servers become inaccessible through the ASA. For example, here is a sample configuration that corresponds to the topology illustrated in the previous section:
hostname ASA1
!
<snip>
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 10.1.1.1 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
<snip>
object network inside-network
subnet 192.168.1.0 255.255.255.0
object network web-server
host 192.168.1.10
!
<snip>
access-list outside_access_in permit tcp any host 192.168.1.10 eq www
access-list outside_access_in permit tcp any host 192.168.1.10 eq https
access-list http-traffic extended permit tcp any any eq www
access-list https-traffic extended permit tcp any any eq https
!
<snip>
scansafe general-options
server primary fqdn proxy193.scansafe.net port 8080
server backup fqdn proxy1363.scansafe.net port 8080
retry-count 5
license <license key>
!
<snip>
object network inside-network
nat (inside,outside) dynamic interface
object network web-server
nat (inside,outside) static 10.1.1.10
!
access-group outside_access_in in interface outside
!
<snip>
class-map http-class
match access-list http_traffic
class-map https-class
match access-list https_traffic
!
policy-map type inspect scansafe http-pmap
parameters
http
policy-map type inspect scansafe https-pmap
parameters
https
!
policy-map outside-policy
class http-class
inspect scansafe http-pmap fail-close
class https-class
inspect scansafe https-pmap fail-close
!
service-policy outside-policy interface inside
With this confguration, the internal web server from outside that uses the IP address 10.1.1.10 might become inaccessible. This issue can be caused by multiple reasons, such as:
- The type of content hosted on the web server.
- The Secure Socket Layer (SSL) certificate of the web server is not trusted by the CWS proxy server.
Solution
Content hosted on any internal server(s) is generally considered trustworthy. Hence, it is not necessary to scan traffic to these servers with CWS. You can add traffic to such internal servers to the allowed list with this configuration:
ASA1(config)# object-group network ScanSafe-bypass
ASA1(config-network-object-group)# network-object host 192.168.1.10
ASA1(config-network-object-group)# exit
ASA1(config)# access-list http_traffic line 1 deny tcp
any object-group ScanSafe-bypass eq www
ASA1(config)# access-list https_traffic line 1 deny tcp
any object-group ScanSafe-bypass eq https
With this configuration, traffic to the internal web server at 192.168.1.10 on TCP ports 80 and 443 are no longer redirected to the CWS proxy servers. If there are multiple servers of this type in the network, you can add them to the object-group named ScanSafe-bypass.
Final Configuration
Here is an example of the final configuration:
hostname ASA1
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 10.1.1.1 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet0/2
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
no nameif
no security-level
no ip address
!
interface Management0/0
management-only
no nameif
no security-level
no ip address
!
object network inside-network
subnet 192.168.1.0 255.255.255.0
object network web-server
host 192.168.1.10
object-group network ScanSafe-bypass
network-object host 192.168.1.10
!
access-list outside_access_in permit tcp any host 192.168.1.10 eq www
access-list outside_access_in permit tcp any host 192.168.1.10 eq https
access-list http_traffic deny tcp any object-group ScanSafe-bypass eq www
access-list http-traffic extended permit tcp any any eq www
access-list https_traffic deny tcp any object-group ScanSafe-bypass eq https
access-list https-traffic extended permit tcp any any eq https
!
scansafe general-options
server primary fqdn proxy193.scansafe.net port 8080
server backup fqdn proxy1363.scansafe.net port 8080
retry-count 5
license <license key>
!
pager lines 24
mtu outside 1500
mtu inside 1500
no asdm history enable
arp timeout 14400
!
object network inside-network
nat (inside,outside) dynamic interface
object network web-server
nat (inside,outside) static 10.1.1.10
!
access-group outside_access_in in interface outside
!
route outside 0.0.0.0 0.0.0.0 10.1.1.254 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
!
class-map http-class
match access-list http_traffic
class-map https-class
match access-list https_traffic
!
policy-map type inspect scansafe
http-pmap
parameters
http
policy-map type inspect scansafe https-pmap
parameters
https
!
policy-map inside-policy
class http-class
inspect scansafe http-pmap fail-close
class https-class
inspect scansafe https-pmap fail-close
!
service-policy inside-policy interface inside
Related Information


 Feedback
Feedback