Introduction
This document describes how to connect a PC to a Cisco Adaptive Security Appliance (ASA) with the use of AnyConnect IPsec (IKEv2) as well as certificate and Authentication, Authorization, and Accounting (AAA) authentication.
Note: The example that is provided in this document describes only the relevant parts that are used in order to obtain an IKEv2 connection between the ASA and AnyConnect. A full configuration example is not provided. Network Address Translation (NAT) or access-list configuration is not described or required in this document.
Prepare for the Connection
This section describes the perparations that are required before you can connect your PC to the ASA.
Certificates with Proper EKU
It is important to note that even though it is not required for the ASA and AnyConnect combination, RFC requires that certificates have Extended Key Usage (EKU):
- The certificate for the ASA must contain the server-auth EKU.
- The certificate for the PC must contain the client-auth EKU.
Note: An IOS router with the recent software revision can place EKUs onto certificates.
Configuration on the ASA
This section describes the ASA configurations that are required before the connection occurs.
Note: The Cisco Adaptive Security Device Manager (ASDM) allows you to create the basic configuration with only a few clicks. Cisco recommends that you use it in order to avoid mistakes.
Crypto Map Configuration
Here is a crypto map example configuration:
crypto dynamic-map DYN 1 set pfs group1
crypto dynamic-map DYN 1 set ikev2 ipsec-proposal secure
crypto dynamic-map DYN 1 set reverse-route
crypto map STATIC 65535 ipsec-isakmp dynamic DYN
crypto map STATIC interface outside
IPsec Proposals
Here is an IPsec proposal example configuration:
crypto ipsec ikev2 ipsec-proposal secure
protocol esp encryption aes 3des
protocol esp integrity sha-1
crypto ipsec ikev2 ipsec-proposal AES256-SHA
protocol esp encryption aes-256
protocol esp integrity sha-1
IKEv2 Policies
Here is an IKEv2 policy example configuration:
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
Client Services and Certificate
You must enable client services and certificates on the correct interface, which is the outside interface in this case. Here is an example configuration:
crypto ikev2 enable outside client-services port 443
crypto ikev2 remote-access trustpoint OUTSIDE
ssl trust-point OUTSIDE outside
Note: The same trustpoint is also assigned for Secure Sockets Layer (SSL), which is intended and required.
Enable AnyConnect Profile
You must enable the AnyConnect profile on the ASA. Here is an example configuration:
webvpn
enable outside
anyconnect image disk0:/anyconnect-win-3.0.5080-k9.pkg 1 regex "Windows NT"
anyconnect profiles Anyconnect disk0:/anyconnect.xml
anyconnect enable
tunnel-group-list enable
Username, Group-Policy, and Tunnel-Group
Here is an example configuration for a basic username, group-policy, and tunnel-group on the ASA:
group-policy GroupPolicy_AC internal
group-policy GroupPolicy_AC attributes
dns-server value 4.2.2.2
vpn-tunnel-protocol ikev1 ikev2 l2tp-ipsec ssl-client ssl-clientless
default-domain value cisco.com
webvpn
anyconnect profiles value Anyconnect type user
username cisco password 3USUcOPFUiMCO4Jk encrypted privilege 15
tunnel-group AC type remote-access
tunnel-group AC general-attributes
address-pool VPN-POOL
default-group-policy GroupPolicy_AC
tunnel-group AC webvpn-attributes
authentication aaa certificate
group-alias AC enable
group-url https://bsns-asa5520-1.cisco.com/AC enable
without-csd
AnyConnect Profile
Here is an example profile with the relevant parts shown in bold:
<?xml version="1.0" encoding="UTF-8"?>
<AnyConnectProfile xmlns="http://schemas.xmlsoap.org/encoding/"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation=
"http://schemas.xmlsoap.org/encoding/ AnyConnectProfile.xsd">
<ClientInitialization>
<UseStartBeforeLogon UserControllable="true">false</UseStartBeforeLogon>
<AutomaticCertSelection UserControllable="true">false
</AutomaticCertSelection>
<ShowPreConnectMessage>false</ShowPreConnectMessage>
<CertificateStore>All</CertificateStore>
<CertificateStoreOverride>false</CertificateStoreOverride>
<ProxySettings>Native</ProxySettings>
<AllowLocalProxyConnections>true</AllowLocalProxyConnections>
<AuthenticationTimeout>12</AuthenticationTimeout>
<AutoConnectOnStart UserControllable="true">false</AutoConnectOnStart>
<MinimizeOnConnect UserControllable="true">true</MinimizeOnConnect>
<LocalLanAccess UserControllable="true">false</LocalLanAccess>
<ClearSmartcardPin UserControllable="true">true</ClearSmartcardPin>
<AutoReconnect UserControllable="false">true
<AutoReconnectBehavior UserControllable="false">DisconnectOnSuspend
</AutoReconnectBehavior>
</AutoReconnect>
<AutoUpdate UserControllable="false">true</AutoUpdate>
<RSASecurIDIntegration UserControllable="true">Automatic
</RSASecurIDIntegration>
<WindowsLogonEnforcement>SingleLocalLogon</WindowsLogonEnforcement>
<WindowsVPNEstablishment>LocalUsersOnly</WindowsVPNEstablishment>
<AutomaticVPNPolicy>false</AutomaticVPNPolicy>
<PPPExclusion UserControllable="false">Disable
<PPPExclusionServerIP UserControllable="false"></PPPExclusionServerIP>
</PPPExclusion>
<EnableScripting UserControllable="false">false</EnableScripting>
<EnableAutomaticServerSelection UserControllable="false">false
<AutoServerSelectionImprovement>20</AutoServerSelectionImprovement>
<AutoServerSelectionSuspendTime>4</AutoServerSelectionSuspendTime>
</EnableAutomaticServerSelection>
<RetainVpnOnLogoff>false
</RetainVpnOnLogoff>
</ClientInitialization>
<ServerList>
<HostEntry>
<HostName>bsns-asa5520-1</HostName>
<HostAddress>bsns-asa5520-1.cisco.com</HostAddress>
<UserGroup>AC</UserGroup>
<PrimaryProtocol>IPsec</PrimaryProtocol>
</HostEntry>
</ServerList>
</AnyConnectProfile>
Here are some important notes about this configuration example:
- When you create the profile, the HostAddress must match the Certificate Name (CN) on the certificate that is used for IKEv2. Enter the crypto ikev2 remote-access trustpoint command in order to define this.
- The UserGroup must match the name of the tunnelgroup to which the IKEv2 connection falls. If they do not match, the connection often fails and the debugs indicate a Diffie-Hellman (DH) group mismatch or a similar false negative.
Make the Connection
This section describes the PC-to-ASA connection when the profile is already present.
Note: The information that you input into the GUI in order to connect is the <HostName> value that is configured in the AnyConnect profile. In this case, bsns-asa5520-1 is entered, not the complete Fully Qualified Domain Name (FQDN).
When you first attempt to connect through AnyConnect, the gateway prompts you to select the certificate (if automatic certificate selection is disabled):
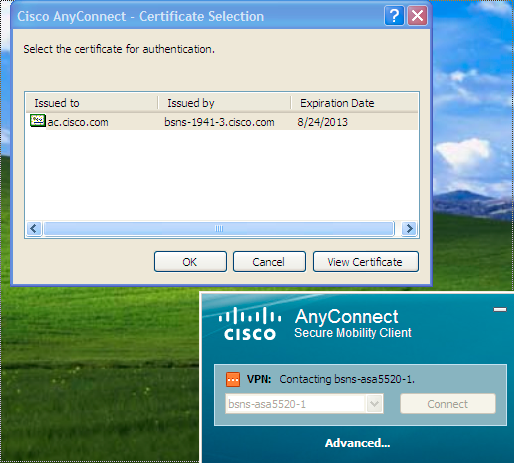
You must then enter the Username and Password:
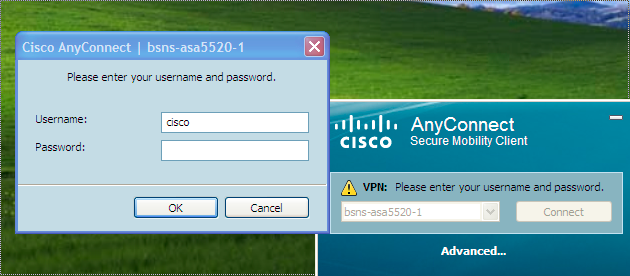
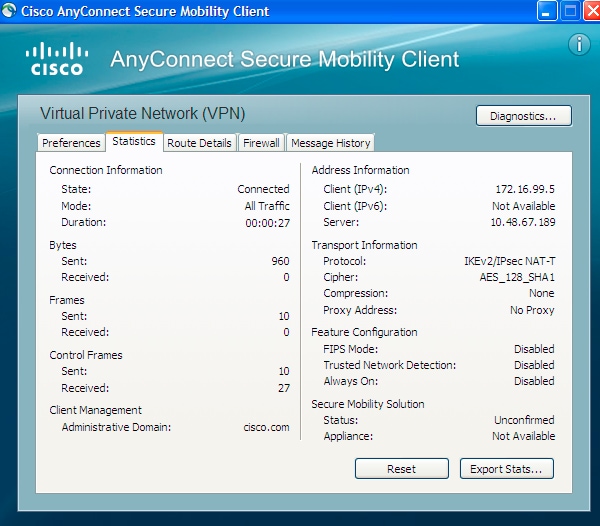
Once the Username and Password are accepted, the connection is successful and the AnyConnect statistics can be verified:
Verification on ASA
Enter this command on the ASA in order to verify that the connection uses IKEv2 as well as AAA and certificate authentication:
bsns-asa5520-1# show vpn-sessiondb detail anyconnect filter name cisco
Session Type: AnyConnect Detailed
Username : cisco Index : 6
Assigned IP : 172.16.99.5 Public IP : 1.2.3.4
Protocol : IKEv2 IPsecOverNatT AnyConnect-Parent
License : AnyConnect Premium
Encryption : AES256 AES128 Hashing : none SHA1 SHA1
Bytes Tx : 0 Bytes Rx : 960
Pkts Tx : 0 Pkts Rx : 10
Pkts Tx Drop : 0 Pkts Rx Drop : 0
Group Policy : GroupPolicy_AC Tunnel Group : AC
Login Time : 15:45:41 UTC Tue Aug 28 2012
Duration : 0h:02m:41s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
IKEv2 Tunnels: 1
IPsecOverNatT Tunnels: 1
AnyConnect-Parent Tunnels: 1
AnyConnect-Parent:
Tunnel ID : 6.1
Public IP : 1.2.3.4
Encryption : none Auth Mode : Certificate and userPassword
Idle Time Out: 30 Minutes Idle TO Left : 27 Minutes
Client Type : AnyConnect
Client Ver : 3.0.08057
IKEv2:
Tunnel ID : 6.2
UDP Src Port : 60468 UDP Dst Port : 4500
Rem Auth Mode: Certificate and userPassword
Loc Auth Mode: rsaCertificate
Encryption : AES256 Hashing : SHA1
Rekey Int (T): 86400 Seconds Rekey Left(T): 86238 Seconds
PRF : SHA1 D/H Group : 5
Filter Name :
Client OS : Windows
IPsecOverNatT:
Tunnel ID : 6.3
Local Addr : 0.0.0.0/0.0.0.0/0/0
Remote Addr : 172.16.99.5/255.255.255.255/0/0
Encryption : AES128 Hashing : SHA1\
Encapsulation: Tunnel
Rekey Int (T): 28800 Seconds Rekey Left(T): 28638 Seconds
Rekey Int (D): 4608000 K-Bytes Rekey Left(D): 4608000 K-Bytes
Idle Time Out: 30 Minutes Idle TO Left : 27 Minutes
Bytes Tx : 0 Bytes Rx : 960
Pkts Tx : 0 Pkts Rx : 10
Known Caveats
These are the known caveats and issues that are related to the information that is described in this document:
- The IKEv2 and SSL trustpoints must be the same.
- Cisco recommends that you use the FQDN as the CN for the ASA-side certificates. Ensure that you reference the same FQDN for the <HostAddress> in the AnyConnect profile.
- Remember to insert the <HostName> value from the AnyConnect profile when you connect.
- Even in the IKEv2 configuration, when AnyConnect connects to the ASA, it downloads profile and binary updates over SSL, but not IPsec.
- The AnyConnect connection over IKEv2 to the ASA uses EAP-AnyConnect, a proprietary mechanism that allows simpler implementation.




 Feedback
Feedback