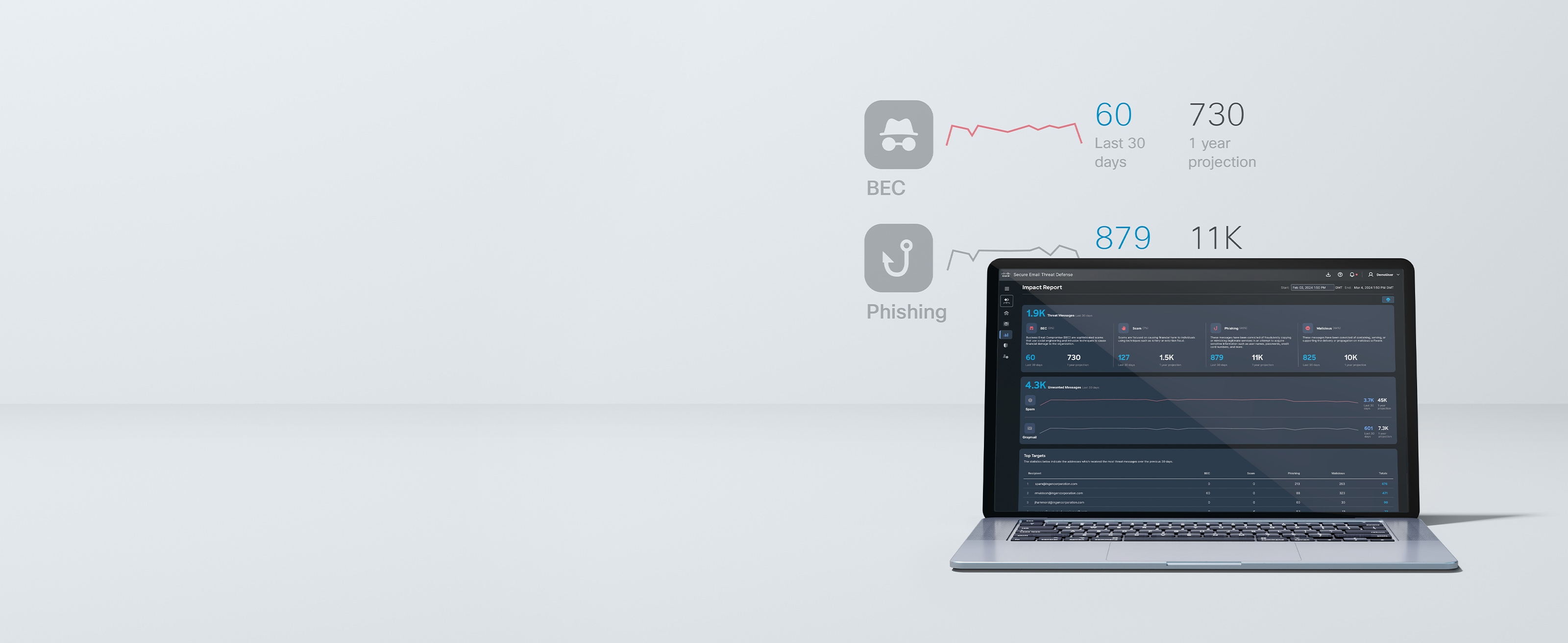
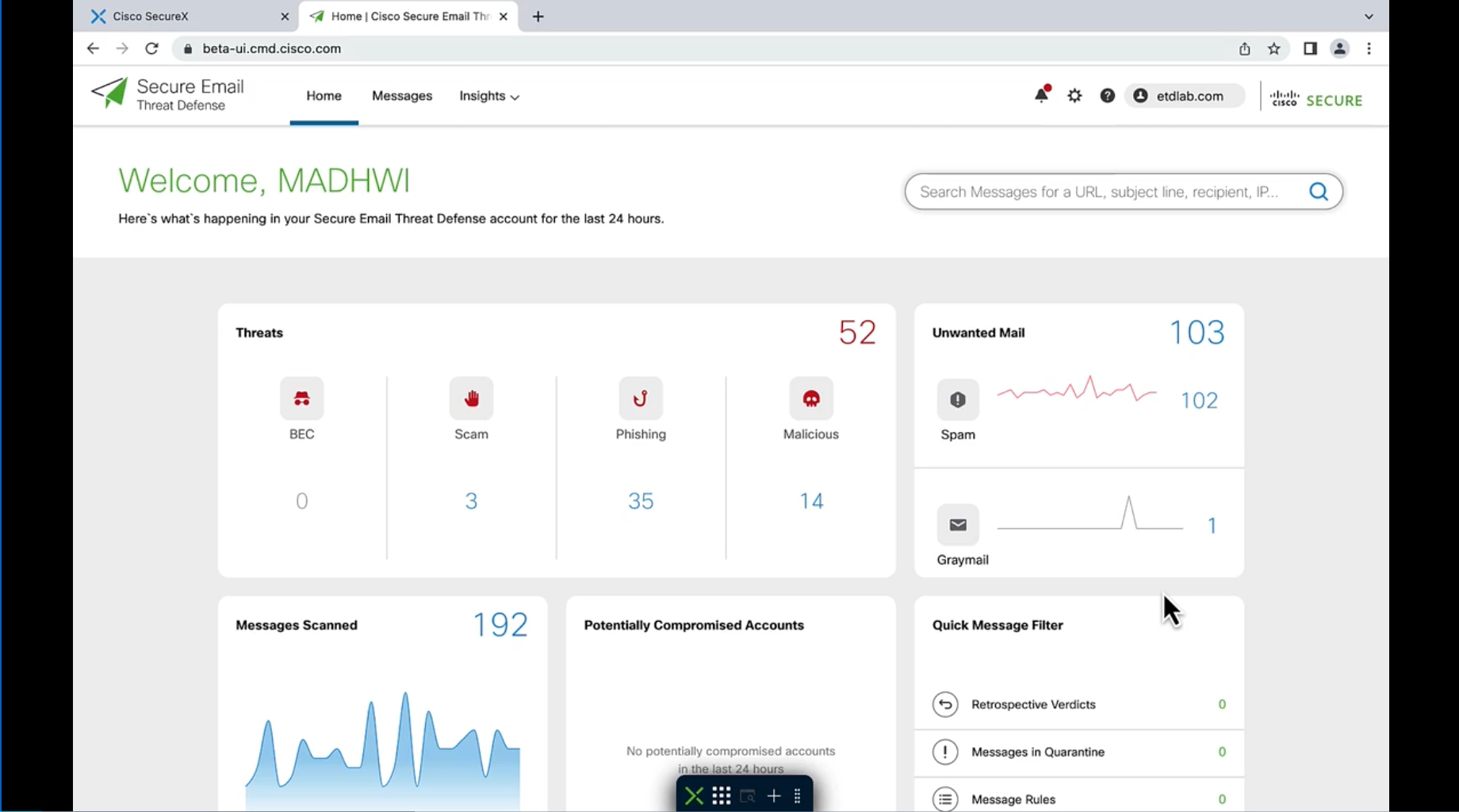
Comprehensive defense for the most damaging threats
Expansive email security protects your employees and organization, while empowering your security response.
Better together
Licensing made easy
Pricing
Pricing for Secure Email Threat Defense is on a per-user basis, which means it applies to a single-knowledge worker.
Terms
All subscriptions have flexible options, including 1-, 3-, and 5-year terms with significant savings on multiyear options. There is no extra charge for scheduled billing (monthly, quarterly, yearly, or full payment).
Financing
All subscriptions can be included in larger Cisco buying programs (Security Bundles, Enterprise Agreements) and can engage Cisco Capital for financing options.
Support
All subscriptions include Cisco Technical Assistance Center (TAC) support (24/7) and customer success for onboarding assistance.