Configuring L2TP Multihop to Perform Several Hops from the NAS to the LNS
Available Languages
Contents
Introduction
Multihop Virtual Private Dialup Network (VPDN) allows you to configure several hops on the way from the L2TP access concentrator (LAC) to the L2TP Network Server (LNS). A maximum of four hops is supported. The tunnel is terminated in every hop (LNS) and reinitiated to the next hop destination. This process allows tunnel switching. Multihopping can be used between ISPs to provide a wholesale Access Virtual Private Network (VPN) service.
Both Layer 2 Forwarding (L2F) and Layer 2 Tunnel Protocol (L2TP) are supported in this scenario. However, since L2TP is becoming the industry standard, this document focuses on L2TP.
Prerequisites
Conventions
For more information on document conventions, see the Cisco Technical Tips Conventions.
Requirements
There are no specific prerequisites for this document.
For an explanation of the VPDN process, refer to Understanding VPDN.
Components Used
The information in this document is based on the software and hardware versions below.
-
Cisco IOS® software versions 12.3(6)
-
L2TP Access Concentrator (LAC): a Cisco AS5400 Access Server
-
L2TP Network Servers (LNS): Cisco 7200 Routers
The information presented in this document was created from devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If you are working in a live network, ensure that you understand the potential impact of any command before using it.
Configure
In this section, you are presented with the information to configure the features described in this document.
Note: To find additional information on the commands used in this document, use the Command Lookup Tool (registered customers only) .
Network Diagram
This document uses the network setup shown in the diagram below.
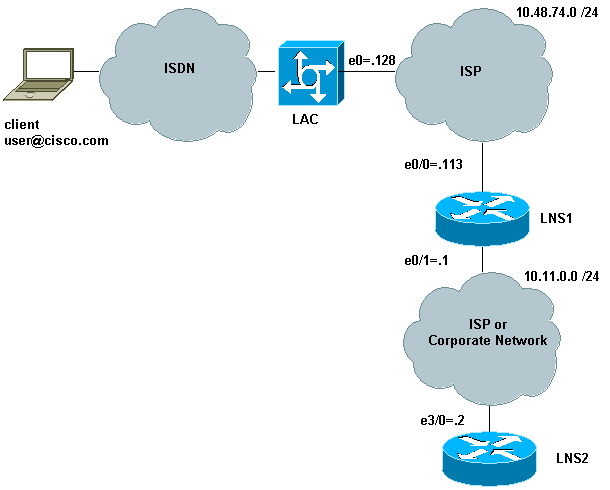
In this setup:
-
The client uses ISDN to dial in the LAC (it could, for instance, use DSL instead).
-
The LAC uses an E1 primary rate interface (PRI) to accept calls.
-
There is no tunnel already open between the L2TP devices.
-
The tunnel and session setup are based on the domain-name. There is no AAA server for authentication or authorization.
-
It uses two LNSs.
The process is as follows:
-
The client dials into the LAC. The client and the LAC negotiate the LCP options. The authentication phase is carried out, and the LAC gets the username (user@cisco.com) and password. Based on the domain name (cisco.com in our example), it opens a tunnel followed by a session to the LNS1.
-
Once the L2TP session is opened between the LAC and the LNS1, the LNS1 gets the LCP options that were negotiated between the LAC and the client, along with the username and password (user@cisco.com, password).
-
The LNS1 has a VPDN group with the same domain (cisco.com) in its configuration. It opens a tunnel and session to the LNS2. If it does not have such a configuration, it terminates the PPP session by authenticating the client, negotiating the IP address and installing the route.
-
Once the L2TP session is opened between the LNS1 and the LNS2, the LNS2 gets the LCP options that were negotiated between the LAC and the client, along with the user and password (user@cisco.com, password). It authenticates the user, negotiates IPCP and installs the route.
Configurations
This document uses the configurations shown below. The minimum number of commands is used here. For instance, the LAC will not terminate any session, so there is no need to configure an IP address in the Dialer1 or Group-async1 interface. The LNS1 will not terminate any PPP session, so there is no IP address under virtual-template1.
| LAC |
|---|
version 12.3 service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname LAC ! boot-start-marker no boot startup-test boot-end-marker ! enable password 7 02050D480809 ! ! ! resource-pool disable spe default-firmware spe-firmware-2 no aaa new-model ip subnet-zero no ip domain lookup ! ip cef ! -- Enables VPDN. vpdn enable ! -- VPDN tunnel authorization is based first on the domain name ! -- (the default is DNIS). ! vpdn search-order domain ! ! -- The LAC opens an L2TP tunnel and session to 10.48.74.113 (LNS1) ! -- using the password LACLNS1 for users whose domain-name is cisco.com. vpdn-group 1 request-dialin protocol l2tp domain cisco.com initiate-to ip 10.48.74.113 l2tp tunnel password LACLNS1 ! isdn switch-type primary-net5 ! ! no voice hpi capture buffer no voice hpi capture destination ! ! controller E1 7/0 pri-group timeslots 1-31 ! interface FastEthernet0/0 ip address 10.48.74.128 255.255.255.0 duplex auto speed auto ! interface Serial7/0:15 no ip address encapsulation ppp dialer rotary-group 1 isdn switch-type primary-net5 ! interface Group-Async1 no ip address encapsulation ppp async mode interactive ppp authentication chap callin group-range 1/00 3/107 ! interface Dialer1 no ip address encapsulation ppp ppp authentication chap callin ! ip classless no ip http server ! ! voice-port 7/0:D ! line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 line 1/00 1/107 modem InOut transport input all line 3/00 3/107 modem InOut transport input all ! scheduler allocate 10000 400 ! end |
| LNS1 |
|---|
version 12.3 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname LNS1 ! boot-start-marker boot-end-marker ! enable password cisco ! clock timezone CET 1 no aaa new-model ip subnet-zero ip cef ! ! no ip domain lookup ! ! -- Enables VPDN. vpdn enable ! -- Enables VPDN multihop. vpdn multihop ! !-- LNS1 accepts L2TP tunnel/session from the router named LAC. !-- The password LACLNS1 is used between LAC and LNS1 for authentication. !-- The virtual-template 1 is used for the PPP phase. vpdn-group FromLAC accept-dialin protocol l2tp virtual-template 1 terminate-from hostname LAC l2tp tunnel password 0 LACLNS1 ! ! -- The LNS1 opens a L2TP tunnel and session to 10.11.0.2 (LNS2) ! -- using the password LNS1LNS2 for users whose domain-name is cisco.com. vpdn-group TowardsLNS2 request-dialin protocol l2tp domain cisco.com initiate-to ip 10.11.0.2 l2tp tunnel password 0 LNS1LNS2 ! ! interface Ethernet0/0 ip address 10.48.74.113 255.255.255.0 no ip proxy-arp half-duplex ! interface Ethernet0/1 ip address 10.11.0.1 255.255.255.0 half-duplex ! interface Virtual-Template1 no ip address ppp authentication chap callin ! no ip http server ip classless ! ! dial-peer cor custom ! line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 exec-timeout 0 0 password ww login ! ntp clock-period 17208915 ntp server 10.48.75.134 ! ! end |
| LNS2 |
|---|
version 12.3 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname LNS2 ! boot-start-marker boot-end-marker ! enable password cisco ! username user@cisco.com password 0 cisco no aaa new-model ip subnet-zero ! ! ip cef ! !-- Enables VPDN. vpdn enable ! !-- LNS2 accepts L2TP tunnel/session from the router named LNS1. !-- The password LNS1LNS2 is used between LNS1 and LNS2 for authentication. !-- The virtual-template 1 is used for the PPP phase. vpdn-group FromLNS1 ! Default L2TP VPDN group accept-dialin protocol l2tp virtual-template 1 l2tp tunnel password 0 LNS1LNS2 ! ! interface Loopback0 ip address 192.168.1.1 255.255.255.0 ! interface Ethernet3/0 ip address 10.11.0.2 255.255.255.0 duplex half ! interface Virtual-Template1 ip unnumbered Loopback0 peer default ip address pool VpdnUsers ppp authentication chap callin ! ip local pool VpdnUsers 192.168.1.2 192.168.1.254 ip classless no ip http server ! ! line con 0 exec-timeout 0 0 transport preferred all transport output all stopbits 1 line aux 0 transport preferred all transport output all stopbits 1 line vty 0 4 login transport preferred all transport input all transport output all ! ! ! end |
Verify
This section provides information you can use to confirm your configuration is working properly.
Certain show commands are supported by the Output Interpreter Tool (registered customers only) , which allows you to view an analysis of show command output.
-
show vpdn - Displays information about active L2TP or L2F Protocol tunnel and message identifiers in a VPDN.
-
show caller user user detail - display caller information.
The output from using these commands on the LAC, LNS1 and LNS2 is shown here:
LAC#show vpdn L2TP Tunnel and Session Information Total tunnels 1 sessions 1 LocID RemID Remote Name State Remote Address Port Sessions VPDN Group 18693 28416 LNS1 est 10.48.74.113 1701 1 1 LocID RemID TunID Intf Username State Last Chg Uniq ID 19 21 18693 Se7/0:3 user@cisco.com est 00:02:04 28 %No active L2F tunnels %No active PPTP tunnels LAC#
We see that LNS1 has two tunnels with one session in each.
LNS1#show vpdn L2TP Tunnel and Session Information Total tunnels 2 sessions 2 LocID RemID Remote Name State Remote Address Port Sessions VPDN Group 28416 18693 LAC est 10.48.74.128 1701 1 FromLAC LocID RemID TunID Intf Username State Last Chg Uniq ID 21 19 28416 SSS Circuit user@cisco.com est 00:02:25 13 LocID RemID Remote Name State Remote Address Port Sessions VPDN Group 30255 35837 LNS2 est 10.11.0.2 1701 1 TowardsLNS2 LocID RemID TunID Intf Username State Last Chg Uniq ID 22 9 30255 SSS Circuit user@cisco.com est 00:02:25 13 %No active L2F tunnels %No active PPTP tunnels LNS1#
LNS2#show vpdn
L2TP Tunnel and Session Information Total tunnels 1 sessions 1
LocID RemID Remote Name State Remote Address Port Sessions VPDN Group
35837 30255 LNS1 est 10.11.0.1 1701 1 FromLNS1
LocID RemID TunID Intf Username State Last Chg Uniq ID
9 22 35837 Vi2.1 user@cisco.com est 00:03:22 8
%No active L2F tunnels
%No active PPTP tunnels
LNS2#
LNS2#show caller user user@cisco.com detail
User: user@cisco.com, line Vi2.1, service PPPoVPDN
Connected for 00:03:33, Idle for 00:00:58
Timeouts: Limit Remaining Timer Type
- - -
PPP: LCP Open, CHAP (<-), IPCP
LCP: -> peer, AuthProto, MagicNumber
<- peer, MagicNumber, EndpointDisc
NCP: Open IPCP
IPCP: <- peer, Address
-> peer, Address
IP: Local 192.168.1.1, remote 192.168.1.2
Counts: 56 packets input, 2562 bytes
57 packets output, 2570 bytes
LNS2#
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
Troubleshooting Commands
Certain show commands are supported by the Output Interpreter Tool (registered customers only) , which allows you to view an analysis of show command output.
Note: Before issuing debug commands, please see Important Information on Debug Commands.
Troubleshooting Commands on the LAC
-
debug isdn q931 - Displays information about call setup and teardown of ISDN network connections (Layer 3) between the local router (user side) and the network.
-
debug vpdn event - Displays L2TP errors and events that are a part of normal tunnel establishment or shutdown for VPDNs.
-
debug vpdn error - Troubleshoots Layer 2 Tunnel Protocol Version 3 (L2TPv3) and the surrounding Layer 2 tunneling infrastructure.
-
debug vpdn l2x-events - Displays events resulting from protocol-specific conditions.
-
vpdn l2x-errors - Displays errors that occur in protocol-specific conditions.
-
debug ppp negotiation - Displays if a client is passing PPP negotiation. You can see what options (for example, callback or MLP) and what protocols (such as IP and IPX) are being negotiated.
Troubleshooting Commands on the LNS1
-
debug vpdn event
-
debug vpdn error
-
debug vpdn l2x event
-
vpdn l2x-erro
-
debug ppp negotiation
-
debug vtemplate error - Displays cloning information for a virtual access interface from the time it is cloned from a virtual template to the time the virtual access interface comes down when the call ends.
-
debug vtemplate event - Displays cloning information for a virtual access interface from the time it is cloned from a virtual template to the time the virtual access interface comes down when the call ends.
Troubleshooting Commands on the LNS2
Same as for LNS1, but with one additional command:
-
debug ip peer - Displays address activity and contains additional output when pool groups are defined.
Debug Output - LAC
The debug output on the LAC is as follows:
LAC#
*Apr 23 08:55:23.579: ISDN Se7/0:15 Q931: RX <- SETUP pd = 8 callref = 0x256F
Sending Complete
Bearer Capability i = 0x8890
Standard = CCITT
Transer Capability = Unrestricted Digital
Transfer Mode = Circuit
Transfer Rate = 64 kbit/s
Channel ID i = 0xA18384
Preferred, Channel 4
Calling Party Number i = 0xA1, '8101'
Plan:ISDN, Type:National
Called Party Number i = 0x81, '7070'
Plan:ISDN, Type:Unknown
Locking Shift to Codeset 6
Codeset 6 IE 0x28 i = 'TAC BRI 8101'
*Apr 23 08:55:23.583: ISDN Se7/0:15 Q931: TX -> CALL_PROC pd = 8 callref = 0xA56F
Channel ID i = 0xA98384
Exclusive, Channel 4
*Apr 23 08:55:23.583: ISDN Se7/0:15 Q931: TX -> CONNECT pd = 8 callref = 0xA56F
Channel ID i = 0xA98384
Exclusive, Channel 4
*Apr 23 08:55:23.583: Se7/0:3 PPP: Using dialer call direction
*Apr 23 08:55:23.583: Se7/0:3 PPP: Treating connection as a callin
*Apr 23 08:55:23.583: Se7/0:3 PPP: Phase is ESTABLISHING, Passive Open
*Apr 23 08:55:23.583: Se7/0:3 LCP: State is Listen
*Apr 23 08:55:23.607: ISDN Se7/0:15 Q931: RX <- CONNECT_ACK pd = 8
callref = 0x256F
*Apr 23 08:55:23.695: Se7/0:3 LCP: I CONFREQ [Listen] id 180 len 31
*Apr 23 08:55:23.695: Se7/0:3 LCP: MagicNumber 0x9028FFED (0x05069028FFED)
*Apr 23 08:55:23.695: Se7/0:3 LCP: MRRU 1524 (0x110405F4)
*Apr 23 08:55:23.695: Se7/0:3 LCP: EndpointDisc 1 user@cisco.com
*Apr 23 08:55:23.695: Se7/0:3 LCP: (0x1311017573657240636973636F2E636F)
*Apr 23 08:55:23.695: Se7/0:3 LCP: (0x6D)
*Apr 23 08:55:23.695: Se7/0:3 LCP: O CONFREQ [Listen] id 1 len 15
*Apr 23 08:55:23.695: Se7/0:3 LCP: AuthProto CHAP (0x0305C22305)
*Apr 23 08:55:23.695: Se7/0:3 LCP: MagicNumber 0x050E44FB (0x0506050E44FB)
*Apr 23 08:55:23.695: Se7/0:3 LCP: O CONFREJ [Listen] id 180 len 8
*Apr 23 08:55:23.695: Se7/0:3 LCP: MRRU 1524 (0x110405F4)
*Apr 23 08:55:23.727: Se7/0:3 LCP: I CONFACK [REQsent] id 1 len 15
*Apr 23 08:55:23.727: Se7/0:3 LCP: AuthProto CHAP (0x0305C22305)
*Apr 23 08:55:23.727: Se7/0:3 LCP: MagicNumber 0x050E44FB (0x0506050E44FB)
*Apr 23 08:55:23.751: Se7/0:3 LCP: I CONFREQ [ACKrcvd] id 181 len 27
*Apr 23 08:55:23.751: Se7/0:3 LCP: MagicNumber 0x9028FFED (0x05069028FFED)
*Apr 23 08:55:23.751: Se7/0:3 LCP: EndpointDisc 1 user@cisco.com
*Apr 23 08:55:23.751: Se7/0:3 LCP: (0x1311017573657240636973636F2E636F)
*Apr 23 08:55:23.751: Se7/0:3 LCP: (0x6D)
*Apr 23 08:55:23.751: Se7/0:3 LCP: O CONFACK [ACKrcvd] id 181 len 27
*Apr 23 08:55:23.751: Se7/0:3 LCP: MagicNumber 0x9028FFED (0x05069028FFED)
*Apr 23 08:55:23.751: Se7/0:3 LCP: EndpointDisc 1 user@cisco.com
*Apr 23 08:55:23.751: Se7/0:3 LCP: (0x1311017573657240636973636F2E636F)
*Apr 23 08:55:23.751: Se7/0:3 LCP: (0x6D)
*Apr 23 08:55:23.751: Se7/0:3 LCP: State is Open
*Apr 23 08:55:23.751: Se7/0:3 PPP: Phase is AUTHENTICATING, by this end
*Apr 23 08:55:23.751: Se7/0:3 CHAP: O CHALLENGE id 1 len 24 from "LAC"
*Apr 23 08:55:23.803: Se7/0:3 CHAP: I RESPONSE id 1 len 35 from "user@cisco.com"
*Apr 23 08:55:23.803: Se7/0:3 PPP: Phase is FORWARDING, Attempting Forward
*Apr 23 08:55:23.807: Tnl/Sn 18693/19 L2TP: Session FS enabled
*Apr 23 08:55:23.807: Tnl/Sn 18693/19 L2TP: Session state change
from idle to wait-for-tunnel
*Apr 23 08:55:23.807: Se7/0:3 Tnl/Sn 18693/19 L2TP: Create session
*Apr 23 08:55:23.807: Tnl 18693 L2TP: SM State idle
*Apr 23 08:55:23.807: Tnl 18693 L2TP: O SCCRQ
*Apr 23 08:55:23.807: Tnl 18693 L2TP: Control channel retransmit delay
set to 1 seconds
*Apr 23 08:55:23.807: Tnl 18693 L2TP: Tunnel state change from idle to
wait-ctl-reply
*Apr 23 08:55:23.807: Tnl 18693 L2TP: SM State wait-ctl-reply
*Apr 23 08:55:23.815: Tnl 18693 L2TP: I SCCRP from LNS1
*Apr 23 08:55:23.815: Tnl 18693 L2TP: Got a challenge from remote peer, LNS1
*Apr 23 08:55:23.815: Tnl 18693 L2TP: Got a response from remote peer, LNS1
*Apr 23 08:55:23.815: Tnl 18693 L2TP: Tunnel Authentication success
*Apr 23 08:55:23.815: Tnl 18693 L2TP: Tunnel state change from
wait-ctl-reply to established
*Apr 23 08:55:23.815: Tnl 18693 L2TP: O SCCCN to LNS1 tnlid 28416
*Apr 23 08:55:23.815: Tnl 18693 L2TP: Control channel retransmit
delay set to 1 seconds
*Apr 23 08:55:23.815: Tnl 18693 L2TP: SM State established
*Apr 23 08:55:23.815: Se7/0:3 Tnl/Sn 18693/19 L2TP: O ICRQ to LNS1 28416/0
*Apr 23 08:55:23.815: Se7/0:3 Tnl/Sn 18693/19 L2TP: Session state change
from wait-for-tunnel to wai
t-reply
*Apr 23 08:55:23.831: Se7/0:3 Tnl/Sn 18693/19 L2TP: O ICCN to LNS1 28416/21
*Apr 23 08:55:23.831: Tnl 18693 L2TP: Control channel retransmit delay
set to 1 seconds
*Apr 23 08:55:23.831: Se7/0:3 Tnl/Sn 18693/19 L2TP: Session state change
from wait-reply to establis
hed
*Apr 23 08:55:23.831: Se7/0:3 Tnl/Sn 18693/19 L2TP: VPDN session up
*Apr 23 08:55:23.831: Se7/0:3 PPP: Phase is FORWARDED, Session Forwarded
*Apr 23 08:55:23.831: Se7/0:3 PPP: Process pending packets
LAC#
Debug Output - LNS1
The debug output on the LNS1 is as follows:
LNS1# .Apr 23 08:57:08.900: L2TP: I SCCRQ from LAC tnl 18693 .Apr 23 08:57:08.900: Tnl 28416 L2TP: Got a challenge in SCCRQ, LAC .Apr 23 08:57:08.900: Tnl 28416 L2TP: New tunnel created for remote LAC, address 10.48.74.128 .Apr 23 08:57:08.904: Tnl 28416 L2TP: O SCCRP to LAC tnlid 18693 .Apr 23 08:57:08.904: Tnl 28416 L2TP: Control channel retransmit delay set to 1 seconds .Apr 23 08:57:08.904: Tnl 28416 L2TP: Tunnel state change from idle to wait-ctl-reply .Apr 23 08:57:08.908: Tnl 28416 L2TP: I SCCCN from LAC tnl 18693 .Apr 23 08:57:08.908: Tnl 28416 L2TP: Got a Challenge Response in SCCCN from LAC .Apr 23 08:57:08.912: Tnl 28416 L2TP: Tunnel Authentication success .Apr 23 08:57:08.912: Tnl 28416 L2TP: Tunnel state change from wait-ctl-reply to established .Apr 23 08:57:08.912: Tnl 28416 L2TP: SM State established .Apr 23 08:57:08.912: Tnl 28416 L2TP: I ICRQ from LAC tnl 18693 .Apr 23 08:57:08.916: Tnl/Sn 28416/21 L2TP: Session FS enabled .Apr 23 08:57:08.916: Tnl/Sn 28416/21 L2TP: Session state change from idle to wait-connect .Apr 23 08:57:08.916: Tnl/Sn 28416/21 L2TP: New session created .Apr 23 08:57:08.916: Tnl/Sn 28416/21 L2TP: O ICRP to LAC 18693/19 .Apr 23 08:57:08.920: Tnl 28416 L2TP: Control channel retransmit delay set to 1 seconds .Apr 23 08:57:08.924: Tnl/Sn 28416/21 L2TP: I ICCN from LAC tnl 18693, cl 19 .Apr 23 08:57:08.924: user@cisco.com Tnl/Sn 28416/21 L2TP: Session state change from wait-connect to wait-for-service-selection .Apr 23 08:57:08.932: ppp13 PPP: Phase is ESTABLISHING .Apr 23 08:57:08.932: ppp13 LCP: I FORCED rcvd CONFACK len 11 .Apr 23 08:57:08.932: ppp13 LCP: AuthProto CHAP (0x0305C22305) .Apr 23 08:57:08.936: ppp13 LCP: MagicNumber 0x050E44FB (0x0506050E44FB) .Apr 23 08:57:08.936: ppp13 LCP: I FORCED sent CONFACK len 23 .Apr 23 08:57:08.936: ppp13 LCP: MagicNumber 0x9028FFED (0x05069028FFED) .Apr 23 08:57:08.936: ppp13 LCP: EndpointDisc 1 user@cisco.com .Apr 23 08:57:08.936: ppp13 LCP: (0x1311017573657240636973636F2E636F) .Apr 23 08:57:08.936: ppp13 LCP: (0x6D) .Apr 23 08:57:08.940: ppp13 PPP: Phase is FORWARDING, Attempting Forward .Apr 23 08:57:08.948: Tnl/Sn 30255/22 L2TP: Session FS enabled .Apr 23 08:57:08.952: Tnl/Sn 30255/22 L2TP: Session state change from idle to wait-for-tunnel .Apr 23 08:57:08.952: uid:13 Tnl/Sn 30255/22 L2TP: Create session .Apr 23 08:57:08.952: Tnl 30255 L2TP: SM State idle .Apr 23 08:57:08.952: Tnl 30255 L2TP: O SCCRQ .Apr 23 08:57:08.956: Tnl 30255 L2TP: Control channel retransmit delay set to 1 seconds .Apr 23 08:57:08.956: Tnl 30255 L2TP: Tunnel state change from idle to wait-ctl-reply .Apr 23 08:57:08.956: Tnl 30255 L2TP: SM State wait-ctl-reply .Apr 23 08:57:08.960: Tnl 30255 L2TP: I SCCRP from LNS2 .Apr 23 08:57:08.960: Tnl 30255 L2TP: Got a challenge from remote peer, LNS2 .Apr 23 08:57:08.964: Tnl 30255 L2TP: Got a response from remote peer, LNS2 .Apr 23 08:57:08.964: Tnl 30255 L2TP: Tunnel Authentication success .Apr 23 08:57:08.964: Tnl 30255 L2TP: Tunnel state change from wait-ctl-reply to established .Apr 23 08:57:08.964: Tnl 30255 L2TP: O SCCCN to LNS2 tnlid 35837 .Apr 23 08:57:08.968: Tnl 30255 L2TP: Control channel retransmit delay set to 1 seconds .Apr 23 08:57:08.968: Tnl 30255 L2TP: SM State established .Apr 23 08:57:08.968: uid:13 Tnl/Sn 30255/22 L2TP: O ICRQ to LNS2 35837/0 .Apr 23 08:57:08.968: uid:13 Tnl/Sn 30255/22 L2TP: Session state change from wait-for-tunnel to wait-reply .Apr 23 08:57:08.972: uid:13 Tnl/Sn 30255/22 L2TP: O ICCN to LNS2 35837/9 .Apr 23 08:57:08.976: Tnl 30255 L2TP: Control channel retransmit delay set to 1 seconds .Apr 23 08:57:08.976: uid:13 Tnl/Sn 30255/22 L2TP: Session state change from wait-reply to established .Apr 23 08:57:08.976: uid:13 Tnl/Sn 30255/22 L2TP: VPDN session up .Apr 23 08:57:08.980: ppp13 PPP: Phase is FORWARDED, Session Forwarded .Apr 23 08:57:08.984: user@cisco.com Tnl/Sn 28416/21 L2TP: Session state change from wait-for-service-selection to established .Apr 23 08:57:08.984: user@cisco.com Tnl/Sn 28416/21 L2TP: VPDN session up .Apr 23 08:57:08.984: ppp13 PPP: Process pending ncp packets LNS1#
Debug Output - LNS2
The debug output on the LNS2 is as follows:
LNS2# *Apr 23 08:57:59.615: L2TP: I SCCRQ from LNS1 tnl 30255 *Apr 23 08:57:59.615: Tnl 35837 L2TP: Got a challenge in SCCRQ, LNS1 *Apr 23 08:57:59.615: Tnl 35837 L2TP: New tunnel created for remote LNS1, address 10.11 .0.1 *Apr 23 08:57:59.615: Tnl 35837 L2TP: O SCCRP to LNS1 tnlid 30255 *Apr 23 08:57:59.615: Tnl 35837 L2TP: Control channel retransmit delay set to 1 seconds *Apr 23 08:57:59.615: Tnl 35837 L2TP: Tunnel state change from idle to wait-ctl-reply *Apr 23 08:57:59.623: Tnl 35837 L2TP: I SCCCN from LNS1 tnl 30255 *Apr 23 08:57:59.623: Tnl 35837 L2TP: Got a Challenge Response in SCCCN from LNS1 *Apr 23 08:57:59.623: Tnl 35837 L2TP: Tunnel Authentication success *Apr 23 08:57:59.623: Tnl 35837 L2TP: Tunnel state change from wait-ctl-reply to establ ished *Apr 23 08:57:59.623: Tnl 35837 L2TP: SM State established *Apr 23 08:57:59.627: Tnl 35837 L2TP: I ICRQ from LNS1 tnl 30255 *Apr 23 08:57:59.627: Tnl/Sn 35837/9 L2TP: Session FS enabled *Apr 23 08:57:59.627: Tnl/Sn 35837/9 L2TP: Session state change from idle to wait-conne ct *Apr 23 08:57:59.627: Tnl/Sn 35837/9 L2TP: New session created *Apr 23 08:57:59.627: Tnl/Sn 35837/9 L2TP: O ICRP to LNS1 30255/22 *Apr 23 08:57:59.627: Tnl 35837 L2TP: Control channel retransmit delay set to 1 seconds *Apr 23 08:57:59.635: Tnl/Sn 35837/9 L2TP: I ICCN from LNS1 tnl 30255, cl 22 *Apr 23 08:57:59.635: user@cisco.com Tnl/Sn 35837/9 L2TP: Session state change from wait - connect to wait-for-service-selection *Apr 23 08:57:59.635: ppp8 PPP: Phase is ESTABLISHING *Apr 23 08:57:59.635: ppp8 LCP: I FORCED rcvd CONFACK len 11 *Apr 23 08:57:59.635: ppp8 LCP: AuthProto CHAP (0x0305C22305) *Apr 23 08:57:59.635: ppp8 LCP: MagicNumber 0x050E44FB (0x0506050E44FB) *Apr 23 08:57:59.635: ppp8 LCP: I FORCED sent CONFACK len 23 *Apr 23 08:57:59.635: ppp8 LCP: MagicNumber 0x9028FFED (0x05069028FFED) *Apr 23 08:57:59.635: ppp8 LCP: EndpointDisc 1 user@cisco.com *Apr 23 08:57:59.635: ppp8 LCP: (0x1311017573657240636973636F2E636F) *Apr 23 08:57:59.635: ppp8 LCP: (0x6D) *Apr 23 08:57:59.635: ppp8 PPP: Phase is FORWARDING, Attempting Forward *Apr 23 08:57:59.639: ppp8 PPP: Phase is AUTHENTICATING, Unauthenticated User *Apr 23 08:57:59.639: ppp8 PPP: Phase is FORWARDING, Attempting Forward *Apr 23 08:57:59.639: VT[Vi2]:Sending vaccess request, id 0x73000015 *Apr 23 08:57:59.639: VT:Processing vaccess requests, 1 outstanding *Apr 23 08:57:59.639: VT:Create and clone subif, base Vi2 Vt1 *Apr 23 08:57:59.639: VT[Vi2.1]:Reuse subinterface, recycle queue size 1 *Apr 23 08:57:59.639: VT[Vi2.1]:Recycled subinterface becomes Vi2.1 *Apr 23 08:57:59.639: VT[Vi2.1]:Cloning a recycled vaccess *Apr 23 08:57:59.639: VT[Vi2.1]:Processing vaccess response, id 0x73000015, result success (1) *Apr 23 08:57:59.643: Vi2.1 Tnl/Sn 35837/9 L2TP: Virtual interface created for user@cisco.com, bandwidth 64 Kbps *Apr 23 08:57:59.643: Vi2.1 Tnl/Sn 35837/9 L2TP: VPDN session up *Apr 23 08:57:59.643: Vi2.1 Tnl/Sn 35837/9 L2TP: Session state change from wait-for-service-selection to established *Apr 23 08:57:59.643: Vi2.1 PPP: Phase is AUTHENTICATING, Authenticated User *Apr 23 08:57:59.643: Vi2.1 CHAP: O SUCCESS id 1 len 4 *Apr 23 08:57:59.643: Vi2.1 PPP: Phase is UP *Apr 23 08:57:59.643: Vi2.1 PPP: Process pending ncp packets *Apr 23 08:57:59.643: Vi2.1 IPCP: O CONFREQ [Closed] id 1 len 10 *Apr 23 08:57:59.643: Vi2.1 IPCP: Address 192.168.1.1 (0x0306C0A80101) *Apr 23 08:57:59.667: Vi2.1 IPCP: I CONFREQ [REQsent] id 125 len 10 *Apr 23 08:57:59.667: Vi2.1 IPCP: Address 0.0.0.0 (0x030600000000) *Apr 23 08:57:59.667: Vi2.1 AAA/AUTHOR/IPCP: Start. Her address 0.0.0.0, we want 0.0.0.0 *Apr 23 08:57:59.667: Vi2.1 AAA/AUTHOR/IPCP: Done. Her address 0.0.0.0, we want 0.0.0.0 *Apr 23 08:57:59.667: Vi2.1: Pools to search : VpdnUsers *Apr 23 08:57:59.667: Vi2.1: Pool VpdnUsers returned address = 192.168.1.2 *Apr 23 08:57:59.667: Vi2.1 IPCP: Pool returned 192.168.1.2 *Apr 23 08:57:59.667: Vi2.1 IPCP: O CONFNAK [REQsent] id 125 len 10 *Apr 23 08:57:59.667: Vi2.1 IPCP: Address 192.168.1.2 (0x0306C0A80102) *Apr 23 08:57:59.683: Vi2.1 IPCP: I CONFACK [REQsent] id 1 len 10 *Apr 23 08:57:59.683: Vi2.1 IPCP: Address 192.168.1.1 (0x0306C0A80101) *Apr 23 08:57:59.699: Vi2.1 IPCP: I CONFREQ [ACKrcvd] id 126 len 10 *Apr 23 08:57:59.699: Vi2.1 IPCP: Address 192.168.1.2 (0x0306C0A80102) *Apr 23 08:57:59.699: Vi2.1 IPCP: O CONFACK [ACKrcvd] id 126 len 10 *Apr 23 08:57:59.699: Vi2.1 IPCP: Address 192.168.1.2 (0x0306C0A80102) *Apr 23 08:57:59.699: Vi2.1 IPCP: State is Open *Apr 23 08:57:59.703: Vi2.1 IPCP: Install route to 192.168.1.2 *Apr 23 08:57:59.703: Vi2.1 IPCP: Add link info for cef entry 192.168.1.2 LNS2#
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
19-Nov-2007 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback