Field Notice: FN - 62568 - 15454-10DME-C/15454-10DME-L - 1G/2G Fibre Channel (FC) Traffic May Fail if Specific Data Patterns are Present - FPGA Update Required
Available Languages
Revised November 13, 2006
November 7, 2006
NOTICE:
THIS FIELD NOTICE IS PROVIDED ON AN "AS IS" BASIS AND DOES NOT IMPLY ANY KIND OF GUARANTEE OR WARRANTY, INCLUDING THE WARRANTY OF MERCHANTABILITY. YOUR USE OF THE INFORMATION ON THE FIELD NOTICE OR MATERIALS LINKED FROM THE FIELD NOTICE IS AT YOUR OWN RISK. CISCO RESERVES THE RIGHT TO CHANGE OR UPDATE THIS FIELD NOTICE AT ANY TIME.
Products Affected
| Products Affected |
Comments |
|---|---|
| 15454W - 15454-10DME-C= |
Running CTC R7.00, 7.01, 7.02, 7.20, 7.21 |
| 15454W - 15454-10DME-L= |
Running CTC R7.00, 7.01, 7.02, 7.20, 7.21 |
Problem Description
1G and 2G Fibre Channel (FC) may fail when operating the 15454-10DME-C or 15454-10DME-L in GFP-T Fibre Channel operation mode if ingress frames containing the below payload byte pattern are repeated. These failures could trigger erroneous Invalid Transmission Word (ITW) detection, resulting in data corruption. Failures will only occur if the following pattern is repeated from the client I/F starting from byte #3 of the FC word.
D21.5, D21.3, D21.3 = xx B5 75 75 D21.5, D21.4, D21.4 = xx B5 95 95 D21.5, D21.7, D21.7 = xx B5 F5 F5 D21.5, D21.6, D21.6 = xx B5 D5 D5 D10.5, D21.4, D21.4 = xx AA 95 95 D10.5, D21.6, D21.6 = xx AA D5 D5
Background
This issue was found at a customer site and resolved through an FPGA update incorporated in CTC NE SW Release 7.03 and 7.22 or later.
Problem Symptoms
Traffic corruption may occur when using 15454-10DME-C or 15454-10DME-L in 1G or 2G GFP-T Fibre Channel operation mode.
If Distance Extension (DE) is ON traffic will hang up and no TX packets will be sent to the far end device. The far end device will not see any errors and CTC will stop counting TX packets.
If DE is OFF, errored packets will be sent to the far end device and both CTC and the far end device will report CRC errors.
Workaround/Solution
This issue has been addressed through an update to the FPGA image for the 15454-MXP-10DME-C and 15454-MXP-10DME-L cards available in CTC NE Release 7.0.3 (available November, 2006), and 7.2.2 (available February, 2007), or later.
Since the update to the FPGA image is disruptive to traffic, customers will need to follow the following procedure during a maintenance window to activate the upgraded FPGA image.
Software Upgrade
-
Go to Node view/Maintenance/Software
-
Download the SW load 7.0.3 or 7.22 or later into the Protection memory area of the active TCC.
-
Once the download is completed, activate the new image.
-
TCC will reboot and the node connection will be lost.
-
Close the CTC window.
-
Go to the CTC Launcher browser window:
-
Delete the CTC Cache.
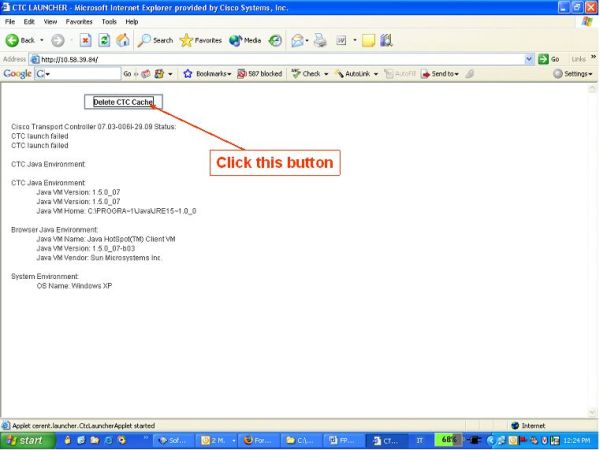
-
Download the SW load 7.0.3 into the Protection memory of the active TCC.
-
Once the download is completed, activate the new image.
-
Close the Browser application.
-
Re-Open the browser and launch CTC on the TCC upgraded to 7.0.3 by specifying the IP address of the NE.
-
Go to Node view and double-click on the MXP10DME card to be upgraded.
-
In the Card view, go to Provisioning/Line.
-
Change the Admin. State of Client ports to OOS, DSBL (unlocked, Disable) and then click Apply.
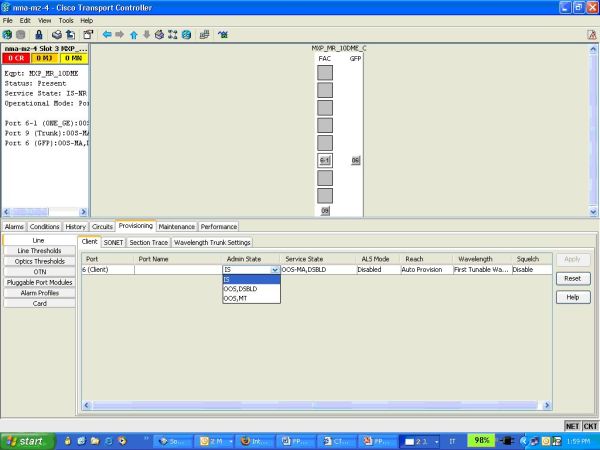
-
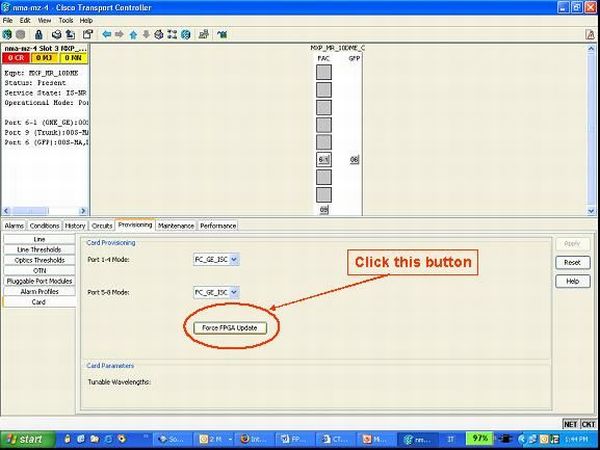
Go to Card view/Provisioning/Card:
-
Click on the button "Force FPGA Update"
-
Card will go through a Reboot and then restart with the updated FPGA.
-
Once the card has completed the reboot, Go to Card view/ Provisioning/Line and revert the Admin. State to IS (unlocked).
Procedure completed.
15454-10DME-C/15454-10DME-L in Y Cable Protection scheme
This FPGA upgrade procedure is applicable only if the Near End (NE) and Far End (FE) node is configured with 2x 15454-10DME-C/15454-10DME-L, Working and Protect, with the Working Active and the Protect Stdby on each protection group supported on the client ports. NE Working card trunk port connected to FE Working card trunk port and NE Protect card trunk port connected to FE Protect card trunk port.
-
Ensure traffic is running on the Working cards, for each protection group supported by the 15454-10DME-C/15454-10DME-L cards.
-
Go to Shelf view, Maintenance tab, Protection sub-tab; select the protection group under evaluation and verify that the Working card client port is reported as Working/Active and that the Protect card client port is reported as Protect/Standby. Repeat this check on Near End and Far End protection groups.
-
Issue a Lockout of Protect to ensure traffic does not switch to Protect.
-
Do this on both NE and FE protection groups.
-
Disable client ports on the Protect cards and complete Force FPGA Upgrade as specified above (Step 15).
-
The upgrade should be hitless since traffic is accommodated on the Working facilities.
-
Once the card has completed SW reset, set the client ports to IS-NR state.
-
Ensure no alarm/condition is present on the Protect cards.
-
Release Lockout of Protection on both ends, on every protection group.
-
Issue a Force to Protect on both NE and FE protection groups so that traffic switches from Working to Protect facilities.
-
Do this on every protection group supported by the 15454-10DME-C/15454-10DME-L cards. The Force to Protect switching is traffic affecting (<50ms).
-
Disable client ports on the Working cards and complete Manual FPGA upgrade as noted above (Step 15).
-
The upgrade should be hitless since traffic is accommodated on the Protect facilities.
-
Once the card has completed SW reset, move back client ports to IS-NR state.
-
Ensure no alarm/condition is present on the Working cards.
-
Release Force to Protect on both ends, on every protection group.
-
If the protection group is revertive, this operation will revert traffic to Working facilities and can result in traffic impact of less than 50ms.
-
If the protection group is non-revertive, the operation will keep traffic on Protect facilities without traffic impact.
DDTS
To follow the bug ID link below and see detailed bug information, you must be a registered user and you must be logged in.
| DDTS |
Description |
|---|---|
| CSCsg00777 (registered customers only) |
Traffic hang up with specific FC pattern |
Revision History
| Revision |
Date |
Comment |
|---|---|---|
| 1.1 |
14-NOV-2006 |
Added Comments to Products Affected and availabilty dates to Workaround/Solution section. |
| 1.0 |
07-NOV-2006 |
Initial Public Release |
For More Information
If you require further assistance, or if you have any further questions regarding this field notice, please contact the Cisco Systems Technical Assistance Center (TAC) by one of the following methods:
Receive Email Notification For New Field Notices
Product Alert Tool - Set up a profile to receive email updates about reliability, safety, network security, and end-of-sale issues for the Cisco products you specify.
 Feedback
Feedback