Basic TACACS+ Configuration Example
Available Languages
Contents
Introduction
This document provides a basic sample configuration for Terminal Access Controller Access Control System+ (TACACS+) for user dial-up authentication to a Network Access Server (NAS).
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
This configuration was developed and tested using the following software and hardware versions:
-
NAS
-
TACACS+ Configuration File (freeware version)
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Note: TACACS+ is a Cisco proprietary version of TACACS so it is only supported with Cisco ACS.
Conventions
For more information on document conventions, see the Cisco Technical Tips Conventions.
Configure
In this section, you are presented with the information to configure the features described in this document.
Note: To find additional information on the commands used in this document, use the Command Lookup Tool ![]() (registered customers only) .
(registered customers only) .
Network Diagram
This document uses the network setup shown in the diagram below.
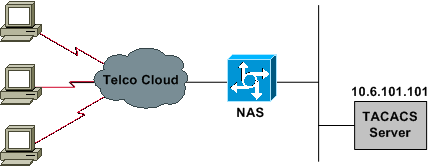
Configurations
This document uses the configurations shown below.
Note: Make sure that dial-in works. Once the modem can connect and authenticate locally, turn on TACACS+.
| NAS |
|---|
version 11.2 ! service timestamps debug datetime msec service timestamps log uptime service password-encryption no service udp-small-servers no service tcp-small-servers ! hostname Cisco3640 ! aaa new-model aaa authentication login default tacacs local aaa authentication login consoleport none aaa authentication ppp default if-needed tacacs aaa authorization network tacacs !--- This is needed for static IP address assignment. ! enable password cisco ! username cisco password letmein ! interface Ethernet0 ip address 10.29.1.3 255.255.255.0 ! Interface Group-Async1 ip unnumbered Ethernet0 encapsulation ppp async mode interactive peer default ip address pool async no cdp enable ppp authentication chap group-range 1 16 ! ip local pool async 10.6.100.101 10.6.100.103 tacacs-server host 10.6.101.101 tacacs-server key cisco ! line con 0 login authentication consoleport !--- This always allows console port access. ! line 1 16 autoselect ppp autoselect during-login modem Dialin transport input all stopbits 1 rxspeed 115200 txspeed 115200 flowcontrol hardware ! line aux 0 ! line vty 0 4 ! end |
| TACACS+ Configuration File (Freeware Version) |
|---|
!--- This creates a superuser (such as one with administrator permissions) !--- who is granted all privileges by "default service = permit", and has a password !--- that allows for connections in any mode.
user = Russ
{
global = cleartext 'bar'
default service = permit
}
!--- This creates a normal PPP user who gets an IP address from the router.
user = Jason
{
chap = cleartext 'letmein'
service = ppp protocol = ip {}
}
!--- This creates a user whose IP address is statically assigned.
user = Laura
{
chap = cleartext 'letmein'
service = ppp protocol = ip
{
addr = 10.1.1.104
}
} |
Verify
There is currently no verification procedure available for this configuration.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
Troubleshooting Commands
Certain show commands are supported by the Output Interpreter Tool ![]() (registered customers only) , which allows you to view an analysis of show command output.
(registered customers only) , which allows you to view an analysis of show command output.
Note: Before issuing debug commands, please see Important Information on Debug Commands.
-
debug ppp negotiation—Shows if a client is passing PPP negotiation; check at this point for address negotiation.
-
debug ppp authentication—Shows if a client is passing authentication. If you are using a Cisco IOS® Software Release earlier than 11.2, issue the debug ppp chap command instead.
-
debug ppp error—Displays protocol errors and error statistics associated with PPP connection negotiation and operation.
-
debug aaa authentication—Shows what method is being used to authenticate (it should be TACACS+ unless the TACACS+ server is down) and whether or not the users are passing authentication.
-
debug aaa authorization—Shows what method is being used for authorization and whether or not the users are passing it.
-
debug tacacs—Shows the messages sent to the server.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
15-Nov-2007 |
Initial Release |
 Feedback
Feedback