Cisco Nexus 1000V Switch for Microsoft Hyper-V Data Sheet
Available Languages
Product Overview
Cisco Nexus® 1000V Switches provide a comprehensive and extensible architectural platform for virtual machine and cloud networking. The switches are designed to accelerate server virtualization and multitenant cloud deployments in a secure and operationally transparent manner.
The Cisco Nexus 1000V Switch for Microsoft Hyper-V is a distributed software switching platform for Microsoft Windows Server 2012 environments. It provides:
● Advanced Cisco® NX-OS Software feature set and associated partner ecosystem
● Innovative network services architecture to support scalable, multitenant environments
● Consistent operating model across physical and virtual environments and across hypervisors
● Tight integration with Microsoft System Center Virtual Machine Manager (SCVMM) 2012 SP1
The Cisco Nexus 1000V Switch brings the robust architecture associated with traditional Cisco physical modular switches to Microsoft Hyper-V environments. The solution has two main components (Figure 1):
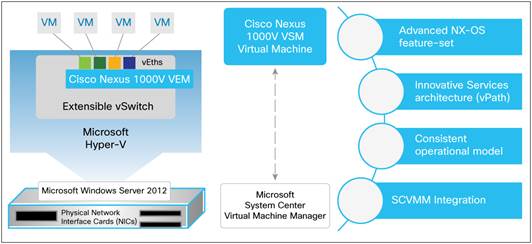
● The Cisco Nexus 1000V virtual Ethernet module (VEM) is a software component deployed on each Microsoft Hyper-V host as a forwarding extension. Each virtual machine on the host is connected to the VEM through virtual Ethernet (vEth) ports.
● The Cisco Nexus 1000V virtual supervisor module (VSM) is the management component that controls multiple VEMs and helps in the definition of virtual machine-focused network policies. It is a virtual machine running Cisco NX-OS on a Microsoft Hyper-V host and is similar to the supervisor module on a physical modular switch.
In addition to the VEM and VSM, Cisco Nexus 1000V Switches include Cisco vPath technology and provide a scalable, multitenant network services infrastructure for Microsoft Hyper-V environments.
For customers seeking a dedicated hardware appliance to host all virtual appliances relevant to the Cisco Nexus 1000V Switch (the VSM and other virtual services blades), Cisco offers the Cisco Nexus 1100 Virtual Services Appliances. With the Cisco Nexus 1110, all critical Cisco Nexus virtual appliances are hosted on a single platform, reducing operational complexity.
The Cisco Nexus 1000V uses the extensible switch framework offered by Microsoft Windows Server 2012 with Hyper-V and the management ecosystem offered by Microsoft SCVMM 2012 SP1 and thus provides a transparent operating experience for Microsoft Hyper-V environments.
Benefits
Cisco Nexus 1000V Switches reduce the operational complexities associated with virtual machine networking and thus help customers gain more of the benefits of server virtualization technology. They offer the following benefits:
● Preserve your existing investments in operational processes and management tools.
◦ Network administrators can manage network policies across both physical and virtual environments using the same interfaces, and staff does not need to be retrained.
◦ Customers can use existing network monitoring, management, and troubleshooting tools to manage both physical and virtual environments.
● Simplify your virtual networking operations.
◦ Visibility into the traffic between virtual machines simplifies network troubleshooting.
◦ Virtualization-aware networking features simplify virtual machine network policy management.
◦ Tight integration with Microsoft SCVMM allows faster policy provisioning.
● Provide better security.
◦ Virtualization-aware networking provides better security by extending network policies and network visibility to the virtual machine level.
Features
Cisco Nexus 1000V offers advanced networking features to Microsoft Hyper-V environments, including:
● Advanced switching features such as private virtual LANs (PVLANs), quality of service (QoS), access control lists (ACLs), port security, and Cisco vPath
● Security features such as Dynamic Host Configuration Protocol (DHCP) snooping, Dynamic Address Resolution Protocol (ARP) Inspection, and IP source guard
● Monitoring features such as Cisco NetFlow, packet statistics, Switched Port Analyzer (SPAN), and Encapsulated Remote SPAN (ERSPAN)
● Manageability features such as Simple Network Management Protocol (SNMP), NetConf, syslog, and advanced troubleshooting command-line interface (CLI) features
● Virtual services using Cisco vPath such as Cisco Virtual Security Gateway (VSG)
Virtualized Network Services with Cisco vPath
Cisco vPath is an innovative architecture that extends the Cisco Nexus 1000V platform to support multiple network services, including firewalls, load balancers, and WAN-optimization services.
The Cisco vPath architecture provides:
● Intelligent traffic steering
◦ Redirect traffic from the server requesting network service to the virtual services node (VSN).
◦ Extend the port profile to include the network services profile.
● Flexible deployment
◦ Each VSN can serve multiple physical servers.
◦ The VSN can be hosted on a separate or dedicated server.
● Network service acceleration
◦ Using network service decision caching, the Cisco Nexus 1000V remembers network service policy from prior traffic, reducing the need for traffic steering.
◦ The performance of virtual network services can be accelerated through enforcement in the hypervisor kernel.
Integration with Microsoft Hyper-V and SCVMM
The Cisco Nexus 1000V VEM is a forwarding extension in the Microsoft Hyper-V extensible switch framework, and it is deployed on each Microsoft Hyper-V host managed by the Cisco Nexus 1000V. The Cisco Nexus 1000V VSM communicates with VEMs as well as with Microsoft SCVMM. All configuration policies defined on the VSM are automatically propagated to Microsoft SCVMM, so the Microsoft SCVMM administrator can use these policies when creating virtual machines.
The Microsoft SCVMM networking model introduces multiple user-defined constructs, including logical networks, network sites, and virtual machine networks to abstract the underlying physical network. A new CLI has been added to the Cisco Nexus 1000V Switch to define these constructs from the VSM.
Figure 2 shows the operating model for the Cisco Nexus 1000V Switch for Microsoft Hyper-V.

Security
The Cisco Nexus 1000V includes Cisco integrated security features that are found on Cisco physical switches to prevent a variety of attack scenarios, as shown in Table 1. In addition, Cisco Virtual Security Gateway (VSG) a virtual firewall available on the Cisco Nexus 1000V, allows you to provide secure logical isolation of virtual machines in a multitenant Microsoft Hyper-V environment.
Table 1. Cisco Integrated Security Features
| Feature |
Capability |
Prevents |
| Port security |
●
Restricts MAC addresses on a port
|
●
MAC address spoofing by rogue virtual machine
|
| IP source guard |
●
Maps IP addresses to MAC addresses
|
●
IP and MAC address spoofing
|
| Dynamic ARP Inspection |
●
Monitors virtual machine ARP transactions, which are also used for VMware vMotion
|
●
ARP cache poisoning on other virtual machines, hosts, and network devices
|
| DHCP snooping |
●
Prevents DHCP client requests from reaching untrusted entities
●
Prevents untrusted entities from acting as DHCP servers
●
Rate-limits DHCP requests to prevent denial-of-service (DoS) attacks
|
●
Rogue DHCP servers
●
DoS to DHCP services
|
High Availability
The Cisco Nexus 1000V is designed to be resilient, and high-availability is built into the system at multiple levels:
● Cisco NX-OS, the OS run by the VSM, is specifically designed for high availability at the network, system, and process levels. Critical processes run independently for ease of isolation, fault containment, and upgrading. Processes can restart independently in milliseconds without losing state information, affecting data forwarding, or affecting adjacent devices or services.
● VSMs are typically deployed in active-standby pairs for high availability. The state and configuration remain constantly synchronized between the two VSMs to provide stateful switchover if the active VSM fails.
VSM and VEM communication is built for reliability. In the event of loss of communication with the VSM, the VEMs can use nonstop forwarding (NSF) to continue to switch traffic according to the last-known configuration.
Maximum Supported Configurations
● 64 Microsoft Windows Server 2012 with Hyper-V hosts per VSM
● 2048 virtual Ethernet ports per VSM, with 216 virtual Ethernet ports per physical host
● 2048 active VLANs
● 2048 port profiles
● 32 physical NICs per physical host
System Requirements
● Microsoft Windows Server 2012 or later (Standard or Data Center)
● Microsoft SCVMM 2012 SP1 (UR2) or later
● Cisco Nexus 1000V VSM
◦ The VSM can be deployed as a virtual machine on Microsoft Windows Server 2012 with Hyper-V or on a Cisco Nexus 1110 appliance
◦ Hard disk: 4 GB
◦ RAM: 4 GB
● Compatible with any upstream physical switches, including all Cisco Nexus and Cisco Catalyst® switches as well as Ethernet switches from other vendors
Essential and Advanced Editions
Cisco Nexus 1000V Switches are offered in two editions:
● Essential Edition: Provides all the basic Layer 2 networking features needed for your Microsoft Hyper-V environments and is available at no cost; this free version enables you to adopt Cisco's virtual network technology without any cost or risk
● Advanced Edition: Includes Cisco VSG, a virtual firewall, and other advanced security capabilities such as DHCP snooping, IP source guard, and Dynamic ARP Inspection
Table 2 summarizes the features of the Cisco Nexus 1000V Editions
Table 2. Feature Comparison of Nexus 1000V Editions
| Feature |
Essential (Free) |
Advanced |
| VLANs, PVLANs, ACLs, QoS, Link Aggregation Control Protocol (LACP), and multicast |
Yes |
Yes |
| Cisco vPath (for virtual services) |
Yes |
Yes |
| Cisco NetFlow, SPAN, and ERSPAN (for traffic visibility) |
Yes |
Yes |
| SNMP, NetConf, syslogs, etc. (for manageability) |
Yes |
Yes |
| Microsoft SCVMM integration |
Yes |
Yes |
| DHCP snooping |
|
Yes |
| IP source guard |
|
Yes |
| Dynamic ARP Inspection |
|
Yes |
| Cisco VSG* |
|
Yes |
Licensing and Ordering Information
The Cisco Nexus 1000V Switch is licensed based on the number of physical CPUs on the server on which the VEM is running. Table 3 provides ordering information for the Cisco Nexus 1000V Switch.
Table 3. Ordering Information
Cisco Services
Cisco Software Application Support plus Upgrades (SASU) is a comprehensive support service that helps you maintain and enhance the availability, security, and performance of your business-critical applications. Cisco SASU includes the following resources:
● Software updates and upgrades: The Cisco SASU service provides timely, uninterrupted access to software updates and upgrades to help you keep existing systems stable and network release levels current. Update releases, including major upgrade releases that may include significant architectural changes and new capabilities for your licensed feature set, are available by software download from Cisco.com or by CD-ROM shipment.
● Cisco Technical Assistance Center (TAC): Cisco TAC engineers provide accurate, rapid diagnosis and resolution of software application problems to help you reduce outages and performance degradation. These specialized software application experts are trained to support the Cisco Nexus 1000V Switch. Their expertise is available to you 24 hours a day, 365 days a year, by telephone, fax, email, or the Internet.
● Online support: Cisco SASU provides access to a wide range of online tools and communities to help you resolve problems quickly, support business continuity, and improve competitiveness.
For More Information
● For more information about the Cisco Nexus 1000V Switch, visit http://www.cisco.com/go/1000v/hyper-v.
● For more information about the Cisco Nexus 1100 Series Cloud Services Platforms, visit http://www.cisco.com/go/1100.
● For more information about the Cisco Virtual Security Gateway, visit http://www.cisco.com/go/vsg.
● For more information about the Cisco Nexus 1000V community, visit http://communities.cisco.com/community/technology/datacenter/nexus1000v.
● For more information about Cisco NX-OS Software, visit http://www.cisco.com/go/nxos.
● For more information about Microsoft Hyper-V, visit http://www.microsoft.com/hyper-v.
● For more information about Microsoft System Center Virtual Machine Manager, visit http://www.microsoft.com/scvmm.
● For more information about how Cisco and Microsoft are working together, visit http://www.cisco.com/go/microsoft.
 Feedback
Feedback